Context Aware Operation Reproduction for Safety Driving Satoshi





- Slides: 17

Context Aware Operation Reproduction for Safety Driving Satoshi Kaede Ritsumeikan University Graduate School of Computer Science Date Engineering Laboratory Japan E-mail kaede@de. is. ritsumei. ac. jp © 2005 Ritsumeikan Univ. All Rights Reserved.

Contents 1. Goal of Our Research 2. Describing Model of a Context 3. Verification of the Model 4. Conclusion and Future works © 2005 Ritsumeikan Univ. All Rights Reserved.

Goal of Our Research n We propose a method to reproduce operations from contexts of the driver and someone on a vehicle. Set a Steering Lock ! Get Your Valuables ! © 2005 Ritsumeikan Univ. All Rights Reserved.

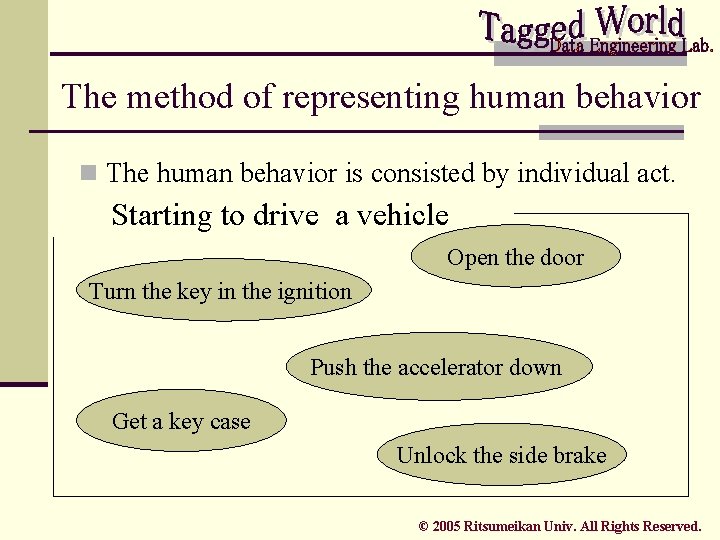
The method of representing human behavior n The human behavior is consisted by individual act. Starting to drive a vehicle Open the door Turn the key in the ignition Push the accelerator down Get a key case Unlock the side brake © 2005 Ritsumeikan Univ. All Rights Reserved.

Bayesian Network n The Bayesian Network n It models dependency relation using probability networks. n The structure of the Network is Directed Acyclic Graph. © 2005 Ritsumeikan Univ. All Rights Reserved.

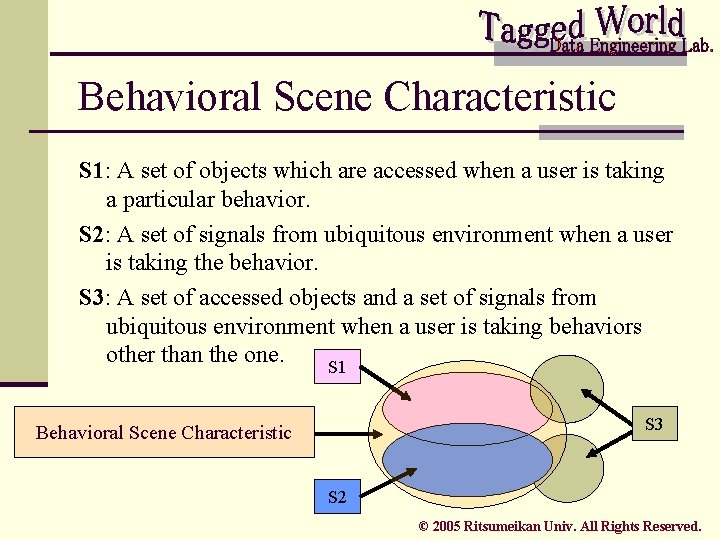
Behavioral Scene Characteristic S 1: A set of objects which are accessed when a user is taking a particular behavior. S 2: A set of signals from ubiquitous environment when a user is taking the behavior. S 3: A set of accessed objects and a set of signals from ubiquitous environment when a user is taking behaviors other than the one. S 1 S 3 Behavioral Scene Characteristic S 2 © 2005 Ritsumeikan Univ. All Rights Reserved.

