Correlation Power Analysis of AES128 By Jessica Liao

Correlation Power Analysis of AES-128 By Jessica Liao, Andover High School and Faraz Iqbal, Franklin High School Professor Yunsi Fei, Electrical and Computer Engineering, Northeastern University Cheng Gongye, Ph. D. Candidate, Northeastern University

Overview: ➢ Cryptography (Understanding it / AES) ➢ Hamming power consumption models and Pearson’s Correlation Coefficient ➢ Implementation through code to recover the AES 128 key
Cryptography: Creator’s Note: Real code does not look as cool as this. Source: Wallpaper. Flare Source: Wiki. Media Source: Flickr
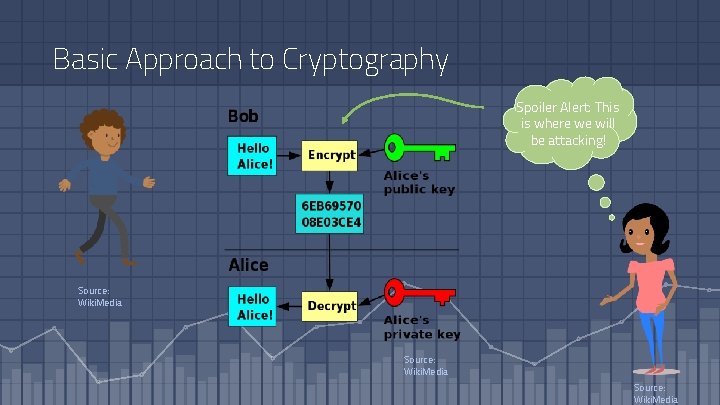
Basic Approach to Cryptography Spoiler Alert: This is where we will be attacking! Source: Wiki. Media
Why research AES-128 and CPA? Security Codes Encryption Protection with AES -128 Source: Needpix Anti-Virus Protection Passwords Source: Pixabay Source: Wiki. Media Source: Freesvg Source: Pngio Because attacks could happen every single day… You will never now. . .

AES-128 - Advanced Encryption System The key bits, is 128 expl which a traili ins the ng 1 28. ore m is a k into s i Th d loo ion aile crypt ned t e d En entio e h t s m r! s e c lie pro ear Source: Professor Yunsi Fei’s Presentation on Power Analysis Attacks
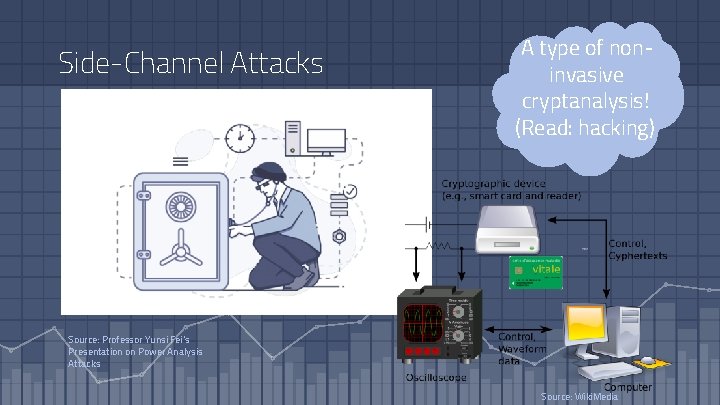
Side-Channel Attacks A type of noninvasive cryptanalysis! (Read: hacking) Source: Professor Yunsi Fei’s Presentation on Power Analysis Attacks Source: Wiki. Media
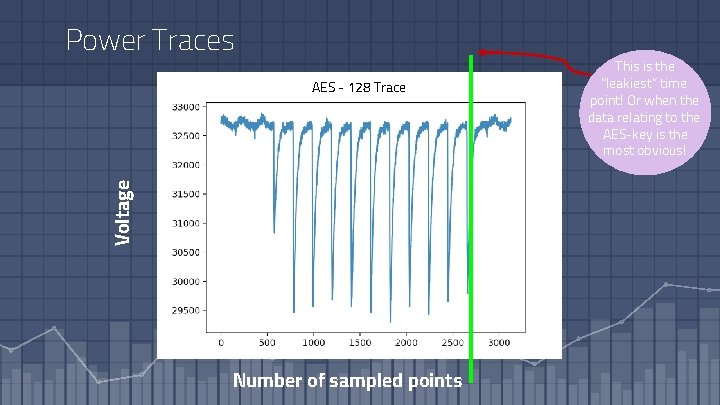
Power Traces Voltage AES - 128 Trace Number of sampled points This is the “leakiest” time point! Or when the data relating to the AES-key is the most obvious!
