COT 5611 Operating Systems Design Principles Spring 2012












- Slides: 42

COT 5611 Operating Systems Design Principles Spring 2012 Dan C. Marinescu Office: HEC 304 Office hours: M-Wd 5: 00 -6: 00 PM

Lecture 10 - Monday February 13 n n Reading assignment: Chapter 7 from the on-line text Last time: Design principles for computer and communication systems Interesting Properties of Networks Isochronous and Asynchronous Multiplexing ¨ Packet Forwarding; Delay ¨ Queuing models for delay determination ¨ 12/19/2021 Lecture 10 2

Today n n n The M/M/1 Queuing model Store and Forward Networks The Internet Layering The Link Layer Bit framing ¨ Frames ¨ Errors ¨ Link properties ¨ 12/19/2021 Lecture 10 3

Delays and waiting time when a resource is shared n n Queuing theory describes systems where you have a shared resource – a server - and customers and both the arrival of the customers and the time it takes to service them are random variables with a certain distribution. There are two stochastic processes involved: Arrival ¨ Service ¨ 12/19/2021 Lecture 10 4

Customer arrival n n n The arrival process describes the pattern of the customers arrive characterized by its probability distribution function e. g. , a uniform, exponential. The distribution can described by one or more parameters such as the average value of the random variables subject to that distribution, e. g. , the arrival rate denoted as �� ¸ or the inter-arrival time (the average time between two consecutive customer arrivals), 1/ ��. For example, if customers arrive in average at two minutes intervals the arrival rate is 1/2 customers/minute and the inter-arrival time is 2 minutes. 12/19/2021 Lecture 10 5

Customer service n n n The service process describes how customers are served. The service processes is characterized by its probability distribution function e. g. , a uniform, exponential, hyper exponential. The distribution can described by ¨ the service rate �� or ¨ n the service time (the average time between two consecutive customer departures from the system) 1/ �� For example, if the service rate is �� = 10 customers per hour, then the service time is 1/ �� = 60 minutes/10 = 5 minutes. 12/19/2021 Lecture 10 6

The pattern of customer behavior n n The customer arrives in the system and joins a waiting queue. The time spent waiting is called waiting time and it is denoted as W. When its turn arrives the customer enters service and the service time is 1/�� When the service is terminated the customer leaves the system. The time spent the customer is called the time in system T = W + 1/��. N is the total number of customers in system, one is in service and (N-1) are waiting in the queue. 12/19/2021 Lecture 10 7

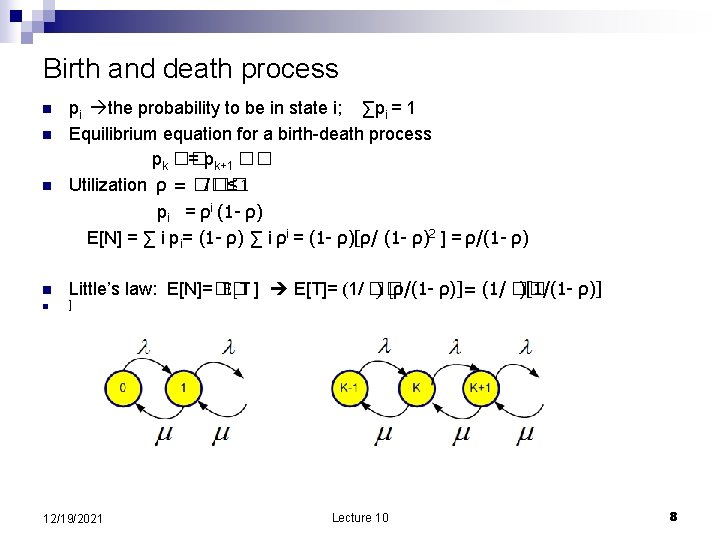
Birth and death process n n n pi the probability to be in state i; ∑pi = 1 Equilibrium equation for a birth-death process pk �� = pk+1 �� Utilization ρ = �� / �� ≤ 1 pi = ρi (1 - ρ) E[N] = ∑ i pi= (1 - ρ) ∑ i ρi = (1 - ρ)[ρ/ (1 - ρ)2 ] = ρ/(1 - ρ) Little’s law: E[N]=�� E[T ] E[T]= (1/ �� ) [ρ/(1 - ρ)]= (1/ �� )[1/(1 - ρ)] ] 12/19/2021 Lecture 10 8

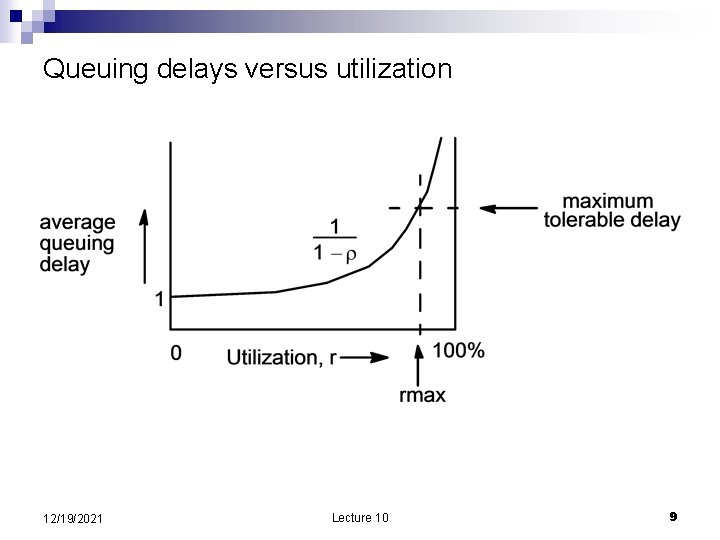
Queuing delays versus utilization 12/19/2021 Lecture 10 9