Bayesian Network n The Bayesian Network n It models dependency relation using probability networks. n The structure of the Network is Directed Acyclic Graph. n K 2 Algorithm n It automatically configures Bayesian Network by statistical data. n It creates a dual directional arrow which represents dependency relationship between nodes. n The allow interferes with configuration of DAG. © 2005 Ritsumeikan Univ. All Rights Reserved.

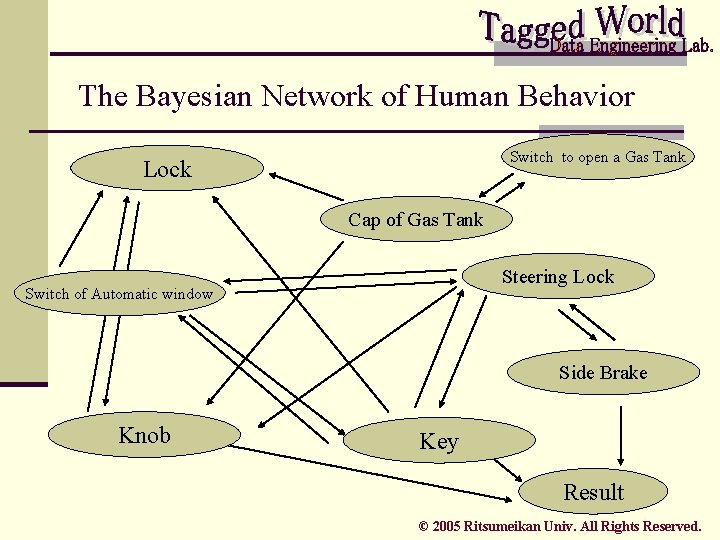
The Bayesian Network of Human Behavior Switch to open a Gas Tank Lock Cap of Gas Tank Steering Lock Switch of Automatic window Side Brake Knob Key Result © 2005 Ritsumeikan Univ. All Rights Reserved.

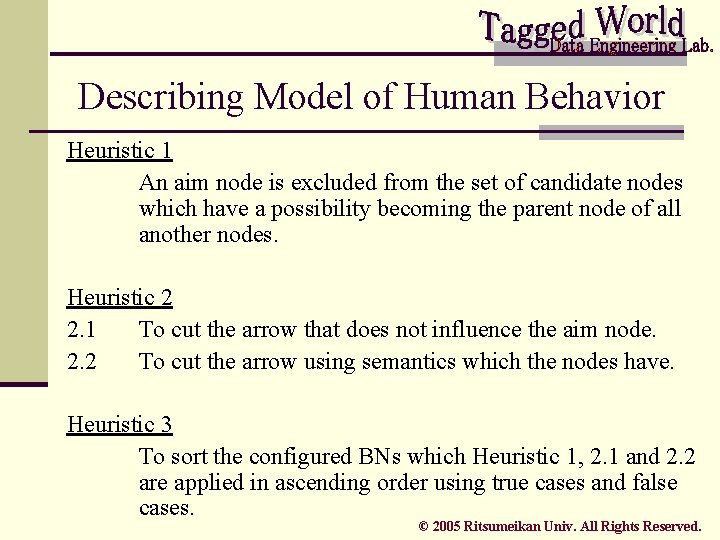
Heuristics Heuristic 1 An aim node is excluded from the set of candidate nodes which have a possibility becoming the parent node of all another nodes. Heuristic 2 2. 1 To cut the arrow that does not influence the aim node. 2. 2 To cut the arrow using semantics which the nodes have. © 2005 Ritsumeikan Univ. All Rights Reserved.

