Confidentiality Integrity Authentication Confidentiality Symmetric Key Encryption n


- Slides: 34

Confidentiality, Integrity & Authentication Confidentiality - Symmetric Key Encryption n. Data Integrity – MD-5, SHA and HMAC n. Public/Private Key mechanism - RSA n. Digital Certificate n. DH algorithm n CN 8816: Network Security 1

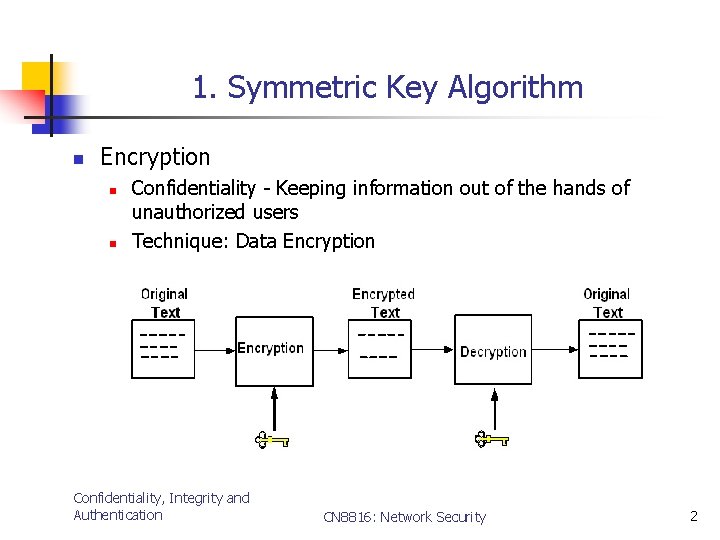
1. Symmetric Key Algorithm n Encryption n n Confidentiality - Keeping information out of the hands of unauthorized users Technique: Data Encryption Confidentiality, Integrity and Authentication CN 8816: Network Security 2

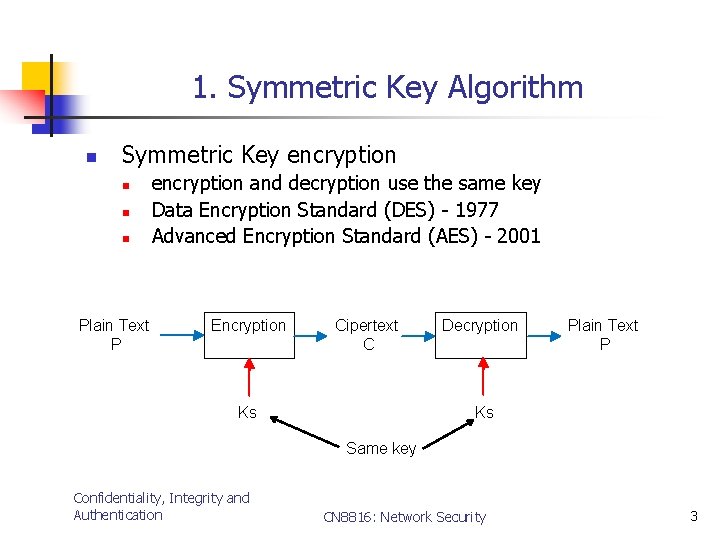
1. Symmetric Key Algorithm n Symmetric Key encryption n Plain Text P encryption and decryption use the same key Data Encryption Standard (DES) - 1977 Advanced Encryption Standard (AES) - 2001 Encryption Cipertext C Ks Decryption Plain Text P Ks Same key Confidentiality, Integrity and Authentication CN 8816: Network Security 3

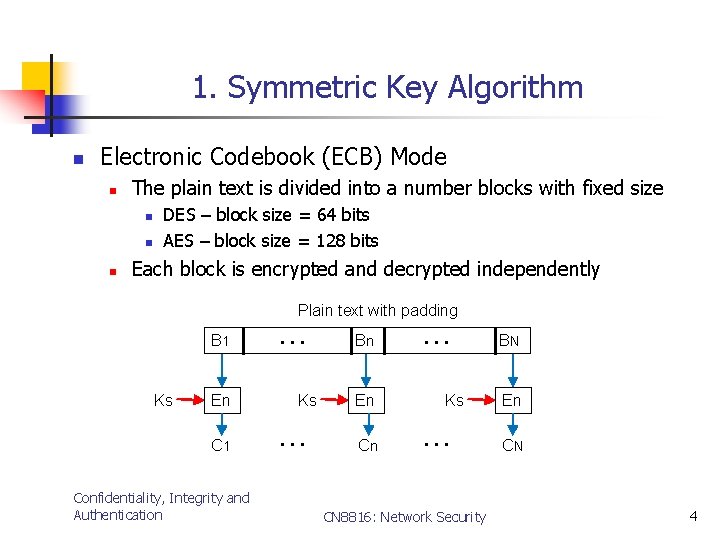
1. Symmetric Key Algorithm n Electronic Codebook (ECB) Mode n The plain text is divided into a number blocks with fixed size n n n DES – block size = 64 bits AES – block size = 128 bits Each block is encrypted and decrypted independently Plain text with padding B 1 Ks En C 1 Confidentiality, Integrity and Authentication … Ks … Bn En Cn … Ks … CN 8816: Network Security BN En CN 4

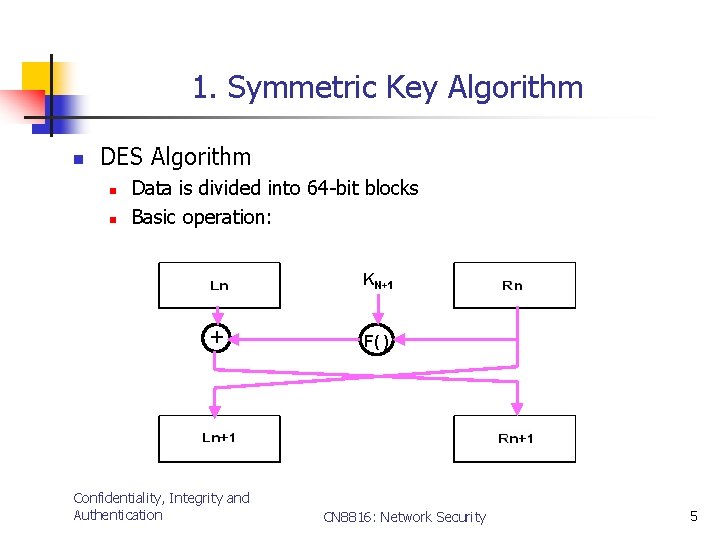
1. Symmetric Key Algorithm n DES Algorithm n n Data is divided into 64 -bit blocks Basic operation: KN+1 + Confidentiality, Integrity and Authentication F( ) CN 8816: Network Security 5

