COP 5611 Operating Systems Spring 2010 Dan C








- Slides: 38

COP 5611 Operating Systems Spring 2010 Dan C. Marinescu Office: HEC 439 B Office hours: M-Wd 2: 00 -3: 00 PM

Lecture 9 n n Reading Assignment: Chapter 7 from the online textbook HW 1 due today. Remember: A progress report for the project is due on every Monday till week 12. Last time: Thread coordination and scheduling Multi-level memories ¨ I/O bottleneck ¨ n Today: Network properties ¨ Layering ¨ Data link layer ¨ n Next time ¨ Network layer 2

Properties of Networks n Physical limitations: Speed of light finite communication latency ¨ Hostile environments ¨ Limited channel capacity limited bandwidth ¨ n Channels are shared - multiplexed Why: n Support any-to-any communication n Share costs ¨ How n Isochronous multiplexing – scheduled access ¨ TDM ¨ FDM n Asynchronous multiplexing ¨ 3

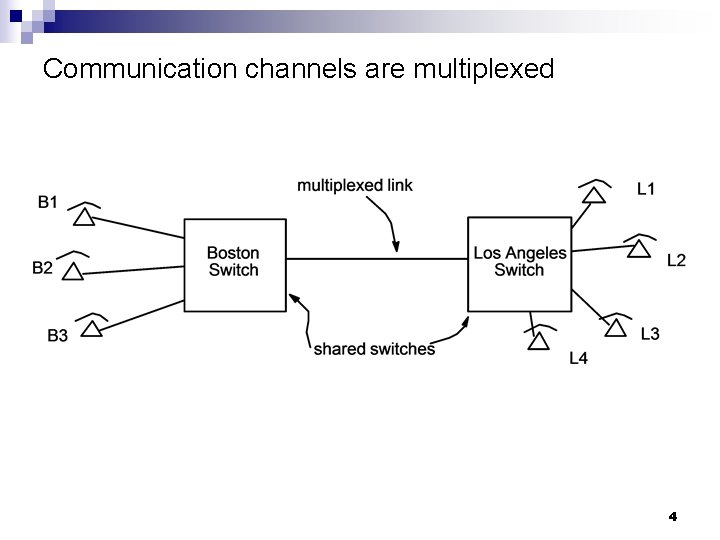
Communication channels are multiplexed 4

