Computer Security Web Security Web Security Important growing

Computer Security Web Security

Web Security Important, growing security area n ~65% of all attacks occur through port 80 (http: //www. incidents. org ) Two major aspects n Server Security Web Server Database Server n Application Security

General Web Process Browser sends request to web server Server processes request Server sends response to browser Browser receives information and code <repeat>
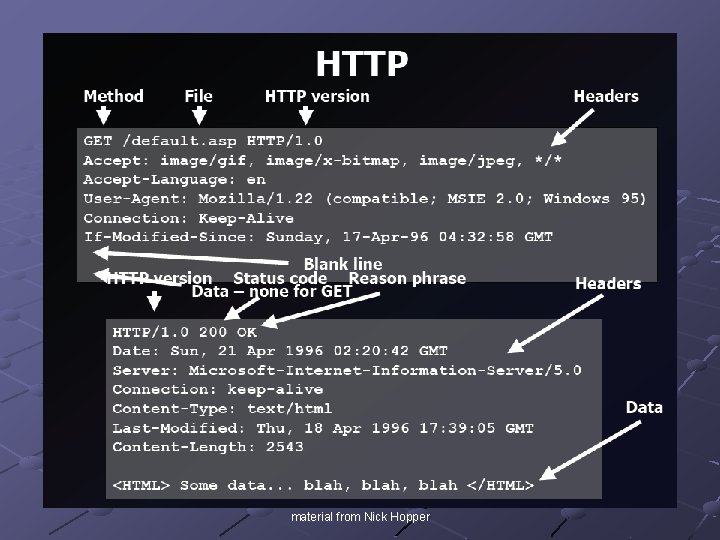
Request/Response Content material from Nick Hopper

Aspects of Web Multiple Languages n HTML, DHTML, XML, Perl, PHP, Cold. Fusion, Java, JSPs, ASP, CGI (in turn, can be Perl, C, C++, Java, …) Multiple Server Types n Apache, IIS, others…. Interaction of Layers n OS Utilities, Shell/Environment, Application Code

Authentication on the Web Two major choices n Container based Done by web container (J 2 EE, . NET) n Application based Done by application itself
Container-Based Authentication Responsibility for authentication is with servlet/JSP container Four methods n n HTTP basic authentication HTTP digest authentication HTTPS client authentication Form-based authentication

HTTP Basic Authentication browser asks for access to resource server sends response asking for username and password browser prompts user for username and password browser sends same request but with authentication information, converted to base 64 problem: not seriously encrypted

HTTP Digest Authentication Server sends response to browser, along with special string called a nonce n nonce contains timestamp, resource info. , server identifier Browser creates a message digest (checksum value) of username, password, nonce value, HTTP method, and requested URL Advantage: encrypted, time-sensitive Problem: not broadly supported

HTTPS Client Authentication User imports a public-key certificate from the server n User must also support SSL Server acknowledges this, maintains secure connection with authorization for this user Advantage: no public communication of information Disadvantages: must support SSL, server must have certificate

Form-Based Authentication Unique to servlet specification Set up login screen as a special HTML file with mandatory input fields j_username and j_password, action set to j_security_check Disadvantage: no encryption

Who is a valid user? Depends on system Can be set up through: n n n separate file (e. g. tomcat-users. xml) operating system users (e. g. Microsoft Internet Information Server (IIS)) external directory server (e. g. Lightweight Directory Access Protocol - LDAP)
Application-Based Authentication Problem with container-based authentication in general: not dynamic n i. e. can’t add users while application running Application-Based Authentication allows dynamic update of users
Application Authentication Process Tasks n n n User registration Login page Authentication mechanism (invoked by login page) Information saved in session scope to prove authentication Validation of session information in all JSPs requiring restricted access

