Control and Accounting Information Systems Chapter 7 Copyright

































- Slides: 46

Control and Accounting Information Systems Chapter 7 Copyright © 2015 Pearson Education, Inc. 7 -1

Learning Objectives • Explain basic control concepts • Compare and contrast the COBIT, COSO, and ERM control frameworks. • Describe the major elements in the internal environment of a company. • Describe the four types of control objectives that companies need to set. • Describe the events that affect uncertainty and the techniques used to identify them. • Explain how to assess and respond to risk using the Enterprise Risk Management model. • Describe control activities commonly used in companies. • Describe how to communicate information and monitor control processes in organizations. Copyright © 2015 Pearson Education, Inc. 7 -2

Internal Controls • Processes implemented to provide reasonable assurance that the following objectives are achieved: ▫ ▫ Safeguard assets Maintain sufficient records Provide accurate and reliable information Prepare financial reports according to established criteria ▫ Promote and improve operational efficiency ▫ Encourage adherence with management policies ▫ Comply with laws and regulations Copyright © 2015 Pearson Education, Inc. 7 -3

Functions of Internal Controls • Preventive controls ▫ Deter problems from occurring • Detective controls ▫ Discover problems that are not prevented • Corrective controls ▫ Identify and correct problems; correct and recover from the problems Copyright © 2015 Pearson Education, Inc. 7 -4

SOX AND THE FOREIGN CORRUPT PRACTICES ACT • In 1977, Congress passed the Foreign Corrupt Practices Act, and to the surprise of the profession, this act incorporated language from an AICPA pronouncement. • The primary purpose of the act was to prevent the bribery of foreign officials to obtain business. • A significant side effect was to require that corporations maintain good systems of internal accounting control. Copyright © 2015 Pearson Education, Inc.

SOX AND THE FOREIGN CORRUPT PRACTICES ACT • In the late 1990 s and early 2000 s, a series of multi-million-dollar accounting frauds made headlines. ▫ The impact on financial markets was substantial, and Congress responded with passage of the Sarbanes-Oxley Act of 2002 (aka, SOX). �Applies to publicly held companies and their auditors Copyright © 2015 Pearson Education, Inc.

SOX AND THE FOREIGN CORRUPT PRACTICES ACT • The intent of SOX is to: ▫ ▫ Prevent financial statement fraud Make financial reports more transparent Protect investors Strengthen internal controls in publicly-held companies ▫ Punish executives who perpetrate fraud • SOX has had a material impact on the way boards of directors, management, and accountants operate. Copyright © 2015 Pearson Education, Inc.

SOX AND THE FOREIGN CORRUPT PRACTICES ACT • Important aspects of SOX include: ▫ Creation of the Public Company Accounting Oversight Board (PCAOB) to oversee the auditing profession. ▫ New rules for auditors ▫ New rules for audit committees ▫ New rules for management ▫ New internal control requirements Copyright © 2015 Pearson Education, Inc.

SOX AND THE FOREIGN CORRUPT PRACTICES ACT • After the passage of SOX, the SEC further mandated that: ▫ Management must base its evaluation on a recognized control framework, developed using a due-process procedure that allows for public comment. The most likely framework is the COSO model discussed later in the chapter. ▫ The report must contain a statement identifying the framework used. Copyright © 2015 Pearson Education, Inc.

Control Frameworks • COBIT ▫ Framework for IT control • COSO ▫ Framework for enterprise internal controls (control-based approach) • COSO-ERM ▫ Expands COSO framework taking a risk-based approach Copyright © 2015 Pearson Education, Inc. 7 -10

COBIT Framework • Current framework version is COBIT 5 • Based on the following principles: ▫ ▫ ▫ Meeting stakeholder needs Covering the enterprise end-to-end Applying a single, integrated framework Enabling a holistic approach Separating governance from management Copyright © 2015 Pearson Education, Inc. 7 -11

CONTROL FRAMEWORKS • COSO’s Internal Control Framework ▫ The Committee of Sponsoring Organizations (COSO) is a private sector group consisting of: �The American Accounting Association �The AICPA �The Institute of Internal Auditors �The Institute of Management Accountants �The Financial Executives Institute Copyright © 2015 Pearson Education, Inc.

