Copyright 2009 11 1 The Cloudy Future of





























![Second-Party Risk-Exposure The [Semi-Arbitrary] Scores Copyright 2009 -11 Dropbox 7. 5 MS Live 7. Second-Party Risk-Exposure The [Semi-Arbitrary] Scores Copyright 2009 -11 Dropbox 7. 5 MS Live 7.](https://slidetodoc.com/presentation_image_h2/9078578db61525ddbd822b4f8e3aa50d/image-41.jpg)





- Slides: 48

Copyright 2009 -11 1

The Cloudy Future of Consumer Computing Roger Clarke Xamax Consultancy and PSARN Security, Canberra Visiting Professor in Computer Science, ANU and in Cyberspace Law & Policy, UNSW ANU RSCS Seminar Information and Human-Centred Computing Group 16 August 2011 http: //www. rogerclarke. com/EC/CCC. html, CCC-ANU. ppt Copyright 2009 -11 2

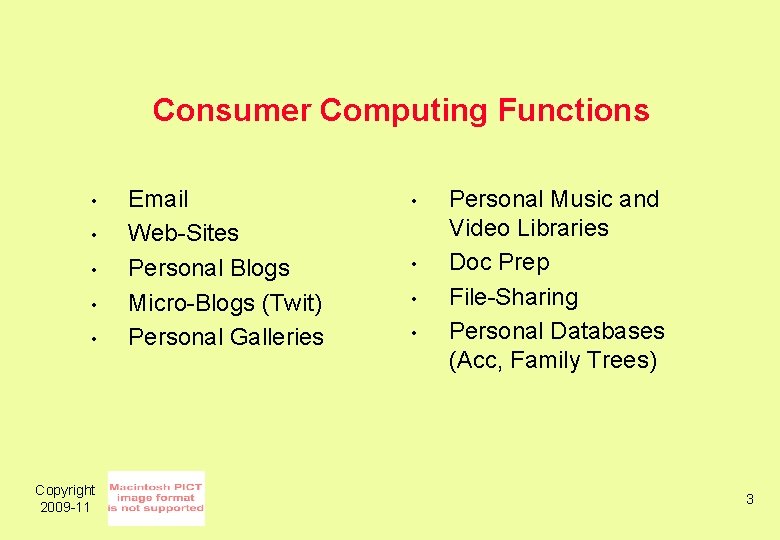
Consumer Computing Functions • • • Copyright 2009 -11 Email Web-Sites Personal Blogs Micro-Blogs (Twit) Personal Galleries • • Personal Music and Video Libraries Doc Prep File-Sharing Personal Databases (Acc, Family Trees) 3

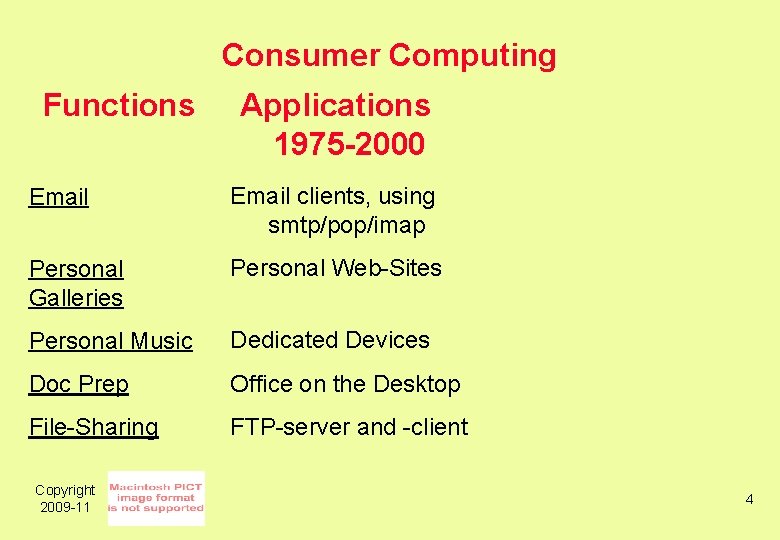
Consumer Computing Functions Applications 1975 -2000 Email clients, using smtp/pop/imap Personal Galleries Personal Web-Sites Personal Music Dedicated Devices Doc Prep Office on the Desktop File-Sharing FTP-server and -client Copyright 2009 -11 4

