Contextaware Computing Slides Prof Golden G Richard III

























































- Slides: 189

Context-aware Computing

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Context-aware Computing ü Beyond application-aware adaptation ü Instead of adapting only to resource levels, adapt to contexts ü Context: – Enumeration-based (categories) – Role-based (roles of context in building mobile applications) 2

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Types of Context ü Computing context includes network connectivity, ü ü 3 communication costs, communication bandwidth, and local resources, such as printers, displays, and workstations User context includes user profiles, location, and people in the vicinity of the user Physical context includes lighting and noise levels, traffic conditions, and temperature Temporal context includes time of day, week, month, and season of the year Context history is the recording of computing, user, and physical context over time

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. The 5 W’s… ü Who is the user? Who are the people with 4 which the user is interacting, or who is nearby? ü What is the user doing? ü Where is the user? Home? Work? Bathroom? Familiar coffee shop? ü When? What time is it? ü Why? Why is the user performing a certain task? What is the task’s priority in the “grand scheme”? ü Low-level vs. High-level details

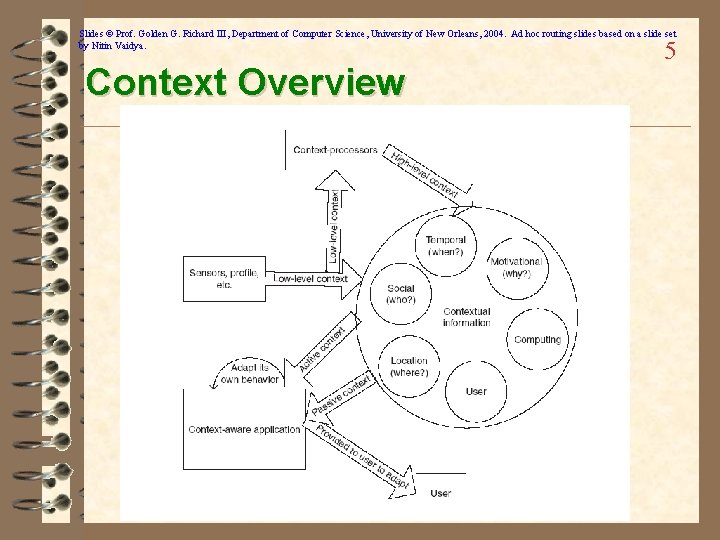
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Context Overview 5

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Context-aware Requirements 6 ü Contextual sensing – detection of environmental states ü Contextual adaptation – capability of the system to adapt its behavior by using contextual information ü Contextual resource discovery – capability to discover available resources in an environment ü Contextual augmentation – capability to associate contextual information with some digital data – Example: association of a particular meeting place and attendees with a set of minutes – Example: association of a digital photo with a specific location

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Designing CA Applications ü Build list of relevant contexts – e. g. , “home”, “office”, “traveling”, “sleeping”, … ü Specify context-aware behaviors – Presentation of context-sensitive information – Automatic discovery of relevant objects (e. g. , 7 nearby people for transmission of business cards) – Modification of the physical and digital environments ü Integration of application with methods for sensing context

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Simple Example: stick-e notes 8 ü Context-aware Post-it notes ü Build list of relevant contexts – Based on location (latitude/longitude via GPS) – Temperature, whatever else can be sensed ü Specify context-aware behaviors – stick-e notes “pop up” on a PDA when contextual info is appropriate – Reminder to return a library book when near the library – Reminder to buy a new winter jacket when temperature drops below 60 F ü Integration of application with methods for sensing context – Most difficult part – Ubiquitous sensing of environmental characteristics, such as location, temperature, number of human beings nearby, the cat is near, not widespread

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Where Does Context Come From? ü Returning to the “difficulty” point on the previous slide ü Environmental sensors – – Temperature, humidity, location, noise, motion Cat sensor Potential need for multiple types of sensors GPS vs. indoor location sensors ü History – Recording user actions and previous contexts ü User’s personal computing environment – Schedules, notes, address books, financial info ü Need real-time analysis to provide context 9

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Example: Location 10 ü Indoor locating systems – e. g. , infrared or ultrasound ü Wireless nanocell communication activity – Association with short-range base stations ü GPS ü Associations with nearby computers ü Motion sensors and cameras, computer vision ü Ask the user!

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service-oriented Architecture 11 ü Provide services to context-aware applications ü Context subscription and delivery service – Delivers contextual information as available ü Context query service – Delivers contextual information on-demand ü Context transformation and synthesis services – Transforms low-level contextual information (location, temperature, lighting levels) into high-level (“YOU’RE IN THE CLOSET IN YOUR BEDROOM”) ü Service discovery – Discovery of nearby services – We’ll examine service discovery protocols next!

Middleware

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Middleware for Mobile Applications ü Difficulties in development mobile apps – Disconnected operation – Resource poverty – Fluctuating resource levels – Need for dynamic discovery of services/peripherals ü Lots of mobile middleware to help – Adaptation middleware – Service discovery – Agent Systems – Toolkits to support disconnected operation –… 13

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Discovery: Motivation 14 ü Automatic configuration of new devices ü Highly dynamic system configurations ü Cooperation between resource poor devices ü Solves peripheral trading problem – Printing, FAX, storage, long-range networking services can be obtained from a nearby server ü Helps reduce duplication of functionality… ü …eliminates "toolbelt" syndrome ü Affects both mobile and wired systems

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Discovery: What? 15 ü Protocol suites for building highly dynamic client/server ü ü ü ü ü architectures Automatic discovery and configuration of new devices plugged into a network Self-healing networks: automatic “demise” of devices removed from a network Highly dynamic system configurations Cooperation between resource poor devices Solves form-factor vs. peripheral richness problem for mobile devices – Printing, FAX, storage, long-range networking services can be obtained from nearby servers Helps reduce duplication of functionality… …eliminates "toolbelt" syndrome Affects both mobile and wired systems Chapter 7 + Service and Device Discovery: Protocols and Programming (G. G. Richard III, Mc. Graw-Hill, 2002)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Discovery: Who? ü Jini – Sun Microsystems (Java) – www. jini. org ü Universal Plug and Play – Microsoft – www. upnp. org ü Service Location Protocol – Internet Engineering Task Force (IETF) – www. srvloc. org 16 ü Salutation – Salutation Consortium – www. salutation. org ü Bluetoooth (SDP) – Bluetooth Special Interest Group – www. bluetooth. com ü Ninja system at Berkeley – ninja. cs. berkeley. edu

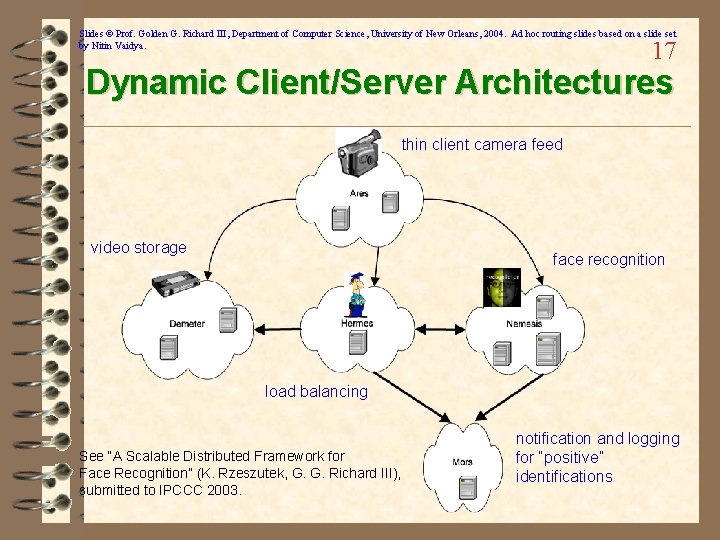
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 17 Dynamic Client/Server Architectures thin client camera feed video storage face recognition load balancing See “A Scalable Distributed Framework for Face Recognition” (K. Rzeszutek, G. G. Richard III), submitted to IPCCC 2003. notification and logging for “positive” identifications

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Discovery: Capabilities ü Protocol suites provide most or all of the following: – – – Ability to advertise available services Automatic discovery of nearby services Potential to discover services that aren’t nearby Ability to "discuss" service capabilities Abstraction • “I just need a printer” – Service catalogs (some) – Garbage collection facility (catalogs, service advertisements) 18

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Discovery: Scenarios 19

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 20 Dynamic Discovery of Devices Anyone need a printer? $$

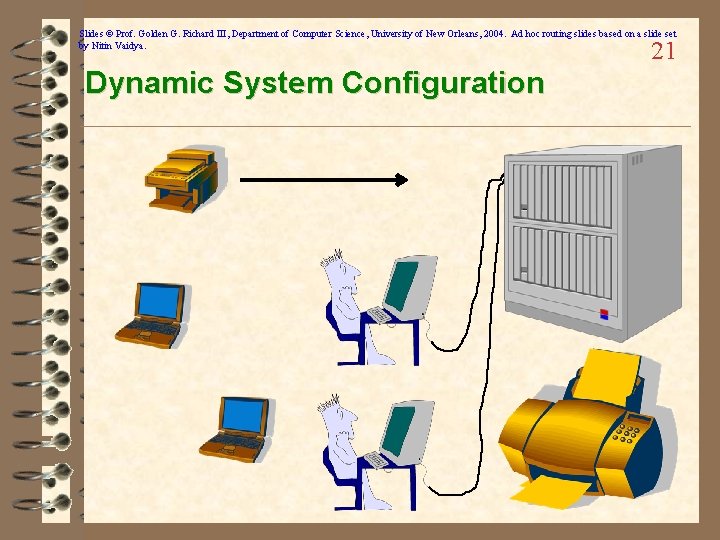
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 21 Dynamic System Configuration

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Discovery: Capabilities 22 ü Most or all of the following: – Ability to announce presence of resources – Automatic discovery of nearby devices – Ability to describe "discuss" capabilities – Abstraction • "I just need a printer" – Minimal human intervention – Everyone helps everyone (almost)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 23 Service Discovery: Components ü Common components include: – Clients (want services) – Services – Registry (catalogue of available services) – Announcement / Registry update – Registry cleanup (leases or similar) – Discovery protocol – Client Service connection

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 24 UPn. P (Universal Plug and Play) ü Microsoft’s offering – UPn. P "core" • • Auto. IP SSDP (Simple Service Discovery Protocol) SOAP (Simple Object Access Protocol) GENA (Generic Event Notification Architecture) ü Discussion based on 1. 0 specs ü No mobile code—instead, standardized protocols and service descriptions ü XML-based service descriptions and device client protocols ü Some discussion about a new spec which replaces SOAP with WSDL? (If so, not right away) ü A very interesting standardization process (…)

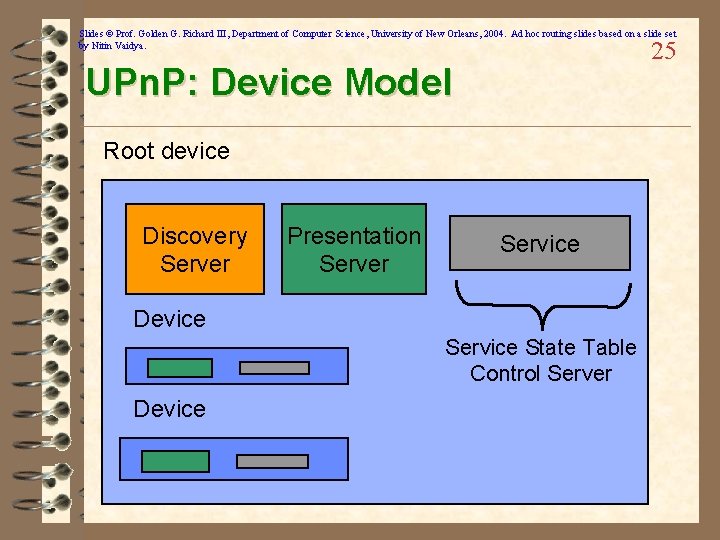
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 25 UPn. P: Device Model Root device Discovery Server Presentation Server Service Device Service State Table Control Server Device

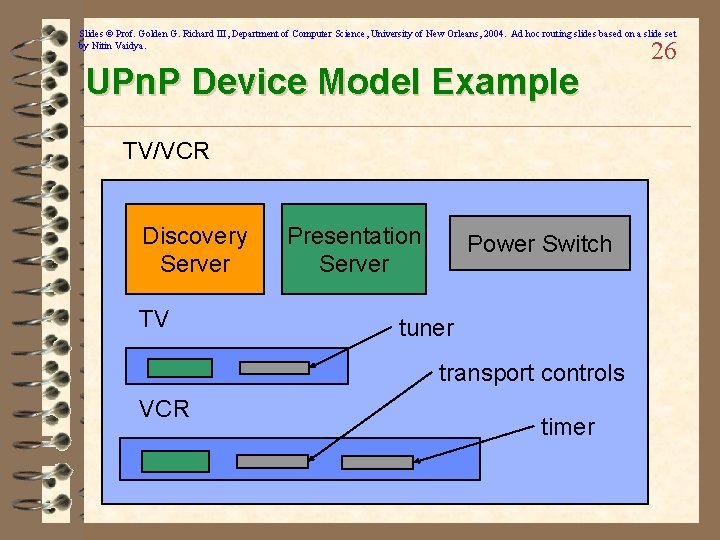
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. UPn. P Device Model Example TV/VCR Discovery Server TV Presentation Server Power Switch tuner transport controls VCR timer 26

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. UPn. P: Six Steps 27 ü Addressing Auto. IP – For the IP address impaired… ü Discovery SSDP – Discovery and advertisement (HTTP) ü Description – What are the characteristics of a service? ü Control SOAP – Making a service do its thing(s) ü Eventing GENA – Updates on interesting service state changes ü Presentation (HTTP) – Device GUI

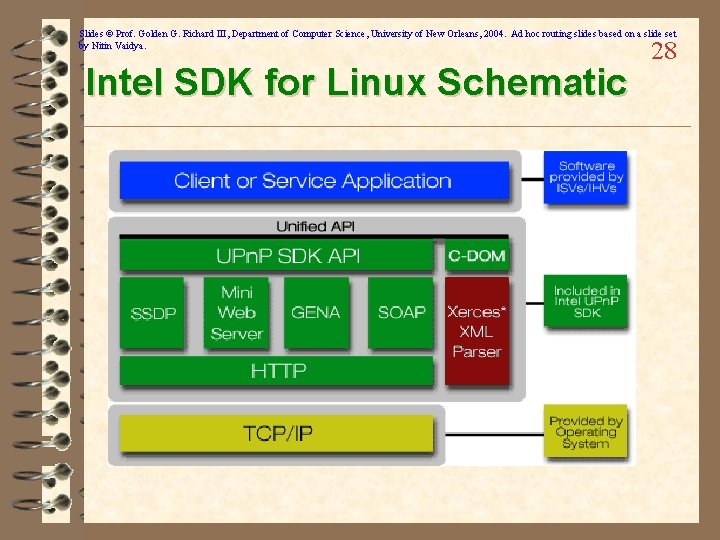
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Intel SDK for Linux Schematic 28

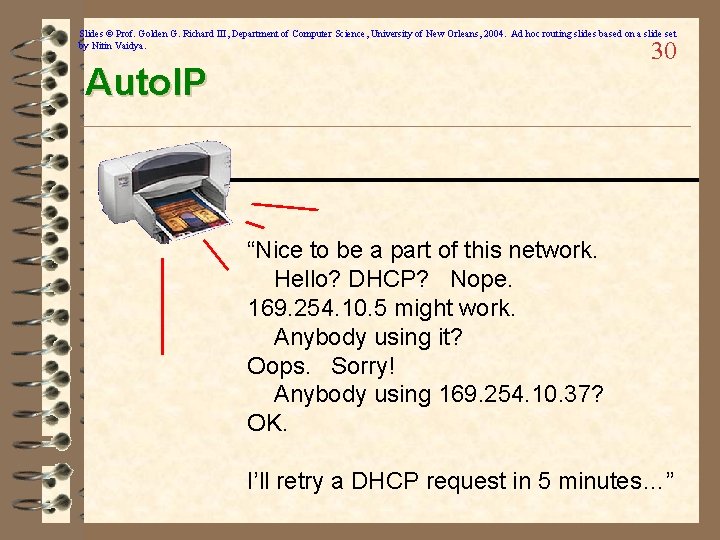
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Addressing: Auto. IP 29 ü IP address assignment w/o DHCP – Try to find DHCP server …on failure… – Pick a random address from a range of local addresses (169. *. *. * range) – ARP: Verify address is not in use – If in use, retry until some max attempts exceeded – Configure and use address – Periodically try to find DHCP server by sending discover query – If DHCP offer is received, use it ü These addresses are not routable!!

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 30 Auto. IP “Nice to be a part of this network. Hello? DHCP? Nope. 169. 254. 10. 5 might work. Anybody using it? Oops. Sorry! Anybody using 169. 254. 10. 37? OK. I’ll retry a DHCP request in 5 minutes…”

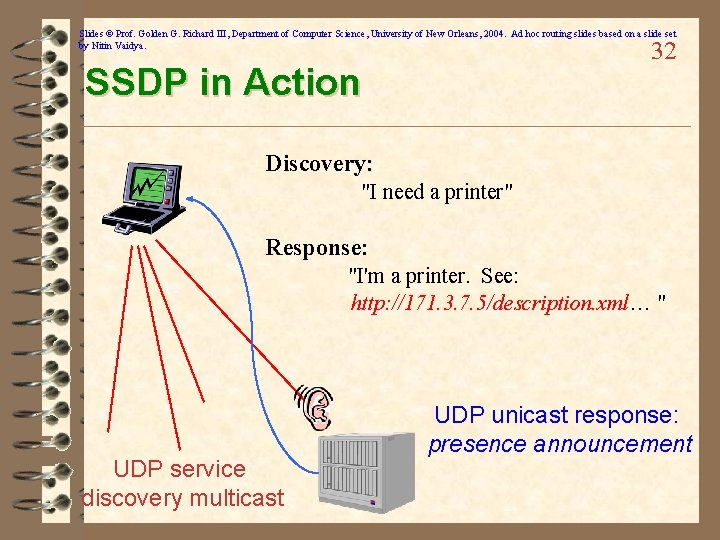
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Discovery: SSDP 31 ü Simple Service Discovery Protocol ü Supports both discovery and advertisement ü Based on UDP multicast / HTTP – local administrative scope multicast address 239. 255. 250 (see RFC 2365) ü Weak search capabilities – service type (multiple responses) or – unique device name (at most one response) ü Responses to discovery are URLs that identify device description documents ü Description document must be retrieved using standard HTTP to learn more about the device

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 32 SSDP in Action Discovery: "I need a printer" Response: "I'm a printer. See: http: //171. 3. 7. 5/description. xml… " UDP service discovery multicast UDP unicast response: presence announcement

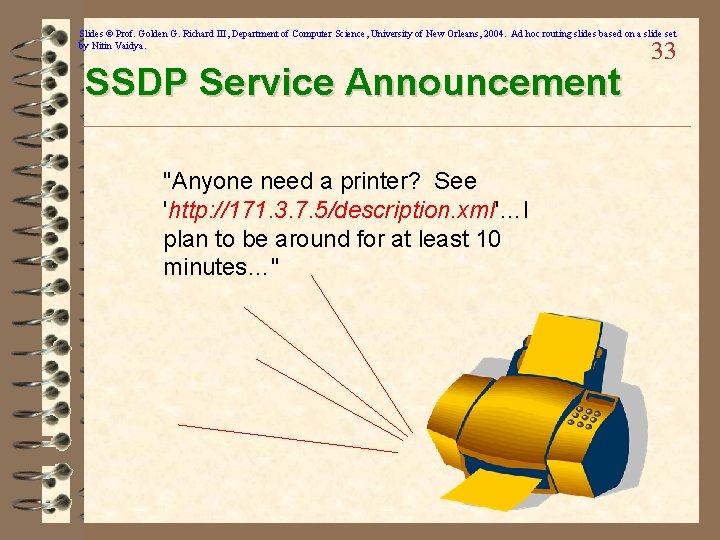
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. SSDP Service Announcement "Anyone need a printer? See 'http: //171. 3. 7. 5/description. xml'…I plan to be around for at least 10 minutes…" 33

