COSC 3213 Computer Networks I Instructor Dr Amir





- Slides: 32

COSC 3213: Computer Networks I Instructor: Dr. Amir Asif Department of Computer Science York University Handout # 7 Section M Medium Access Control (MAC) Topics: 1. Multiple Access Communications: Channelization vs MAC 2. MAC: Random Access Protocols vs Scheduled Approaches 3. Random Access Protocols: ALOHA, Slotted ALOHA, CSMA/CD Garcia: Sections 6. 1 – 6. 2

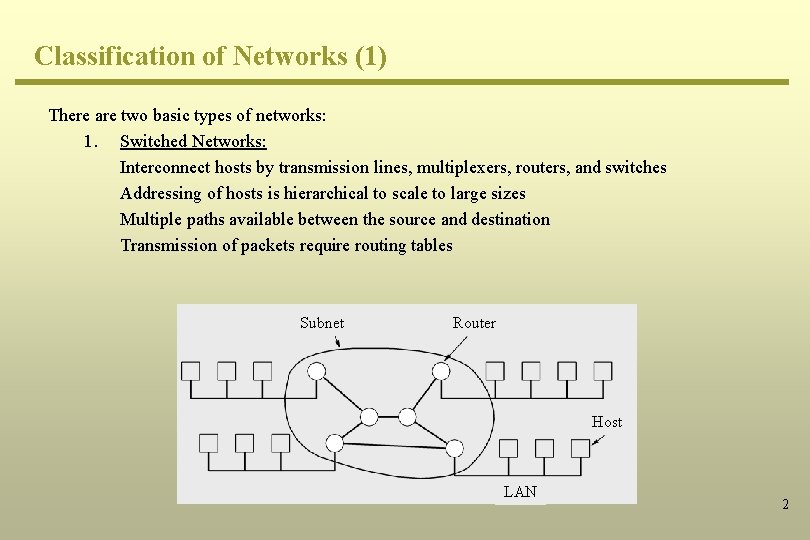
Classification of Networks (1) There are two basic types of networks: 1. Switched Networks: Interconnect hosts by transmission lines, multiplexers, routers, and switches Addressing of hosts is hierarchical to scale to large sizes Multiple paths available between the source and destination Transmission of packets require routing tables Subnet Router Host LAN 2

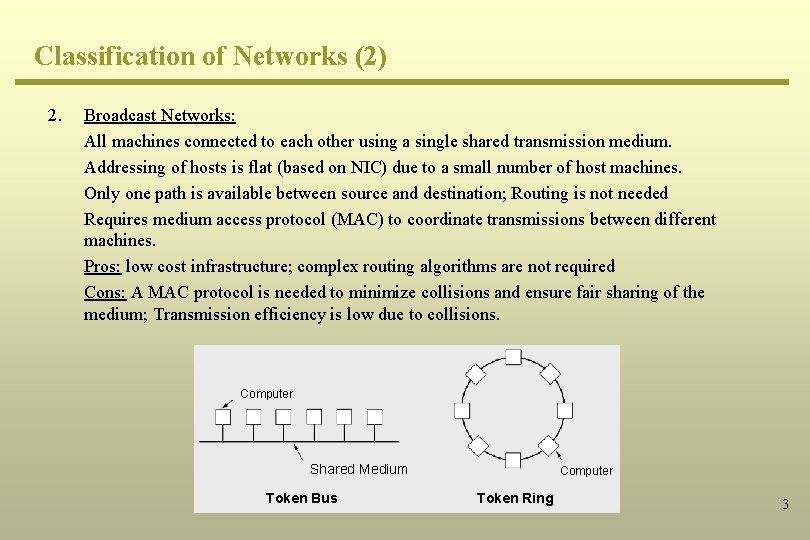
Classification of Networks (2) 2. Broadcast Networks: All machines connected to each other using a single shared transmission medium. Addressing of hosts is flat (based on NIC) due to a small number of host machines. Only one path is available between source and destination; Routing is not needed Requires medium access protocol (MAC) to coordinate transmissions between different machines. Pros: low cost infrastructure; complex routing algorithms are not required Cons: A MAC protocol is needed to minimize collisions and ensure fair sharing of the medium; Transmission efficiency is low due to collisions. Computer Shared Medium Token Bus Computer Token Ring 3

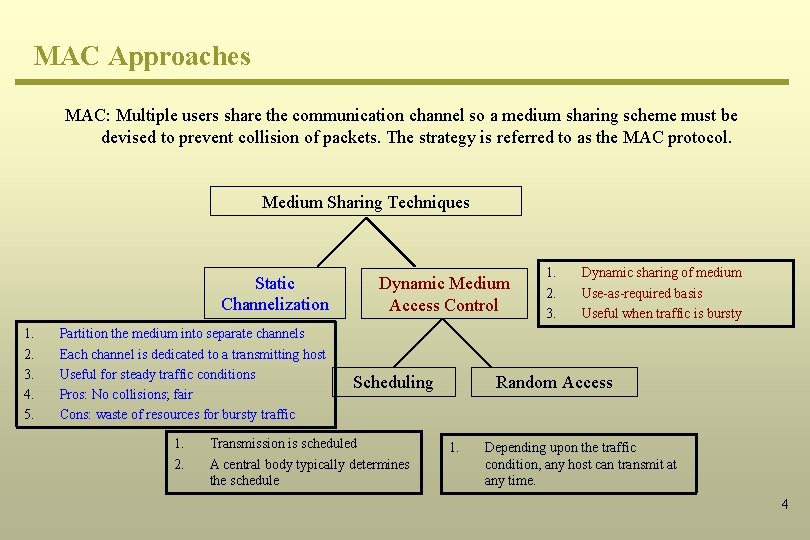
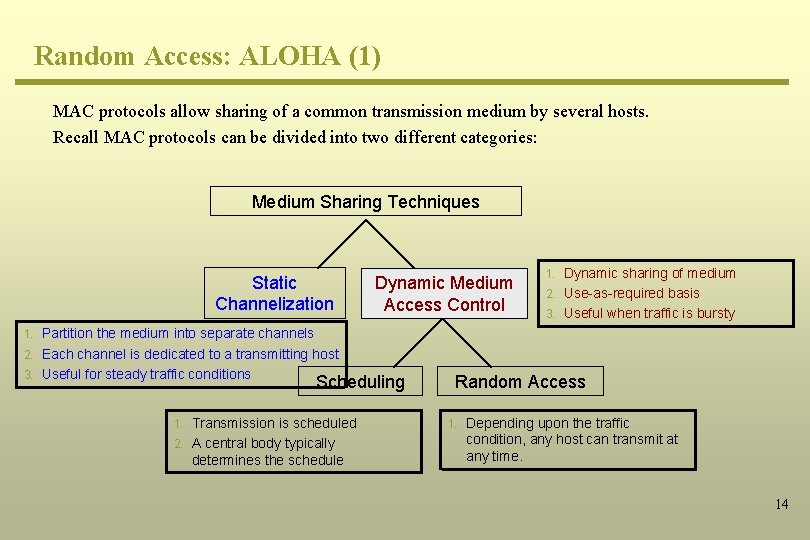
MAC Approaches MAC: Multiple users share the communication channel so a medium sharing scheme must be devised to prevent collision of packets. The strategy is referred to as the MAC protocol. Medium Sharing Techniques Static Channelization 1. 2. 3. 4. 5. Partition the medium into separate channels Each channel is dedicated to a transmitting host Useful for steady traffic conditions Pros: No collisions; fair Cons: waste of resources for bursty traffic 1. 2. Dynamic Medium Access Control Scheduling Transmission is scheduled A central body typically determines the schedule 1. 2. 3. Dynamic sharing of medium Use-as-required basis Useful when traffic is bursty Random Access 1. Depending upon the traffic condition, any host can transmit at any time. 4