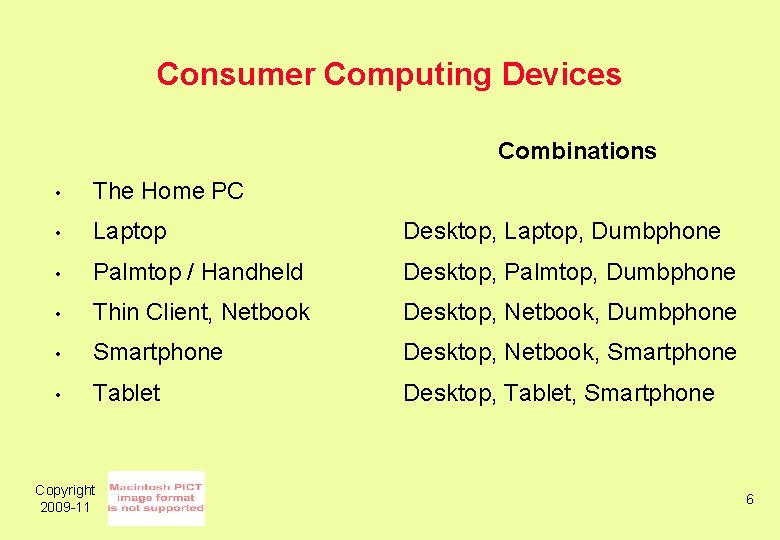
Consumer Computing Devices • The Home PC • Laptop • Palmtop / Handheld • Thin Client, Netbook • Smartphone • Tablet Copyright 2009 -11 5

Consumer Computing Devices Combinations • The Home PC • Laptop Desktop, Laptop, Dumbphone • Palmtop / Handheld Desktop, Palmtop, Dumbphone • Thin Client, Netbook Desktop, Netbook, Dumbphone • Smartphone Desktop, Netbook, Smartphone • Tablet Desktop, Tablet, Smartphone Copyright 2009 -11 6

Consumer Computing Devices Screen-Size Tech Capability • The Home PC Substantial Some Needed • Laptop Substantial Some Needed • Palmtop / Handheld Limited None Needed • Thin Client, Netbook Moderate Some Needed • Smartphone Limited None Needed • Tablet Moderate None Allowed Copyright 2009 -11 7

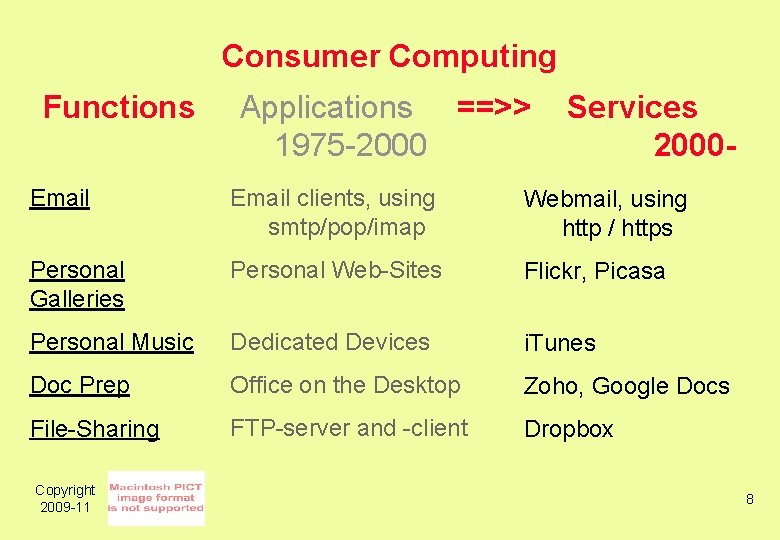
Consumer Computing Functions Applications ==>> 1975 -2000 Services 2000 - Email clients, using smtp/pop/imap Webmail, using http / https Personal Galleries Personal Web-Sites Flickr, Picasa Personal Music Dedicated Devices i. Tunes Doc Prep Office on the Desktop Zoho, Google Docs File-Sharing FTP-server and -client Dropbox Copyright 2009 -11 8