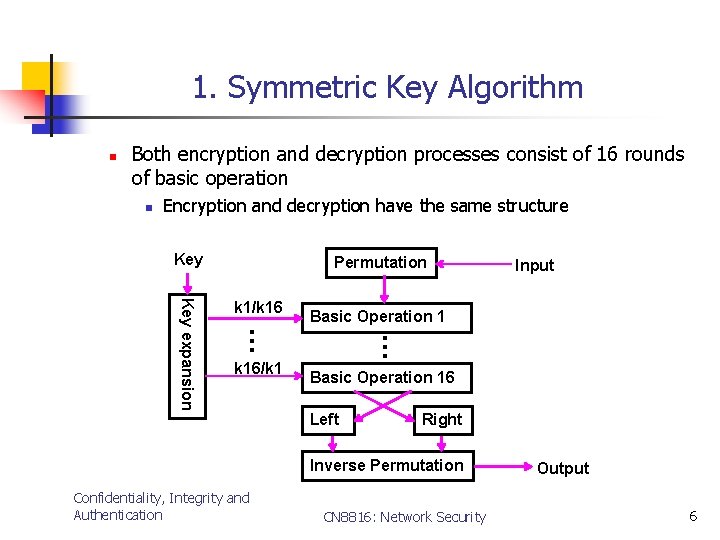
1. Symmetric Key Algorithm n Both encryption and decryption processes consist of 16 rounds of basic operation n Encryption and decryption have the same structure Key Permutation Basic Operation 1 k 16/k 1 … … Key expansion k 1/k 16 Basic Operation 16 Left Right Inverse Permutation Confidentiality, Integrity and Authentication Input CN 8816: Network Security Output 6

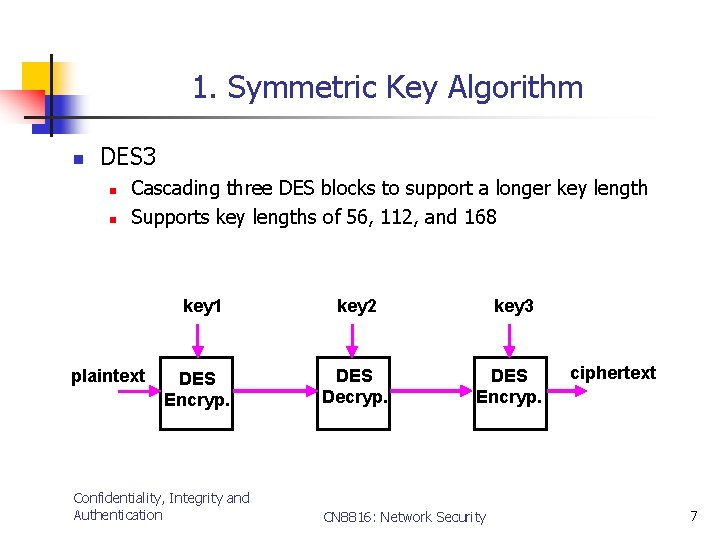
1. Symmetric Key Algorithm n DES 3 n n Cascading three DES blocks to support a longer key length Supports key lengths of 56, 112, and 168 key 1 plaintext DES Encryp. Confidentiality, Integrity and Authentication key 2 key 3 DES Decryp. DES Encryp. CN 8816: Network Security ciphertext 7

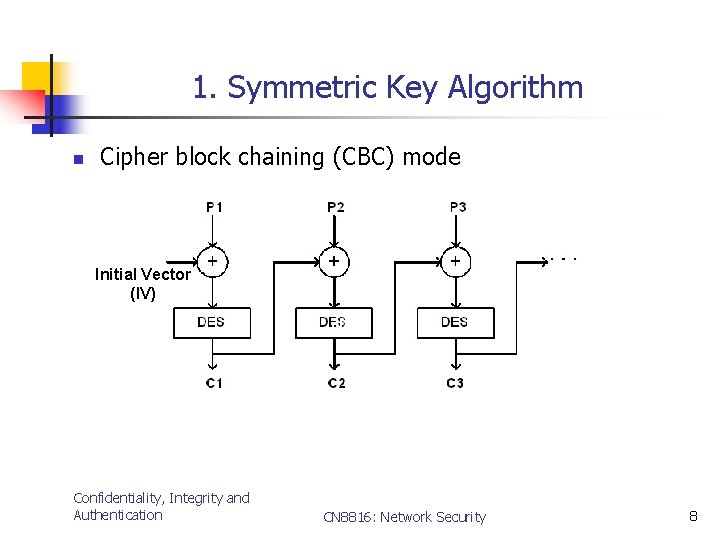
1. Symmetric Key Algorithm n Cipher block chaining (CBC) mode Initial Vector (IV) Confidentiality, Integrity and Authentication CN 8816: Network Security 8

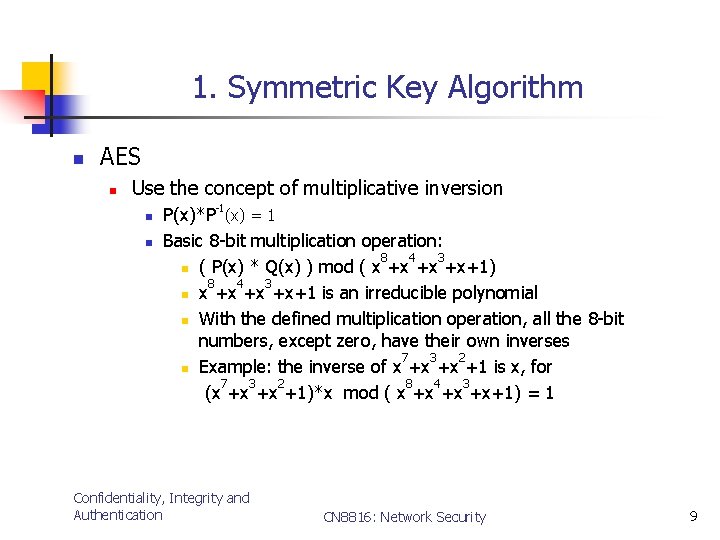
1. Symmetric Key Algorithm n AES n Use the concept of multiplicative inversion n n -1 P(x)*P (x) = 1 Basic 8 -bit multiplication operation: 8 4 3 n ( P(x) * Q(x) ) mod ( x +x +x +x+1) 8 4 3 n x +x +x +x+1 is an irreducible polynomial n With the defined multiplication operation, all the 8 -bit numbers, except zero, have their own inverses 7 3 2 n Example: the inverse of x +x +x +1 is x, for 7 3 2 8 4 3 (x +x +x +1)*x mod ( x +x +x +x+1) = 1 Confidentiality, Integrity and Authentication CN 8816: Network Security 9