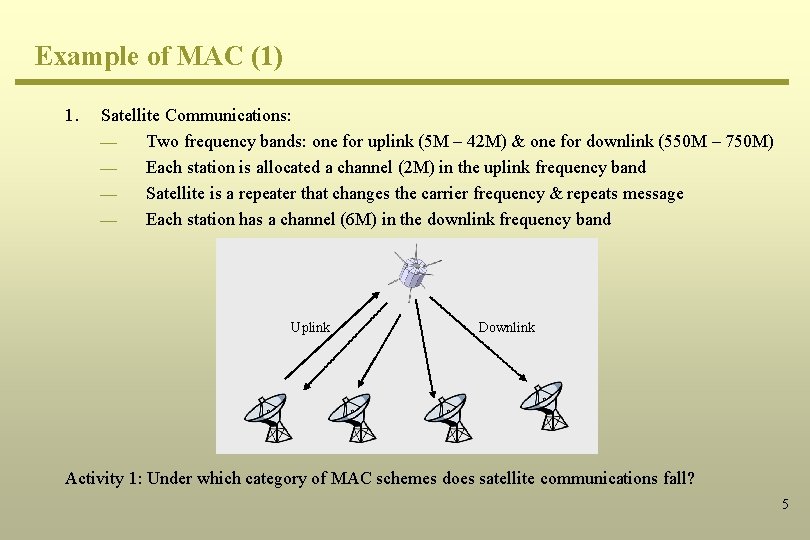
Example of MAC (1) 1. Satellite Communications: ¾ Two frequency bands: one for uplink (5 M – 42 M) & one for downlink (550 M – 750 M) ¾ Each station is allocated a channel (2 M) in the uplink frequency band ¾ Satellite is a repeater that changes the carrier frequency & repeats message ¾ Each station has a channel (6 M) in the downlink frequency band Uplink Downlink Activity 1: Under which category of MAC schemes does satellite communications fall? 5

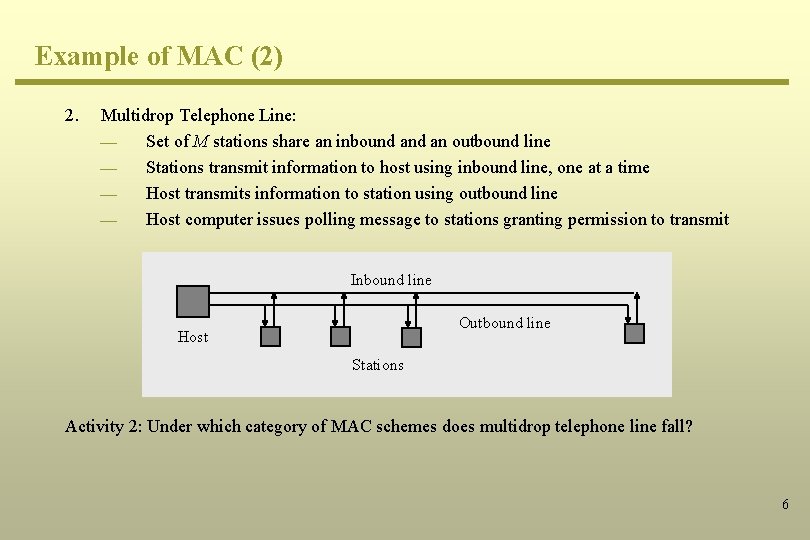
Example of MAC (2) 2. Multidrop Telephone Line: ¾ Set of M stations share an inbound an outbound line ¾ Stations transmit information to host using inbound line, one at a time ¾ Host transmits information to station using outbound line ¾ Host computer issues polling message to stations granting permission to transmit Inbound line Outbound line Host Stations Activity 2: Under which category of MAC schemes does multidrop telephone line fall? 6

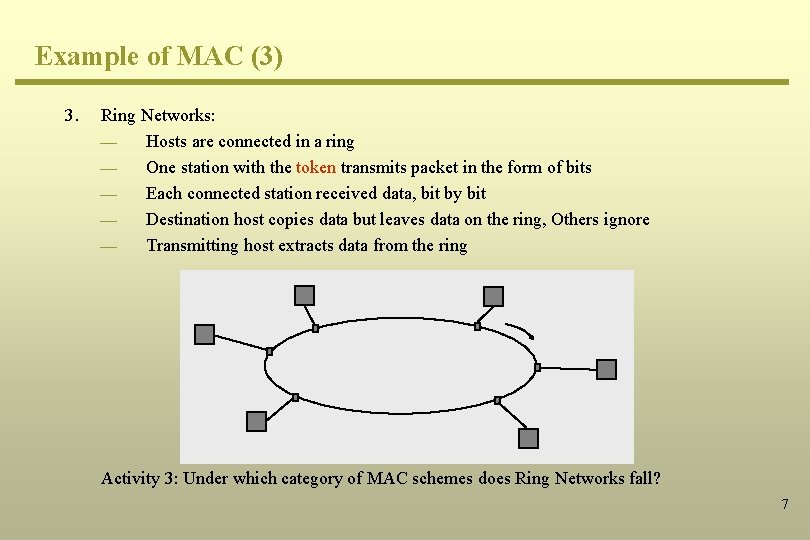
Example of MAC (3) 3. Ring Networks: ¾ Hosts are connected in a ring ¾ One station with the token transmits packet in the form of bits ¾ Each connected station received data, bit by bit ¾ Destination host copies data but leaves data on the ring, Others ignore ¾ Transmitting host extracts data from the ring Activity 3: Under which category of MAC schemes does Ring Networks fall? 7