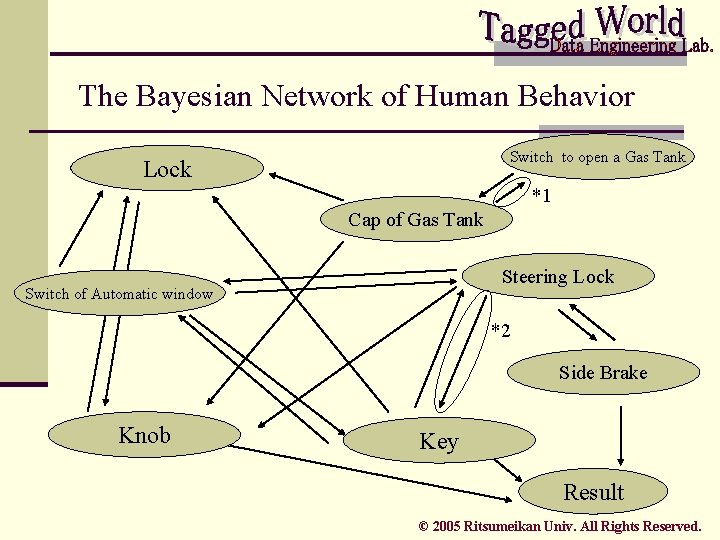
The Bayesian Network of Human Behavior Switch to open a Gas Tank Lock *1 Cap of Gas Tank Steering Lock Switch of Automatic window *2 Side Brake Knob Key Result © 2005 Ritsumeikan Univ. All Rights Reserved.

Describing Model of Human Behavior Heuristic 1 An aim node is excluded from the set of candidate nodes which have a possibility becoming the parent node of all another nodes. Heuristic 2 2. 1 To cut the arrow that does not influence the aim node. 2. 2 To cut the arrow using semantics which the nodes have. Heuristic 3 To sort the configured BNs which Heuristic 1, 2. 1 and 2. 2 are applied in ascending order using true cases and false cases. © 2005 Ritsumeikan Univ. All Rights Reserved.

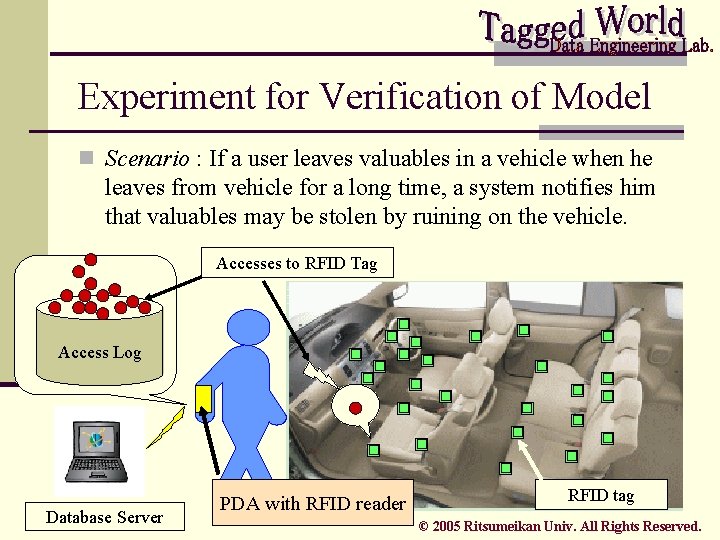
Experiment for Verification of Model n Scenario : If a user leaves valuables in a vehicle when he leaves from vehicle for a long time, a system notifies him that valuables may be stolen by ruining on the vehicle. Accesses to RFID Tag Access Log Database Server PDA with RFID reader RFID tag © 2005 Ritsumeikan Univ. All Rights Reserved.

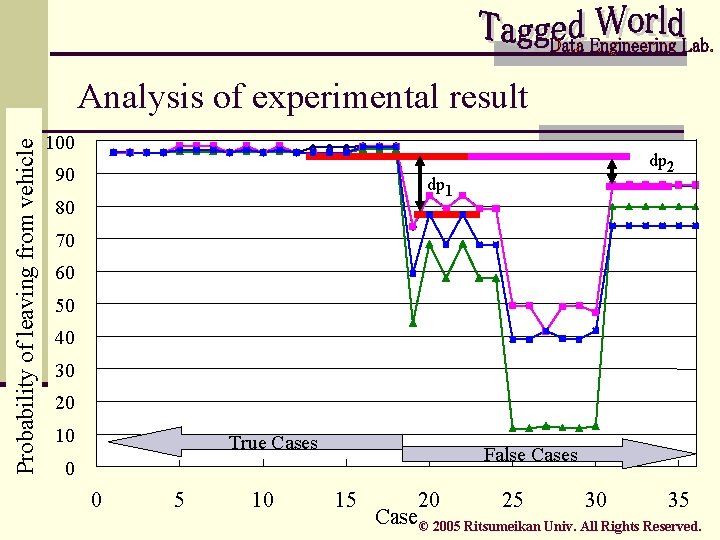
Probability of leaving from vehicle Analysis of experimental result 100 90 dp 2 dp 1 80 70 60 50 40 30 20 10 True Cases False Cases 0 0 5 10 15 20 25 30 35 Case © 2005 Ritsumeikan Univ. All Rights Reserved.