Authentication Overall problem approaches n n n Bad (weak or misused) cryptography Using username or a user ID only as authentication Using a session ID as authentication
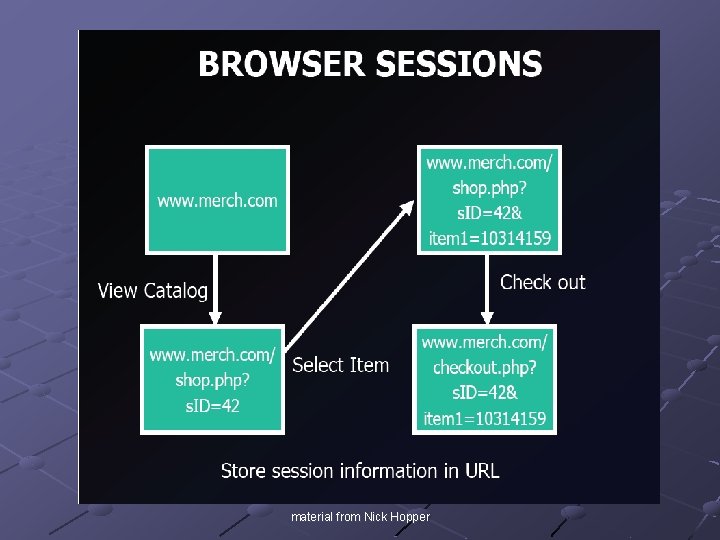
Browser Sessions material from Nick Hopper
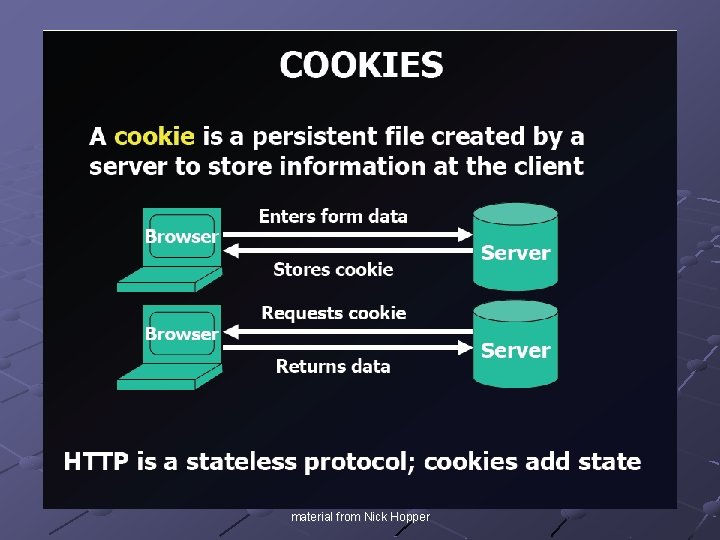
Cookies material from Nick Hopper

Cookies (2) Cookies specify which web sites can access them n Usually only the creating site can access the cookie Cookies can be persistent or temporary Cookies are a privacy risk n Can store browsing habits, personal information Cookies are often not secured against malicious attack n Should be encrypted with good crypto some material from Nick Hopper

Privacy Proxies Stand between Browser and Network Can intercept HTTP requests and responses to enforce a given privacy policy n Examples Modify cookies before sending to browser or server Filter ads Block certain sites

Issues with Application Authentication and Encryption SSL can protect data, but…. Headers are still unencrypted, open to attack One solution: IPSec (IP Security) n n Transport Mode: data only encrypted Tunnel Mode: data and headers encrypted Used to implement virtual private networks (VPNs) RFC 2411
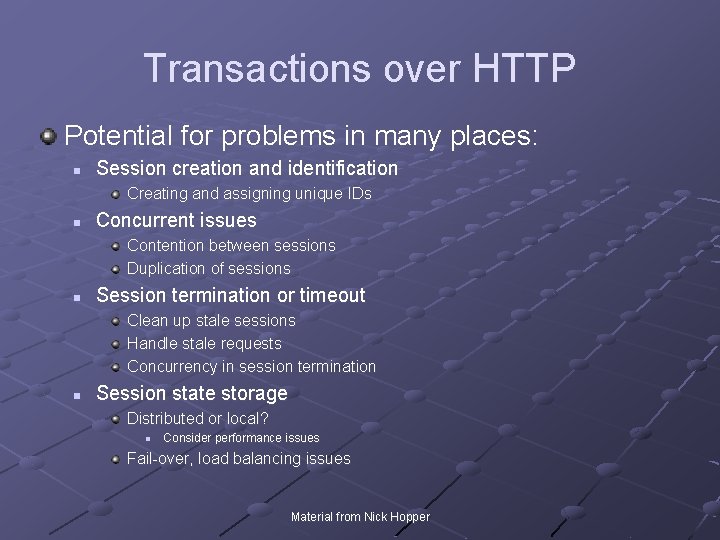
Transactions over HTTP Potential for problems in many places: n Session creation and identification Creating and assigning unique IDs n Concurrent issues Contention between sessions Duplication of sessions n Session termination or timeout Clean up stale sessions Handle stale requests Concurrency in session termination n Session state storage Distributed or local? n Consider performance issues Fail-over, load balancing issues Material from Nick Hopper