Store and Forward Networks n Vast range of: Data rates ¨ Propagation, transmission, queuing, and processing delays ¨ Loads ¨ Number of users ¨ n Problems Noise ¨ Changes in topology – links and routers fail ¨ n Best-effort networks ¨ ¨ ¨ Variable delays Variable transmission rates Discarded packets Duplicated packets Maximum packet length limitation on some links Reordered delivery 12/19/2021 Lecture 10 10

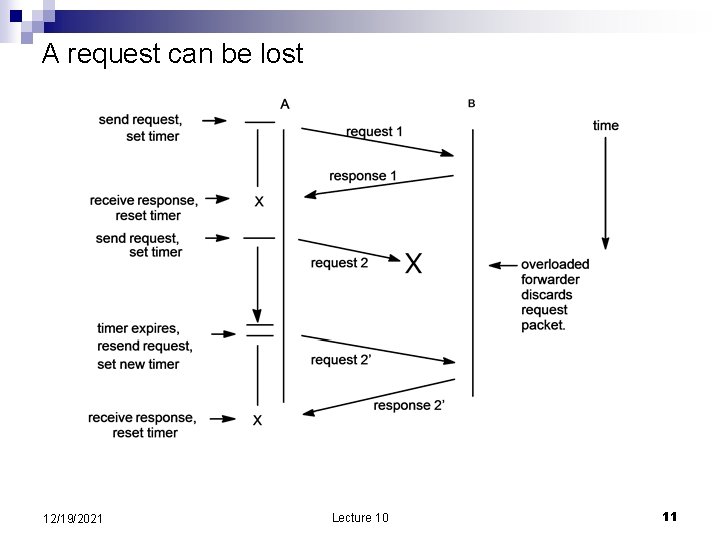
A request can be lost 12/19/2021 Lecture 10 11

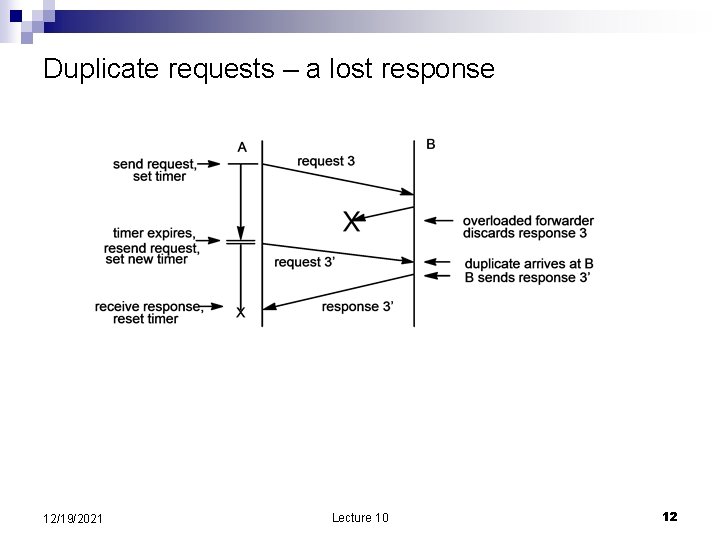
Duplicate requests – a lost response 12/19/2021 Lecture 10 12

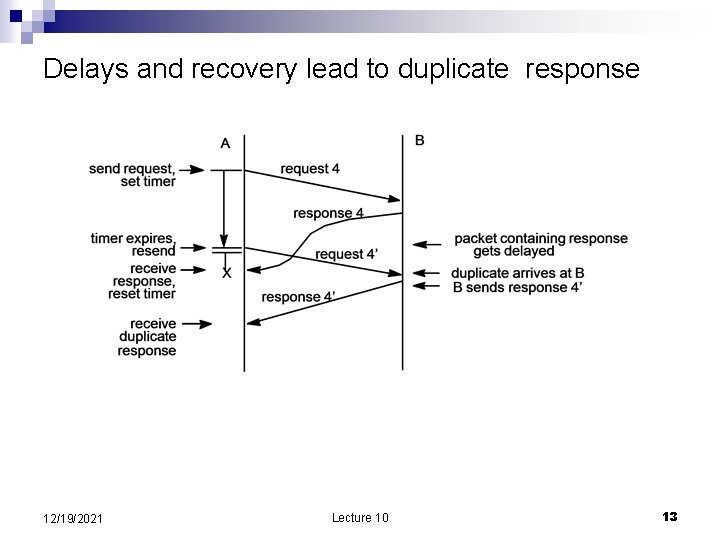
Delays and recovery lead to duplicate response 12/19/2021 Lecture 10 13