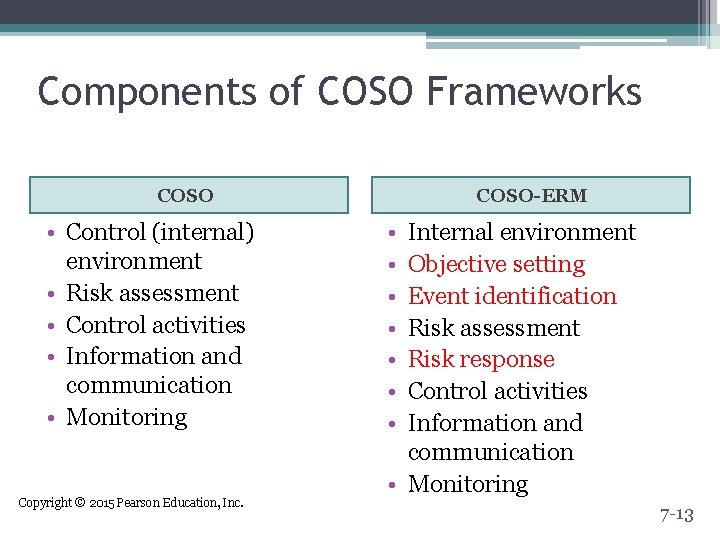
Components of COSO Frameworks COSO • Control (internal) environment • Risk assessment • Control activities • Information and communication • Monitoring Copyright © 2015 Pearson Education, Inc. COSO-ERM • • Internal environment Objective setting Event identification Risk assessment Risk response Control activities Information and communication • Monitoring 7 -13

CONTROL FRAMEWORKS • ERM Framework ▫ Takes a risk-based, rather than controls-based, approach to the organization. ▫ Oriented toward future and constant change. ▫ Incorporates rather than replaces COSO’s internal control framework and contains three additional elements: �Setting objectives. �Identifying positive and negative events that may affect the company’s ability to implement strategy and achieve objectives. �Developing a response to assessed risk. Copyright © 2015 Pearson Education, Inc.

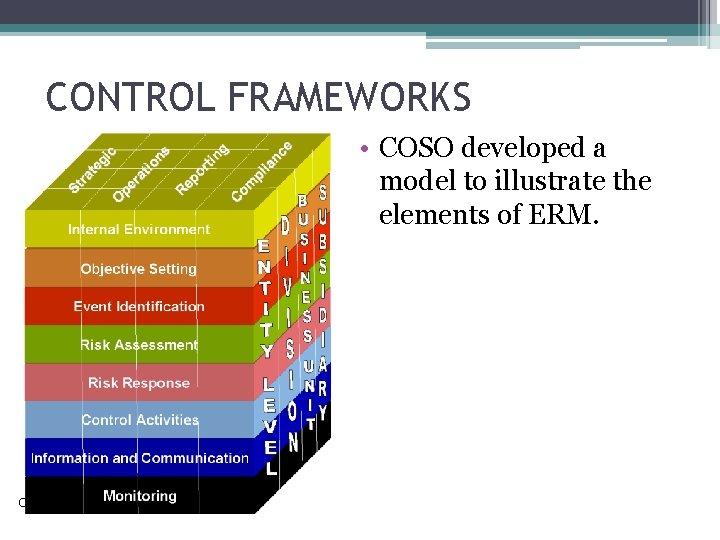
CONTROL FRAMEWORKS • COSO developed a model to illustrate the elements of ERM. Copyright © 2015 Pearson Education, Inc.