The Research Question How well are Consumer Computing Services satisfying consumers’ needs? To the extent that there are problems, what should be done about them? Copyright 2009 -11 9

Challenges Inherent in the Research Domain • Diversity among: • Consumers • Technologies • Consumer uses of technologies • Ongoing, rapid change / unstable phenomena • Can 'consumer requirements' be operationalised? • Can 'consumer disbenefits and risks' be evaluated? Copyright 2009 -11 10

Consumers – Segmentation • • Opportunity-Awareness Leadership / Followership Risk-Awareness, Risk-Aversion • Age / 'Generation' • • Copyright 2009 -11 Education, Income, Wealth Infrastructure Availability Technical Capability 11

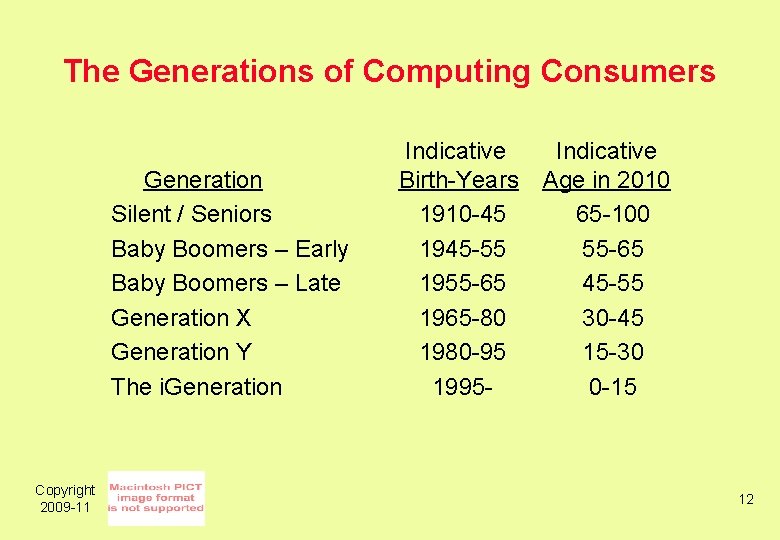
The Generations of Computing Consumers Generation Silent / Seniors Baby Boomers – Early Baby Boomers – Late Generation X Generation Y The i. Generation Copyright 2009 -11 Indicative Birth-Years 1910 -45 1945 -55 1955 -65 1965 -80 1980 -95 1995 - Indicative Age in 2010 65 -100 55 -65 45 -55 30 -45 15 -30 0 -15 12

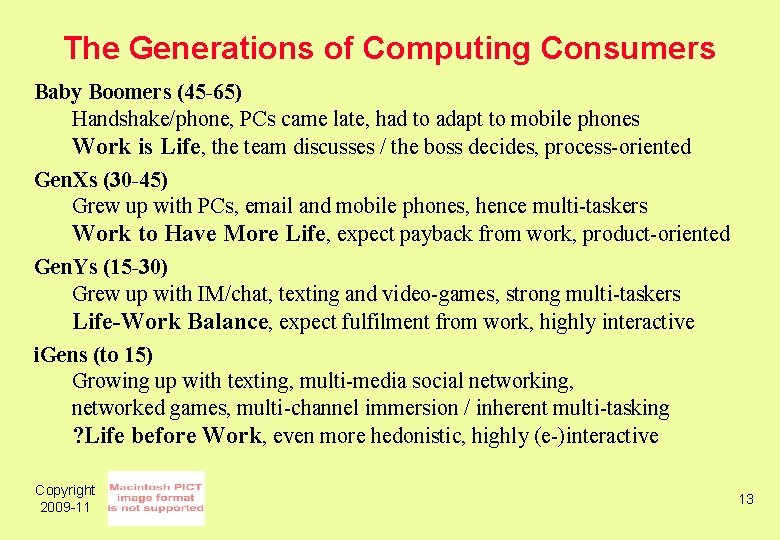
The Generations of Computing Consumers Baby Boomers (45 -65) Handshake/phone, PCs came late, had to adapt to mobile phones Work is Life, the team discusses / the boss decides, process-oriented Gen. Xs (30 -45) Grew up with PCs, email and mobile phones, hence multi-taskers Work to Have More Life, expect payback from work, product-oriented Gen. Ys (15 -30) Grew up with IM/chat, texting and video-games, strong multi-taskers Life-Work Balance, expect fulfilment from work, highly interactive i. Gens (to 15) Growing up with texting, multi-media social networking, networked games, multi-channel immersion / inherent multi-tasking ? Life before Work, even more hedonistic, highly (e-)interactive Copyright 2009 -11 13

