Connected and Autonomous Vehicles Supply Chain Security Dr















- Slides: 23

Connected and Autonomous Vehicles Supply Chain Security Dr Paul Martin CTO

Contents • A View of the Supply Chain • Technical Issues • Commercial Issues • Risk Management

Contents • A View of the Supply Chain • Technical Issues • Commercial Issues • Risk Management

Traditional Supply Chain OEM Tier 1 Tier 2

Additions to Supply Chain for CAV Traditional Supply Chain Plus Communication Network Operators • Mobile Network Operators • Public Wifi networks • Satellite providers • Other Vehicles (V 2 V) Data Providers and Acquirers • Vehicle is now one part of a wider commercially-oriented system

Contents • A View of the Supply Chain • Technical Issues • Commercial Issues • Risk Management

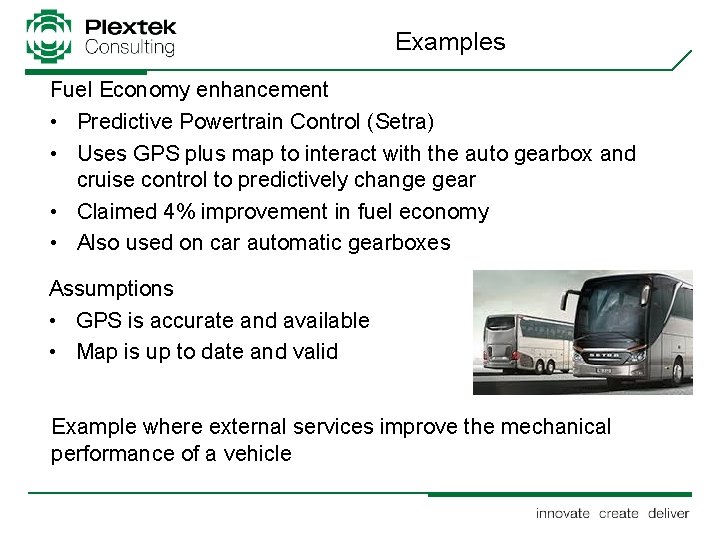
Examples Fuel Economy enhancement • Predictive Powertrain Control (Setra) • Uses GPS plus map to interact with the auto gearbox and cruise control to predictively change gear • Claimed 4% improvement in fuel economy • Also used on car automatic gearboxes Assumptions • GPS is accurate and available • Map is up to date and valid Example where external services improve the mechanical performance of a vehicle

Examples Securing the Chain of Supply How do I verify that the vehicle rolling off the production line has the correct hardware and correct software? • Recognise counterfeit or incorrect components • Recognise incorrect or modified software • This has to span the supply chain and work across worldwide design and manufacturing centres

Examples Securing the Vehicle after Supply As bugs and vulnerabilities are discovered, how do they get fixed? How does a driver/passenger know their vehicle is cyber secure? How is data from the extended CAV supply chain verified? • • OEM, Tier 1, Tier 2 could cooperate to fix Over The Air (OTA) software download helps Who is responsible and who is paying? Does government need to legislate (Cyber MOT? )

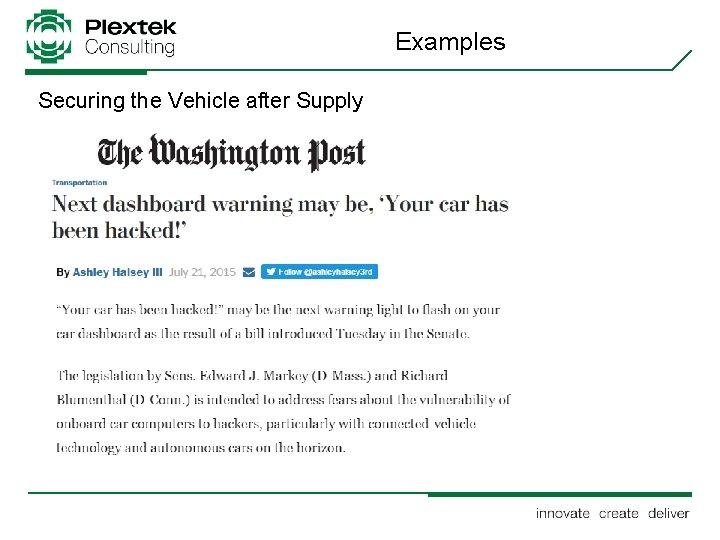
Examples Securing the Vehicle after Supply