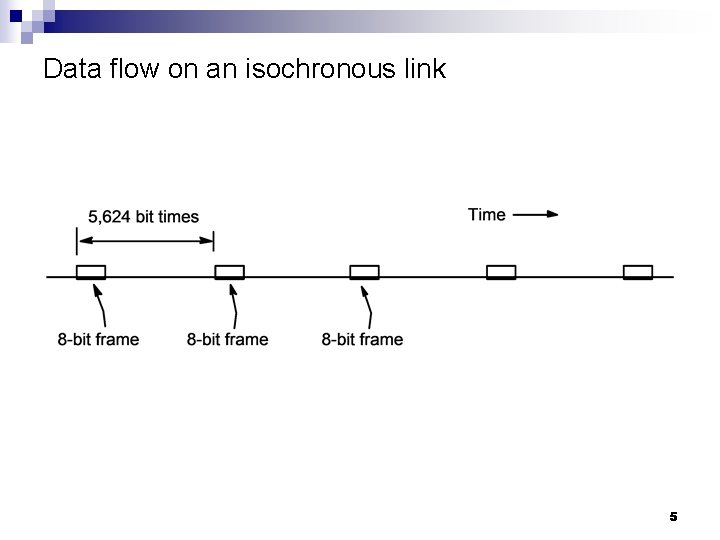
Data flow on an isochronous link 5

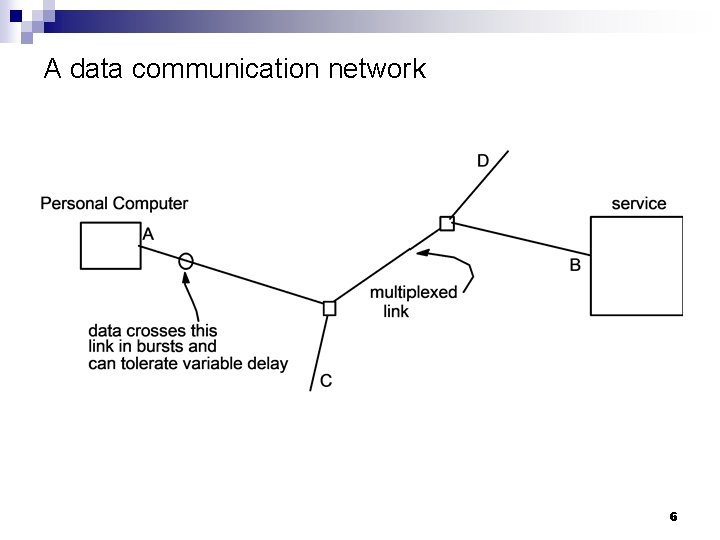
A data communication network 6

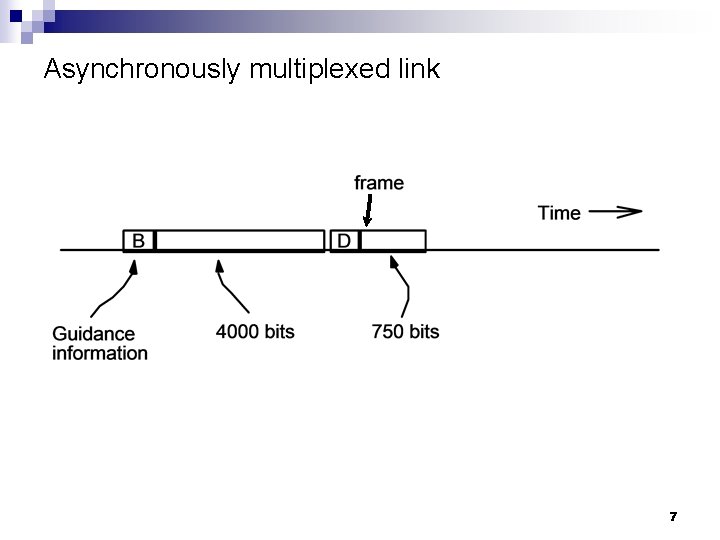
Asynchronously multiplexed link 7

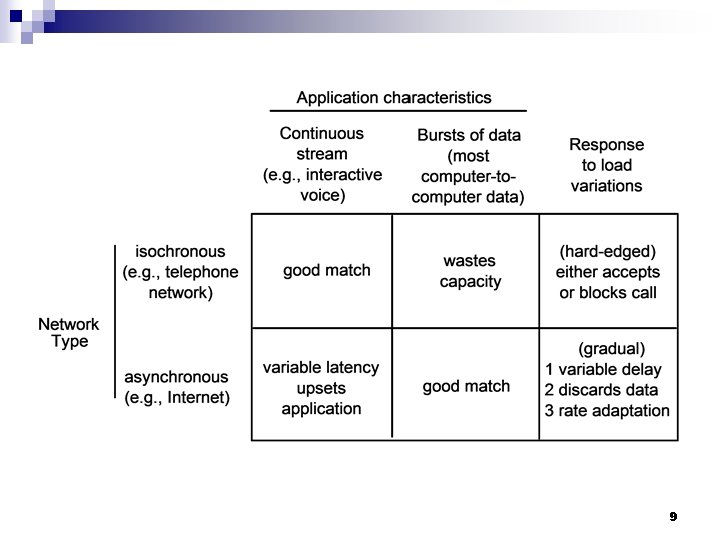
Communication n Continuous versus bursty The old phone network versus data networks ¨ Human versus computer communication ¨ n n Connection-oriented versus connectionless communication Packet-forwarding networks Routing problem ¨ Delays ¨ 8

9

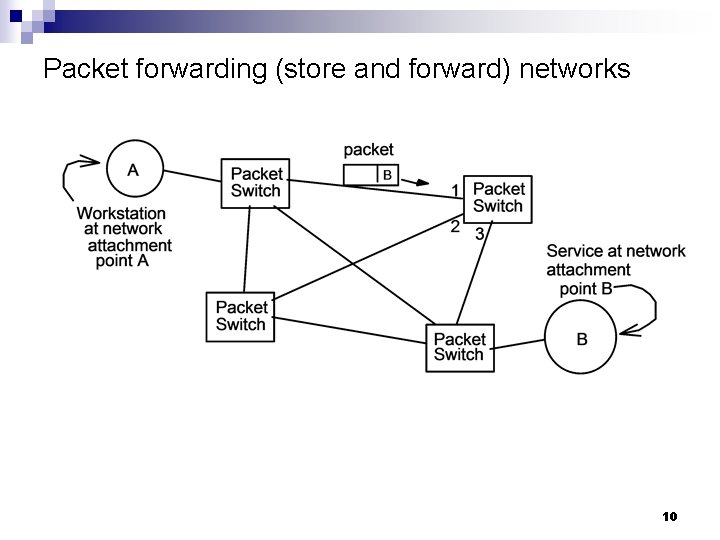
Packet forwarding (store and forward) networks 10

