Connectivity between WAN and Microsoft Logical Diagram Routing

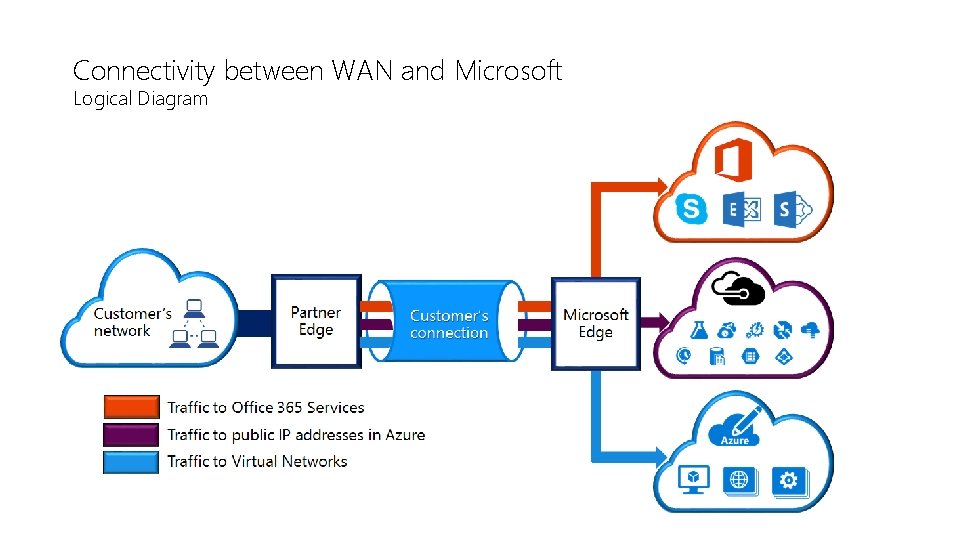
Connectivity between WAN and Microsoft Logical Diagram
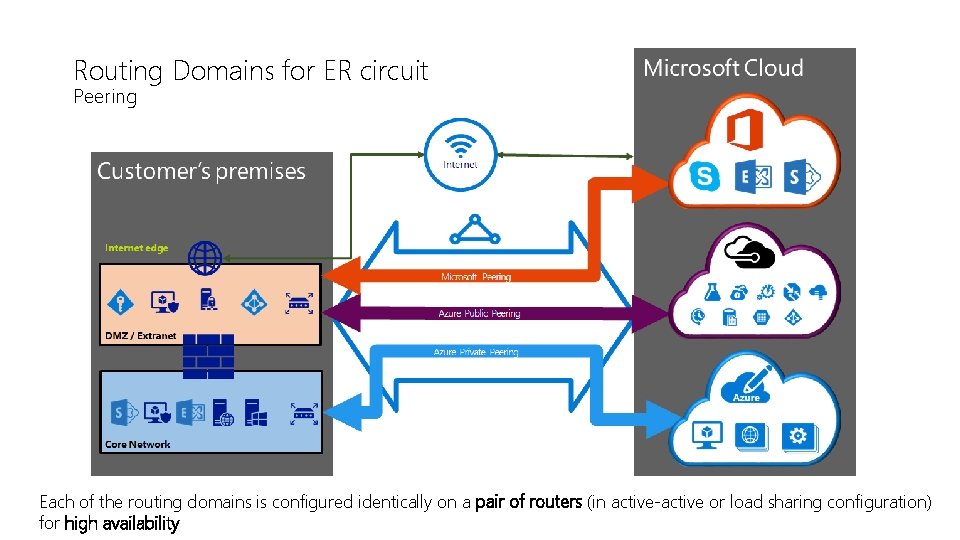
Routing Domains for ER circuit Peering Each of the routing domains is configured identically on a pair of routers (in active-active or load sharing configuration) for high availability
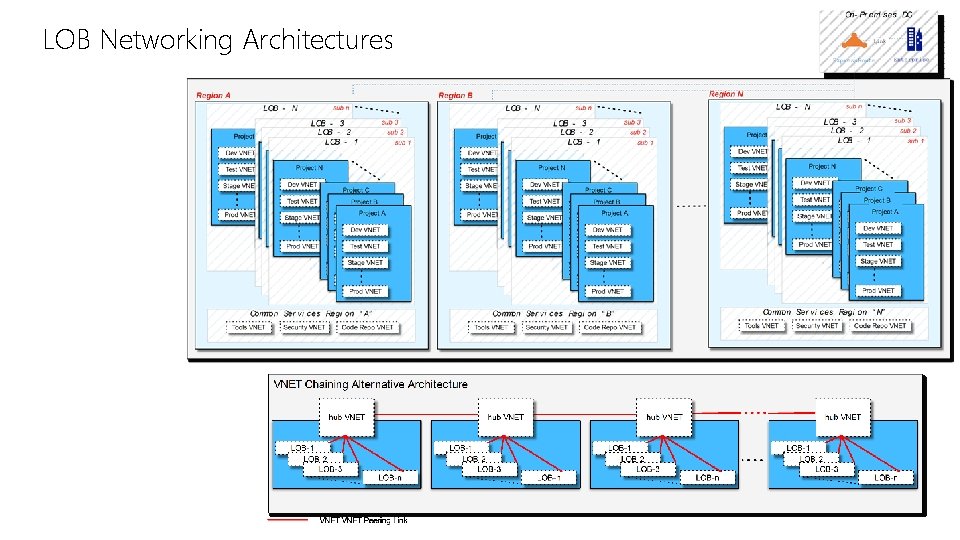
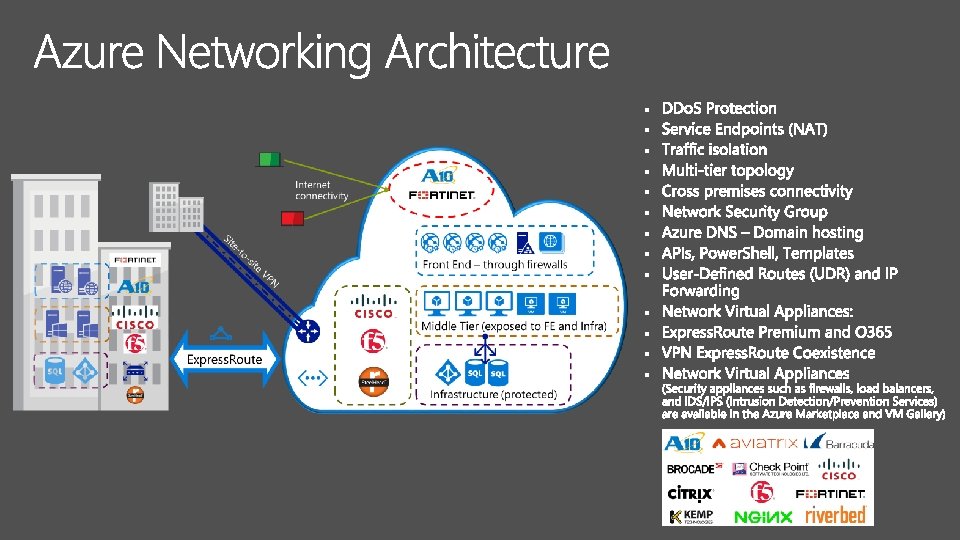
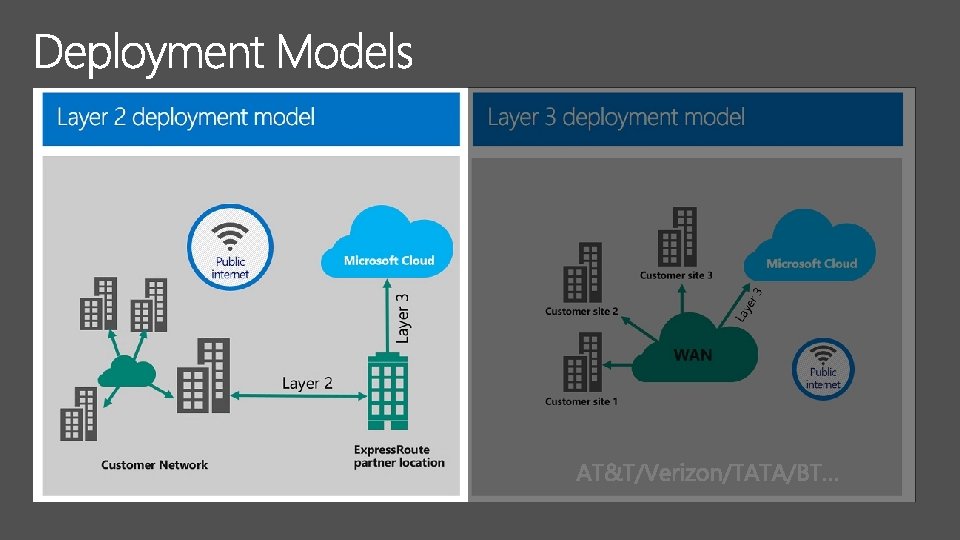
LOB Networking Architectures
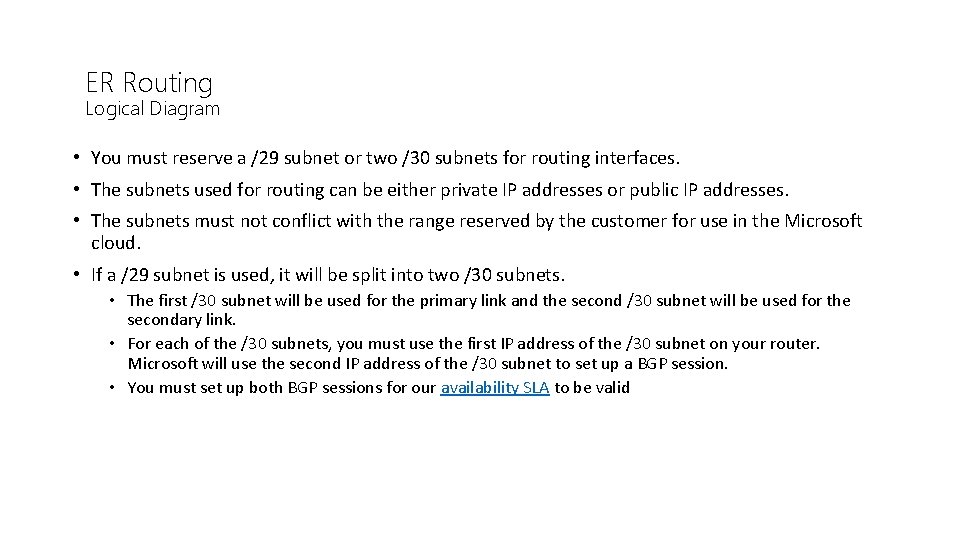
ER Routing Logical Diagram • You must reserve a /29 subnet or two /30 subnets for routing interfaces. • The subnets used for routing