E-Commerce Systems Layers on Front-End Server n n Catalog Shopping Cart Session Management Payment System Layers on Back-End DB Server n Inventory, Customers, etc. Separate servers n Payment, Credit

Shopping Cart Issues Allow remote command execution Store temporary information in clear-text temporary files Allow arbitrary command execution on server Insecure hidden fields with price, identification information Unencrypted transmission of information between any servers, or between client and server
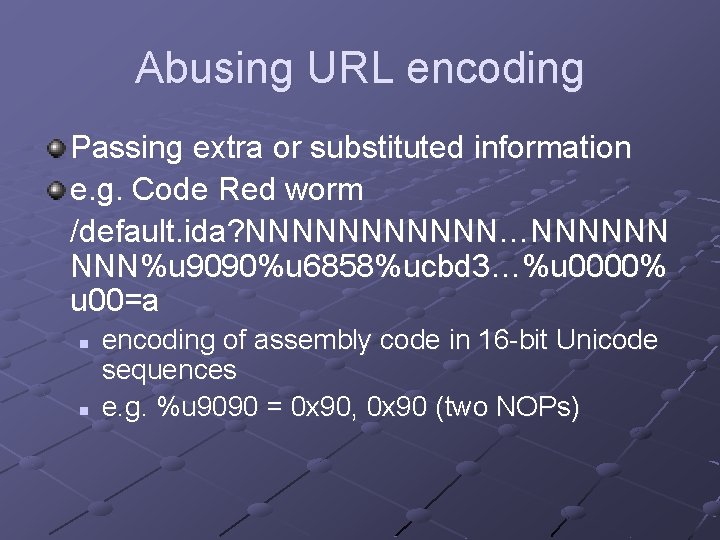
Abusing URL encoding Passing extra or substituted information e. g. Code Red worm /default. ida? NNNNNN…NNNNNN NNN%u 9090%u 6858%ucbd 3…%u 0000% u 00=a n n encoding of assembly code in 16 -bit Unicode sequences e. g. %u 9090 = 0 x 90, 0 x 90 (two NOPs)

Footprinting Web Applications Forcing errors can cause display of useful information, such as DB type Countermeasures n n n Configure web server to return minimum amount of information in HTTP Header Do not return any plug-in information Don’t send error information back to browser
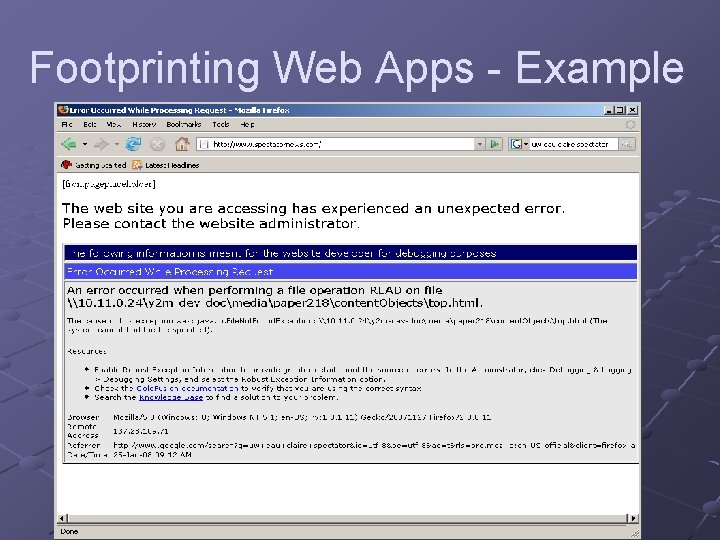
Footprinting Web Apps - Example

