Contents Introduction n Computer Architecture n ARM Architecture











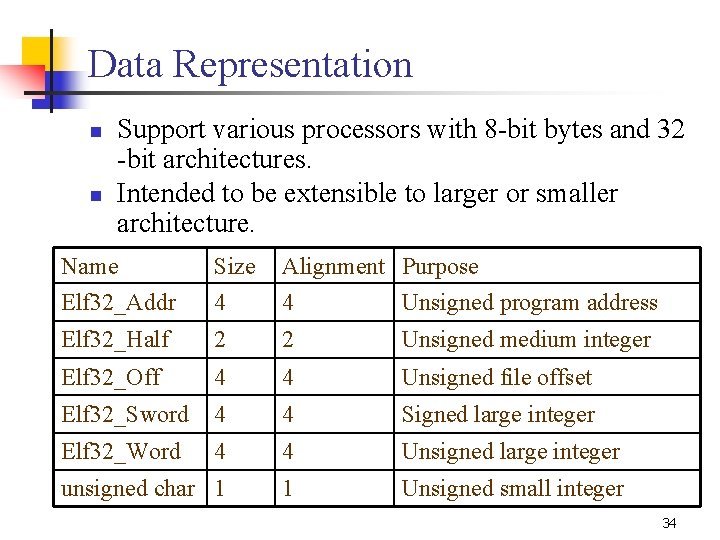
![Example: Section Headers: [Nr] Name Type Addr Off Size ES Flg Lk Inf Al Example: Section Headers: [Nr] Name Type Addr Off Size ES Flg Lk Inf Al](https://slidetodoc.com/presentation_image_h/be11297a3faa77f9292afed5c7fbf4f5/image-32.jpg)













- Slides: 72


Contents Introduction n Computer Architecture n ARM Architecture n Development Tools : GNU Development Tools n ARM Instruction Set n ARM Assembly Language n ARM Assembly Programming : GNU ARM Tool. Chain n Interrupts and Monitor n 2

Lecture 10 Interrupts and Monitor

Outline n n n Exception Handling and Software Interrupts ELF: Executable and Linking Format ARM Monitor and Program Loading 4

Normal Program Flow vs. Exception n n Normally, programs execute sequentially (with a few branches to make life interesting) Normally, programs execute in user mode Exceptions and interrupts break the sequential flow of a program, jumping to architecturally defined memory locations In ARM, Soft. Ware Interrupt (SWI) is the “system call” exception 5

ARM Exceptions n Types of ARM exceptions l l l l Reset: when CPU reset pin is asserted undefined instruction: when CPU tries to execute an undefined op code software interrupt: when CPU executes the SWI instruction prefetch abort: when CPU tries to execute an instruction pre fetched from an illegal address data abort: when data transfer instruction tries to read or write at an illegal address IRQ: when CPU's external interrupt request pin is asserted FIQ: when CPU's external fast interrupt request pin is asserted 6

The Programmer’s Model n Processor Modes (of interest) l User: the “normal” program execution mode. IRQ: used for general purpose interrupt handling. l Supervisor: a protected mode for the operating system. l n The Register Set l l Registers R 0 R 15 + CPSR R 13: Stack Pointer (by convention) R 14: Link Register (hardwired) R 15: Program Counter where bits 0: 1 are ignored (hardwired) 7

Terminology n n The terms exception and interrupt are often confused Exception usually refers to an internal CPU event l l l n Interrupt usually refers to an external I/O event l l n floating point overflow MMU fault (e. g. , page fault) trap (SWI) I/O device request reset In the ARM architecture manuals, the two terms are mixed together 8

What do SWIs do? n n SWIs (often called software traps) allow a user program to “call” the OS that is, SWIs are how system calls are implemented. When SWIs execute, the processor changes modes (from User to Supervisor mode on the ARM) and disables interrupts. 9

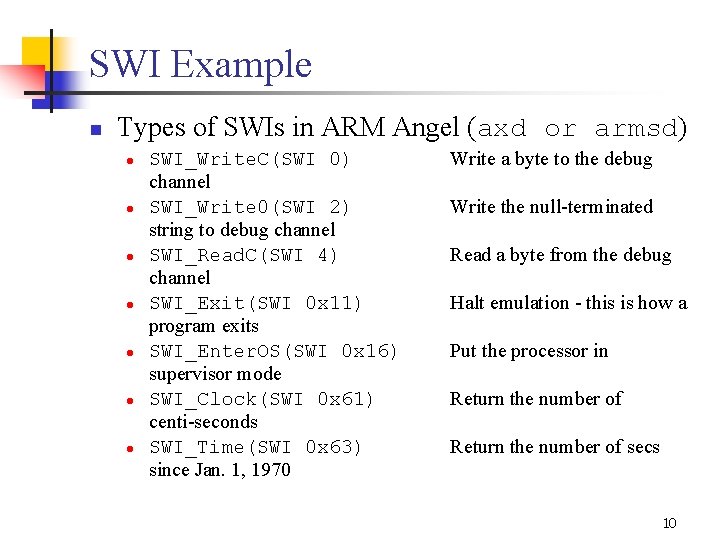
SWI Example n Types of SWIs in ARM Angel (axd or armsd) l l l l SWI_Write. C(SWI 0) channel SWI_Write 0(SWI 2) string to debug channel SWI_Read. C(SWI 4) channel SWI_Exit(SWI 0 x 11) program exits SWI_Enter. OS(SWI 0 x 16) supervisor mode SWI_Clock(SWI 0 x 61) centi seconds SWI_Time(SWI 0 x 63) since Jan. 1, 1970 Write a byte to the debug Write the null terminated Read a byte from the debug Halt emulation this is how a Put the processor in Return the number of secs 10

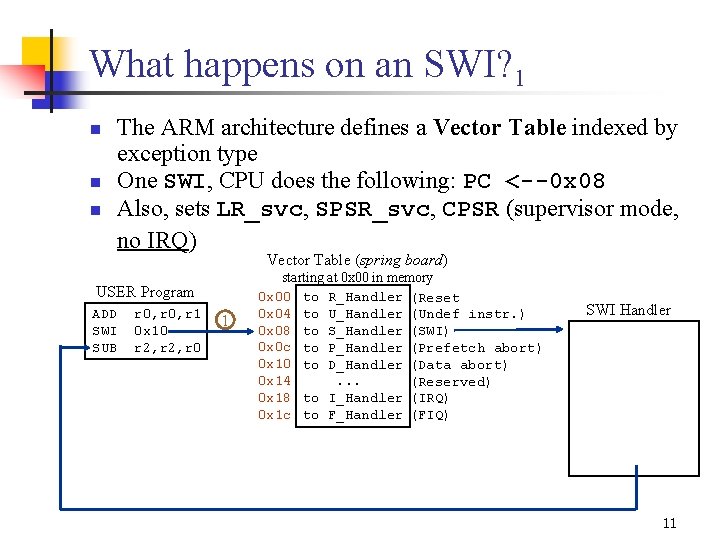
What happens on an SWI? 1 n n n The ARM architecture defines a Vector Table indexed by exception type One SWI, CPU does the following: PC < 0 x 08 Also, sets LR_svc, SPSR_svc, CPSR (supervisor mode, no IRQ) Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 1 starting at 0 x 00 in memory 0 x 00 to R_Handler (Reset 0 x 04 to U_Handler (Undef instr. ) 0 x 08 to S_Handler (SWI) 0 x 0 c to P_Handler (Prefetch abort) 0 x 10 to D_Handler (Data abort) 0 x 14. . . (Reserved) 0 x 18 to I_Handler (IRQ) 0 x 1 c to F_Handler (FIQ) SWI Handler 11

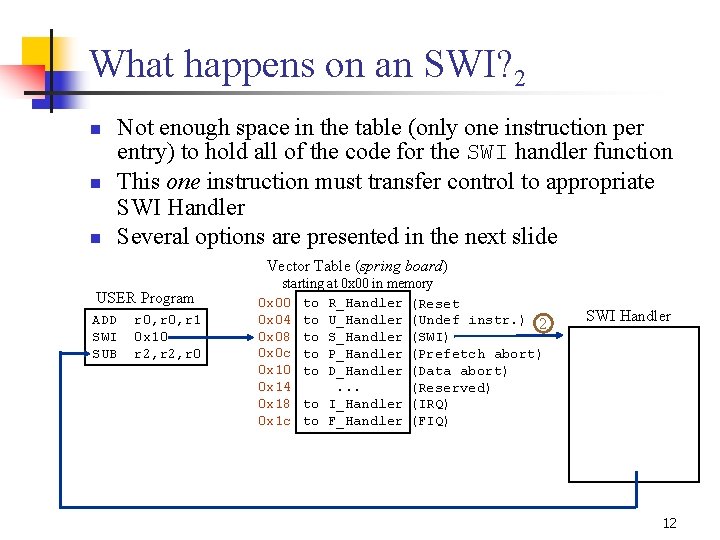
What happens on an SWI? 2 n n n Not enough space in the table (only one instruction per entry) to hold all of the code for the SWI handler function This one instruction must transfer control to appropriate SWI Handler Several options are presented in the next slide Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 starting at 0 x 00 in memory 0 x 00 to R_Handler (Reset 0 x 04 to U_Handler (Undef instr. ) 2 0 x 08 to S_Handler (SWI) 0 x 0 c to P_Handler (Prefetch abort) 0 x 10 to D_Handler (Data abort) 0 x 14. . . (Reserved) 0 x 18 to I_Handler (IRQ) 0 x 1 c to F_Handler (FIQ) SWI Handler 12

