Concurrency Deadlock Starvation Chapter summary Chapter 6 Principles








- Slides: 17

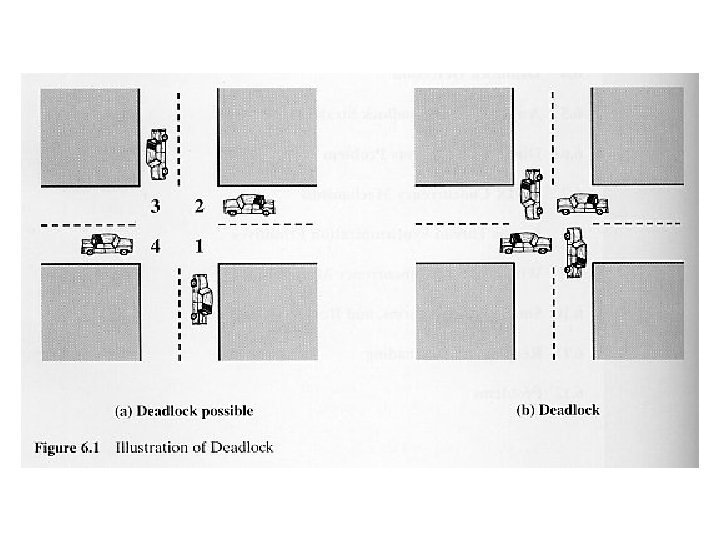
Concurrency: Deadlock & Starvation • Chapter summary: (Chapter 6) – Principles of deadlock & starvation problem – Three common approaches to deal with deadlock: prevention, detection, and avoidance – Dining philosophers problem • Deadlock is defined as the permanent blocking of a set of processes that either compete for system resources or communicate with each other. • All deadlocks involve conflicting needs for resources by two or more processes.




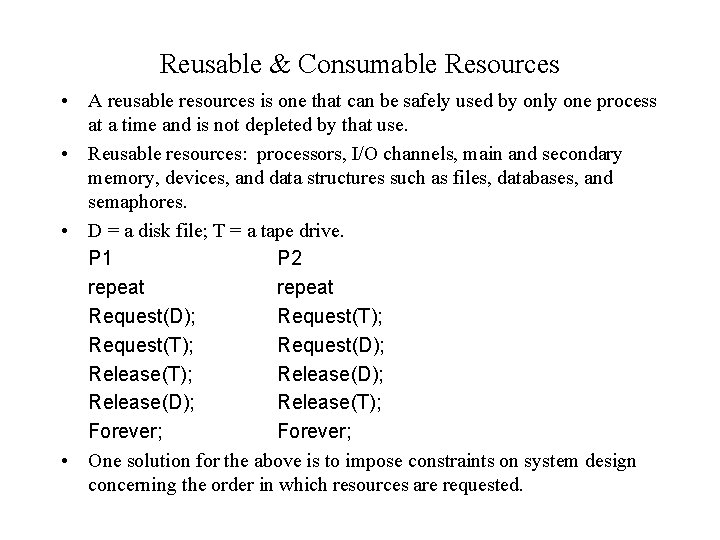
Reusable & Consumable Resources • A reusable resources is one that can be safely used by only one process at a time and is not depleted by that use. • Reusable resources: processors, I/O channels, main and secondary memory, devices, and data structures such as files, databases, and semaphores. • D = a disk file; T = a tape drive. P 1 P 2 repeat Request(D); Request(T); Request(D); Release(T); Release(D); Release(T); Forever; • One solution for the above is to impose constraints on system design concerning the order in which resources are requested.