can be either private IP addresses or public IP addresses. • The subnets must not conflict with the range reserved by the customer for use in the Microsoft cloud. • If a /29 subnet is used, it will be split into two /30 subnets. • The first /30 subnet will be used for the primary link and the second /30 subnet will be used for the secondary link. • For each of the /30 subnets, you must use the first IP address of the /30 subnet on your router. Microsoft will use the second IP address of the /30 subnet to set up a BGP session. • You must set up both BGP sessions for our availability SLA to be valid
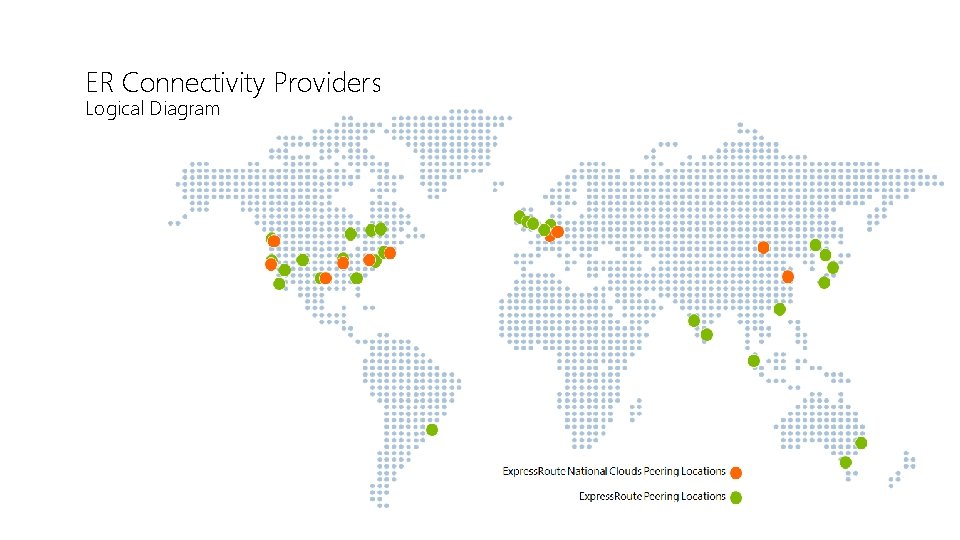
ER Connectivity Providers Logical Diagram
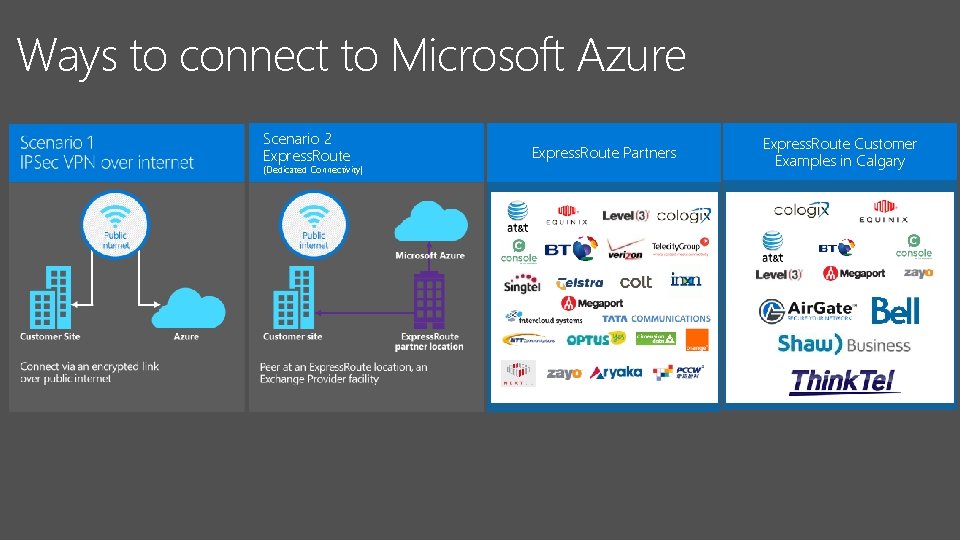