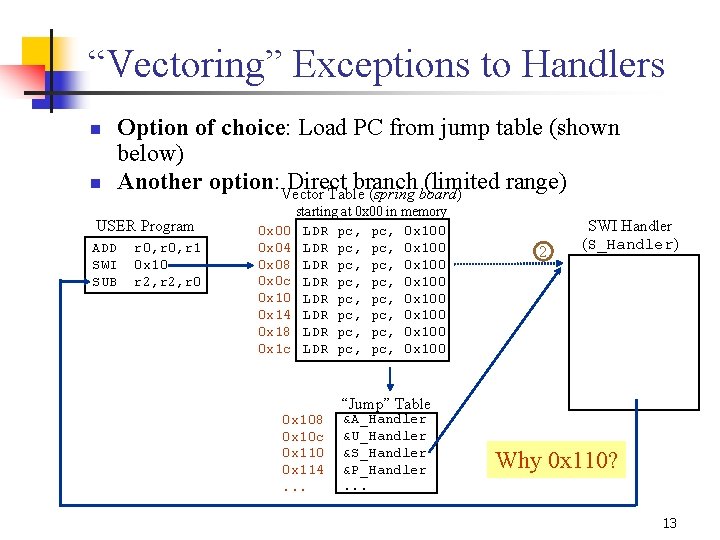
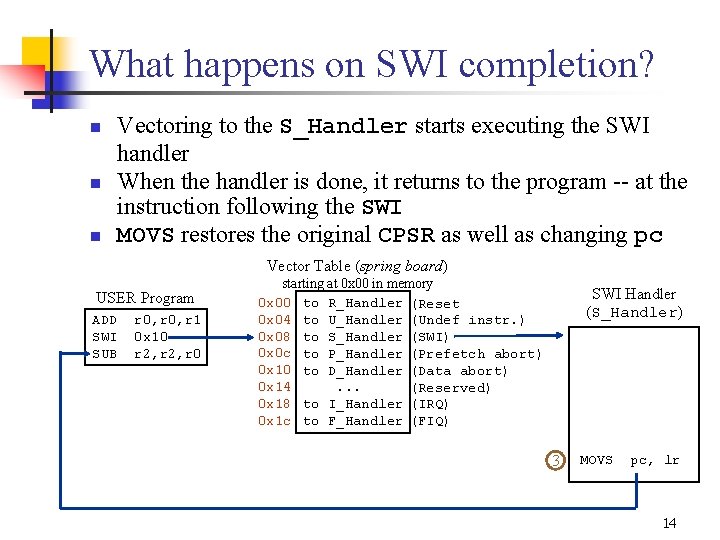
“Vectoring” Exceptions to Handlers n n Option of choice: Load PC from jump table (shown below) Another option: Vector Direct branch (limited range) Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 0 x 04 0 x 08 0 x 0 c 0 x 10 0 x 14 0 x 18 0 x 1 c starting at 0 x 00 in memory LDR pc, pc, 0 x 100 LDR pc, pc, 0 x 100 0 x 108 0 x 10 c 0 x 110 0 x 114. . . 2 SWI Handler (S_Handler) “Jump” Table &A_Handler &U_Handler &S_Handler &P_Handler. . . Why 0 x 110? 13

What happens on SWI completion? n n n Vectoring to the S_Handler starts executing the SWI handler When the handler is done, it returns to the program at the instruction following the SWI MOVS restores the original CPSR as well as changing pc Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 starting at 0 x 00 in memory 0 x 00 to R_Handler (Reset 0 x 04 to U_Handler (Undef instr. ) 0 x 08 to S_Handler (SWI) 0 x 0 c to P_Handler (Prefetch abort) 0 x 10 to D_Handler (Data abort) 0 x 14. . . (Reserved) 0 x 18 to I_Handler (IRQ) 0 x 1 c to F_Handler (FIQ) SWI Handler (S_Handler) 3 MOVS pc, lr 14

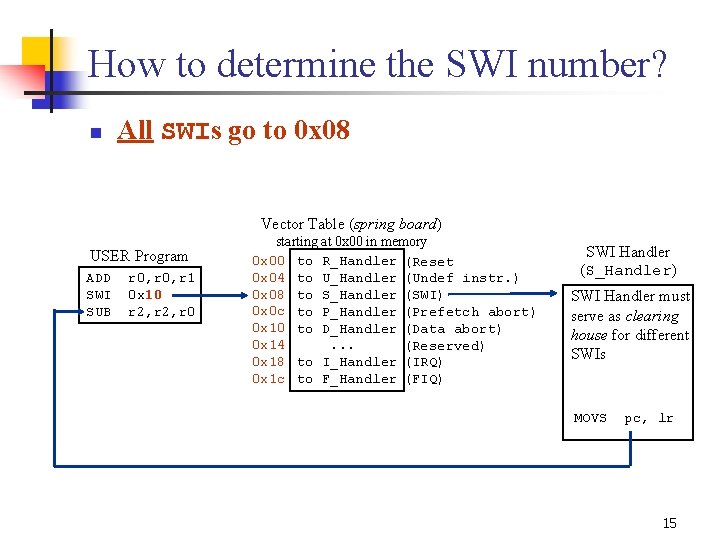
How to determine the SWI number? n All SWIs go to 0 x 08 Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 starting at 0 x 00 in memory 0 x 00 to R_Handler (Reset 0 x 04 to U_Handler (Undef instr. ) 0 x 08 to S_Handler (SWI) 0 x 0 c to P_Handler (Prefetch abort) 0 x 10 to D_Handler (Data abort) 0 x 14. . . (Reserved) 0 x 18 to I_Handler (IRQ) 0 x 1 c to F_Handler (FIQ) SWI Handler (S_Handler) SWI Handler must serve as clearing house for different SWIs MOVS pc, lr 15

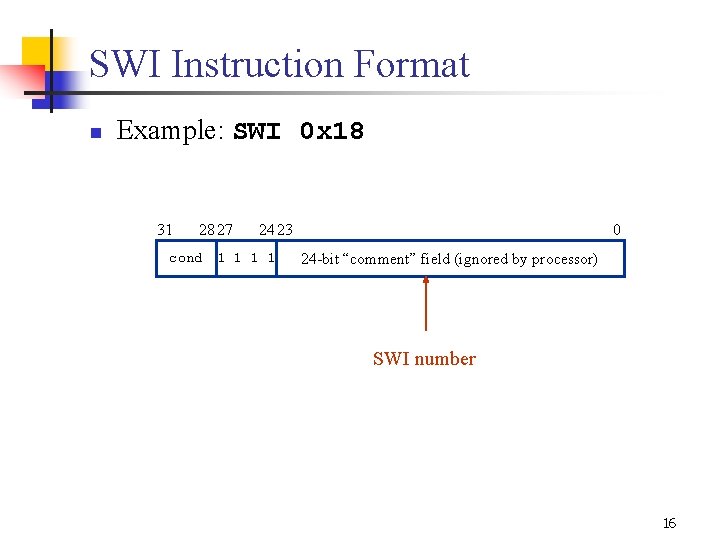
SWI Instruction Format n Example: SWI 0 x 18 31 28 27 24 23 cond 1 1 0 24 bit “comment” field (ignored by processor) SWI number 16

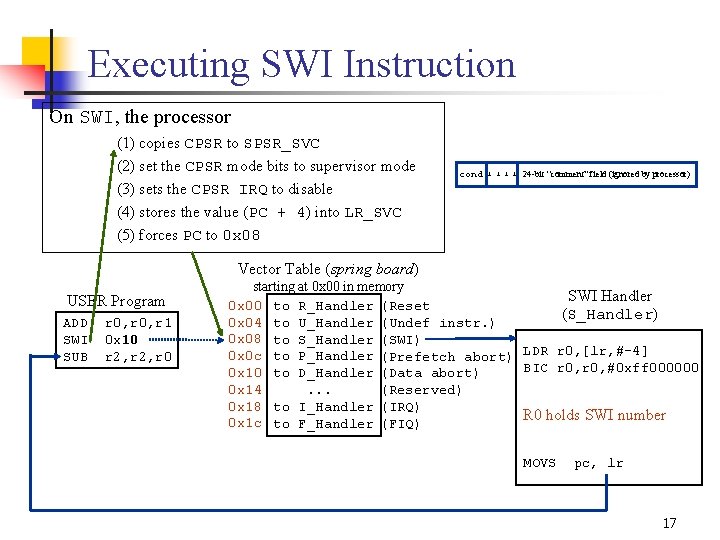
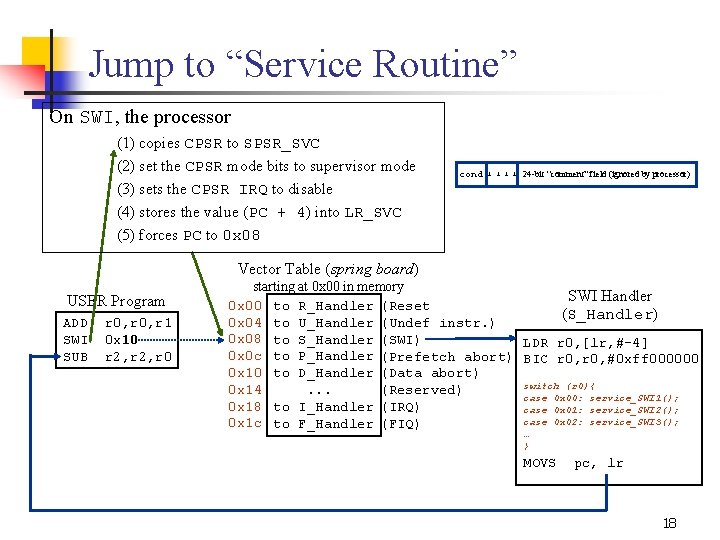
Executing SWI Instruction On SWI, the processor (1) copies CPSR to SPSR_SVC (2) set the CPSR mode bits to supervisor mode (3) sets the CPSR IRQ to disable (4) stores the value (PC + 4) into LR_SVC (5) forces PC to 0 x 08 cond 1 1 24 bit “comment” field (ignored by processor) Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 starting at 0 x 00 in memory SWI Handler 0 x 00 to R_Handler (Reset (S_Handler) 0 x 04 to U_Handler (Undef instr. ) 0 x 08 to S_Handler (SWI) 0 x 0 c to P_Handler (Prefetch abort) LDR r 0, [lr, # 4] BIC r 0, #0 xff 000000 0 x 10 to D_Handler (Data abort) 0 x 14. . . (Reserved) 0 x 18 to I_Handler (IRQ) R 0 holds SWI number 0 x 1 c to F_Handler (FIQ) MOVS pc, lr 17

