Cookies COEN 351 Ecommerce Security Client Session Identification




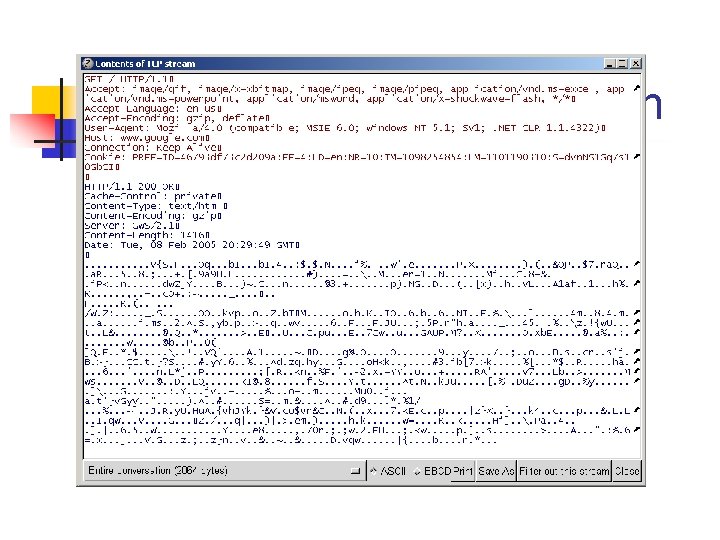










![Cookies n Version 0 cookies (Netscape cookies) Set-Cookie: name=value [; expires=date] [; path=path] [; Cookies n Version 0 cookies (Netscape cookies) Set-Cookie: name=value [; expires=date] [; path=path] [;](https://slidetodoc.com/presentation_image_h/936dc0348c394f8f0b39fe23a7d45459/image-18.jpg)








- Slides: 27

Cookies COEN 351 E-commerce Security

Client / Session Identification n n HTTP does not maintain state. State Information can be passed using: n n n HTTP Headers Client IP Address HTTP User Login FAT URLs Cookies

Client / Session Identification: HTTP Header n HTTP Header fields: n “From” n User’s email address, request. n n “User-Agent” n n Could be used by all browsers, but are only used for web-bots gathering data. User’s browser software, request. “Referer” (Sic) n Page user came from by following link

Client / Session Identification HTTP Header fields: n “Authorization” n n n “Client-ip” “X-Forwarded-For” n n User name and password Client-ip “Cookie”

Client / Session Identification n User-Agent n Gives the server information about the browser.

Client / Session Identification: HTTP Header n n All contents of the header / URL can be easily forged. Secure protocols need to use good encryption and a challenge / response scheme to avoid replay attacks.

Client / Session Identification n Client IP Address n n n Not part of the HTTP header Available from the package Easily spoofed Changed by NATs and Proxies Not secure for maintaining state

Client / Session Identification: HTTP Authentication HTTP login based on WWW-Authenticate and Authorization headers. n 1. 2. 3. 4. 5. 6. Browser requests page with GET Server answers with: 401 Login Required, WWW-authenticate: Basic realm=“joe” Browser pop’s up login dialog that users fills out. Browser resends GET request, adds Authorization: Basic am 98 re 45 Server fulfills request. Browser now will resend stored user-name with every request.

Client / Session Identification: HTTP Authentication n HTTP Authentication Details n n n Realms allow the web-site to have many secure areas. HTTP packs user-name and password together, separated by a colon and encodes them in Base 64 encoding. HTTP allows authentication by proxies. n n User goes to proxy site for authentication. User-name and password are then used to go to the target sites.

Client / Session Identification: HTTP Authentication n HTTP Authentication Security Risks n Username and password are encoded, not encrypted. n n Authentication information does not change between different requests. n n n Base 64 encoding and decoding tools are freely available for those that do not want to program themselves. Sniffer can replay! Requesting unnecessary authentication leads to password sharing. Basic authentication only authenticates the browser (user), not the server. n Impersonating websites could harvest passwords.