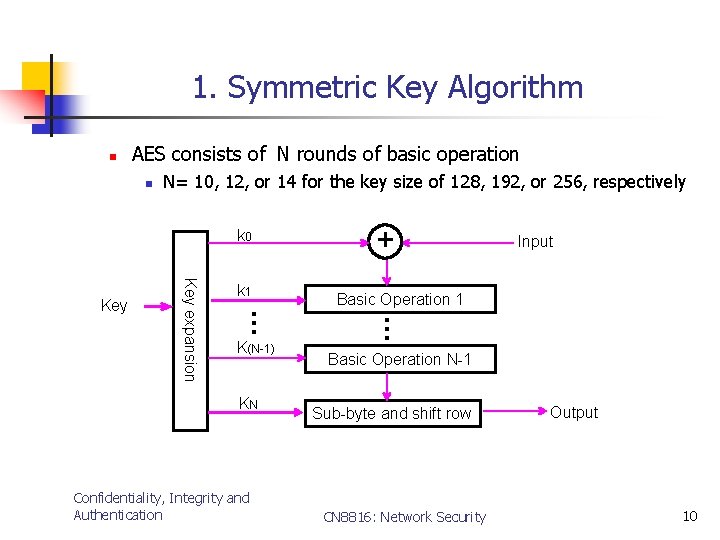
1. Symmetric Key Algorithm n AES consists of N rounds of basic operation n N= 10, 12, or 14 for the key size of 128, 192, or 256, respectively k 0 K(N-1) KN Confidentiality, Integrity and Authentication Input Basic Operation 1 … … Key expansion Key k 1 + Basic Operation N-1 Sub-byte and shift row CN 8816: Network Security Output 10

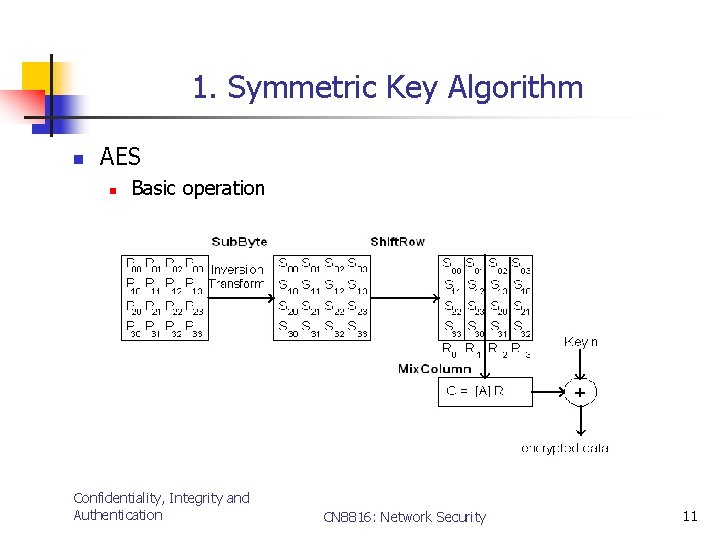
1. Symmetric Key Algorithm n AES n Basic operation Confidentiality, Integrity and Authentication CN 8816: Network Security 11

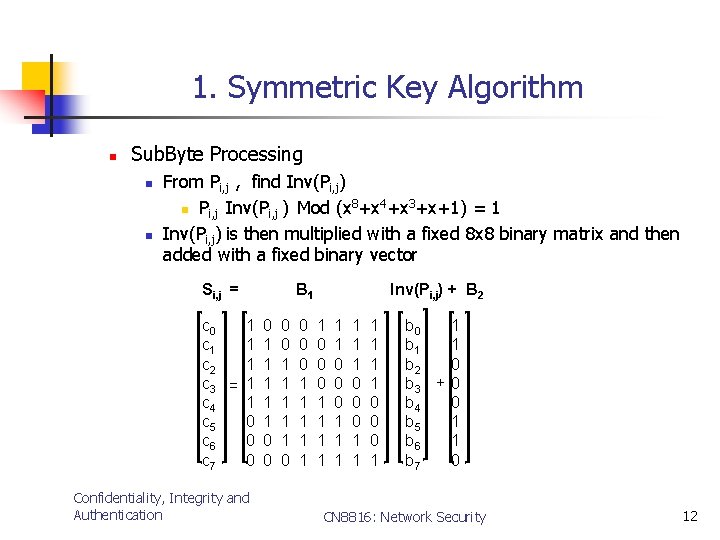
1. Symmetric Key Algorithm n Sub. Byte Processing n n From Pi, j , find Inv(Pi, j) 8 4 3 n Pi, j Inv(Pi, j ) Mod (x +x +x +x+1) = 1 Inv(Pi, j) is then multiplied with a fixed 8 x 8 binary matrix and then added with a fixed binary vector Si, j = B 1 c 0 1 0 0 0 c 1 1 1 0 0 c 2 1 1 1 0 c 3 = 1 1 c 4 1 1 c 5 0 1 1 1 c 6 0 0 1 1 c 7 0 0 0 1 Confidentiality, Integrity and Authentication Inv(Pi, j) + B 2 1 0 0 0 1 1 1 0 0 0 1 1 1 0 0 0 1 b 1 1 b 2 0 b 3 + 0 b 4 0 b 5 1 b 6 1 b 7 0 CN 8816: Network Security 12

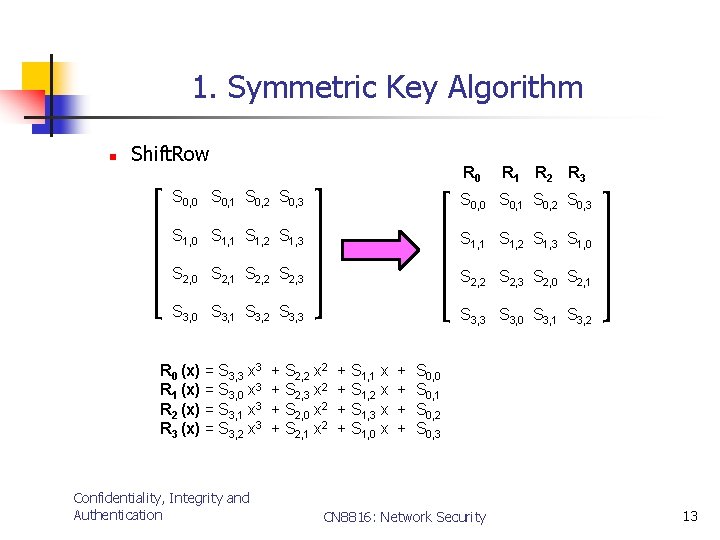
1. Symmetric Key Algorithm n Shift. Row R 0 R 1 R 2 R 3 S 0, 0 S 0, 1 S 0, 2 S 0, 3 S 1, 0 S 1, 1 S 1, 2 S 1, 3 S 1, 0 S 2, 1 S 2, 2 S 2, 3 S 2, 0 S 2, 1 S 3, 0 S 3, 1 S 3, 2 S 3, 3 S 3, 0 S 3, 1 S 3, 2 R 0 (x) = S 3, 3 x 3 R 1 (x) = S 3, 0 x 3 R 2 (x) = S 3, 1 x 3 R 3 (x) = S 3, 2 x 3 Confidentiality, Integrity and Authentication + S 2, 2 x 2 + S 2, 3 x 2 + S 2, 0 x 2 + S 2, 1 x 2 + S 1, 1 x + S 1, 2 x + S 1, 3 x + S 1, 0 x + + S 0, 0 S 0, 1 S 0, 2 S 0, 3 CN 8816: Network Security 13

