Concurrent Models of Computation Edward A Lee Professor
















- Slides: 73

Concurrent Models of Computation Edward A. Lee Professor, UC Berkeley Ptolemy Project CHESS: Center for Hybrid and Embedded Software Systems HP Workshop on Advanced Software Technologies July 20 -22 HP Labs, Palo Alto, CA

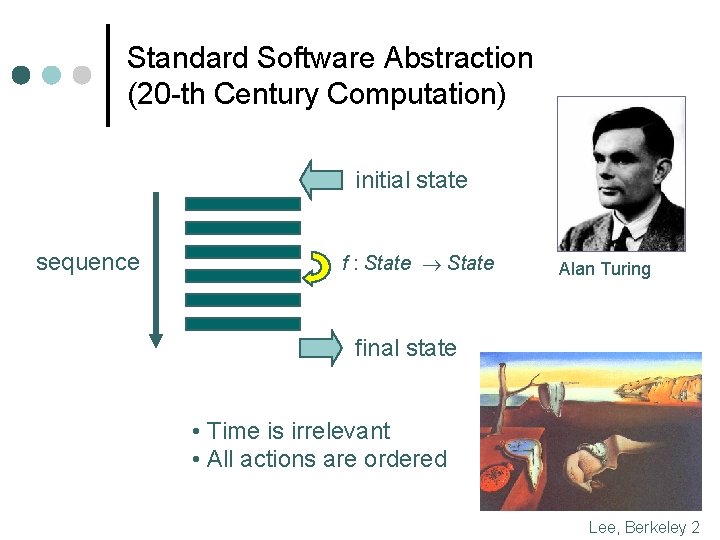
Standard Software Abstraction (20 -th Century Computation) initial state sequence f : State Alan Turing final state • Time is irrelevant • All actions are ordered Lee, Berkeley 2

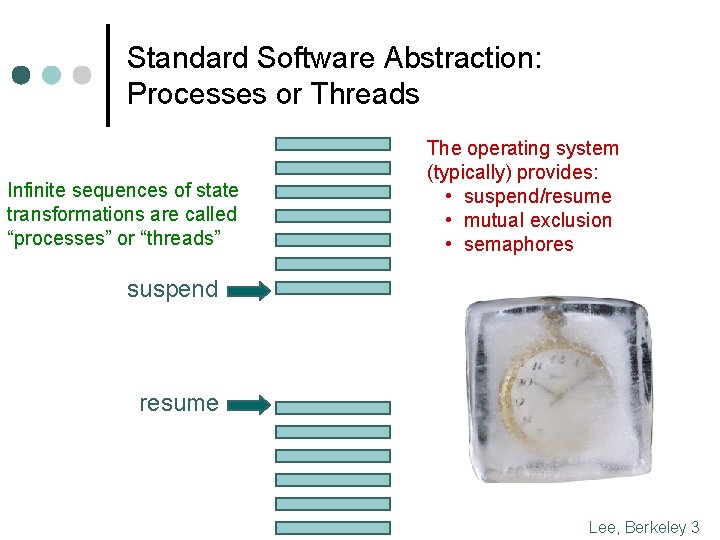
Standard Software Abstraction: Processes or Threads Infinite sequences of state transformations are called “processes” or “threads” The operating system (typically) provides: • suspend/resume • mutual exclusion • semaphores suspend resume Lee, Berkeley 3

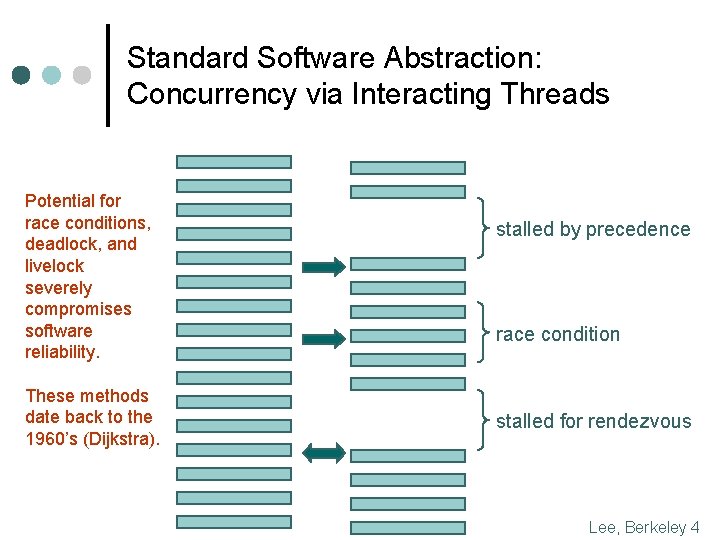
Standard Software Abstraction: Concurrency via Interacting Threads Potential for race conditions, deadlock, and livelock severely compromises software reliability. These methods date back to the 1960’s (Dijkstra). stalled by precedence race condition stalled for rendezvous Lee, Berkeley 4

A Stake in the Ground Nontrivial concurrent programs based on processes, threads, semaphores, and mutexes are incomprehensible to humans. l No amount of process improvement is going to change this. • the human brain doesn’t work this way. l Formal methods may help • scalability? • understandability? l Better concurrency abstractions will help more Lee, Berkeley 5

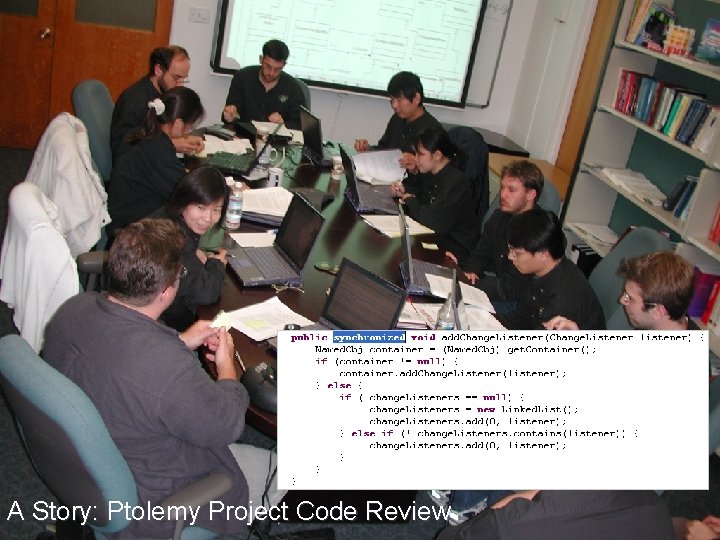
A Story: Ptolemy Project Code Review Lee, Berkeley 6

Ptolemy Project Code Review A Typical Story ¢ Code review discovers that a method needs to be synchronized to ensure that multiple threads do not reverse each other’s actions. No problems had been detected in 4 years of using the code. Three days after making the change, users started reporting deadlocks caused by the new mutex. Analysis and correction of the deadlock is hard. ¢ But code review successfully identified the flaw. ¢ ¢ ¢ Lee, Berkeley 7

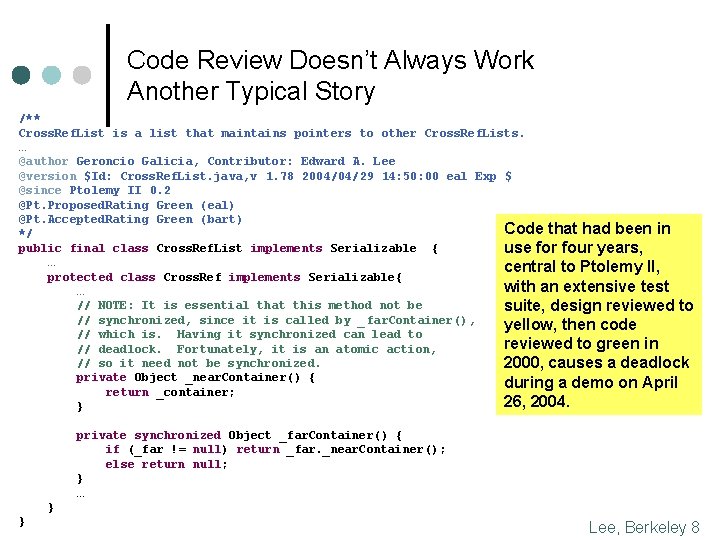
Code Review Doesn’t Always Work Another Typical Story /** Cross. Ref. List is a list that maintains pointers to other Cross. Ref. Lists. … @author Geroncio Galicia, Contributor: Edward A. Lee @version $Id: Cross. Ref. List. java, v 1. 78 2004/04/29 14: 50: 00 eal Exp $ @since Ptolemy II 0. 2 @Pt. Proposed. Rating Green (eal) @Pt. Accepted. Rating Green (bart) Code that had been in */ public final class Cross. Ref. List implements Serializable { use for four years, … central to Ptolemy II, protected class Cross. Ref implements Serializable{ with an extensive test … // NOTE: It is essential that this method not be suite, design reviewed to // synchronized, since it is called by _ far. Container(), yellow, then code // which is. Having it synchronized can lead to reviewed to green in // deadlock. Fortunately, it is an atomic action, // so it need not be synchronized. 2000, causes a deadlock private Object _near. Container() { during a demo on April return _container; 26, 2004. } private synchronized Object _far. Container() { if (_far != null) return _far. _near. Container(); else return null; } … } } Lee, Berkeley 8

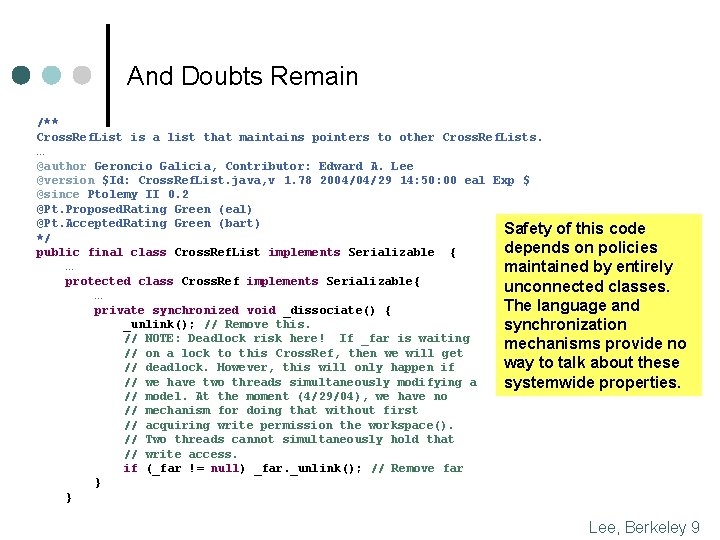
And Doubts Remain /** Cross. Ref. List is a list that maintains pointers to other Cross. Ref. Lists. … @author Geroncio Galicia, Contributor: Edward A. Lee @version $Id: Cross. Ref. List. java, v 1. 78 2004/04/29 14: 50: 00 eal Exp $ @since Ptolemy II 0. 2 @Pt. Proposed. Rating Green (eal) @Pt. Accepted. Rating Green (bart) Safety of this code */ depends on policies public final class Cross. Ref. List implements Serializable { … maintained by entirely protected class Cross. Ref implements Serializable{ unconnected classes. … The language and private synchronized void _dissociate() { _unlink(); // Remove this. synchronization // NOTE: Deadlock risk here! If _far is waiting mechanisms provide no // on a lock to this Cross. Ref, then we will get way to talk about these // deadlock. However, this will only happen if // we have two threads simultaneously modifying a systemwide properties. // model. At the moment (4/29/04), we have no // mechanism for doing that without first // acquiring write permission the workspace(). // Two threads cannot simultaneously hold that // write access. if (_far != null) _far. _unlink(); // Remove far } } Lee, Berkeley 9