Requirements, Disbenefits and Risks The Organisational Perspective 1. Operational Requirements Dependability on a day-to-day basis 2. Contingent Risks Low likelihood, but highly significant 3. Security Risks 4. Commercial Disbenefits and Risks 5. Compliance Disbenefits and Risks Copyright 2009 -11 14

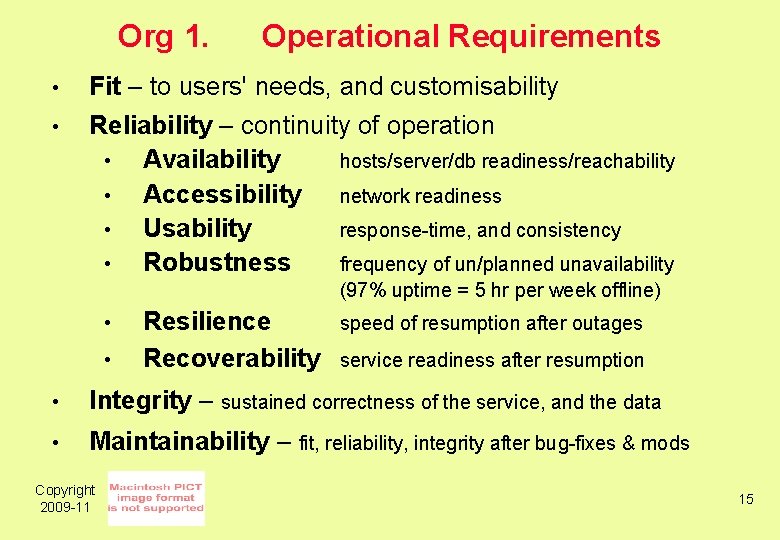
Org 1. • • Operational Requirements Fit – to users' needs, and customisability Reliability – continuity of operation • Availability hosts/server/db readiness/reachability • Accessibility network readiness • Usability response-time, and consistency • Robustness frequency of un/planned unavailability (97% uptime = 5 hr per week offline) • • Resilience Recoverability speed of resumption after outages service readiness after resumption • Integrity – sustained correctness of the service, and the data • Maintainability – fit, reliability, integrity after bug-fixes & mods Copyright 2009 -11 15

Org 2. • • Contingent Risks Major Service Interruptions Service Survival – supplier collapse or withdrawal Safeguards include software escrow; escrow inspection; proven recovery procedures; rights that are proof against actions by receivers • • Data Survival – data backup/mirroring/synch, accessibility Data Acessibility – blockage by opponents or a foreign power Compatibility – software, versions, protocols, data formats Flexibility Customisation Forward-Compatibility Backward-Compatibility Lateral Compatibility Copyright 2009 -11 to migrate to new levels to protect legacy systems to enable dual-sourcing and escape 16

Consumer Requirements and Risks – 1 of 3 The Basic Needs • • Does it do what I want it to do? [Fit] Will it be there when I want it? [Availability, Reliability] Copyright 2009 -11 17

Consumer Requirements and Risks – 1 of 3 The Basic Needs • • Does it do what I want it to do? [Fit] Will it be there when I want it? [Availability, Reliability] The Basic Protections • • • How do I keep going if it stays fallen over for a long time? [Service Interruptions] Will you respond helpfully and quickly enough when I ask for help? [Customer Service] Will you lose my data, or muck it up? [Data Integrity] Do I get my data back if you fall over or withdraw the service? [Survival] Can I move my data to another supplier? [Lateral Compatibility] Who can I complain to if I get dudded, and will they actually help me? [Consumer Protection] Copyright 2009 -11 18