Contents • A View of the Supply Chain • Technical Issues • Commercial Issues • Risk Management

Vested Interests • • • Car OEMs Truck OEMs Intelligent Traffic System OEMs Emergency Services Insurance Companies Legal Industry Commerce Government Departments International Standardisation

Commercial Issues – Supply Chain Traditional Supply Chain (Tier 1 s and Tier 2 s to OEMs) • Business is very competitive • Global Competition • Sometimes Dutch auctions used Result • Tier 1 and Tier 2 suppliers forced to exploit aggressive cost saving • Innovation very difficult • Market discourages future proofing capability

The Importance of Data Commercial Global Mobile Internet Advertising Revenue 2012 - $8. 76 Bn 2013 - $17. 96 Bn (Google 50%, Facebook 17. 5%) 2014 - $31. 45 Bn Source: e. Marketing Autonomous vehicles can increase advertising revenue

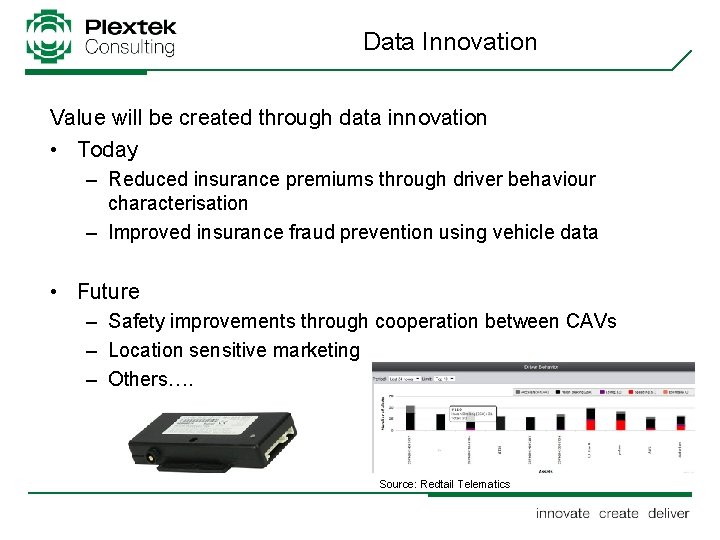
Data Innovation Value will be created through data innovation • Today – Reduced insurance premiums through driver behaviour characterisation – Improved insurance fraud prevention using vehicle data • Future – Safety improvements through cooperation between CAVs – Location sensitive marketing – Others…. Source: Redtail Telematics

Contents • A View of the Supply Chain • Technical Issues • Commercial Issues • Risk Management

Risk Management Risks • Design Assumptions – The XXX system is always working-no exception handling needed – Examples • GNSS jamming • GNSS spoofing • GPS on 26 th Jan 2016 • Answer – Increased rigour in design reviews – Ensure design reviews cover external interface vulnerabilities

Risk Management Risks • Threats – Commercial – Vehicles and their cargo are high value items in society and attract attention – Transport and vehicle data is increasing in commercial value and is attracting attention – The benefits of CAV will improve traffic flow. Disrupting CAV technology operation will have an effect much larger than today’s traffic jams – Answer – ensure that the commercial value of the threat is reviewed regularly and appropriate risk reduction taken

