Conformity Performance ISO 28000 ISO 28000 Security Management
























- Slides: 36

Conformity & Performance ISO 28000

ISO 28000 – Security Management System The security of the business operations NOT the security operations of the business • Unless this is the required objective.

Common terms of reference Conformance & Performance conformity or conformance • compliance in actions, behaviour, etc, with certain standards or norms • correspondence or likeness in form or appearance; congruity; agreement performance • manner or quality of functioning • any accomplishment Collins English Dictionary - Complete & Unabridged 10 th Edition

Security Performance Security is a performance issue Security must be addressing the needs of the organisation: • • Proactive in addressing plausible security issues • Alert to changes in organisational security risks • Responsive to changing organisational security objectives • Security management activities must be fit for purpose, in situ and for meeting security targets SECURITY PERFORMANCE MUST MEET OR EXCEED THE SECURITY REQUIREMENTS OF THE ORGANISATION – Not just conform to a predefined set of instruments

What is ISO 28000 • A Security Management System that defines best practice methodologies for managing organisational security needs. • Four overarching requirements of any security program A. Consistent with business model and objectives B. Legal and statutory compliance C. Identification and understanding of security risks D. Management of the security risks • ISO 28000 allows any organisation, public or private, large or small, to meet these requirements in a structured and systematic manner – facilitating program reliability and consistent performance.

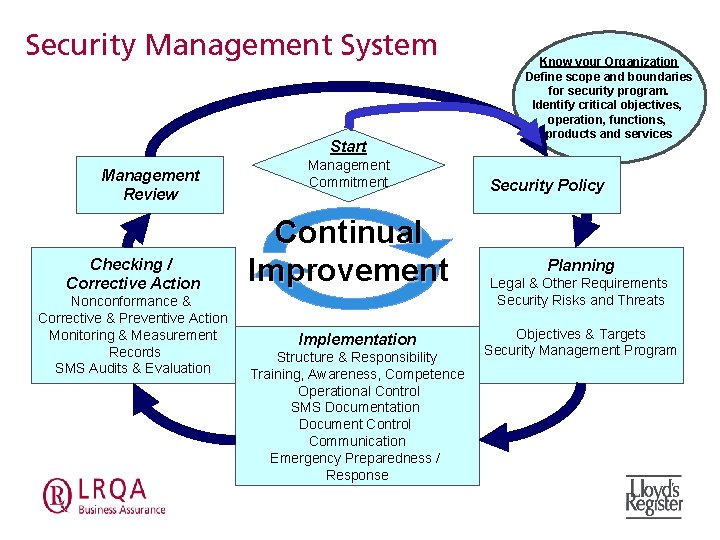
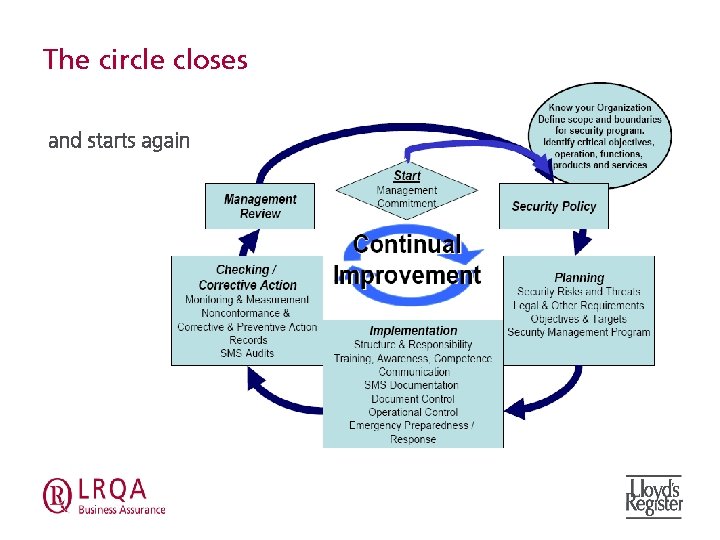
Security Management System Start Management Review Checking / Corrective Action Nonconformance & Corrective & Preventive Action Monitoring & Measurement Records SMS Audits & Evaluation Management Commitment Continual Improvement Implementation Structure & Responsibility Training, Awareness, Competence Operational Control SMS Documentation Document Control Communication Emergency Preparedness / Response Know your Organization Define scope and boundaries for security program. Identify critical objectives, operation, functions, products and services Security Policy Planning Legal & Other Requirements Security Risks and Threats Objectives & Targets Security Management Program