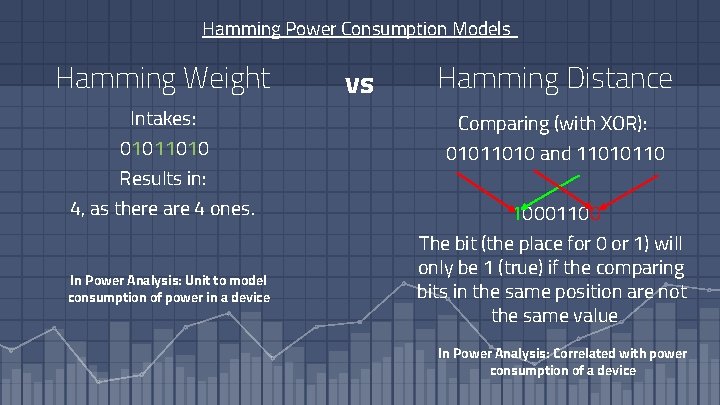
Hamming Power Consumption Models Hamming Weight Intakes: 01011010 Results in: 4, as there are 4 ones. In Power Analysis: Unit to model consumption of power in a device vs Hamming Distance Comparing (with XOR): 01011010 and 11010110 10001100 The bit (the place for 0 or 1) will only be 1 (true) if the comparing bits in the same position are not the same value In Power Analysis: Correlated with power consumption of a device
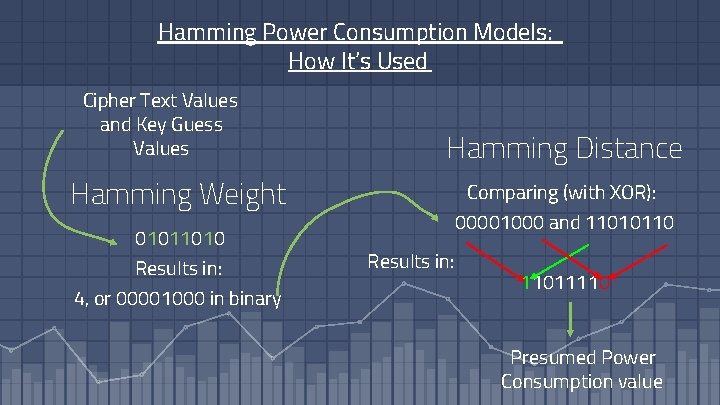
Hamming Power Consumption Models: How It’s Used Cipher Text Values and Key Guess Values Hamming Distance Hamming Weight 01011010 Results in: 4, or 00001000 in binary Comparing (with XOR): 00001000 and 11010110 Results in: 11011110 Presumed Power Consumption value