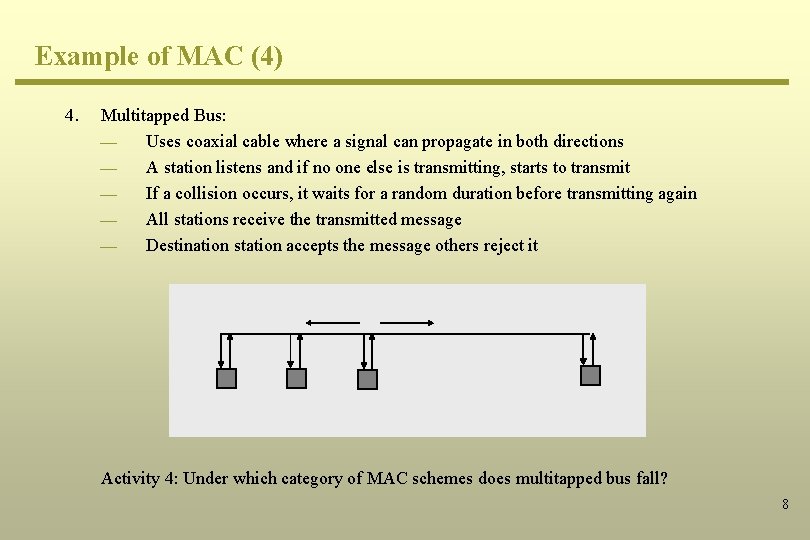
Example of MAC (4) 4. Multitapped Bus: ¾ Uses coaxial cable where a signal can propagate in both directions ¾ A station listens and if no one else is transmitting, starts to transmit ¾ If a collision occurs, it waits for a random duration before transmitting again ¾ All stations receive the transmitted message ¾ Destination station accepts the message others reject it Activity 4: Under which category of MAC schemes does multitapped bus fall? 8

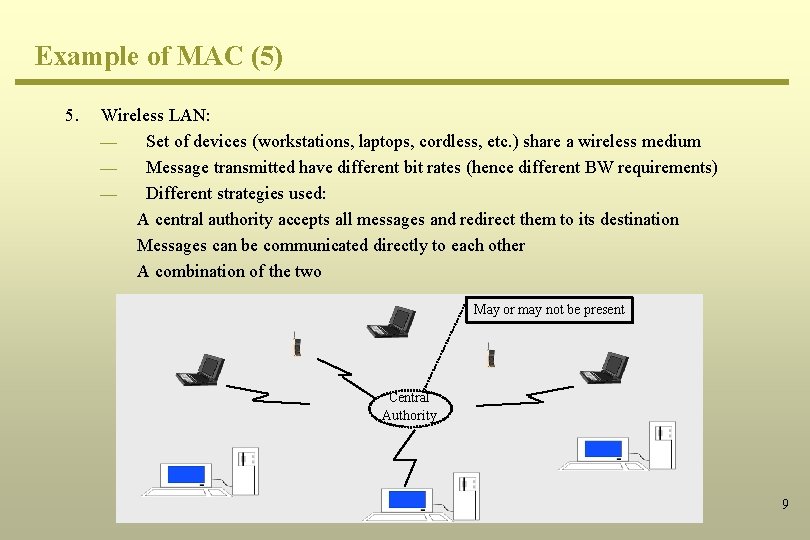
Example of MAC (5) 5. Wireless LAN: ¾ Set of devices (workstations, laptops, cordless, etc. ) share a wireless medium ¾ Message transmitted have different bit rates (hence different BW requirements) ¾ Different strategies used: A central authority accepts all messages and redirect them to its destination Messages can be communicated directly to each other A combination of the two May or may not be present Central Authority 9

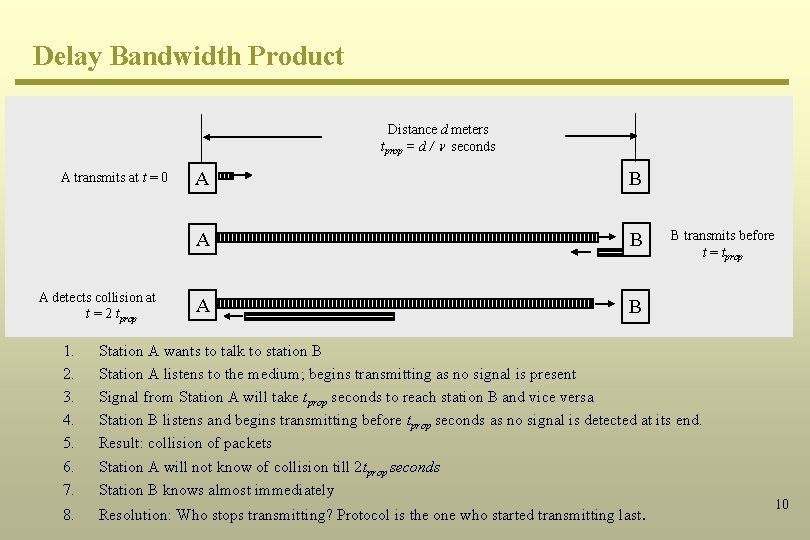
Delay Bandwidth Product Distance d meters tprop = d / seconds A transmits at t = 0 A detects collision at t = 2 tprop A B A B B transmits before t = tprop 1. 2. 3. 4. 5. 6. 7. Station A wants to talk to station B Station A listens to the medium; begins transmitting as no signal is present Signal from Station A will take tprop seconds to reach station B and vice versa Station B listens and begins transmitting before tprop seconds as no signal is detected at its end. Result: collision of packets Station A will not know of collision till 2 tprop seconds Station B knows almost immediately 8. Resolution: Who stops transmitting? Protocol is the one who started transmitting last. 10

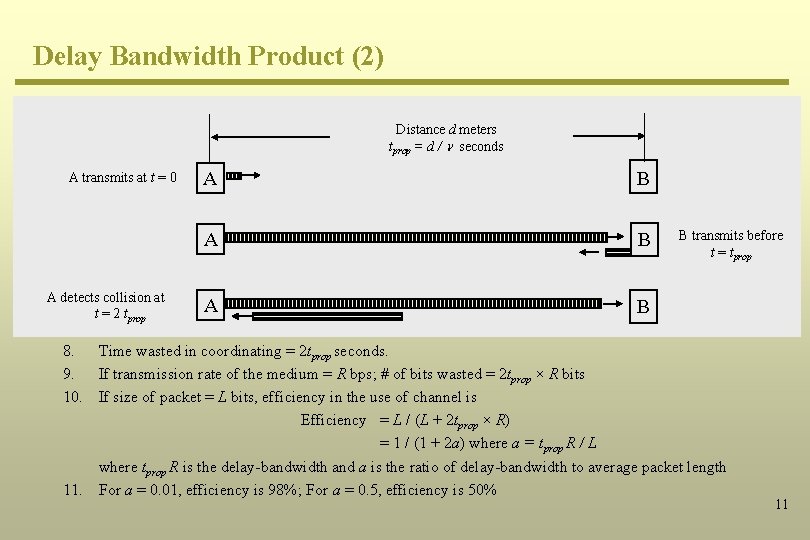
Delay Bandwidth Product (2) Distance d meters tprop = d / seconds A transmits at t = 0 A detects collision at t = 2 tprop A B A B B transmits before t = tprop 8. Time wasted in coordinating = 2 tprop seconds. 9. If transmission rate of the medium = R bps; # of bits wasted = 2 tprop × R bits 10. If size of packet = L bits, efficiency in the use of channel is Efficiency = L / (L + 2 tprop × R) = 1 / (1 + 2 a) where a = tprop R / L where tprop R is the delay-bandwidth and a is the ratio of delay-bandwidth to average packet length 11. For a = 0. 01, efficiency is 98%; For a = 0. 5, efficiency is 50% 11