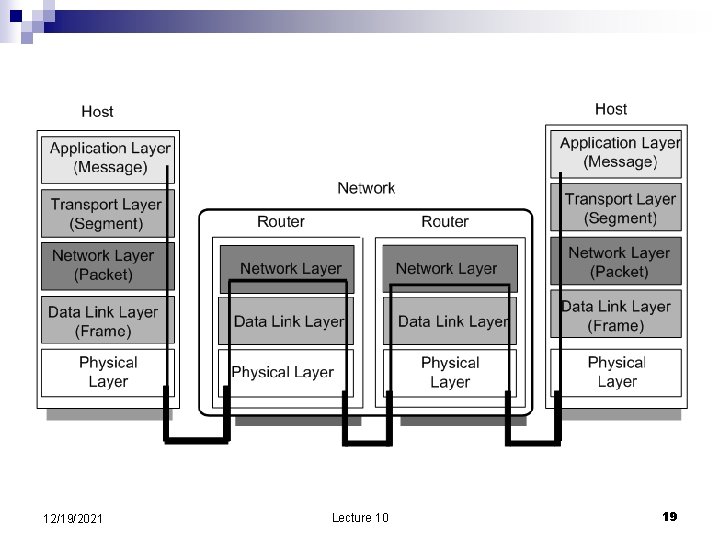
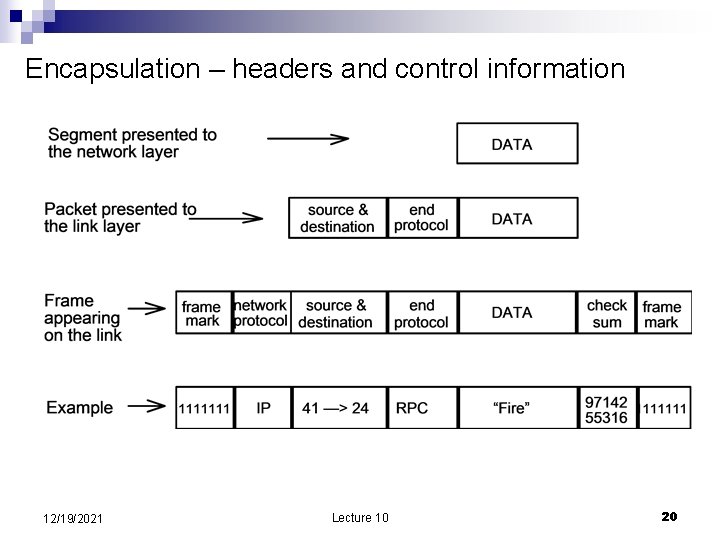
Network layers for store and forward networks n Every module has three interfaces: To the layers above ¨ To the layers below ¨ To the peer layer on another system ¨ n n Each layer hides the operation of the layer below from the layer above and provides its own interpretation of the important features of the layers below. A minimum of three layers are necessary: Link layer move data from one point to another. Includes ¨ Network layer forward data through intermediate node towards the destination ¨ End-to-end-layer provides all the functions required by the application including ¨ n Encapsulation: each layer treats information received from the layers above as raw data and adds control information (headers and trailers) understood only by its peer. 12/19/2021 Lecture 10 14