Objectives • Strategic objectives ▫ High-level goals • Operations objectives ▫ Effectiveness and efficiency of operations • Reporting objectives ▫ Improve decision making and monitor performance • Compliance objectives ▫ Compliance with applicable laws and regulations Copyright © 2015 Pearson Education, Inc. 7 -16

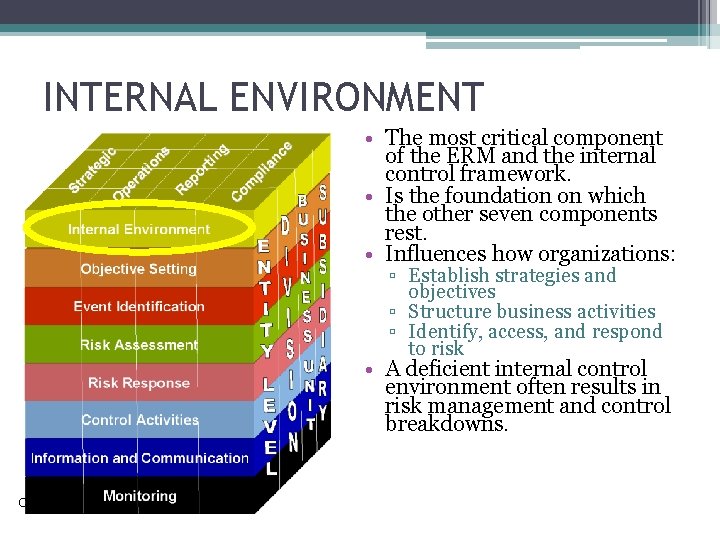
INTERNAL ENVIRONMENT • The most critical component of the ERM and the internal control framework. • Is the foundation on which the other seven components rest. • Influences how organizations: ▫ Establish strategies and objectives ▫ Structure business activities ▫ Identify, access, and respond to risk • A deficient internal control environment often results in risk management and control breakdowns. Copyright © 2015 Pearson Education, Inc.

Internal Environment • Management’s philosophy, operating style, and risk appetite • Commitment to integrity, ethical values, and competence • Internal control oversight by Board of Directors • Organizing structure • Methods of assigning authority and responsibility • Human resource standards Copyright © 2015 Pearson Education, Inc. 7 -18

INTERNAL ENVIRONMENT • The following human resource policies and procedures are important: ▫ ▫ ▫ ▫ Hiring Compensating Training Evaluating and promoting Discharging Managing disgruntled employees Vacations and rotation of duties Confidentiality, insurance and fidelity bonds Copyright © 2015 Pearson Education, Inc.

OBJECTIVE SETTING • Objective setting is the second ERM component. • It must precede many of the other six components. • For example, you must set objectives before you can define events that affect your ability to achieve objectives Copyright © 2015 Pearson Education, Inc.

OBJECTIVE SETTING • Top management, with board approval, must articulate why the company exists and what it hopes to achieve. ▫ Often referred to as the corporate vision or mission. • Uses the mission statement as a base from which to set corporate objectives. • The objectives: ▫ Need to be easy to understand measure. ▫ Should be prioritized. ▫ Should be aligned with the company’s risk appetite. Copyright © 2015 Pearson Education, Inc.

EVENT IDENTIFICATION • Events are: ▫ Incidents or occurrences that emanate from internal or external sources ▫ That affect implementation of strategy or achievement of objectives. ▫ Impact can be positive, negative, or both. ▫ Events can range from obvious to obscure. ▫ Effects can range from inconsequential to highly significant. Copyright © 2015 Pearson Education, Inc.

Event Identification Identifying incidents both external and internal to the organization that could affect the achievement of the organizations objectives Key Management Questions: • What could go wrong? • How can it go wrong? • What is the potential harm? • What can be done about it? Copyright © 2015 Pearson Education, Inc. 7 -23

