Copyright 2012 Ping Identity Corporation All rights reserved











- Slides: 22

Copyright © 2012 Ping Identity Corporation. All rights reserved.

Unified Identity in Cloud Architectures EEMA 2012 • • • John Bradley @ve 7 jtb Office of the CTO • 2 Copyright © 2012 Ping Identity Corporation. All rights reserved.

Future of IT Architecture • Thousands of applications and services -- everywhere – Some you can control • Local web services • Local infrastructure • Apps/Services on Iaa. S – Many you can’t control • • 3 © 2011 Ping Identity Corporation Saa. S APIs Paa. S APIs Iaa. S APIs Partner APIs Copyright © 2012 Ping Identity Corporation. All rights reserved. 3

Ultimate Decentralization • Diversity of Architecture – If the cloud vendor’s coding philosophy conflicts with yours, you must adapt • Limited Visibility – No database access – No direct audit file access • No Contractual Power – Like it or lump it 4 Copyright © 2012 Ping Identity Corporation. All rights reserved. 4

Decentralization == Chaos? • Business Managers operating administration consoles • Developers writing API code for the business – Native Mobile apps – Mashups – Are they security specialists? • Silos of work with no central control 5 © 2011 Ping Identity Corporation Copyright © 2012 Ping Identity Corporation. All rights reserved. 5

Fragmentation Causes Risk • Business Agility suffers – Decision making is impaired • IT response time is low – Every application and service has to be treated differently • Productivity suffers – Every application looks and feels different – No secure “ceremony” for users – Developers must re-invent a new process every time • Risk to the organization increases – What happens when you fire somebody? 6 © 2011 Ping Identity Corporation Copyright © 2012 Ping Identity Corporation. All rights reserved. 6

Solution: Centralize & Adapt • Industry has adopted “federated identity” to move security decisions into central infrastructure • Federated protocols now exist to protect both web applications and APIs • Eg SAML, WS-Trust, OAuth 2. 0, and open. ID Connect 7 © 2011 Ping Identity Corporation Copyright © 2012 Ping Identity Corporation. All rights reserved. 7

What does this mean? • Developers don’t set passwords in code – They ask for a token – Token is used during API calls • Applications don’t store passwords – They rely on a central authority to identify the user – They validate the central authority not the user • Central Infrastructure does the rest – Password validation, security, risk/fraud 8 Copyright © 2012 Ping Identity Corporation. All rights reserved. 8

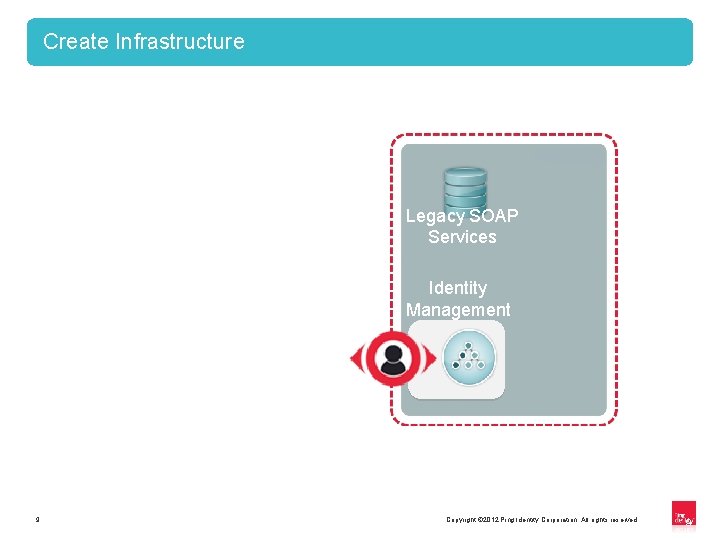
Create Infrastructure Legacy SOAP Services Identity Management 9 Copyright © 2012 Ping Identity Corporation. All rights reserved. 9