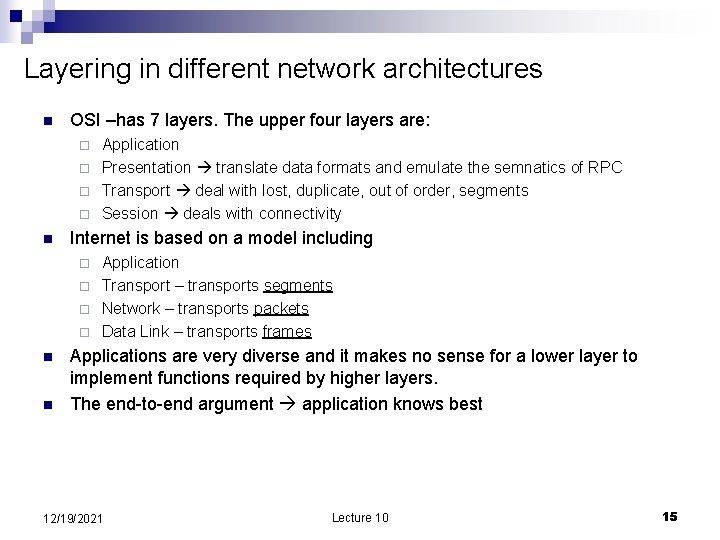
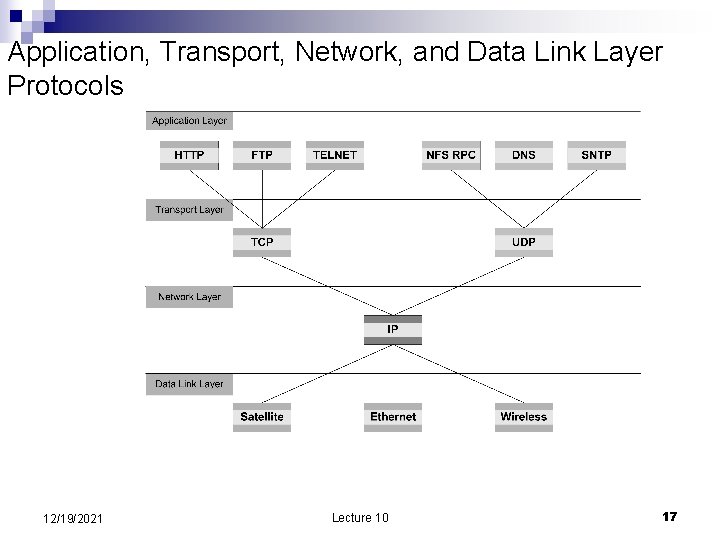
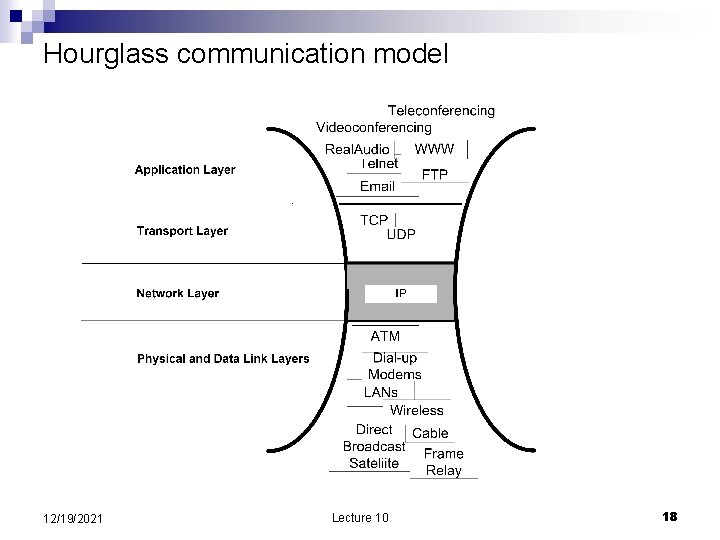
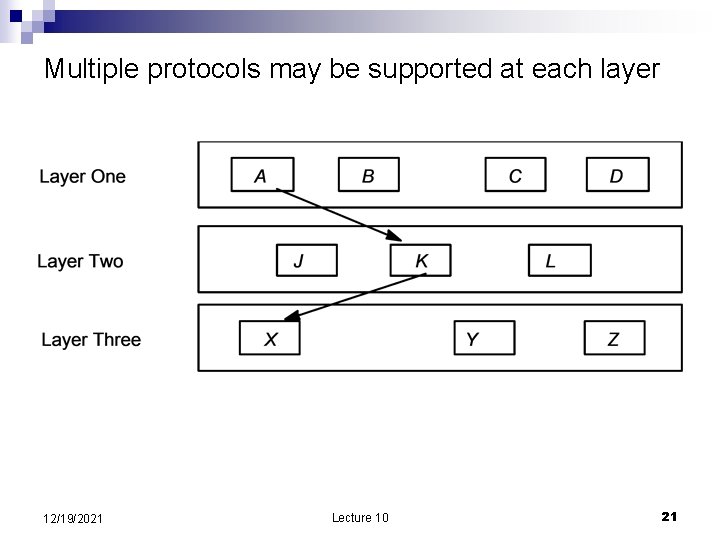
Layering in different network architectures n OSI –has 7 layers. The upper four layers are: Application ¨ Presentation translate data formats and emulate the semnatics of RPC ¨ Transport deal with lost, duplicate, out of order, segments ¨ Session deals with connectivity ¨ n Internet is based on a model including Application ¨ Transport – transports segments ¨ Network – transports packets ¨ Data Link – transports frames ¨ n n Applications are very diverse and it makes no sense for a lower layer to implement functions required by higher layers. The end-to-end argument application knows best 12/19/2021 Lecture 10 15

Example of an end-to end argument n n Should we have a checksum implemented at the link layer or should leave it for the application protocol e. g. , a file transfer protocol? If we implement it at the link layer ¨ Advantage: detect earlier an error ¨ Disadvantage: the data may still be affected by errors when buffered at the upper layers. 12/19/2021 Lecture 10 16

Application, Transport, Network, and Data Link Layer Protocols 12/19/2021 Lecture 10 17

Hourglass communication model 12/19/2021 Lecture 10 18

12/19/2021 Lecture 10 19

Encapsulation – headers and control information 12/19/2021 Lecture 10 20

Multiple protocols may be supported at each layer 12/19/2021 Lecture 10 21

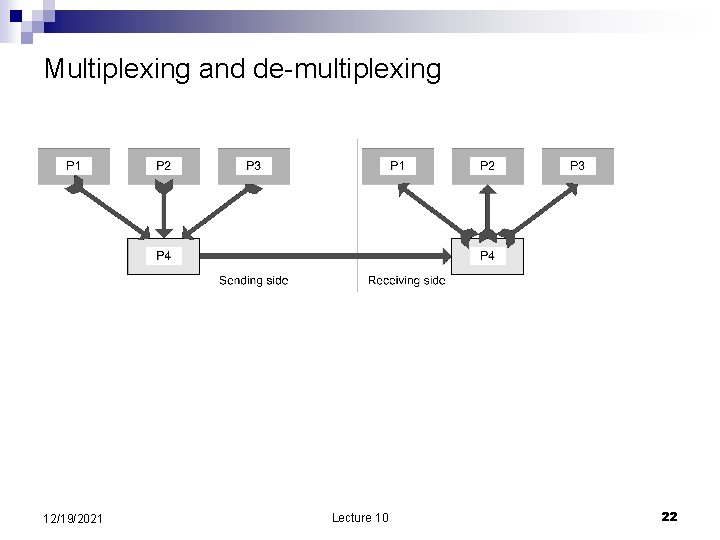
Multiplexing and de-multiplexing 12/19/2021 Lecture 10 22