Consumer Requirements and Risks – 2 of 3 More Advanced Needs • • • Will it keep doing what it does now? [Service Integrity] Will it stay up-to-date? [Future Fit] Will it fall over too often? [Robustness] Will it come back quickly after it falls over? [Resilience] Is my service protected against you, them and the gods? [Service Security] If bits of it are broken, will you fix it without breaking it some more? [Maintainability] Can I fiddle with it a bit if I need to? [Flexibility] Can I move my data to an upgraded version? [Forward Compatibility] How long will old versions keep working for me? [Backward Compatibility] Am I breaking the law if I use the service? [Legal Compliance] Copyright 2009 -11 19

Consumer Requirements and Risks – 3 of 3 More Advanced Protections • • Am I going to get gouged? [Cost] Can only appropriate people get in and do things? [Authentication and Authorisation] Can I get access to all data that you hold about me? [Subject Access] Is my data protected against you, them and the gods? [Data Security] Is my privacy protected against you, them and the gods? [Privacy Controls] If I terminate our relationship, will my data be irretrievably deleted? [Fully Effective Withdrawal] What happens to my data if I die? [Archival / Memorialisation] Copyright 2009 -11 20

How well are Consumer Computing Services satisfying consumers’ needs? Copyright 2009 -11 • Ask Consumers • using Surveys • using Focus Groups • using Reps and Advocates • Conduct Field Studies • of Consumer Behaviour • of Corporate Undertakings 21

How are Consumer Requirements Satisfied? & How are Consumer Risks Managed? Copyright 2009 -11 • Through the Provider: • Practices • Policies • Terms of Service • Through the State: • Law • Regulatory Resources • Regulatory Enforcement • Through Private Litigation 22

How are Consumer Requirements Satisfied? & How are Consumer Risks Managed? Copyright 2009 -11 • Through the Provider: • Practices • Policies • Terms of Service (To. S) • Through the State: • Law • Regulatory Resources • Regulatory Enforcement • Through Private Litigation 23

Research Method Preliminary Phase • . . . Copyright 2009 -11 Empirical Phase • Validation of the Spec for Consumer Requirements • Sample Selection • In-Depth To. S Studies • Comparative To. S Studies Articulation Phase • . . . 24

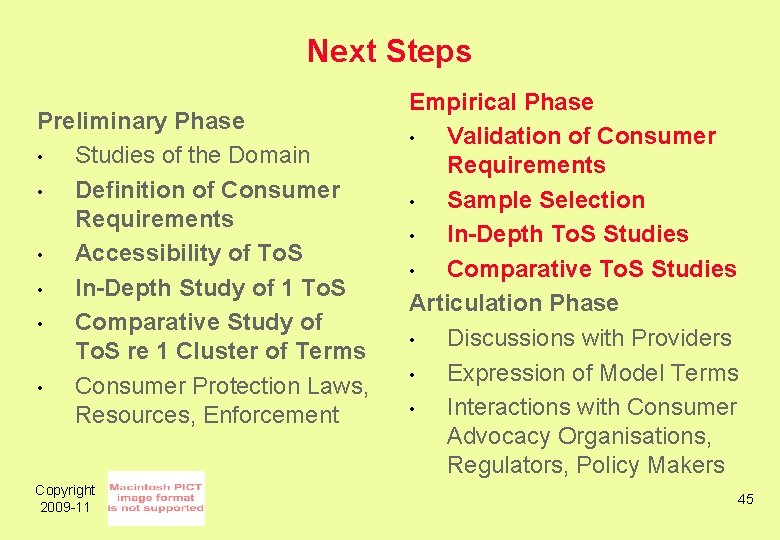
Research Method Preliminary Phase • Studies of the Domain • Specification of Consumer Requirements • Accessibility of To. S • In-Depth Study of 1 To. S • Comparative Study of To. S re 1 Cluster of Terms • Consumer Protection Laws, Resources, Enforcement Copyright 2009 -11 Empirical Phase • Validation of the Spec for Consumer Requirements • Sample Selection • In-Depth To. S Studies • Comparative To. S Studies Articulation Phase • . . . 25