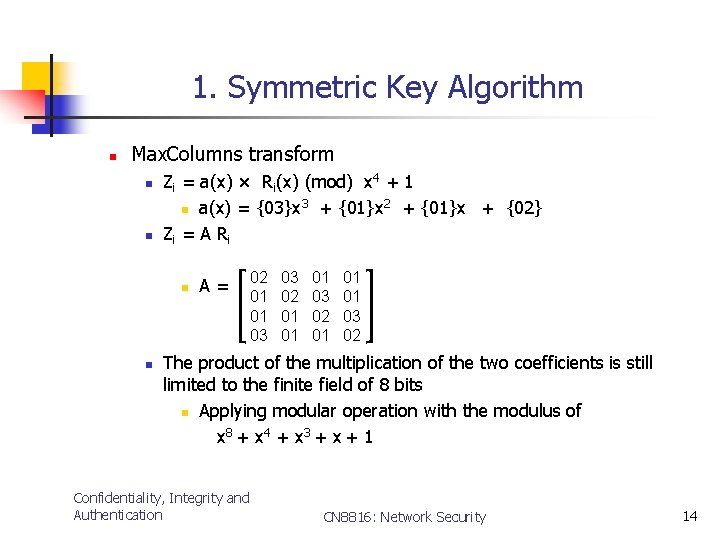
1. Symmetric Key Algorithm n Max. Columns transform n n Zi = a(x) × Ri(x) (mod) x 4 + 1 3 + {01}x 2 + {01}x + {02} n a(x) = {03}x Zi = A R i n n A= 02 01 01 03 03 02 01 01 01 03 02 The product of the multiplication of the two coefficients is still limited to the finite field of 8 bits n Applying modular operation with the modulus of x 8 + x 4 + x 3 + x + 1 Confidentiality, Integrity and Authentication CN 8816: Network Security 14

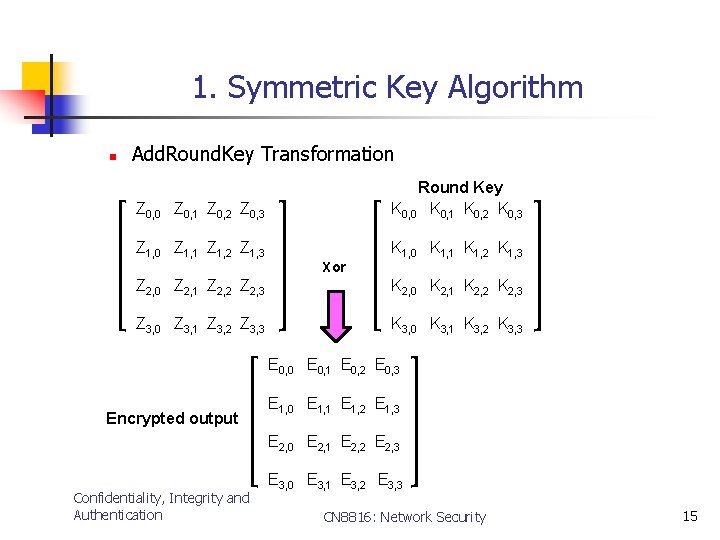
1. Symmetric Key Algorithm n Add. Round. Key Transformation Z 0, 0 Z 0, 1 Z 0, 2 Z 0, 3 Round Key K 0, 0 K 0, 1 K 0, 2 K 0, 3 Z 1, 0 Z 1, 1 Z 1, 2 Z 1, 3 K 1, 0 K 1, 1 K 1, 2 K 1, 3 Xor Z 2, 0 Z 2, 1 Z 2, 2 Z 2, 3 K 2, 0 K 2, 1 K 2, 2 K 2, 3 Z 3, 0 Z 3, 1 Z 3, 2 Z 3, 3 K 3, 0 K 3, 1 K 3, 2 K 3, 3 E 0, 0 E 0, 1 E 0, 2 E 0, 3 Encrypted output E 1, 0 E 1, 1 E 1, 2 E 1, 3 E 2, 0 E 2, 1 E 2, 2 E 2, 3 Confidentiality, Integrity and Authentication E 3, 0 E 3, 1 E 3, 2 E 3, 3 CN 8816: Network Security 15

2. Data Integrity n Message Digest n n The digest is the hash function of a message A small change of the message will completely change the hash value Data: 1001011010… Data: 10010… Confidentiality, Integrity and Authentication Hash 01101110 11011001 CN 8816: Network Security 16

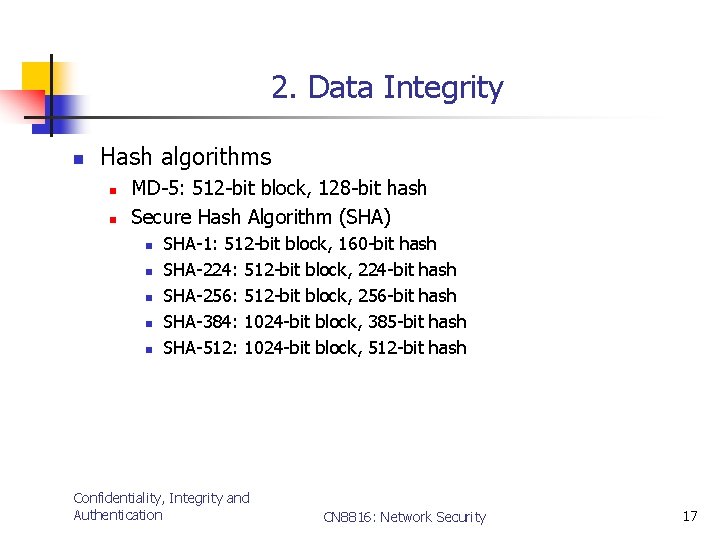
2. Data Integrity n Hash algorithms n n MD-5: 512 -bit block, 128 -bit hash Secure Hash Algorithm (SHA) n n n SHA-1: 512 -bit block, 160 -bit hash SHA-224: 512 -bit block, 224 -bit hash SHA-256: 512 -bit block, 256 -bit hash SHA-384: 1024 -bit block, 385 -bit hash SHA-512: 1024 -bit block, 512 -bit hash Confidentiality, Integrity and Authentication CN 8816: Network Security 17