Site Linkage Analysis Use webcrawlers to analyze site Several webcrawlers commonly used for this n n n GNU wget Black. Widow Funnel Web Profiler
Issues – Cross Site Scripting (XSS) Occurs on writeable web sites (e. g. guestbooks, BBS systems) Attacker writes in Java. Script, HTTP link, etc. n Often encoded in hex to make it look less suspicious Unwary subject clicks on link, can be rerouted to rogue site, with several possible problems n n Session hijacking Information and/or cookie theft Prevention n n (Server-side) Don’t trust input, filter metacharacters (Client-side) Be careful when following links, go directly to known sites http: //www. cgisecurity. com/articles/xss-faq. shtml

Issues – Poisoning Cache poisoning n My site/script loads as your actual URL Cookie poisoning n Set my cookies for your site some material from Nick Hopper
Issues – Use of Non-Secrets www. fatbrain. com (now part of Barnes and Noble) Use logged in, assigned a session ID in URL Knowing the s. ID allows access to a session IDs were assigned as follows: global_current_id = random_integer(); while (more sessions) next_id = global_current_id++; Similar problem with major wireless carrier! material from Nick Hopper

Issues – Cyber Graffiti Use of scripts to gain access to system, modify pages Sometimes automated (e. g. if web site has automatic upload area)

Issues – E-Shoplifting Alteration of hidden fields in forms sent as part of process n n n Avoid use of such hidden fields Ensure information encrypted in process Don’t use client-side scripts to validate input

Web Site Security Challenging, for a variety of reasons: n n Sessions store state on the client side Inputs come from unknown, untrusted sources Stateless model of HTTP allows attacks through replays, modification, injection, etc. Mutually untrusted applications may use the same server, interact

Issues – Server Side Buffer overflows, format string errors, integer overflows Command line injection n E. g. “cat reply | mail $user” => “cat reply | mail user@example. com | rm –rf / “ SQL/Xpath Injection n More soon URL Injection n n PHP fopen(“/local/file”, “r”) PHP fopen(http: //www. example. com/remote/file, “r”)
Issues - Interaction of Web and Database Server Do not pass data in URL n Hacker can often find pattern in syntax Various forms of SQL injection/poisoning n n Data producing Error producing
Issues – Interaction of Java and Web Server Isolate core Java servlets from application servlets Prohibit execution of unregistered servlets (e. g. Web. Sphere) Bind servlets to resource types Validate input thoroughly Disable direct application servlet invocation Unregister unused and example servlets

Web Services Security Two Major Issues n Security of Components in different implementations Java – J 2 EE, EJBs. NET – ADO. NET, . NET Framework n Security of Common Structure XML SOAP WSDL n Generalized Markup Language – SAML Security Assertion Markup Language

Overall Defense Validate any input from web n Check that is valid format Example: email only alphanum, @, . n Whitelist valid characters Not as effective to blacklist known bad characters n n Apply checking before and after all decoding and conversions Use language-specific tools Example: Perl taint mode material from Nick Hopper

References “Hacking Web Applications Exposed”, Scambray and Shema, Mc. Graw. Hill/Osborne, 2002 “Web Hacking: Attacks and Defense”, Mc. Clure, Shah and Shah, Addison. Wesley, 2003 “Web Security, Privacy and Commerce”, Garfinkel and Spafford, O’Reilly, 2002 “Mastering Web Services Security”, Hartman et. al. , Wiley, 2003
- Slides: 39