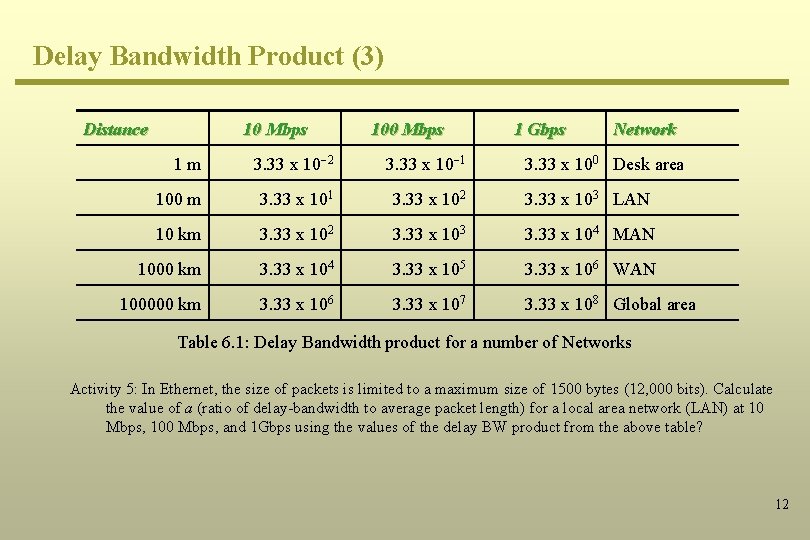
Delay Bandwidth Product (3) Distance 10 Mbps 100 Mbps 1 Gbps Network 1 m 3. 33 x 10 -2 3. 33 x 10 -1 100 m 3. 33 x 101 3. 33 x 102 3. 33 x 103 LAN 10 km 3. 33 x 102 3. 33 x 103 3. 33 x 104 MAN 1000 km 3. 33 x 104 3. 33 x 105 3. 33 x 106 WAN 100000 km 3. 33 x 106 3. 33 x 107 3. 33 x 108 Global area 3. 33 x 100 Desk area Table 6. 1: Delay Bandwidth product for a number of Networks Activity 5: In Ethernet, the size of packets is limited to a maximum size of 1500 bytes (12, 000 bits). Calculate the value of a (ratio of delay-bandwidth to average packet length) for a local area network (LAN) at 10 Mbps, 100 Mbps, and 1 Gbps using the values of the delay BW product from the above table? 12

Definitions Frame Transfer Delay (T): Duration between the time when the first bit of frame leaves the MAC layer of the source to the time when the last bit reaches the MAC layer of the destination. Throughput (Sout): Effective rate of transmission (based on successful deliver of frames) in frames/s across a network Suppose that the transmission rate of a network is R bps Length of a frame is L bits Maximum throughtput = R / L frames/s Actual throughput < R / L frames/s, Why? Load (G): Load (total number of frames) on the channel in frames per X seconds. Topology: Way a network is structured, i. e. , ring versus bus versus star topology. Technology: Set of protocols used for a network to function. 13

Random Access: ALOHA (1) MAC protocols allow sharing of a common transmission medium by several hosts. Recall MAC protocols can be divided into two different categories: Medium Sharing Techniques Static Channelization Dynamic Medium Access Control 1. Dynamic sharing of medium 2. Use-as-required basis 3. Useful when traffic is bursty 1. Partition the medium into separate channels 2. Each channel is dedicated to a transmitting host 3. Useful for steady traffic conditions Scheduling 1. Transmission is scheduled 2. A central body typically determines the schedule Random Access 1. Depending upon the traffic condition, any host can transmit at any time. 14

Random Access: ALOHA (2) Random Access: MAC protocols include 1. ALOHA: ¾ Earliest random access method. Developed at University of Hawaii in 1970 s to interconnect university campuses on different islands through a microwave link ¾ Transmitter: Transmits the frame as soon as the MAC layer receives it ¾ Channel: If a collision occurs, frames received by the receiver will contain errors ¾ Receiver: In case of errors, no acknowledgement is transmitted to the receiver. (Alternatively, a request for retransmission may be made in case of errors) ¾ Transmitter: If the transmitter receives no ACK within timeout (2 × propagation delay), it backs off for a random period of time. On the expiry of backoff tine, the transmitter retransmits the frame. Aloha is successful for light traffic. Note that collision is different from errors since it affects two host stations. For the scheme to work, it is vital that the host stations wait for a random period of time before retransmitting. If both stations wait an equal time before retransmitting, there will always be collisions. 15

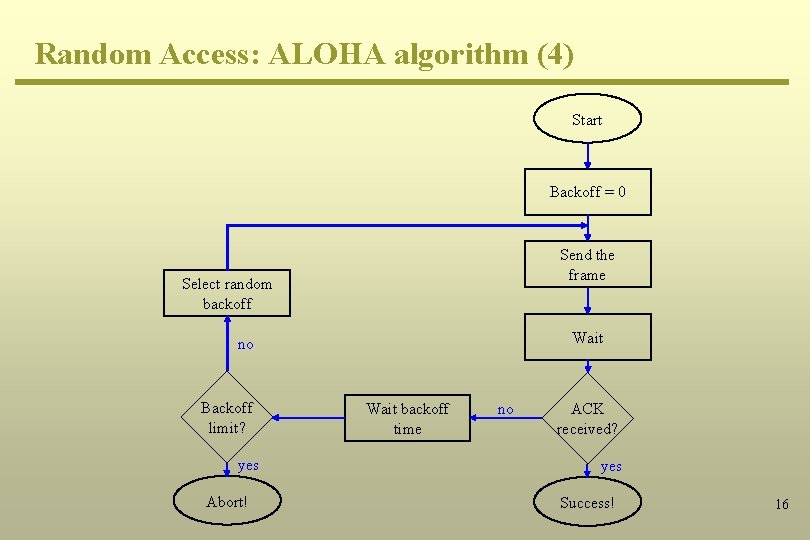
Random Access: ALOHA algorithm (4) Start Backoff = 0 Send the frame Select random backoff Wait no Backoff limit? yes Abort! Wait backoff time no ACK received? yes Success! 16