Research Method Preliminary Phase • Studies of the Domain • Specification of Consumer Requirements • Accessibility of To. S • In-Depth Study of 1 To. S • Comparative Study of To. S re 1 Cluster of Terms • Consumer Protection Laws, Resources, Enforcement Copyright 2009 -11 Empirical Phase • Validation of the Spec for Consumer Requirements • Sample Selection • In-Depth To. S Studies • Comparative To. S Studies Articulation Phase • Discussions with Providers • Expression of Model Terms • Interactions with Consumer Advocacy Organisations, Regulators, Policy Makers 26

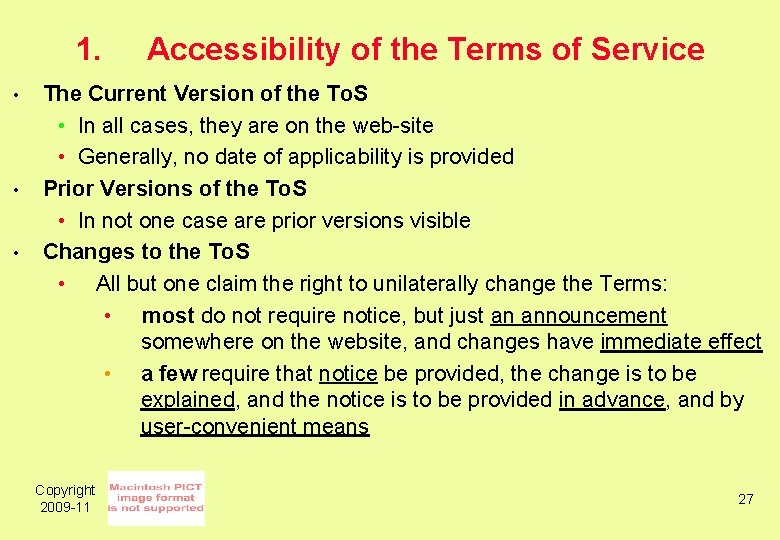
1. • • • Accessibility of the Terms of Service The Current Version of the To. S • In all cases, they are on the web-site • Generally, no date of applicability is provided Prior Versions of the To. S • In not one case are prior versions visible Changes to the To. S • All but one claim the right to unilaterally change the Terms: • most do not require notice, but just an announcement somewhere on the website, and changes have immediate effect • a few require that notice be provided, the change is to be explained, and the notice is to be provided in advance, and by user-convenient means Copyright 2009 -11 27

Accessibility of the Terms of Service The Significance for Consumers • • Consumers can only know what Terms apply to an earlier transaction if they mirrored the Terms at the time The Terms applicable to the next transaction may not be the same as they were for previous transactions The Terms applicable to transactions and to the consumer’s data are entirely under the provider's control Consumers can place no reliance on what they may have previously read or heard about the Terms Copyright 2009 -11 28

2. In-Depth Study of Terms of Service Linked. In A (‘social’) networking service for professionals A Priori: • Its users should be well-informed and demanding • So the provider is likely to: • address its customers' needs • balance their interests against the company's • Copyright 2009 -11 So it can be expected to provide a benchmark 29

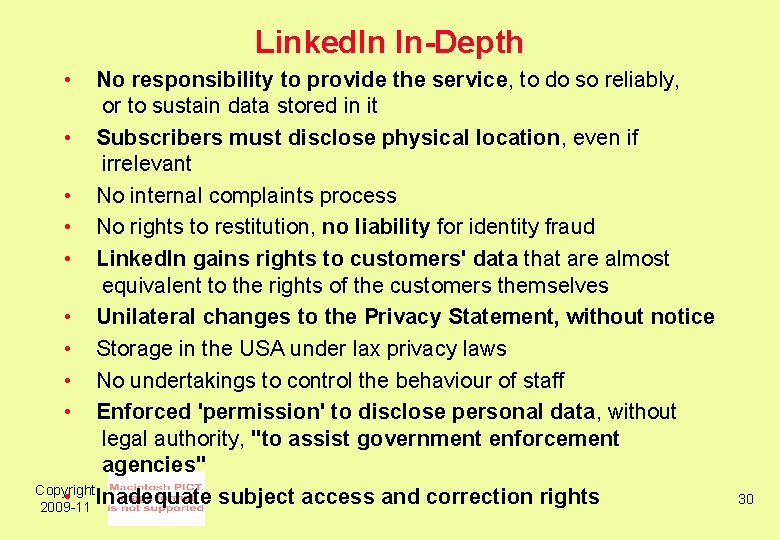
Linked. In In-Depth • No responsibility to provide the service, to do so reliably, or to sustain data stored in it • Subscribers must disclose physical location, even if irrelevant • No internal complaints process • No rights to restitution, no liability for identity fraud • Linked. In gains rights to customers' data that are almost equivalent to the rights of the customers themselves • Unilateral changes to the Privacy Statement, without notice • Storage in the USA under lax privacy laws • No undertakings to control the behaviour of staff • Enforced 'permission' to disclose personal data, without legal authority, "to assist government enforcement agencies" Copyright • Inadequate subject access and correction rights 2009 -11 30