Ways to connect to Microsoft Azure Scenario 2 Express. Route (Dedicated Connectivity) Express. Route Partners Express. Route Customer Examples in Calgary
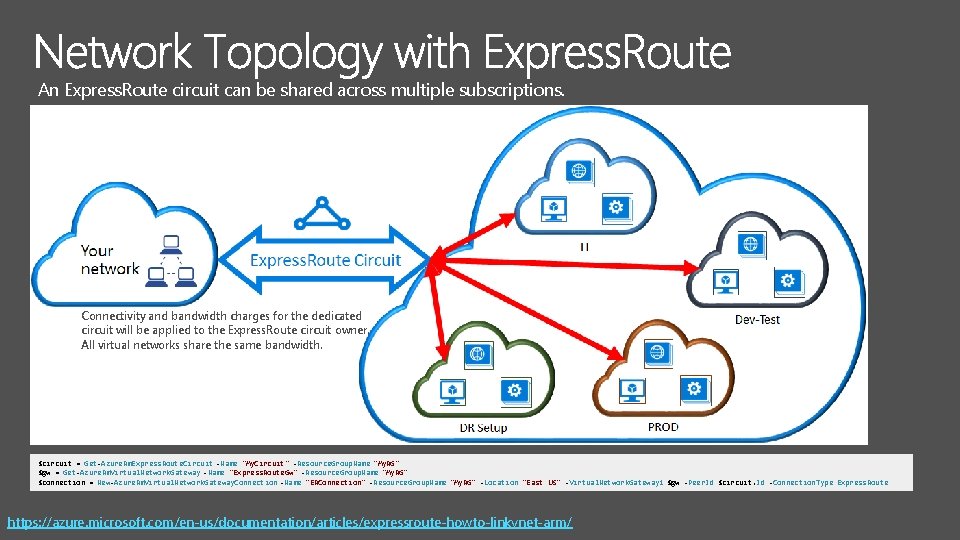
An Express. Route circuit can be shared across multiple subscriptions. Connectivity and bandwidth charges for the dedicated circuit will be applied to the Express. Route circuit owner. All virtual networks share the same bandwidth. $circuit = Get-Azure. Rm. Express. Route. Circuit -Name "My. Circuit" -Resource. Group. Name "My. RG" $gw = Get-Azure. Rm. Virtual. Network. Gateway -Name "Express. Route. Gw" -Resource. Group. Name "My. RG" $connection = New-Azure. Rm. Virtual. Network. Gateway. Connection -Name "ERConnection" -Resource. Group. Name "My. RG" -Location "East US" -Virtual. Network. Gateway 1 $gw -Peer. Id $circuit. Id -Connection. Type Express. Route https: //azure. microsoft. com/en-us/documentation/articles/expressroute-howto-linkvnet-arm/
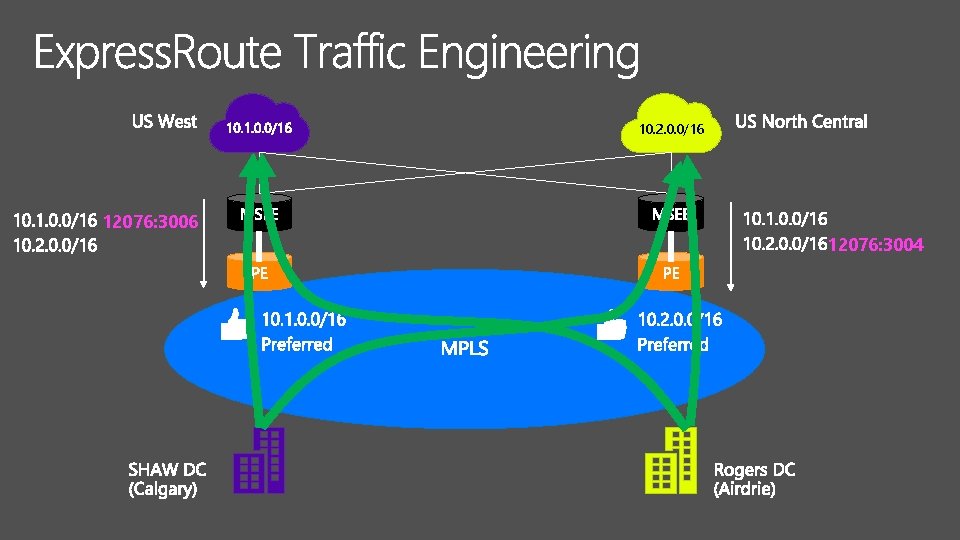
10. 2. 0. 0/16 12076: 3004
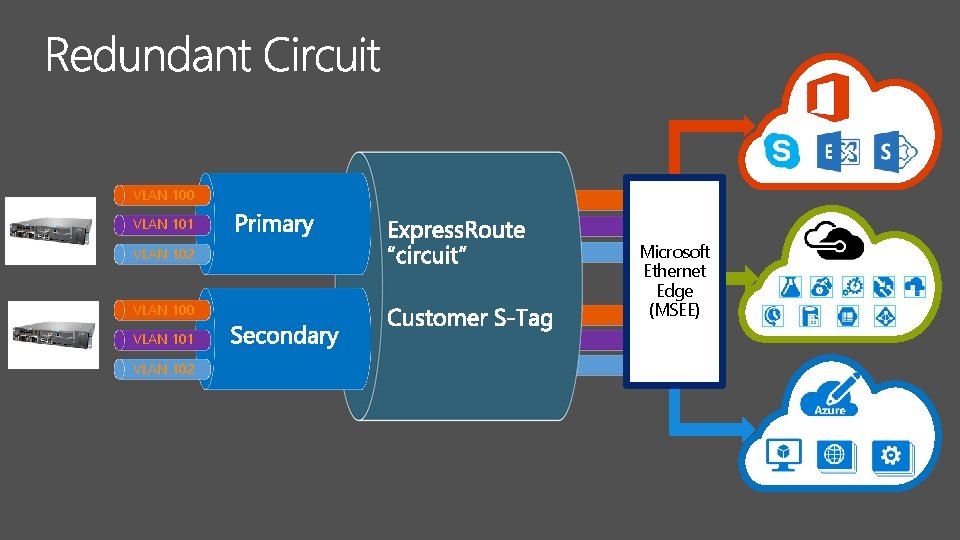
VLAN 100 VLAN 101 VLAN 102 Microsoft Ethernet Edge (MSEE)
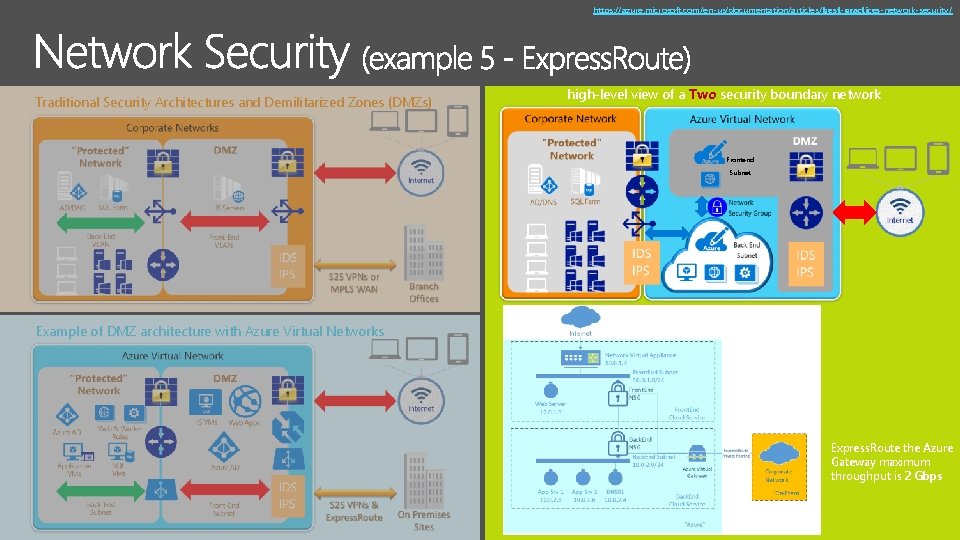
https: //azure. microsoft. com/en-us/documentation/articles/best-practices-network-security/ Traditional Security Architectures and Demilitarized Zones (DMZs) high-level view of a Two security boundary network Frontend Subnet Example of DMZ architecture with Azure Virtual Networks Express. Route the Azure Gateway maximum throughput is 2 Gbps