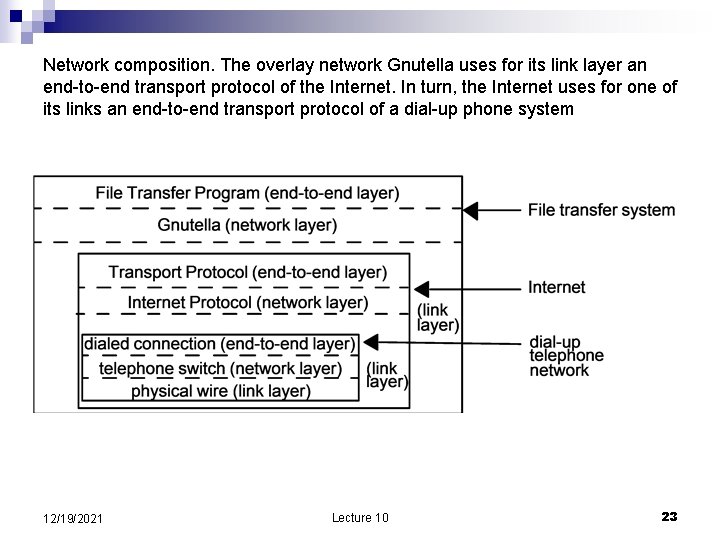
Network composition. The overlay network Gnutella uses for its link layer an end-to-end transport protocol of the Internet. In turn, the Internet uses for one of its links an end-to-end transport protocol of a dial-up phone system 12/19/2021 Lecture 10 23

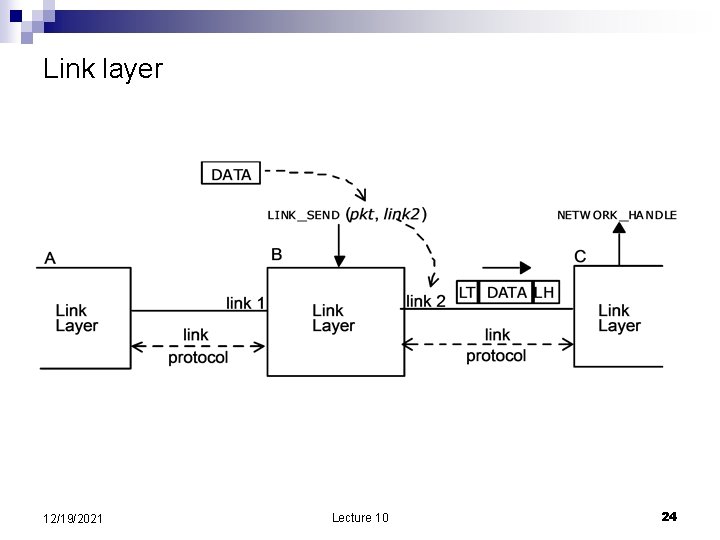
Link layer 12/19/2021 Lecture 10 24

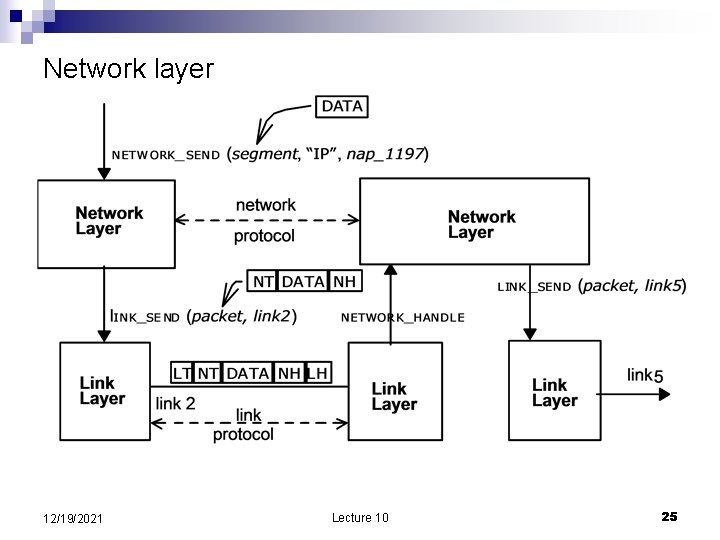
Network layer 12/19/2021 Lecture 10 25

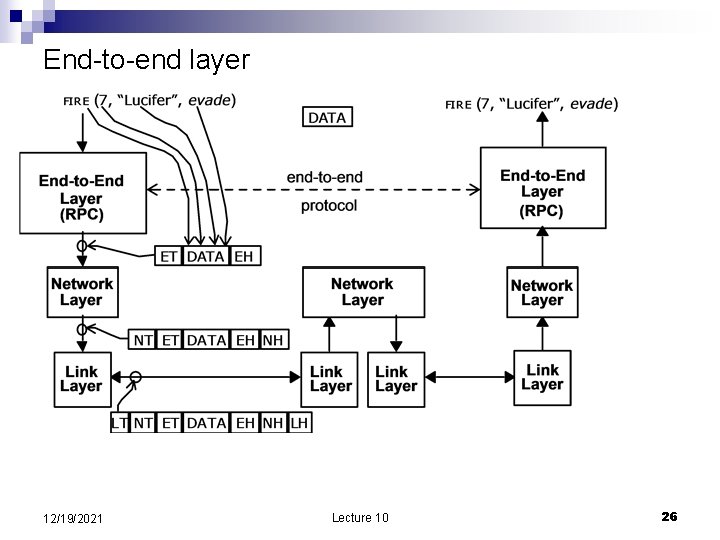
End-to-end layer 12/19/2021 Lecture 10 26