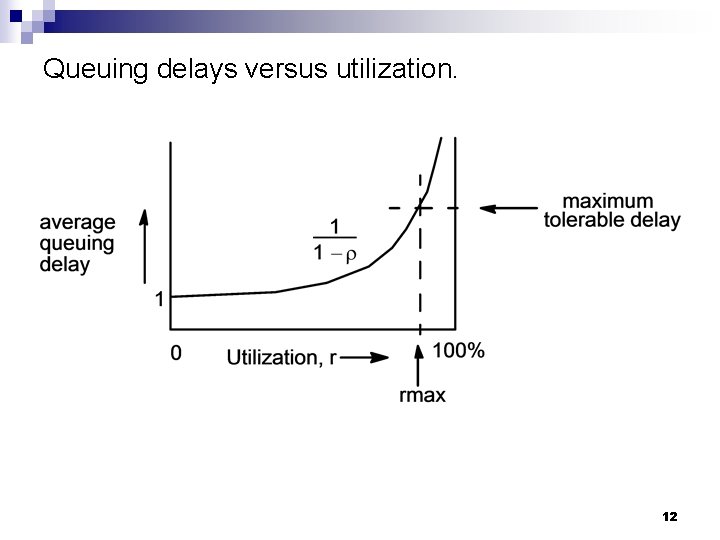
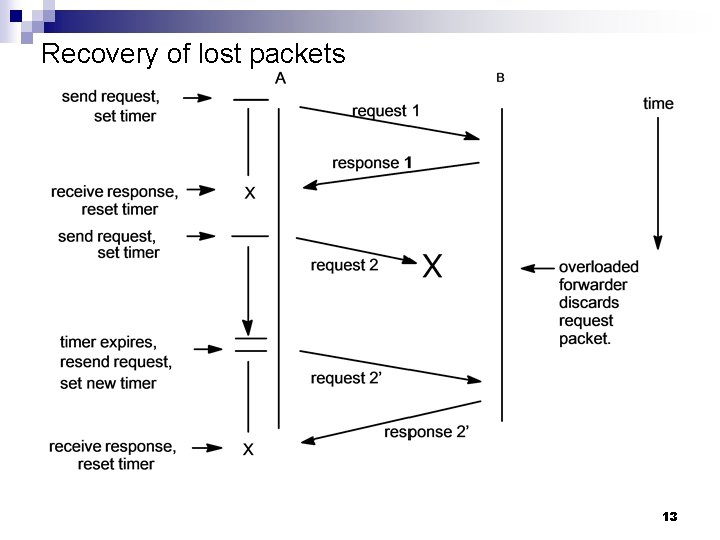
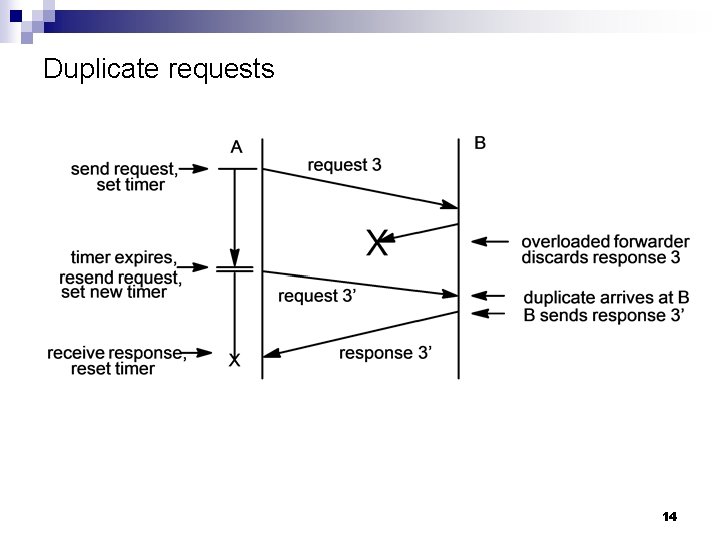
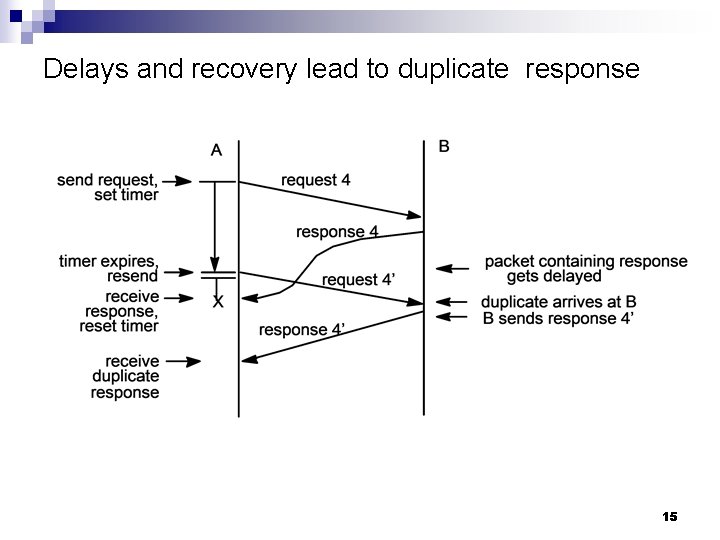
Problems in packet forwarding networks n Delay Propagation delay ¨ Transmission delay ¨ Processing delay ¨ Queuing delay ¨ n n Resources are finite and a worst case design is not feasible heavy tail distributions of resource needs Buffer overflow and discarded packets Adaptive rate modulated by information regarding network congestion ¨ Timers and packet retransmission ¨ Duplicate packets ¨ 11