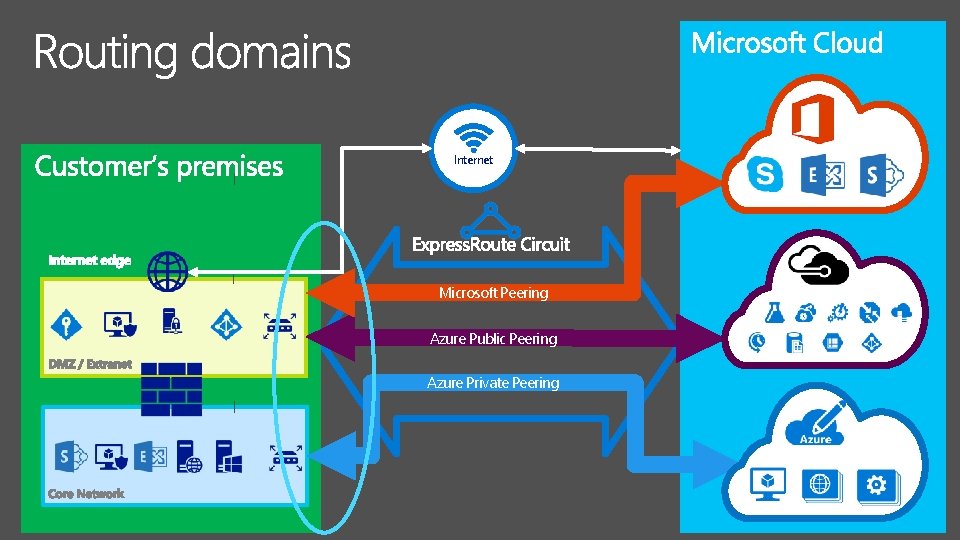
Internet Microsoft Peering Azure Public Peering Azure Private Peering
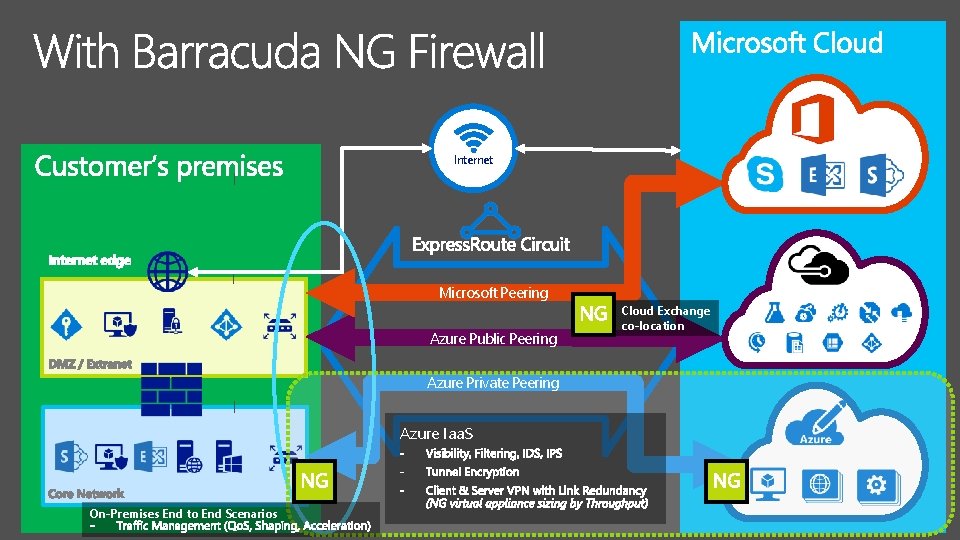
Internet Microsoft Peering Azure Public Peering Azure Private Peering Azure Iaa. S On-Premises End to End Scenarios Cloud Exchange co-location

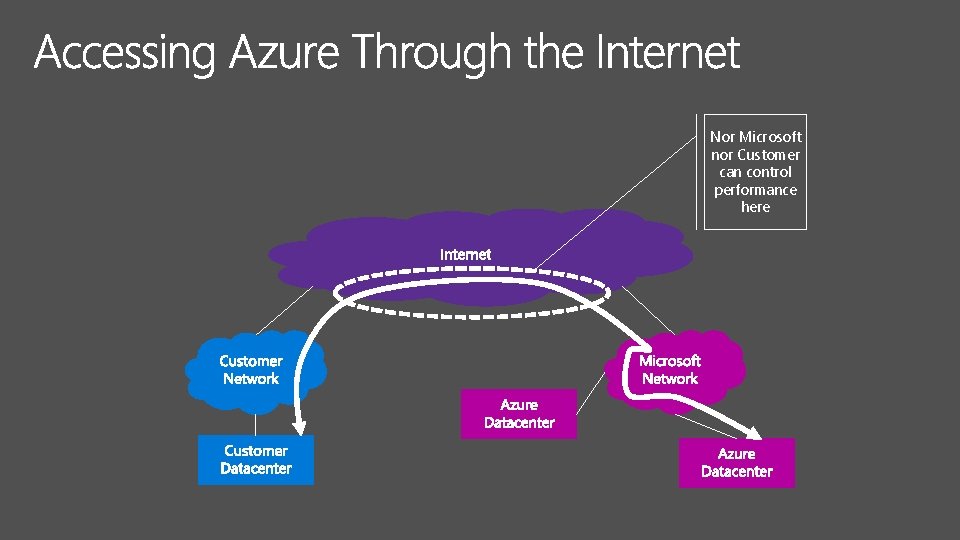
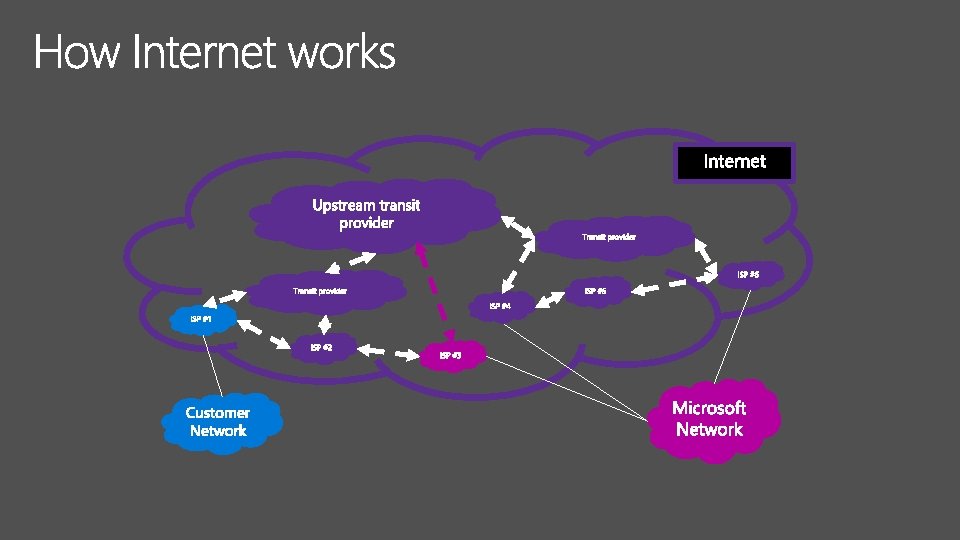
Nor Microsoft nor Customer can control performance here
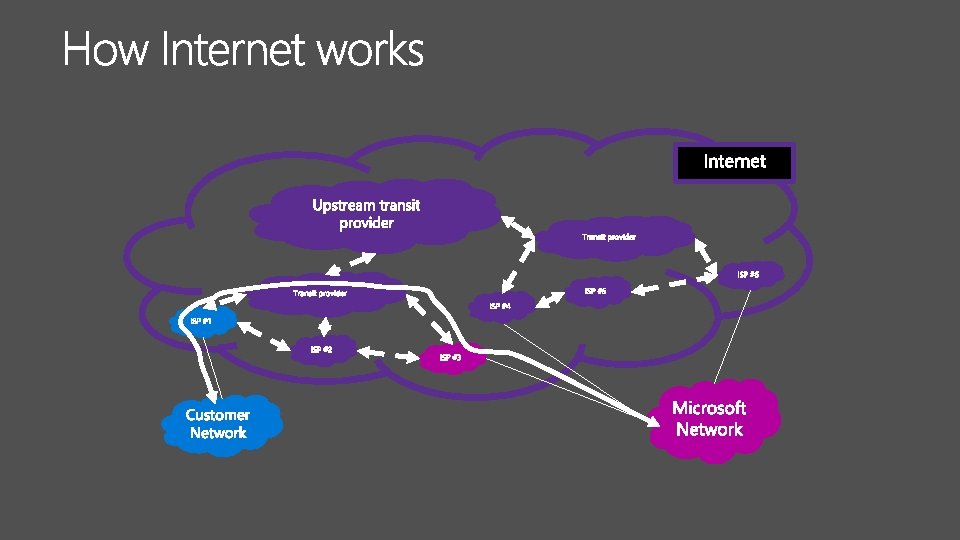
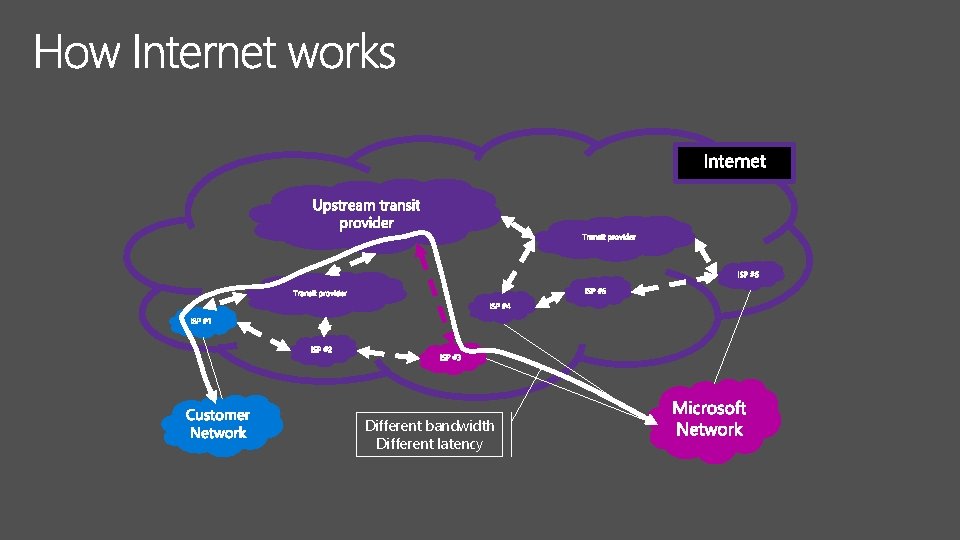
Different bandwidth Different latency
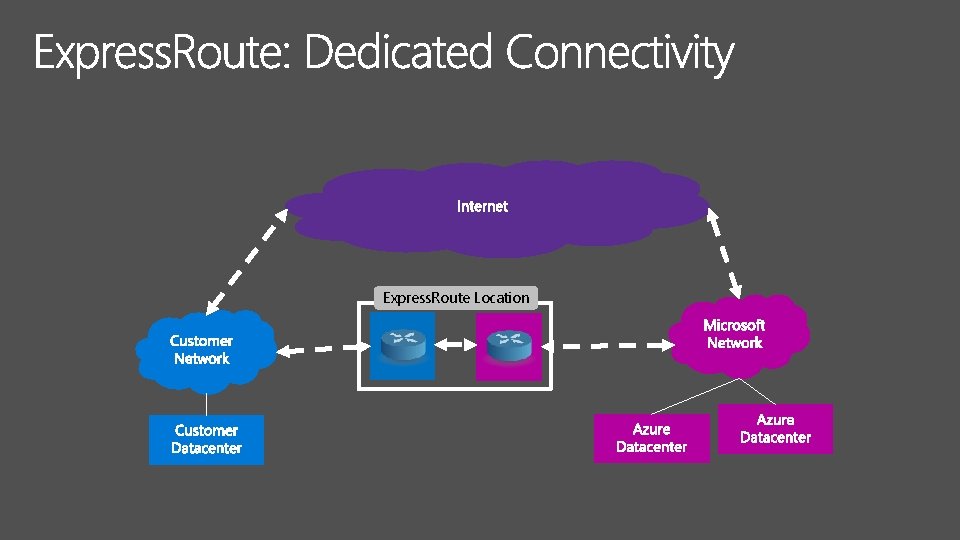