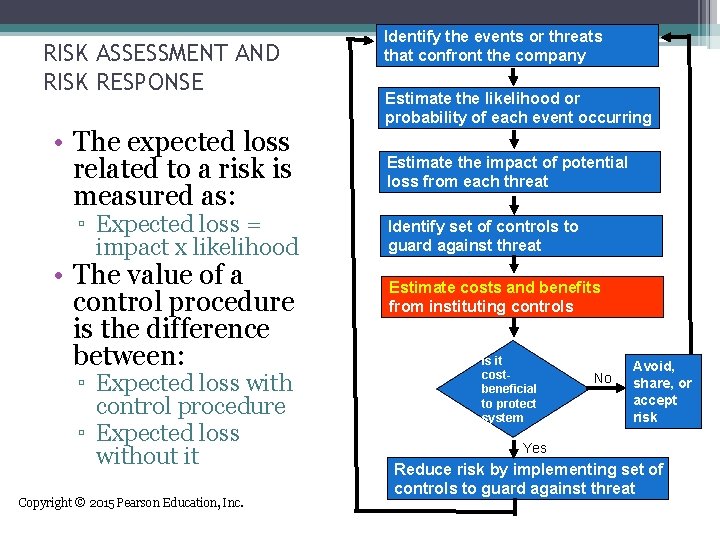
RISK ASSESSMENT AND RISK RESPONSE • The fourth and fifth components of COSO’s ERM model are risk assessment and risk response. • COSO indicates there are two types of risk: ▫ Inherent risk ▫ Residual risk Copyright © 2015 Pearson Education, Inc.

Risk Assessment • Any potential adverse occurrence or unwanted event that could be injurious to either the accounting information system or the organization is referred to as a threat or an event. • The potential dollar loss should a particular threat become a reality is referred to as the exposure or impact of the threat. • The probability that the threat will happen is the likelihood associated with the threat Copyright © 2015 Pearson Education, Inc. 7 -25

Risk Response • Reduce ▫ Implement effective internal control • Accept ▫ Do nothing, accept likelihood and impact of risk • Share ▫ Buy insurance, outsource, or hedge • Avoid ▫ Do not engage in the activity Copyright © 2015 Pearson Education, Inc. 7 -26

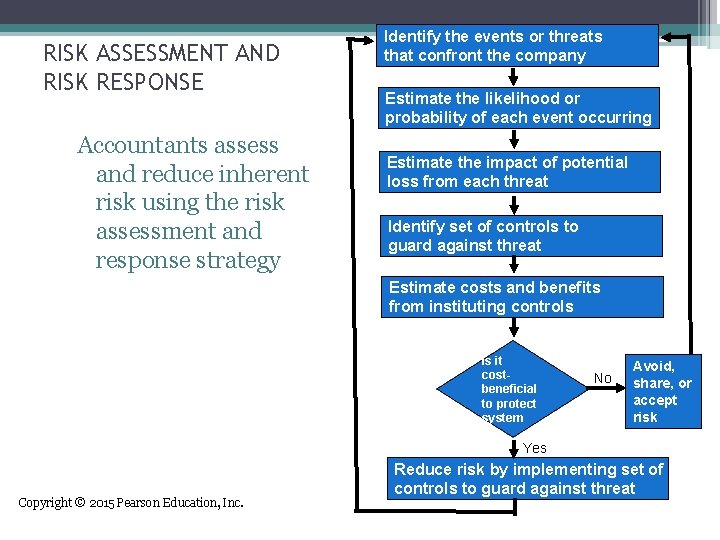
RISK ASSESSMENT AND RISK RESPONSE Accountants assess and reduce inherent risk using the risk assessment and response strategy Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Is it costbeneficial to protect system No Avoid, share, or accept risk Yes Copyright © 2015 Pearson Education, Inc. Reduce risk by implementing set of controls to guard against threat

RISK ASSESSMENT AND RISK RESPONSE • The expected loss related to a risk is measured as: ▫ Expected loss = impact x likelihood • The value of a control procedure is the difference between: ▫ Expected loss with control procedure ▫ Expected loss without it Copyright © 2015 Pearson Education, Inc. Identify the events or threats that confront the company Estimate the likelihood or probability of each event occurring Estimate the impact of potential loss from each threat Identify set of controls to guard against threat Estimate costs and benefits from instituting controls Is it costbeneficial to protect system No Avoid, share, or accept risk Yes Reduce risk by implementing set of controls to guard against threat

RISK ASSESSMENT AND RISK RESPONSE • Let’s go through an example: ▫ Hobby Hole is trying to decide whether to install a motion detector system in its warehouse to reduce the probability of a catastrophic theft. ▫ A catastrophic theft could result in losses of $800, 000. ▫ Local crime statistics suggest that the probability of a catastrophic theft at Hobby Hole is 12%. ▫ Companies with motion detectors only have about a. 5% probability of catastrophic theft. ▫ The present value of purchasing and installing a motion detector system and paying future security costs is estimated to be about $43, 000. ▫ Should Hobby Hole install the motion detectors? Copyright © 2015 Pearson Education, Inc.