Image “borrowed” from an Iomega advertisement for Y 2 K software and disk drives, Scientific American, September 1999. What it Feels Like to Use the synchronized Keyword in Java Lee, Berkeley 10

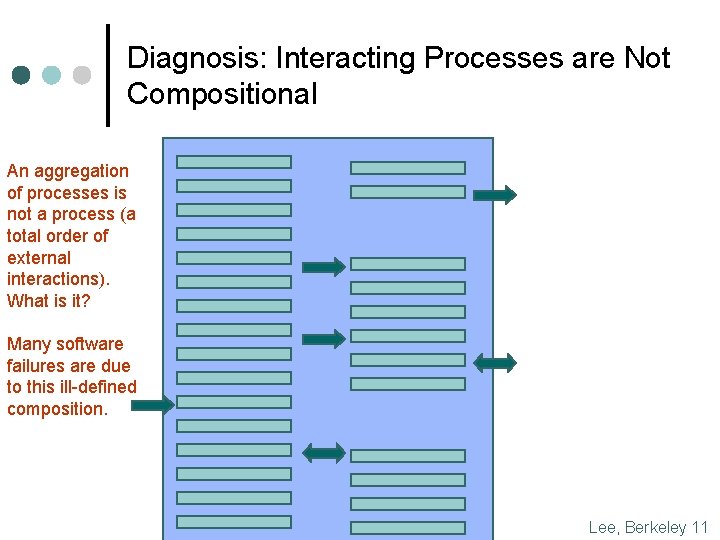
Diagnosis: Interacting Processes are Not Compositional An aggregation of processes is not a process (a total order of external interactions). What is it? Many software failures are due to this ill-defined composition. Lee, Berkeley 11

Distributed Version of 20 -th Century Computation Force-fitting the sequential abstraction onto parallel hardware. remote procedure call Lee, Berkeley 12

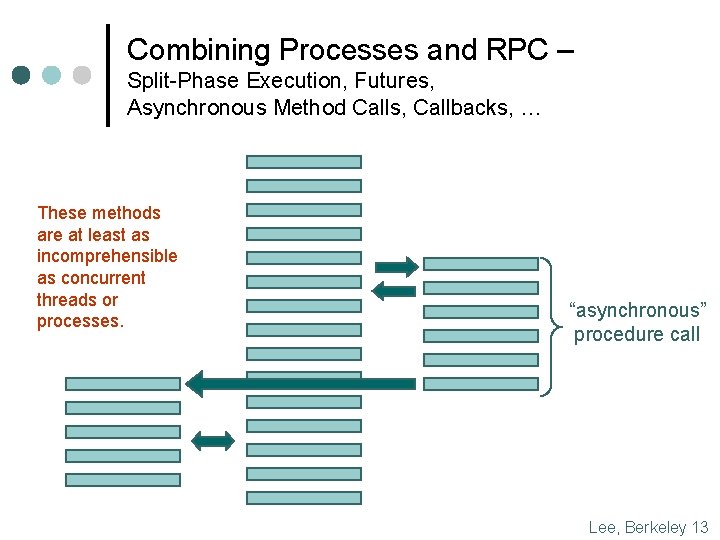
Combining Processes and RPC – Split-Phase Execution, Futures, Asynchronous Method Calls, Callbacks, … These methods are at least as incomprehensible as concurrent threads or processes. “asynchronous” procedure call Lee, Berkeley 13

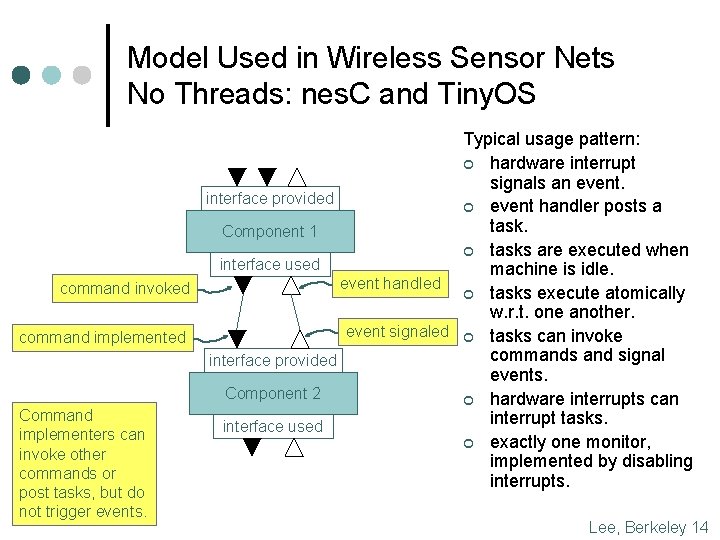
Model Used in Wireless Sensor Nets No Threads: nes. C and Tiny. OS Typical usage pattern: ¢ hardware interrupt signals an event. interface provided ¢ event handler posts a task. Component 1 ¢ tasks are executed when interface used machine is idle. event handled command invoked ¢ tasks execute atomically w. r. t. one another. event signaled ¢ tasks can invoke command implemented commands and signal interface provided events. Component 2 ¢ hardware interrupts can Command interrupt tasks. interface used implementers can ¢ exactly one monitor, invoke other implemented by disabling commands or interrupts. post tasks, but do not trigger events. Lee, Berkeley 14

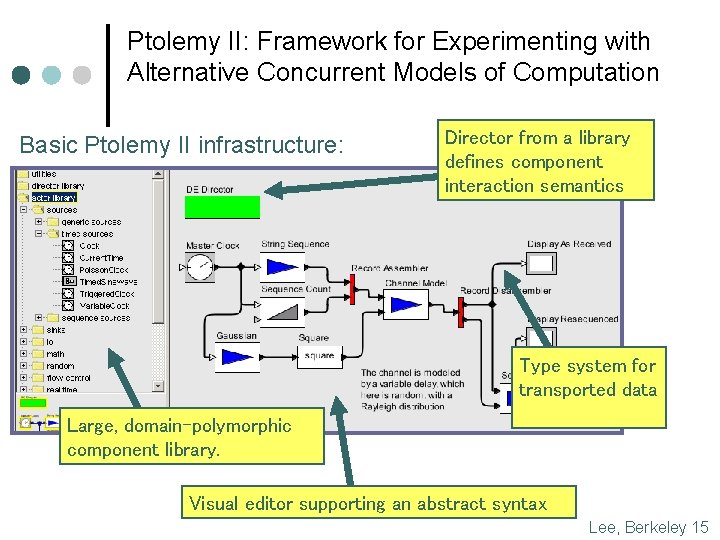
Ptolemy II: Framework for Experimenting with Alternative Concurrent Models of Computation Basic Ptolemy II infrastructure: Director from a library defines component interaction semantics Type system for transported data Large, domain-polymorphic component library. Visual editor supporting an abstract syntax Lee, Berkeley 15

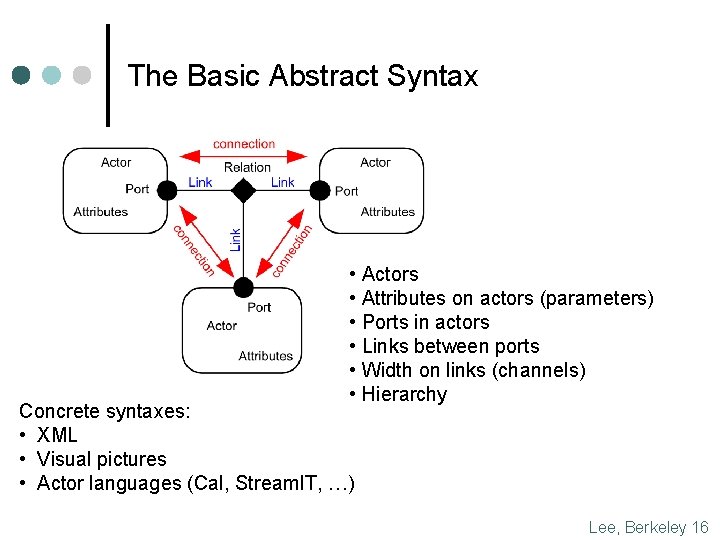
The Basic Abstract Syntax • Actors • Attributes on actors (parameters) • Ports in actors • Links between ports • Width on links (channels) • Hierarchy Concrete syntaxes: • XML • Visual pictures • Actor languages (Cal, Stream. IT, …) Lee, Berkeley 16

Hierarchy - Composite Components Relation dangling Port Actor opaque Port transparent or opaque Composite. Actor toplevel Composite. Actor Lee, Berkeley 17

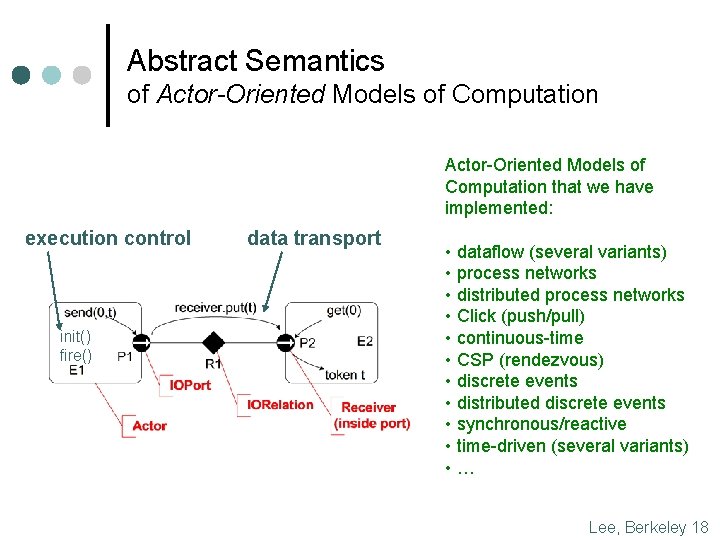
Abstract Semantics of Actor-Oriented Models of Computation that we have implemented: execution control init() fire() data transport • dataflow (several variants) • process networks • distributed process networks • Click (push/pull) • continuous-time • CSP (rendezvous) • discrete events • distributed discrete events • synchronous/reactive • time-driven (several variants) • … Lee, Berkeley 18