Queuing delays versus utilization. 12

Recovery of lost packets 13

Duplicate requests 14

Delays and recovery lead to duplicate response 15

16

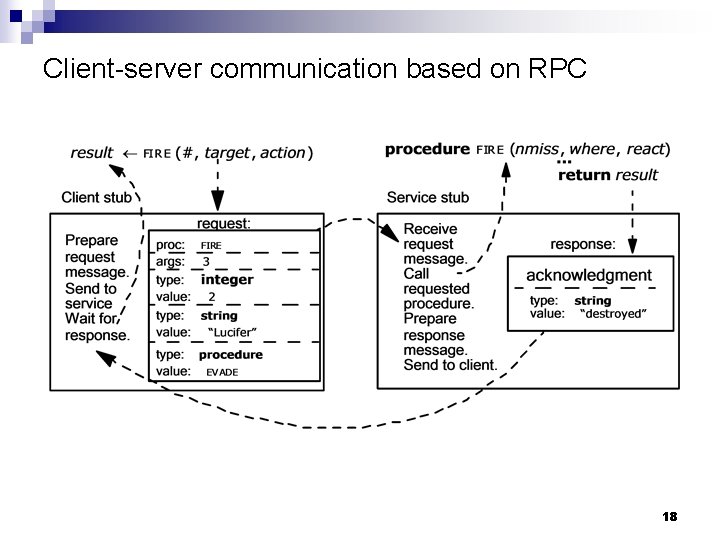
Layering n n Simplify the design Example- RPC 17