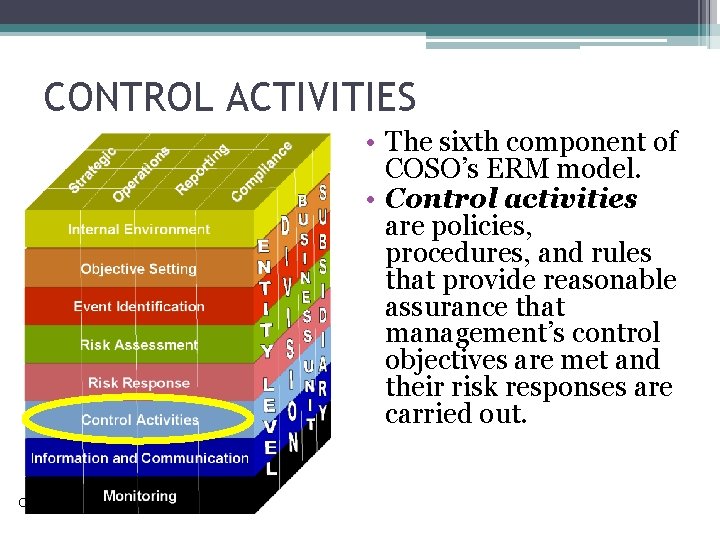
CONTROL ACTIVITIES • The sixth component of COSO’s ERM model. • Control activities are policies, procedures, and rules that provide reasonable assurance that management’s control objectives are met and their risk responses are carried out. Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • It is critical that controls be in place during the year-end holiday season. A disproportionate amount of computer fraud and security breakins occur during this time because: ▫ More people are on vacation and fewer around to mind the store. ▫ Students are not tied up with school. Copyright © 2015 Pearson Education, Inc.

Control Activities • Proper authorization of transactions and activities • Segregation of duties • Project development and acquisition controls • Change management controls • Design and use of documents and records • Safeguarding assets, records, and data • Independent checks on performance Copyright © 2015 Pearson Education, Inc. 7 -32

CONTROL ACTIVITIES • Proper Authorization of Transactions and Activities ▫ Management lacks the time and resources to supervise each employee activity and decision. ▫ Consequently, they establish policies and empower employees to perform activities within policy. ▫ This empowerment is called authorization and is an important part of an organization’s control procedures. Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Typically at least two levels of authorization: ▫ General authorization �Management authorizes employees to handle routine transactions without special approval. ▫ Special authorization �For activities or transactions that are of significant consequences, management review and approval is required. �Might apply to sales, capital expenditures, or write-offs over a particular dollar limit. • Management should have written policies for both types of authorization and for all types of transactions. Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Segregation of Duties ▫ Good internal control requires that no single employee be given too much responsibility over business transactions or processes. ▫ An employee should not be in a position to commit and conceal fraud or unintentional errors. ▫ Segregation of duties is discussed in two sections: �Segregation of accounting duties �Segregation of duties within the systems function Copyright © 2015 Pearson Education, Inc.