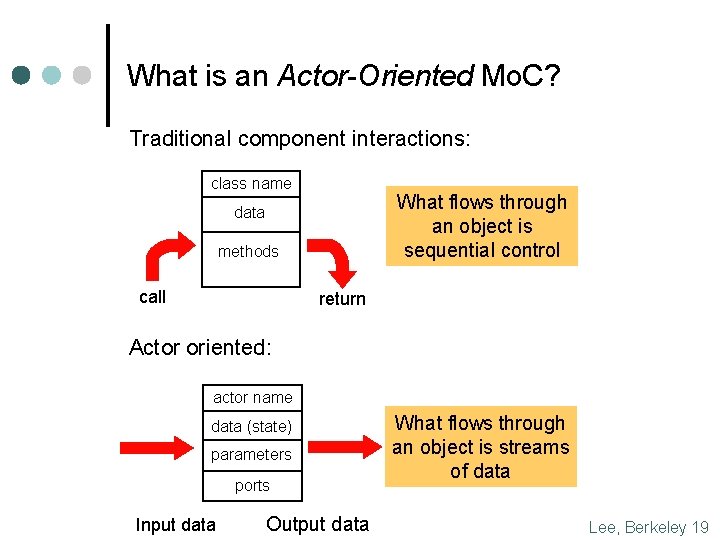
What is an Actor-Oriented Mo. C? Traditional component interactions: class name What flows through an object is sequential control data methods call return Actor oriented: actor name data (state) parameters ports Input data Output data What flows through an object is streams of data Lee, Berkeley 19

Models of Computation Implemented in Ptolemy II ¢ ¢ ¢ ¢ CI – Push/pull component interaction Click – Push/pull with method invocation CSP – concurrent threads with rendezvous CT – continuous-time modeling DE – discrete-event systems DDE – distributed discrete events FSM – finite state machines DT – discrete time (cycle driven) Giotto – synchronous periodic GR – 2 -D and 3 -D graphics PN – process networks DPN – distributed process networks SDF – synchronous dataflow SR – synchronous/reactive TM – timed multitasking Most of these are actor oriented. Lee, Berkeley 20

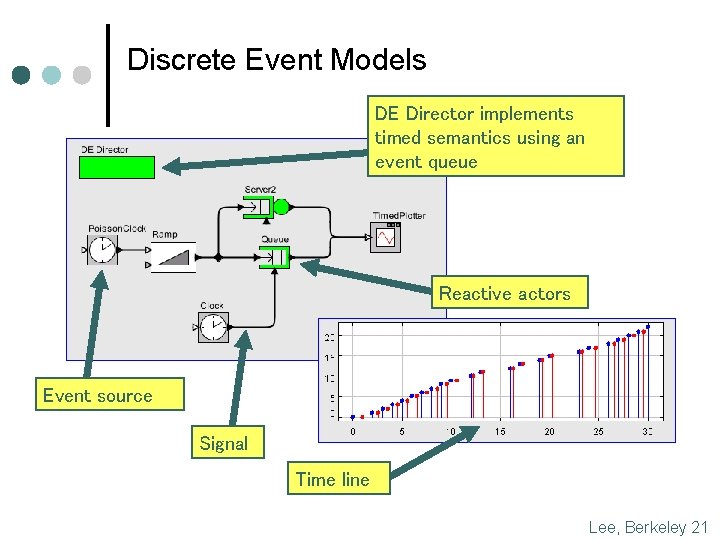
Discrete Event Models DE Director implements timed semantics using an event queue Reactive actors Event source Signal Time line Lee, Berkeley 21

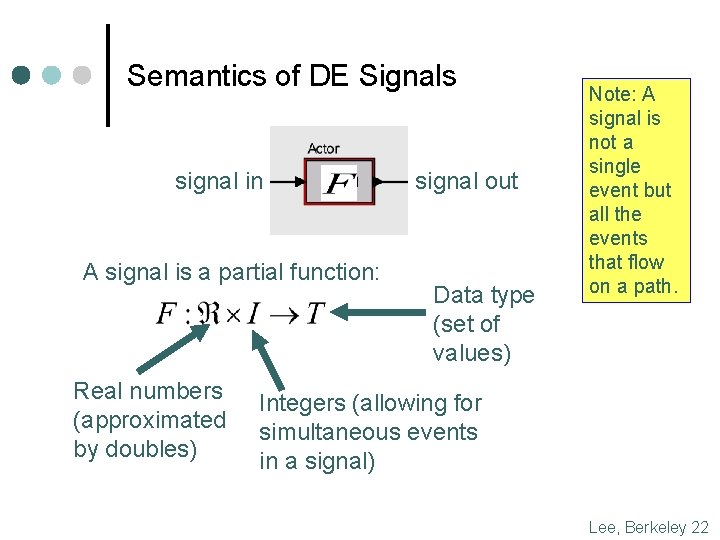
Semantics of DE Signals signal in A signal is a partial function: Real numbers (approximated by doubles) signal out Data type (set of values) Note: A signal is not a single event but all the events that flow on a path. Integers (allowing for simultaneous events in a signal) Lee, Berkeley 22

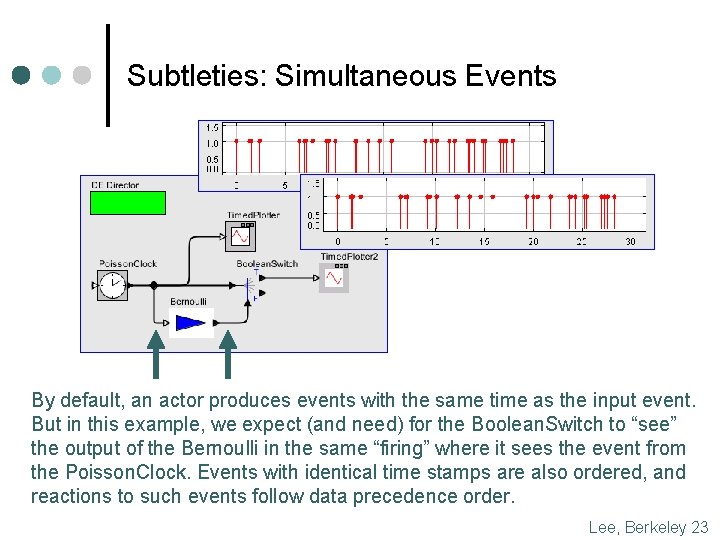
Subtleties: Simultaneous Events By default, an actor produces events with the same time as the input event. But in this example, we expect (and need) for the Boolean. Switch to “see” the output of the Bernoulli in the same “firing” where it sees the event from the Poisson. Clock. Events with identical time stamps are also ordered, and reactions to such events follow data precedence order. Lee, Berkeley 23

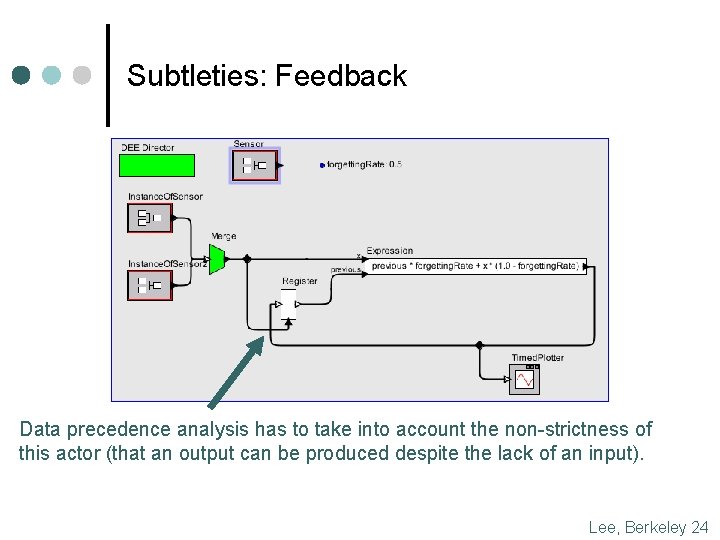
Subtleties: Feedback Data precedence analysis has to take into account the non-strictness of this actor (that an output can be produced despite the lack of an input). Lee, Berkeley 24

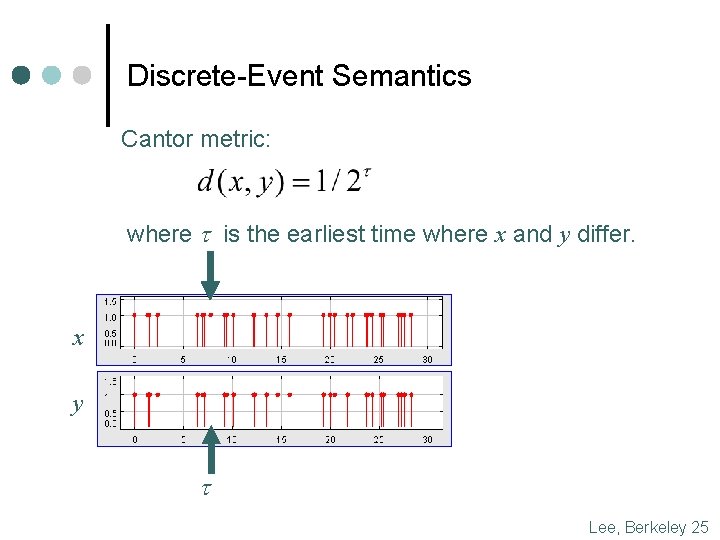
Discrete-Event Semantics Cantor metric: where t is the earliest time where x and y differ. x y t Lee, Berkeley 25

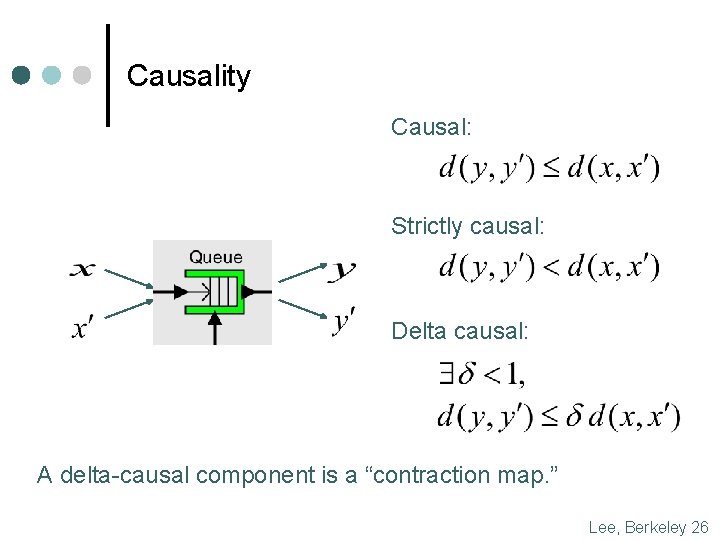
Causality Causal: Strictly causal: Delta causal: A delta-causal component is a “contraction map. ” Lee, Berkeley 26

