Computer Security Principles and Practice Chapter 9 Firewalls




















- Slides: 43

Computer Security: Principles and Practice Chapter 9 – Firewalls and Intrusion Prevention Systems Second Edition by William Stallings and Lawrie Brown Lecture slides by Susan Lincke & Lawrie Brown

Chapter Objectives: The student should be able to: Describe the different types of firewalls: Circuit, Application Proxy, Packet, Stateful, Personal including how they differ in an example attack that each can fend off. Describe 3 firewall vulnerabilities Draw configurations for network types: double inline, T, multihomed, distributed, load balanced. Describe what a firewall policy is, give an example policy, and indicate how a policy may be used Describe each of the following: border router, static and dynamic NAT and PAT.

Security: Defense in Depth Border Router Perimeter firewall Internal firewall Intrusion Detection System Policies & Procedures & Audits Authentication Access Controls

Firewall Required Functions: Serve as an entry point into a network Screens all packets entering the network Service control Direction control User control Behavior control (access only part of Web service) Log and alarm events Perform Network Address Translation functions (optional) Perform Virtual Private Network functions (optional) Support no other functions (that can be compromised)

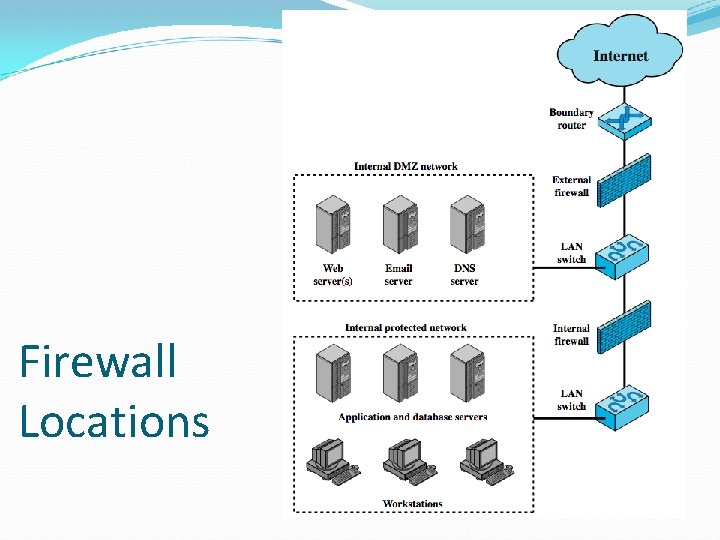
Firewall Locations

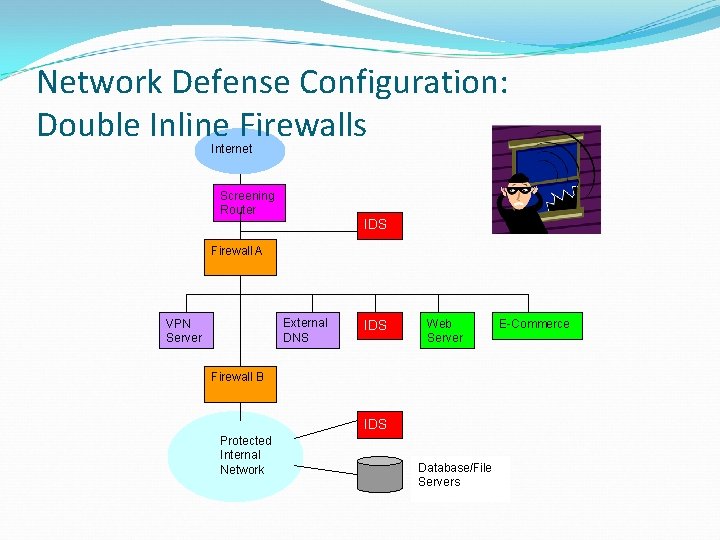
Network Defense Configuration: Double Inline Firewalls Internet Screening Router IDS Firewall A External DNS VPN Server IDS Web Server Firewall B IDS Protected Internal Network Database/File Servers E-Commerce