Jump to “Service Routine” On SWI, the processor (1) copies CPSR to SPSR_SVC (2) set the CPSR mode bits to supervisor mode (3) sets the CPSR IRQ to disable (4) stores the value (PC + 4) into LR_SVC (5) forces PC to 0 x 08 cond 1 1 24 bit “comment” field (ignored by processor) Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 starting at 0 x 00 in memory SWI Handler 0 x 00 to R_Handler (Reset (S_Handler) 0 x 04 to U_Handler (Undef instr. ) 0 x 08 to S_Handler (SWI) LDR r 0, [lr, # 4] 0 x 0 c to P_Handler (Prefetch abort) BIC r 0, #0 xff 000000 0 x 10 to D_Handler (Data abort) switch (r 0){ 0 x 14. . . (Reserved) case 0 x 00: service_SWI 1(); 0 x 18 to I_Handler (IRQ) case 0 x 01: service_SWI 2(); case 0 x 02: service_SWI 3(); 0 x 1 c to F_Handler (FIQ) … } MOVS pc, lr 18

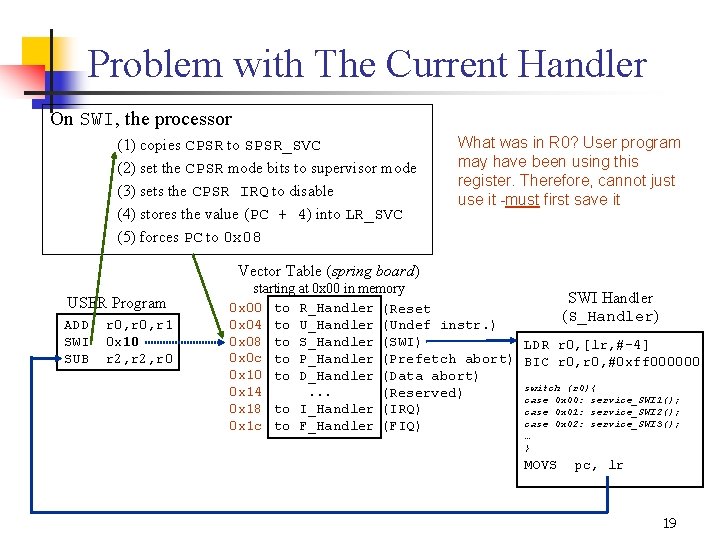
Problem with The Current Handler On SWI, the processor (1) copies CPSR to SPSR_SVC (2) set the CPSR mode bits to supervisor mode (3) sets the CPSR IRQ to disable (4) stores the value (PC + 4) into LR_SVC (5) forces PC to 0 x 08 What was in R 0? User program may have been using this register. Therefore, cannot just use it must first save it Vector Table (spring board) USER Program ADD SWI SUB r 0, r 1 0 x 10 r 2, r 0 starting at 0 x 00 in memory SWI Handler 0 x 00 to R_Handler (Reset (S_Handler) 0 x 04 to U_Handler (Undef instr. ) 0 x 08 to S_Handler (SWI) LDR r 0, [lr, # 4] 0 x 0 c to P_Handler (Prefetch abort) BIC r 0, #0 xff 000000 0 x 10 to D_Handler (Data abort) switch (r 0){ 0 x 14. . . (Reserved) case 0 x 00: service_SWI 1(); 0 x 18 to I_Handler (IRQ) case 0 x 01: service_SWI 2(); case 0 x 02: service_SWI 3(); 0 x 1 c to F_Handler (FIQ) … } MOVS pc, lr 19

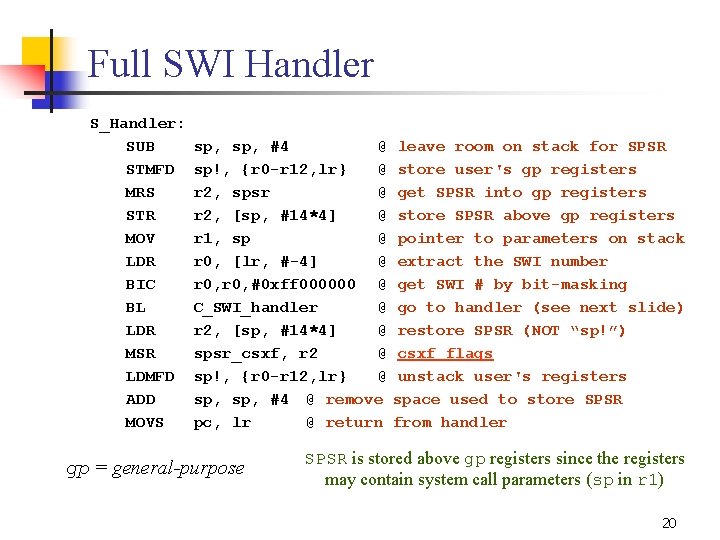
Full SWI Handler S_Handler: SUB STMFD MRS STR MOV LDR BIC BL LDR MSR LDMFD ADD MOVS sp, #4 @ sp!, {r 0 r 12, lr} @ r 2, spsr @ r 2, [sp, #14*4] @ r 1, sp @ r 0, [lr, # 4] @ r 0, #0 xff 000000 @ C_SWI_handler @ r 2, [sp, #14*4] @ spsr_csxf, r 2 @ sp!, {r 0 r 12, lr} @ sp, #4 @ remove pc, lr @ return gp = general-purpose leave room on stack for SPSR store user's gp registers get SPSR into gp registers store SPSR above gp registers pointer to parameters on stack extract the SWI number get SWI # by bit masking go to handler (see next slide) restore SPSR (NOT “sp!”) csxf flags unstack user's registers space used to store SPSR from handler SPSR is stored above gp registers since the registers may contain system call parameters (sp in r 1) 20

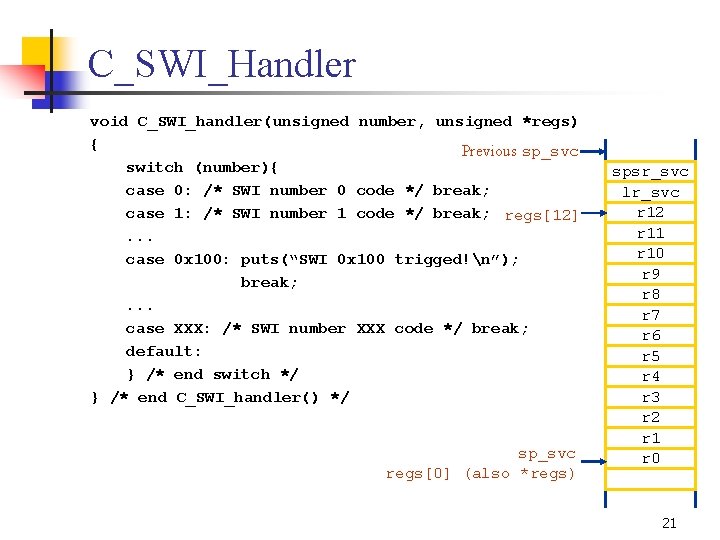
C_SWI_Handler void C_SWI_handler(unsigned number, unsigned *regs) { Previous sp_svc switch (number){ case 0: /* SWI number 0 code */ break; case 1: /* SWI number 1 code */ break; regs[12]. . . case 0 x 100: puts(“SWI 0 x 100 trigged!n”); break; . . . case XXX: /* SWI number XXX code */ break; default: } /* end switch */ } /* end C_SWI_handler() */ sp_svc regs[0] (also *regs) spsr_svc lr_svc r 12 r 11 r 10 r 9 r 8 r 7 r 6 r 5 r 4 r 3 r 2 r 1 r 0 21

Loading the Vector Table /* For 18 349, the Vector Table will use the ``LDR PC, * offset'' springboard approach */ unsigned Install_Handler(unsigned int routine, unsigned int *vector) { unsigned int pcload_instr, old_handler, *soft_vector; pcload_instr = *vector; /* read the Vector Table instr (LDR. . . ) */ pcload_instr &= 0 xfff; /* compute offset of jump table entry */ pcload_instr += 0 x 8 + (unsigned)vector; /* == offset adjusted by PC and prefetch */ soft_vector = (unsigned *)pcload_instr; /* address to load pc from */ old_handler = *soft_vector; /* remember the old handler */ *soft_vector = routine; /* set up new handler in jump table */ return (old_handler); /* return old handler address */ } /* end Install_Handler() */ Called as Install_Handler ((unsigned) S_Handler, swivec); where, unsigned *swivec = (unsigned *) 0 x 08; 22

Example: SWI Application extern void S_Handler(); extern void trigger(); int main() { unsigned *swivec = (unsigned *) 0 x 08; unsigned backup; backup = Install_Handler ((unsigned) S_Handler, swivec); trigger(); Install_Handler (backup, swivec); }. text. align 2. global trigger: STMFD SWI LDMFD sp!, {lr} #0 x 100 sp!, {pc} 23

Exercise #3 n Write a service routine that receives a file name from a trigger and display the first lines of the file on the screen. l n Write a trigger that pass a file name as an argument to the above service routine through SWI #0 x 101. l n Void service 101(char *filename); void trigger 101(char *filename); Write a main program to perform a demonstration. 24

Outline n n n Exception Handling and Software Interrupts ELF: Executable and Linking Format ARM Monitor and Program Loading 25

Introduction to ELF n n n Executable and Linking Format Developed by Unix System Lab. Default binary format on Linux, Solaris 2. x, etc… Some of the capabilities of ELF are dynamic linking, dynamic loading, imposing runtime control on a program, and an improved method for creating shared libraries. The ELF representation of control data in an object file is platform independent. 26

Three Types of ELF Files n Relocatable file l n Executable file l n describes how it should be linked with other object files to create an executable file or shared library. supplies information necessary for the operating system to create a process image suitable for executing the code and accessing the data contained within the file. Shared object file l contains information needed in both static and dynamic linking. 27

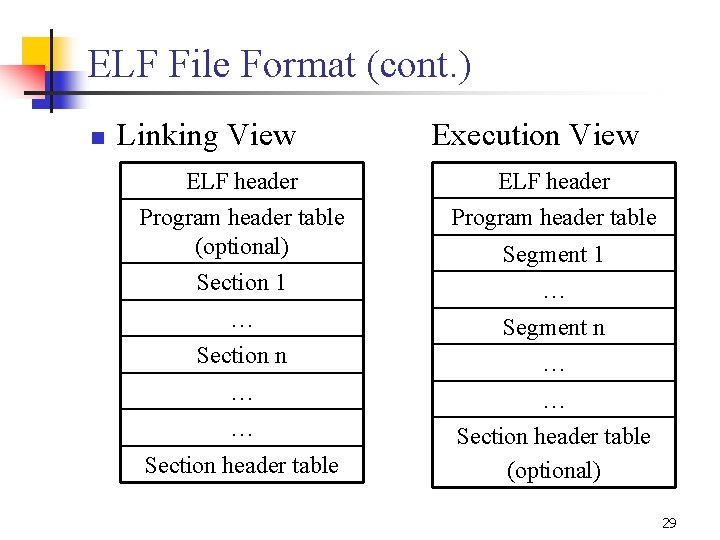
ELF File Format n Two views for each of the three file types. l n These views support both the linking and execution of a program. l l n Linking view and execution view Linking view is partitioned by sections. Execution view is partitioned by segments. The ELF access library, libelf, provides tools to extract and manipulate ELF object files. 28