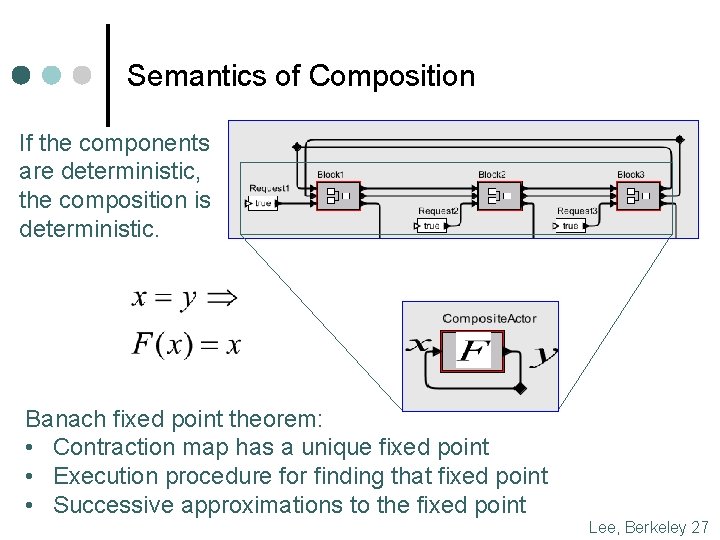
Semantics of Composition If the components are deterministic, the composition is deterministic. Banach fixed point theorem: • Contraction map has a unique fixed point • Execution procedure for finding that fixed point • Successive approximations to the fixed point Lee, Berkeley 27

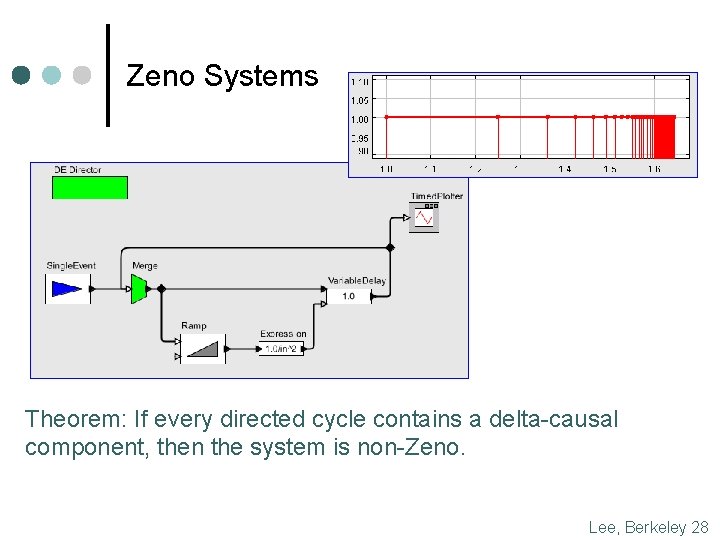
Zeno Systems Theorem: If every directed cycle contains a delta-causal component, then the system is non-Zeno. Lee, Berkeley 28

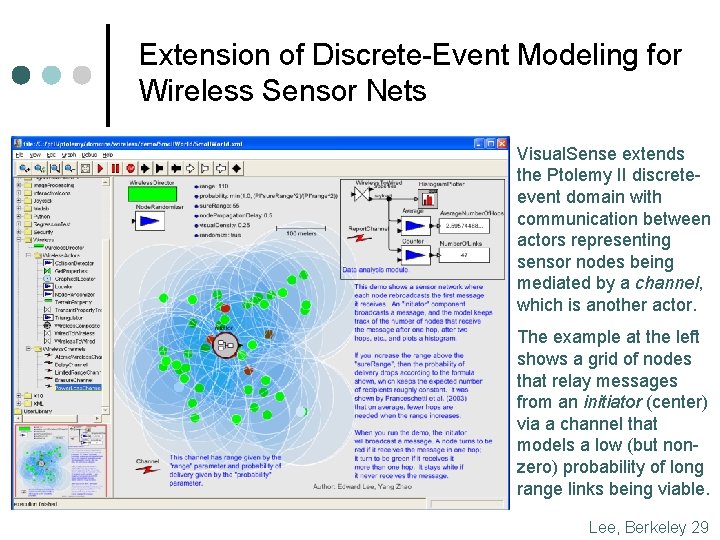
Extension of Discrete-Event Modeling for Wireless Sensor Nets Visual. Sense extends the Ptolemy II discreteevent domain with communication between actors representing sensor nodes being mediated by a channel, which is another actor. The example at the left shows a grid of nodes that relay messages from an initiator (center) via a channel that models a low (but nonzero) probability of long range links being viable. Lee, Berkeley 29

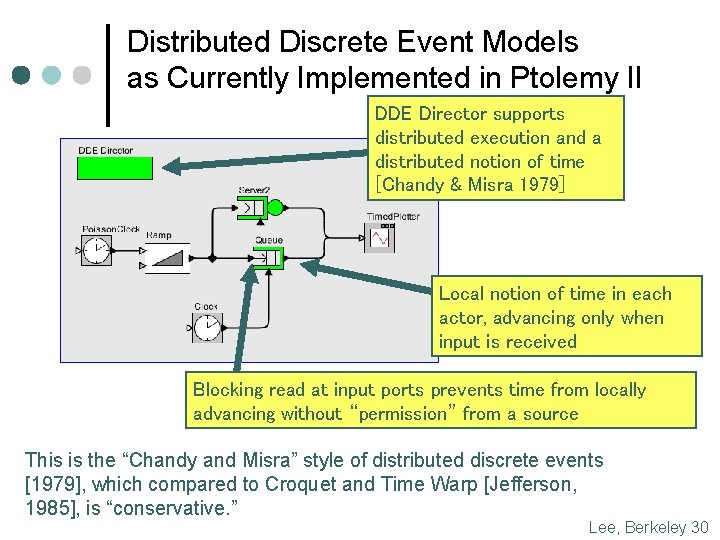
Distributed Discrete Event Models as Currently Implemented in Ptolemy II DDE Director supports distributed execution and a distributed notion of time [Chandy & Misra 1979] Local notion of time in each actor, advancing only when input is received Blocking read at input ports prevents time from locally advancing without “permission” from a source This is the “Chandy and Misra” style of distributed discrete events [1979], which compared to Croquet and Time Warp [Jefferson, 1985], is “conservative. ” Lee, Berkeley 30

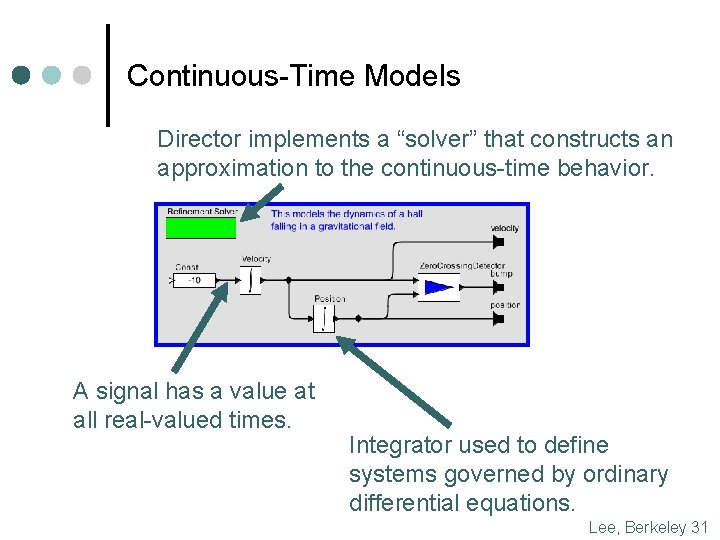
Continuous-Time Models Director implements a “solver” that constructs an approximation to the continuous-time behavior. A signal has a value at all real-valued times. Integrator used to define systems governed by ordinary differential equations. Lee, Berkeley 31

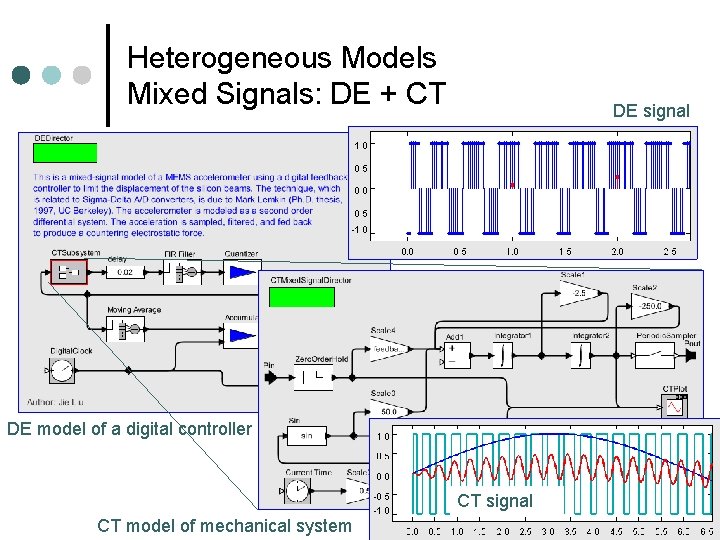
Heterogeneous Models Mixed Signals: DE + CT DE signal DE model of a digital controller CT signal CT model of mechanical system Lee, Berkeley 32

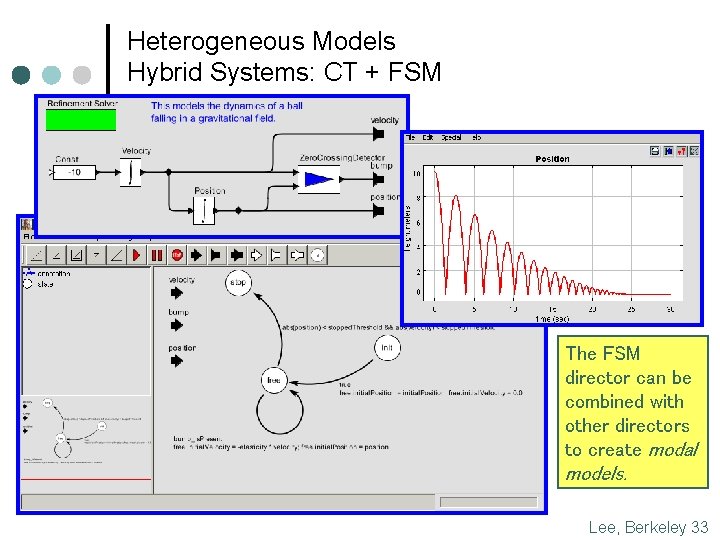
Heterogeneous Models Hybrid Systems: CT + FSM The FSM director can be combined with other directors to create modal models. Lee, Berkeley 33