Exceptions • What happens when things go wrong? 1) What if this was caused by a malicious cyber attack? • • • Economic gain - eg extortion Impact - eg terrorism For “fun”

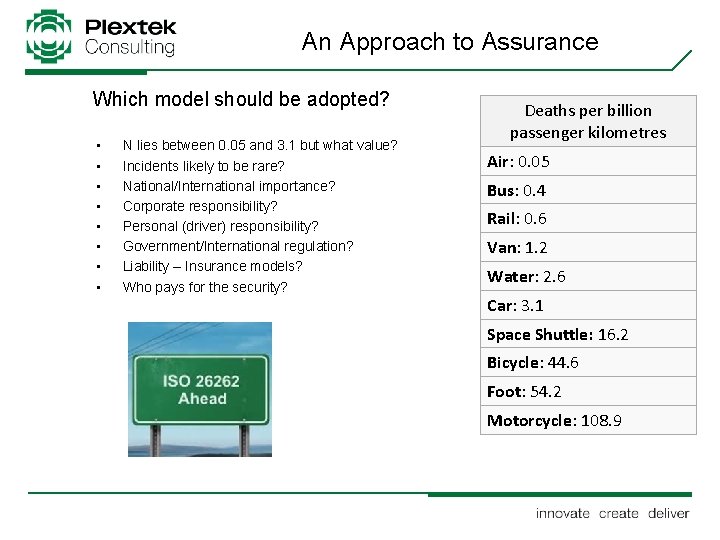
An Approach to Assurance Which model should be adopted? • • N lies between 0. 05 and 3. 1 but what value? Incidents likely to be rare? National/International importance? Corporate responsibility? Personal (driver) responsibility? Government/International regulation? Liability – Insurance models? Who pays for the security? Deaths per billion passenger kilometres Air: 0. 05 Bus: 0. 4 Rail: 0. 6 Van: 1. 2 Water: 2. 6 Car: 3. 1 Space Shuttle: 16. 2 Bicycle: 44. 6 Foot: 54. 2 Motorcycle: 108. 9

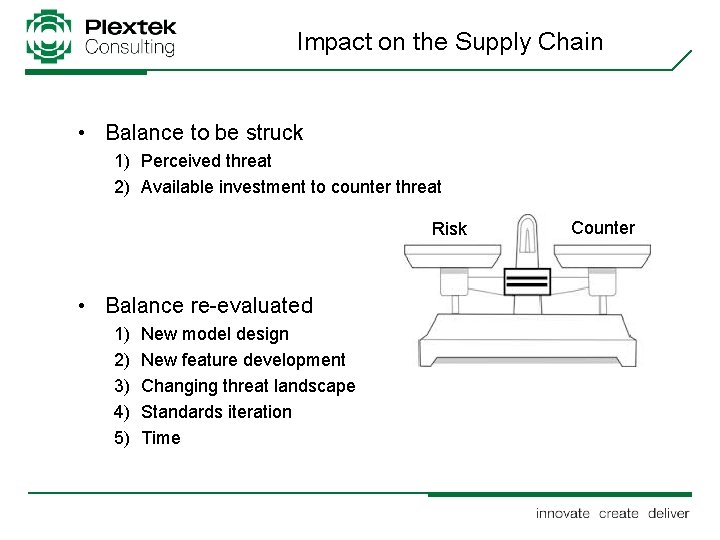
Impact on the Supply Chain • Balance to be struck 1) Perceived threat 2) Available investment to counter threat Risk • Balance re-evaluated 1) 2) 3) 4) 5) New model design New feature development Changing threat landscape Standards iteration Time Counter

Thank You Dr Paul Martin CTO Plextek Consulting

World class Products, Systems and Services • Innovative, Independent, Entrepreneurial • Based near Cambridge, UK • Part of Plextek Group • Privately owned - established 1989 • 200 staff • Markets • Automotive and Transport • Defence and Security • Healthcare • IOT • Wearable Devices