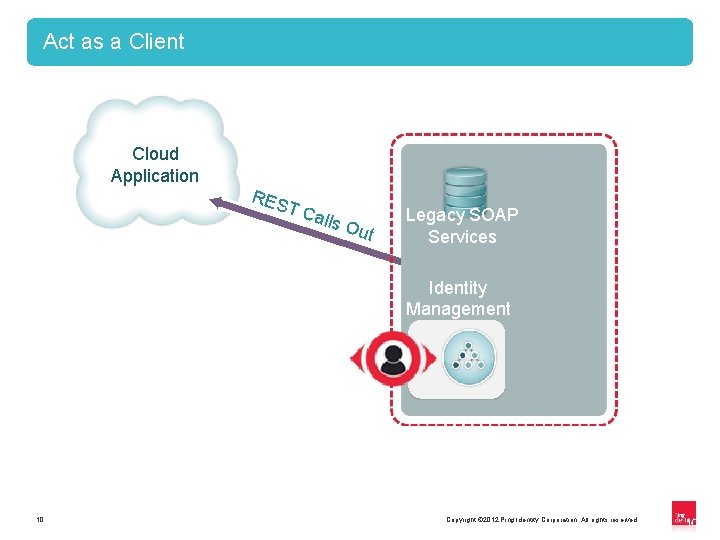
Act as a Client Cloud Application RES TC alls Out Legacy SOAP Services Identity Management 10 Copyright © 2012 Ping Identity Corporation. All rights reserved. 10

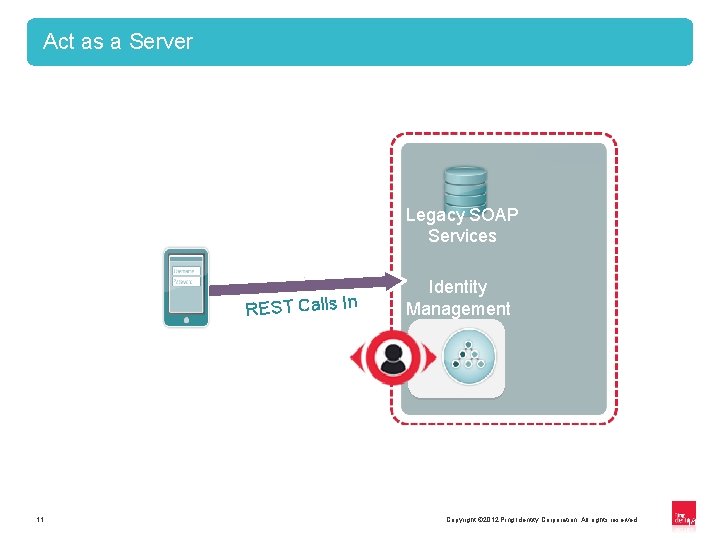
Act as a Server Legacy SOAP Services REST Calls In 11 Identity Management Copyright © 2012 Ping Identity Corporation. All rights reserved. 11

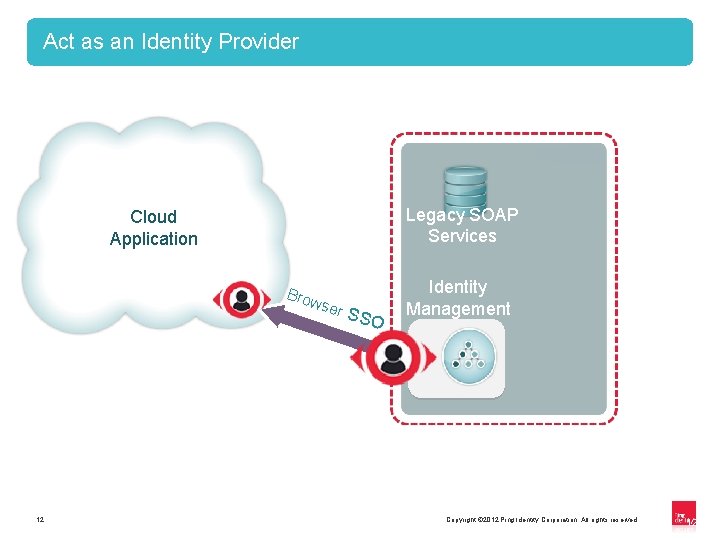
Act as an Identity Provider Legacy SOAP Services Cloud Application Brow ser 12 SSO Identity Management Copyright © 2012 Ping Identity Corporation. All rights reserved. 12