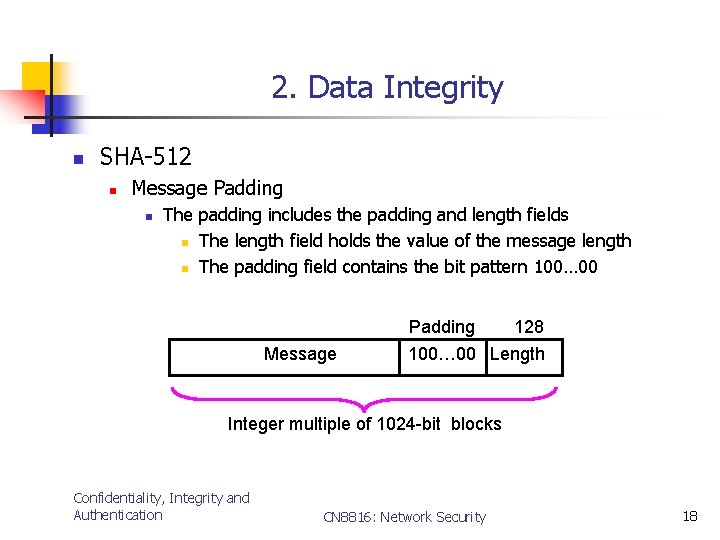
2. Data Integrity n SHA-512 n Message Padding n The padding includes the padding and length fields n The length field holds the value of the message length n The padding field contains the bit pattern 100… 00 Padding Message 128 100… 00 Length Integer multiple of 1024 -bit blocks Confidentiality, Integrity and Authentication CN 8816: Network Security 18

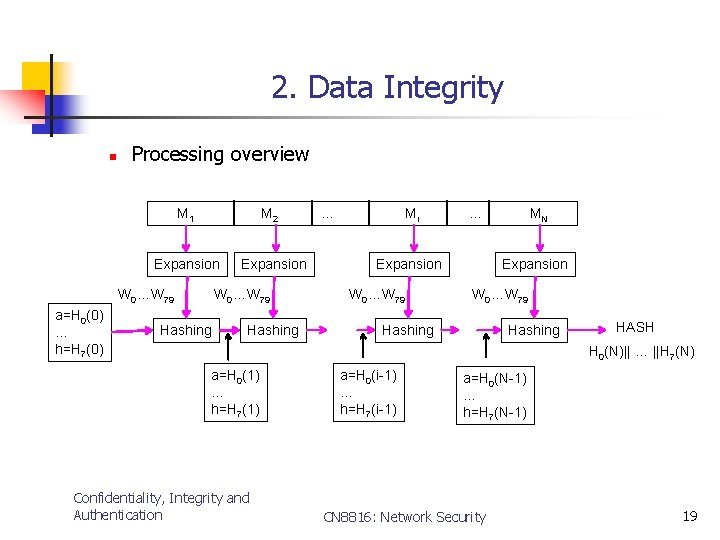
2. Data Integrity n Processing overview M 1 M 2 Expansion W 0…W 79 a=H 0(0) … h=H 7(0) Expansion W 0…W 79 Hashing … Mi … Expansion W 0…W 79 MN Expansion W 0…W 79 Hashing HASH H 0(N)|| … ||H 7(N) a=H 0(1) … h=H 7(1) Confidentiality, Integrity and Authentication a=H 0(i-1) … h=H 7(i-1) a=H 0(N-1) … h=H 7(N-1) CN 8816: Network Security 19

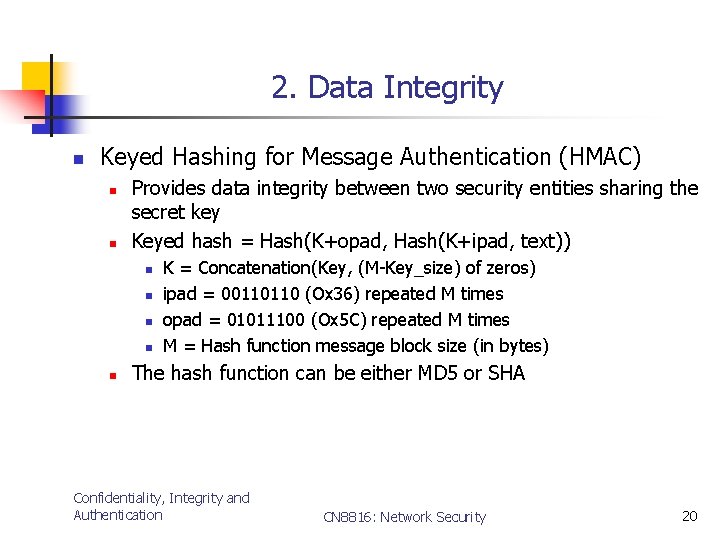
2. Data Integrity n Keyed Hashing for Message Authentication (HMAC) n n Provides data integrity between two security entities sharing the secret key Keyed hash = Hash(K+opad, Hash(K+ipad, text)) n n n K = Concatenation(Key, (M-Key_size) of zeros) ipad = 00110110 (Ox 36) repeated M times opad = 01011100 (Ox 5 C) repeated M times M = Hash function message block size (in bytes) The hash function can be either MD 5 or SHA Confidentiality, Integrity and Authentication CN 8816: Network Security 20

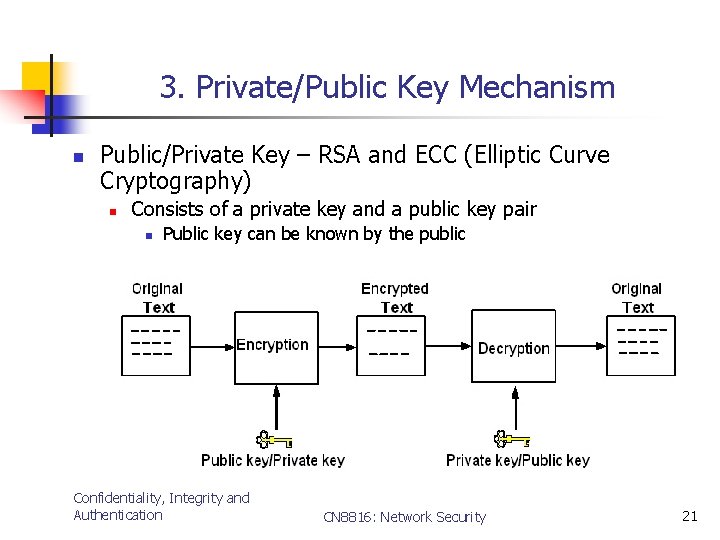
3. Private/Public Key Mechanism n Public/Private Key – RSA and ECC (Elliptic Curve Cryptography) n Consists of a private key and a public key pair n Public key can be known by the public Confidentiality, Integrity and Authentication CN 8816: Network Security 21