Client / Session Identification: Digest Authentication n HTTP Digest Authentication n A rarely used alternative that is more secure. n n Prevents replay attacks by using nonces. Encrypts passwords. Optionally protects message integrity. …

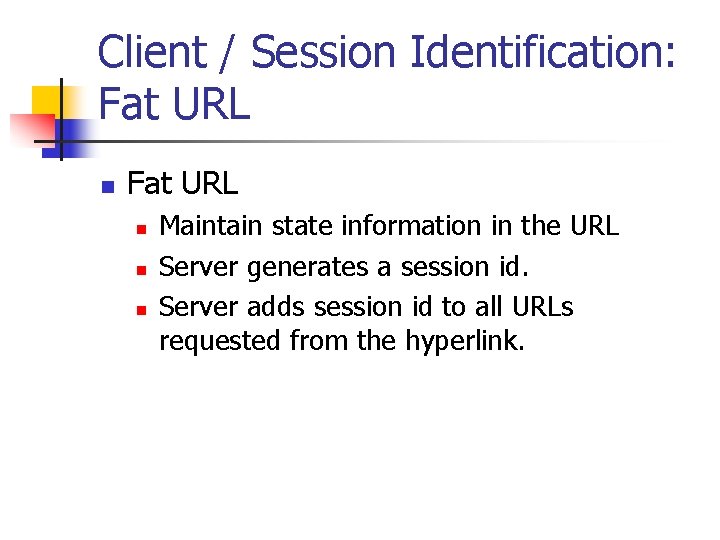
Client / Session Identification: Fat URL n n n Maintain state information in the URL Server generates a session id. Server adds session id to all URLs requested from the hyperlink.

Client / Session Identification: Fat URL n URLs can be easily faked. n n n FAT URLs need to be encrypted. Website needs to do more processing for fat URLs. Sharing URLs can lead to sharing authentication. Caching no longer works. Access is lost when user leaves the website temporarily.

Cookies n Cookies: n n ASCI strings stored at the browser. Submitted with each request to a target website.

Cookies n Cookies: n Session cookies n n Stored only for the duration of a web-session. Persistent cookies n Remain stored until they expire.

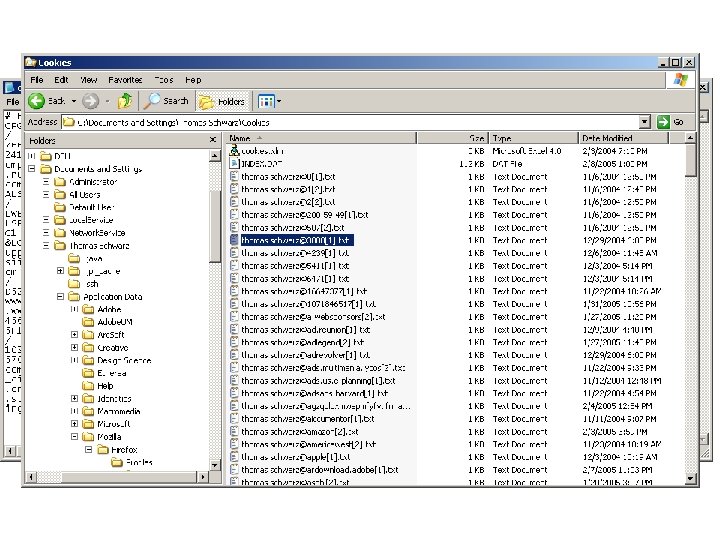
Cookies n Cookie-Jar n n n Client-side state storage Netscape / Firefox store cookies in a single text file called cookies. txt MS IE stores cookies in the cache.