ELF File Format (cont. ) n Linking View Execution View ELF header Program header table (optional) Program header table Section 1 … … Segment n Section n … … Section header table (optional) Section header table Segment 1 29

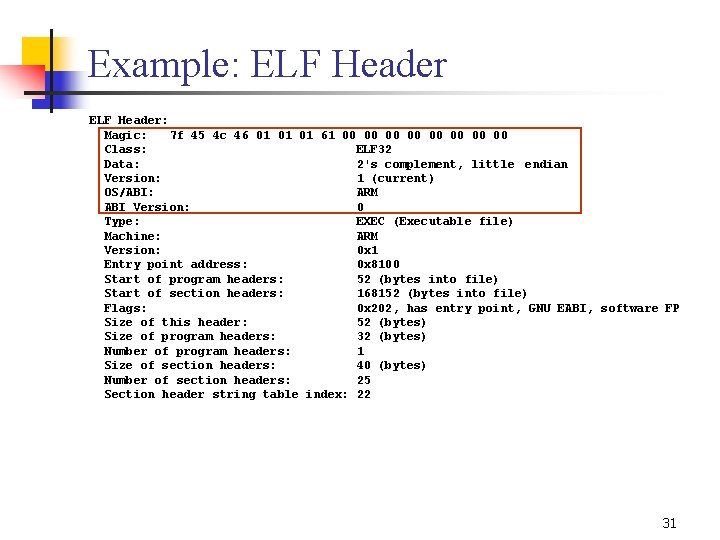
Example: readelf n n We can use “readelf” to output ELF information Example l use “ e” option to read all header from the executable file of “hello. c” $ cat hello. c /* hello. c, a simple example program */ #define GREETING "Hello, World!n" int main() { puts(GREETING); } $ arm elf gcc –o hello. elf hello. c $ arm elf readelf –e hello. elf 30

Example: ELF Header: Magic: 7 f 45 4 c 46 01 01 01 61 00 00 Class: ELF 32 Data: 2's complement, little endian Version: 1 (current) OS/ABI: ARM ABI Version: 0 Type: EXEC (Executable file) Machine: ARM Version: 0 x 1 Entry point address: 0 x 8100 Start of program headers: 52 (bytes into file) Start of section headers: 168152 (bytes into file) Flags: 0 x 202, has entry point, GNU EABI, software FP Size of this header: 52 (bytes) Size of program headers: 32 (bytes) Number of program headers: 1 Size of section headers: 40 (bytes) Number of section headers: 25 Section header string table index: 22 31
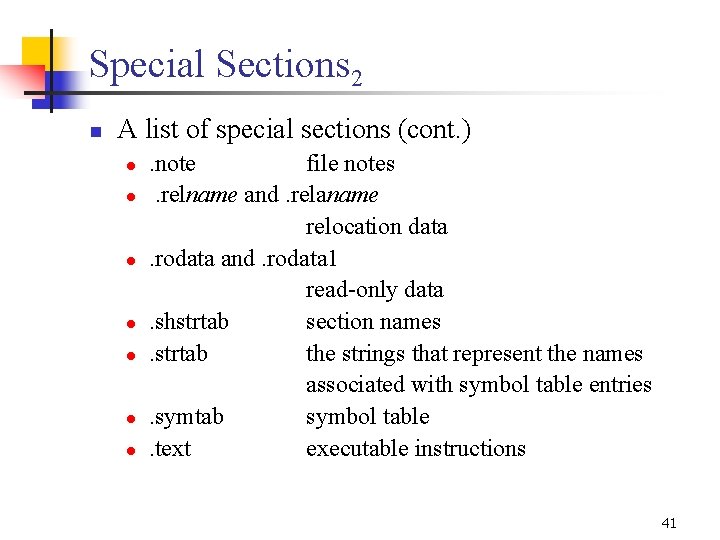
![Example Section Headers Nr Name Type Addr Off Size ES Flg Lk Inf Al Example: Section Headers: [Nr] Name Type Addr Off Size ES Flg Lk Inf Al](https://slidetodoc.com/presentation_image_h/be11297a3faa77f9292afed5c7fbf4f5/image-32.jpg)
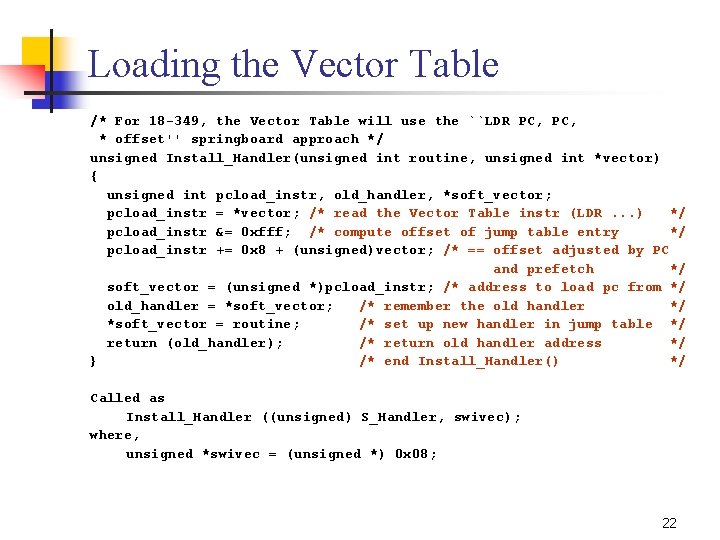
Example: Section Headers: [Nr] Name Type Addr Off Size ES Flg Lk Inf Al [ 0] NULL 000000 00 0 [ 1]. init PROGBITS 00008000 000020 00 AX 0 0 4 [ 2]. text PROGBITS 00008020 0030 e 8 00 AX 0 0 4 [ 3]. fini PROGBITS 0000 b 108 00001 c 00 AX 0 0 4 [ 4]. rodata PROGBITS 0000 b 124 000020 00 A 0 0 4 [ 5]. data PROGBITS 0000 b 244 00092 c 00 WA 0 0 4 [ 6]. eh_frame PROGBITS 0000 bb 70 000004 00 A 0 0 4 [ 7]. ctors PROGBITS 0000 bb 74 000008 00 WA 0 0 4 [ 8]. dtors PROGBITS 0000 bb 7 c 000008 00 WA 0 0 4 [ 9]. jcr PROGBITS 0000 bb 84 000004 00 WA 0 0 4 [10]. bss NOBITS 0000 bb 88 00010 c 00 WA 0 0 4 [11]. comment PROGBITS 0000 00 bb 88 000288 00 0 0 1 [12]. debug_aranges PROGBITS 0000 00 be 10 000420 00 0 0 8 [13]. debug_pubnames PROGBITS 0000 00 c 230 000726 00 0 0 1 [14]. debug_info PROGBITS 0000 00 c 956 011 f 48 00 0 0 1 [15]. debug_abbrev PROGBITS 0000 01 e 89 e 0031 f 4 00 0 0 1 [16]. debug_line PROGBITS 0000 021 a 92 002 a 14 00 0 0 1 [17]. debug_frame PROGBITS 0000 0244 a 8 000 a 14 00 0 0 4 [18]. debug_str PROGBITS 0000 024 ebc 001406 01 MS 0 0 1 [19]. debug_loc PROGBITS 0000 0262 c 2 002 be 0 00 0 0 1 [20]. stack PROGBITS 00080000 028 ea 2 000000 00 W 0 0 1 [21]. debug_ranges PROGBITS 0000 028 ea 2 000150 00 0 0 1 [22]. shstrtab STRTAB 0000 028 ff 2 0000 e 3 00 0 0 1 [23]. symtab SYMTAB 0000 0294 c 0 001590 10 24 ef 4 [24]. strtab STRTAB 0000 02 aa 50 0007 f 9 00 0 0 1 Key to Flags: W (write), A (alloc), X (execute), M (merge), S (strings) I (info), L (link order), G (group), x (unknown) O (extra OS processing required) o (OS specific), p (processor specific) 32

Example: Program Headers: Type Offset Virt. Addr Phys. Addr File. Siz Mem. Siz Flg Align LOAD 0 x 008000 0 x 00008000 0 x 03 b 88 0 x 03 c 94 RWE 0 x 8000 Section to Segment mapping: Segment Sections. . . 00 . init. text. fini. rodata. eh_frame. ctors. dtors. jcr. bss 33

Data Representation n n Support various processors with 8 bit bytes and 32 bit architectures. Intended to be extensible to larger or smaller architecture. Name Elf 32_Addr Size 4 Alignment Purpose 4 Unsigned program address Elf 32_Half 2 2 Unsigned medium integer Elf 32_Off 4 4 Unsigned file offset Elf 32_Sword 4 4 Signed large integer Elf 32_Word 4 4 Unsigned large integer unsigned char 1 1 Unsigned small integer 34

ELF Header 1 n n n It is always the first section of the file. Describes the type of the object file. Its target architecture, and the version of ELF it is using. The location of the Program Header table, Section Header table, and String table along with associated number and size of entries for each table are also given. Contains the location of the first executable instruction. 35