Conclusion and Future works n We proposed the heuristics to configure behavioral scene characteristic from the context using Bayesian Network and the K 2 Algorithm. n Dual directional arrows are cut to configure candidate set of Bayesian networks by using proposed heuristics. n We will get more experimental logs for verification model. © 2005 Ritsumeikan Univ. All Rights Reserved.

Thank you for listening. Thank you very much. © 2005 Ritsumeikan Univ. All Rights Reserved.

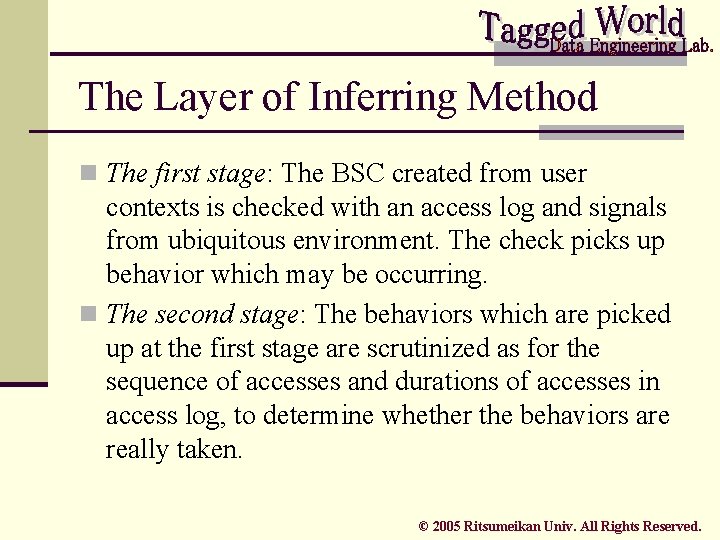
The Layer of Inferring Method n The first stage: The BSC created from user contexts is checked with an access log and signals from ubiquitous environment. The check picks up behavior which may be occurring. n The second stage: The behaviors which are picked up at the first stage are scrutinized as for the sequence of accesses and durations of accesses in access log, to determine whether the behaviors are really taken. © 2005 Ritsumeikan Univ. All Rights Reserved.

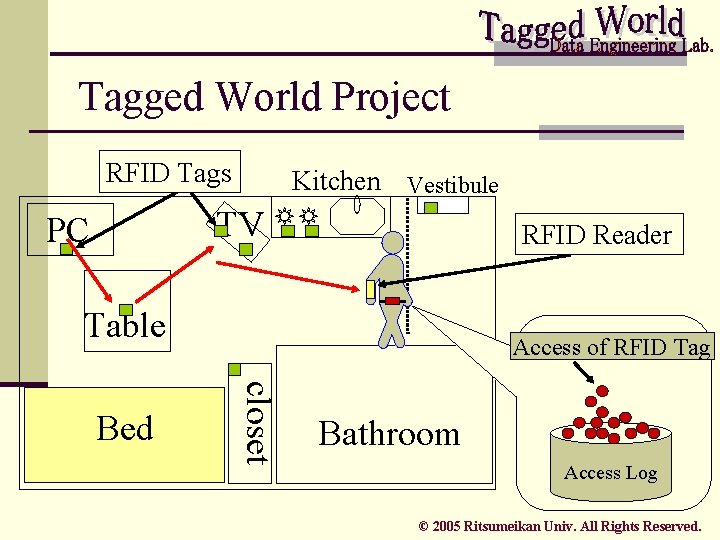
Tagged World Project RFID Tags Kitchen Vestibule TV PC RFID Reader Table closet Bed Access of RFID Tag Bathroom Access Log © 2005 Ritsumeikan Univ. All Rights Reserved.