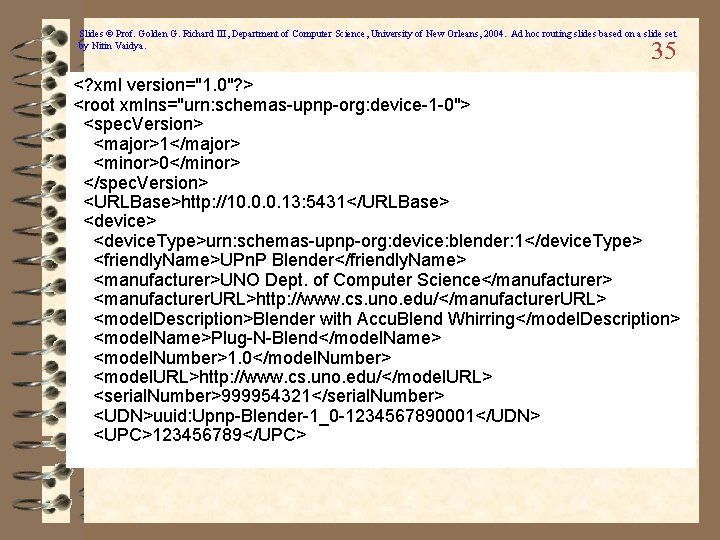
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. UPn. P Description Documents 34 ü XML description document contains: – Essential characteristics of device – Presentation URL • Provides link to HTML GUI for device – Service types offered by device – Control URLs for services • Entry point for device commands – Event subscription URLs for services • Allows subscription to device's event service • Significant device changes will result in notification • Provide our own event sink URL to subscribe – Pointers to Service Control Protocol (SCP) documents for services (these are also XML)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 35 <? xml version="1. 0"? > <root xmlns="urn: schemas-upnp-org: device-1 -0"> <spec. Version> <major>1</major> <minor>0</minor> </spec. Version> <URLBase>http: //10. 0. 0. 13: 5431</URLBase> <device. Type>urn: schemas-upnp-org: device: blender: 1</device. Type> <friendly. Name>UPn. P Blender</friendly. Name> <manufacturer>UNO Dept. of Computer Science</manufacturer> <manufacturer. URL>http: //www. cs. uno. edu/</manufacturer. URL> <model. Description>Blender with Accu. Blend Whirring</model. Description> <model. Name>Plug-N-Blend</model. Name> <model. Number>1. 0</model. Number> <model. URL>http: //www. cs. uno. edu/</model. URL> <serial. Number>999954321</serial. Number> <UDN>uuid: Upnp-Blender-1_0 -1234567890001</UDN> <UPC>123456789</UPC>

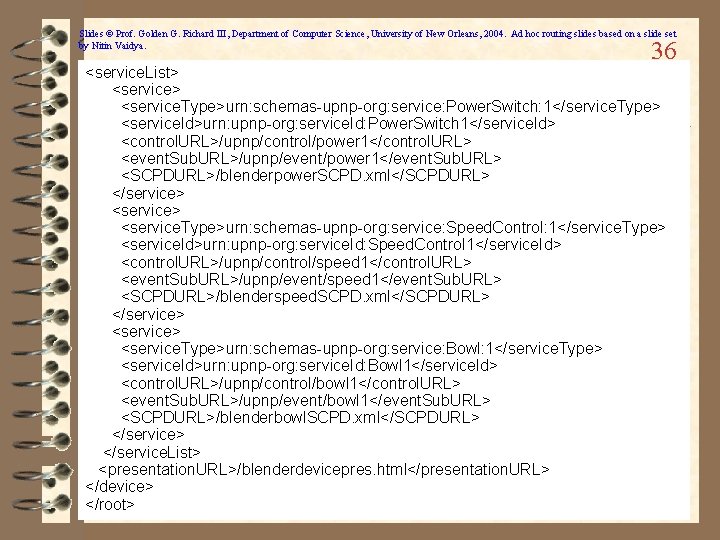
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 36 <service. List> <service. Type>urn: schemas-upnp-org: service: Power. Switch: 1</service. Type> <service. Id>urn: upnp-org: service. Id: Power. Switch 1</service. Id> <control. URL>/upnp/control/power 1</control. URL> <event. Sub. URL>/upnp/event/power 1</event. Sub. URL> <SCPDURL>/blenderpower. SCPD. xml</SCPDURL> </service> <service. Type>urn: schemas-upnp-org: service: Speed. Control: 1</service. Type> <service. Id>urn: upnp-org: service. Id: Speed. Control 1</service. Id> <control. URL>/upnp/control/speed 1</control. URL> <event. Sub. URL>/upnp/event/speed 1</event. Sub. URL> <SCPDURL>/blenderspeed. SCPD. xml</SCPDURL> </service> <service. Type>urn: schemas-upnp-org: service: Bowl: 1</service. Type> <service. Id>urn: upnp-org: service. Id: Bowl 1</service. Id> <control. URL>/upnp/control/bowl 1</control. URL> <event. Sub. URL>/upnp/event/bowl 1</event. Sub. URL> <SCPDURL>/blenderbowl. SCPD. xml</SCPDURL> </service. List> <presentation. URL>/blenderdevicepres. html</presentation. URL> </device> </root>

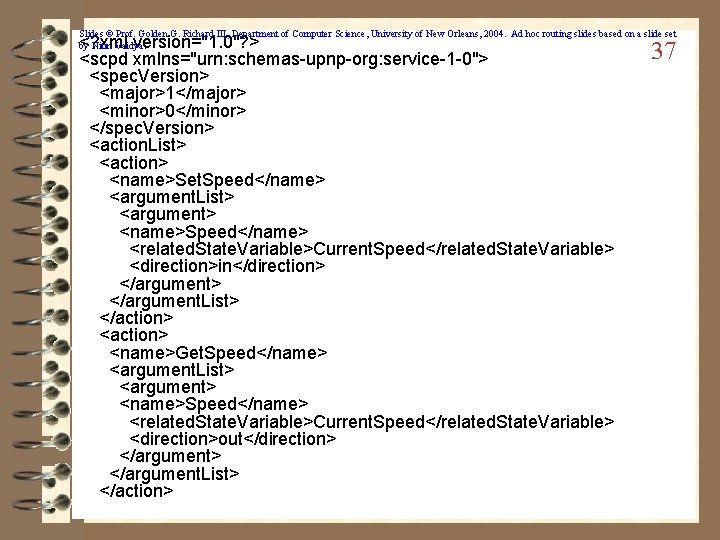
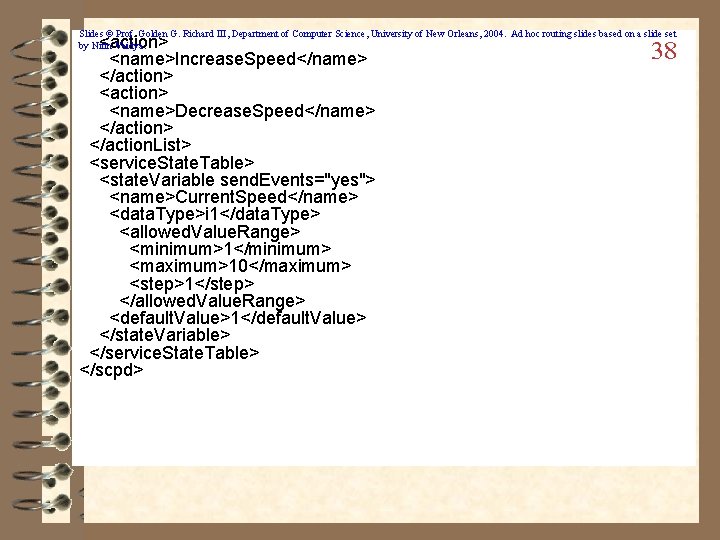
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. <? xml version="1. 0"? > <scpd xmlns="urn: schemas-upnp-org: service-1 -0"> <spec. Version> <major>1</major> <minor>0</minor> </spec. Version> <action. List> <action> <name>Set. Speed</name> <argument. List> <argument> <name>Speed</name> <related. State. Variable>Current. Speed</related. State. Variable> <direction>in</direction> </argument. List> </action> <name>Get. Speed</name> <argument. List> <argument> <name>Speed</name> <related. State. Variable>Current. Speed</related. State. Variable> <direction>out</direction> </argument. List> </action> 37

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. <action> <name>Increase. Speed</name> </action> <name>Decrease. Speed</name> </action. List> <service. State. Table> <state. Variable send. Events="yes"> <name>Current. Speed</name> <data. Type>i 1</data. Type> <allowed. Value. Range> <minimum>1</minimum> <maximum>10</maximum> <step>1</step> </allowed. Value. Range> <default. Value>1</default. Value> </state. Variable> </service. State. Table> </scpd> 38

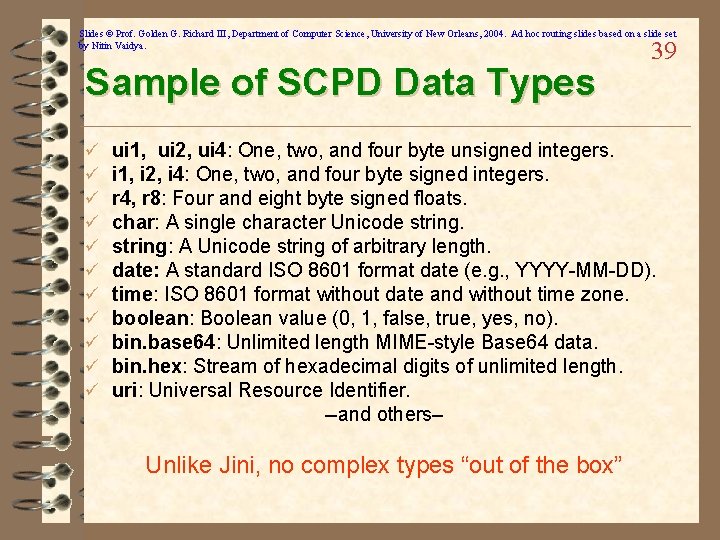
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Sample of SCPD Data Types ü ü ü 39 ui 1, ui 2, ui 4: One, two, and four byte unsigned integers. i 1, i 2, i 4: One, two, and four byte signed integers. r 4, r 8: Four and eight byte signed floats. char: A single character Unicode string: A Unicode string of arbitrary length. date: A standard ISO 8601 format date (e. g. , YYYY-MM-DD). time: ISO 8601 format without date and without time zone. boolean: Boolean value (0, 1, false, true, yes, no). bin. base 64: Unlimited length MIME-style Base 64 data. bin. hex: Stream of hexadecimal digits of unlimited length. uri: Universal Resource Identifier. --and others– Unlike Jini, no complex types “out of the box”

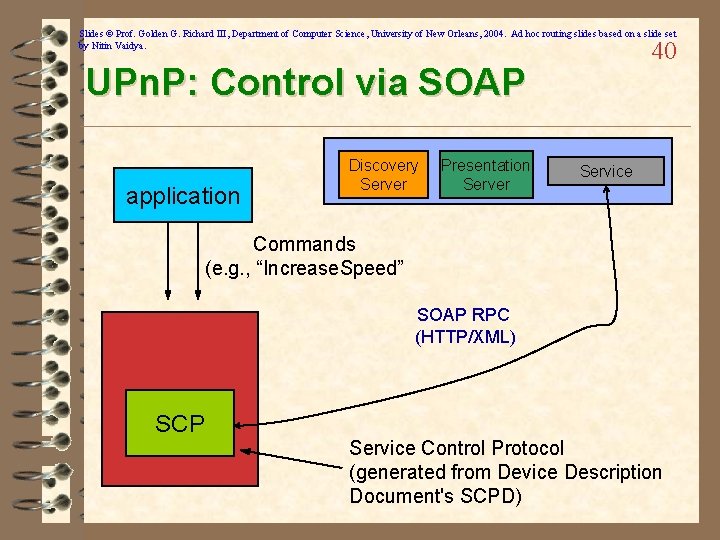
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 40 UPn. P: Control via SOAP application Discovery Server Presentation Server Service Commands (e. g. , “Increase. Speed” SOAP RPC (HTTP/XML) SCP Service Control Protocol (generated from Device Description Document's SCPD)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. UPn. P: Events (GENA) General Event Notification Architecture Expired IETF Draft (Microsoft authors) Subscription-based event notification service Subscribe (service of interest, callback URL) Resubscribe Unsubscribe Reports changes in state variable values for UPn. P devices ü Event messages contain XML-encoded state variables/values ü Unreliable, administratively-scoped UDP multicast and extensions to HTTP ü ü ü ü 41

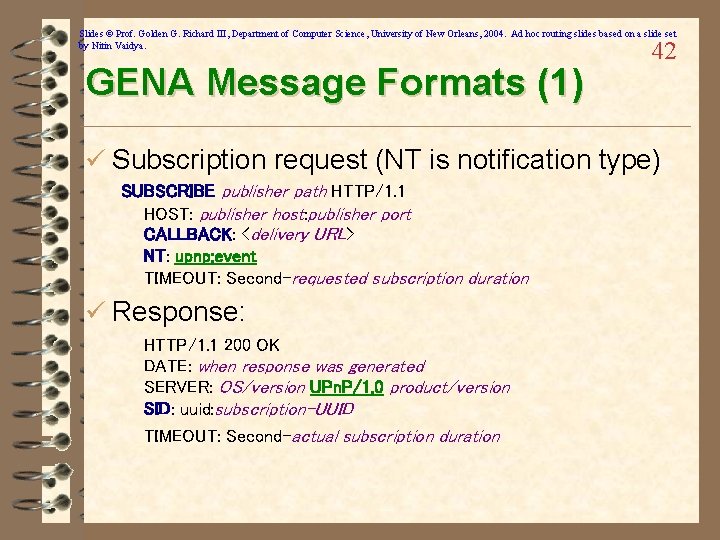
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. GENA Message Formats (1) 42 ü Subscription request (NT is notification type) SUBSCRIBE publisher path HTTP/1. 1 HOST: publisher host: publisher port CALLBACK: <delivery URL> NT: upnp: event TIMEOUT: Second-requested subscription duration ü Response: HTTP/1. 1 200 OK DATE: when response was generated SERVER: OS/version UPn. P/1. 0 product/version SID: uuid: subscription-UUID TIMEOUT: Second-actual subscription duration

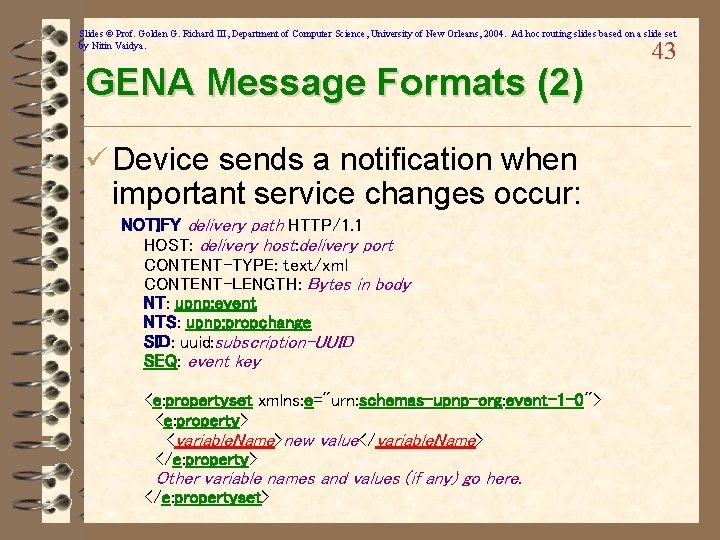
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. GENA Message Formats (2) ü Device sends a notification when important service changes occur: NOTIFY delivery path HTTP/1. 1 HOST: delivery host: delivery port CONTENT-TYPE: text/xml CONTENT-LENGTH: Bytes in body NT: upnp: event NTS: upnp: propchange SID: uuid: subscription-UUID SEQ: event key <e: propertyset xmlns: e="urn: schemas-upnp-org: event-1 -0"> <e: property> <variable. Name>new value</variable. Name> </e: property> Other variable names and values (if any) go here. </e: propertyset> 43

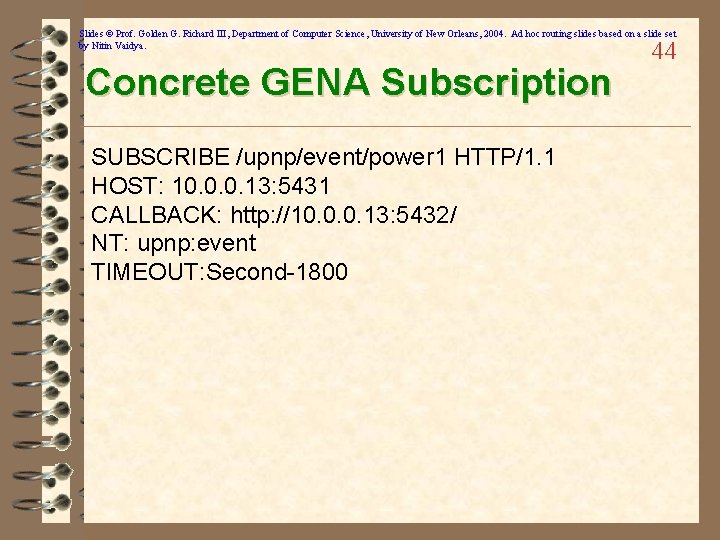
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Concrete GENA Subscription SUBSCRIBE /upnp/event/power 1 HTTP/1. 1 HOST: 10. 0. 0. 13: 5431 CALLBACK: http: //10. 0. 0. 13: 5432/ NT: upnp: event TIMEOUT: Second-1800 44

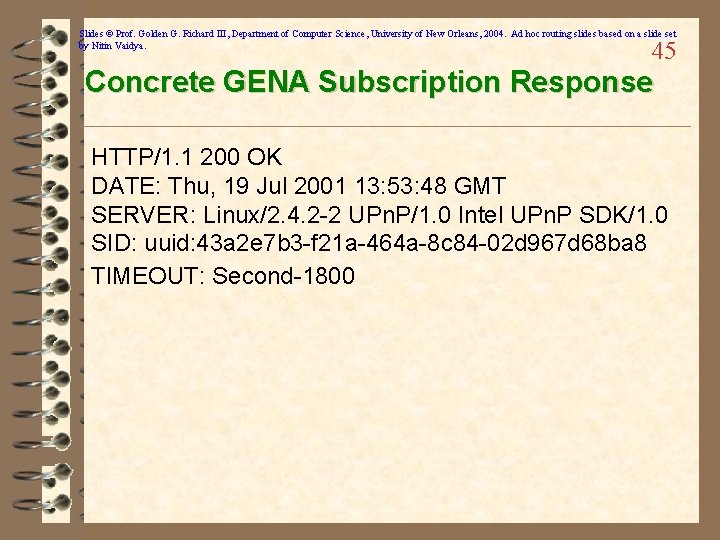
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 45 Concrete GENA Subscription Response HTTP/1. 1 200 OK DATE: Thu, 19 Jul 2001 13: 53: 48 GMT SERVER: Linux/2. 4. 2 -2 UPn. P/1. 0 Intel UPn. P SDK/1. 0 SID: uuid: 43 a 2 e 7 b 3 -f 21 a-464 a-8 c 84 -02 d 967 d 68 ba 8 TIMEOUT: Second-1800