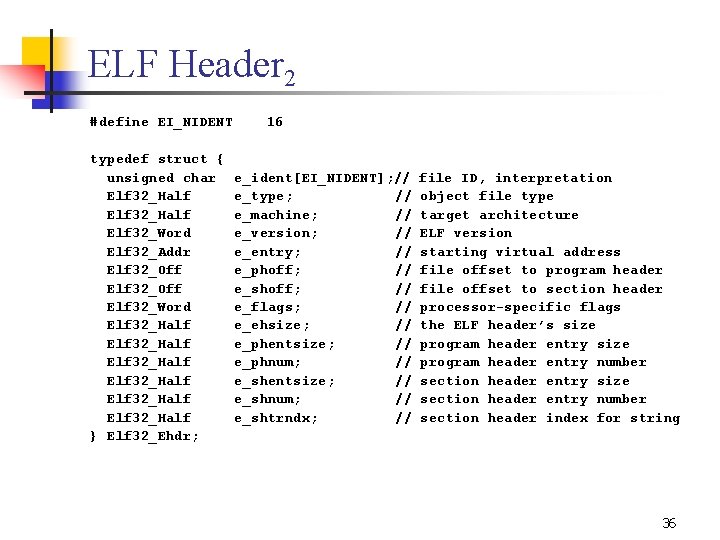
ELF Header 2 #define EI_NIDENT typedef struct { unsigned char Elf 32_Half Elf 32_Word Elf 32_Addr Elf 32_Off Elf 32_Word Elf 32_Half Elf 32_Half } Elf 32_Ehdr; 16 e_ident[EI_NIDENT]; // e_type; // e_machine; // e_version; // e_entry; // e_phoff; // e_shoff; // e_flags; // e_ehsize; // e_phentsize; // e_phnum; // e_shentsize; // e_shnum; // e_shtrndx; // file ID, interpretation object file type target architecture ELF version starting virtual address file offset to program header file offset to section header processor specific flags the ELF header’s size program header entry number section header entry size section header entry number section header index for string 36

Section Header n n The section header table is an array of structures. A section header table index is a subscript into this array. Each entry correlates to a section in the file. The entry provides the name, type, memory image starting address, file offset, the section’s size in bytes, alignment. 37

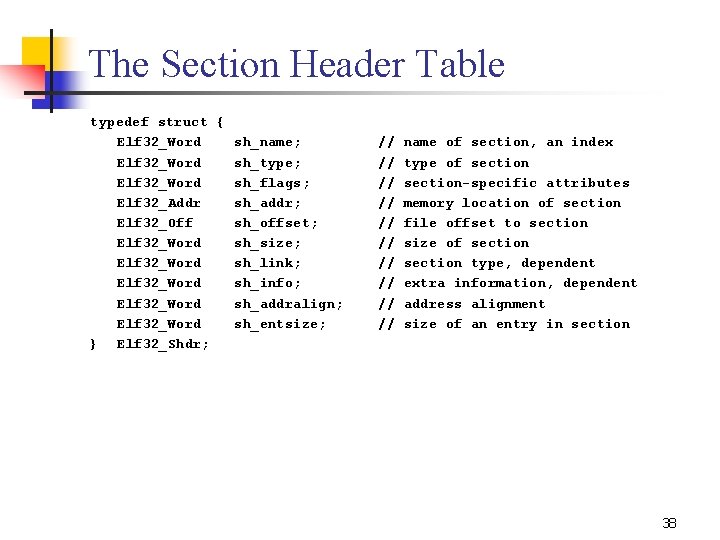
The Section Header Table typedef struct { Elf 32_Word sh_name; Elf 32_Word sh_type; Elf 32_Word sh_flags; Elf 32_Addr sh_addr; Elf 32_Off sh_offset; Elf 32_Word sh_size; Elf 32_Word sh_link; Elf 32_Word sh_info; Elf 32_Word sh_addralign; Elf 32_Word sh_entsize; } Elf 32_Shdr; // // // name of section, an index type of section specific attributes memory location of section file offset to section size of section type, dependent extra information, dependent address alignment size of an entry in section 38

ELF Sections n n A number of types of sections described by entries in the section header table. Sections can hold executable code, data, dynamic linking information, debugging data, symbol tables, relocation information, comments, string tables, and notes. 39

Special Sections 1 n n Various sections in ELF are pre defined. A list of special sections l l l l . bss un initialized data. comment version control information. data and. data 1 initialized data present. debug… information for symbolic debugging. dynamic linking information. dynstr strings needed for dynamic linking. hash symbol hash table. line number information for debugging 40

Special Sections 2 n A list of special sections (cont. ) l l l l . note file notes. relname and. relaname relocation data. rodata and. rodata 1 read only data. shstrtab section names. strtab the strings that represent the names associated with symbol table entries. symtab symbol table. text executable instructions 41

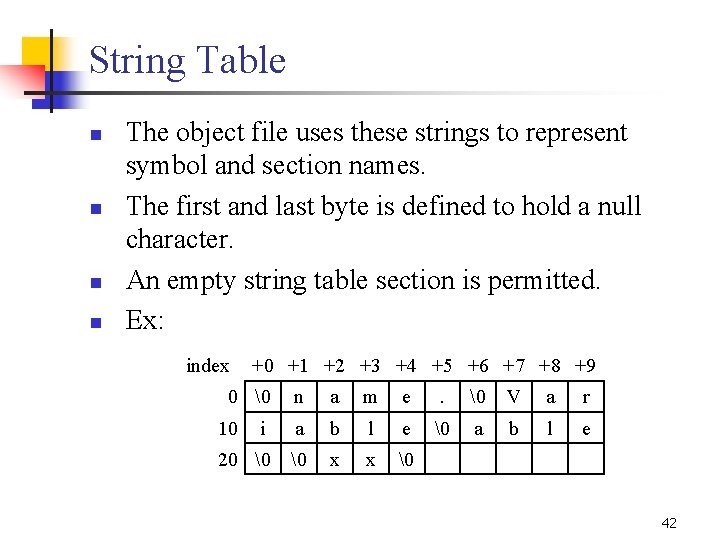
String Table n n The object file uses these strings to represent symbol and section names. The first and last byte is defined to hold a null character. An empty string table section is permitted. Ex: index +0 +1 +2 +3 +4 +5 +6 +7 +8 +9 0 � n a m e . � V a r i a b l e � a b l e 20 � � x x � 10 42

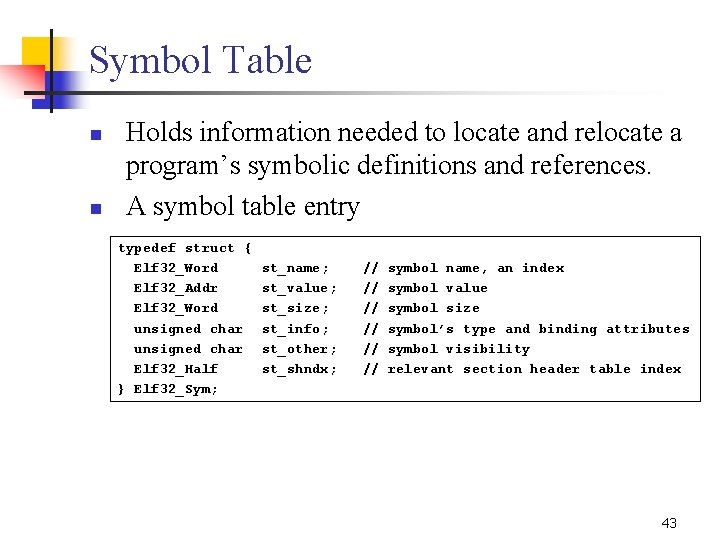
Symbol Table n n Holds information needed to locate and relocate a program’s symbolic definitions and references. A symbol table entry typedef struct { Elf 32_Word Elf 32_Addr Elf 32_Word unsigned char Elf 32_Half } Elf 32_Sym; st_name; st_value; st_size; st_info; st_other; st_shndx; // // // symbol name, an index symbol value symbol size symbol’s type and binding attributes symbol visibility relevant section header table index 43

Program Header n n Program headers are meaningful only for executable and shared object files. The program header table is an array of structures, each describing a segment or other information. An object file segment contains one or more sections. A file specifies its own program header size with the ELF header’s e_phentsize & e_phnum. 44

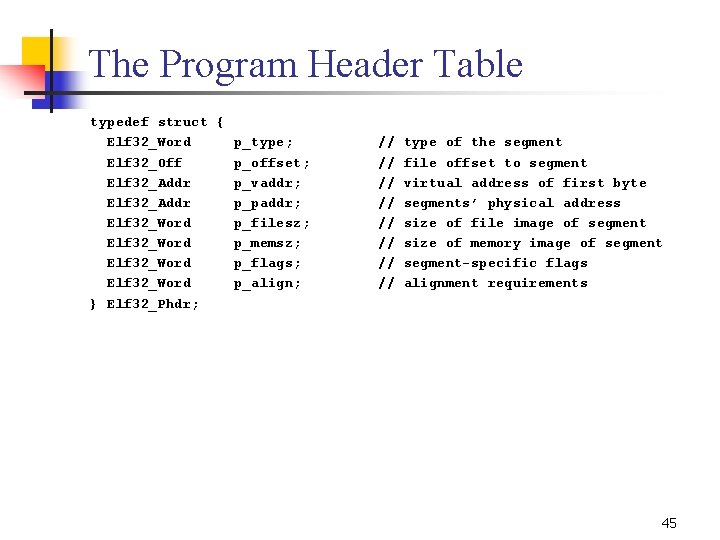
The Program Header Table typedef struct { Elf 32_Word p_type; Elf 32_Off p_offset; Elf 32_Addr p_vaddr; Elf 32_Addr p_paddr; Elf 32_Word p_filesz; Elf 32_Word p_memsz; Elf 32_Word p_flags; Elf 32_Word p_align; } Elf 32_Phdr; // // type of the segment file offset to segment virtual address of first byte segments’ physical address size of file image of segment size of memory image of segment specific flags alignment requirements 45

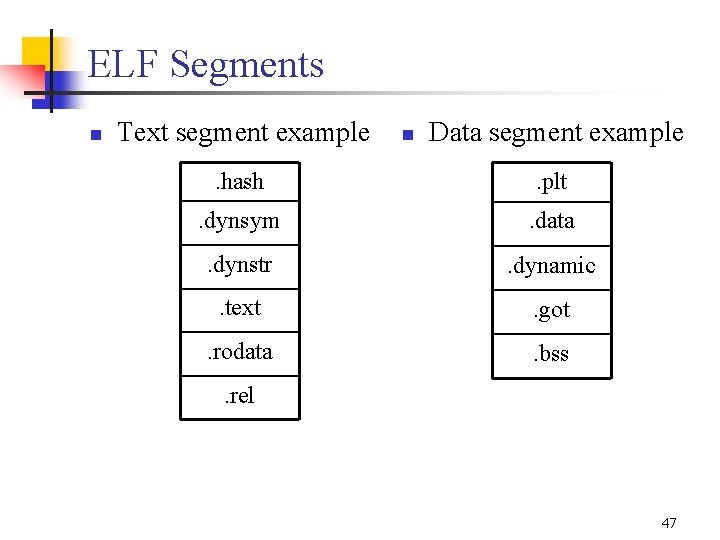
Executable Programs n n A program to be loaded by the system must have at least one loadable segment. Segments are a way of grouping related sections. A process image is created by loading and interpreting segments. Segment contents l l l A segment comprises one or more sections. Text segments contain read only instructions and data. Data segments contain writable data and instructions 46