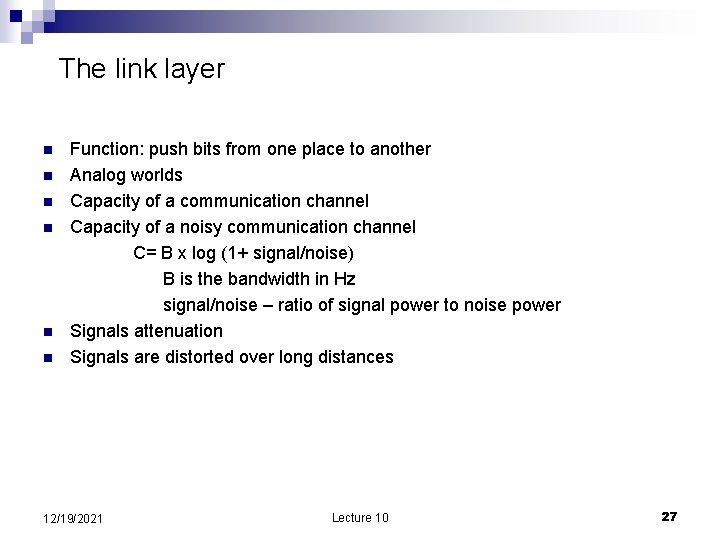
The link layer n n n Function: push bits from one place to another Analog worlds Capacity of a communication channel Capacity of a noisy communication channel C= B x log (1+ signal/noise) B is the bandwidth in Hz signal/noise – ratio of signal power to noise power Signals attenuation Signals are distorted over long distances 12/19/2021 Lecture 10 27

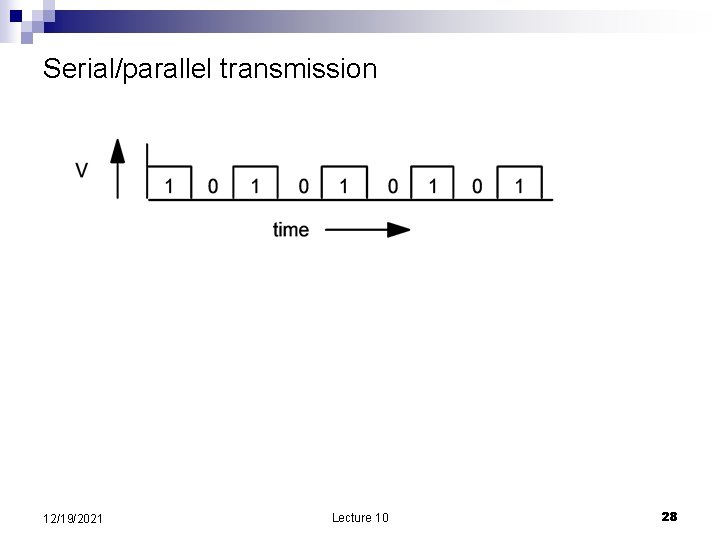
Serial/parallel transmission 12/19/2021 Lecture 10 28

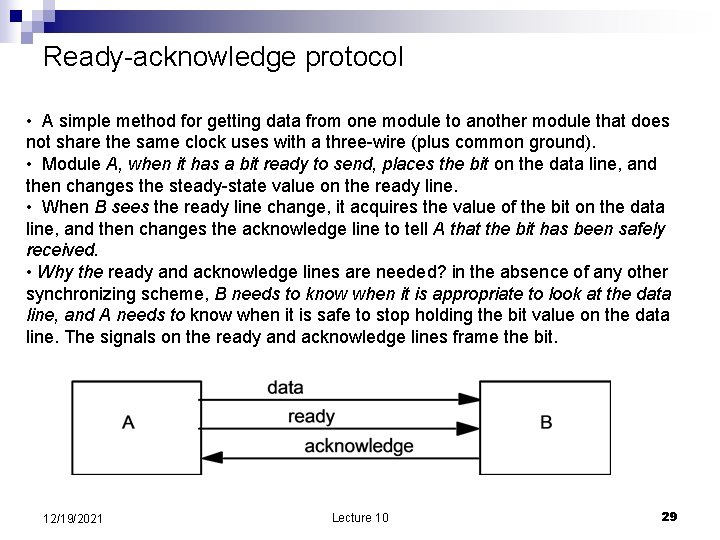
Ready-acknowledge protocol • A simple method for getting data from one module to another module that does not share the same clock uses with a three-wire (plus common ground). • Module A, when it has a bit ready to send, places the bit on the data line, and then changes the steady-state value on the ready line. • When B sees the ready line change, it acquires the value of the bit on the data line, and then changes the acknowledge line to tell A that the bit has been safely received. • Why the ready and acknowledge lines are needed? in the absence of any other synchronizing scheme, B needs to know when it is appropriate to look at the data line, and A needs to know when it is safe to stop holding the bit value on the data line. The signals on the ready and acknowledge lines frame the bit. 12/19/2021 Lecture 10 29