Client-server communication based on RPC 18

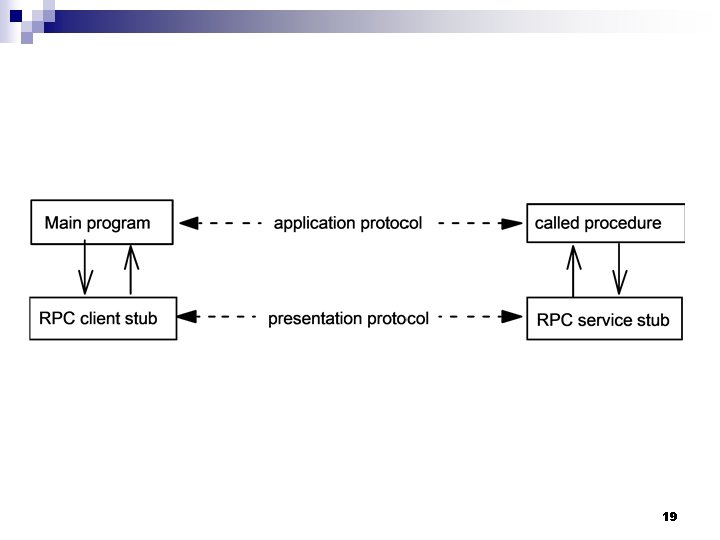
19

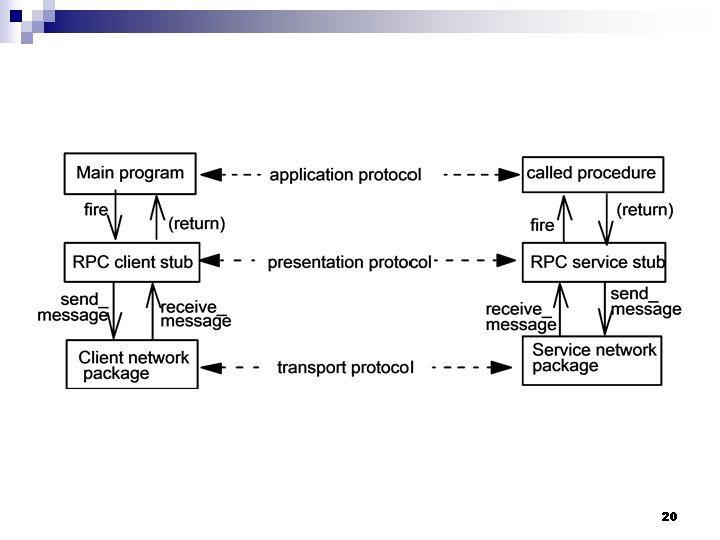
20

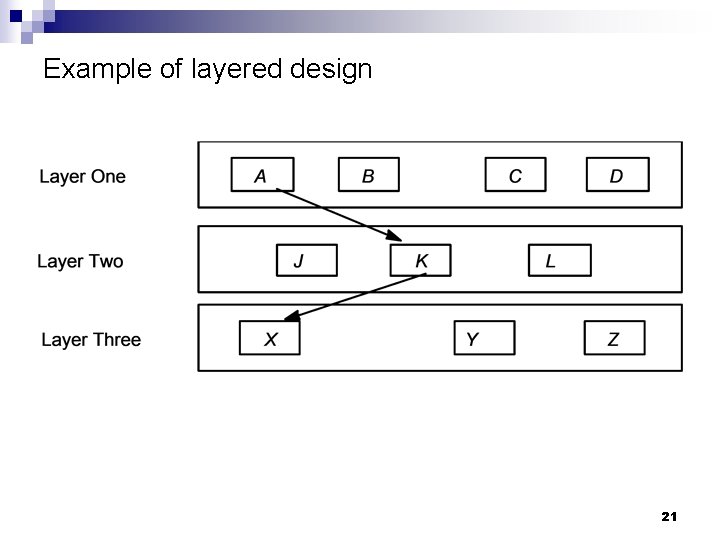
Example of layered design 21

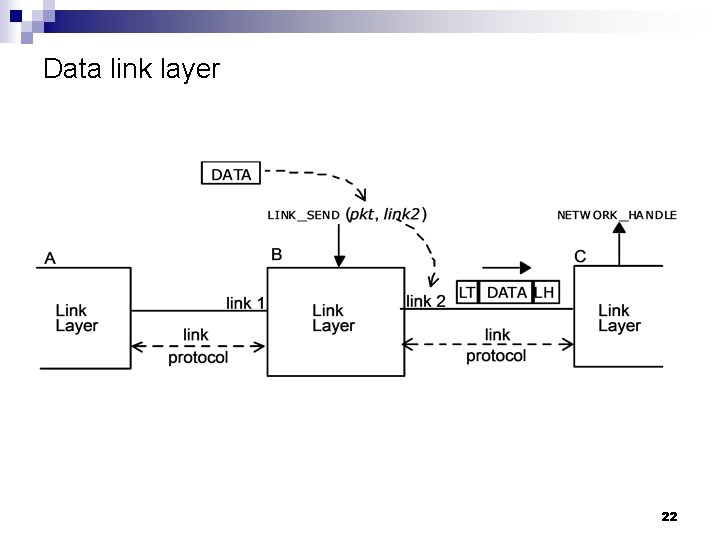
Data link layer 22

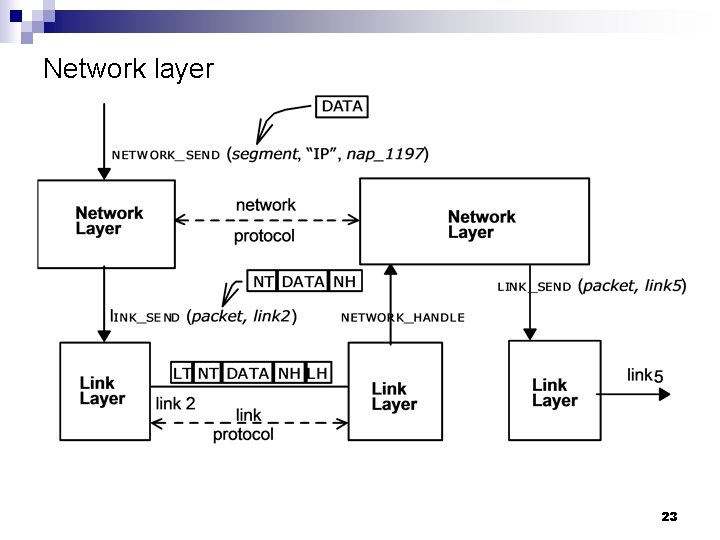
Network layer 23

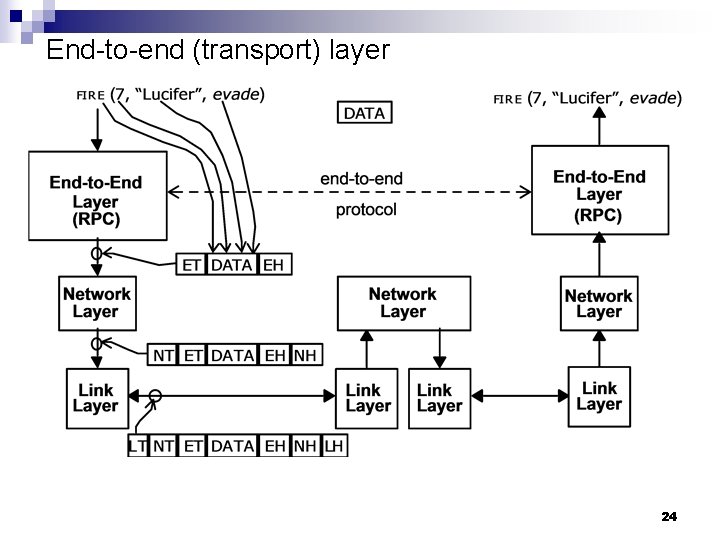
End-to-end (transport) layer 24

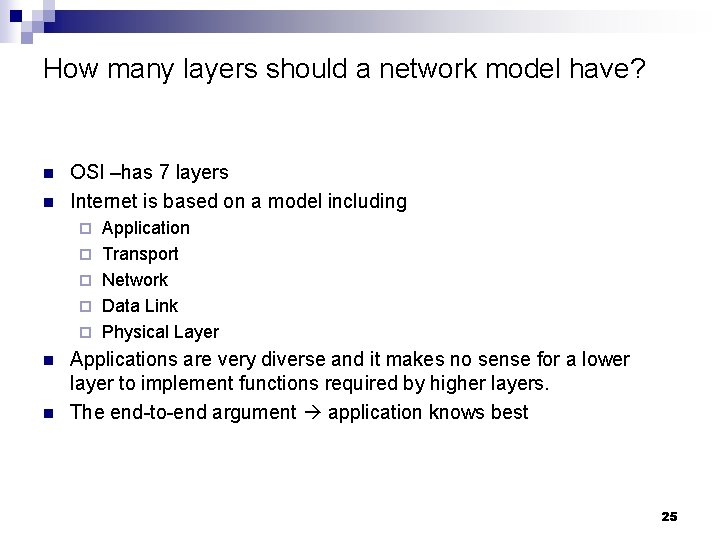
How many layers should a network model have? n n OSI –has 7 layers Internet is based on a model including ¨ ¨ ¨ n n Application Transport Network Data Link Physical Layer Applications are very diverse and it makes no sense for a lower