Linked. In In-Depth The Significance for Consumers • • Linked. In projects itself as a networking service for well-informed and demanding professionals It was expected to provide a benchmark In fact, many aspects are badly handled • Not a benchmark, but rather a serious concern • Copyright 2009 -11 31

Copyright 2009 -11 32

. . . Copyright 2009 -11 http: //www. theregister. co. uk/2011/08/12/linkedin_social_ads_trust/ 33

Terms of Service 3. Clusters • • • Copyright 2009 -11 Service-Level Warranties and Indemnities Lateral Compatibility ('Can I get my data out? ') Authentication and Authorisation Second-Party Risk Exposure Third-Party Risk Exposure Data Deletion Subject Access Customer Service Complaints-Handling – Internal, External 34

Terms of Service 3. Clusters • • • Copyright 2009 -11 Service-Level Warranties and Indemnities Lateral Compatibility ('Can I get my data out? ') Authentication and Authorisation Second-Party Risk Exposure Third-Party Risk Exposure Data Deletion Subject Access Customer Service Complaints-Handling – Internal, External 35

Consumer Requirements and Risks – 3 of 3 More Advanced Protections • • Am I going to get gouged? [Cost] Can only appropriate people get in and do things? [Authentication and Authorisation] Can I get access to all data that you hold about me? [Subject Access] Is my data protected against you, them and the gods? [Data Security] Is my privacy protected against you, them and the gods? [Privacy Controls] If I terminate our relationship, will my data be irretrievably deleted? [Fully Effective Withdrawal] What happens to my data if I die? [Archival / Memorialisation] Copyright 2009 -11 36

Second-Party Risk-Exposure Scope Definition • • Copyright 2009 -11 Not data relevant to the commercial relationship Not uses of data that are necessary as part of the service being provided 'Private data' intended for use by the consumer only 'Restricted data' intended to be accessible by some other parties, but not by parties generally 37

Comparative Table Copyright 2009 -11 38

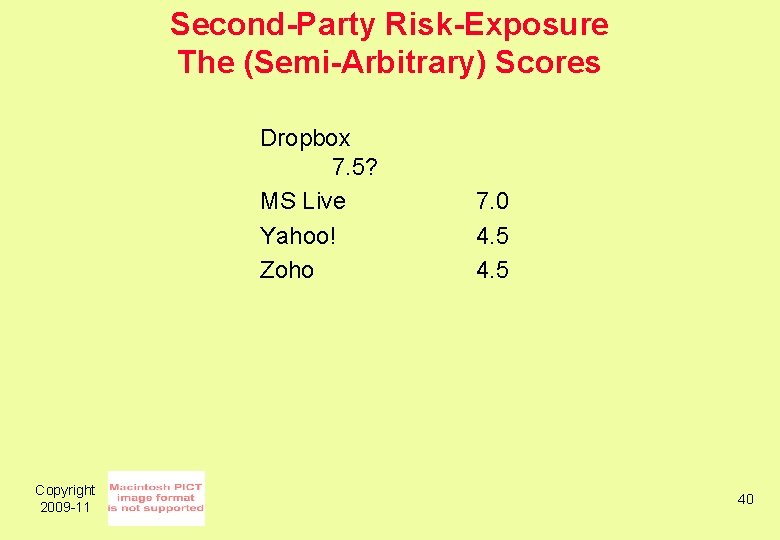
Second-Party Risk-Exposure Summary of Results • 3 – the Terms provide the ISP with no right to use the data (iinet, Internode, Yahoo!) 2 – use is authorised, but. . . only in a manner directly related to the contract (Infinite, Zoho) • 1 – use is limited to 'access' - although what that limitation means is unclear (Dropbox) • 1 – use is authorised "to provide the service" - which can be readily interpreted as being the service as a whole not just the service provided to that user (MS Live) • • 2 – the ISP has very substantial rights (Google, Linked. In) • Copyright 2009 -11 39