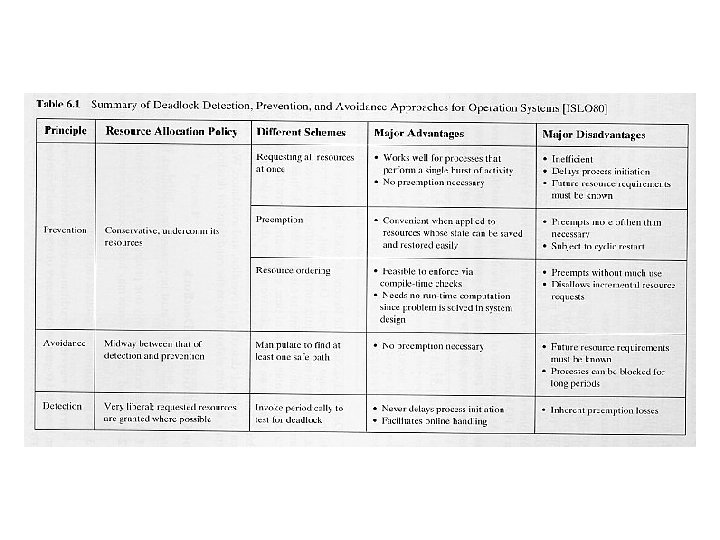
Reusable & Consumable Resources (continue) • • • Main memory available = 200 KB; P 1 P 2 Request 80 KB Request 70 KB Request 60 KB Request 80 KB Solution: use virtual memory (Chapter 7) A consumable resource is one that can be created (produced) and destroyed (consumed). Consumable resources: interrupts, signals, messages, and information in I/O buffers. Deadlock occurs if the Receive is blocking. P 1 P 2 Receive(P 2, M); Receive(P 1, Q); Send(P 2, N); Send(P 1, R); Table 5. 1 summarizes the key elements of the most important approaches that have been developed: prevention, detection, & avoidance.

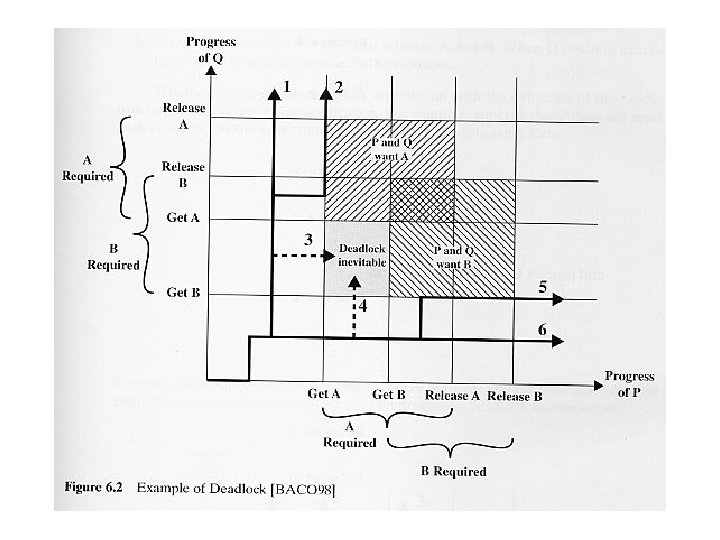
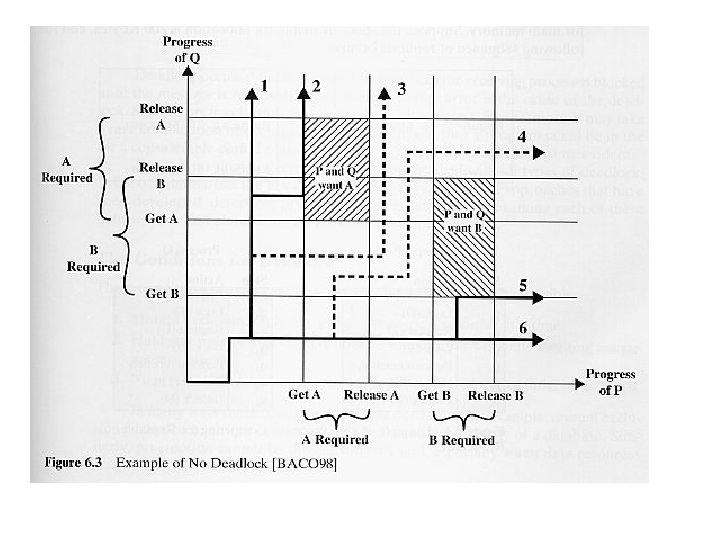
The Conditions for Deadlock Three conditions of policy must be present for it to be possible for a deadlock to occur: • Mutual exclusion: Only one process may use a resource at a time. • Hold-and-wait: A process may hold allocated resources while awaiting assignment of others. • No preemption: No resource can be forcibly removed from a process holding it. Deadlock can exist with these three conditions but may not exist with only these conditions. For deadlock actually to take place, a fourth condition is required: • Circular wait: A closed chain of processes exists, such that each process holds at least one resource needed by the next process in the chain.