layer to implement functions required by higher layers. The end-to-end argument application knows best 25

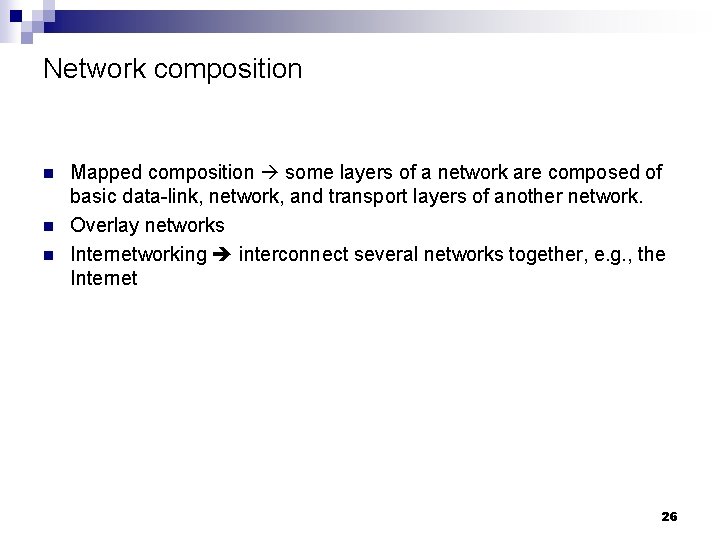
Network composition n Mapped composition some layers of a network are composed of basic data-link, network, and transport layers of another network. Overlay networks Internetworking interconnect several networks together, e. g. , the Internet 26

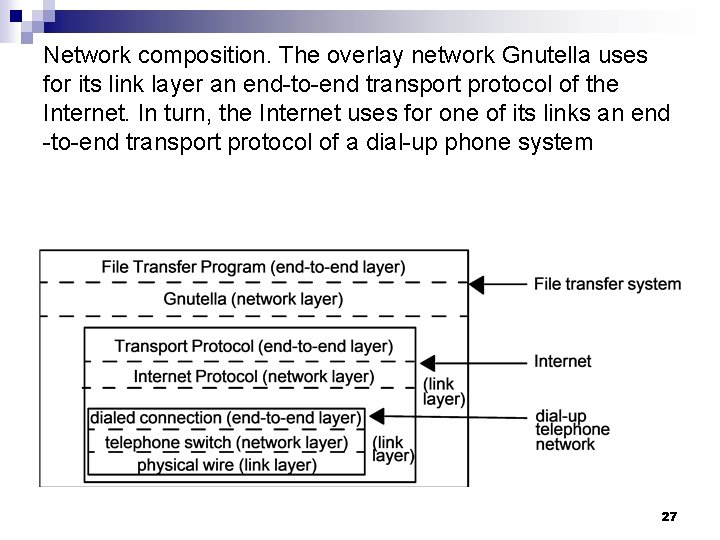
Network composition. The overlay network Gnutella uses for its link layer an end-to-end transport protocol of the Internet. In turn, the Internet uses for one of its links an end -to-end transport protocol of a dial-up phone system 27