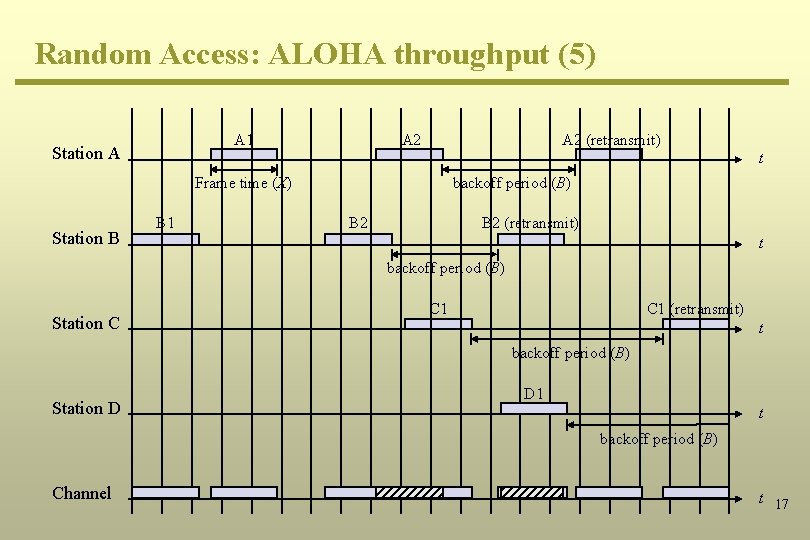
Random Access: ALOHA throughput (5) A 1 Station A A 2 (retransmit) t Frame time (X) Station B B 1 backoff period (B) B 2 (retransmit) t backoff period (B) Station C C 1 (retransmit) t backoff period (B) Station D D 1 t backoff period (B) Channel t 17

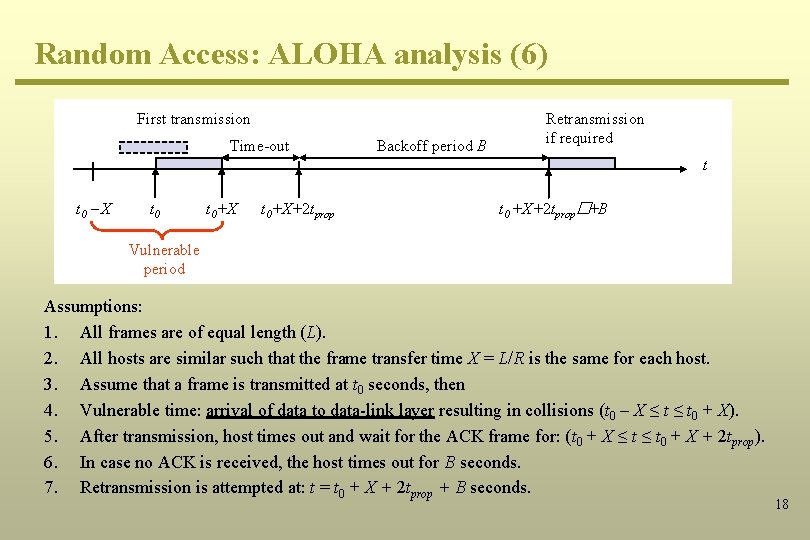
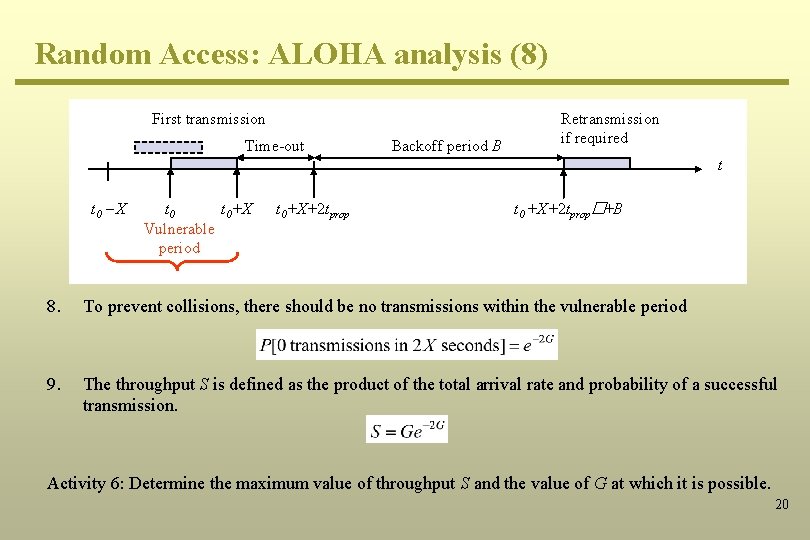
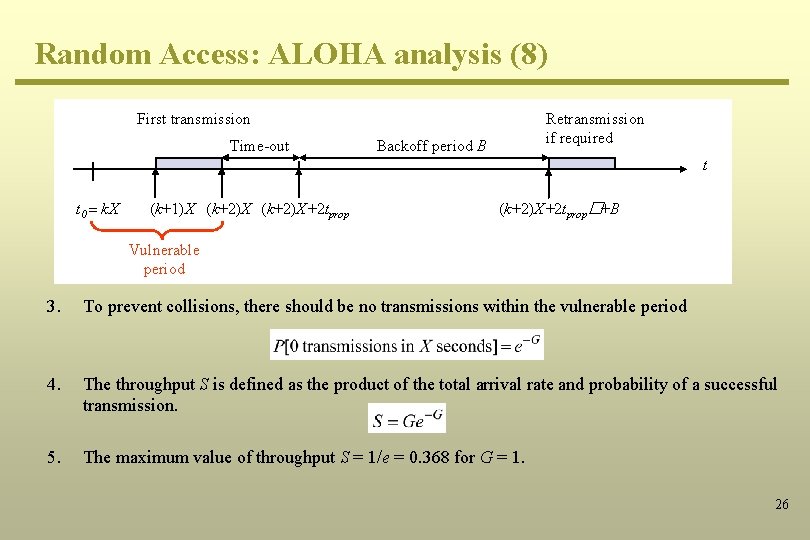
Random Access: ALOHA analysis (6) First transmission Time-out Backoff period B Retransmission if required t t 0 - X t 0+X+2 tprop t 0 +X+2 tprop�+B Vulnerable period Assumptions: 1. All frames are of equal length (L). 2. All hosts are similar such that the frame transfer time X = L/R is the same for each host. 3. Assume that a frame is transmitted at t 0 seconds, then 4. Vulnerable time: arrival of data to data-link layer resulting in collisions (t 0 – X ≤ t 0 + X). 5. After transmission, host times out and wait for the ACK frame for: (t 0 + X ≤ t 0 + X + 2 tprop). 6. In case no ACK is received, the host times out for B seconds. 7. Retransmission is attempted at: t = t 0 + X + 2 tprop + B seconds. 18