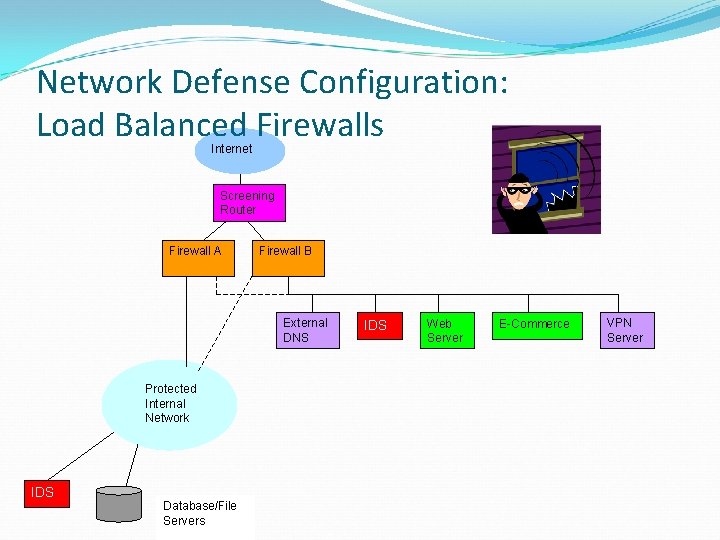
Network Defense Configuration: Load Balanced Firewalls Internet Screening Router Firewall A Firewall B External DNS Protected Internal Network IDS Database/File Servers IDS Web Server E-Commerce VPN Server

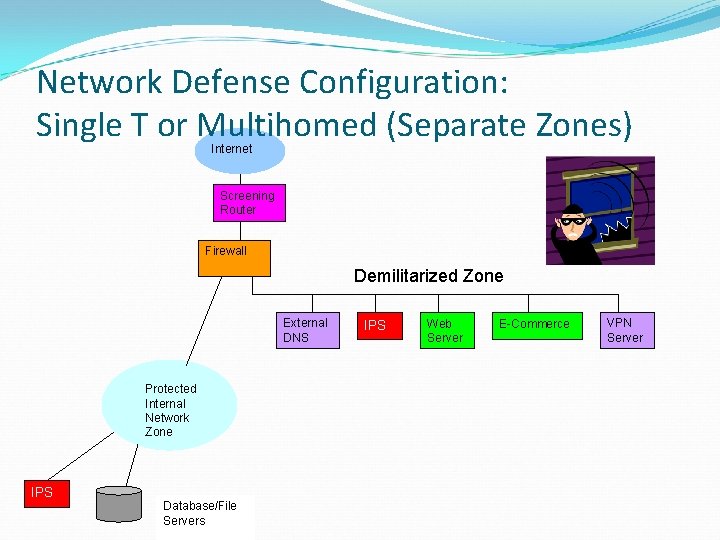
Network Defense Configuration: Single T or Multihomed (Separate Zones) Internet Screening Router Firewall Demilitarized Zone External DNS Protected Internal Network Zone IPS Database/File Servers IPS Web Server E-Commerce VPN Server