Deadlock Prevention • To design a system in such a way that the possibility of deadlock is excluded a priori. • Two methods: 1) indirect way to prevent the occurrence of one of the three conditions; 2) direct way to prevent the occurrence of a circular wait; • Mutual Exclusion: If you need it, you cannot prevent it! • Hold-and-Wait: Request all the resources at one time and blocking the process until all request can be granted simultaneously. This is inefficient: – 1) a process may be held up for a long time, waiting for all its resources request to be filled, while instead it can start with some of its resources; – 2) resources may remain used for a long time, but cannot be used by other processes.

Deadlock Prevention (continue) • No Preemption: 1) If a process holding certain resources is denied a further request, that process must release its original resources and if necessary request them again, together with the additional resource; 2) if a process requests a resource that is currently held by another process, the OS may preempt the second process and require it to release its resources; This approach is practical only when applied to resources whose states can be easily saved and restored later, as in the case with a processor. • Circular Wait: By defining a linear ordering of resources types. If a process has been allocated resources of type R, then it may subsequently request only those resources of type following R in the ordering. As with Hold-and-Wait prevention, circular wait prevention may be inefficient, slowing down processes and denying resource access unnecessarily.

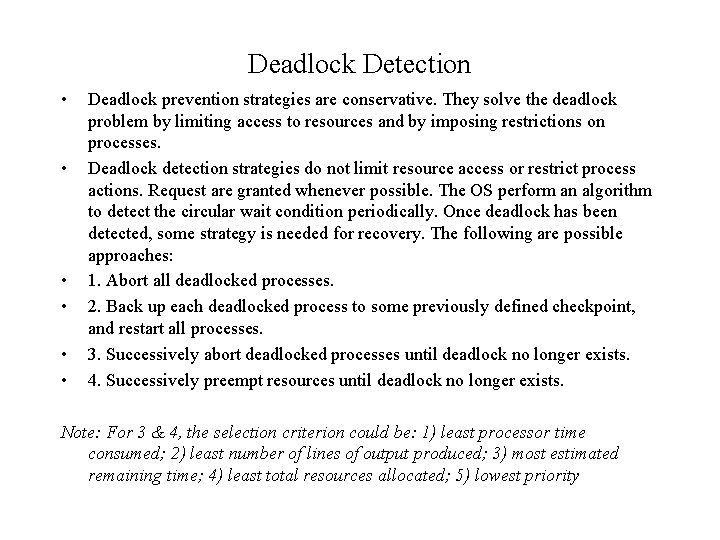
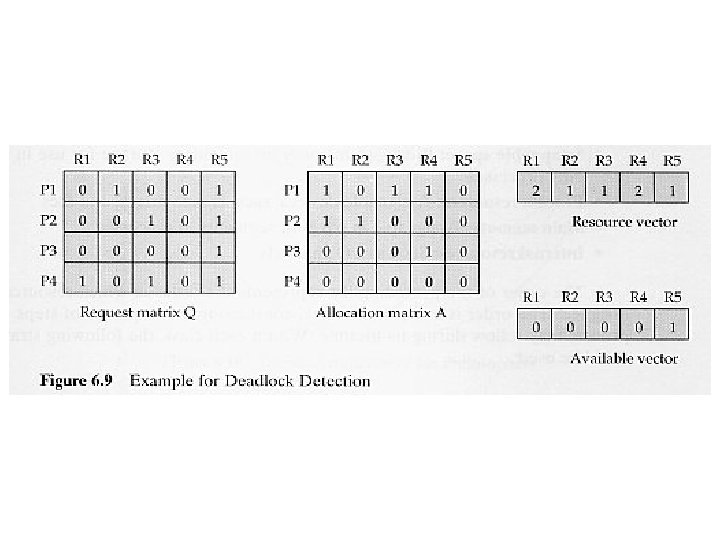
Deadlock Detection • • • Deadlock prevention strategies are conservative. They solve the deadlock problem by limiting access to resources and by imposing restrictions on processes. Deadlock detection strategies do not limit resource access or restrict process actions. Request are granted whenever possible. The OS perform an algorithm to detect the circular wait condition periodically. Once deadlock has been detected, some strategy is needed for recovery. The following are possible approaches: 1. Abort all deadlocked processes. 2. Back up each deadlocked process to some previously defined checkpoint, and restart all processes. 3. Successively abort deadlocked processes until deadlock no longer exists. 4. Successively preempt resources until deadlock no longer exists. Note: For 3 & 4, the selection criterion could be: 1) least processor time consumed; 2) least number of lines of output produced; 3) most estimated remaining time; 4) least total resources allocated; 5) lowest priority