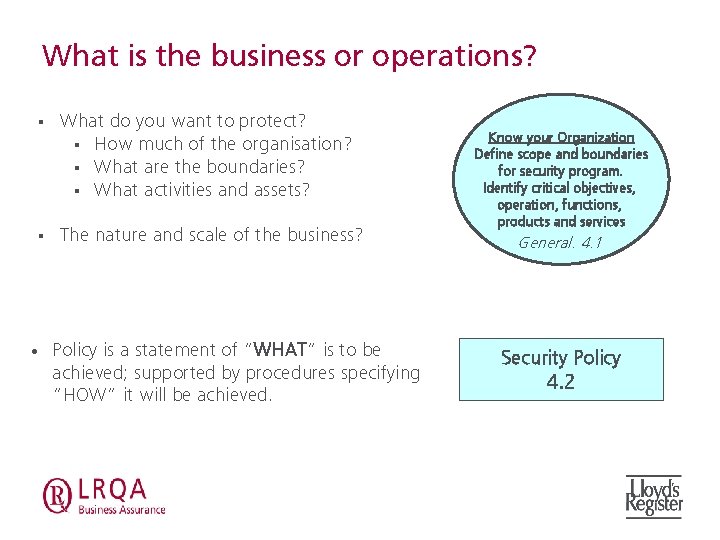
What is the business or operations? § § • What do you want to protect? § How much of the organisation? § What are the boundaries? § What activities and assets? The nature and scale of the business? Policy is a statement of “WHAT” is to be achieved; supported by procedures specifying “HOW” it will be achieved. Know your Organization Define scope and boundaries for security program. Identify critical objectives, operation, functions, products and services General. 4. 1 Security Policy 4. 2

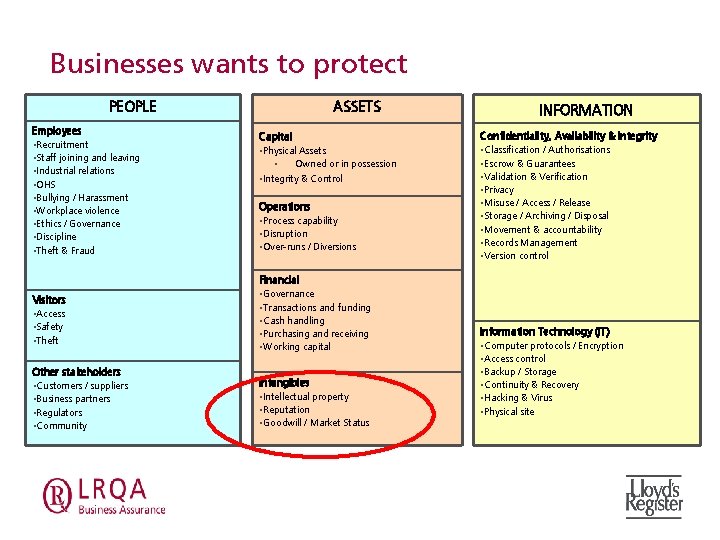
Businesses wants to protect PEOPLE Employees • Recruitment • Staff joining and leaving • Industrial relations • OHS • Bullying / Harassment • Workplace violence • Ethics / Governance • Discipline • Theft & Fraud ASSETS INFORMATION Capital Confidentiality, Availability & Integrity • Physical • Classification Assets Owned or in possession • Integrity & Control • Operations • Process capability • Disruption • Over-runs / Diversions / Authorisations & Guarantees • Validation & Verification • Privacy • Misuse / Access / Release • Storage / Archiving / Disposal • Movement & accountability • Records Management • Version control • Escrow Financial Visitors • Access • Safety • Theft • Governance • Transactions and funding handling • Purchasing and receiving • Working capital • Cash Information Technology (IT) • Computer protocols / Encryption control • Backup / Storage • Continuity & Recovery • Hacking & Virus • Physical site • Access Other stakeholders • Customers / suppliers • Business partners • Regulators • Community Intangibles • Intellectual property • Reputation • Goodwill / Market Status

