Counter Mode Output Feedback Mode Network Security 1

Counter Mode, Output Feedback Mode Network Security 1
Counter Mode, Output Feedback Mode Objectives of the Topic • After completing this topic, a student will be able to – explain counter and output feedback modes. 2

Counter Mode, Output Feedback Mode Figures and material in this topic have been adapted from • “Network Security Essentials”, 2014, by William Stallings. • W. Stallings, “Crypto. and Network Security Principles and Practice”, Pearson Education, 2014 3
Counter Mode, Output Feedback Mode • Electronic Codebook Mode (ECB) • Cipher Block Chaining Mode (CBC) • Cipher Feedback Mode (CFB) • Output Feedback (OFB) • Counter Mode (CTR) 4
Counter Mode, Output Feedback Mode • Similar in structure to that of CFB. • For OFB, the output of encryption function is fed back to become the input for encrypting the next block of plaintext. 5
Counter Mode, Output Feedback Mode • The OFB mode operates on full blocks of plaintext and ciphertext, whereas CFB operates on an sbit subset. 6
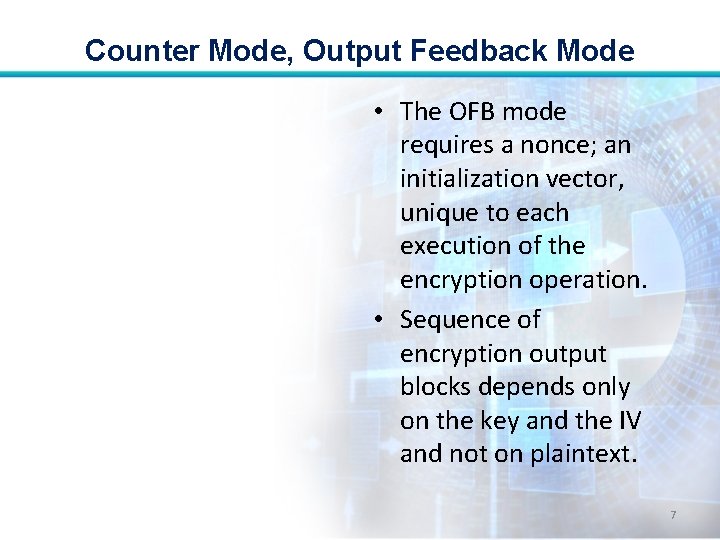
Counter Mode, Output Feedback Mode • The OFB mode requires a nonce; an initialization vector, unique to each execution of the encryption operation. • Sequence of encryption output blocks depends only on the key and the IV and not on plaintext. 7