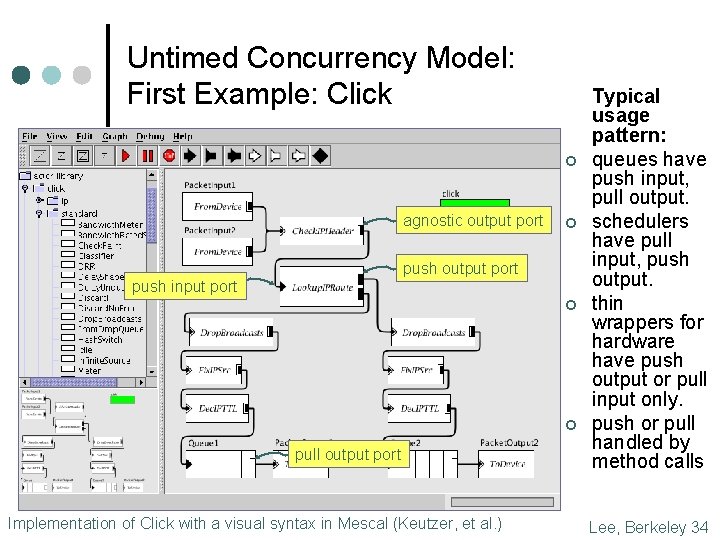
Untimed Concurrency Model: First Example: Click ¢ agnostic output port ¢ push output port push input port ¢ ¢ pull output port Implementation of Click with a visual syntax in Mescal (Keutzer, et al. ) Typical usage pattern: queues have push input, pull output. schedulers have pull input, push output. thin wrappers for hardware have push output or pull input only. push or pull handled by method calls Lee, Berkeley 34

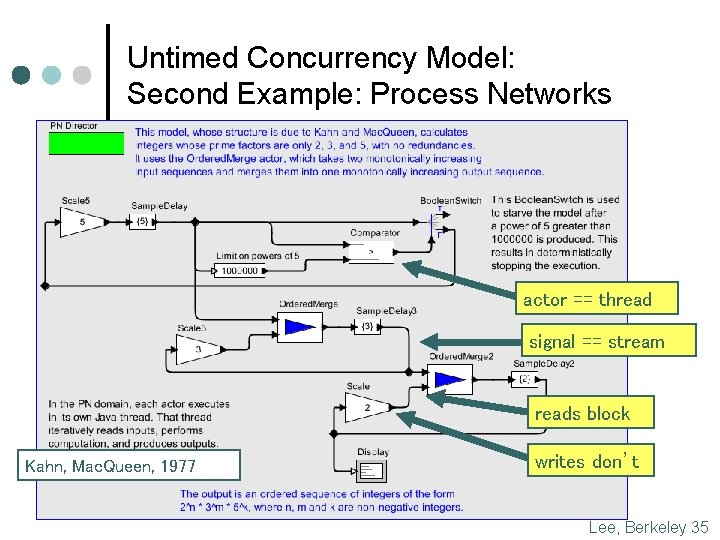
Untimed Concurrency Model: Second Example: Process Networks actor == thread signal == stream reads block Kahn, Mac. Queen, 1977 writes don’t Lee, Berkeley 35

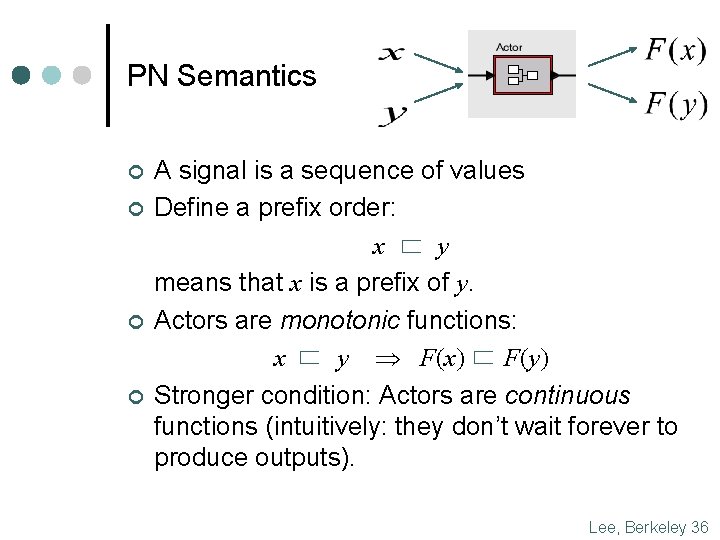
PN Semantics ¢ ¢ A signal is a sequence of values Define a prefix order: x y means that x is a prefix of y. Actors are monotonic functions: x y F(x) F(y) Stronger condition: Actors are continuous functions (intuitively: they don’t wait forever to produce outputs). Lee, Berkeley 36

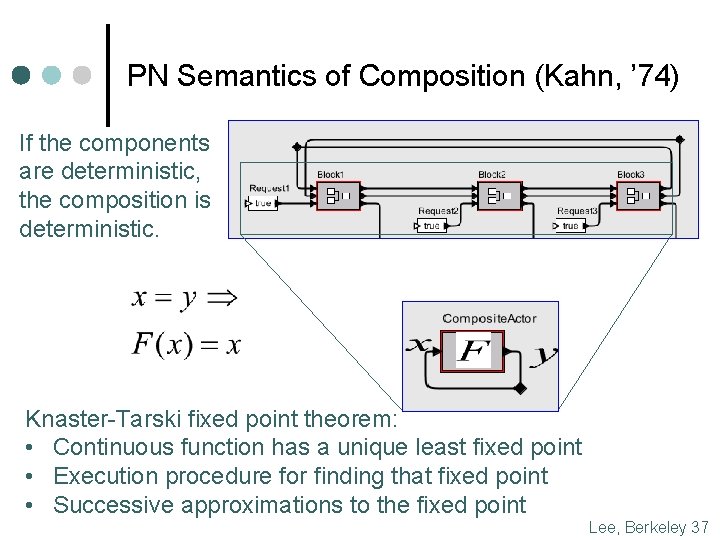
PN Semantics of Composition (Kahn, ’ 74) If the components are deterministic, the composition is deterministic. Knaster-Tarski fixed point theorem: • Continuous function has a unique least fixed point • Execution procedure for finding that fixed point • Successive approximations to the fixed point Lee, Berkeley 37

Distributed Process Networks Transport mechanism between hosts is provided by the director. Transparently provides guaranteed delivery and ordered messages. Created by Dominique Ragot, Thales Communications Lee, Berkeley 38

Kepler: Extensions to Ptolemy II for Scientific Workflows Example showing a web service wrapper (Thanks to Bertram Ludaecher, San Diego Supercomputer Center) Lee, Berkeley 39

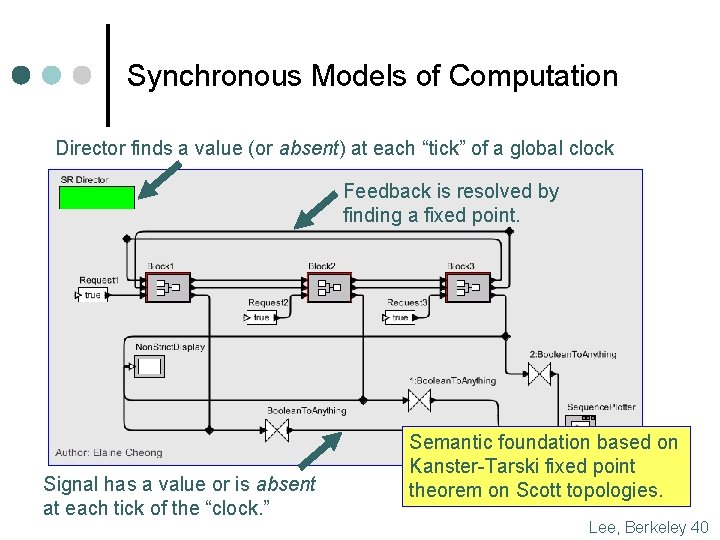
Synchronous Models of Computation Director finds a value (or absent) at each “tick” of a global clock Feedback is resolved by finding a fixed point. Signal has a value or is absent at each tick of the “clock. ” Semantic foundation based on Kanster-Tarski fixed point theorem on Scott topologies. Lee, Berkeley 40

Languages Based on the Synchronous Model of Computation ¢ ¢ ¢ Lustre (and SCADE) Esterel Signal Statecharts (and UML state machines) Argos … Lee, Berkeley 41

Dataflow Models of Computation ¢ ¢ ¢ ¢ ¢ Computation graphs [Karp & Miller - 1966] Process networks [Kahn - 1974] Static dataflow [Dennis - 1974] Dynamic dataflow [Arvind, 1981] K-bounded loops [Culler, 1986] Synchronous dataflow [Lee & Messerschmitt, 1986] Structured dataflow [Kodosky, 1986] PGM: Processing Graph Method [Kaplan, 1987] Synchronous languages [Lustre, Signal, 1980’s] Well-behaved dataflow [Gao, 1992] Boolean dataflow [Buck and Lee, 1993] Multidimensional SDF [Lee, 1993] Cyclo-static dataflow [Lauwereins, 1994] Integer dataflow [Buck, 1994] Bounded dynamic dataflow [Lee and Parks, 1995] Heterochronous dataflow [Girault, Lee, & Lee, 1997] … Many tools, software frameworks, and hardware architectures have been built to support one or more of these. Lee, Berkeley 42

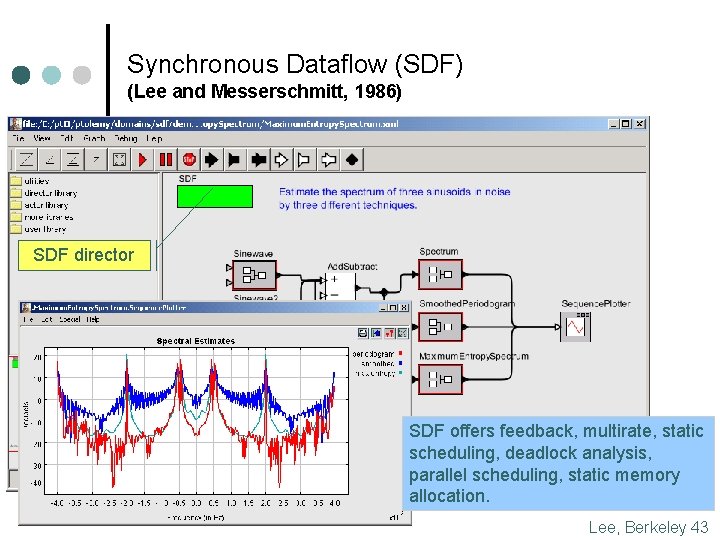
Synchronous Dataflow (SDF) (Lee and Messerschmitt, 1986) SDF director SDF offers feedback, multirate, static scheduling, deadlock analysis, parallel scheduling, static memory allocation. Lee, Berkeley 43

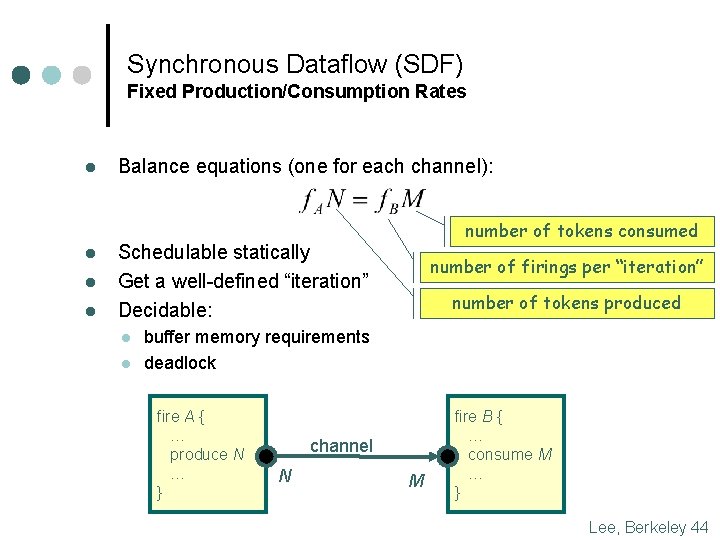
Synchronous Dataflow (SDF) Fixed Production/Consumption Rates l l Balance equations (one for each channel): number of tokens consumed Schedulable statically Get a well-defined “iteration” Decidable: l l number of firings per “iteration” number of tokens produced buffer memory requirements deadlock fire A { … produce N … } channel N M fire B { … consume M … } Lee, Berkeley 44