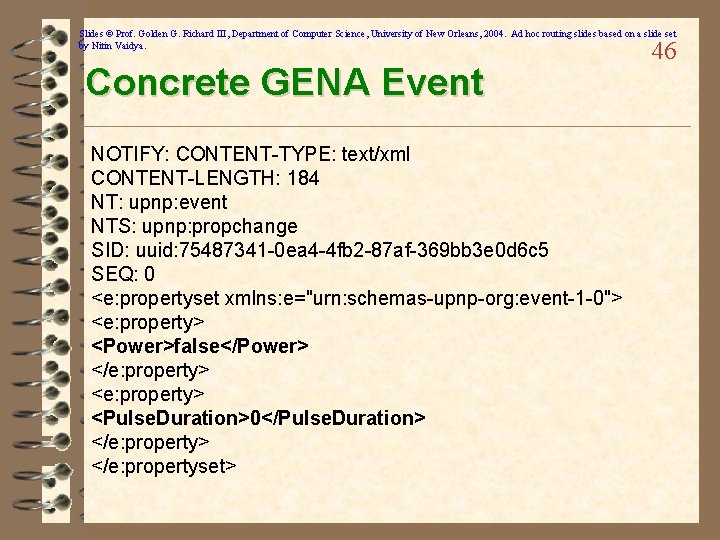
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Concrete GENA Event NOTIFY: CONTENT-TYPE: text/xml CONTENT-LENGTH: 184 NT: upnp: event NTS: upnp: propchange SID: uuid: 75487341 -0 ea 4 -4 fb 2 -87 af-369 bb 3 e 0 d 6 c 5 SEQ: 0 <e: propertyset xmlns: e="urn: schemas-upnp-org: event-1 -0"> <e: property> <Power>false</Power> </e: property> <Pulse. Duration>0</Pulse. Duration> </e: propertyset> 46

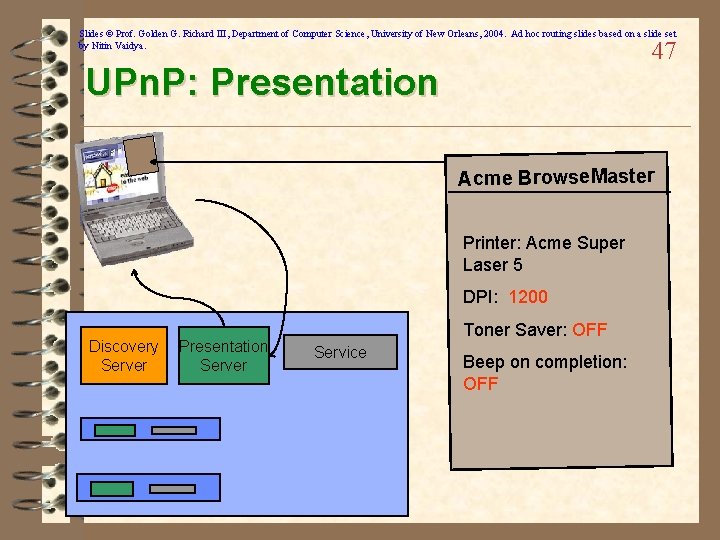
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 47 UPn. P: Presentation Acme Browse. Master Printer: Acme Super Laser 5 DPI: 1200 Discovery Server Presentation Server Toner Saver: OFF Service Beep on completion: OFF

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. UPn. P: Thoughts ü Lighter weight than Jini ü Some serious limitations… – No directory agents – No security architecture – Limited search capabilities (…) – How much community involvement? ü Some scary language (to me) in the standardization process ü Widespread adoption almost certain 48

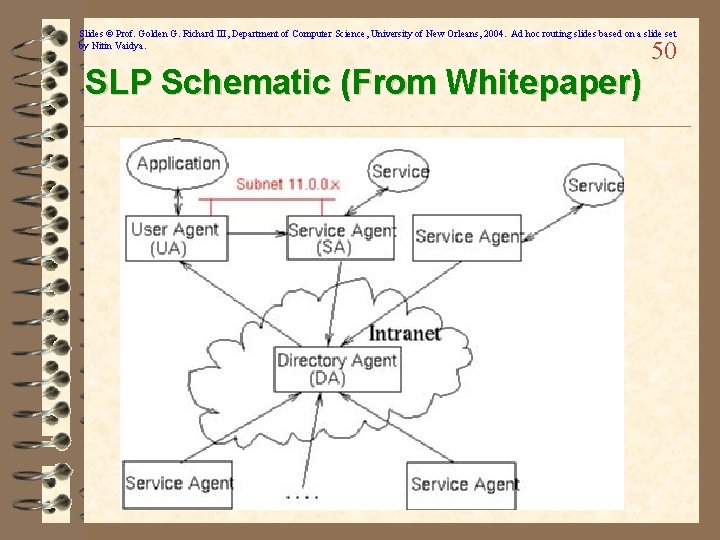
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 49 SLP: Service Location Protocol ü SLP: IETF draft protocol ü Defines three types of agents: – User Agents: acquire service handles for apps – Service Agents: advertise service handles – Directory Agents, cache service handles ü Main concerns: – Allow UA's to obtain service handles – Maintain directory of advertised services – Discover available service types, attributes – Finding directory agents – Allow service discovery/advertisements even in the absence of directory agents

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. SLP Schematic (From Whitepaper) 50

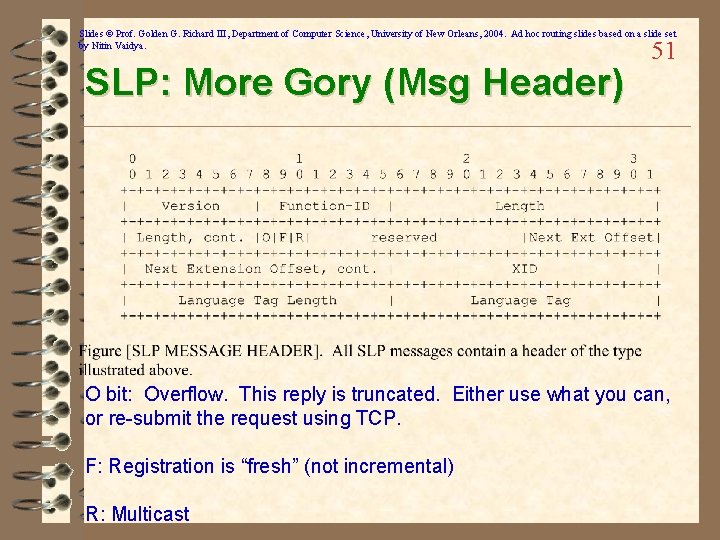
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. SLP: More Gory (Msg Header) 51 O bit: Overflow. This reply is truncated. Either use what you can, or re-submit the request using TCP. F: Registration is “fresh” (not incremental) R: Multicast

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Identifying Services 52 ü Service templates define the format of a URL for a specific type of service ü Examples of Service URLS: ü service: echo-service. test: tcp: //10. 0. 0. 13: 5000 ü service: printer: lpr: //printer. cs. uno. edu/laser ü service: image-service. test: //imaging. cs. uno. edu/ Susanne. jpeg; format=JPEG; resolution=1024 x 768

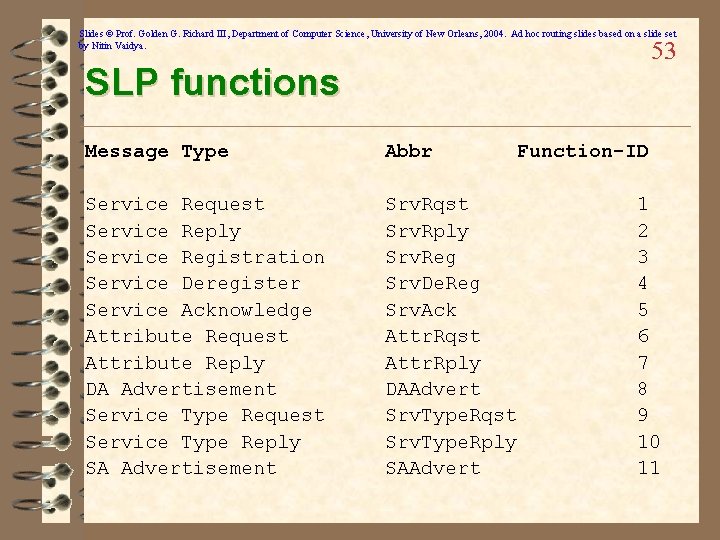
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 53 SLP functions Message Type Abbr Service Request Service Reply Service Registration Service Deregister Service Acknowledge Attribute Request Attribute Reply DA Advertisement Service Type Request Service Type Reply SA Advertisement Srv. Rqst Srv. Rply Srv. Reg Srv. De. Reg Srv. Ack Attr. Rqst Attr. Rply DAAdvert Srv. Type. Rqst Srv. Type. Rply SAAdvert Function-ID 1 2 3 4 5 6 7 8 9 10 11

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Advertisements 54

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Requests 55

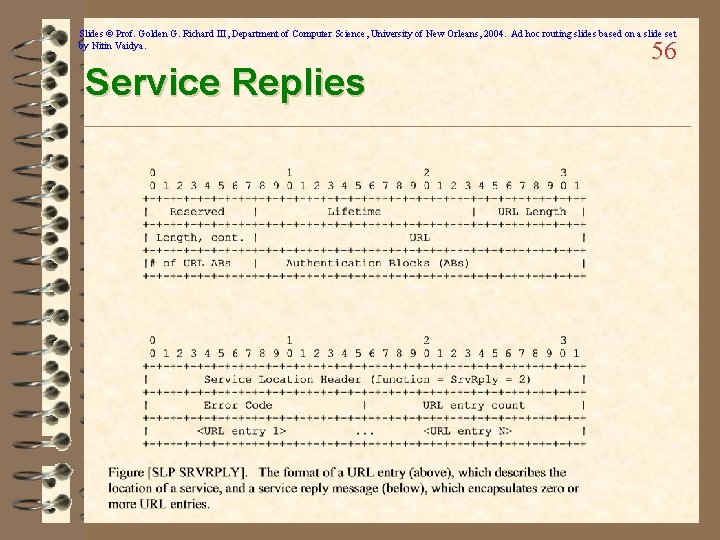
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Service Replies 56

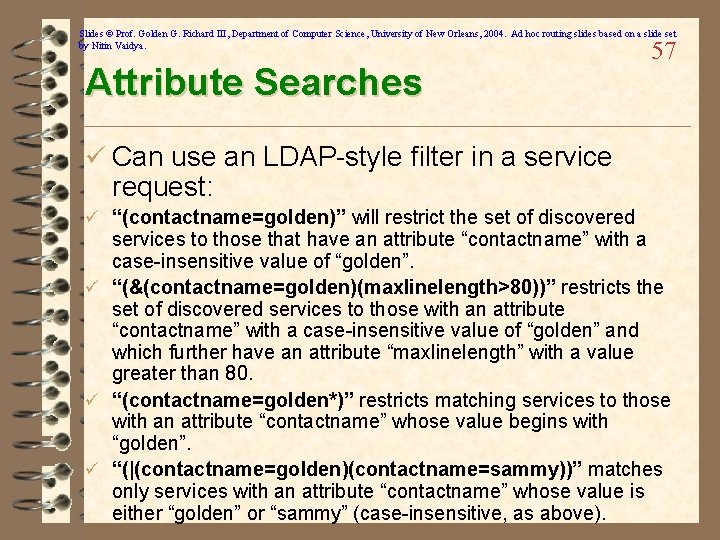
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Attribute Searches 57 ü Can use an LDAP-style filter in a service request: ü “(contactname=golden)” will restrict the set of discovered services to those that have an attribute “contactname” with a case-insensitive value of “golden”. ü “(&(contactname=golden)(maxlinelength>80))” restricts the set of discovered services to those with an attribute “contactname” with a case-insensitive value of “golden” and which further have an attribute “maxlinelength” with a value greater than 80. ü “(contactname=golden*)” restricts matching services to those with an attribute “contactname” whose value begins with “golden”. ü “(|(contactname=golden)(contactname=sammy))” matches only services with an attribute “contactname” whose value is either “golden” or “sammy” (case-insensitive, as above).

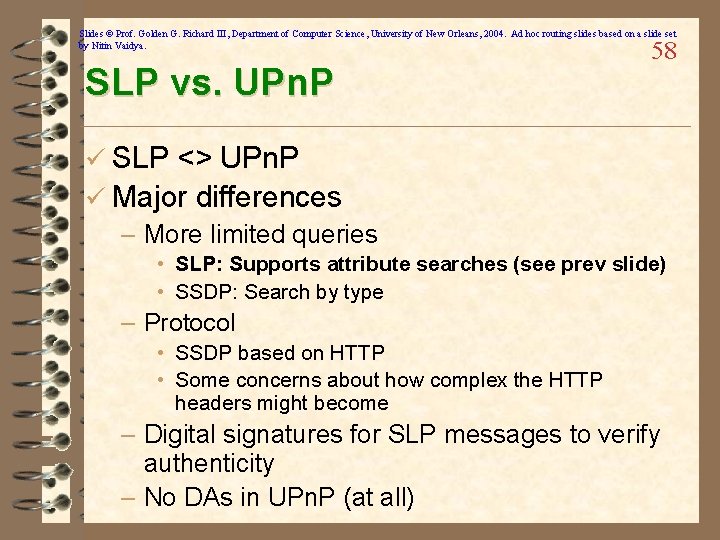
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. SLP vs. UPn. P 58 ü SLP <> UPn. P ü Major differences – More limited queries • SLP: Supports attribute searches (see prev slide) • SSDP: Search by type – Protocol • SSDP based on HTTP • Some concerns about how complex the HTTP headers might become – Digital signatures for SLP messages to verify authenticity – No DAs in UPn. P (at all)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Ninja Project (UC Berkeley) 59 Java-based service discovery protocol XML service descriptions and queries Focus on higher security All communication encrypted (Authenticated RMI) All entities have digital certificates Authentication of endpoints (e. g. , clients, services) Rather than only restrict access to services, restrict knowledge of existence of services ü See “An Architecture for a Secure Service Discovery Service” (Czerwinski, Zhao, Hodes, Joseph, Katz), Mobicom ’ 99, pp. 24 -35. ü ü ü ü

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Interoperability 60 ü Why? – Most service discovery suites are (moderately) healthy – Not reasonable for cheap devices to implement more than one service discovery technology – In current “dog eat dog” phase, not too much work on interoperability coming out of the SIGs themselves – If you’re a systems type, excuse for hacking ü It’s not easy – Different standardization approaches: textual vs. interfaces – Mobile code vs. standardized protocols – Java interfaces can expose very complex data structures • Hashtables of sets of vectors of… – – Arguments to UPn. P RPCs are generally simple types Service catalogs vs. peer-to-peer for discovery/advertisement Eventing Different security architectures

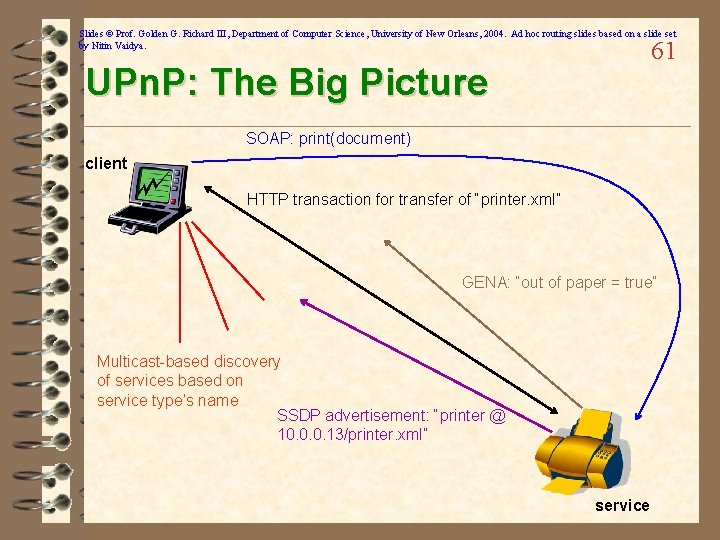
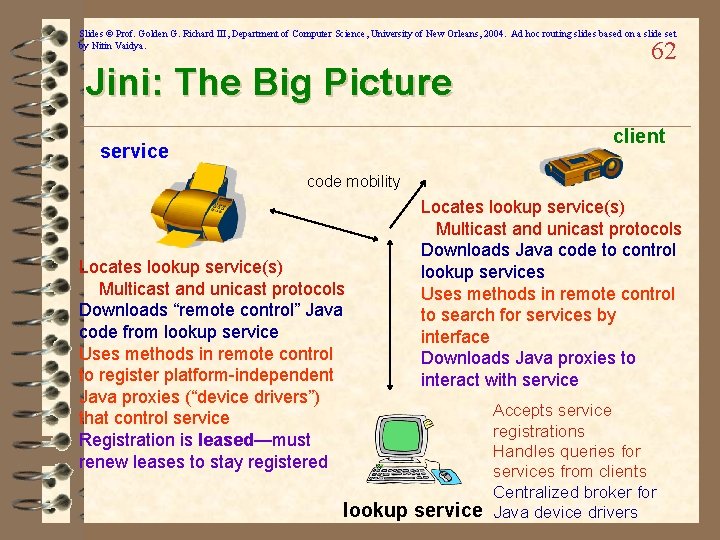
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 61 UPn. P: The Big Picture SOAP: print(document) client HTTP transaction for transfer of “printer. xml” GENA: “out of paper = true” Multicast-based discovery of services based on service type’s name SSDP advertisement: “printer @ 10. 0. 0. 13/printer. xml” service

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Jini: The Big Picture 62 client service code mobility Locates lookup service(s) Multicast and unicast protocols Downloads “remote control” Java code from lookup service Uses methods in remote control to register platform-independent Java proxies (“device drivers”) that control service Registration is leased—must renew leases to stay registered Locates lookup service(s) Multicast and unicast protocols Downloads Java code to control lookup services Uses methods in remote control to search for services by interface Downloads Java proxies to interact with service Accepts service registrations Handles queries for services from clients Centralized broker for lookup service Java device drivers

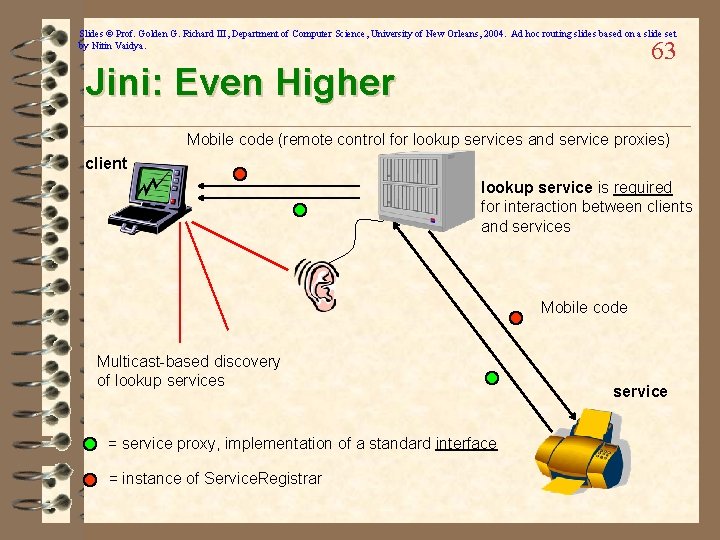
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 63 Jini: Even Higher Mobile code (remote control for lookup services and service proxies) client lookup service is required for interaction between clients and services Mobile code Multicast-based discovery of lookup services = service proxy, implementation of a standard interface = instance of Service. Registrar service

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 64 Jini Meets UPn. P: Our Requirements ü Bidirectional interoperability ü No changes to existing UPn. P/Jini clients/services ü Thus: interoperability framework is invisible to existing clients and services ü No requirement that source code for clients/services be available – But it doesn’t hurt… ü Discovery, advertisement, and garbage collection facilities must work as expected ü Service-specific proxies handle transformations ü Implementation of these proxies must be as easy as possible – Means: lots of standard “glue” included in the framework – Goal: “an afternoon’s hacking by a smart graduate student” to support a new service type

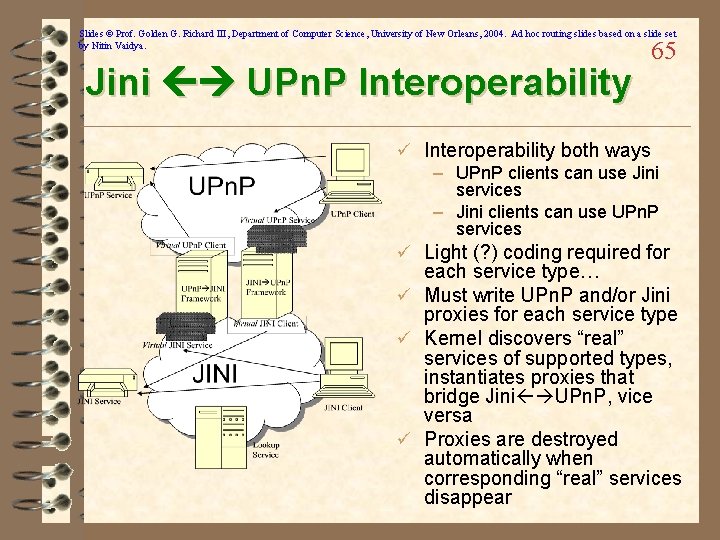
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Jini UPn. P Interoperability 65 ü Interoperability both ways – UPn. P clients can use Jini services – Jini clients can use UPn. P services ü Light (? ) coding required for each service type… ü Must write UPn. P and/or Jini proxies for each service type ü Kernel discovers “real” services of supported types, instantiates proxies that bridge Jini UPn. P, vice versa ü Proxies are destroyed automatically when corresponding “real” services disappear

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Jini UPn. P Interoperability (2) 66 See “Jini Meets UPn. P: An Architecture for Jini/UPn. P Interoperability” (J. Allard, V. Chinta, S. Gundala, G. G. Richard III), SAINT 2003 (Orlando).