Leverage with Mobile Apps en e Tok 3. Us I Calls P For A REST Calls In Legacy SOAP Services 2. Transform Attributes Identity Management 1. Fet Use B ch O ro auth wser 2. 0 to Tok en 13 Copyright © 2012 Ping Identity Corporation. All rights reserved. 13

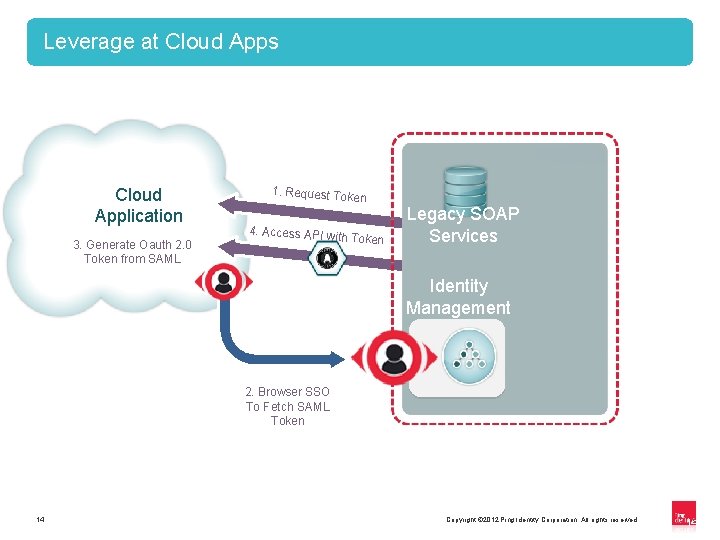
Leverage at Cloud Apps Cloud Application 3. Generate Oauth 2. 0 Token from SAML 1. Request Toke n 4. Access API with Token Legacy SOAP Services Identity Management 2. Browser SSO To Fetch SAML Token 14 Copyright © 2012 Ping Identity Corporation. All rights reserved. 14

Concrete Example: OAuth 2. 0 with SAML 15 Copyright © 2012 Ping Identity Corporation. All rights reserved. 15

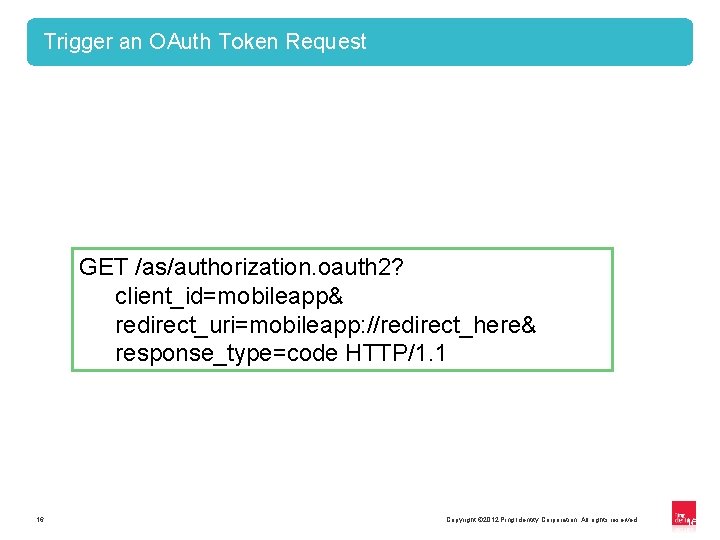
Trigger an OAuth Token Request GET /as/authorization. oauth 2? client_id=mobileapp& redirect_uri=mobileapp: //redirect_here& response_type=code HTTP/1. 1 16 Copyright © 2012 Ping Identity Corporation. All rights reserved. 16