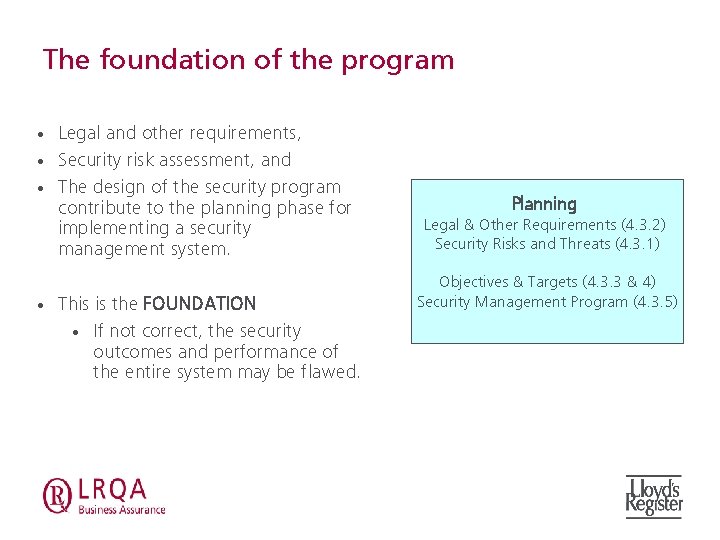
The foundation of the program • • Legal and other requirements, Security risk assessment, and The design of the security program contribute to the planning phase for implementing a security management system. This is the FOUNDATION • If not correct, the security outcomes and performance of the entire system may be flawed. Planning Legal & Other Requirements (4. 3. 2) Security Risks and Threats (4. 3. 1) Objectives & Targets (4. 3. 3 & 4) Security Management Program (4. 3. 5)

What Legal requirements? • Legal and other requirements to which the organisation is bound or subscribes to. • Statue Law Planning • Traffic and parking laws Legal & Other Requirements (4. 3. 2) • Firearms laws • Privacy laws • Security licensing laws & regulations • Signage and safety laws/regulations • Government schemes i. e. PS Prep, TSA – Secure Freight, FDA – Pharma security, etc. • International Conventions • Industry codes/standards

Security Risk Assessments Overall process of risk identification, risk analysis and risk evaluation (ISO Guide 73 – Risk Management, Vocabulary) • • A procedure detailing how security risks are identified, assessed, and evaluated, including threats to and from stakeholders. • Risk assessments shall be conducted by qualified personnel using recognised methodologies. • The methodology and grading criterion shall be documented, allowing for a consistently applied process. • Plausible threats have been identified and risks evaluated. Results of security risk assessments shall be documented and provided input to other areas of the Security Management System.

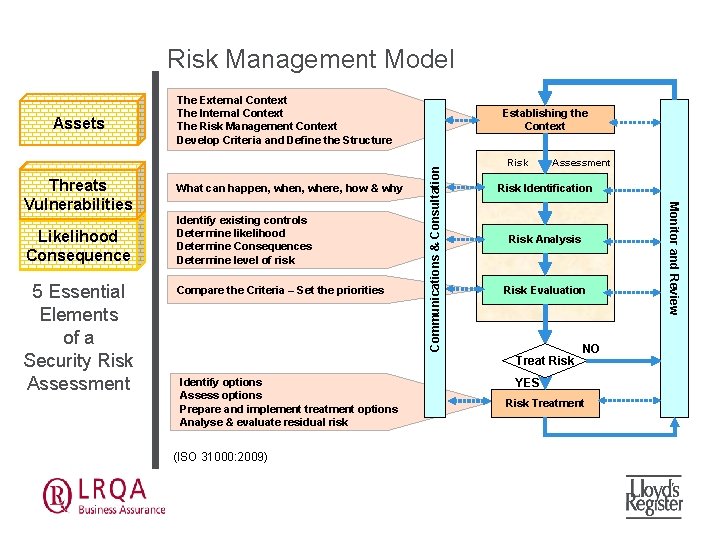
Risk Management Model Likelihood Consequence 5 Essential Elements of a Security Risk Assessment What can happen, where, how & why Identify existing controls Determine likelihood Determine Consequences Determine level of risk Compare the Criteria – Set the priorities Risk Assessment Risk Identification Risk Analysis Risk Evaluation Treat Risk Identify options Assess options Prepare and implement treatment options Analyse & evaluate residual risk (ISO 31000: 2009) NO YES Risk Treatment Monitor and Review Threats Vulnerabilities Establishing the Context Communications & Consultation Assets The External Context The Internal Context The Risk Management Context Develop Criteria and Define the Structure