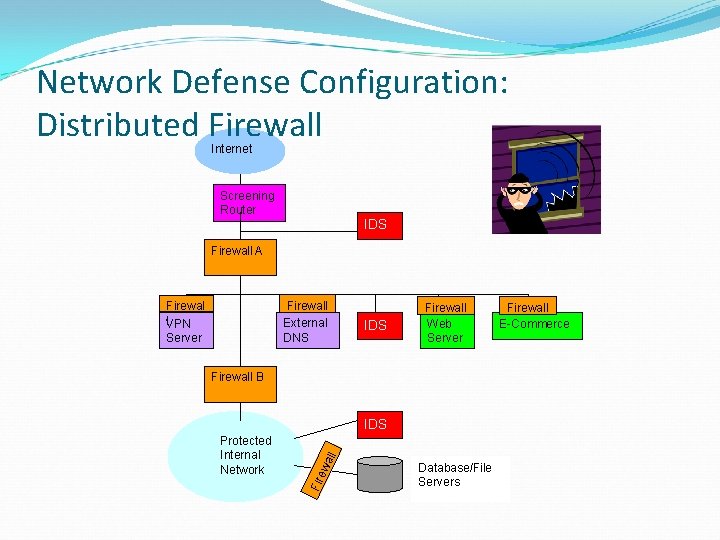
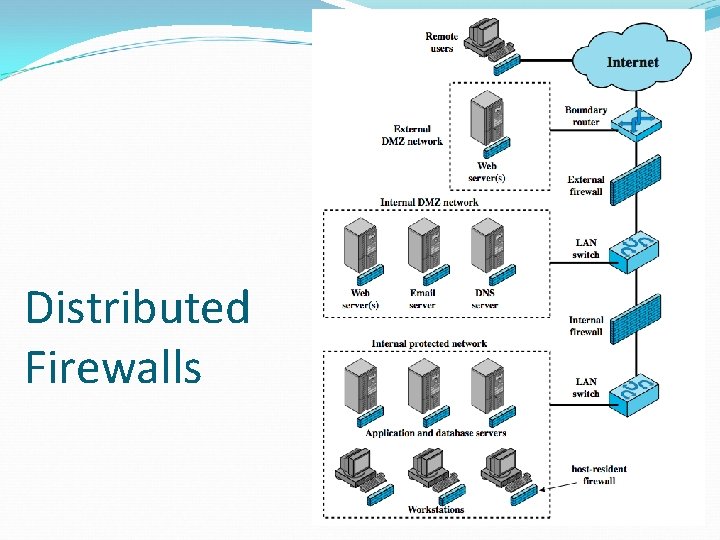
Network Defense Configuration: Distributed Firewall Internet Screening Router IDS Firewall A Firewall External DNS Firewal l. VPN Server IDS Firewall Web Server Firewall B Fir ew Protected Internal Network all IDS Database/File Servers Firewall E-Commerce

Bastion Hosts critical strongpoint in network hosts application/circuit-level gateways common characteristics: runs secure O/S, only essential services may require user auth to access proxy or host each proxy can restrict services & hosts accessed each proxy small, simple, checked for security each proxy is independent, non-privileged proxy disk use is boot only; hence read-only code

Firewall Topologies host-resident firewall screening router single bastion inline: One firewall single bastion T: with 3 zones double bastion inline: Serial firewalls double bastion T: with 3 zones distributed firewall configuration: double with host firewalls

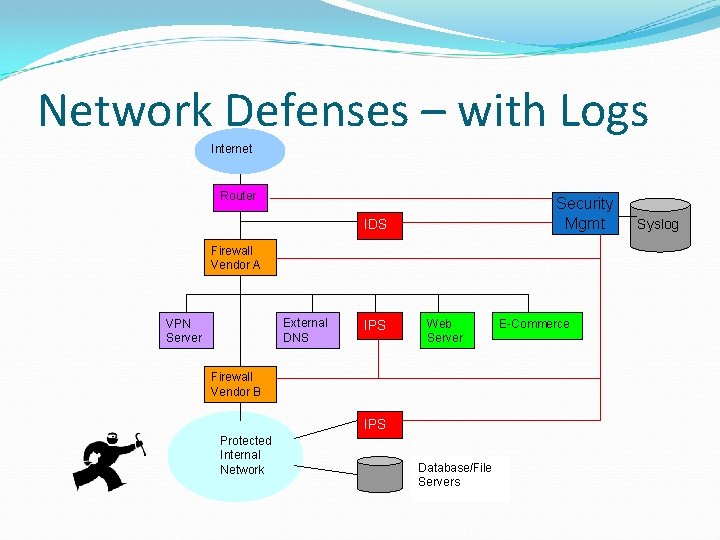
Network Defenses – with Logs Internet Router Security Mgmt IDS Firewall Vendor A External DNS VPN Server IPS Web Server Firewall Vendor B IPS Protected Internal Network Database/File Servers E-Commerce Syslog