ELF Segments n Text segment example n Data segment example . hash . plt . dynsym . data . dynstr . dynamic . text . got . rodata . bss . rel 47

Exercise #4 n Write a service routine that receives the name of an ELF executable file as a parameter and display the offset of program header on the screen. l n Write a trigger that pass a file name to the above service routine through SWI #102. l n Void service 102(char *filename); void trigger 102(char *filename); Write a main program to perform a demonstration. 48

Outline n n n Exception Handling and Software Interrupts ELF: Executable and Linking Format ARM Monitor and Program Loading 49

Overview of ARM Debug Monitor n n The ARM Debug Monitor is called “Angel” (earlier versions called it the “Demon” – get it? ) Provides l n lowlevel programming C library and debugging environment When the X board first boots, they load the demon from flash memory (emulator pretends that this happens) l This activity is called “bootstrapping” 50

Memory Map of Demon 0 x 0000 0 x 0004 0 x 0020 0 x 0400 0 x 0500 0 x 0600 0 x 0700 0 x 0800 0 x 1000 0 x 2000 0 x 8000 CPU reset vector. . . 0 x 1 c CPU undefined instruction. . . CPU Fast Interrupt Vector ~1 K Bytes for FIQ and FIQ mode stack 256 bytes for IRQ mode stack 256 bytes for Undefined mode stack 256 bytes for Abort mode stack 256 bytes for SVC mode stack Debug monitor private workspace Free for user supplied Debug Monitor Floating Point Emulation Space Application Space top of memory SWI_Getenv returns top of memory = 0 x 08000000 51

Monitor Program n Provide Capability to l l n Setup Hardware on startup Load and run programs Debug code Minimal OS functionality Many embedded systems are just l l l Monitor + application Monitor still handles other types of interrupts (we'll cover this later) l timer, I/O (e. g. , keypad, switches, LED, LCD) 52

Example System n Interrupt from external devices l n keyboards, timers, disk drives We refer to each piece of software as a process l l n Codes Program counter Registers Stack Other terms l l Task Thread 53

Debug Monitor SWIs n Angel provides a number of SWIs that you can use SWI_Write. C (0) SWI_Write 0(2) SWI_Read. C(4) SWI_Exit (0 x 11) SWI_Enter. OS (0 x 16) SWI_Get. Errno (0 x 60) SWI_Clock (0 x 61) SWI_Time (0 x 63) SWI_Remove (0 x 64) SWI_Rename (0 x 65) SWI_Open (0 x 66) SWI_Close (0 x 68) SWI_Write (0 x 69) SWI_Read (0 x 6 a) SWI_Seek (0 x 6 b) SWI_Flen (0 x 6 c) SWI_Install. Handler(0 x 70) Write a byte to the debug channel Write the null terminated string to debug channel Read a byte from the debug channel Halt emulation this is how a program exits Put the processor in supervisor mode Returns (r 0) the value of the C library err no variable Return the number of centi seconds Return the number of seconds since Jan. 1, 1970 Deletes the file named by pointer in r 0 Renames a file Open file (or device) Close a file (or device) Read a file Write a file Seek to a specific location in a file Returns length of the file object installs a handler for a hardware exception 54

Program Loading n Monitor reads program from ? ? ? and puts it into RAM l l Does it just copy the executable into RAM? ? Where does it put it? ? Who sets up the user stack? ? Who sets up the user heap? ? 55

ARM File Formats n n ARM supports many formats for executables Executable ARM Image Format (AIF) l l n ARM ELF l n n Non executable ARM Image Format (AIF) ARM Object Format (AOF) ARM Object Library Format ARM Symbolic Debug Table Format Specialized version of ELF Each provides code + data + other information We will focus on ARM ELF 56

ARM ELF n ARM ELF l l n ELF (Executable and Linking Format) header Image's code Image's initialized static data Debug and relocation information (optional) We will use static linking (no dynamic linking or shared libraries) ELF Header Program Header Table Segment 1 Segment 2 …… Section Header Table optional ARM ELF File 57

Loading an Executable 1 n Read the executable file l l n Parse the header to determine the size of the image l n n ARMulator gets stuff from the native file system Loader uses the SWI_Open and SWI_Read Monitor system calls Starting location and image base Create new address space for program large enough to hold text and data segments, along with a stack segment Copy instructions and data from executable file into the new address space 58

Loading an Executable 2 n n n Zero init the un initialized data Copy arguments passed to the program onto the stack Initializes machine registers l n n Most registers cleared, but stack pointer assigned address of 1 st free stack location Jumps to start up routine that copies program’s arguments from stack to registers and sets the PC If main routine returns, start up routine terminates program with the SWI_Exit system call 59

Optional ARM ELF Components n Compression l n Relocation l n n Self relocation code included in image Debugging l n Self decompression code included in image Symbol table for debugger use String tables for efficient allocation of strings Can have more than one section per segment 60

Starting a Program n We discussed how an application's initial PC is set l l n The loader gets the address of the starting instruction from the object file header To start the program, the loader moves the specified address into the PC Is main() the starting point? l l In other words, does the PC initially get set to the address of main()? Let's look at an example 61

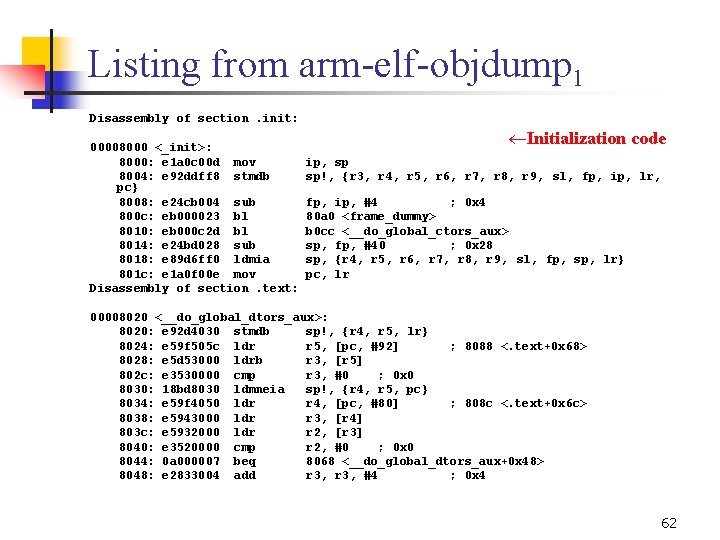
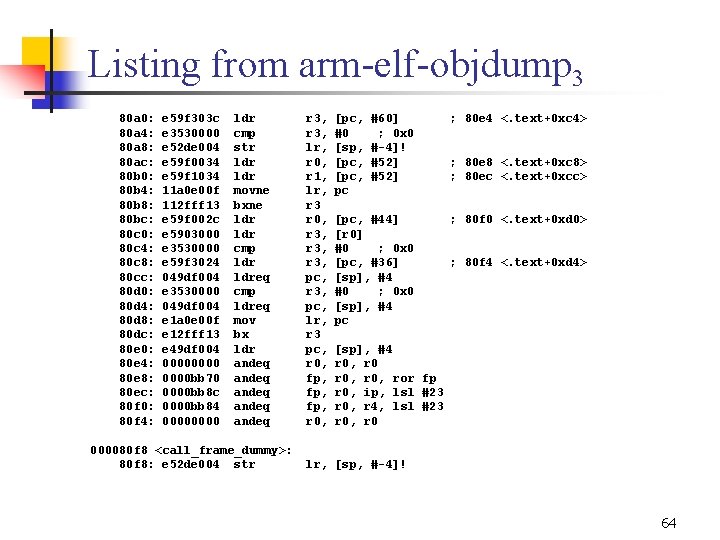
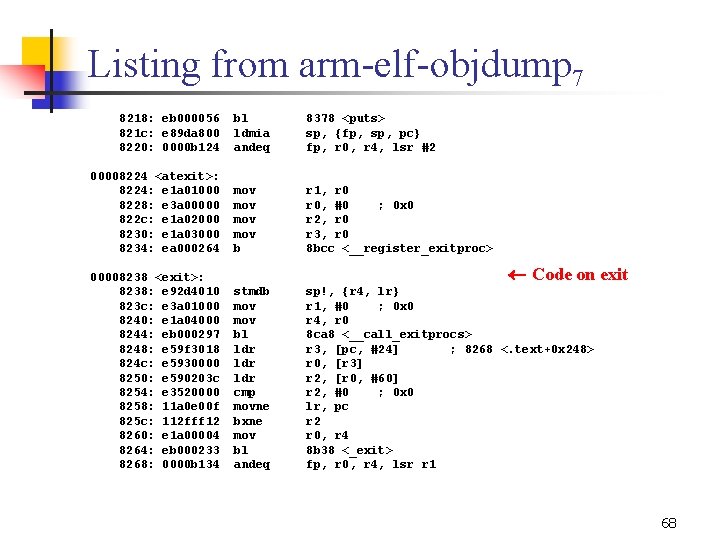
Listing from arm elf objdump 1 Disassembly of section. init: 00008000 <_init>: 8000: e 1 a 0 c 00 d mov 8004: e 92 ddff 8 stmdb pc} 8008: e 24 cb 004 sub 800 c: eb 000023 bl 8010: eb 000 c 2 d bl 8014: e 24 bd 028 sub 8018: e 89 d 6 ff 0 ldmia 801 c: e 1 a 0 f 00 e mov Disassembly of section. text: ¬Initialization code ip, sp sp!, {r 3, r 4, r 5, r 6, r 7, r 8, r 9, sl, fp, ip, lr, fp, ip, #4 ; 0 x 4 80 a 0 <frame_dummy> b 0 cc <__do_global_ctors_aux> sp, fp, #40 ; 0 x 28 sp, {r 4, r 5, r 6, r 7, r 8, r 9, sl, fp, sp, lr} pc, lr 00008020 <__do_global_dtors_aux>: 8020: e 92 d 4030 stmdb sp!, {r 4, r 5, lr} 8024: e 59 f 505 c ldr r 5, [pc, #92] ; 8088 <. text+0 x 68> 8028: e 5 d 53000 ldrb r 3, [r 5] 802 c: e 3530000 cmp r 3, #0 ; 0 x 0 8030: 18 bd 8030 ldmneia sp!, {r 4, r 5, pc} 8034: e 59 f 4050 ldr r 4, [pc, #80] ; 808 c <. text+0 x 6 c> 8038: e 5943000 ldr r 3, [r 4] 803 c: e 5932000 ldr r 2, [r 3] 8040: e 3520000 cmp r 2, #0 ; 0 x 0 8044: 0 a 000007 beq 8068 <__do_global_dtors_aux+0 x 48> 8048: e 2833004 add r 3, #4 ; 0 x 4 62