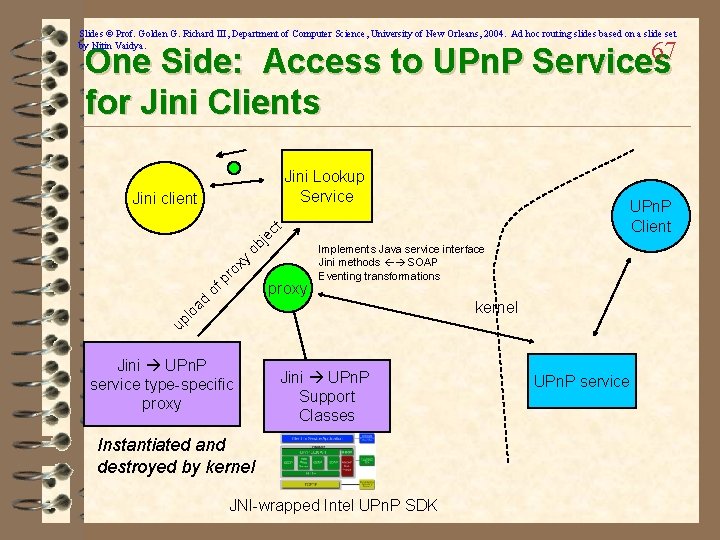
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 67 One Side: Access to UPn. P Services for Jini Clients Jini Lookup Service UPn. P Client of p ro xy ob je ct Jini client proxy Implements Java service interface Jini methods SOAP Eventing transformations up lo ad kernel Jini UPn. P service type-specific proxy Jini UPn. P Support Classes Instantiated and destroyed by kernel JNI-wrapped Intel UPn. P SDK UPn. P service

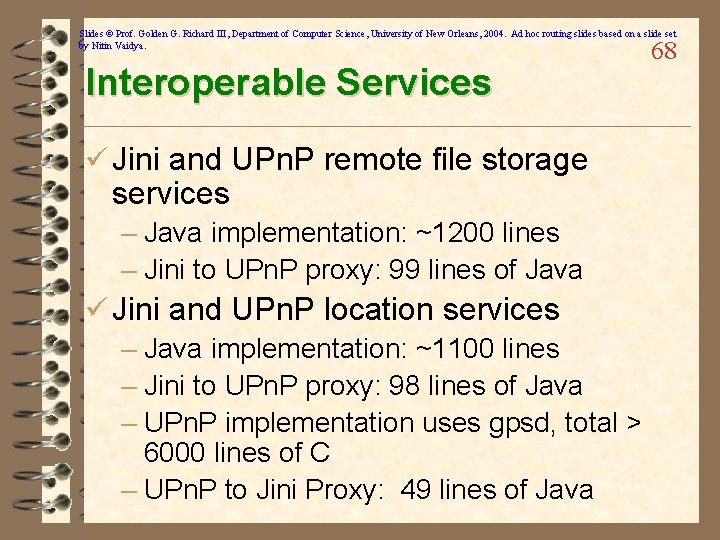
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Interoperable Services ü Jini and UPn. P remote file storage services – Java implementation: ~1200 lines – Jini to UPn. P proxy: 99 lines of Java ü Jini and UPn. P location services – Java implementation: ~1100 lines – Jini to UPn. P proxy: 98 lines of Java – UPn. P implementation uses gpsd, total > 6000 lines of C – UPn. P to Jini Proxy: 49 lines of Java 68

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Other Interoperability ü Salutation uses SLP directories beyond the local network 69 segment ü There is a Jini SLP bridge – “Smart” agent finds Jini-enabled SLP services and registers them with Jini lookup services – “Enabled” means the service has a bundle of static Java code – Static code is a factory—can instantiate a live object to speak the appropriate protocol for communicating with the service – Simply: The static code is a Java device driver – Service does not run a JVM – One direction only—does not provide access to SLP services for Jini clients – See “Automatic Discovery of Thin Servers: SLP, Jini and the SLP-Jini Bridge” (E. Guttman, J. Kempf), IECON, San Jose, 1999.

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Interoperability (2) 70 ü Everything over Bluetooth – Can run IP over Bluetooth, thus Jini et al – Either use Bluetooth as data link protocol and forget Bluetooth SDP, or map protocol operations to Bluetooth SDP operations ü Salutation over Bluetooth – As above (Salutation over IP over Bluetooth) – Some work on mapping Salutation API directly to Bluetooth SDP – See paper “Mapping Salutation Architecture APIs to Bluetooth Service Discovery Layer” – http: //www. salutation. org/whitepaper/Btooth. Mapping. PDF

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 71 Service Discovery: Random Thoughts ü "I'm transport-independent—you're IP!" ü "You require Java!" ü "You require standard device protocols!" ü Standardizing Jini interfaces will be challenging… ü But standardizing protocols (UPn. P, Salutation) isn’t easy either ü Device manufacturers are unlikely to be thrilled w/ supporting multiple approaches ü Best technical approach (which is? ? ), as usual, isn’t guaranteed to win ü Each has some interesting features – Nested devices in UPn. P – Javaspaces/Transaction management in Jini – Security architecture in SLP

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Summary 72 ü Service discovery great for building highly dynamic ü ü ü ü systems Enabler for small information appliances Lots of contenders for the title Best technical approach won’t necessarily be the winner So far, very little standardization of service types (for any of the protocol suites) Good device standards critical Interoperability important Security very important Lots of industrial need consulting, contracts

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Agents: Motivation ü Mobile agent systems support dynamic migration of bits of software ü These “bits of software” are agents, and perform tasks remotely in support of some local computation ü Some advantages: – Disconnected operation – Customized, “do once” operations without customizing server software – Attacks resource-poverty problem for mobile computing • Less bandwidth, power, CPU needed 73

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 74 Searching Tech Reports: No Agents Tech report server MH Queries, responses, transfer of documents

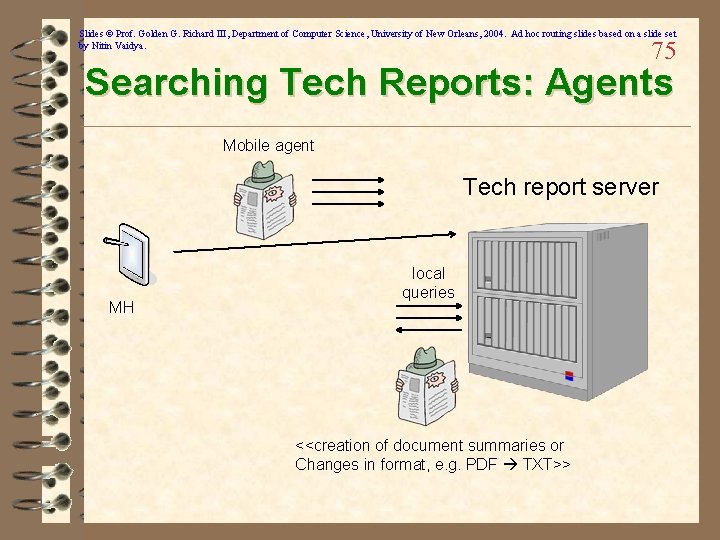
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 75 Searching Tech Reports: Agents Mobile agent Tech report server MH local queries <<creation of document summaries or Changes in format, e. g. PDF TXT>>

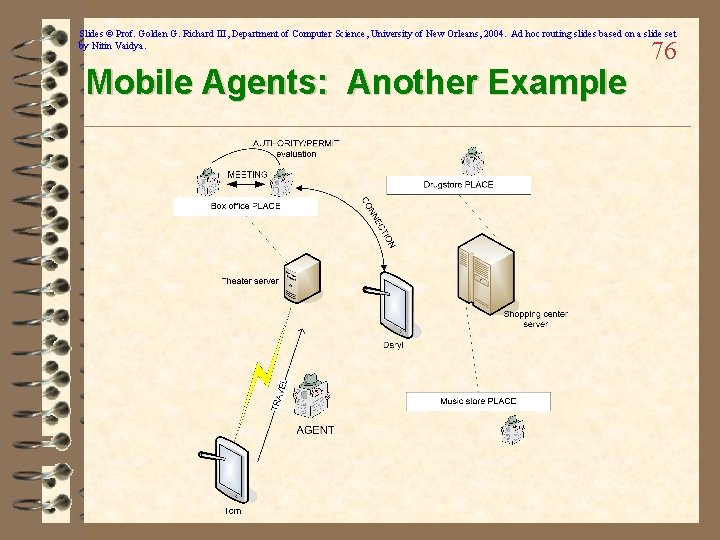
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Agents: Another Example 76

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Agents: Roadblocks 77 ü Security ü Users’ trust in mobile code has been badly damaged – Applets, Javascript, other scripting languages are far less sophisticated than agents, but… ü Infrastructure ü Lack of a “killer” application ü Standardization ü (Security)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Agents: Technical Issues ü Security! ü Implementation language for agents – Interpreted languages easier – Don’t want to insist on homogeneous architectures! ü Migration strategy – Again, easier with languages like Java – Otherwise, becomes a process checkpointing problem ü Communication strategy – Temporal locality: must communicate with other agents while they’re around, or not? – Spatial locality: must be able to name and locate other agents to communicate 78

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Agent Communication: Traditional 79 ü Sockets, RMI, … ü Strong temporal locality ü Other guy must be around to communicate ü Other guy’s “name” reveals his location

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 80 Agent Communication: Meeting Places ü A “meeting room” for agents ü Agents must migrate to the meeting room to communicate ü Temporal locality—other agents must be present to communicate ü Spatial locality—communicate with other agents in the meeting place, can dynamically determine who’s there

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 81 Agent Communication: Tuple Spaces ü Communicate by dropping objects into a shared space ü Relaxes temporal and spatial locality ü Can drop objects for other agents whether they’re around or not ü Don’t have to know their names or locations ü Simpler to use local tuple spaces (one per place? ) ü Can use reactions, which cause code to be executed when a certain type of object (e. g. , a “cash” object) is dropped into the space

Ad hoc / sensor networks (Ch 8 ) Slides 82 -158 are based on a slide set by Nitin Vaidya of UIUC (formerly, Texas A&M) and are used with his permission.

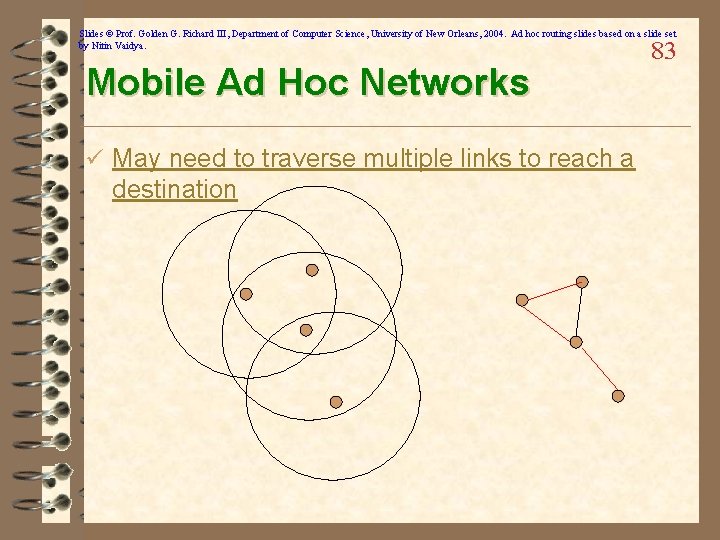
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Ad Hoc Networks ü May need to traverse multiple links to reach a destination 83

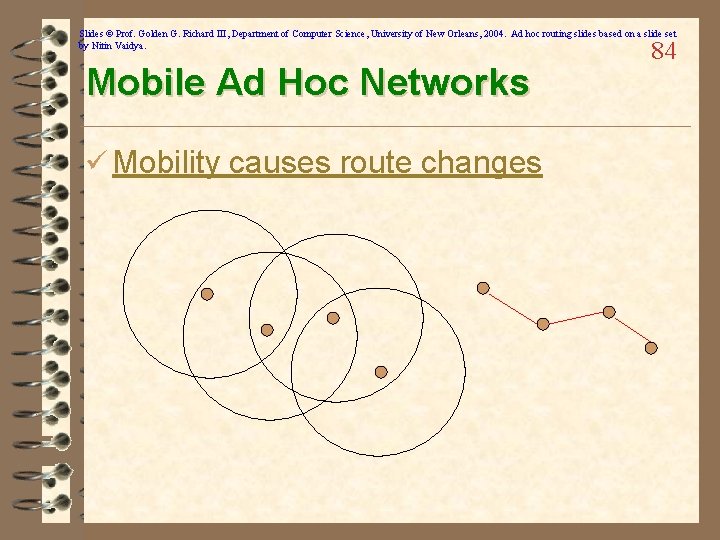
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Ad Hoc Networks ü Mobility causes route changes 84

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Ad Hoc Networks 85 ü Formed by wireless hosts which may be mobile ü Don’t need a pre-existing infrastructure – ie, don’t need a backbone network, routers, etc. ü Routes between nodes potentially contain multiple hops ü Why MANET? – Ease, speed of deployment – Decreased dependence on infrastructure – Can use in many scenarios where deployment of a wired network is impractical or impossible – Lots of military applications, but there are others… ,

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Many Applications 86 ü Personal area networking – cell phone, laptop, ear phone, wrist watch ü Civilian environments – meeting rooms – sports stadiums – groups of boats, small aircraft (wired REALLY impractical!!) ü Emergency operations – search-and-rescue – policing and fire fighting ü Sensor networks – Groups of sensors embedded in the environment or scattered over a target area

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Many Variations ü Fully Symmetric Environment – all nodes have identical capabilities and responsibilities ü Asymmetric Capabilities – – transmission ranges and radios may differ battery life at different nodes may differ processing capacity may be different at different nodes speed of movement different ü Asymmetric Responsibilities – only some nodes may route packets – some nodes may act as leaders of nearby nodes (e. g. , “cluster head”) 87

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Many Variations ü Traffic characteristics may differ – bandwidth – timeliness constraints – reliability requirements – unicast / broadcast / multicast / geocast ü May co-exist (and co-operate) with an infrastructure-based network 88

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Many Variations 89 ü Mobility patterns may be different – people sitting at an airport lounge (little mobility) – taxi cabs (highly mobile) – military movements (mostly clustered? ) – personal area network (again, mostly clustered? ) ü Mobility characteristics – speed – predictability • direction of movement • pattern of movement – uniformity (or lack thereof) of mobility characteristics among different nodes

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Challenges 90 Limited wireless transmission range Broadcast nature of the wireless medium Packet losses due to transmission errors Environmental issues (“chop that tree!!”) Mobility-induced route changes Mobility-induced packet losses Battery constraints Potentially frequent network partitions Ease of snooping on wireless transmissions (security hazard) ü Sensor networks: very resource-constrained! ü ü ü ü ü

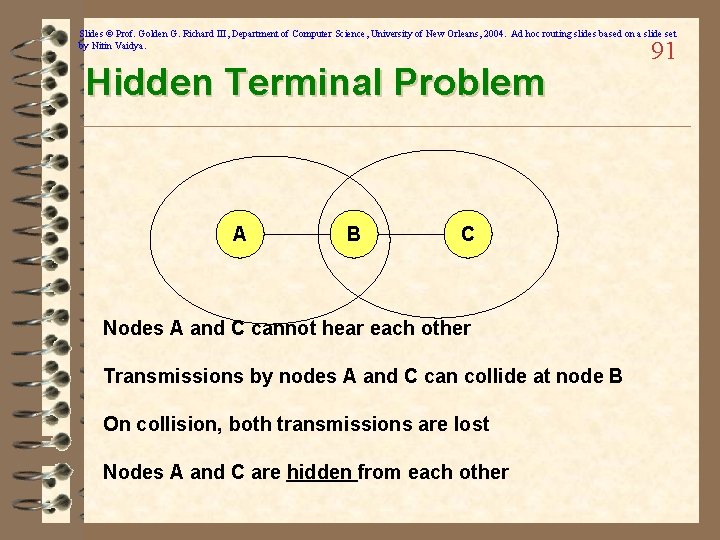
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Hidden Terminal Problem A B C Nodes A and C cannot hear each other Transmissions by nodes A and C can collide at node B On collision, both transmissions are lost Nodes A and C are hidden from each other 91

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. First Issue: Routing 92 ü Why is Ad hoc Routing Different? ü Host mobility – link failure/repair due to mobility may have different characteristics than those due to other causes – traditional routing algorithms assume relatively stable network topology, few router failures ü Rate of link failure/repair may be high when nodes move fast ü New performance criteria may be used – route stability despite mobility – energy consumption

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Routing Protocols ü Proactive protocols – Determine routes independent of traffic pattern – Traditional routing protocols for wired networks are proactive ü Reactive protocols – Discover/maintain routes only if needed 93

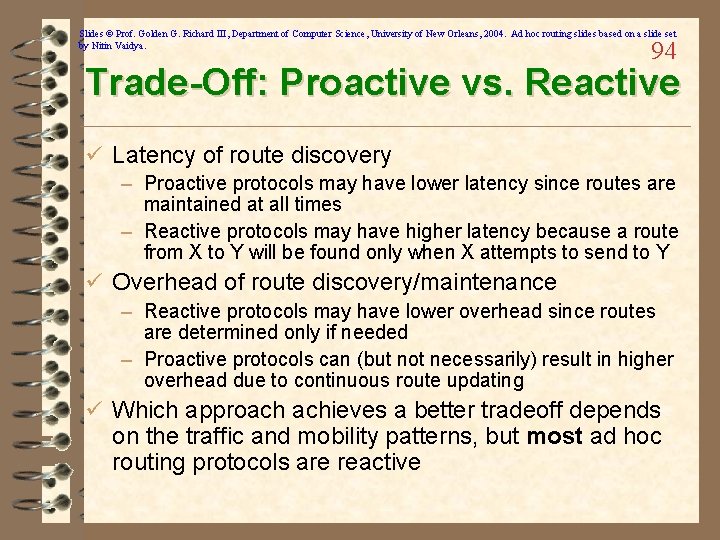
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 94 Trade-Off: Proactive vs. Reactive ü Latency of route discovery – Proactive protocols may have lower latency since routes are maintained at all times – Reactive protocols may have higher latency because a route from X to Y will be found only when X attempts to send to Y ü Overhead of route discovery/maintenance – Reactive protocols may have lower overhead since routes are determined only if needed – Proactive protocols can (but not necessarily) result in higher overhead due to continuous route updating ü Which approach achieves a better tradeoff depends on the traffic and mobility patterns, but most ad hoc routing protocols are reactive