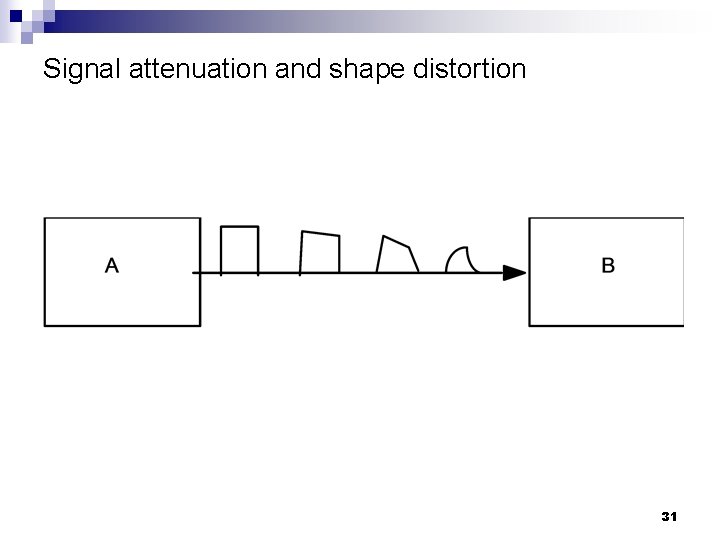
More about the link layer n n n Function: push bits from one place to another Analog worlds Capacity of a communication channel Capacity of a noisy communication channel C= B x log (1+ signal/noise) B is the bandwidth in Hz signal/noise – ratio of signal power to noise power Signals attenuation Signals are distorted over long distances 28

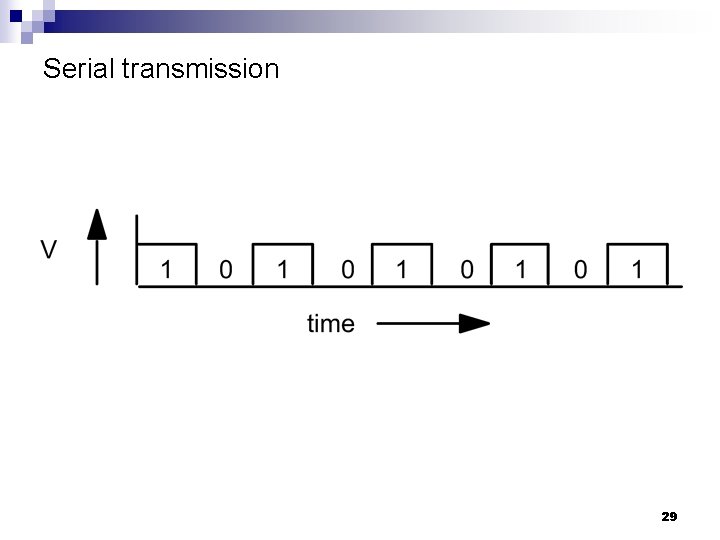
Serial transmission 29

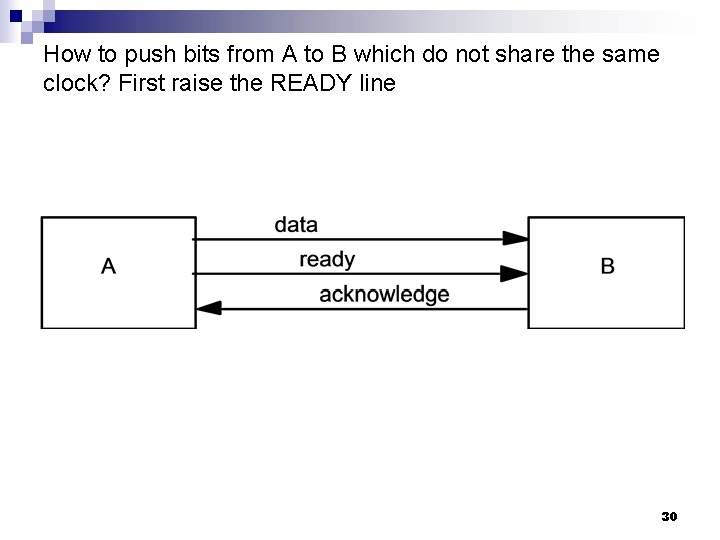
How to push bits from A to B which do not share the same clock? First raise the READY line 30