Security Management Objectives, Targets & Programs The security risks identified through the assessment – lead to; • What risks require attention? • Where does it need to happen? • What security outcomes are sought? • When does it need to happen? • How will we manage the risk? Planning Objectives & Targets (4. 3. 3 & 4) Security Management Program (4. 3. 5)

Setting objectives Identified security risks in operational areas are prioritised • A determination of the desired improvement for each risk. Some options include; • Reduce the security risk? • Reduce the likelihood? • Reduce the consequence? • Accept the risk? • Transfer the risk? • Improve incident management? • Improve business performance? • Cost and resource improvement?

How to achieve this security? • Who is accountable? • Who has responsibilities? • Can they do the job? • Authorities required at different levels? • Competence • What security tools are needed? • Preparations for security emergencies? • How is the security program captured? Implementation Structure & Responsibility (4. 4. 1) Training, Awareness, Competence (4. 4. 2) Operational Control (4. 4. 6) SMS Documentation (4. 4. 4) Document Control (4. 4. 5) Communication (4. 4. 3) Emergency Preparedness / Response (4. 4. 7)

Implementing the security program • Policy driven, protecting the business and based on legal requirements and identified security risks. • Programs address security objectives and targets. • The people are competent and authorised for the tasks. • Utilising “fit-for-purpose" security tools to manage the security. • With security emergency plans. • Security manual and/or procedures. • Communications and consultative processes. Implementation Structure & Responsibility (4. 4. 1) Training, Awareness, Competence (4. 4. 2) Operational Control (4. 4. 6) SMS Documentation (4. 4. 4) Document Control (4. 4. 5) Communication (4. 4. 3) Emergency Preparedness / Response (4. 4. 7)

Is the security working • Are the security programs effective? • Has security been enhanced? • Is the program proactive? • Are problems being identified, managed and rectified? • Adequate resources – to do the job? • The data needed to manage the system is recorded and managed? • Consistently compliant with obligations? • Confirmation of the security program and system performance? Checking / Corrective Action Nonconformance & Corrective & Preventive Action (4. 5. 3) Monitoring & Measurement (4. 5. 1) Records (4. 5. 4) SMS Audits (4. 5. 5) System Evaluation (4. 5. 2)

Management review and Continual Improvement • • Top management reviews the security management system at planned intervals. • Legal and stakeholder considerations reviewed. • Considers security and management systems performance and improvements • Discussions and decisions recorded. The review includes the mandatory inputs specified in ISO 28000: 2007 and opportunities for improvement or any need for change. Management Review

The circle closes and starts again

ISO 28000 Conformance + Performance Conformance • The specifications of the management system, require; • A security policy • Compliance with legal and regulatory requirements • An effective and accurate Security Risk Assessment • The development of security objectives and targets, as well as a planning process for meeting them. • The use of operational controls to manage the identified security risks • Audits and reviews • Top management involvement and continual improvement of the security management system and objectives. • Documentation of the program to ensure consistent application

ISO 28000 Conformance + Performance • Through the security management system, organisations are; • Applying security programs appropriate to the nature and scale of the organisation • Identifying and managing those security risks applicable to the site • Selecting and utilising operational controls that are fit for purpose, maintained and calibrated where required • Ensuring that operational controls address the security objectives of the organisation, these may include business processes and security tools. • Evaluating the performance and effectiveness of the security program • Consistently monitoring the security program and maintaining optimum performance or adjusting when conditions change. • Motivating top management involvement and continual improvement of the security program. • Maintaining the appropriate levels of security in a consistent manner.