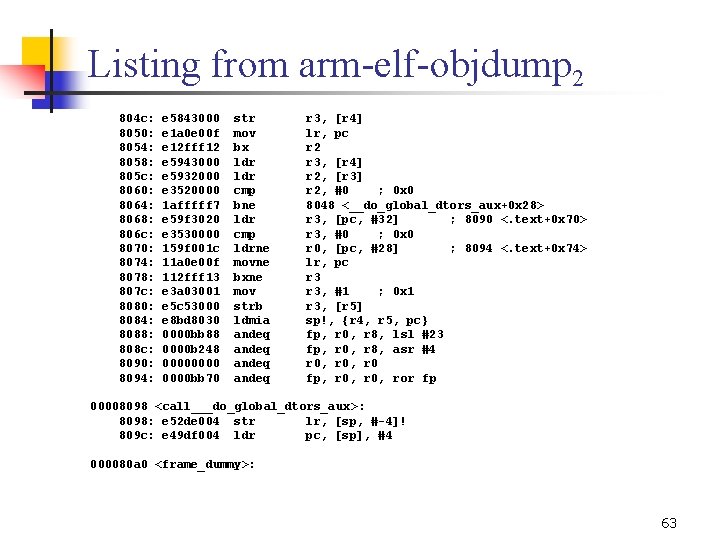
Listing from arm elf objdump 2 804 c: 8050: 8054: 8058: 805 c: 8060: 8064: 8068: 806 c: 8070: 8074: 8078: 807 c: 8080: 8084: 8088: 808 c: 8090: 8094: e 5843000 e 1 a 0 e 00 f e 12 fff 12 e 5943000 e 5932000 e 3520000 1 afffff 7 e 59 f 3020 e 3530000 159 f 001 c 11 a 0 e 00 f 112 fff 13 e 3 a 03001 e 5 c 53000 e 8 bd 8030 0000 bb 88 0000 b 248 0000 bb 70 str mov bx ldr cmp bne ldr cmp ldrne movne bxne mov strb ldmia andeq r 3, [r 4] lr, pc r 2 r 3, [r 4] r 2, [r 3] r 2, #0 ; 0 x 0 8048 <__do_global_dtors_aux+0 x 28> r 3, [pc, #32] ; 8090 <. text+0 x 70> r 3, #0 ; 0 x 0 r 0, [pc, #28] ; 8094 <. text+0 x 74> lr, pc r 3, #1 ; 0 x 1 r 3, [r 5] sp!, {r 4, r 5, pc} fp, r 0, r 8, lsl #23 fp, r 0, r 8, asr #4 r 0, r 0 fp, r 0, ror fp 00008098 <call___do_global_dtors_aux >: 8098: e 52 de 004 str lr, [sp, # 4]! 809 c: e 49 df 004 ldr pc, [sp], #4 000080 a 0 <frame_dummy>: 63

Listing from arm elf objdump 3 80 a 0: 80 a 4: 80 a 8: 80 ac: 80 b 0: 80 b 4: 80 b 8: 80 bc: 80 c 0: 80 c 4: 80 c 8: 80 cc: 80 d 0: 80 d 4: 80 d 8: 80 dc: 80 e 0: 80 e 4: 80 e 8: 80 ec: 80 f 0: 80 f 4: e 59 f 303 c e 3530000 e 52 de 004 e 59 f 0034 e 59 f 1034 11 a 0 e 00 f 112 fff 13 e 59 f 002 c e 5903000 e 3530000 e 59 f 3024 049 df 004 e 3530000 049 df 004 e 1 a 0 e 00 f e 12 fff 13 e 49 df 004 0000 bb 70 0000 bb 8 c 0000 bb 84 0000 ldr cmp str ldr movne bxne ldr cmp ldreq mov bx ldr andeq andeq 000080 f 8 <call_frame_dummy>: 80 f 8: e 52 de 004 str r 3, lr, r 0, r 1, lr, r 3 r 0, r 3, pc, lr, r 3 pc, r 0, fp, fp, r 0, [pc, #0 [sp, [pc, pc #60] ; 0 x 0 # 4]! #52] ; 80 e 4 <. text+0 xc 4> [pc, #44] [r 0] #0 ; 0 x 0 [pc, #36] [sp], #4 #0 ; 0 x 0 [sp], #4 pc ; 80 f 0 <. text+0 xd 0> ; 80 e 8 <. text+0 xc 8> ; 80 ec <. text+0 xcc> ; 80 f 4 <. text+0 xd 4> [sp], #4 r 0, ror fp r 0, ip, lsl #23 r 0, r 4, lsl #23 r 0, r 0 lr, [sp, # 4]! 64

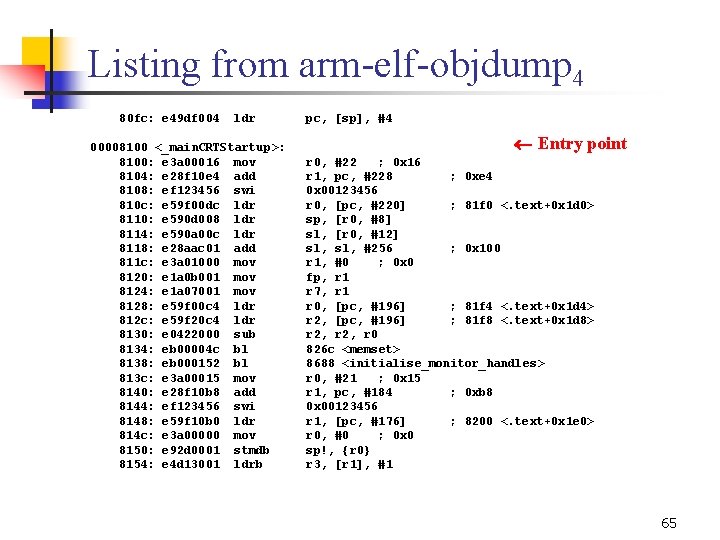
Listing from arm elf objdump 4 80 fc: e 49 df 004 ldr 00008100 <_main. CRTStartup>: 8100: e 3 a 00016 mov 8104: e 28 f 10 e 4 add 8108: ef 123456 swi 810 c: e 59 f 00 dc ldr 8110: e 590 d 008 ldr 8114: e 590 a 00 c ldr 8118: e 28 aac 01 add 811 c: e 3 a 01000 mov 8120: e 1 a 0 b 001 mov 8124: e 1 a 07001 mov 8128: e 59 f 00 c 4 ldr 812 c: e 59 f 20 c 4 ldr 8130: e 0422000 sub 8134: eb 00004 c bl 8138: eb 000152 bl 813 c: e 3 a 00015 mov 8140: e 28 f 10 b 8 add 8144: ef 123456 swi 8148: e 59 f 10 b 0 ldr 814 c: e 3 a 00000 mov 8150: e 92 d 0001 stmdb 8154: e 4 d 13001 ldrb pc, [sp], #4 Entry point r 0, #22 ; 0 x 16 r 1, pc, #228 ; 0 xe 4 0 x 00123456 r 0, [pc, #220] ; 81 f 0 <. text+0 x 1 d 0> sp, [r 0, #8] sl, [r 0, #12] sl, #256 ; 0 x 100 r 1, #0 ; 0 x 0 fp, r 1 r 7, r 1 r 0, [pc, #196] ; 81 f 4 <. text+0 x 1 d 4> r 2, [pc, #196] ; 81 f 8 <. text+0 x 1 d 8> r 2, r 0 826 c <memset> 8688 <initialise_monitor_handles > r 0, #21 ; 0 x 15 r 1, pc, #184 ; 0 xb 8 0 x 00123456 r 1, [pc, #176] ; 8200 <. text+0 x 1 e 0> r 0, #0 ; 0 x 0 sp!, {r 0} r 3, [r 1], #1 65