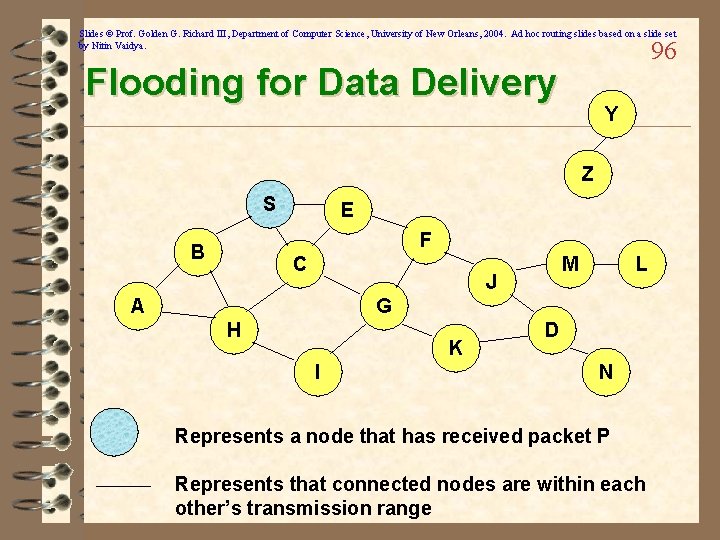
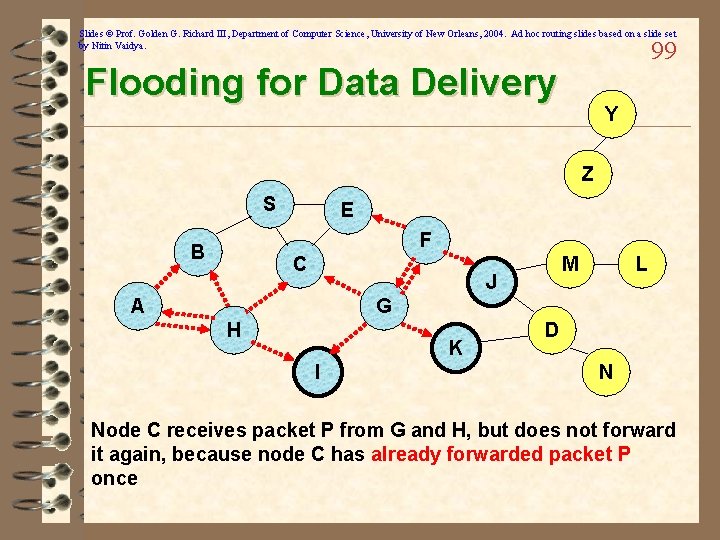
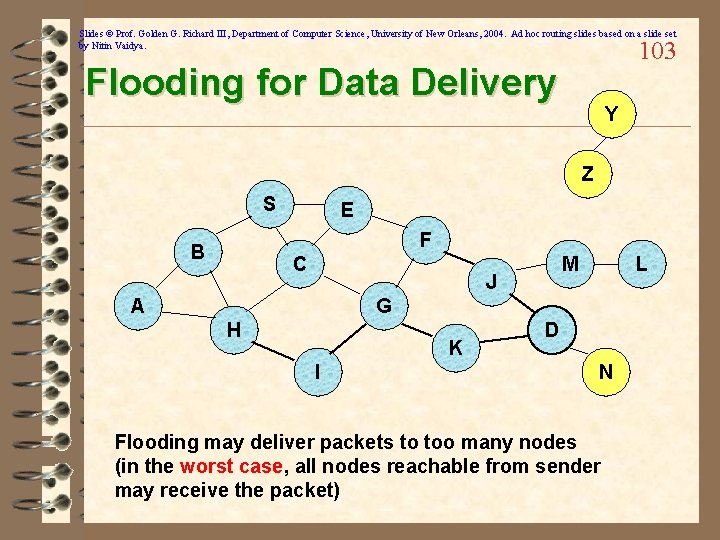
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Flooding for Data Delivery 95 ü Sender S broadcasts data packet P to all its neighbors ü Each node receiving P forwards P to its neighbors ü Sequence numbers used to avoid the possibility of forwarding the same packet more than once ü Packet P reaches destination D provided that D is reachable from sender S ü Node D does not forward the packet

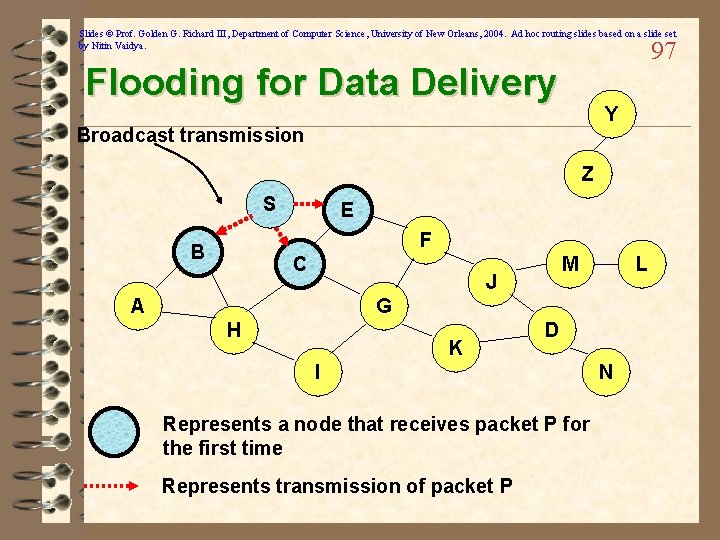
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 96 Flooding for Data Delivery Y Z S E F B C M J A L G H K I D N Represents a node that has received packet P Represents that connected nodes are within each other’s transmission range

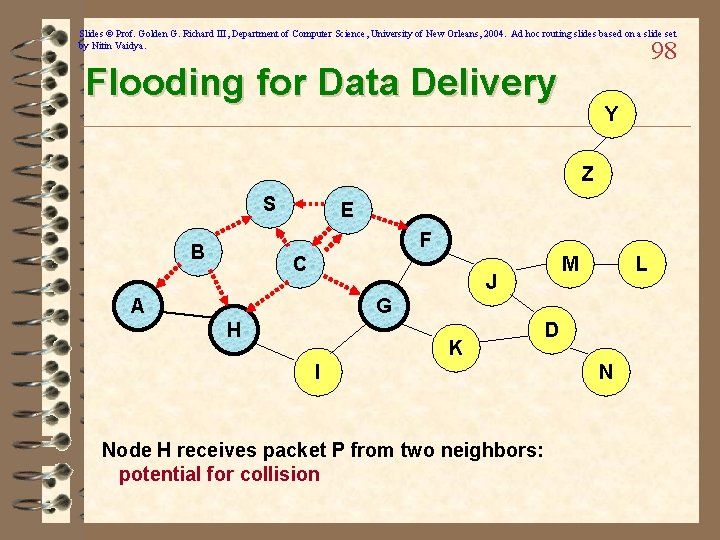
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 97 Flooding for Data Delivery Y Broadcast transmission Z S E F B C M J A L G H K D I Represents a node that receives packet P for the first time Represents transmission of packet P N

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 98 Flooding for Data Delivery Y Z S E F B C M J A L G H K I Node H receives packet P from two neighbors: potential for collision D N

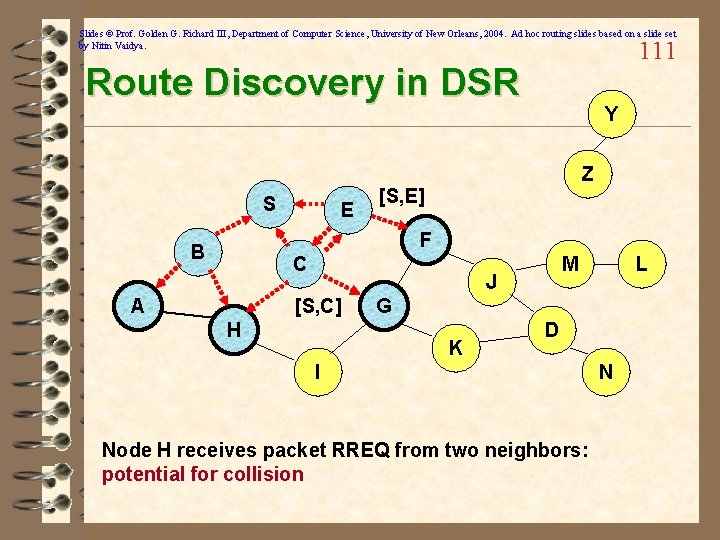
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 99 Flooding for Data Delivery Y Z S E F B C M J A L G H K I D N Node C receives packet P from G and H, but does not forward it again, because node C has already forwarded packet P once

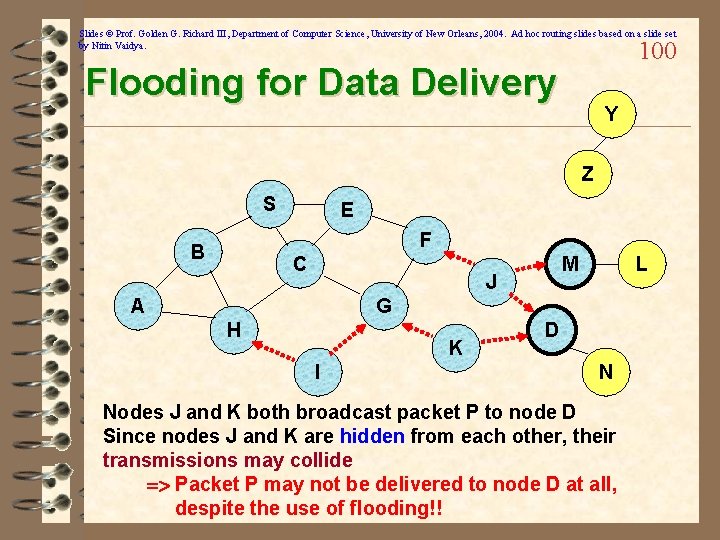
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 100 Flooding for Data Delivery Y Z S E F B C M J A L G H K I D N Nodes J and K both broadcast packet P to node D Since nodes J and K are hidden from each other, their transmissions may collide => Packet P may not be delivered to node D at all, despite the use of flooding!!

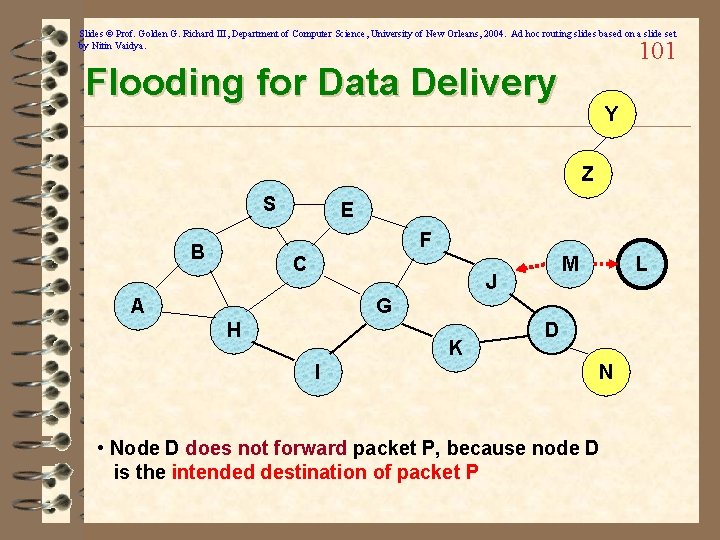
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 101 Flooding for Data Delivery Y Z S E F B C M J A L G H K I D N • Node D does not forward packet P, because node D is the intended destination of packet P

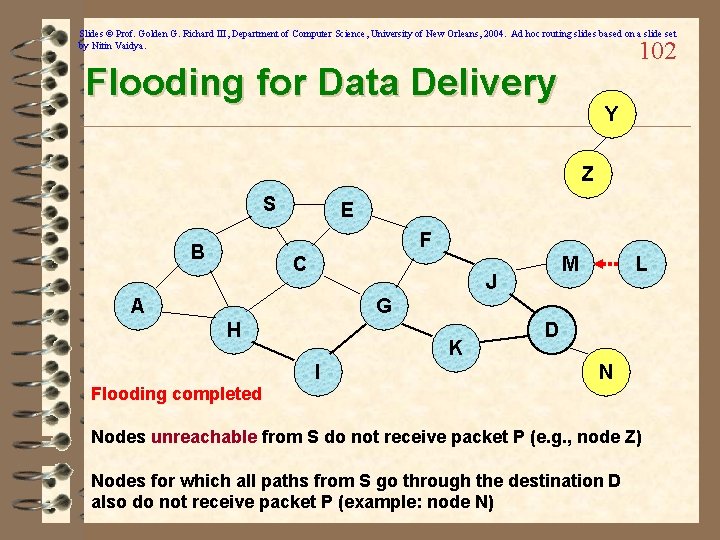
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 102 Flooding for Data Delivery Y Z S E F B C M J A L G H K I D N Flooding completed Nodes unreachable from S do not receive packet P (e. g. , node Z) Nodes for which all paths from S go through the destination D also do not receive packet P (example: node N)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 103 Flooding for Data Delivery Y Z S E F B C M J A L G H K I D N Flooding may deliver packets to too many nodes (in the worst case, all nodes reachable from sender may receive the packet)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 104 Flooding for Data Delivery: Advantages ü Simplicity ü May be more efficient than other protocols when rate of information transmission is low enough that the overhead of explicit route discovery/maintenance incurred by other protocols is relatively higher – this scenario may occur, for instance, when nodes transmit small data packets relatively infrequently, and many topology changes occur between consecutive packet transmissions ü Potentially higher reliability of data delivery – Because packets may be delivered to the destination on multiple paths ü For high mobility patterns, may be the only reasonable choice?

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 105 Flooding for Data Delivery: Disadvantages ü Potentially, very high overhead – Data packets may be delivered to too many nodes who do not need to receive them ü Potentially, lower reliability of data delivery – Flooding uses broadcasting -- hard to implement reliable broadcast delivery without significantly increasing overhead – Broadcasting in IEEE 802. 11 MAC is unreliable – In our example, nodes J and K may transmit to node D simultaneously, resulting in loss of the packet – in this case, destination would not receive the packet at all

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Flooding of Control Packets 106 ü Many protocols perform (potentially limited) flooding of control packets, instead of data packets ü The control packets are used to discover routes ü Discovered routes are subsequently used to send data packet(s) without flooding ü Overhead of control packet flooding is amortized over data packets transmitted between consecutive control packet floods

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Metrics for Ad Hoc Routing 107 ü Want to optimize something… – Number of hops – Distance – Latency – Load balancing for congested links – Cost ($$$) –… ü Many existing ad hoc routing descriptions use # of hops ü More work recently on latency, load balancing, etc.

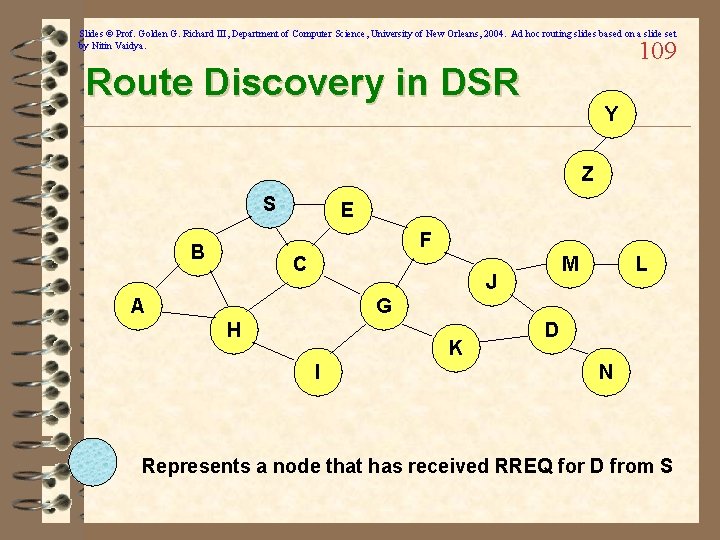
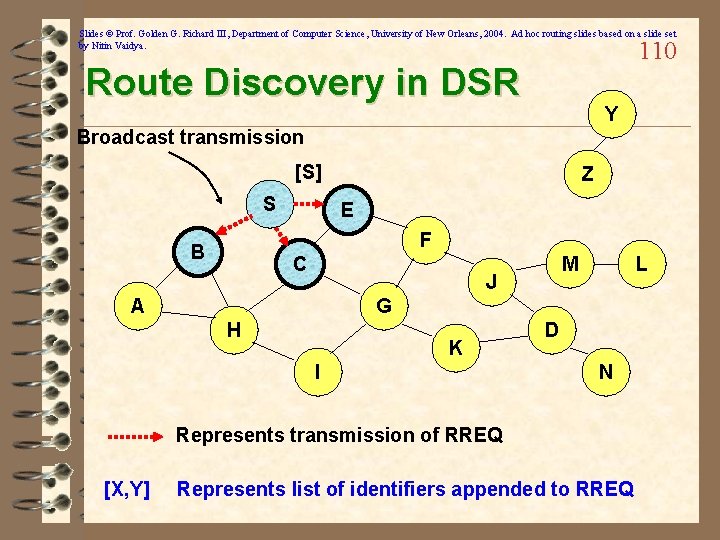
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 108 Dynamic Source Routing (DSR) ü When node S wants to send a packet to node D, but does not know a route to D, node S initiates a route discovery ü When node S sends a data packet to D, the entire route is included in the packet header – hence the name source routing ü Intermediate nodes use the source route included in a packet to determine to whom a packet should be forwarded ü Reactive: Routes are discovered only when a node wants to send data and route to destination is unavailable ü Source node S floods Route Request (RREQ) ü Each node appends own identifier when forwarding RREQ

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 109 Route Discovery in DSR Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 110 Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C M J A L G H K I D N Represents transmission of RREQ [X, Y] Represents list of identifiers appended to RREQ

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 111 Route Discovery in DSR S E Y Z [S, E] F B C A M J [S, C] H L G K D I Node H receives packet RREQ from two neighbors: potential for collision N

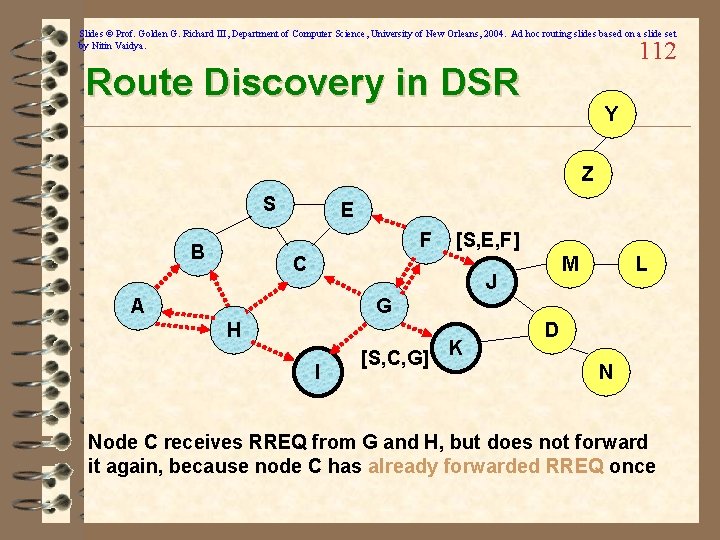
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 112 Route Discovery in DSR Y Z S E F B [S, E, F] C M J A L G H I [S, C, G] K D N Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once