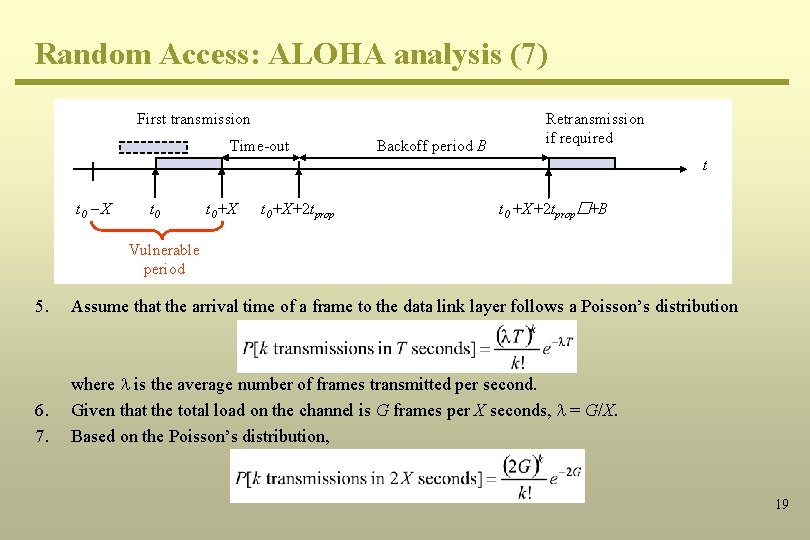
Random Access: ALOHA analysis (7) First transmission Time-out Backoff period B Retransmission if required t t 0 - X t 0+X+2 tprop t 0 +X+2 tprop�+B Vulnerable period 5. Assume that the arrival time of a frame to the data link layer follows a Poisson’s distribution 6. 7. where l is the average number of frames transmitted per second. Given that the total load on the channel is G frames per X seconds, l = G/X. Based on the Poisson’s distribution, 19

Random Access: ALOHA analysis (8) First transmission Time-out Backoff period B Retransmission if required t t 0 - X t 0+X Vulnerable period t 0+X+2 tprop t 0 +X+2 tprop�+B 8. To prevent collisions, there should be no transmissions within the vulnerable period 9. The throughput S is defined as the product of the total arrival rate and probability of a successful transmission. Activity 6: Determine the maximum value of throughput S and the value of G at which it is possible. 20

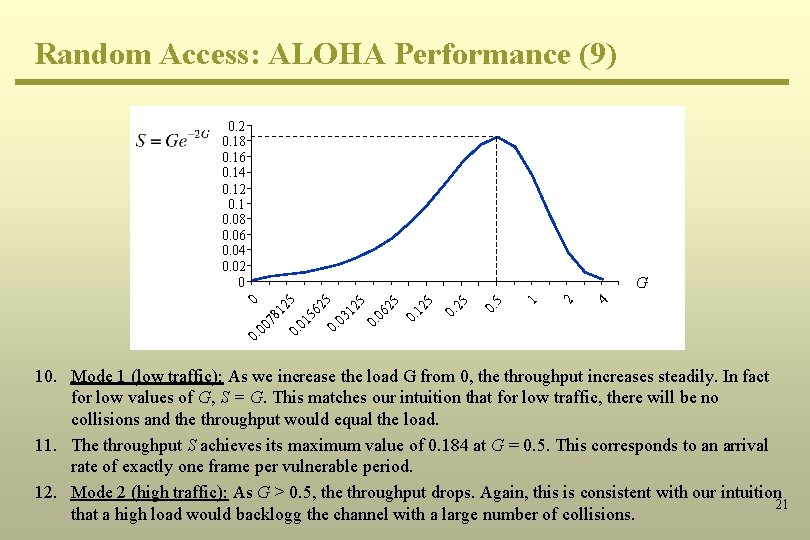
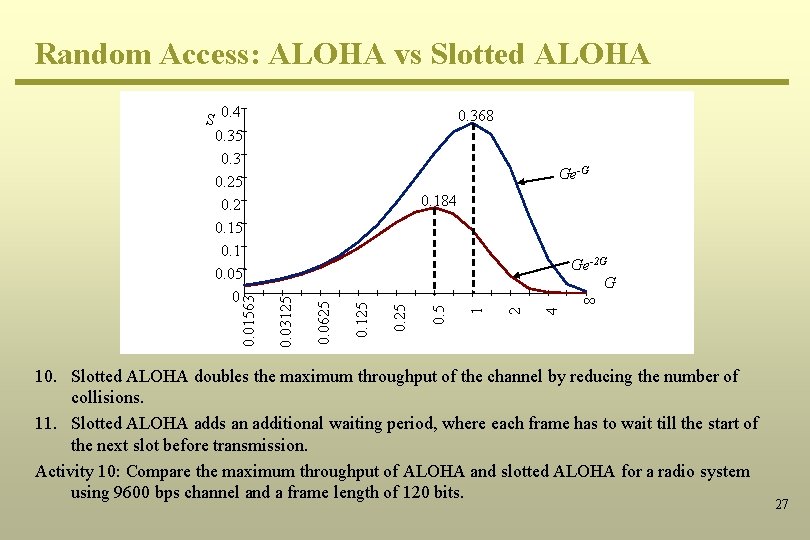
Random Access: ALOHA Performance (9) 4 2 1 5 0. 25 G 0. 0 0 07 81 25 0. 01 56 2 0. 5 03 12 5 0. 06 25 0. 12 5 0. 2 0. 18 0. 16 0. 14 0. 12 0. 1 0. 08 0. 06 0. 04 0. 02 0 10. Mode 1 (low traffic): As we increase the load G from 0, the throughput increases steadily. In fact for low values of G, S = G. This matches our intuition that for low traffic, there will be no collisions and the throughput would equal the load. 11. The throughput S achieves its maximum value of 0. 184 at G = 0. 5. This corresponds to an arrival rate of exactly one frame per vulnerable period. 12. Mode 2 (high traffic): As G > 0. 5, the throughput drops. Again, this is consistent with our intuition 21 that a high load would backlogg the channel with a large number of collisions.

Random Access: ALOHA (10) Activity 7: Suppose that the ALOHA protocol is used to share a 56 kbps satellite channel. Suppose that the frames are 1000 bits long. What is the maximum throughput of the system in frames/s if the propagation time is ignored. Solution: Maximum throughput for ALOHA = 0. 184 frames / X seconds. Frame transfer delay (X) = 1000/56000 = 1/56 seconds Maximum throughput in frames/s = 0. 184 × 56, or approximately 10 frames/sec. 22

Random Access: Slotted ALOHA (1) 1. 2. 3. 4. The maximum throughput of ALOHA is 0. 184 frames per frame transfer time. The first attempt to increase throughput is called the Slotted ALOHA, which includes the following modifications to ALOHA. ¾ Divide the time into slots. ¾ Any station is only allowed to transmit at the beginning of a slot. ¾ Rest of the procedure is same as for ALOHA. Drawback: Additional complexity in the protocol as stations must be synchronized with the beginning of slots. Advantage: Number of collisions are reduced as frames would collide only at the beginning of a time slot. 23