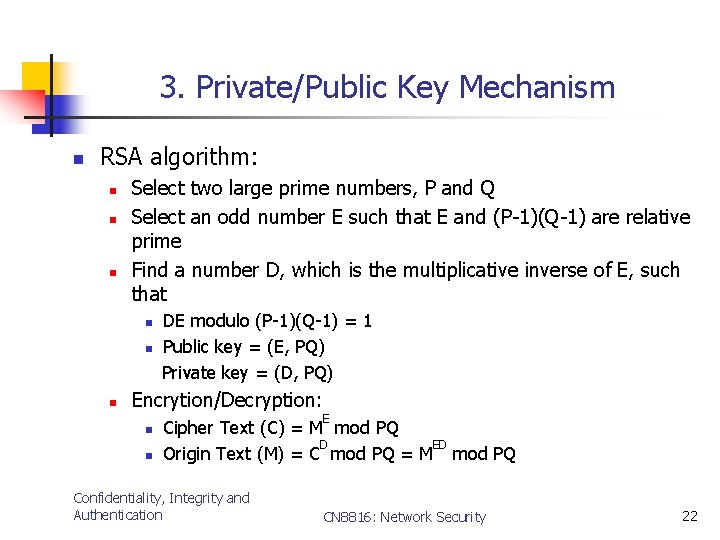
3. Private/Public Key Mechanism n RSA algorithm: n n n Select two large prime numbers, P and Q Select an odd number E such that E and (P-1)(Q-1) are relative prime Find a number D, which is the multiplicative inverse of E, such that n n n DE modulo (P-1)(Q-1) = 1 Public key = (E, PQ) Private key = (D, PQ) Encrytion/Decryption: n n E Cipher Text (C) = M mod PQ D ED Origin Text (M) = C mod PQ = M mod PQ Confidentiality, Integrity and Authentication CN 8816: Network Security 22

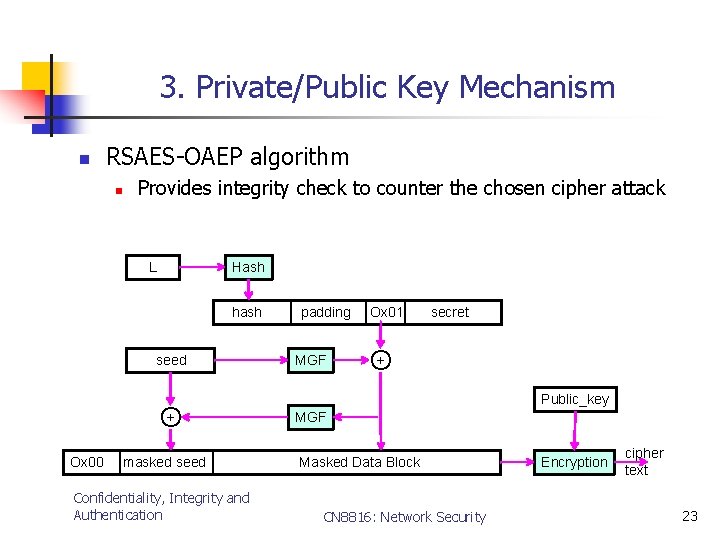
3. Private/Public Key Mechanism n RSAES-OAEP algorithm n Provides integrity check to counter the chosen cipher attack L Hash hash seed + O Ox 00 masked seed Confidentiality, Integrity and Authentication padding MGF Ox 01 secret + O Public_key MGF Masked Data Block CN 8816: Network Security Encryption cipher text 23

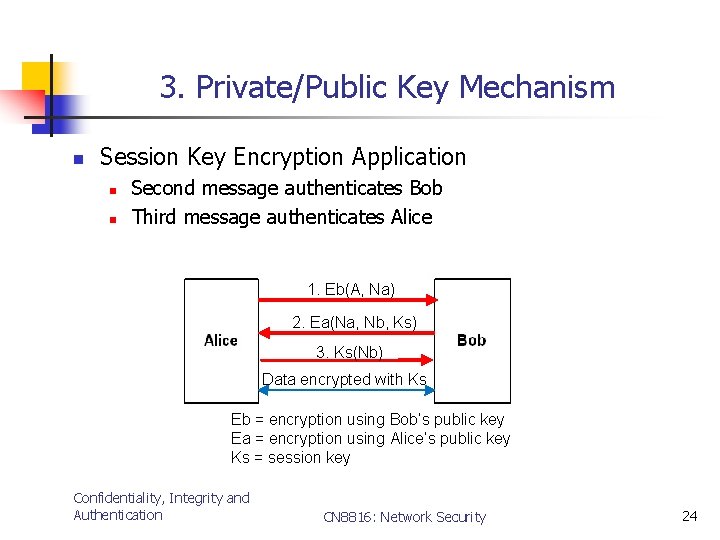
3. Private/Public Key Mechanism n Session Key Encryption Application n n Second message authenticates Bob Third message authenticates Alice 1. Eb(A, Na) 2. Ea(Na, Nb, Ks) 3. Ks(Nb) Data encrypted with Ks Eb = encryption using Bob’s public key Ea = encryption using Alice’s public key Ks = session key Confidentiality, Integrity and Authentication CN 8816: Network Security 24

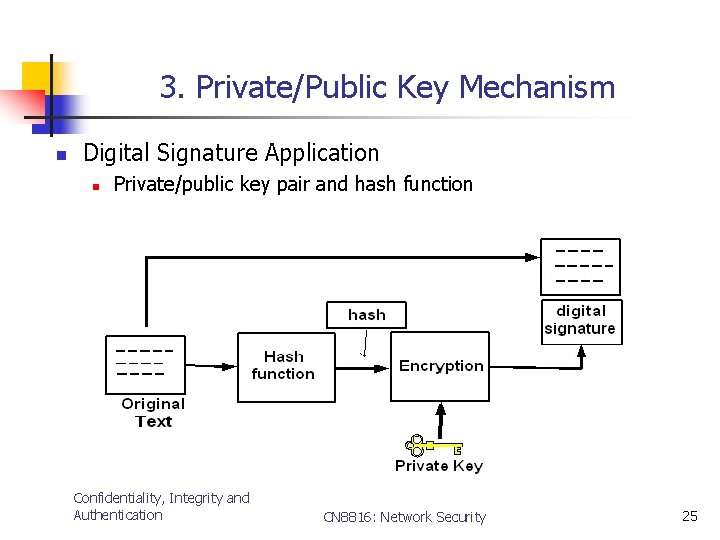
3. Private/Public Key Mechanism n Digital Signature Application n Private/public key pair and hash function Confidentiality, Integrity and Authentication CN 8816: Network Security 25