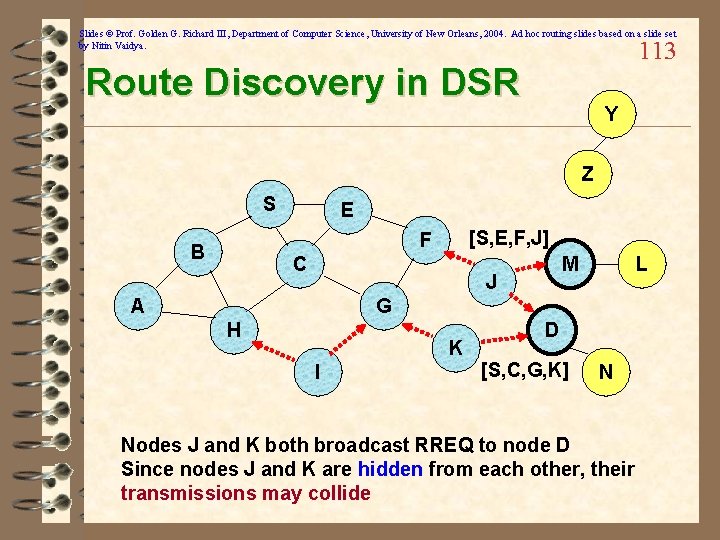
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 113 Route Discovery in DSR Y Z S E [S, E, F, J] F B C M J A L G H K I D [S, C, G, K] N Nodes J and K both broadcast RREQ to node D Since nodes J and K are hidden from each other, their transmissions may collide

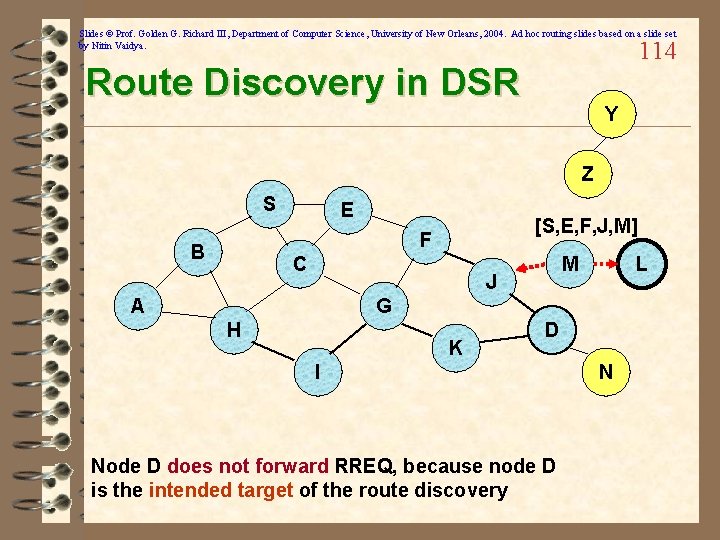
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 114 Route Discovery in DSR Y Z S E [S, E, F, J, M] F B C M J A L G H K D I Node D does not forward RREQ, because node D is the intended target of the route discovery N

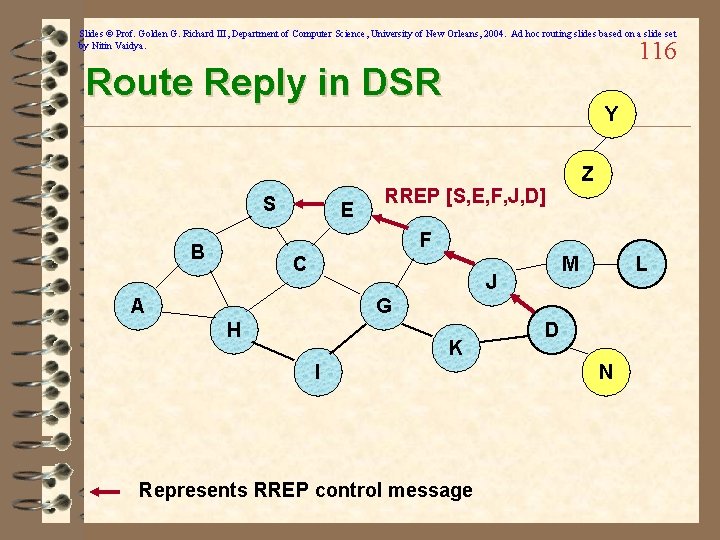
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 115 Route Discovery in DSR: Part 2 ü Destination D, on receiving the first RREQ, sends a Route Reply (RREP) ü RREP is sent on a route obtained by reversing the route appended to received RREQ ü RREP includes the route from S to D (and from D to S) on which RREQ was received by node D

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 116 Route Reply in DSR S E Y Z RREP [S, E, F, J, D] F B C M J A L G H K I Represents RREP control message D N

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Route Reply in DSR 117 ü Route Reply can be sent by reversing the route in Route Request (RREQ) only if links are guaranteed to be bi-directional – To ensure this, RREQ should be forwarded only if it received on a link that is known to be bi-directional ü If unidirectional (asymmetric) links are allowed, then RREP may need a route discovery for S from node D – Unless node D already knows a route to node S – If a route discovery is initiated by D for a route to S, then the Route Reply is piggybacked on the Route Request from D. ü Node S on receiving RREP, caches the route included in the RREP

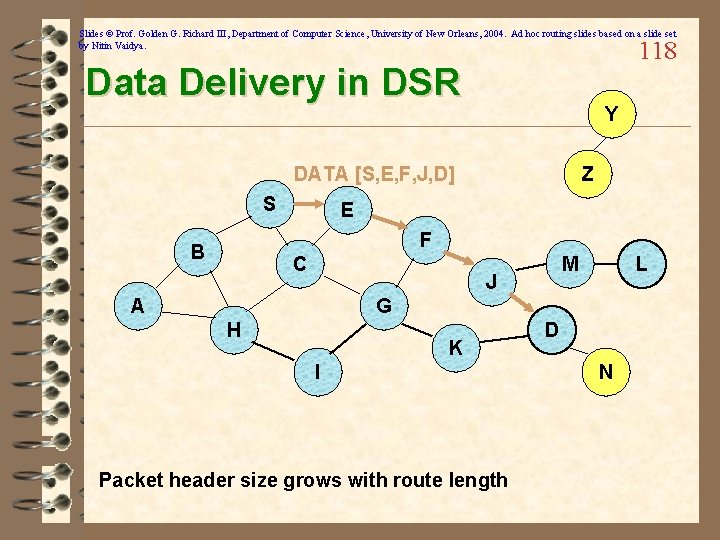
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 118 Data Delivery in DSR Y DATA [S, E, F, J, D] S Z E F B C M J A L G H K I Packet header size grows with route length D N

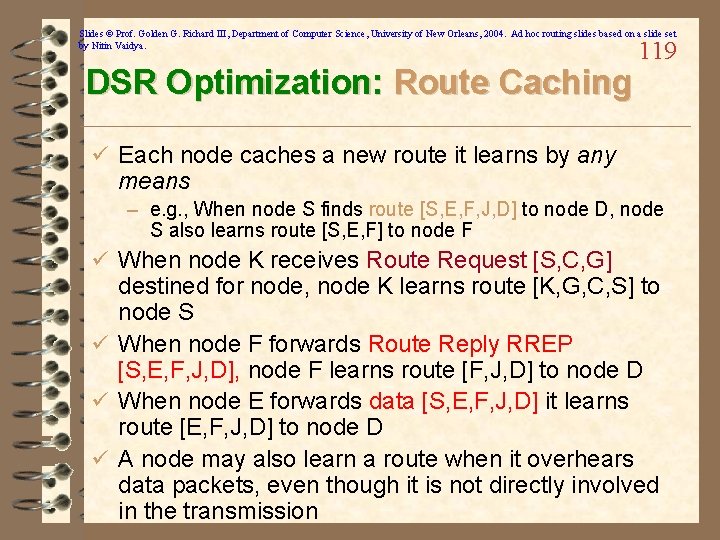
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. DSR Optimization: Route Caching 119 ü Each node caches a new route it learns by any means – e. g. , When node S finds route [S, E, F, J, D] to node D, node S also learns route [S, E, F] to node F ü When node K receives Route Request [S, C, G] destined for node, node K learns route [K, G, C, S] to node S ü When node F forwards Route Reply RREP [S, E, F, J, D], node F learns route [F, J, D] to node D ü When node E forwards data [S, E, F, J, D] it learns route [E, F, J, D] to node D ü A node may also learn a route when it overhears data packets, even though it is not directly involved in the transmission

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Route Caching (2) 120 ü When node S learns that a route to node D is broken, it uses another route from its local cache, if such a route to D exists in its cache. ü Otherwise, node S initiates route discovery by sending a route request ü Node X, on receiving a Route Request for some node D, can send a Route Reply directly if node X knows a route to node D ü Use of route cache – can speed up route discovery – can reduce propagation of route requests

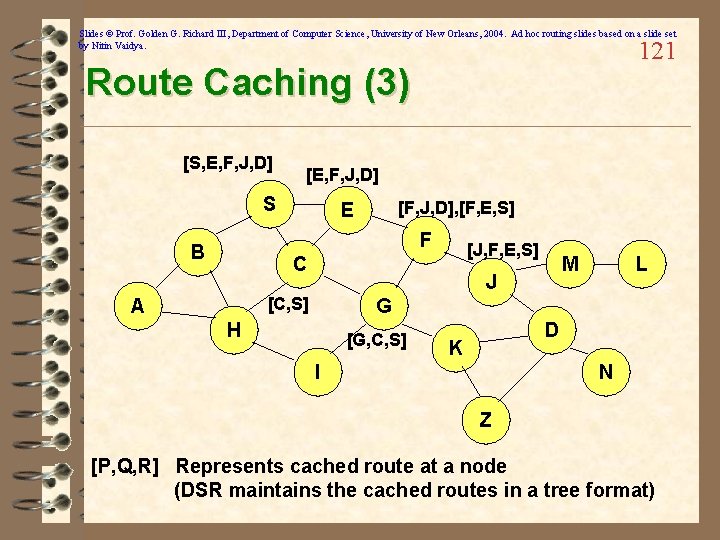
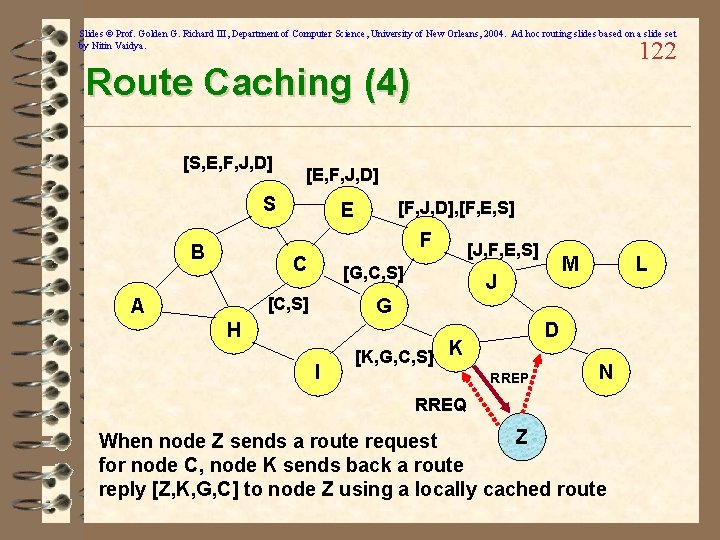
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 121 Route Caching (3) [S, E, F, J, D] [E, F, J, D] S [F, J, D], [F, E, S] E F B [J, F, E, S] C J [C, S] A M L G H [G, C, S] D K I N Z [P, Q, R] Represents cached route at a node (DSR maintains the cached routes in a tree format)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 122 Route Caching (4) [S, E, F, J, D] [E, F, J, D] S [F, J, D], [F, E, S] E F B C [G, C, S] [C, S] A [J, F, E, S] M J L G H I D [K, G, C, S] K RREP N RREQ Z When node Z sends a route request for node C, node K sends back a route reply [Z, K, G, C] to node Z using a locally cached route

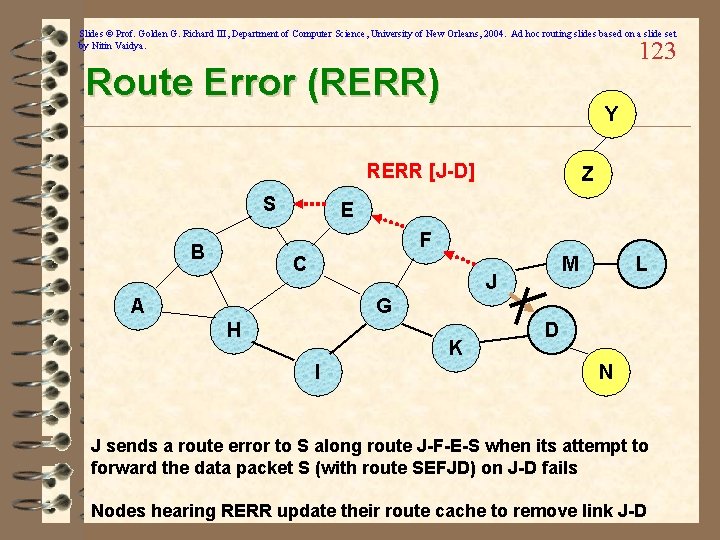
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 123 Route Error (RERR) Y RERR [J-D] S Z E F B C M J A L G H K I D N J sends a route error to S along route J-F-E-S when its attempt to forward the data packet S (with route SEFJD) on J-D fails Nodes hearing RERR update their route cache to remove link J-D

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Route Caching: Beware! 124 ü Stale caches can adversely affect performance ü With passage of time and host mobility, cached routes may become invalid ü A sender host may try several stale routes (obtained from local cache, or replied from cache by other nodes), before finding a good route ü It may be more expensive to try several broken routes than to simply discover a new one!! ü RERR messages are unreliable, so news of broken routes may not even propagate completely!

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. DSR: Advantages 125 ü Routes maintained only between nodes who need to communicate – reduces overhead of route maintenance ü Route caching can further reduce route discovery overhead ü A single route discovery may yield many routes to the destination, due to intermediate nodes replying from local caches

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. DSR: Disadvantages 126 ü Packet header size grows with route length due to source routing ü Flood of route requests may potentially reach all nodes in the network ü Care must be taken to avoid collisions between route requests propagated by neighboring nodes – insertion of random delays before forwarding RREQ ü Increased contention if too many route replies come back due to nodes replying using their local cache – Route Reply Storm problem – Reply storm may be eased by preventing a node from sending RREP if it hears another RREP with a shorter route

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. DSR: Disadvantages (2) 127 ü An intermediate node may send Route Reply using a stale cached route, thus polluting other caches ü This problem can be eased if some mechanism to purge (potentially) invalid cached routes is incorporated. – Static timeouts – Adaptive timeouts based on expected rate of mobility… – …e. g. , number of changes to routing table, or number of routes that get expired – Abdul Altalhi’s algorithm uses the latter

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 128 DSR w/ Implicit Source Routing ü Enhancement to make transmission of data packets cheaper ü Don’t send entire source route with data packet ü Instead, establish a numbered “flow” between source and destination ü Flow identifier is attached to data packets instead of route

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 129 Details of Implicit Source Routing (1) ü Replace source route on each data packet with the following tuple: – <source address, destination address, flow. ID> ü Source address and destination address can actually be obtained from IP header ü Each node maintains a flow table that identifies current flows ü Flows are established with a flow establishment packet – Contains source route + unique flow ID + timeout

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 130 Details of Implicit Source Routing (2) ü In addition to forwarding flow packet toward the destination, a forwarding node makes an entry in its flow table ü Entry will be removed from the flow table if a packet doesn’t traverse the flow for duration timeout ü Subsequent data packets, after initial flow establishment, contain only the tuple previously described

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 131 Details of Implicit Source Routing (3) ü If a node receives a tuple <source address, destination address, flow. ID> and does not understand the flow. ID, then a FLOW UNKNOWN error is transmitted toward the sender ü Upon receiving FLOW UNKNOWN, sender must reestablish the flow ü Paper assumes three duplicate flow establishment packets are sent ü Redundancy increases likelihood that at least one flow establishment will be received at each node in the source route

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Default Flows ü Can use most recent flow for each <source, ü ü ü 132 destination> as default Transmit no additional info on data packets Nodes on path between source and destination examine TTL of packet to see if they should forward If source, destination, TTL match most recent flow, forward as if flow ID were present Problem (? ): DEFAULT FLOW UNKNOWNs sent by nodes new to the area which are not on the route between source and destination? Or sent only if they are on the path between source and destination?

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. DSR/ISR Route Shortening 133 ü Illustration: – S A B C D is source route – C overhears packet when S transmits – C sends gratuitous ROUTE REPLY to S, containing S C D to replace old route ü With implicit source routing: – Associate a hop count with each flow table entry – Hearing a packet with a hop count less than expected means gratuitous ROUTE REPLY should be sent

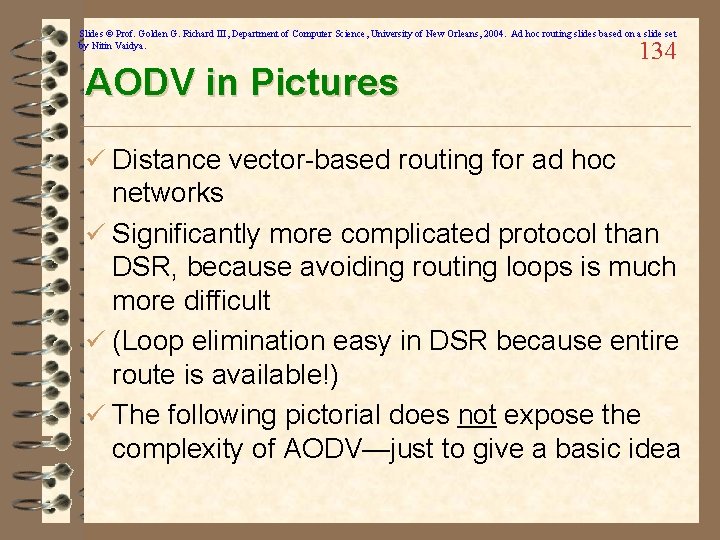
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. AODV in Pictures 134 ü Distance vector-based routing for ad hoc networks ü Significantly more complicated protocol than DSR, because avoiding routing loops is much more difficult ü (Loop elimination easy in DSR because entire route is available!) ü The following pictorial does not expose the complexity of AODV—just to give a basic idea

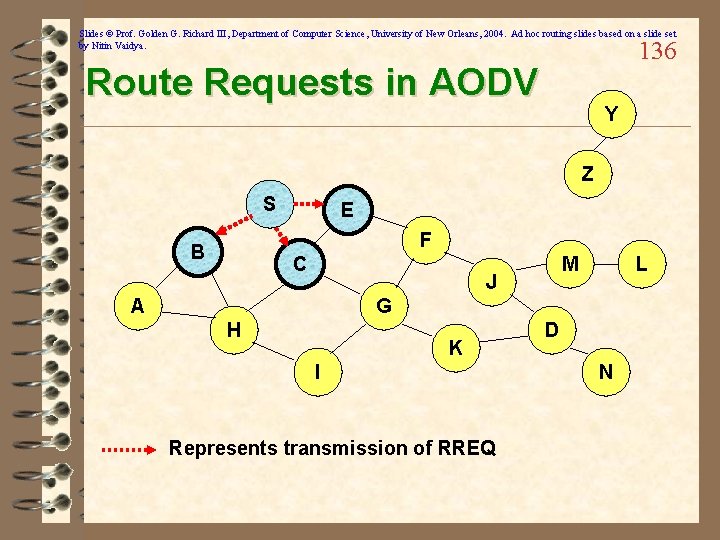
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 135 Route Requests in AODV Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S