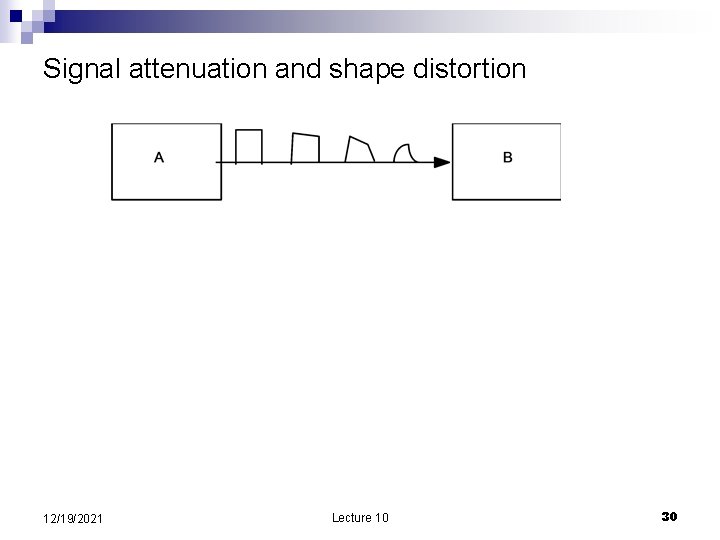
Signal attenuation and shape distortion 12/19/2021 Lecture 10 30

Encoding schemes • How could the receiver know exactly when to sample the incoming line? • Solution involves the two ends agree on an approximate data rate; the receiver runs a voltage-controlled oscillator (VCO) at about that same data rate. • Phase-locked loop Lock the VCO to both the frequency and phase of the arriving signal. • Complication there may be no transitions in the data stream, in which case the phase-locked loop will not be able to synchronize, e. g. , in a long string of zeros). • Phase encoding, at least one level transition associated with every data bit. • Manchester code the transmitter encodes each bit as two bits: a zero is encoded as a zero followed by a one, while a one is encoded as a one followed by a zero. • Guarantees that there is a level transition in the center of every transmitted bit, thus supplying the receiver with plenty of clocking information. • Disadvantage the maximum data rate of the communication channel is effectively cut in half, but the resulting simplicity of both the transmitter and the receiver is often worth this price. • More elaborate, encoding schemes do not reduce the maximum data rate as much, but they complicate encoding, decoding, and synchronization. 12/19/2021 Lecture 10 31

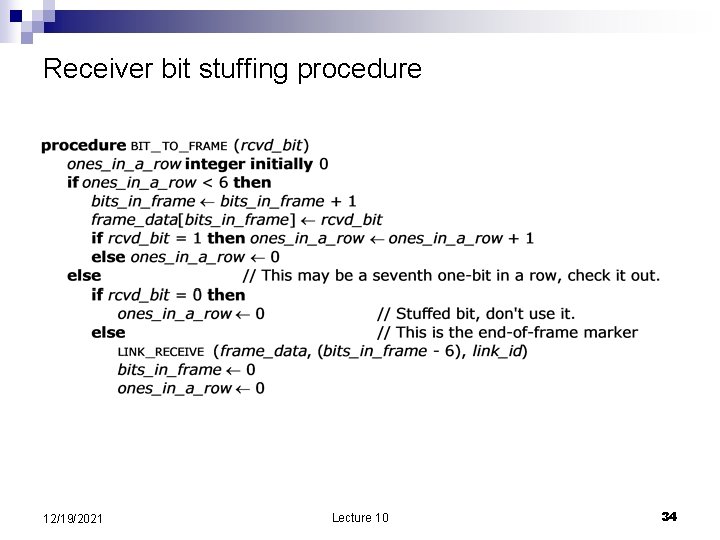
Framing n n The data link layer sends frames. Framing detecting when a frame stares and where it ends; different than bit framing. ¨ ¨ n n Using a pattern of bits Add a frame header and a frame trailer A pattern of bits serve as a frame delimiter – e. g. , seven 1’s Bit stuffing: ¨ The sender: add a 0 whenever it encounters a pattern of six 1’s in data ¨ The receiver: remove a 0 following a pattern of six 1’s in data 12/19/2021 Lecture 10 32

Sender bit stuffing procedure 12/19/2021 Lecture 10 33

Receiver bit stuffing procedure 12/19/2021 Lecture 10 34

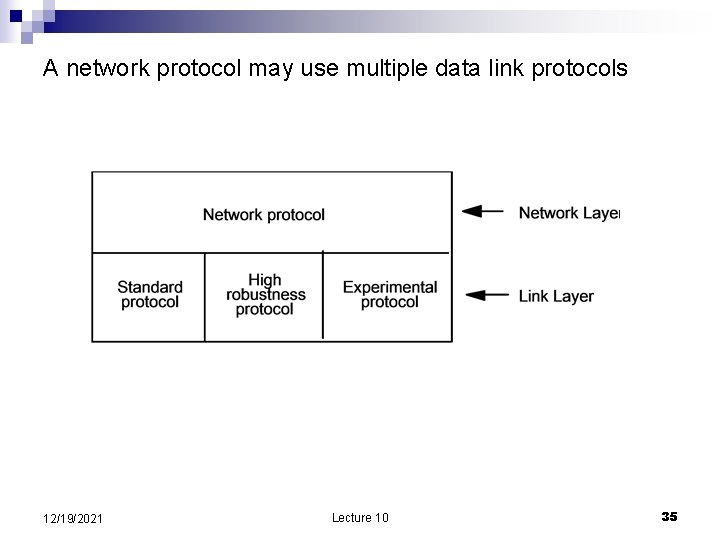
A network protocol may use multiple data link protocols 12/19/2021 Lecture 10 35