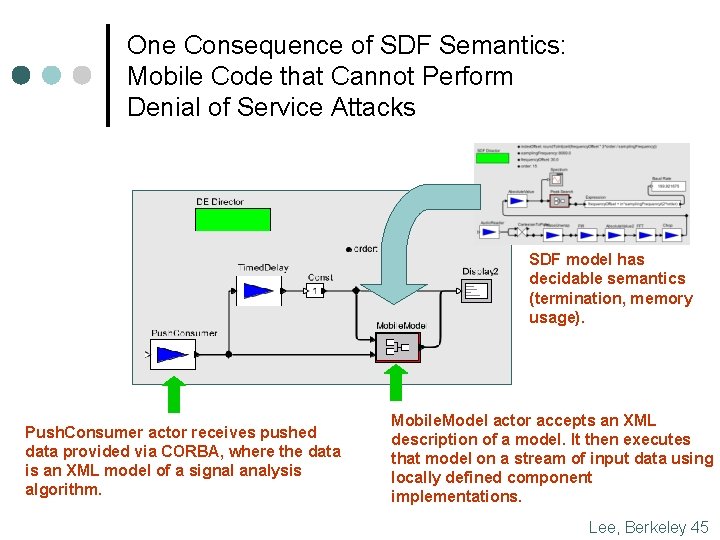
One Consequence of SDF Semantics: Mobile Code that Cannot Perform Denial of Service Attacks SDF model has decidable semantics (termination, memory usage). Push. Consumer actor receives pushed data provided via CORBA, where the data is an XML model of a signal analysis algorithm. Mobile. Model actor accepts an XML description of a model. It then executes that model on a stream of input data using locally defined component implementations. Lee, Berkeley 45

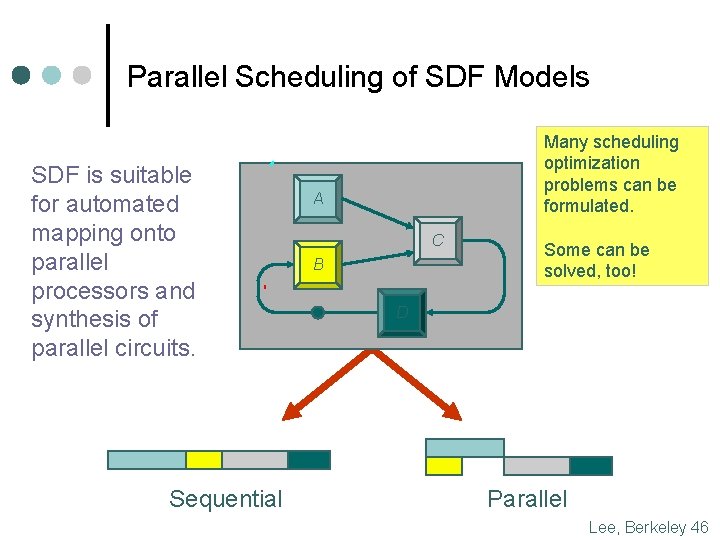
Parallel Scheduling of SDF Models SDF is suitable for automated mapping onto parallel processors and synthesis of parallel circuits. Sequential Many scheduling optimization problems can be formulated. A C B Some can be solved, too! D Parallel Lee, Berkeley 46

Scheduling Tradeoffs (Bhattacharyya, Parks, Pino) Scheduling strategy Code Data Minimum buffer schedule, no looping 13735 32 Minimum buffer schedule, with looping 9400 32 Worst minimum code size schedule 170 1021 Best minimum code size schedule 170 264 Source: Shuvra Bhattacharyya Lee, Berkeley 47

Minimum Buffer Schedule ABABCABCDEAFFFFFBABCABCABABCDE AFFFFFBCABABCABCABABCDEAFFFFFBCABABCABC DEAFFFFFBABCABCABCDEAFFFFFBABCABCA BABCDEAFFFFFBCABABCABCABABCDEAFFFFFEBCA FFFFFBABCABCDEAFFFFFBABCABCABCDEAF FFFFBABCABCABABCDEAFFFFFBCABABCABCABABC DEAFFFFFBCABABCABCDEAFFFFFBABCABCABABCA BCDEAFFFFFBABCABCABABCDEAFFFFFEBCAFFFFFB ABCABCABABCDEAFFFFFBCABABCABCDEAFFFFFBA BCABCABCDEAFFFFFBABCABCABABCDEAFFF FFBCABABCABCABABCDEAFFFFFBCABABCABCDEAF FFFFBABCABCABCDEAFFFFFEBAFFFFFBCABC ABABCDEAFFFFFBCABABCABCABABCDEAFFFFFBCA BABCABCDEAFFFFFBABCABCABCDEAFFFFFB ABCABCABABCDEAFFFFFBCABABCABCABABCDEAF FFFFBCABABCABCDEFFFFF Source: Shuvra Bhattacharyya Lee, Berkeley 48

Selected Generalizations ¢ Multidimensional Synchronous Dataflow (1993) l l ¢ Cyclo-Static Dataflow (Lauwereins, et al. , 1994) l ¢ l l Firings scheduled at run time Challenge: maintain bounded memory, deadlock freedom, liveness Demand driven, data driven, and fair policies all fail Kahn Process Networks (1974 -) l l ¢ Balance equations are solved symbolically Permits data-dependent routing of tokens Heuristic-based scheduling (undecidable) Dynamic Dataflow (1981 -) l ¢ Periodically varying production/consumption rates Boolean & Integer Dataflow (1993/4) l ¢ Arcs carry multidimensional streams One balance equation per dimension per arc Replace discrete firings with process suspension Challenge: maintain bounded memory, deadlock freedom, liveness Heterochronous Dataflow (1997) l l Combines state machines with SDF graphs Very expressive, yet decidable Lee, Berkeley 49

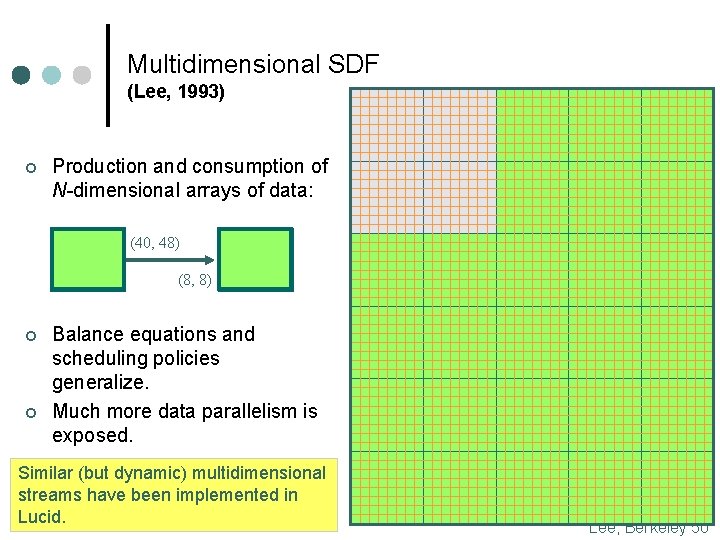
Multidimensional SDF (Lee, 1993) ¢ Production and consumption of N-dimensional arrays of data: (40, 48) (8, 8) ¢ ¢ Balance equations and scheduling policies generalize. Much more data parallelism is exposed. Similar (but dynamic) multidimensional streams have been implemented in Lucid. Lee, Berkeley 50

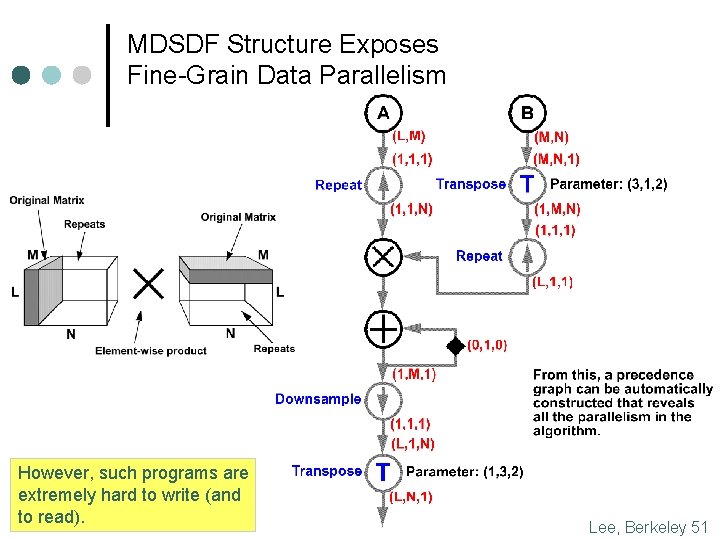
MDSDF Structure Exposes Fine-Grain Data Parallelism However, such programs are extremely hard to write (and to read). Lee, Berkeley 51

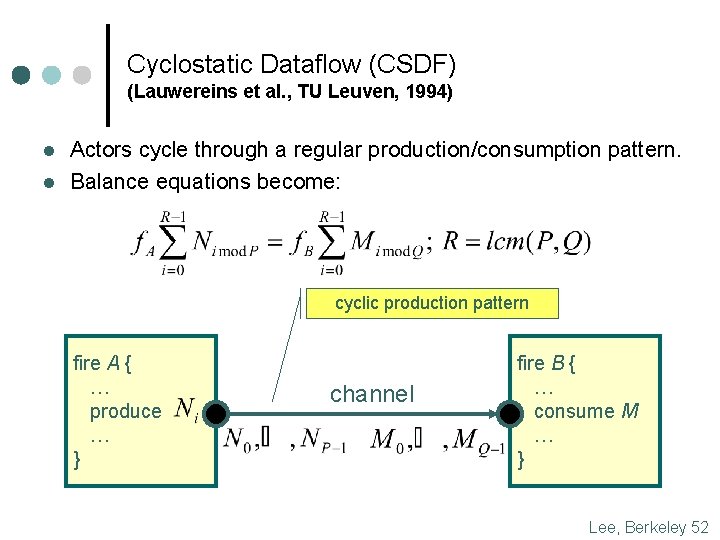
Cyclostatic Dataflow (CSDF) (Lauwereins et al. , TU Leuven, 1994) l l Actors cycle through a regular production/consumption pattern. Balance equations become: cyclic production pattern fire A { … produce … } channel fire B { … consume M … } Lee, Berkeley 52