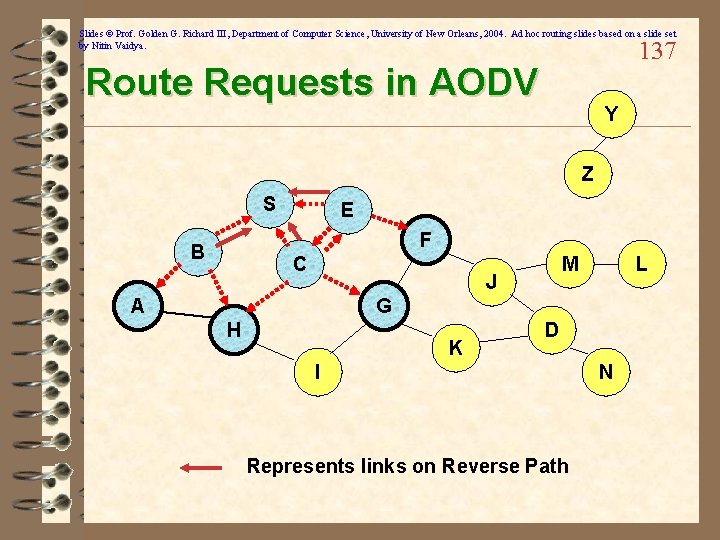
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 136 Route Requests in AODV Y Z S E F B C M J A L G H K I Represents transmission of RREQ D N

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 137 Route Requests in AODV Y Z S E F B C M J A L G H K D I Represents links on Reverse Path N

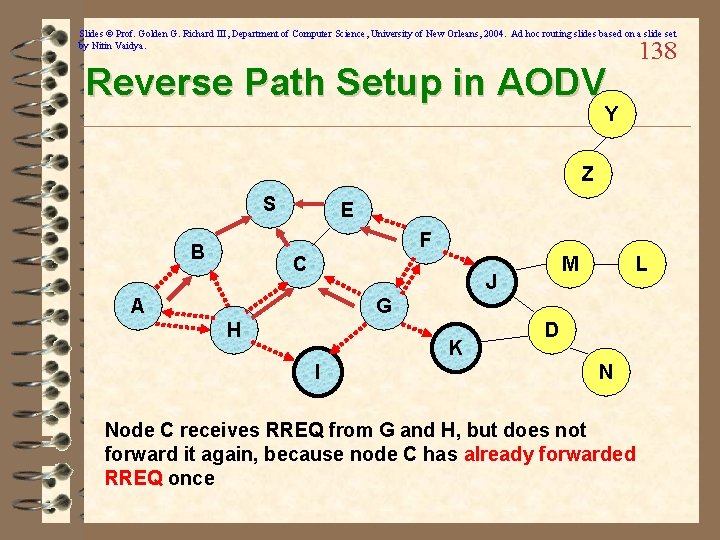
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Reverse Path Setup in AODV 138 Y Z S E F B C M J A L G H K I D N Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once

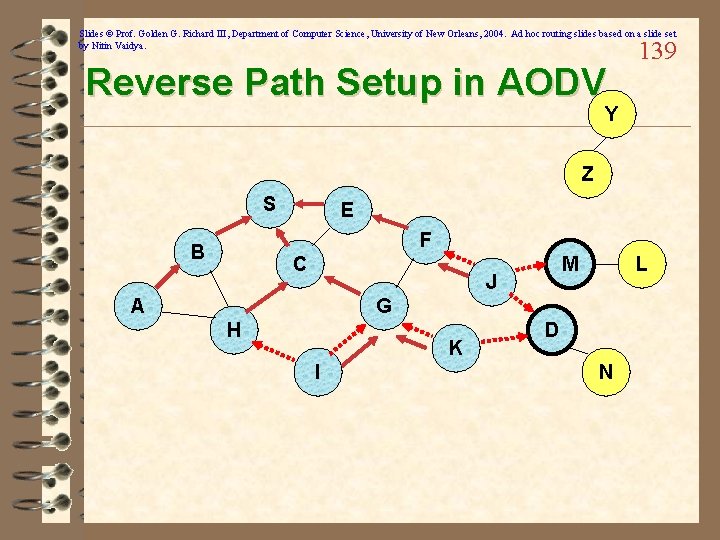
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Reverse Path Setup in AODV 139 Y Z S E F B C M J A L G H K I D N

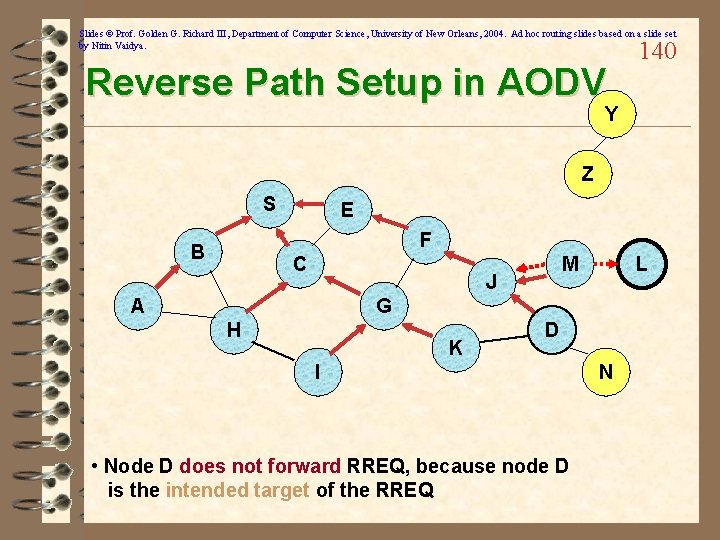
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Reverse Path Setup in AODV 140 Y Z S E F B C M J A L G H K D I • Node D does not forward RREQ, because node D is the intended target of the RREQ N

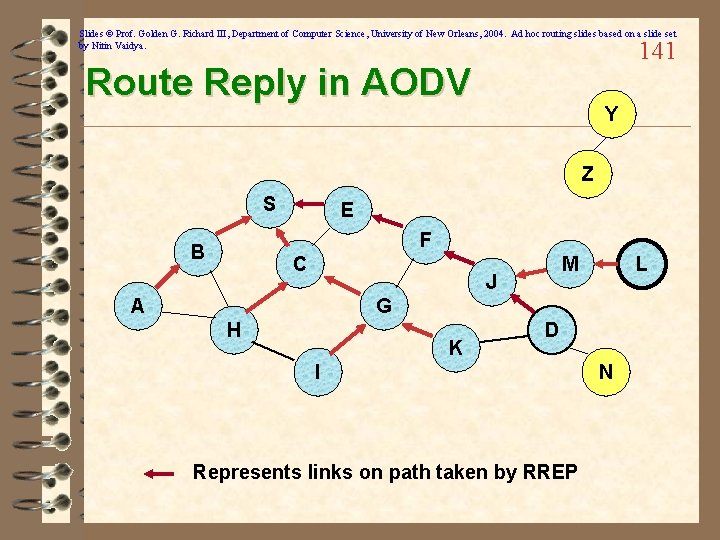
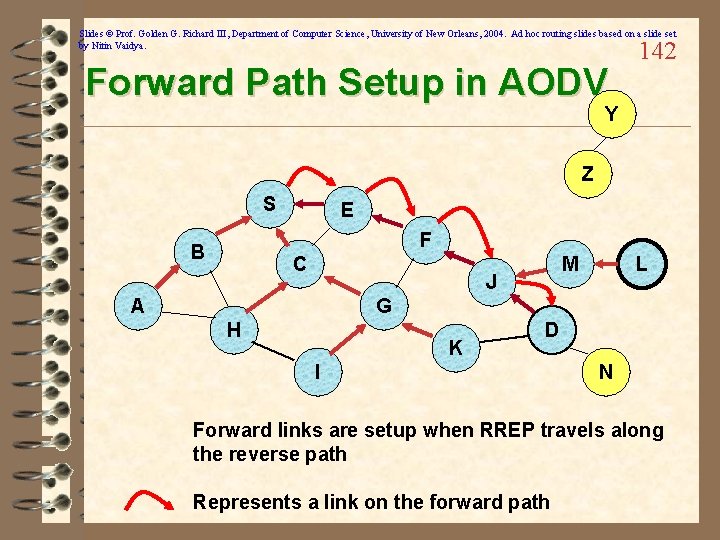
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 141 Route Reply in AODV Y Z S E F B C M J A L G H K D I Represents links on path taken by RREP N

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Forward Path Setup in AODV 142 Y Z S E F B C M J A L G H K D I N Forward links are setup when RREP travels along the reverse path Represents a link on the forward path

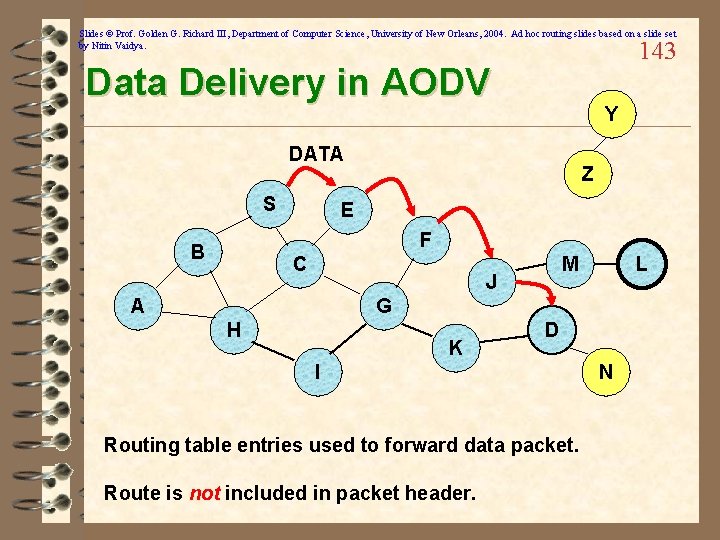
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 143 Data Delivery in AODV Y DATA S Z E F B C M J A L G H K D I Routing table entries used to forward data packet. Route is not included in packet header. N

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Geocasting 144 ü Geocast group is defined as the set of nodes that reside in a specified geographical region ü Unlike multicast, where nodes explicitly join and leave a group, membership in a geocast group is a function of “standing in the right place” ü Geocasts are useful to deliver location-dependent information – Only the people standing or walking near a building – “Attack!!” for units in a particular region ü “Geocast region” defines delivery area

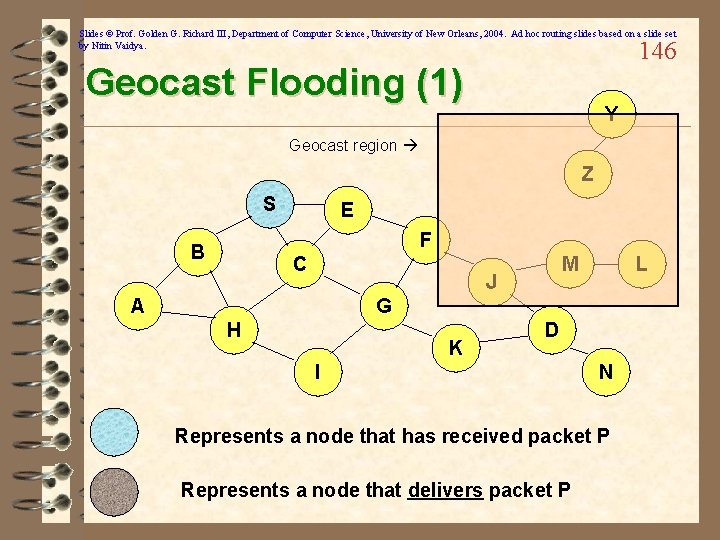
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Geocasting by Flooding 145 ü Use the basic flooding algorithm, where a packet sent ü ü by a geocast sender is flooded to all reachable nodes in the network The geocast region is tagged onto the geocast message Regions are generally circular or rectangular, but can (in theory) be any shape When a node receives a geocast packet by the basic flooding protocol, the packet is delivered to the application only if the node’s location is within the geocast region GPS (or similar) is used to know location

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 146 Geocast Flooding (1) Y Geocast region Z S E F B C M J A L G H K D I N Represents a node that has received packet P Represents a node that delivers packet P

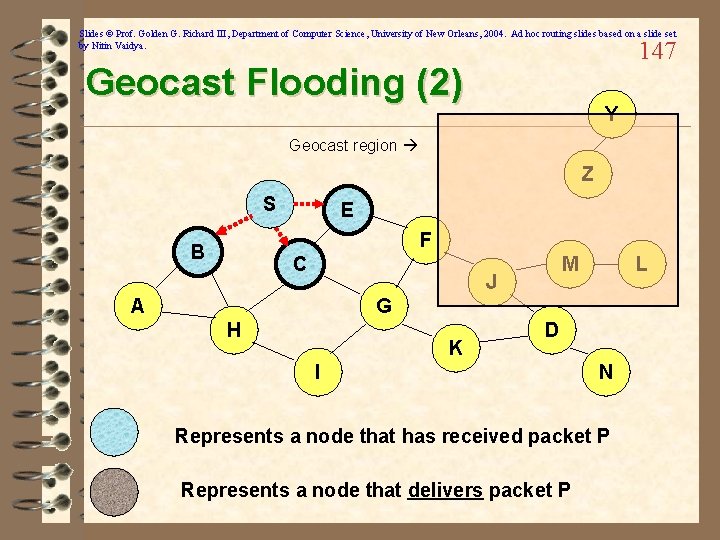
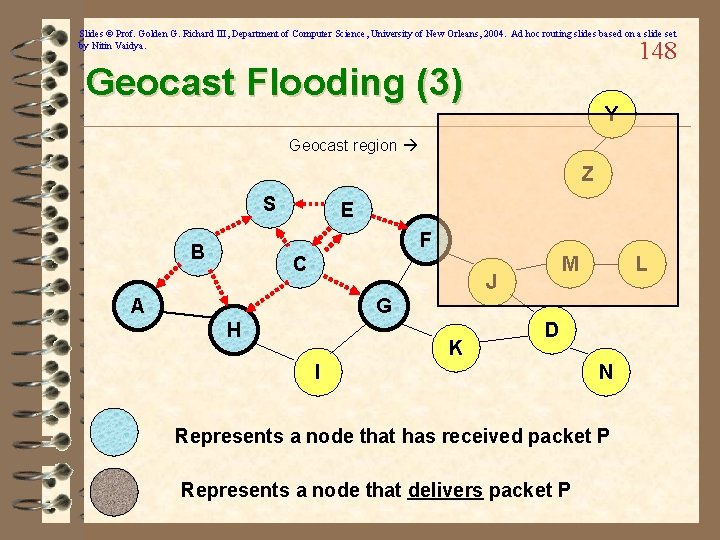
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 147 Geocast Flooding (2) Y Geocast region Z S E F B C M J A L G H K D I N Represents a node that has received packet P Represents a node that delivers packet P

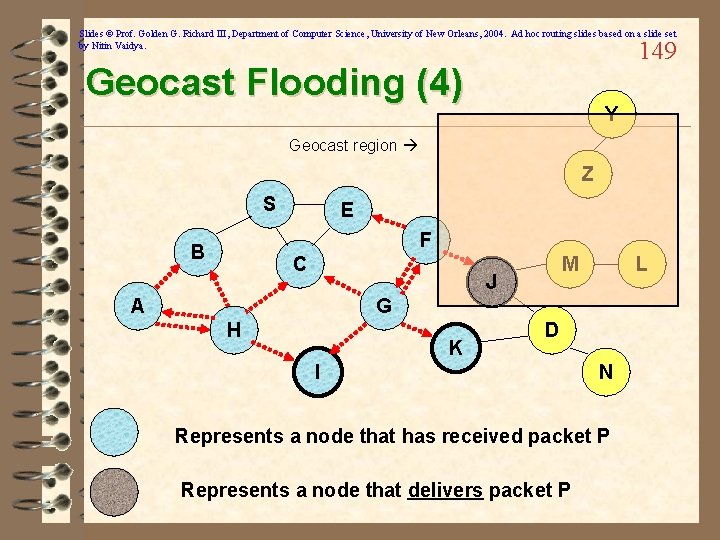
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 148 Geocast Flooding (3) Y Geocast region Z S E F B C M J A L G H K D I N Represents a node that has received packet P Represents a node that delivers packet P

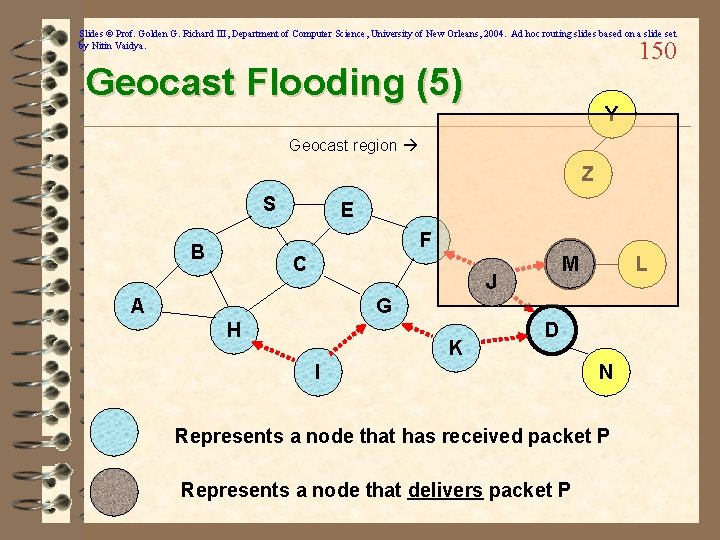
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 149 Geocast Flooding (4) Y Geocast region Z S E F B C M J A L G H K D I N Represents a node that has received packet P Represents a node that delivers packet P

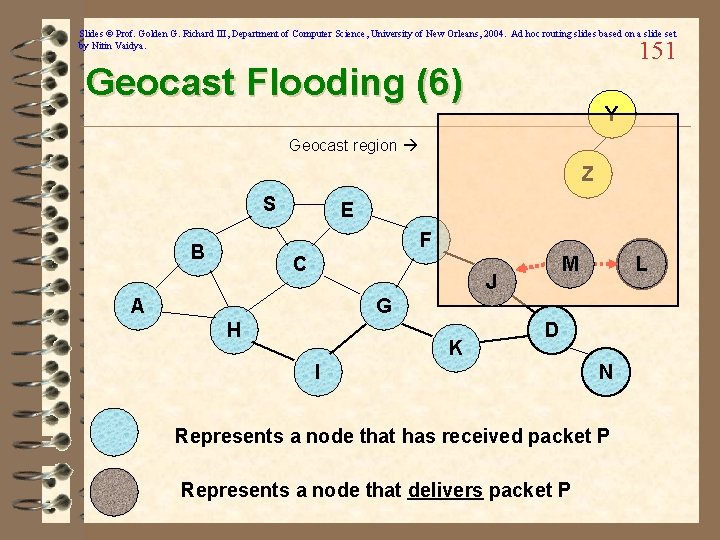
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 150 Geocast Flooding (5) Y Geocast region Z S E F B C M J A L G H K D I N Represents a node that has received packet P Represents a node that delivers packet P

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 151 Geocast Flooding (6) Y Geocast region Z S E F B C M J A L G H K D I N Represents a node that has received packet P Represents a node that delivers packet P

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Geocast Flooding: Evaluation 152 ü Advantages: – Usual advantages of flooding – Simple – About as accurate as possible—really gives each node a chance to receive/not receive based on location ü Disadvantages – Usual disadvantages of flooding – High overhead • Nodes must process messages they aren’t interested in • Potential network congestion – Packet reaches all nodes reachable from the source, even nodes far from geocast region