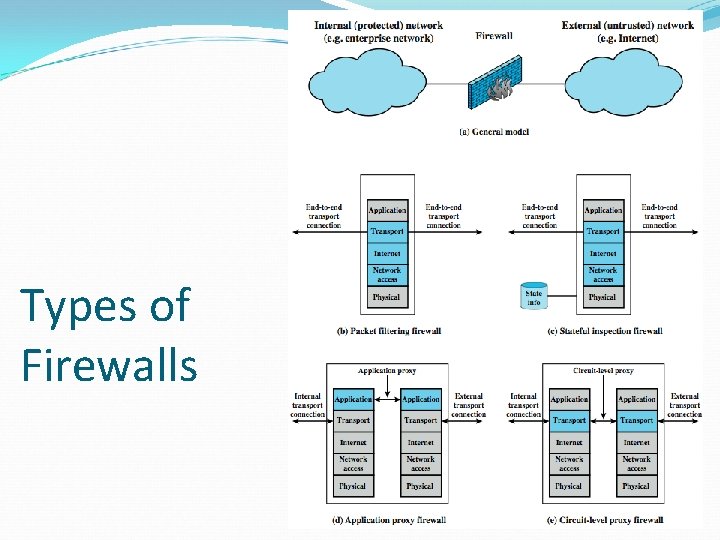
Types of Firewalls

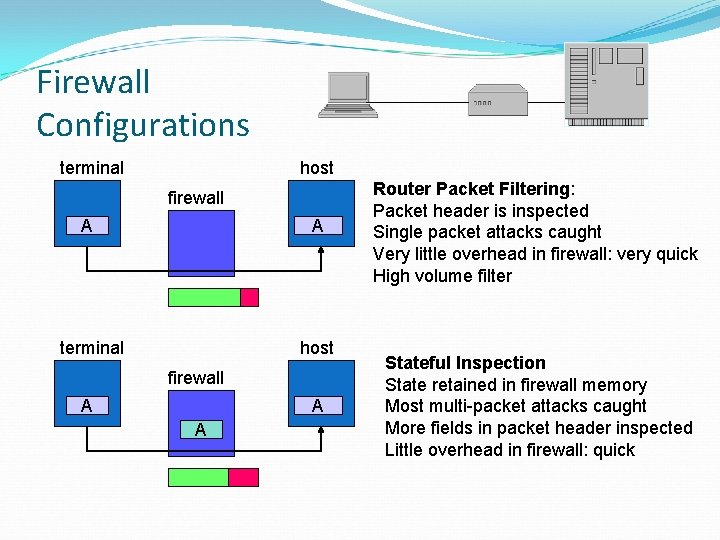
Firewall Configurations terminal host firewall A A A Router Packet Filtering: Packet header is inspected Single packet attacks caught Very little overhead in firewall: very quick High volume filter Stateful Inspection State retained in firewall memory Most multi-packet attacks caught More fields in packet header inspected Little overhead in firewall: quick

Packet Filtering Firewall applies rules to packets in/out of firewall based on information in packet header src/dest IP addr & port, IP protocol, interface typically a list of rules of matches on fields if match rule says if forward or discard packet two default policies: discard - prohibit unless expressly permitted forward - permit unless expressly prohibited

Packet Filter Problems In heavy load may forward all packets without logging Cannot catch application-level errors ICMP can have invalid contents FTP, RPC use ports > 1023, dynamically allocated Cannot recognized spoofed IP or port addresses Do not support advanced user authentication Tiny fragments can hide attacks Improper configuration can lead to breaches Routers can do packet filtering, most firewalls do more