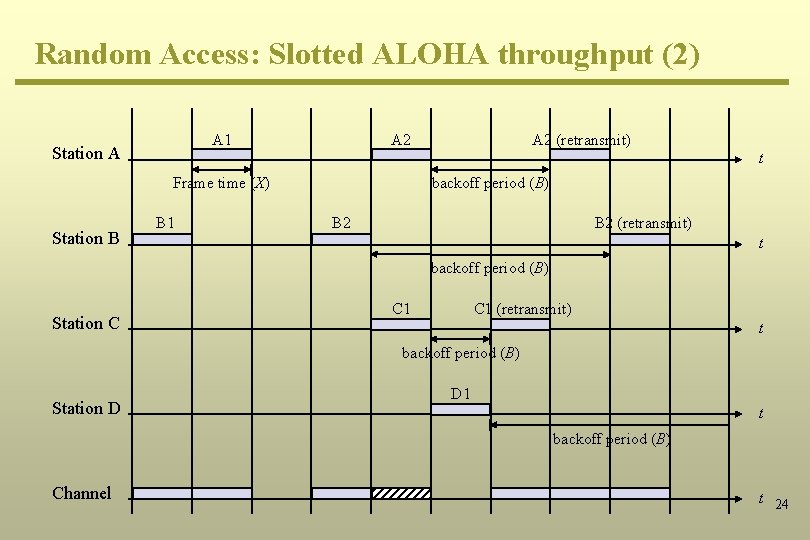
Random Access: Slotted ALOHA throughput (2) A 1 Station A A 2 t Frame time (X) Station B A 2 (retransmit) B 1 backoff period (B) B 2 (retransmit) t backoff period (B) Station C C 1 (retransmit) t backoff period (B) Station D D 1 t backoff period (B) Channel t 24

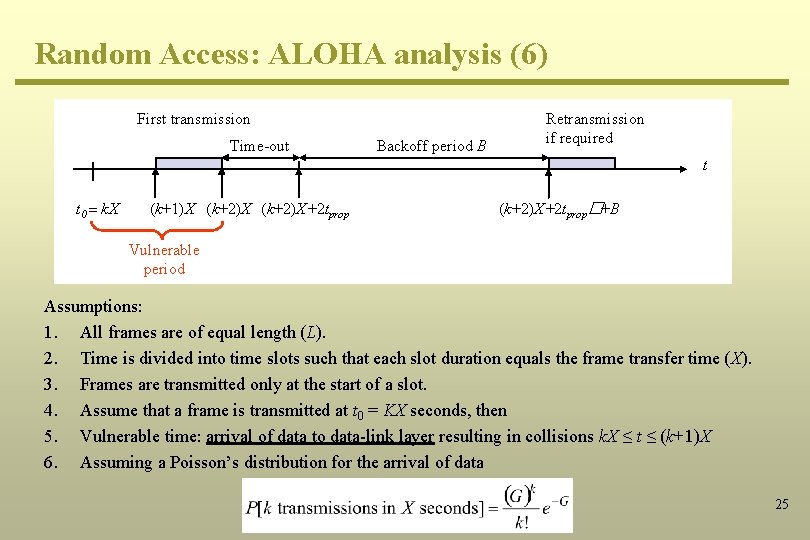
Random Access: ALOHA analysis (6) First transmission Time-out Backoff period B Retransmission if required t t 0 = k. X (k+1)X (k+2)X+2 tprop�+B Vulnerable period Assumptions: 1. All frames are of equal length (L). 2. Time is divided into time slots such that each slot duration equals the frame transfer time (X). 3. Frames are transmitted only at the start of a slot. 4. Assume that a frame is transmitted at t 0 = KX seconds, then 5. Vulnerable time: arrival of data to data-link layer resulting in collisions k. X ≤ t ≤ (k+1)X 6. Assuming a Poisson’s distribution for the arrival of data 25

Random Access: ALOHA analysis (8) First transmission Time-out Retransmission if required Backoff period B t t 0 = k. X (k+1)X (k+2)X+2 tprop�+B Vulnerable period 3. To prevent collisions, there should be no transmissions within the vulnerable period 4. The throughput S is defined as the product of the total arrival rate and probability of a successful transmission. 5. The maximum value of throughput S = 1/e = 0. 368 for G = 1. 26

Random Access: ALOHA vs Slotted ALOHA 0. 368 Ge-G 0. 184 8 4 2 1 0. 5 0. 25 0. 125 0. 0625 Ge-2 G G 0. 03125 0. 01563 S 0. 4 0. 35 0. 3 0. 25 0. 2 0. 15 0. 1 0. 05 0 10. Slotted ALOHA doubles the maximum throughput of the channel by reducing the number of collisions. 11. Slotted ALOHA adds an additional waiting period, where each frame has to wait till the start of the next slot before transmission. Activity 10: Compare the maximum throughput of ALOHA and slotted ALOHA for a radio system using 9600 bps channel and a frame length of 120 bits. 27

Random Access: CSMA (1) Carrier Sensitive Multiple Access (CSMA): ¾ An improvement over ALOHA by providing carrier sense to the station. ¾ Before transmitting, the station senses if any carrier (or signal) is present on the shared medium. ¾ If a carrier is present, the station waits and transmits again when the medium indicates no carrier. ¾ Depending upon how the duration of the wait period is decided, CSMA can be classified in different categories: a) 1 -Persistent CSMA: If the channel is busy, the station transmits immediately as soon as the medium becomes idle (free of any carrier). b) Non-persistent CSMA: If the medium is busy, station runs a backoff algorithm to reschedule a future sensing period. It senses again after a certain wait and transmits only if the medium is free. c) P-persistent CSMA: Station senses for carrier. If the carrier is absent, it transmits with a p probability. If busy, it persists with sensing until the medium is free. 28

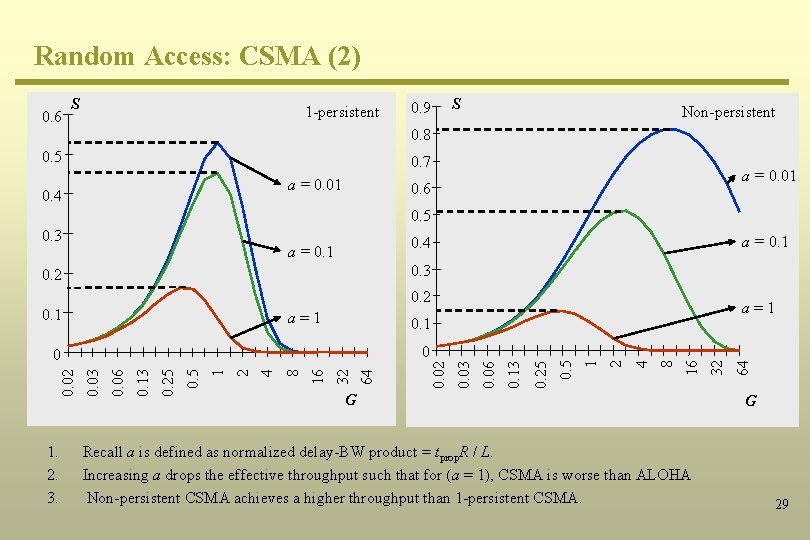
Random Access: CSMA (2) 0. 6 S 1 -persistent 0. 5 0. 9 0. 53 0. 8 0. 45 0. 7 a = 0. 01 0. 4 S Non-persistent a = 0. 01 0. 6 0. 5 0. 3 0. 16 0. 2 a=1 G Recall a is defined as normalized delay-BW product = tprop. R / L. Increasing a drops the effective throughput such that for (a = 1), CSMA is worse than ALOHA Non-persistent CSMA achieves a higher throughput than 1 -persistent CSMA. 32 16 8 4 2 0. 25 0. 13 0. 06 0. 03 64 32 16 8 4 2 1 0. 5 0. 25 0. 13 0. 06 0. 03 0. 02 0 1 0 1. 2. 3. a=1 0. 5 0. 1 64 0. 2 a = 0. 1 0. 4 a = 0. 1 G 29