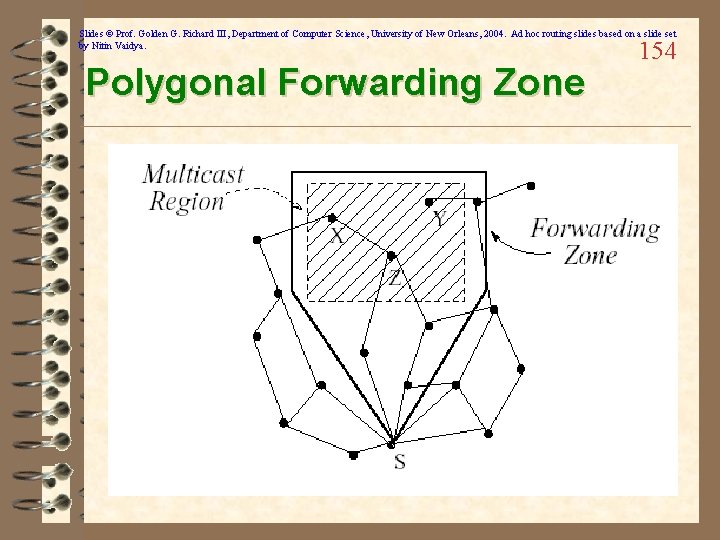
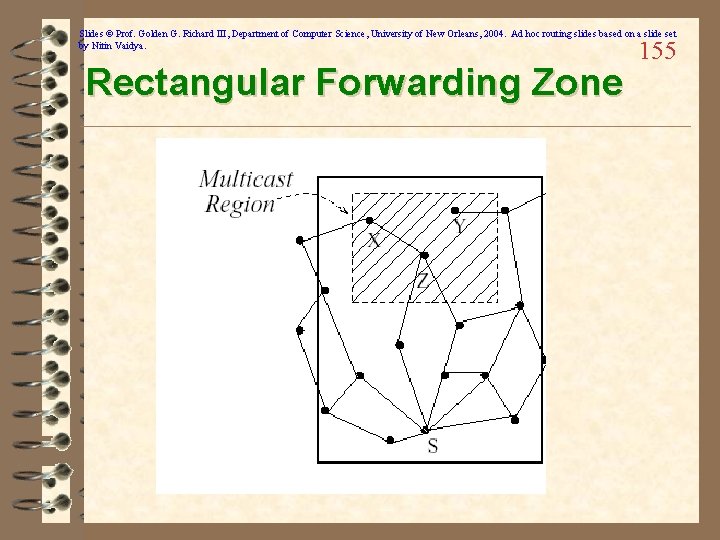
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Optimization for Geocast Flooding 153 ü “Geocasting in Mobile Ad Hoc Networks: Location-Based Multicast Algorithms” (Ko/Vaidya) ü Uses a forwarding zone to reduce flooding ü Only nodes in forwarding zone continue the flooding operation ü Nodes outside the multicast region must be included in the forwarding zone if the source of the geocast isn’t in the multicast region…

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Polygonal Forwarding Zone 154

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Rectangular Forwarding Zone 155

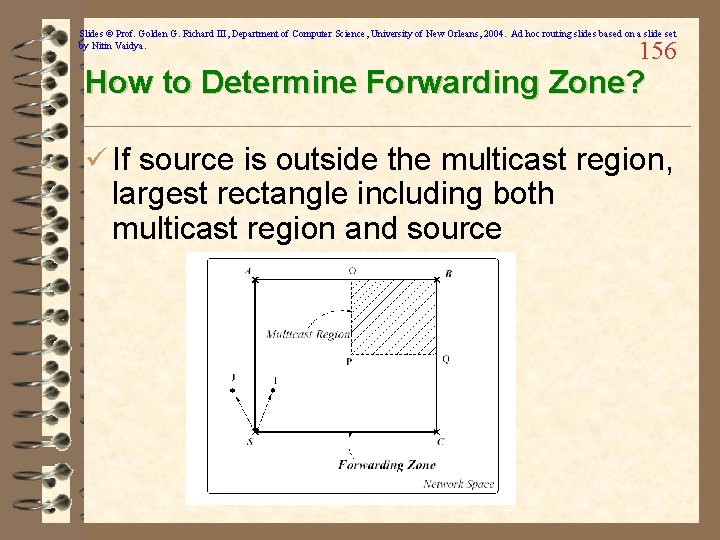
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 156 How to Determine Forwarding Zone? ü If source is outside the multicast region, largest rectangle including both multicast region and source

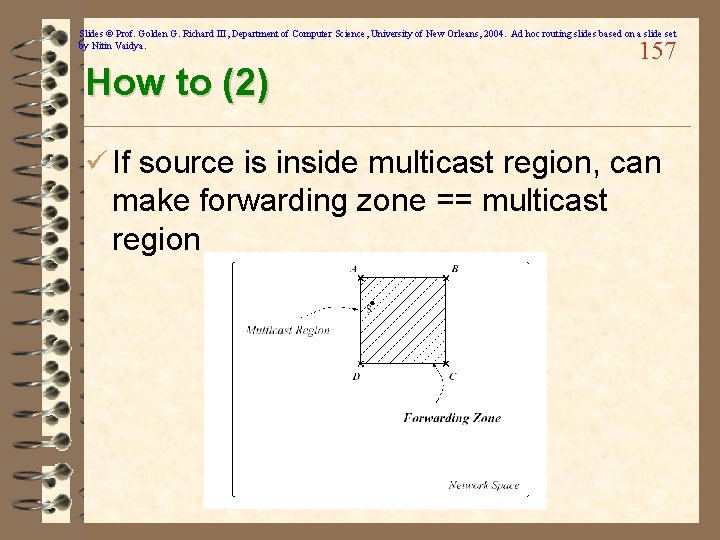
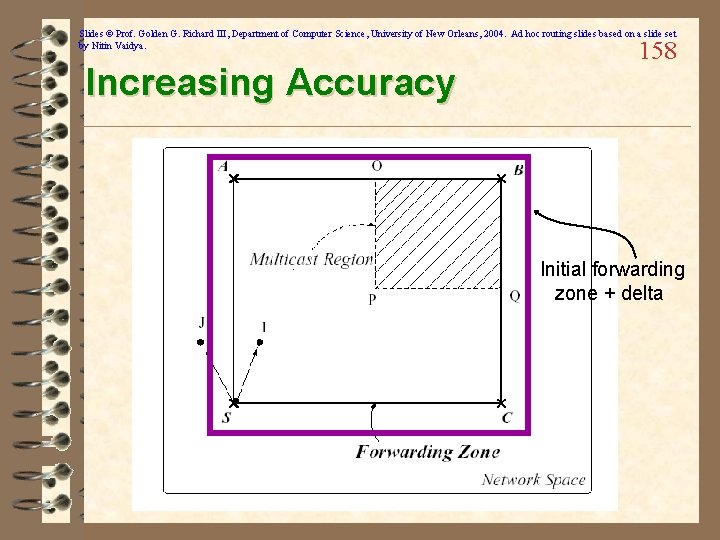
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. How to (2) 157 ü If source is inside multicast region, can make forwarding zone == multicast region

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Increasing Accuracy 158 Initial forwarding zone + delta

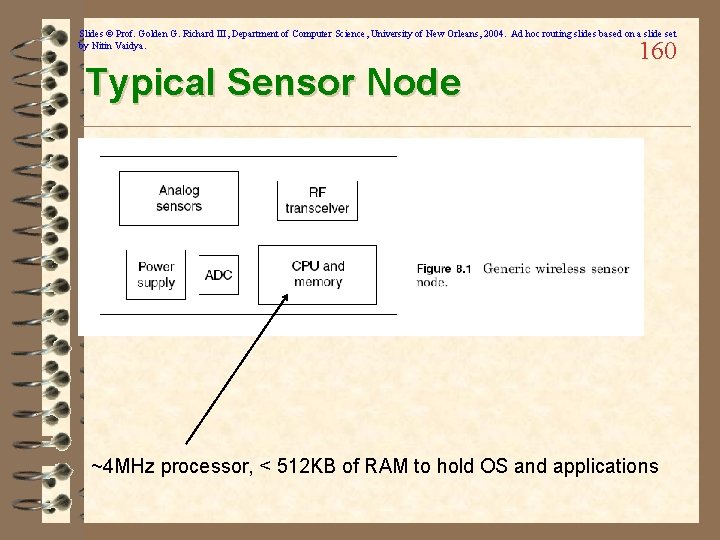
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Sensor Networks 159 ü Special case of the general ad hoc networking problem ü Much more resource constrained than network of PDAs or laptops ü Generally, special-purpose ü May have special restrictions, such as: – Re-deployment, movement impossible – Recharge impossible – Likelihood of many nodes being destroyed

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Typical Sensor Node 160 ~4 MHz processor, < 512 KB of RAM to hold OS and applications

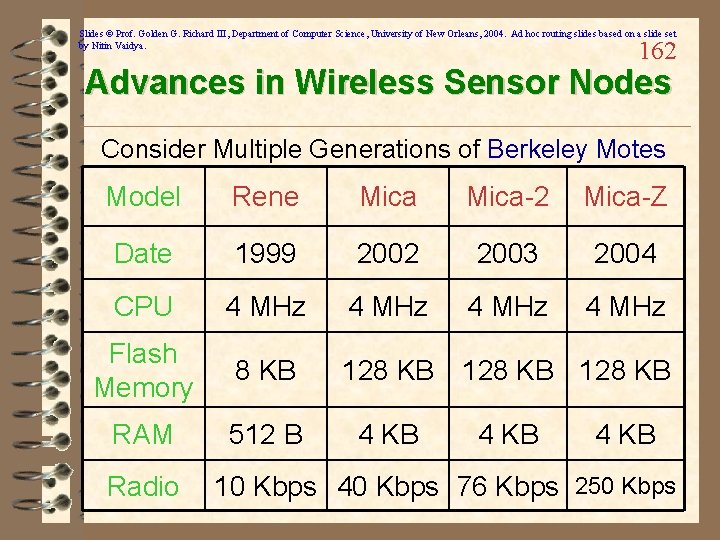
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Typical Sensor Node Features ü A sensor node has: – Sensing Material • Physical – Magnetic, Light, Sound • Chemical – CO, Chemical Weapons • Biological – Bacteria, Viruses, Proteins – Integrated Circuitry (VLSI) • A-to-D converter from sensor to circuitry – Packaging for environmental safety – Power Supply • Passive – Solar, Vibration • Active – Battery power, RF Inductance 161

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 162 Advances in Wireless Sensor Nodes Consider Multiple Generations of Berkeley Motes Model Rene Mica-2 Mica-Z Date 1999 2002 2003 2004 CPU 4 MHz Flash Memory 8 KB 128 KB RAM 512 B 4 KB Radio 4 KB 10 Kbps 40 Kbps 76 Kbps 250 Kbps

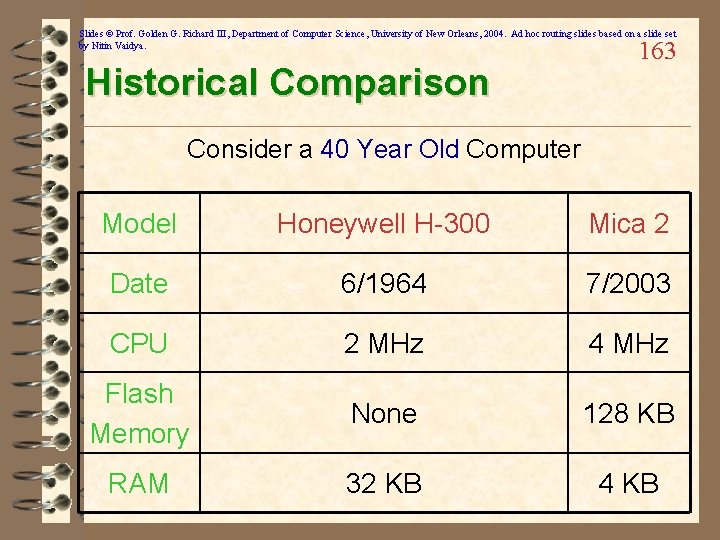
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Historical Comparison 163 Consider a 40 Year Old Computer Model Honeywell H-300 Mica 2 Date 6/1964 7/2003 CPU 2 MHz 4 MHz Flash Memory None 128 KB RAM 32 KB 4 KB

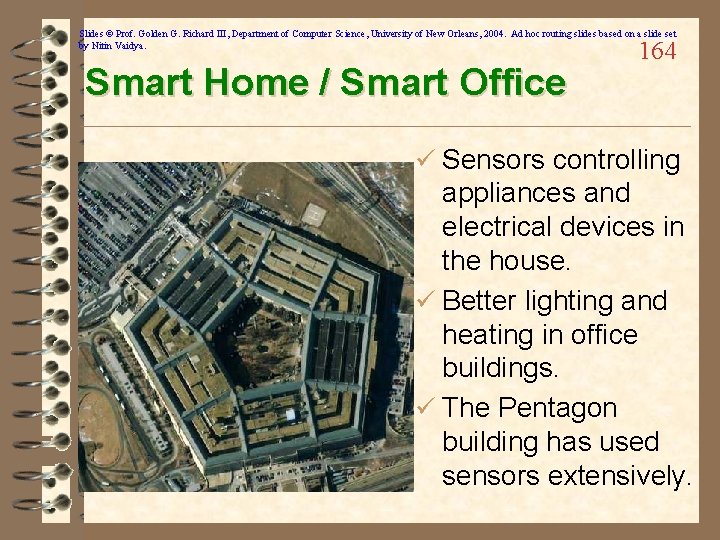
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Smart Home / Smart Office 164 ü Sensors controlling appliances and electrical devices in the house. ü Better lighting and heating in office buildings. ü The Pentagon building has used sensors extensively.

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Biomedical / Medical ü Health Monitors – Glucose – Heart rate – Cancer detection ü Chronic Diseases – Artificial retina – Cochlear implants ü Hospital Sensors – Monitor vital signs – Record anomalies 165

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Military 166 Remote deployment of sensors for tactical monitoring of enemy troop movements.

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Industrial & Commercial 167 ü Numerous industrial and commercial applications: – Agricultural Crop Conditions – Inventory Tracking – In-Process Parts Tracking – Automated Problem Reporting – RFID – Theft Deterrent and Customer Tracing – Plant Equipment Maintenance Monitoring

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 168 Traffic Management & Monitoring ü Future cars could use wireless sensors to: – Handle Accidents – Handle Thefts üSensors embedded in the roads to: –Monitor traffic flows –Provide real-time route updates

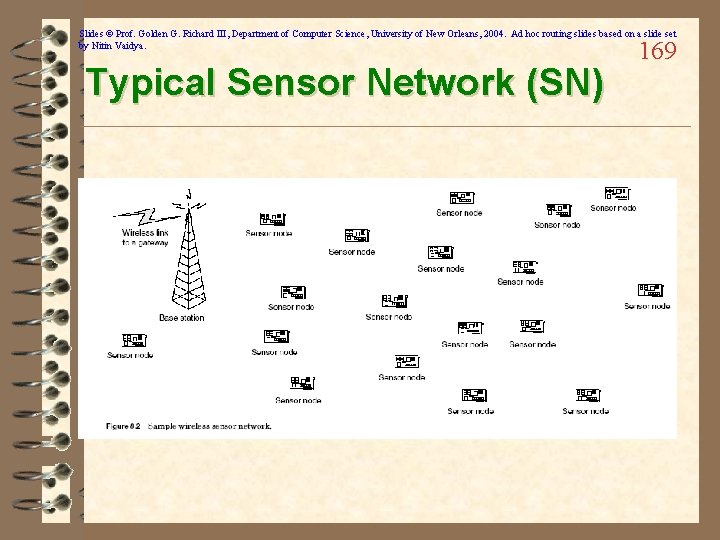
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Typical Sensor Network (SN) 169

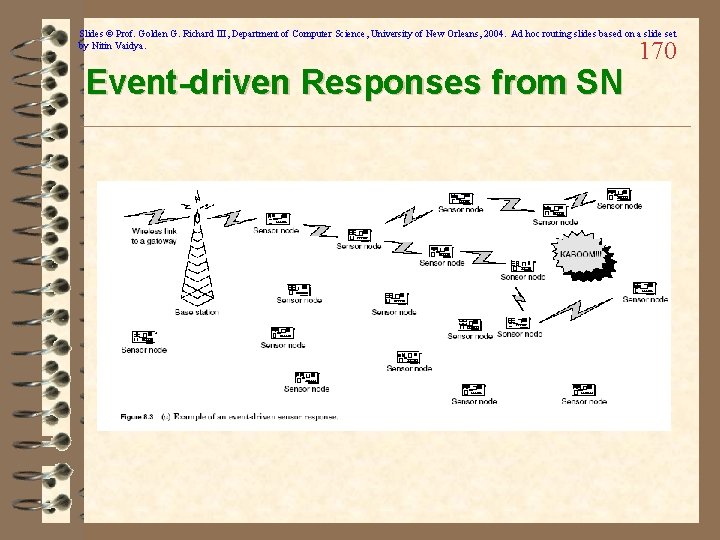
Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Event-driven Responses from SN 170

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Periodic Responses from SN 171

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 172 Sensor Networks: More Issues ü Neighbor discovery ü Self configuration ü Sensing, sensor data processing ü Data aggregation, storage, and caching ü Target detection, target tracking, and target monitoring ü Topology control for energy savings, localization ü Time synchronization ü Routing ü Medium access control

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Some Issues, e. g. , Noisy Sensors 173 Sensor readings can be inaccurate. Protocols need to recognize this. GPS Sensor Accurate within 2. 8 meters Relative Humidity Sensor Accuracy of ± 5% ± 8% at 90% Relative Humidity ± 2% with calibration

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Wireless Channel Conditions ü Limitations of wireless channels – Noisy – Interference – Link Contention – Unidirectional Links ü But inherently a broadcast medium 174

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Environmental Factors 175 ü Wireless sensors need to operate in conditions that are not encountered by typical computing devices: – Rain, sleet, snow, hail, etc. – Wide temperature variations • May require separating sensor from electronics – High humidity – Saline or other corrosive substances – High wind speeds

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Autoconfiguration 176 ü Autoconfiguration protocols allow sensor nodes to adapt automatically to their environment ü When nodes die or are replaced, manual configuration could be extremely tedious ü Naming… – Generation of unique names ü Location determination – Direct use of GPS – Probes to other GPS-equipped sensor nodes ü Discovery of nearby nodes… – e. g. , Probe/ACK ü Service discovery… – Need lighter-weight protocols than we examined earlier – Currently, an area for research

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Need a Standardized Interface 177 ü Automated interaction between sensors implies some standard mechanism for communication! – Requires compatible wireless technology – Standardization a common theme • TCP/IP for the Internet • Java for Internet programming • Jini, SLP, etc. for 802. 11 wireless devices ü Need a service discovery protocol – Enables standard interface among sensors

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Security Issues 178 ü Concerns about misuse and privacy – Privacy issues may slow consumer adoption of technology • User tracking – RFID concerns • Has not proved true on the Internet! – Authentication and privacy are not always complementary objectives – Do not want your medical sensor hacked!! – Data tampering and computer viruses could be a nightmare!

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Clustering to Save Resources 179

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 180 Aggregation/Duplicate Suppression ü Another attempt to save resources ü Sensor nodes whose values match those of other sensor nodes, on forwarding messages, can simply annotate the message ü Or just remain silent, on overhearing identical (or “similar enough”) values

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Sensor Deployment 181 ü Manual ü Random (e. g. , scattering) ü Automatic movement to better locations

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Mobile Sensors 182 Sensors with Micromachines Low-Power Motors that Support Mobility

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 183 Asking a Sensor Network a Question ü Can have sensor nodes periodically transmit sensor readings ü More likely: Ask the sensor network a question and receive an answer ü Issue: Getting the request out to the nodes ü Issue: Getting responses back from sensor nodes who have answers ü Directed Diffusion Routing ü Geographic Forwarding (related to geocasting)

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Asking the Question 184

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 185 Response to Base Station: Initial

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Responses, After Some Guidance 186 Neighboring nodes, upon receiving duplicate messages, can provide some Guidance to allow responses to be more efficiently delivered in the future…

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. Geographic Forwarding 187

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 188 Accuracy: Searching for Agreement

Slides © Prof. Golden G. Richard III, Department of Computer Science, University of New Orleans, 2004. Ad hoc routing slides based on a slide set by Nitin Vaidya. 189 Searching for Agreement: Clusters