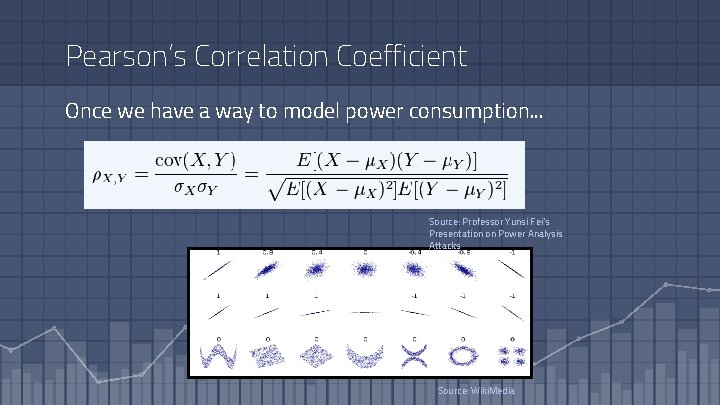
Pearson’s Correlation Coefficient Once we have a way to model power consumption. . . Source: Professor Yunsi Fei’s Presentation on Power Analysis Attacks Source: Wiki. Media
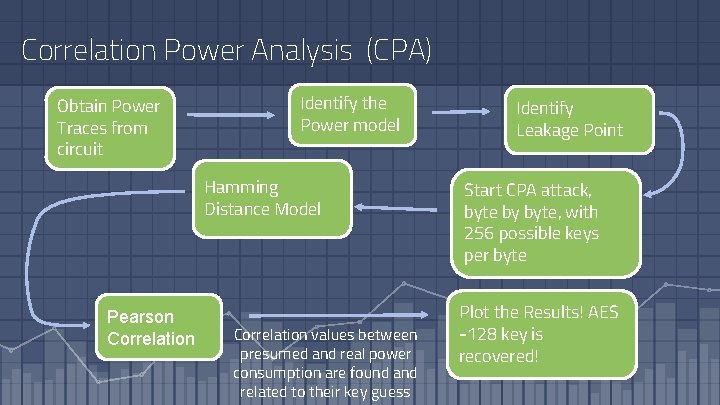
Correlation Power Analysis (CPA) Obtain Power Traces from circuit Identify the Power model Hamming Distance Model Pearson Correlation values between presumed and real power consumption are found and related to their key guess Identify Leakage Point Start CPA attack, byte by byte, with 256 possible keys per byte Plot the Results! AES -128 key is recovered!
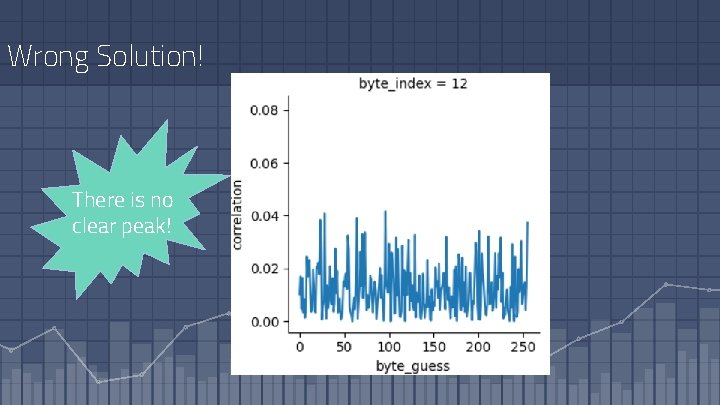
Wrong Solution! There is no clear peak!
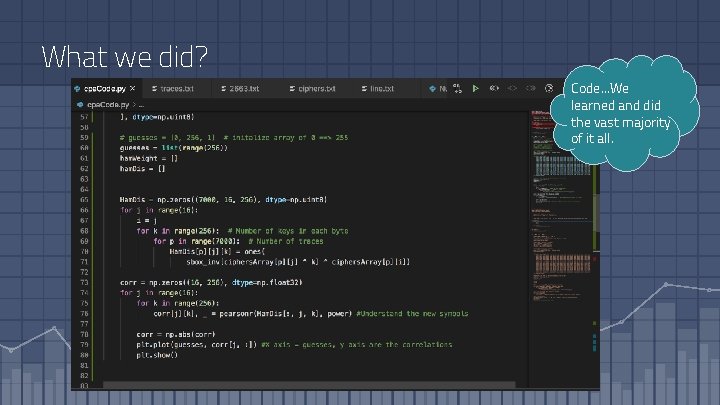
What we did? Code. . . We learned and did the vast majority of it all.