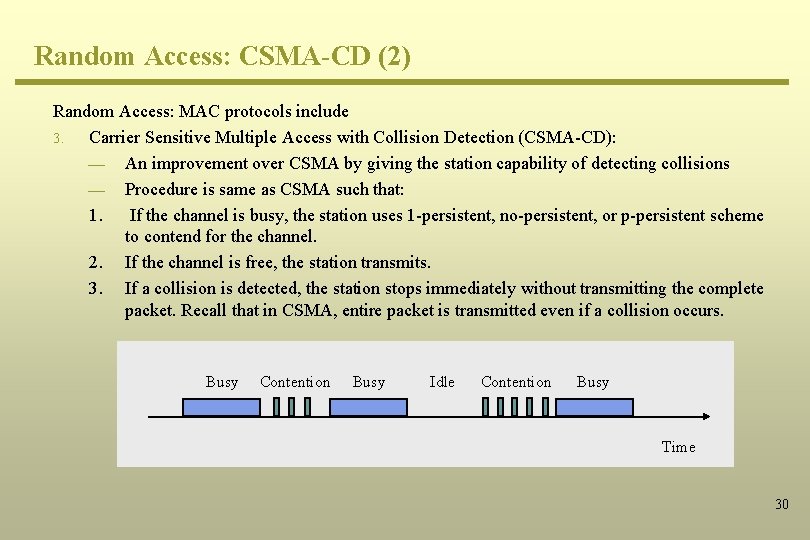
Random Access: CSMA-CD (2) Random Access: MAC protocols include 3. Carrier Sensitive Multiple Access with Collision Detection (CSMA-CD): ¾ An improvement over CSMA by giving the station capability of detecting collisions ¾ Procedure is same as CSMA such that: 1. If the channel is busy, the station uses 1 -persistent, no-persistent, or p-persistent scheme to contend for the channel. 2. If the channel is free, the station transmits. 3. If a collision is detected, the station stops immediately without transmitting the complete packet. Recall that in CSMA, entire packet is transmitted even if a collision occurs. Busy Contention Busy Idle Contention Busy Time 30

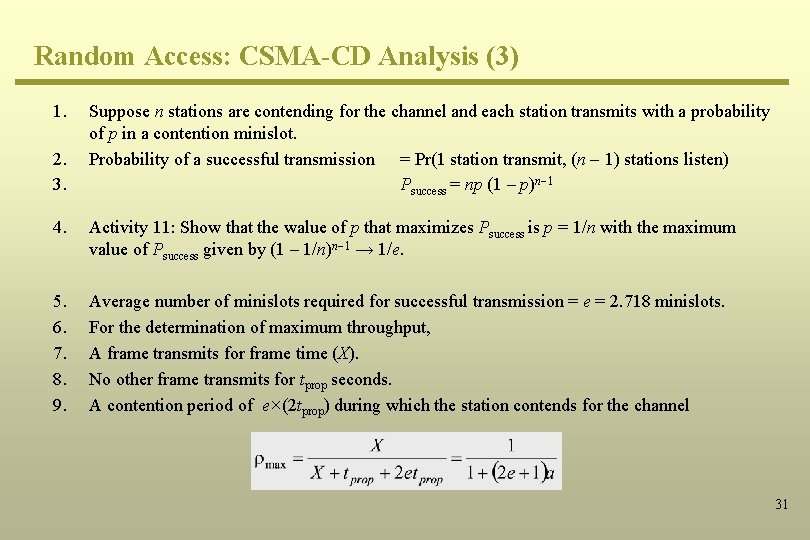
Random Access: CSMA-CD Analysis (3) 1. 2. 3. Suppose n stations are contending for the channel and each station transmits with a probability of p in a contention minislot. Probability of a successful transmission = Pr(1 station transmit, (n - 1) stations listen) Psuccess = np (1 – p)n-1 4. Activity 11: Show that the walue of p that maximizes Psuccess is p = 1/n with the maximum value of Psuccess given by (1 – 1/n)n-1 → 1/e. 5. 6. 7. 8. 9. Average number of minislots required for successful transmission = e = 2. 718 minislots. For the determination of maximum throughput, A frame transmits for frame time (X). No other frame transmits for tprop seconds. A contention period of e×(2 tprop) during which the station contends for the channel 31

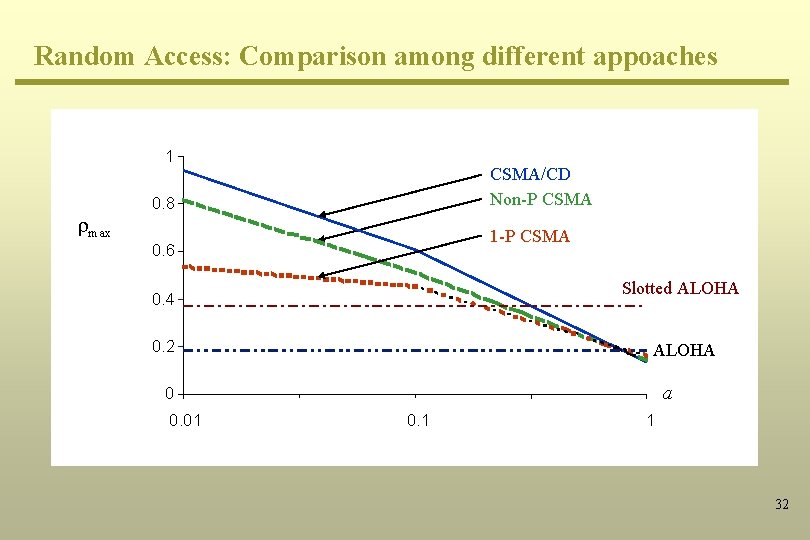
Random Access: Comparison among different appoaches 1 rmax CSMA/CD Non-P CSMA 0. 8 1 -P CSMA 0. 6 Slotted ALOHA 0. 4 0. 2 ALOHA a 0 0. 01 0. 1 1 32