Certification or Validation Certification to ISO 28000: 2007. (three year certificate) § § Two stage assessment process divided between; § Stage 1 Assessment § Stage 2 Assessment Followed by systematic ongoing surveillance to confirm conformance and performance of the security management system.

Certification - Stage 1 The Stage 1 will be a full assessment of the following: • Scope, Policy and Legal • Security Risk Assessment – Asset identification – Identification of threat sources – Consequence analysis – Vulnerability review and analysis – Likelihood evaluation • SRA methodology, including, criteria, risk grading and prioritization • Risk mitigation and planning – Management System “Objectives, Targets and Programs” • Planning of protective security measures [Operational Controls (procedures, personnel and technology)] for managing the security objectives and targets.

Certification - Stage 2 The Stage 2 visit confirms that: • The policies, objectives, controls and procedures are effectively in practice • The required management of significant security processes within the management system are effective • Operational controls meet the stated mitigation objectives and are fit for purpose • The management system conforms with all the requirements of ISO 28000, and that the documented procedures consistently ensure systematic performance and improvement. • The internal audits have evaluated the Security Management System and Top Management reviews support continual improvement.

Surveillance Once certified, the organisation must demonstrate continuing conformance and performance through surveillance visits, which normally take place every six months, but not exceeding 12 months. This surveillance process ensures that a security program if functional at all times, and • the organisation monitors and responds to changes in security risks and is capable of managing security incident or changes to threats, vulnerabilities and assets, • the risk treatment plan is reviewed for progress with actions, and that the security program is providing the appropriate level of protection. • Certification surveillance visits ensure the continued optimal performance of the security program to manage any identified security risks to the operations throughout the life of the certification cycle. At this time there is no other verification or certification of any security program that offers this ongoing assurance that trusted “secure traders” (e. g. C-TPAT, AEO) are consistently maintaining appropriate security.

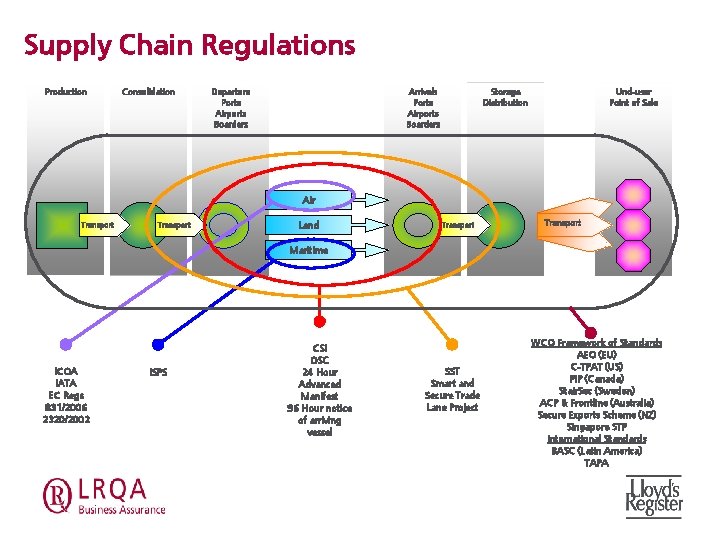
Supply Chain Regulations Production Consolidation Departure Ports Airports Boarders Arrivals Ports Airports Boarders Storage Distribution Und-user Point of Sale Air Transport Land Transport Maritime ICOA IATA EC Regs 831/2006 2320/2002 ISPS CSI OSC 24 Hour Advanced Manifest 96 Hour notice of arriving vessel SST Smart and Secure Trade Lane Project WCO Framework of Standards AEO (EU) C-TPAT (US) PIP (Canada) Stair. Sec (Sweden) ACP & Frontline (Australia) Secure Exports Scheme (NZ) Singapore STP International Standards BASC (Latin America) TAPA