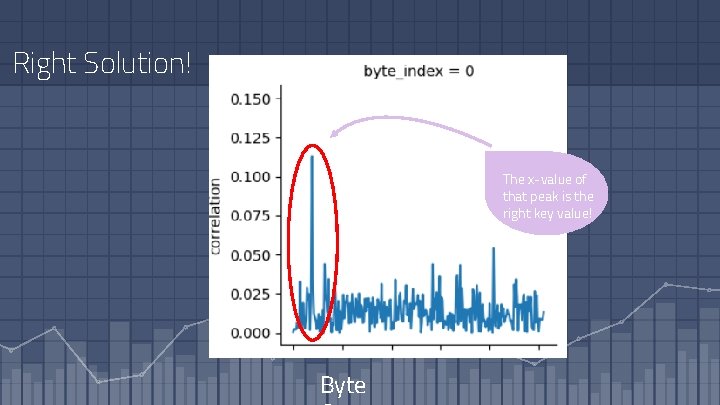
Right Solution! The x-value of that peak is the right key value! Byte
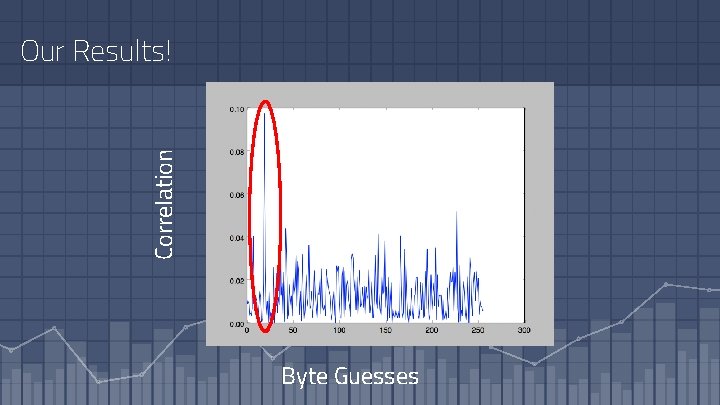
Correlation Our Results! Byte Guesses
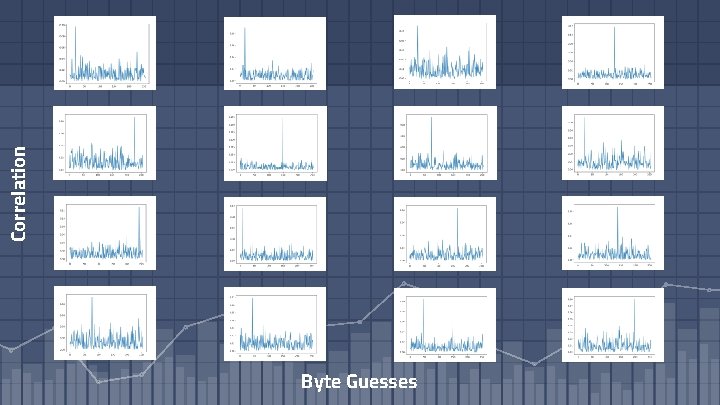
Correlation Byte Guesses

Conclusions, Future Studies, Takeaways ▫ CPA can be used to recover AES-128 keys ▫ The recovering of the AES-128 key for one byte can be extended to find all 16 bytes ▫ This can be used to test the security of a computer’s hardware with this specific type of encryption algorithm ▫ The effect of AES-128 on computer hardware while running can be tested for different ways to mitigate the amounts of information being released
Acknowledgements Department of Electrical and Computer Engineering: Professor Yunsi Fei, Electrical and Computer Engineering, Northeastern University you k n a Th all!! Cheng Gongye, Ph. D Candidate, Northeastern University Center for STEM Education: Nataasha Zaarour and Salima Amiji, YSP Coordinators, Center for STEM Education Claire Duggans, Program Director, Center for STEM Education Nicholas Fuchs, Project Implementation Coordinator, Center for STEM Education This work was supported in part by the National Science Foundation under grants Sa. TC 1929300 and Sa. TC 1563697.