Express. Route Location
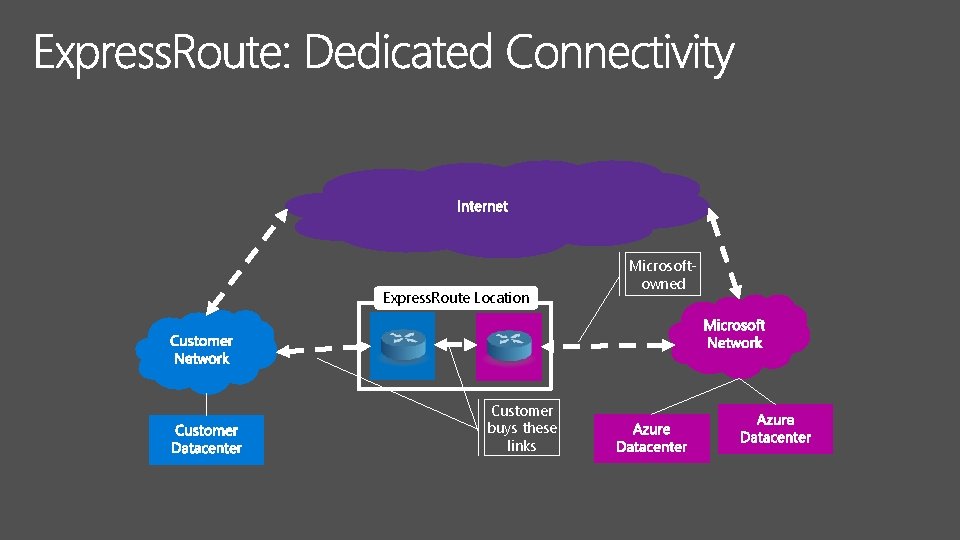
Express. Route Location Customer buys these links Microsoftowned
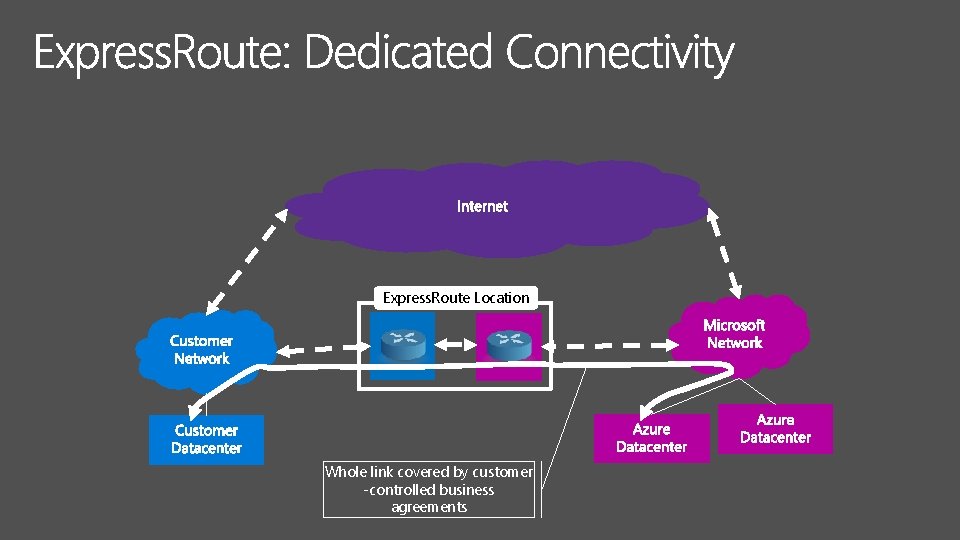
Express. Route Location Whole link covered by customer -controlled business agreements
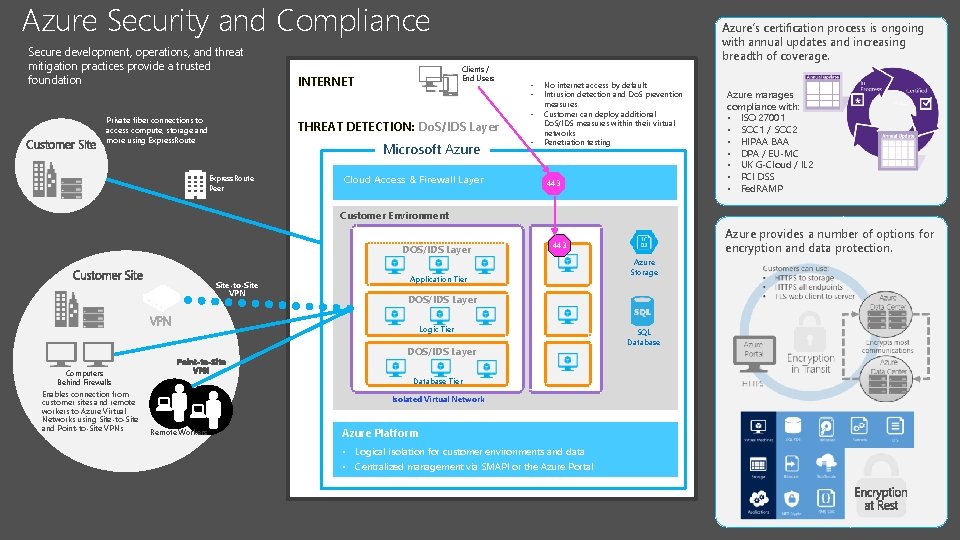
Azure Security and Compliance Secure development, operations, and threat mitigation practices provide a trusted foundation Clients / End Users INTERNET Azure’s certification process is ongoing with annual updates and increasing breadth of coverage. • • • Private fiber connections to access compute, storage and more using Express. Route THREAT DETECTION: Do. S/IDS Layer Microsoft Azure Express. Route Peer Cloud Access & Firewall Layer • No internet access by default Intrusion detection and Do. S prevention measures Customer can deploy additional Do. S/IDS measures within their virtual networks Penetration testing 443 Azure manages compliance with: • ISO 27001 • SOC 1 / SOC 2 • HIPAA BAA • DPA / EU-MC • UK G-Cloud / IL 2 • PCI DSS • Fed. RAMP Customer Environment DOS/IDS Layer Site-to-Site VPN Application Tier Logic Tier DOS/IDS Layer Database Tier Isolated Virtual Network Remote Workers Azure Storage DOS/IDS Layer VPN Computers Behind Firewalls Enables connection from customer sites and remote workers to Azure Virtual Networks using Site-to-Site and Point-to-Site VPNs Azure provides a number of options for encryption and data protection. 443 Azure Platform • Logical isolation for customer environments and data • Centralized management via SMAPI or the Azure Portal SQL Database
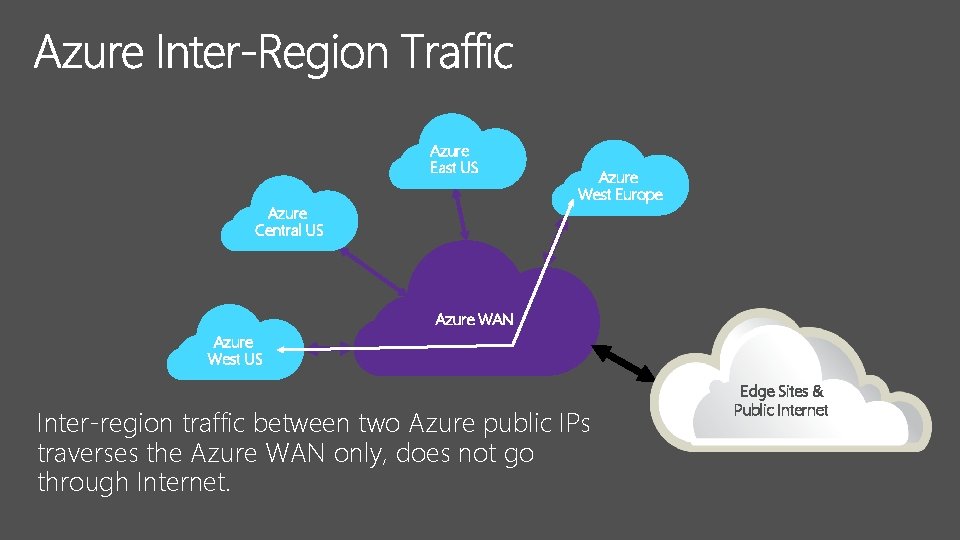
Azure East US Azure Central US Azure West Europe Azure WAN Azure West US Inter-region traffic between two Azure public IPs traverses the Azure WAN only, does not go through Internet. Edge Sites & Public Internet
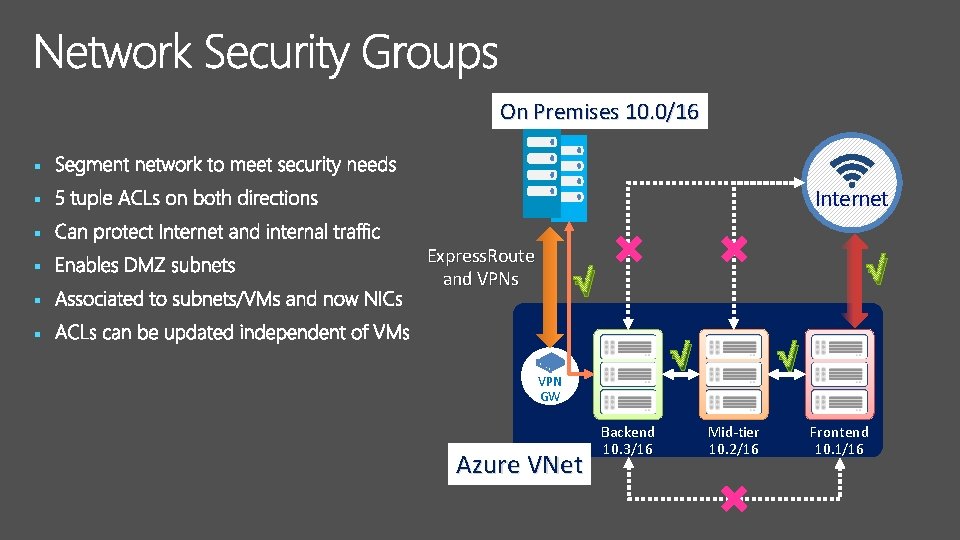
On Premises 10. 0/16 § Internet § § Express. Route and VPNs √ √ § √ VPN GW Azure VNet Backend 10. 3/16 √ Mid-tier 10. 2/16 Frontend 10. 1/16

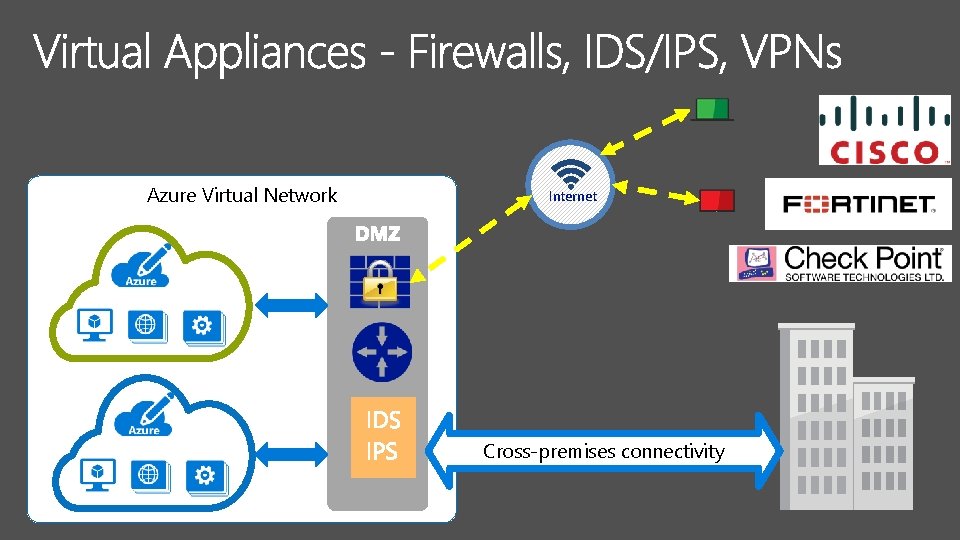
Azure Virtual Network Internet Cross-premises connectivity
- Slides: 32