Second-Party Risk-Exposure The (Semi-Arbitrary) Scores Dropbox 7. 5? MS Live Yahoo! Zoho Copyright 2009 -11 7. 0 4. 5 40
![SecondParty RiskExposure The SemiArbitrary Scores Copyright 2009 11 Dropbox 7 5 MS Live 7 Second-Party Risk-Exposure The [Semi-Arbitrary] Scores Copyright 2009 -11 Dropbox 7. 5 MS Live 7.](https://slidetodoc.com/presentation_image_h2/9078578db61525ddbd822b4f8e3aa50d/image-41.jpg)
Second-Party Risk-Exposure The [Semi-Arbitrary] Scores Copyright 2009 -11 Dropbox 7. 5 MS Live 7. 0 Yahoo! 4. 5 Zoho 4. 5 __________ __ Google Gmail 0. 0 Docs 0. 0 Groups 0. 0 Apps 0. 0 41

Cloudy Consumer Computing AGENDA • The Research Domain • • Copyright 2009 -11 Consumer Computing Consumer Apps ==>> Consumer Services Consumer Requirements and Risks The Research Method Preliminary Results (Tentative) Conclusions and Next Steps 42

Preliminary Phase Policy-Relevant Results Consumers dependent on C. C. Services are at dire risk Service malfunctions, loss of data, provider exploitation of their data, low standards of accessibility and clarity of Terms, largely unfettered scope for providers to change the Terms • Consumer Protections are essential, but seriously inadequate Transnationality of Internet commerce, dominance of US marketing morés, pro-corporate and anti-consumer stance of US regulators, meekness of regulators in other countries, the lack of organised resistance by consumer reps, advocacy bodies • Serious consumer disappointments are inevitable • Recriminations against out-/cloud-sourcing are inevitable Copyright • 2009 -11 43

Preliminary Phase Research-Relevant Results • • • Copyright 2009 -11 The Research Method’s feasibility has been demonstrated The project is giving rise to new and deeper information Complementary research is needed In-depth studies of actual cases of harm to consumers In-depth studies of scenarios likely to lead to harm Studies of different categories of service Studies of different categories of consumers • across the Generations • across different levels of consumer sophistication Results from all lines of research need to be combined Feedforward is needed into providers’ Terms of Service 44

Next Steps Preliminary Phase • Studies of the Domain • Definition of Consumer Requirements • Accessibility of To. S • In-Depth Study of 1 To. S • Comparative Study of To. S re 1 Cluster of Terms • Consumer Protection Laws, Resources, Enforcement Copyright 2009 -11 Empirical Phase • Validation of Consumer Requirements • Sample Selection • In-Depth To. S Studies • Comparative To. S Studies Articulation Phase • Discussions with Providers • Expression of Model Terms • Interactions with Consumer Advocacy Organisations, Regulators, Policy Makers 45

Will Consumers Come to be Banned From Owning General-Purpose Computing Devices? Copyright 2009 -11 46

Will Consumers Come to be Banned From Owning General-Purpose Computing Devices? Some powerful groups might like to achieve it • • • Copyright-Dependent Corporations Government Censors The Moral Minority, who want governments to extend censorship to whatever content the moral minority thinks the majority shouldn't have access to (Dominant) Computing Device Providers Law Enforcement & National Security Agencies (LEANs) 'Fraud Experts' Copyright 2009 -11 Re 'fraud experts': http: //www. itnews. com. au/News/263042, jailbroken-phones-not-safe-for-banking. aspx – 8 Jul 2011 47

The Cloudy Future of Consumer Computing Roger Clarke Xamax Consultancy and PSARN Security, Canberra Visiting Professor in Computer Science, ANU and in Cyberspace Law & Policy, UNSW http: //www. rogerclarke. com/EC/CCC. html, CCC-ANU. ppt Copyright 2009 -11 48