Segregation of Duties Copyright © 2015 Pearson Education, Inc. 7 -36

CONTROL ACTIVITIES • Segregation of Duties Within the Systems Function ▫ In a highly integrated information system, procedures once performed by separate individuals are combined. ▫ Therefore, anyone who has unrestricted access to the computer, its programs, and live data could have the opportunity to perpetrate and conceal fraud. ▫ To combat this threat, organizations must implement effective segregation of duties within the IS function. Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Authority and responsibility must be divided clearly among the following functions: ▫ ▫ ▫ ▫ ▫ Systems administration Network management Security management Change management Users Systems analysts Programming Computer operations Information systems library Data control Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Project Development and Acquisition Controls ▫ It’s important to have a formal, appropriate, and proven methodology to govern the development, acquisition, implementation, and maintenance of information systems and related technologies. �Should contain appropriate controls for: �Management review and approval �User involvement �Analysis �Design �Testing �Implementation �Conversion Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Change Management Controls ▫ Organizations constantly modify their information systems to reflect new business practices and take advantage of information technology advances. ▫ Change management is the process of making sure that the changes do not negatively affect: �Systems reliability �Security �Confidentiality �Integrity �Availability Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Design and Use of Adequate Documents and Records ▫ Proper design and use of documents and records helps ensure accurate and complete recording of all relevant transaction data. ▫ Form and content should be kept as simple as possible to: �Promote efficient record keeping �Minimize recording errors �Facilitate review and verification ▫ Documents that initiate a transaction should contain a space for authorization. ▫ Those used to transfer assets should have a space for the receiving party’s signature. Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Safeguard Assets, Records, and Data ▫ When people consider safeguarding assets, they most often think of cash and physical assets, such as inventory and equipment. ▫ Another company asset that needs to be protected is information. Copyright © 2015 Pearson Education, Inc.

CONTROL ACTIVITIES • Independent checks ▫ Top-level reviews ▫ Analytical reviews ▫ Reconciliation of independently maintained sets of records ▫ Comparison of actual quantities with recorded amounts ▫ Double-entry accounting ▫ Independent review Copyright © 2015 Pearson Education, Inc.

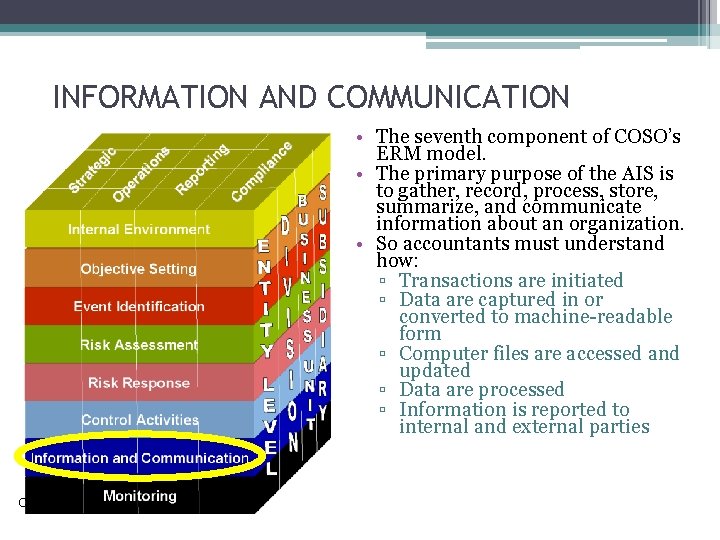
INFORMATION AND COMMUNICATION • The seventh component of COSO’s ERM model. • The primary purpose of the AIS is to gather, record, process, store, summarize, and communicate information about an organization. • So accountants must understand how: ▫ Transactions are initiated ▫ Data are captured in or converted to machine-readable form ▫ Computer files are accessed and updated ▫ Data are processed ▫ Information is reported to internal and external parties Copyright © 2015 Pearson Education, Inc.

MONITORING • The eighth component of COSO’s ERM model. • Monitoring can be accomplished with a series of ongoing events or by separate evaluations. Copyright © 2015 Pearson Education, Inc.

Monitoring • Perform internal control evaluations (e. g. , internal audit) • Implement effective supervision • Use responsibility accounting systems (e. g. , budgets) • Monitor system activities • Track purchased software and mobile devices • Conduct periodic audits (e. g. , external, internal, network security) • Employ computer security officer • Engage forensic specialists • Install fraud detection software • Implement fraud hotline Copyright © 2015 Pearson Education, Inc. 7 -46