Signal attenuation and shape distortion 31

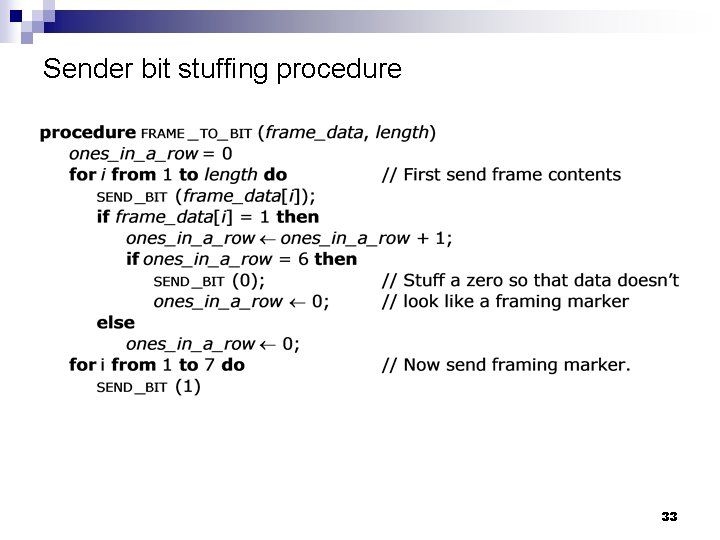
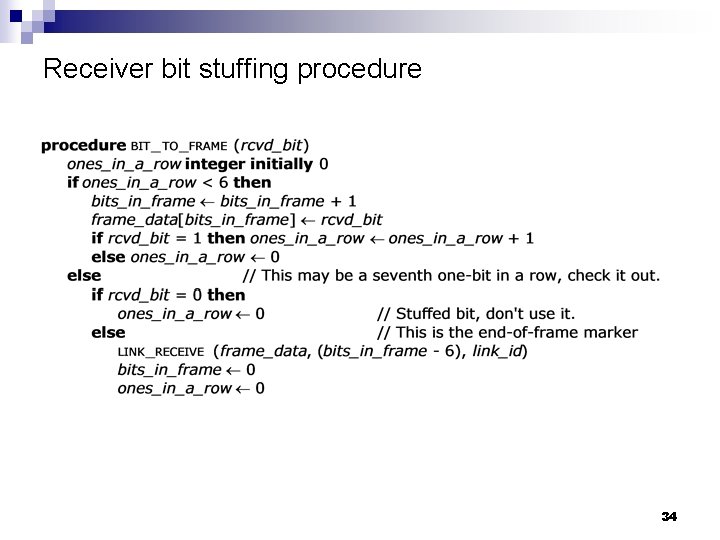
Framing n n A pattern of bits serve as a frame delimiter – e. g. , seven 1’s Bit stuffing: The sender: add a 0 whenever it encounters a pattern of six 1’s in data ¨ The receiver: remove a 0 following a pattern of six 1’s in data ¨ n n Add a frame header Add a frame trailer 32

Sender bit stuffing procedure 33

Receiver bit stuffing procedure 34

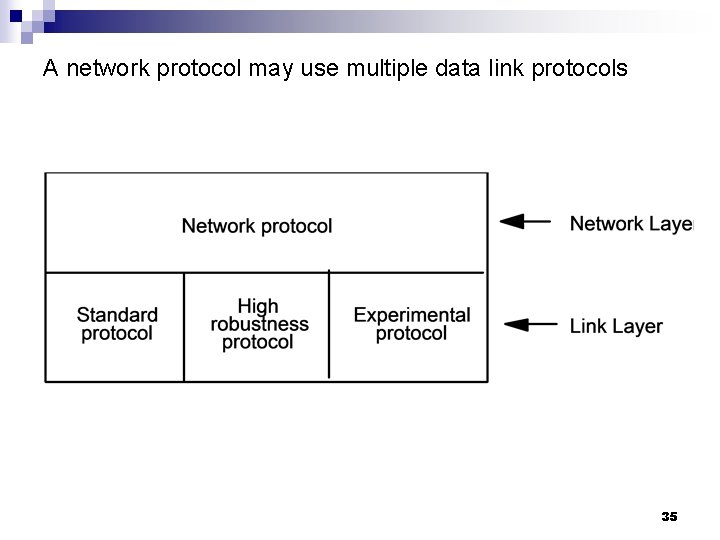
A network protocol may use multiple data link protocols 35

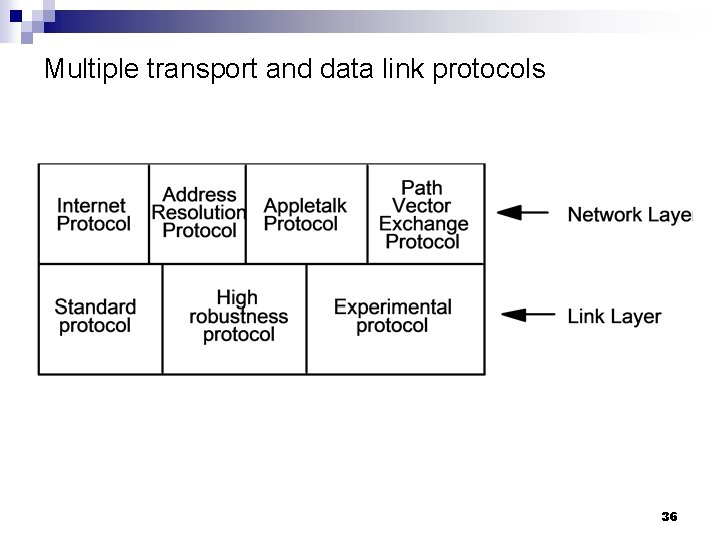
Multiple transport and data link protocols 36

Sending a frame 37

Receiving a frame 38