Boolean and Integer Dataflow (BDF, IDF) (Lee and Buck, 1993) ¢ A D b B b 1 - b C 1 - b select ¢ Balance equations are solved symbolically in terms of unknowns that become known at run time. An annotated schedule is constructed with predicates guarding each action. Existence of such an annotated schedule is undecidable (as is deadlock & bounded memory) switch ¢ E b Production rate is unknown and is represented symbolically by a variable (b). Lee, Berkeley 53

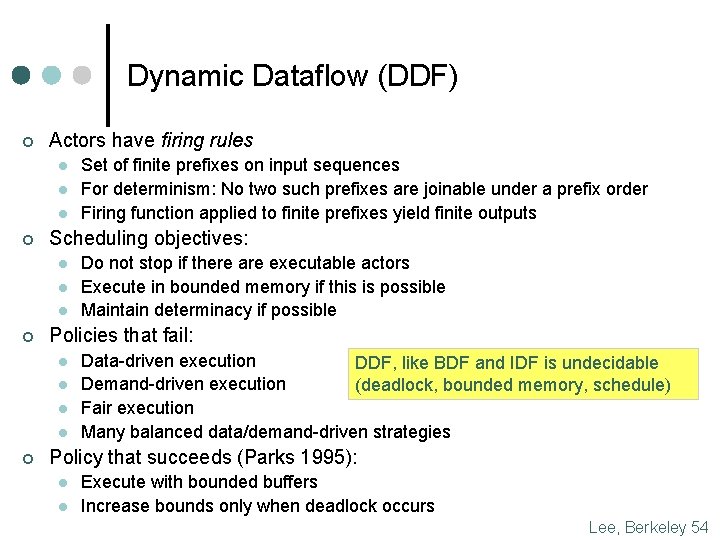
Dynamic Dataflow (DDF) ¢ Actors have firing rules l l l ¢ Scheduling objectives: l l l ¢ Do not stop if there are executable actors Execute in bounded memory if this is possible Maintain determinacy if possible Policies that fail: l l ¢ Set of finite prefixes on input sequences For determinism: No two such prefixes are joinable under a prefix order Firing function applied to finite prefixes yield finite outputs Data-driven execution DDF, like BDF and IDF is undecidable Demand-driven execution (deadlock, bounded memory, schedule) Fair execution Many balanced data/demand-driven strategies Policy that succeeds (Parks 1995): l l Execute with bounded buffers Increase bounds only when deadlock occurs Lee, Berkeley 54

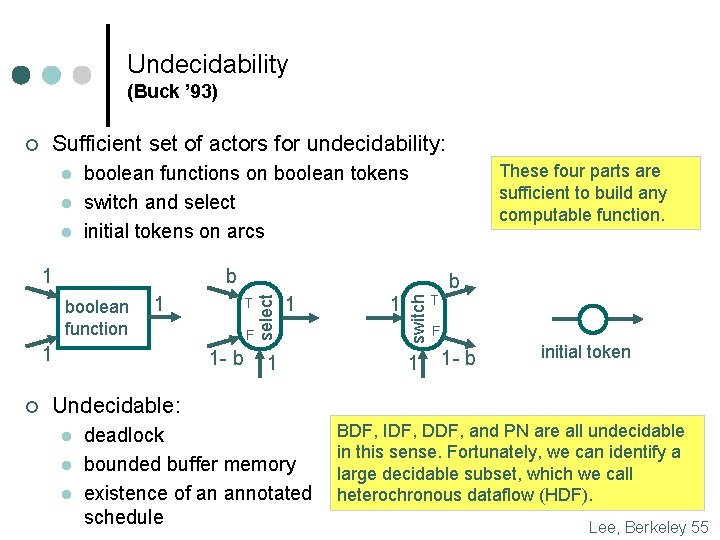
Undecidability (Buck ’ 93) Sufficient set of actors for undecidability: l l l b boolean function 1 1 b T F 1 - b 1 1 1 switch 1 ¢ These four parts are sufficient to build any computable function. boolean functions on boolean tokens switch and select initial tokens on arcs select ¢ 1 T F 1 - b initial token Undecidable: l l l deadlock bounded buffer memory existence of an annotated schedule BDF, IDF, DDF, and PN are all undecidable in this sense. Fortunately, we can identify a large decidable subset, which we call heterochronous dataflow (HDF). Lee, Berkeley 55

Example of a Heterochronous Dataflow Model An actor consists of a state machine and refinements to the states that define behavior. Lee, Berkeley 56

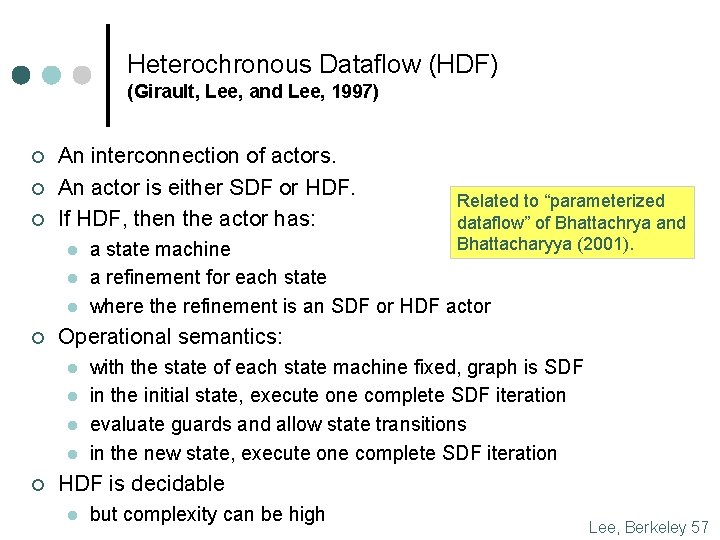
Heterochronous Dataflow (HDF) (Girault, Lee, and Lee, 1997) ¢ ¢ ¢ An interconnection of actors. An actor is either SDF or HDF. If HDF, then the actor has: l l l ¢ a state machine a refinement for each state where the refinement is an SDF or HDF actor Operational semantics: l l ¢ Related to “parameterized dataflow” of Bhattachrya and Bhattacharyya (2001). with the state of each state machine fixed, graph is SDF in the initial state, execute one complete SDF iteration evaluate guards and allow state transitions in the new state, execute one complete SDF iteration HDF is decidable l but complexity can be high Lee, Berkeley 57

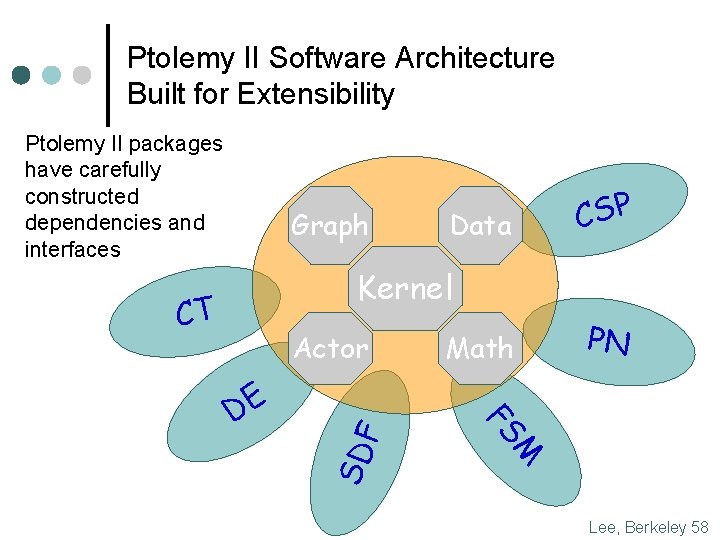
Ptolemy II Software Architecture Built for Extensibility Ptolemy II packages have carefully constructed dependencies and interfaces Graph Data CSP Kernel CT Math PN M FS DE SD F Actor Lee, Berkeley 58

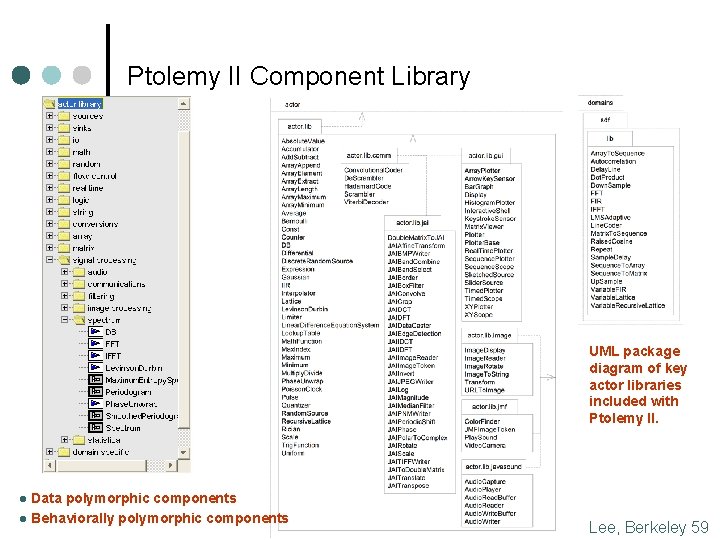
Ptolemy II Component Library UML package diagram of key actor libraries included with Ptolemy II. Data polymorphic components l Behaviorally polymorphic components l Lee, Berkeley 59

Polymorphic Components - Component Library Works Across Data Types and Domains ¢ Data polymorphism: l l ¢ Add numbers (int, float, double, Complex) Add strings (concatenation) Add composite types (arrays, records, matrices) Add user-defined types Behavioral polymorphism: l l l l In dataflow, add when all connected inputs have data In a time-triggered model, add when the clock ticks In discrete-event, add when any connected input has data, and add in zero time In process networks, execute an infinite loop in a thread that blocks when reading empty inputs In CSP, execute an infinite loop that performs rendezvous on input or output In push/pull, ports are push or pull (declared or inferred) and behave accordingly In real-time CORBA, priorities are associated with ports and a dispatcher determines when to add By not choosing among these when defining the component, we get a huge increment in component reusability. But how do we ensure that the component will work in all these circumstances? Lee, Berkeley 60

Shared Infrastructure Modularity Mechanisms execution local class definition instance inherited actors override actors subclass Lee, Berkeley 61

More Shared Infrastructure: Hierarchical Heterogeneity and Modal Models continuoustime model modal model dataflow controller example Ptolemy II model: hybrid control system Lee, Berkeley 62