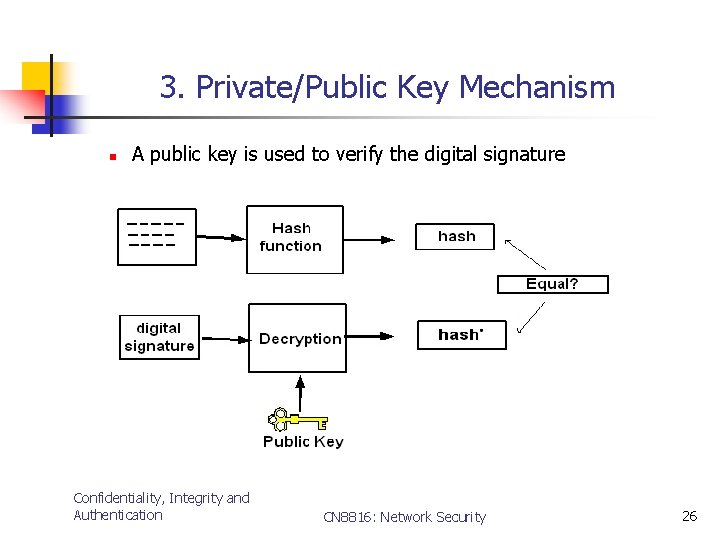
3. Private/Public Key Mechanism n A public key is used to verify the digital signature Confidentiality, Integrity and Authentication CN 8816: Network Security 26

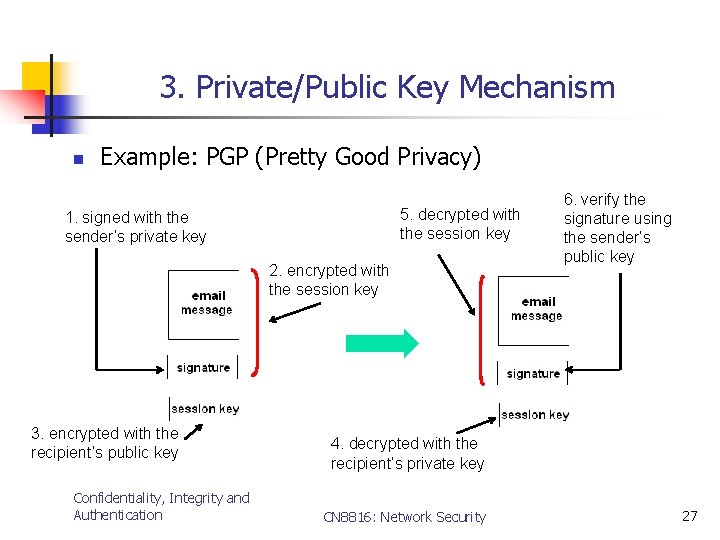
3. Private/Public Key Mechanism n Example: PGP (Pretty Good Privacy) 5. decrypted with the session key 1. signed with the sender’s private key 2. encrypted with the session key 3. encrypted with the recipient’s public key Confidentiality, Integrity and Authentication 6. verify the signature using the sender’s public key 4. decrypted with the recipient’s private key CN 8816: Network Security 27

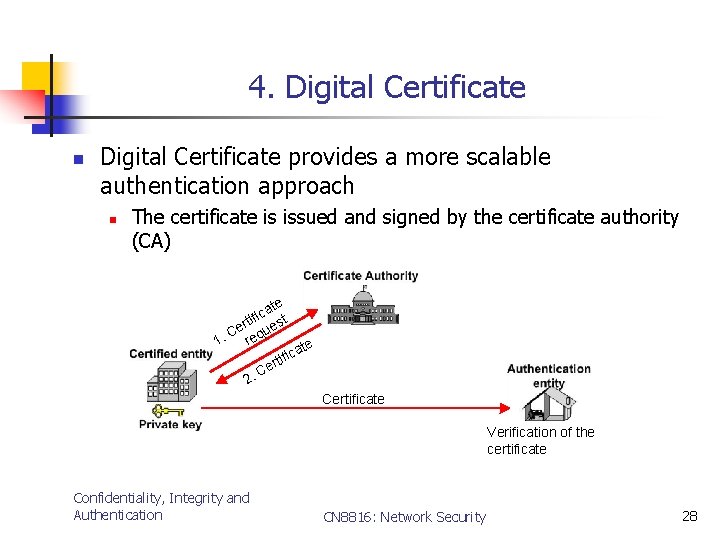
4. Digital Certificate n Digital Certificate provides a more scalable authentication approach n The certificate is issued and signed by the certificate authority (CA) ate c i f i t ert ues C q 1. re ate c i f i ert C 2. Certificate Verification of the certificate Confidentiality, Integrity and Authentication CN 8816: Network Security 28

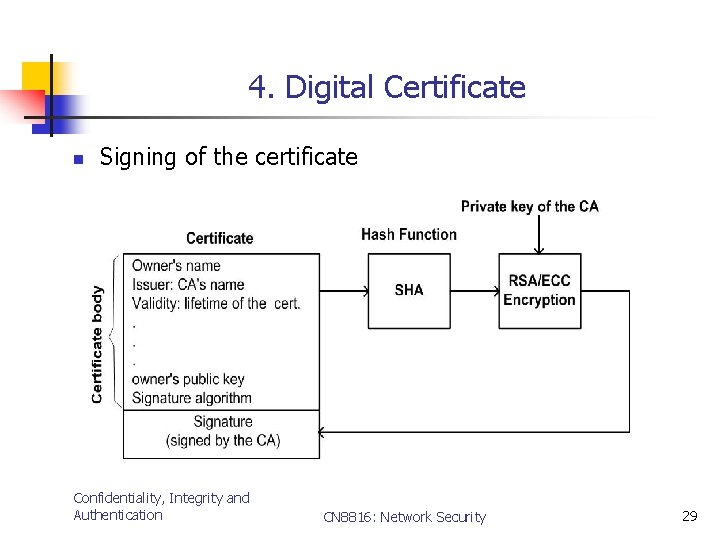
4. Digital Certificate n Signing of the certificate Confidentiality, Integrity and Authentication CN 8816: Network Security 29

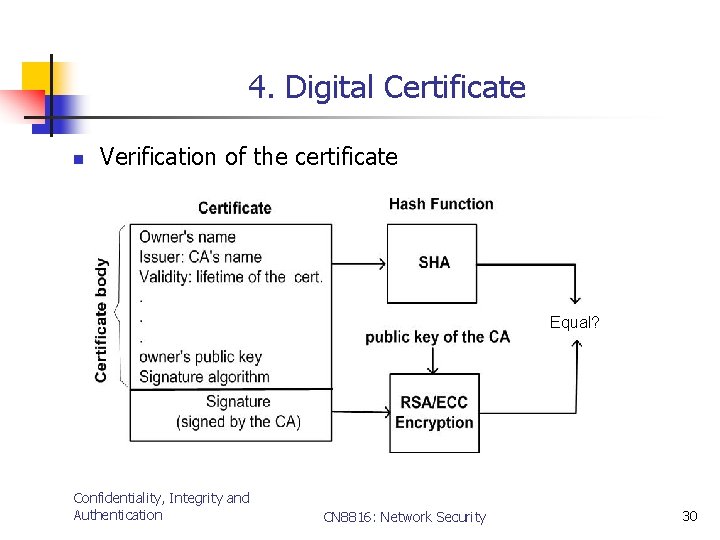
4. Digital Certificate n Verification of the certificate Equal? Confidentiality, Integrity and Authentication CN 8816: Network Security 30