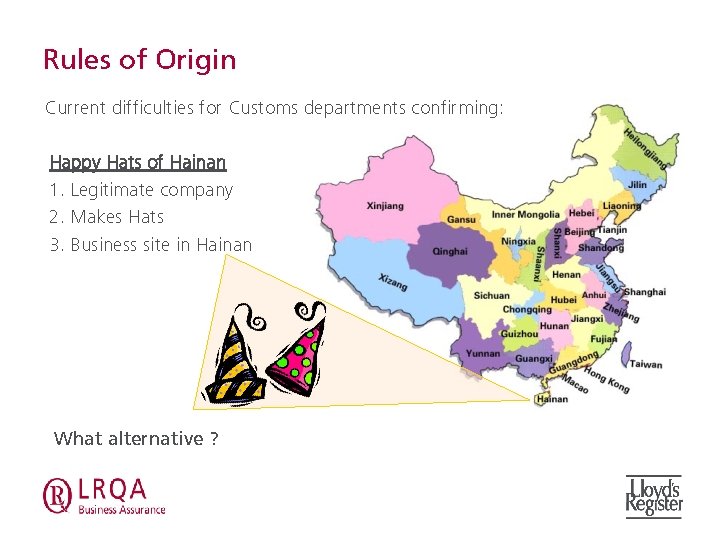
Advantages through ISO 28000 • The answer to global supply chain security rests in the hands of the majority of businesses operators within the global production, storage and movement of goods and products – the SME/SMB. • SME/SMB should participate as “secure traders” based on managing the security issues applicable to their sites. • Risk based security of businesses within any supply chain. • SME/SMB not burdened with extensive set – lists of “security requirement” – both relevant or not applicable. • ISO 28000 certification delivered by professional auditing organisations offers a global solution to cross boarder challenges. • “Rules of Origin” e. g. Happy Hats of Hainan?

Rules of Origin Current difficulties for Customs departments confirming: Happy Hats of Hainan 1. Legitimate company 2. Makes Hats 3. Business site in Hainan What alternative ?

Using ISO 28000 for a Risk Based AEO Model • WCO SAFE recommends all of WCO SFo. S 5. 2 to be applied. A – M (13) Conditions and Requirements for AEO. • In 5. 2 par 1, “These are the standards, practices and procedures which members of the trade business community aspiring to AEO status are expected to adopt into routine usage, based on risk assessment and AEO business model” • Note: based on risk and business model • Using ISO 28000 to identify the security risks and therefore the need to apply the “security related” AEO Criteria meets and/or exceed all existing major National programs. • A combined WCO-AEO & ISO 28000 model should facilitate the opportunities for mutual recognition in respect to similar programs based on Section 5. 2 WCO SAFE Framework of Standards. • WCO SAFE 5. 4 mandates for the design of validation and authorisation process.