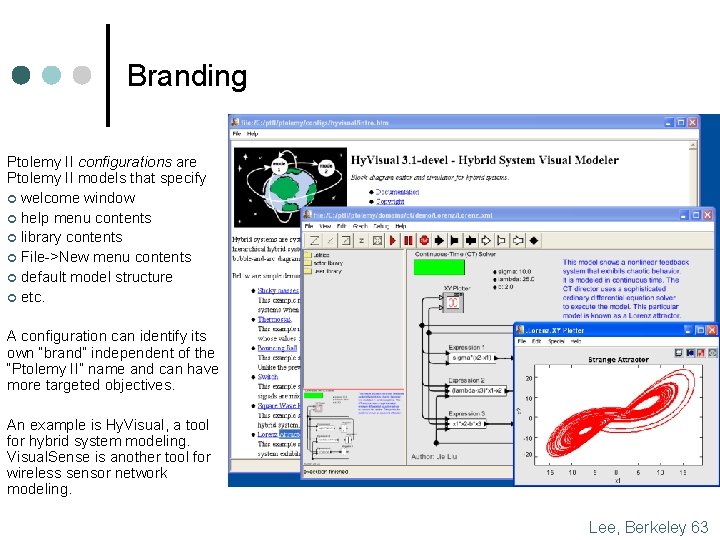
Branding Ptolemy II configurations are Ptolemy II models that specify ¢ welcome window ¢ help menu contents ¢ library contents ¢ File->New menu contents ¢ default model structure ¢ etc. A configuration can identify its own “brand” independent of the “Ptolemy II” name and can have more targeted objectives. An example is Hy. Visual, a tool for hybrid system modeling. Visual. Sense is another tool for wireless sensor network modeling. Lee, Berkeley 63

Ptolemy II Extension Points ¢ ¢ ¢ ¢ Define actors Interface to foreign tools (e. g. Python, MATLAB) Interface to verification tools (e. g. Chic) Define actor definition languages Define directors (and models of computation) Define visual editors Define textual syntaxes and editors Packaged, branded configurations All of our “domains” are extensions built on a core infrastructure. Lee, Berkeley 64

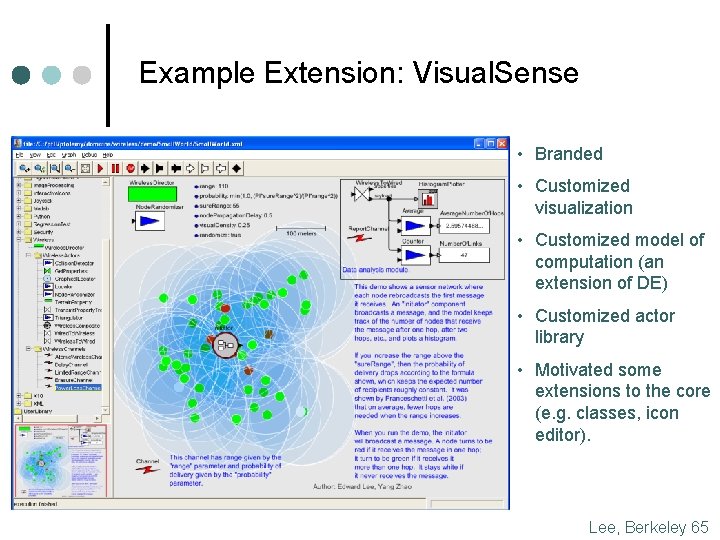
Example Extension: Visual. Sense • Branded • Customized visualization • Customized model of computation (an extension of DE) • Customized actor library • Motivated some extensions to the core (e. g. classes, icon editor). Lee, Berkeley 65

Example Extensions: Self-Repairing Models Concept demonstration built together with Boeing to show to write actors that adaptively reconstruct connections when the model structure changes. Lee, Berkeley 66

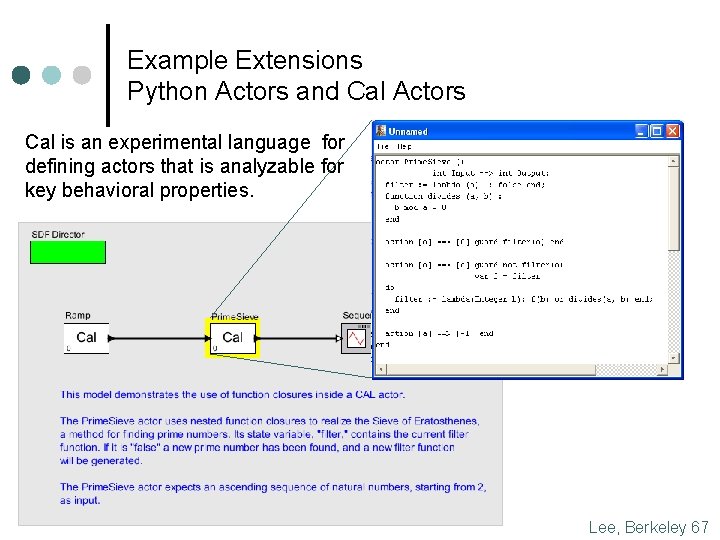
Example Extensions Python Actors and Cal Actors Cal is an experimental language for defining actors that is analyzable for key behavioral properties. Lee, Berkeley 67

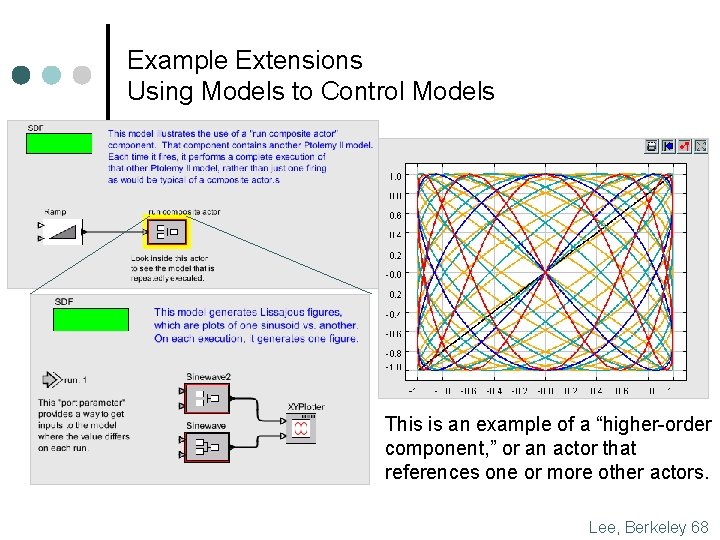
Example Extensions Using Models to Control Models This is an example of a “higher-order component, ” or an actor that references one or more other actors. Lee, Berkeley 68

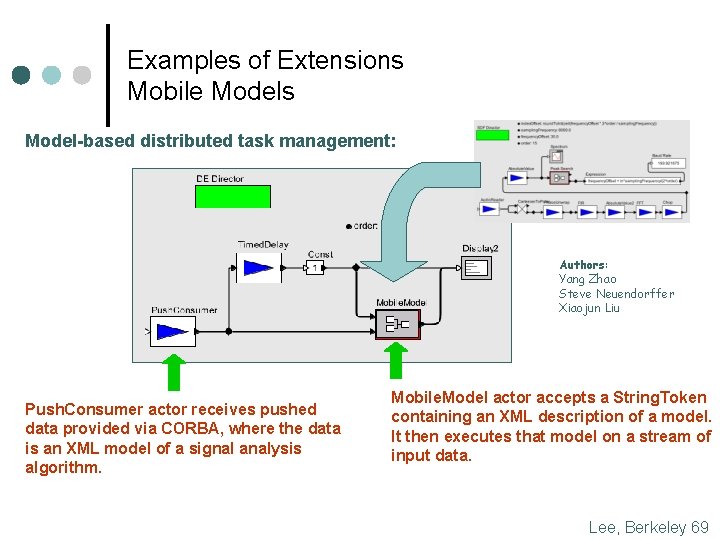
Examples of Extensions Mobile Models Model-based distributed task management: Authors: Yang Zhao Steve Neuendorffer Xiaojun Liu Push. Consumer actor receives pushed data provided via CORBA, where the data is an XML model of a signal analysis algorithm. Mobile. Model actor accepts a String. Token containing an XML description of a model. It then executes that model on a stream of input data. Lee, Berkeley 69

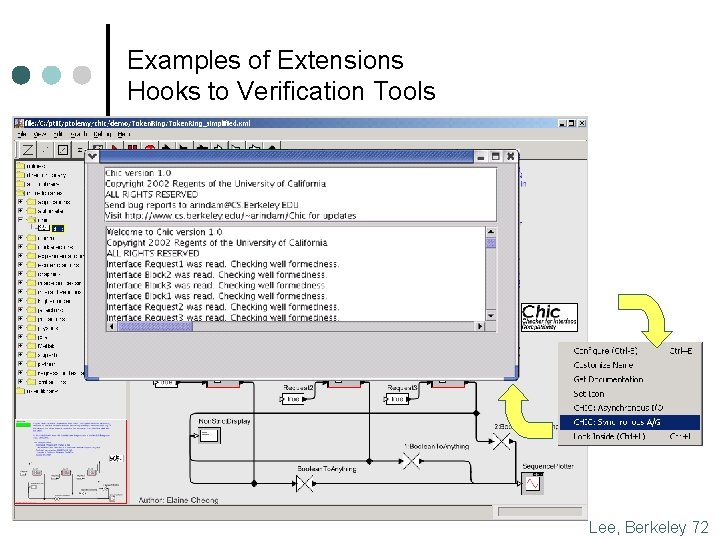
Examples of Extensions Hooks to Verification Tools New component interfaces to Chic verification tool Authors: Arindam Chakrabarti Eleftherios Matsikoudis Lee, Berkeley 70

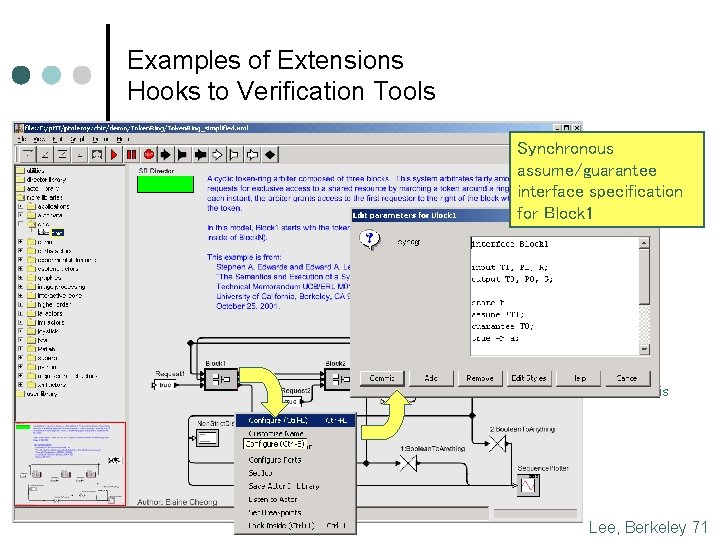
Examples of Extensions Hooks to Verification Tools Synchronous assume/guarantee interface specification for Block 1 Authors: Arindam Chakrabarti Eleftherios Matsikoudis Lee, Berkeley 71

Examples of Extensions Hooks to Verification Tools Lee, Berkeley 72

Conclusion ¢ ¢ ¢ Threads suck There are many alternative concurrent Mo. Cs The ones you know are the tip of the iceberg Ptolemy II is a lab for experimenting with them Specializing Mo. Cs can be useful Mixing specialized Mo. Cs can be useful. Lee, Berkeley 73