User Logs in at Enterprise 17 Copyright © 2012 Ping Identity Corporation. All rights reserved. 17

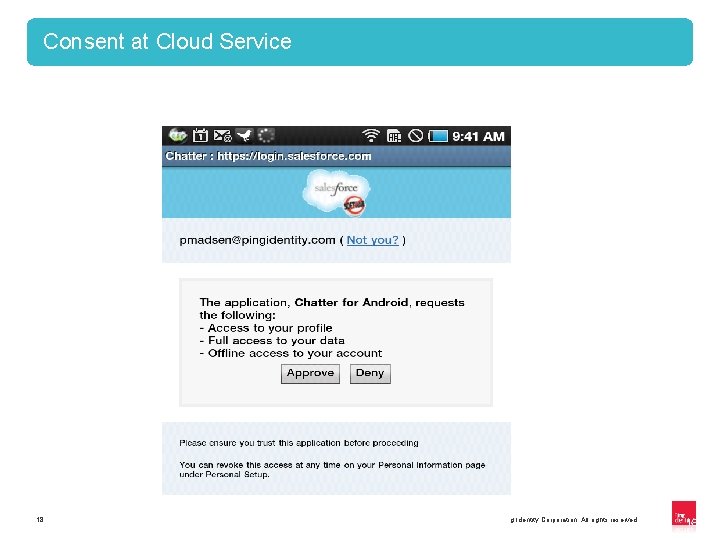
Consent at Cloud Service 18 Copyright © 2012 Ping Identity Corporation. All rights reserved. 18

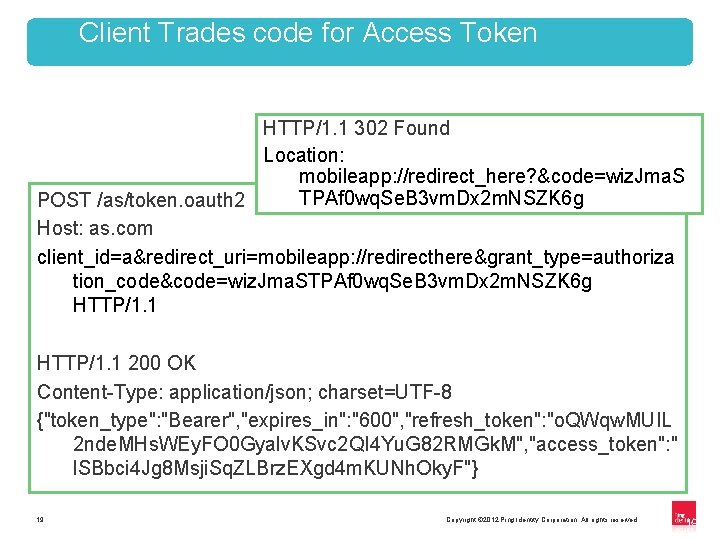
Client Trades code for Access Token HTTP/1. 1 302 Found Location: mobileapp: //redirect_here? &code=wiz. Jma. S TPAf 0 wq. Se. B 3 vm. Dx 2 m. NSZK 6 g POST /as/token. oauth 2 Host: as. com client_id=a&redirect_uri=mobileapp: //redirecthere&grant_type=authoriza tion_code&code=wiz. Jma. STPAf 0 wq. Se. B 3 vm. Dx 2 m. NSZK 6 g HTTP/1. 1 200 OK Content-Type: application/json; charset=UTF-8 {"token_type": "Bearer", "expires_in": "600", "refresh_token": "o. QWqw. MUIL 2 nde. MHs. WEy. FO 0 Gyalv. KSvc 2 QI 4 Yu. G 82 RMGk. M", "access_token": " l. SBbci 4 Jg 8 Msji. Sq. ZLBrz. EXgd 4 m. KUNh. Oky. F"} 19 Copyright © 2012 Ping Identity Corporation. All rights reserved. 19