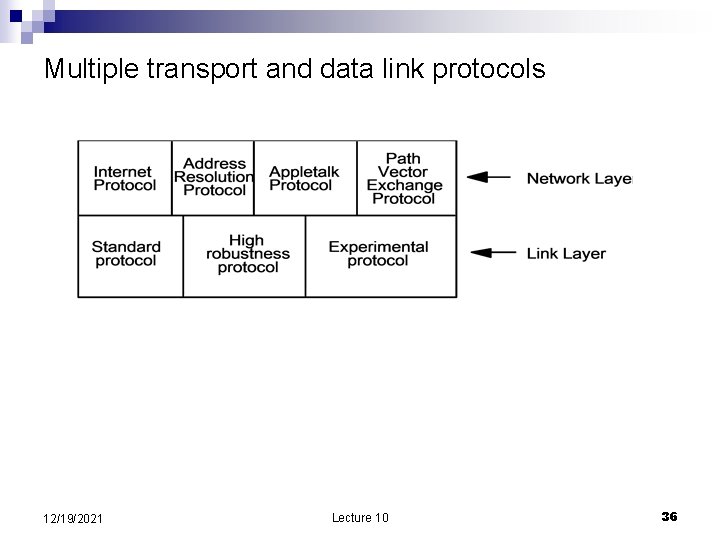
Multiple transport and data link protocols 12/19/2021 Lecture 10 36

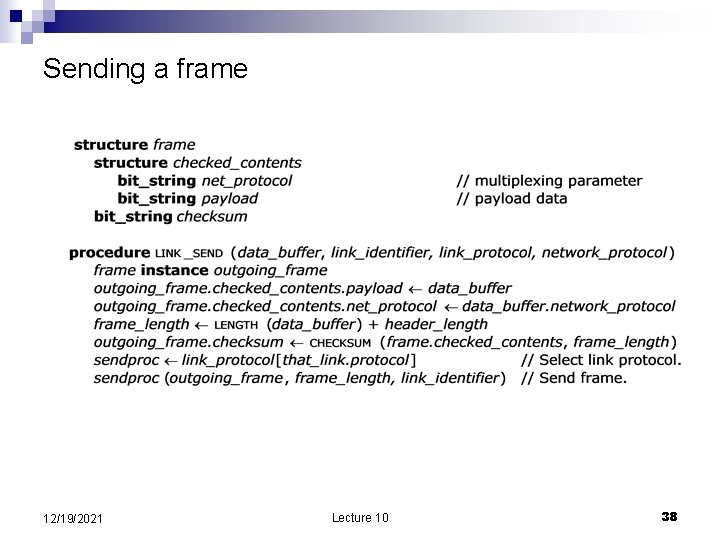
The link layer interface n n n LINK_SEND the network layer asks the link layer to send a packet NETWORK_HANDLE the link layer to alert the network layer that a packet arrived. To accommodate multiple lower-layer protocols, and higher-layer protocol multiplexing LINK_SEND (data_buffer, link_identifier, link_protocol, network_protocol) 12/19/2021 Lecture 10 37

Sending a frame 12/19/2021 Lecture 10 38

Receiving a frame 12/19/2021 Lecture 10 39

Error handling – the receiver detects an error n n Error correction Ask the sender to retransmit the frame in error. The sender should hold the frame in a buffer until the receiver has had a chance to recalculate and compare its checksum. ¨ The sender needs to know when it is safe to reuse this buffer for another frame. In most such designs the receiver explicitly acknowledges the correct (or incorrect) receipt of every frame. ¨ If the propagation time from sender to receiver is long compared with the time required to send a single frame, there may be several frames in flight, and acknowledgments (especially the ones that ask for retransmission) are disruptive. On a high performance link an explicit acknowledgment system can be surprisingly complex. ¨ n The receiver discard the frame. ¨ Reasonable choice as congestion in higher network levels must be handled by discarding packets anyway. Whatever higher-level protocol is used to deal with those discarded packets will also take care of any frames that are discarded because they contained errors. 12/19/2021 Lecture 10 40

Link properties n A point-to-point link directly connects exactly two communicating entities. ¨ n A simplex link has a transmitter at one end a receiver at the other; two-way communication requires installing two such links, one going in each direction. A duplex link has both a transmitter and a receiver at each end, allowing the same link to be used in both directions. A half-duplex link a duplex link in which transmission can take place in only one direction at a time, whereas a full-duplex link allows transmission in both directions at the same time over the same physical medium. A broadcast link transmission medium shared by several transmitters and receivers. 12/19/2021 Lecture 10 41

Maximum transmission unit (MTU) n n n Time The MTU puts an upper bound on the time that a link will be tied up once it begins to transmit the frame. More important for slow links than for fast ones. Error rate For a given bit error rate, the longer a frame the greater the chance of an uncorrectable error in that frame. Since the frame is usually also the unit of error control, an uncorrectable error generally means loss of the entire frame, so as the frame length increases not only does the probability of loss increase, but the cost of the loss increases because the entire frame will probably have to be retransmitted. The MTU puts a ceiling on both of these costs. Congestion if a forwarder to discards a packet due to congestion, the MTU limits the amount of transmission capacity required to retransmit the packet. Mechanical limits a hardware interface may have a small buffer or a short counter register tracking the number of bits in the frame. Software limitations originally designed for another application or to comply with some interoperability standard. 12/19/2021 Lecture 10 42