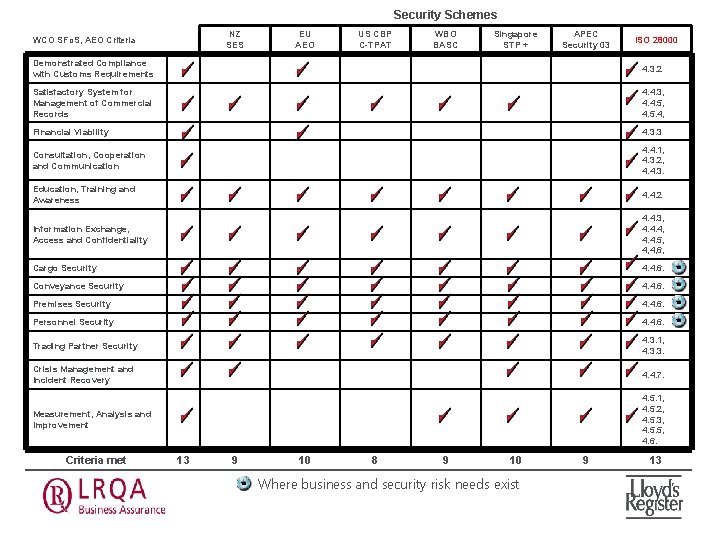
Security Schemes NZ SES WCO SFo. S, AEO Criteria EU AEO US CBP C-TPAT WBO BASC Singapore STP + APEC Security 03 ISO 28000 Demonstrated Compliance with Customs Requirements 4. 3. 2 Satisfactory System for Management of Commercial Records 4. 4. 3, 4. 4. 5, 4. 5. 4, Financial Viability 4. 3. 3 Consultation, Cooperation and Communication 4. 4. 1, 4. 3. 2, 4. 4. 3. Education, Training and Awareness 4. 4. 2 Information Exchange, Access and Confidentiality 4. 4. 3, 4. 4. 4, 4. 4. 5, 4, 4, 6, Cargo Security 4. 4. 6. Conveyance Security 4. 4. 6. Premises Security 4. 4. 6. Personnel Security 4. 4. 6. Trading Partner Security 4. 3. 1, 4. 3. 3. Crisis Management and Incident Recovery 4. 4. 7. Measurement, Analysis and Improvement 4. 5. 1, 4. 5. 2, 4. 5. 3, 4. 5. 5, 4. 6. Criteria met 13 9 10 8 9 10 Where business and security risk needs exist 9 13

WCO requires Validation WCO SAFE 5. 4 and 5. 5 – Validation process required. • Customs Departments retain ultimate authority for accrediting, suspending or revoking AEO status. • Validation processes may be delegated to 3 rd Parties. • 3 rd Party validation should not inhibit mutual recognition. • Customs administrations should not burden the international trade community with different sets of requirements.

Validation of conformity Validation. - vb, validation, - n 1. to confirm or corroborate 2. to give legal force or official confirmation to; declare legally valid 3. Collins English Dictionary - Complete & Unabridged 10 th Edition Self- validating. - adjective; • requiring no external confirmation, sanction, or validation. Random House Dictionary, © Random House, Inc. 2010. • There are currently some government and industry security schemes that allow self-validation, either during initial accreditation/licence issue or during annual self-declarations of continued compliance by business.

When is a Secure Business not a “Secure Trader” Is a business that is professionally validated as; • accurately identifying, analysing and evaluating all their security risk, • managing those risk, • monitoring the performance of their security program, • proactively adaptive to changes in the security environment • maintaining optimum security programs for business advantage, and • consistently seeking to improve their security and business benefits any less secure than the business that; • adopts a list of government specified security measures – needed or not, thereafter applying a fix & forget approach until next licence/approval application cycle.

Government Benefits of 3 rd Party Validation • • • It is anticipated that the EU may have up to 600, 000 businesses eligible for EU AEO on a three-year cycle, which equates to 200, 000 visits per year, excluding performance monitoring. Hong Kong may have up to 200, 000 businesses eligible to apply for AEO, again on a three-year cycle. • 48 full working weeks pa = 240 days • 200, 000 ÷ 3 = 66, 000 per year, ÷ 240 = 278 audits per day Alternatively Governments “Licence” a number of International Certification Bodies and manage the auditing performance. • Government establish standards, appraise and maintain AEO certification service delivery, including ongoing performance reviews of Licensed AEO auditing companies.

• The US Government is already preparing for independent (3 rd Party) validation of some national security programs, • The EU and Asia are familiar with and widely utilise ISO management system standards, • Promoting the model of “secure supply chains” globally must involve a broader business acceptance and participation, • Conformity to WCO AEO principles, coupled with the security performance processes through verified/certified ISO 28000 offers a model that can cross boarders. Manage the global AEO / C-TPAT consistency and quality, not just conformity.

For more information, please contact: Peter Boyce Senior Business Manager, Security Management Systems Lloyd’s Register Quality Assurance Limited 3501, China Merchants Tower Connaught Rd, Central, Hong Kong. T +852 2287 9307 E peter. boyce@lrqa. com w www. lrqa. com