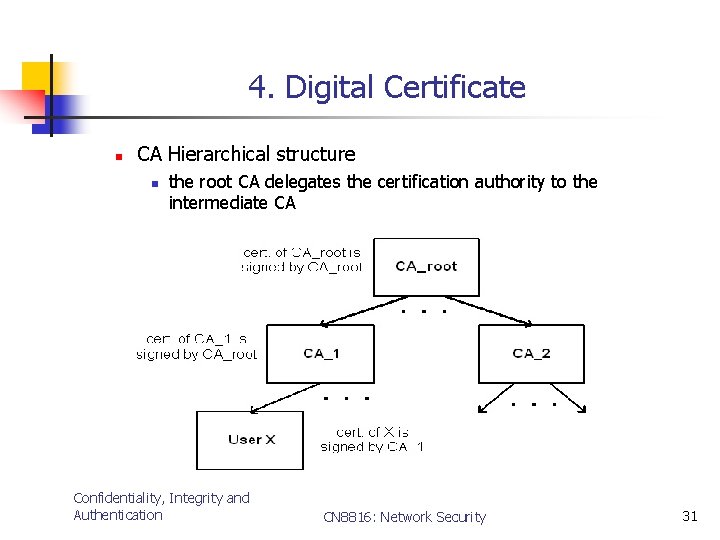
4. Digital Certificate n CA Hierarchical structure n the root CA delegates the certification authority to the intermediate CA Confidentiality, Integrity and Authentication CN 8816: Network Security 31

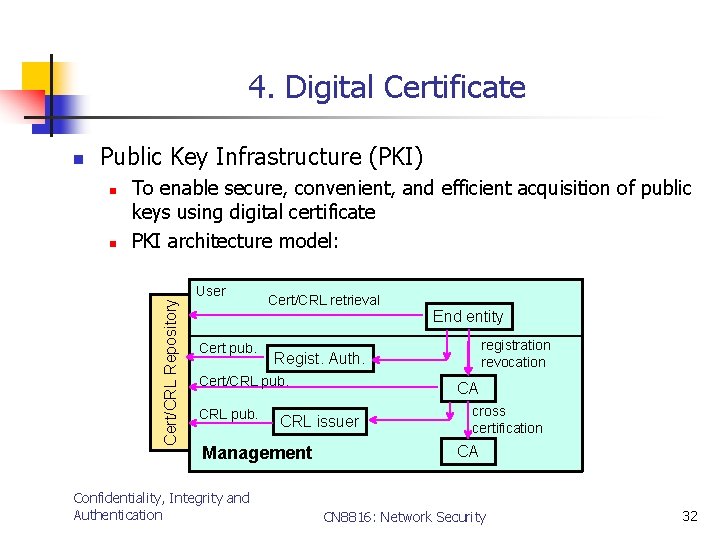
4. Digital Certificate n Public Key Infrastructure (PKI) n Cert/CRL Repository n To enable secure, convenient, and efficient acquisition of public keys using digital certificate PKI architecture model: User Cert pub. Cert/CRL retrieval CA CRL issuer Management Confidentiality, Integrity and Authentication registration revocation Regist. Auth. Cert/CRL pub. End entity cross certification CA CN 8816: Network Security 32

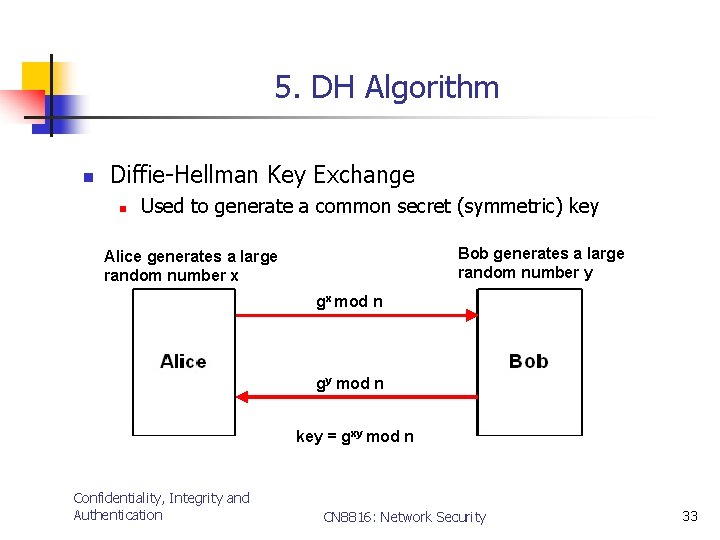
5. DH Algorithm n Diffie-Hellman Key Exchange n Used to generate a common secret (symmetric) key Bob generates a large random number y Alice generates a large random number x gx mod n gy mod n key = gxy mod n Confidentiality, Integrity and Authentication CN 8816: Network Security 33

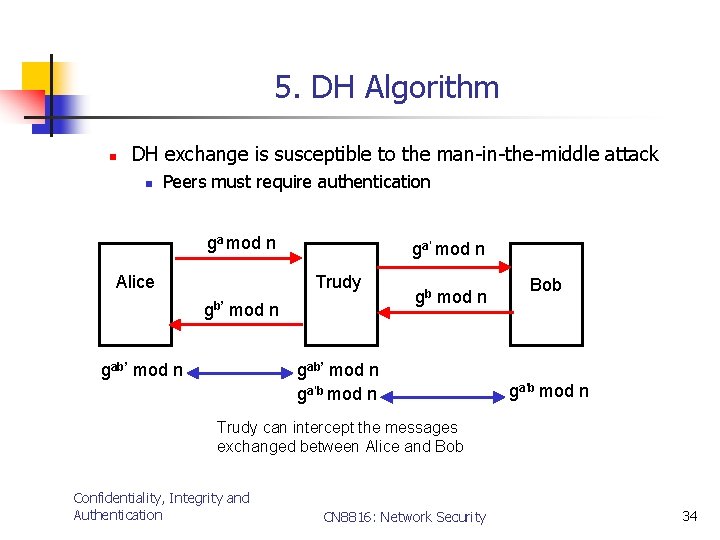
5. DH Algorithm n DH exchange is susceptible to the man-in-the-middle attack n Peers must require authentication ga mod n Alice ga’ mod n Trudy gb’ mod n gab’ mod n gb mod n gab’ mod n ga’b mod n Bob ga’b mod n Trudy can intercept the messages exchanged between Alice and Bob Confidentiality, Integrity and Authentication CN 8816: Network Security 34