Deadlock Avoidance Deadlock avoidance allows the three necessary conditions but makes judicious choices to assure that the deadlock point is never reached. Two approaches to deadlock avoidance: • Do not start a process if its demands might lead to deadlock • Do not grant an incremental resource request to a process if this allocation might lead to deadlock Process Initiation Denial: • All resources are either allocated or available • No process can claim more than the total amount of resources in the system • No process is allocated more resources of any type than the process originally claimed to need • A process is started only if the maximum claim of all current processes plus those of the new process can be met.

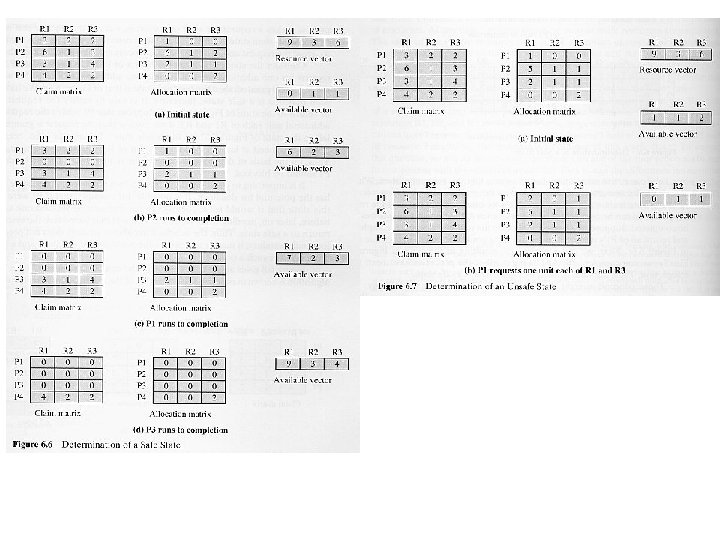
Deadlock Avoidance (continue) Resource Allocation Denial: • Referred to as Banker's algorithm. • Safe and Unsafe state: – A safe state is a state in which there is at least one order in which all the processes can be run to completion without resulting in a deadlock. – An unsafe state is a state that is not safe!! • Resource is granted to a process only if such allocation leads the system to a safe state. Otherwise, the resource will not be granted and the process blocked. (Refer to Figure 6. 6 & 6. 7) Disadvantages: – The Max. resources requirement for each process must be stated in advance. – The processes under consideration must be independent; – There must be a fixed number of resources to allocate and a fixed number of processes.



An Integrated Deadlock Strategy • • • Group resources into a number of different resource classes. Use linear ordering strategy for the prevention of circular wait. Within a resource class, use the algorithm that is most appropriate for that class. Categorized resources into the following classes: – Swappable space: Block of memory on sec. storage. – Process resources: Assignable devices, such as tape drives, and files. – Main memory: Assignable in pages or segments to processes. – Internal resources: I/O channels. Strategy for each class: – Swappable space: Prevention -- requiring that all the required resources be allocated at one time. – Process resources: Avoidance -- since resources required are usually declared ahead of time. – Main memory: Prevention by preemption. When a process is preempted, it is simply swapped to sec. memory, freeing space to resolve the deadlock. – Internal resources: Prevention by means of resources ordering can be used.