Counter Mode, Output Feedback Mode 8
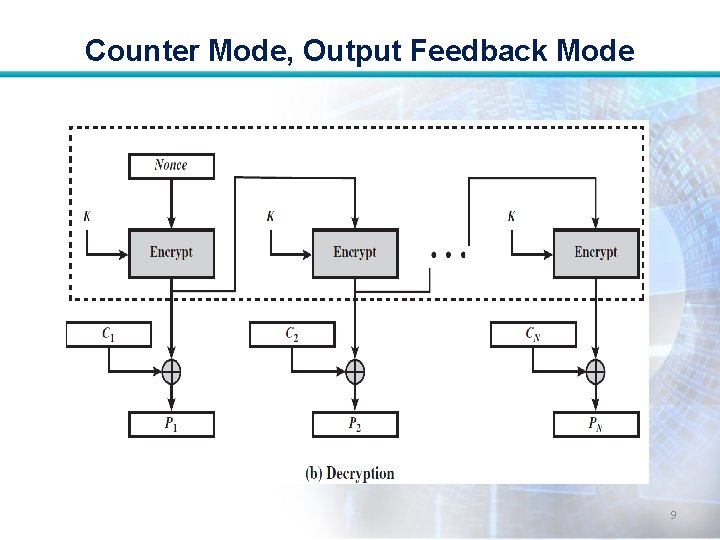
Counter Mode, Output Feedback Mode 9
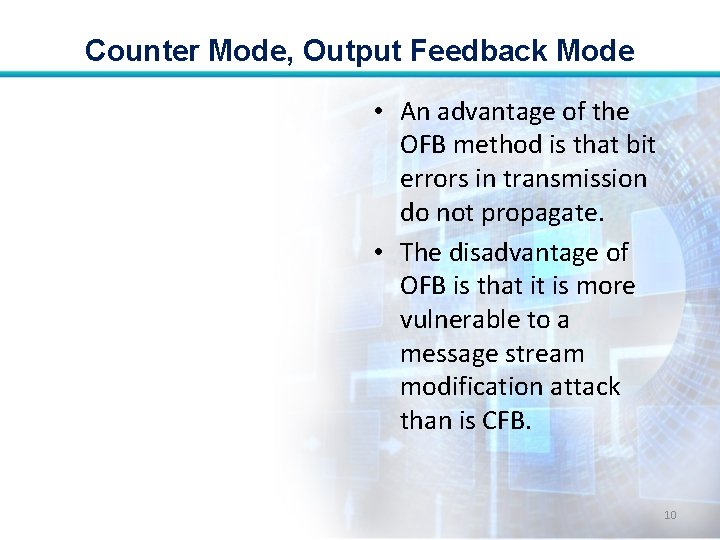
Counter Mode, Output Feedback Mode • An advantage of the OFB method is that bit errors in transmission do not propagate. • The disadvantage of OFB is that it is more vulnerable to a message stream modification attack than is CFB. 10
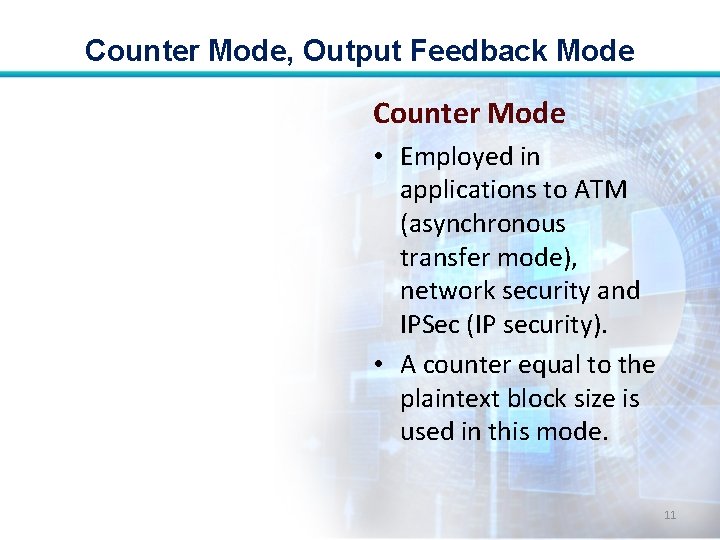
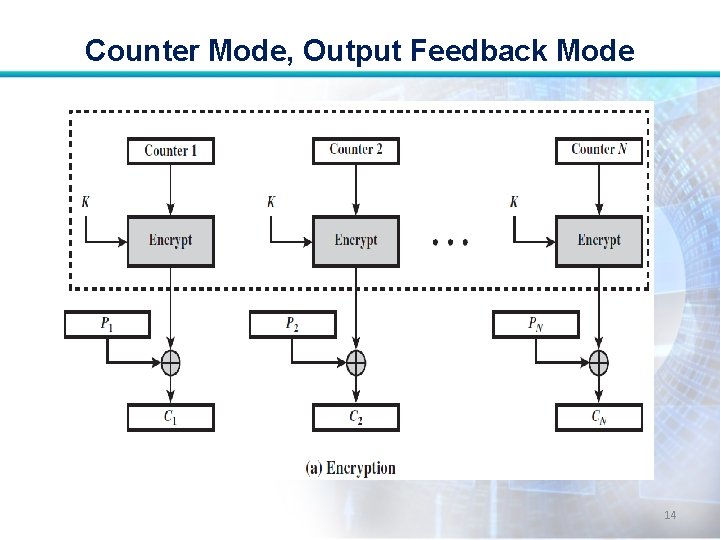
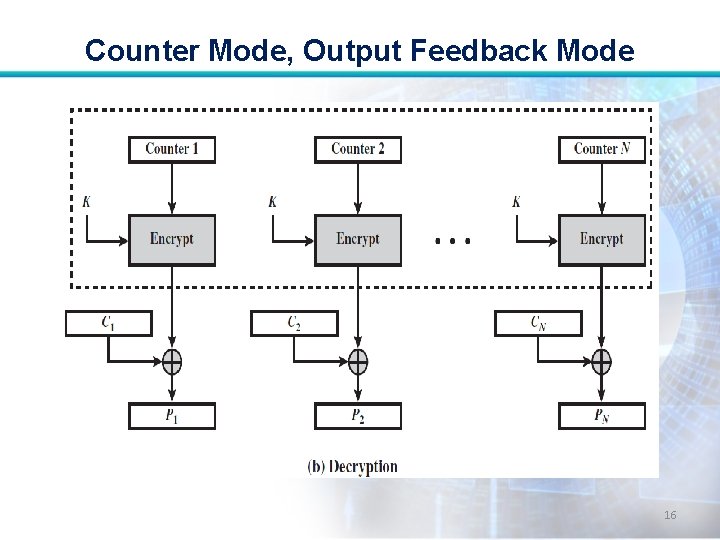
Counter Mode, Output Feedback Mode Counter Mode • Employed in applications to ATM (asynchronous transfer mode), network security and IPSec (IP security). • A counter equal to the plaintext block size is used in this mode. 11
Counter Mode, Output Feedback Mode • The counter value must be different for each plaintext block that is encrypted. • Typically, the counter is initialized to some value and then incremented by 1 for each subsequent block (modulo 2 b, where b is block size). 12
Counter Mode, Output Feedback Mode • For encryption, the counter is encrypted and then XORed with the plaintext block to produce the ciphertext block. • There is no chaining. 13
Counter Mode, Output Feedback Mode 14
Counter Mode, Output Feedback Mode • For decryption, the same sequence of counter values is used, with each encrypted counter XORed with a ciphertext block to recover the corresponding plaintext block. 15
Counter Mode, Output Feedback Mode 16
Counter Mode, Output Feedback Mode Advantages of Counter Mode: • Preprocessing • when the plaintext or ciphertext input is presented, the only computation is a series of XORs, greatly enhancing throughput. 17
Counter Mode, Output Feedback Mode • Random access • The ith block of plaintext or ciphertext can be processed in random-access fashion • Provable security • CTR can be shown to be at least as secure as the other modes. 18
Counter Mode, Output Feedback Mode • Hardware efficiency • Encryption/decryption can be done in parallel on multiple blocks of plaintext or ciphertext • Software efficiency • Processors that support parallel features can be effectively utilized. 19
Counter Mode, Output Feedback Mode • Simplicity • Requires only the implementation of the encryption algorithm and not the decryption algorithm End 20
- Slides: 20