References ▫ Brier E. , Clavier C. , Olivier F. (2004) Correlation Power Analysis with a Leakage Model. In: Joye M. , Quisquater JJ. (eds) Cryptographic Hardware and Embedded Systems - CHES 2004. Lecture Notes in Computer Science, vol 3156. Springer, Berlin, Heidelberg ▫ Kocher P. , Jaffe J. , Jun B. (1999) Differential Power Analysis. In: Wiener M. (eds) Advances in Cryptology — CRYPTO’ 99. CRYPTO 1999. Lecture Notes in Computer Science, vol 1666. Springer, Berlin, Heidelberg. ▫ Professor Yunsi Fei’s Slideshow on DPA and CPA Attacks

Want to see this presentation again? Questions? Feel free to contact us: ➢ Jessica: jessica. jia. liao@gmail. com ➢ Faraz: faraz. norwood@gmail. com Check out our posters!
Posters Link More Text: https: //docs. google. com/presentation/d/1 Es. RWdx. Gw 1 rsms. Gli. On 9 EHube. GZ 1 Bjuf. N Do. XFp-zy. Hew/edit#slide=id. p 1 Less Text: https: //docs. google. com/presentation/d/1 Az 8 g 2 p. WHN 7 o. Ci 2 q. Yr 363 n. C 7 WMNj 9 p 3 QH 5 RUpfu. Gdyg/edit? usp=sharing

Image Credits Slide 3: Gustafson, A. (2007, December 27). We don't speak pig latin. . . Retrieved from https: //www. flickr. com/photos/aarongustafson/2140099480 HD wallpaper: Photo of Green Data Matrix, access, close-up, coded, codes. (n. d. ). Retrieved from https: //www. wallpaperflare. com/photo-of-green-data-matrixaccess-close-up-coded-codes-wallpaper-arvcy Cipher - https: //commons. wikimedia. org/wiki/File: Ac 2_cipher_key. png Cesar Shift - https: //commons. wikimedia. org/wiki/File: Caesar_cipher_Encode_and_Decode. PNG Slide 4: File: Black Man Walking Cartoon Vector. svg. (n. d. ). Retrieved from https: //commons. wikimedia. org/wiki/File: Black_Man_Walking_Cartoon_Vector. svg File: Public key encryption. svg. (n. d. ). Retrieved from https: //commons. wikimedia. org/wiki/File: Public_key_encryption. svg Vedran. (n. d. ). Cartoon girl with black hair. Retrieved from https: //freesvg. org/cartoon-girl-with-black-hair Slide 5: File: Credit or Debit Card Flat Icon Vector. svg. (n. d. ). Retrieved from https: //commons. wikimedia. org/wiki/File: Credit_or_Debit_Card_Flat_Icon_Vector. svg Piggy bank, piggy, bank, transparent, money - free image from needpix. com. (n. d. ). Retrieved from https: //www. needpix. com/photo/641997/piggy-bank-piggy-banktransparent-money-finance-pig-currency-save Silver Shield Png. (n. d. ). Retrieved from https: //pngio. com/PNG/a 37871 -silver-shield-png. html Vedran. (n. d. ). Anonymous hacker vector image. Retrieved from https: //freesvg. org/anonymous-hacker-vector-image Padlock File - https: //pixabay. com/illustrations/padlock-files-passwords-secure-3998764/ Slide 6: AES Diagram - Professor Yunsi Fei’s Presentation on Power Analysis Attacks Slide 7: Blue Person - Professor Yunsi Fei’s Presentation on Power Analysis Attacks Side Channel Attacks: Power analysis. (2020, July 23). Retrieved from https: //en. wikipedia. org/wiki/Power_analysis#/media/File: Differential_power_analysis. svg Slide 11: Pearson Correlation - Professor Yunsi Fei’s Presentation on Power Analysis Attacks Side Channel Attacks: https: //commons. wikimedia. org/wiki/File: Correlation_examples. png
- Slides: 23