Cookies n Server specifies optional domain. n n n Cookie gets sent with all requests to this domain. Server specifies optional expiration date Server can specify “secure” option: n Cookie is only sent when using SSL.
![Cookies n Version 0 cookies Netscape cookies SetCookie namevalue expiresdate pathpath Cookies n Version 0 cookies (Netscape cookies) Set-Cookie: name=value [; expires=date] [; path=path] [;](https://slidetodoc.com/presentation_image_h/936dc0348c394f8f0b39fe23a7d45459/image-18.jpg)
Cookies n Version 0 cookies (Netscape cookies) Set-Cookie: name=value [; expires=date] [; path=path] [; domain-name = value] [; secure] Set-Cookie: customer=Mary; expires Wednesday, 09 -September-2006 24: 00: 01 GMT; domain=“scu. edu”; path=/soe; secure

Cookies n Version 1 cookies (RFC 296) n n Less-used Provides a number of extensions

Cookies n Privacy risk n n Can be controlled by web-browser. Used to track consumer behavior. n Harder, but possible to track an individual user.

Cookies n Security Risk n Users can change cookies before continuing to browse. n n Users could swap / steal cookies. n n Counter-measure: strong encryption E. g. when used for authentication Session Hijacking

Cookies n Session Hijacking n Counter measure: n n Server needs to send a new cookie after every change in state and verify that a request comes with a valid cookie. For example, by appending a MAC of session state to the cookie after each change of state.

Cookies n Poor practices: n Poor encryption of cookies. n Web-based email uses a cookie for authentication. n n n Cookie contains the user name encrypted by XOR-ing with a secret string. Attacker can crack the cookie encryption by creating fake accounts. Attacker can now craft a cookie useful for authentication. n Something similar happened to hotmail and yahoo early on.

Cookies n Poor practices: n Poor encryption of cookies. n Shopping cart encoded in cookie. n n n Cookie contained shopping cart details in plain text. Attacker changed prices of items. Relying on cookie for authentication n n Cookie is sniffed from the net. Cookie is stolen by impersonating a web-site.

Cookie Alternative: Web Bugs n Used to track viewers of web-sites. n HTML page contains a request to download a resource from a “counting” site. n n The resource is so small that the viewer does notice the download. Counting site receives the request and adds IP address to its user database.

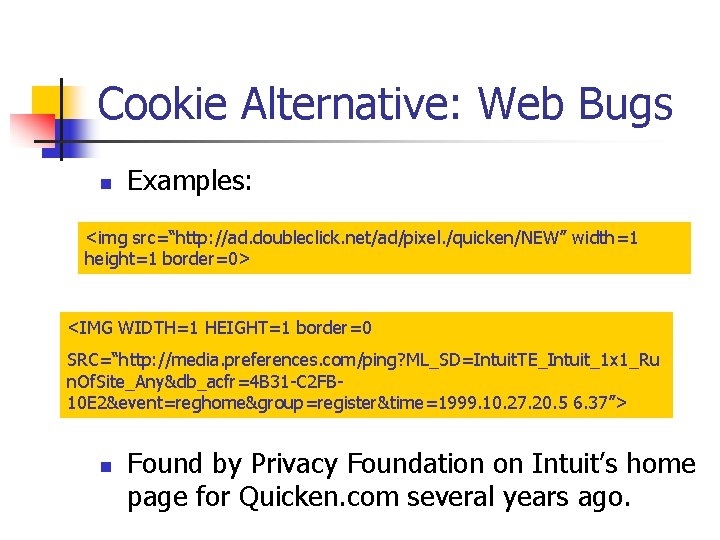
Cookie Alternative: Web Bugs n Examples: <img src=“http: //ad. doubleclick. net/ad/pixel. /quicken/NEW” width=1 height=1 border=0> <IMG WIDTH=1 HEIGHT=1 border=0 SRC=“http: //media. preferences. com/ping? ML_SD=Intuit. TE_Intuit_1 x 1_Ru n. Of. Site_Any&db_acfr=4 B 31 -C 2 FB 10 E 2&event=reghome&group=register&time=1999. 10. 27. 20. 5 6. 37”> n Found by Privacy Foundation on Intuit’s home page for Quicken. com several years ago.

Cookie Alternative: Web Bugs n Can be embedded in any html code. n n User profiles written in html. Email messages. n n But only when read with a client that can display HTML messages and with a computer connected to the internet. Usenet messages.