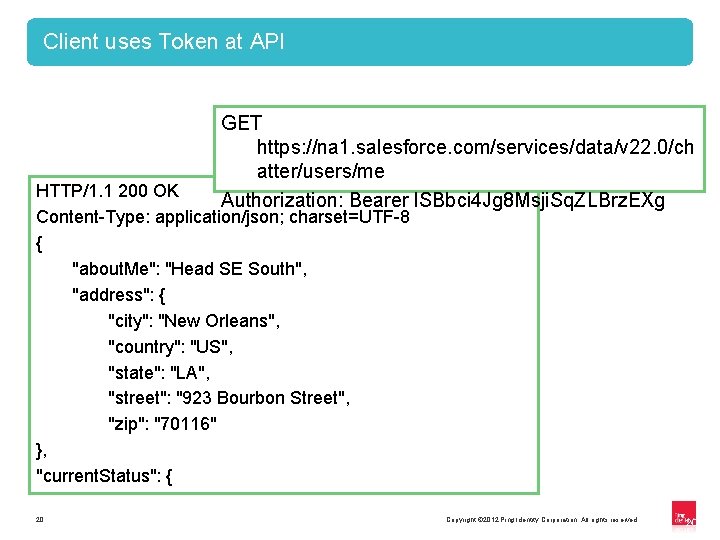
Client uses Token at API GET https: //na 1. salesforce. com/services/data/v 22. 0/ch atter/users/me Authorization: Bearer l. SBbci 4 Jg 8 Msji. Sq. ZLBrz. EXg HTTP/1. 1 200 OK Content-Type: application/json; charset=UTF-8 { "about. Me": "Head SE South", "address": { "city": "New Orleans", "country": "US", "state": "LA", "street": "923 Bourbon Street", "zip": "70116" }, "current. Status": { 20 Copyright © 2012 Ping Identity Corporation. All rights reserved. 20

Architecture Advantages • Users always authenticate in the same place – Teach them to expect your ceremony – Protect against the Password Antipattern • Developers never see or store passwords – Only need to know how to ask for a token and use it at APIs – Or –ask once for credentials but never store them • IT oversees every authentication – One attack surface & security plan – One audit point • Same infrastructure regardless of medium – Web or web service 21 Copyright © 2012 Ping Identity Corporation. All rights reserved.

Cloud Identity Management • Centralizes Cloud Access Control • Strengthens Security • Integrates with Existing Infrastructure • Simplifies Password Maintenance • Deploys in Days • http: //www. pingidentity. com 22 © 2011 Ping Identity Corporation Copyright © 2012 Ping Identity Corporation. All rights reserved. 22
 Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Copyright 2015 all rights reserved
Copyright 2015 all rights reserved Copyright 2015 all rights reserved
Copyright 2015 all rights reserved Dell all rights reserved copyright 2009
Dell all rights reserved copyright 2009 Copyright © 2018 all rights reserved
Copyright © 2018 all rights reserved All rights reserved example
All rights reserved example All rights reserved sentence
All rights reserved sentence Freesound content licence
Freesound content licence Confidential all rights reserved
Confidential all rights reserved Sentinel-controlled repetition
Sentinel-controlled repetition Pearson education inc all rights reserved
Pearson education inc all rights reserved Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Warning all rights reserved
Warning all rights reserved All rights reserved c
All rights reserved c All rights reserved formula
All rights reserved formula Warning all rights reserved
Warning all rights reserved Confidential all rights reserved
Confidential all rights reserved Pearson education inc. all rights reserved
Pearson education inc. all rights reserved 2017 all rights reserved
2017 all rights reserved Copyright 2010 pearson education inc
Copyright 2010 pearson education inc