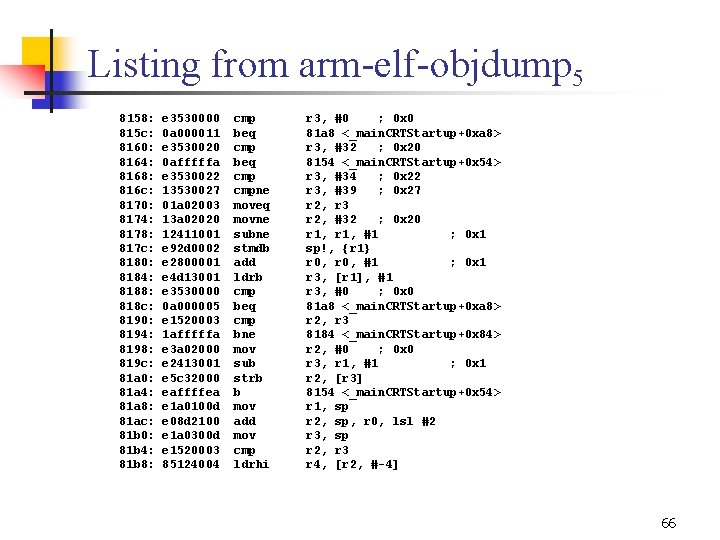
Listing from arm elf objdump 5 8158: 815 c: 8160: 8164: 8168: 816 c: 8170: 8174: 8178: 817 c: 8180: 8184: 8188: 818 c: 8190: 8194: 8198: 819 c: 81 a 0: 81 a 4: 81 a 8: 81 ac: 81 b 0: 81 b 4: 81 b 8: e 3530000 0 a 000011 e 3530020 0 afffffa e 3530022 13530027 01 a 02003 13 a 02020 12411001 e 92 d 0002 e 2800001 e 4 d 13001 e 3530000 0 a 000005 e 1520003 1 afffffa e 3 a 02000 e 2413001 e 5 c 32000 eaffffea e 1 a 0100 d e 08 d 2100 e 1 a 0300 d e 1520003 85124004 cmp beq cmpne moveq movne subne stmdb add ldrb cmp beq cmp bne mov sub strb b mov add mov cmp ldrhi r 3, #0 ; 0 x 0 81 a 8 <_main. CRTStartup+0 xa 8> r 3, #32 ; 0 x 20 8154 <_main. CRTStartup+0 x 54> r 3, #34 ; 0 x 22 r 3, #39 ; 0 x 27 r 2, r 3 r 2, #32 ; 0 x 20 r 1, #1 ; 0 x 1 sp!, {r 1} r 0, #1 ; 0 x 1 r 3, [r 1], #1 r 3, #0 ; 0 x 0 81 a 8 <_main. CRTStartup+0 xa 8> r 2, r 3 8184 <_main. CRTStartup+0 x 84> r 2, #0 ; 0 x 0 r 3, r 1, #1 ; 0 x 1 r 2, [r 3] 8154 <_main. CRTStartup+0 x 54> r 1, sp r 2, sp, r 0, lsl #2 r 3, sp r 2, r 3 r 4, [r 2, # 4] 66

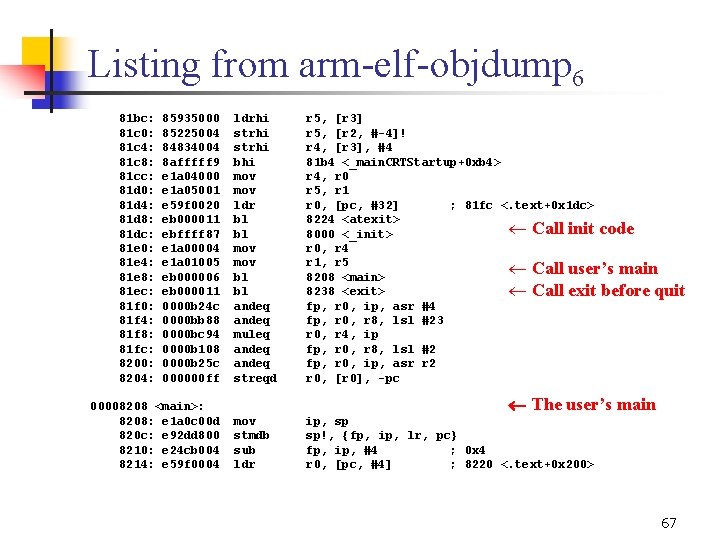
Listing from arm elf objdump 6 81 bc: 81 c 0: 81 c 4: 81 c 8: 81 cc: 81 d 0: 81 d 4: 81 d 8: 81 dc: 81 e 0: 81 e 4: 81 e 8: 81 ec: 81 f 0: 81 f 4: 81 f 8: 81 fc: 8200: 8204: 85935000 85225004 84834004 8 afffff 9 e 1 a 04000 e 1 a 05001 e 59 f 0020 eb 000011 ebffff 87 e 1 a 00004 e 1 a 01005 eb 000006 eb 000011 0000 b 24 c 0000 bb 88 0000 bc 94 0000 b 108 0000 b 25 c 000000 ff 00008208 <main>: 8208: e 1 a 0 c 00 d 820 c: e 92 dd 800 8210: e 24 cb 004 8214: e 59 f 0004 ldrhi strhi bhi mov ldr bl bl mov bl bl andeq muleq andeq streqd r 5, [r 3] r 5, [r 2, # 4]! r 4, [r 3], #4 81 b 4 <_main. CRTStartup+0 xb 4> r 4, r 0 r 5, r 1 r 0, [pc, #32] ; 81 fc <. text+0 x 1 dc> 8224 <atexit> ¬ Call init code 8000 <_init> r 0, r 4 r 1, r 5 ¬ Call user’s main 8208 <main> 8238 <exit> ¬ Call exit before quit fp, r 0, ip, asr #4 fp, r 0, r 8, lsl #23 r 0, r 4, ip fp, r 0, r 8, lsl #2 fp, r 0, ip, asr r 2 r 0, [r 0], pc The user’s main mov stmdb sub ldr ip, sp sp!, {fp, ip, lr, pc} fp, ip, #4 ; 0 x 4 r 0, [pc, #4] ; 8220 <. text+0 x 200> 67

Listing from arm elf objdump 7 8218: eb 000056 821 c: e 89 da 800 8220: 0000 b 124 00008224 <atexit>: 8224: e 1 a 01000 8228: e 3 a 00000 822 c: e 1 a 02000 8230: e 1 a 03000 8234: ea 000264 00008238 <exit>: 8238: e 92 d 4010 823 c: e 3 a 01000 8240: e 1 a 04000 8244: eb 000297 8248: e 59 f 3018 824 c: e 5930000 8250: e 590203 c 8254: e 3520000 8258: 11 a 0 e 00 f 825 c: 112 fff 12 8260: e 1 a 00004 8264: eb 000233 8268: 0000 b 134 bl ldmia andeq 8378 <puts> sp, {fp, sp, pc} fp, r 0, r 4, lsr #2 mov mov b r 1, r 0, #0 ; 0 x 0 r 2, r 0 r 3, r 0 8 bcc <__register_exitproc> Code on exit stmdb mov bl ldr ldr cmp movne bxne mov bl andeq sp!, {r 4, lr} r 1, #0 ; 0 x 0 r 4, r 0 8 ca 8 <__call_exitprocs> r 3, [pc, #24] ; 8268 <. text+0 x 248> r 0, [r 3] r 2, [r 0, #60] r 2, #0 ; 0 x 0 lr, pc r 2 r 0, r 4 8 b 38 <_exit> fp, r 0, r 4, lsr r 1 68

Starting a C Program n To get to main() takes hundreds of instructions! l l l In a modern OS, it can take several thousands of instructions! Why? Because the C compiler generates code for a number of setup routines before the call to main(). These setup routines handle the stack, data segments, heap and other miscellaneous functions. 69

Starting an Assembly Program n What about assembly code? l l n If the assembly code interfaces to C code and the ENTRY point is the C function main(), then the C compiler will generate the setup code But, if the entire program is written in assembly OR there is no C function called main(), then the setup code is not generated. What does this mean for you? l What's the SP register pointing to when you start your program? 70

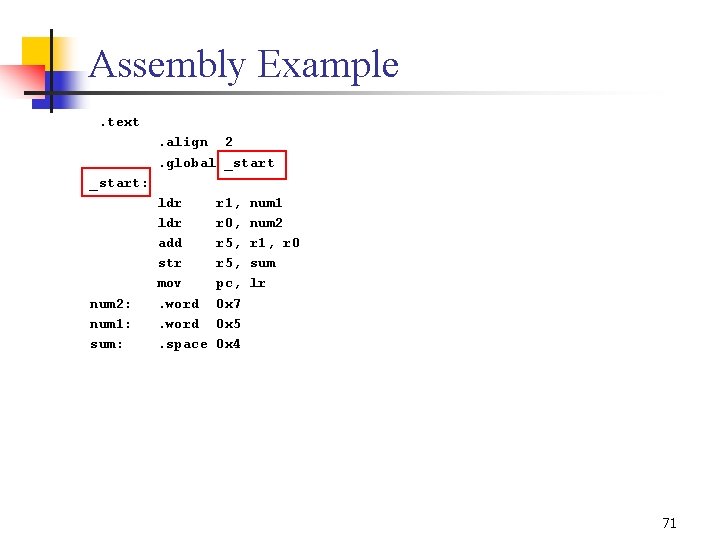
Assembly Example. text. align 2. global _start: num 2: num 1: sum: ldr add str mov. word. space r 1, r 0, r 5, pc, 0 x 7 0 x 5 0 x 4 num 1 num 2 r 1, r 0 sum lr 71

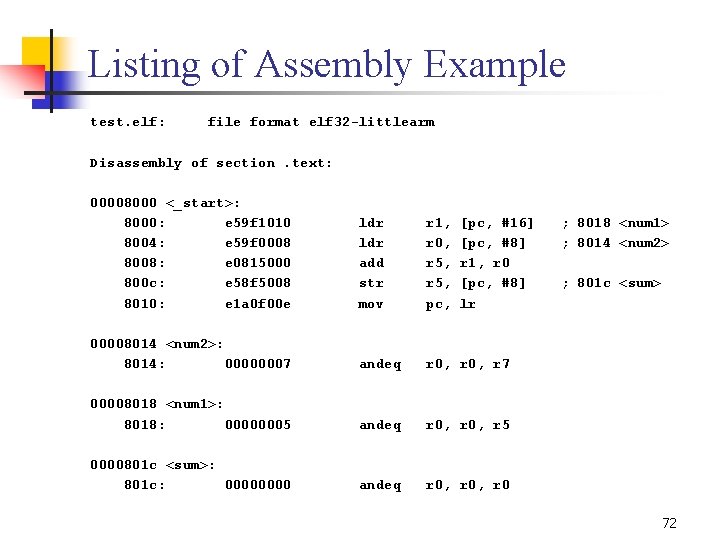
Listing of Assembly Example test. elf: file format elf 32 littlearm Disassembly of section. text: 00008000 <_start>: 8000: e 59 f 1010 8004: e 59 f 0008 8008: e 0815000 800 c: e 58 f 5008 8010: e 1 a 0 f 00 e ldr add str mov r 1, r 0, r 5, pc, 00008014 <num 2>: 8014: 00000007 andeq r 0, r 7 00008018 <num 1>: 8018: 00000005 andeq r 0, r 5 0000801 c <sum>: 801 c: 0000 andeq r 0, r 0 [pc, #16] [pc, #8] r 1, r 0 [pc, #8] lr ; 8018 <num 1> ; 8014 <num 2> ; 801 c <sum> 72