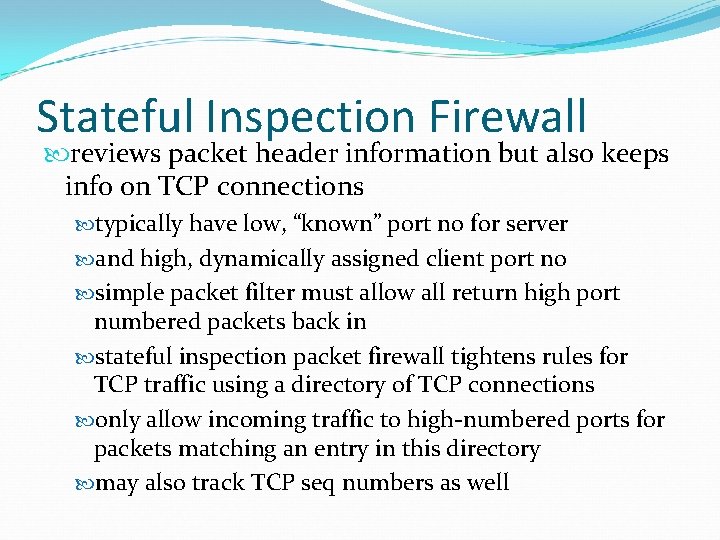
Stateful Inspection Firewall reviews packet header information but also keeps info on TCP connections typically have low, “known” port no for server and high, dynamically assigned client port no simple packet filter must allow all return high port numbered packets back in stateful inspection packet firewall tightens rules for TCP traffic using a directory of TCP connections only allow incoming traffic to high-numbered ports for packets matching an entry in this directory may also track TCP seq numbers as well

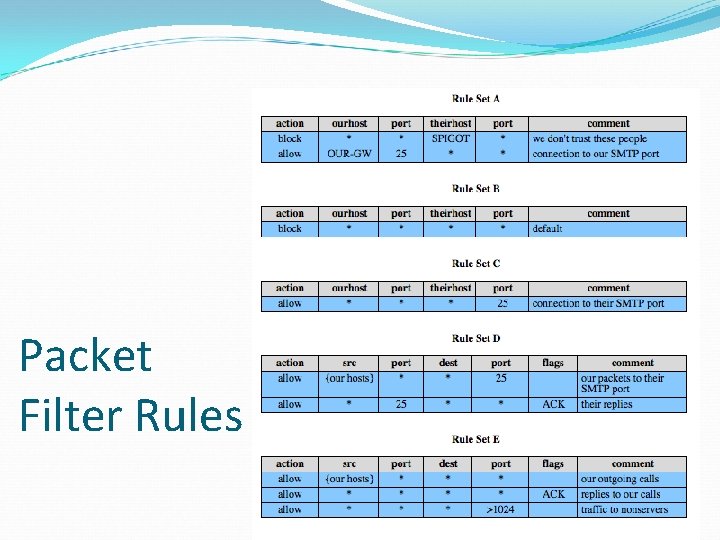
Packet Filter Rules

Stateful Packet Filters Tracks TCP/UDP connection status Can configure outbound-only connections Packets are allowed in if connection is established Records source/destination IP and port addresses, protocol (TCP/UDP), timer expiration TCP: Also supports TCP state, Sequence numbers UDP: Supports expiration timer, pseudo state May prevent fragmentation attacks Advantage: Supports higher loads than Circuit-Level Firewalls at same memory/processor speed levels Problems ICMP: Messages may come from intermediate node, not destination. Must accept/reject all ICMP messages of type N DOS Attack: Establish connections to fill table Applications change ports or use multiple ports: e. g. , ftp Application attacks not detected since application protocols not scanned Some routers support Stateful packet filtering; nearly all firewalls do

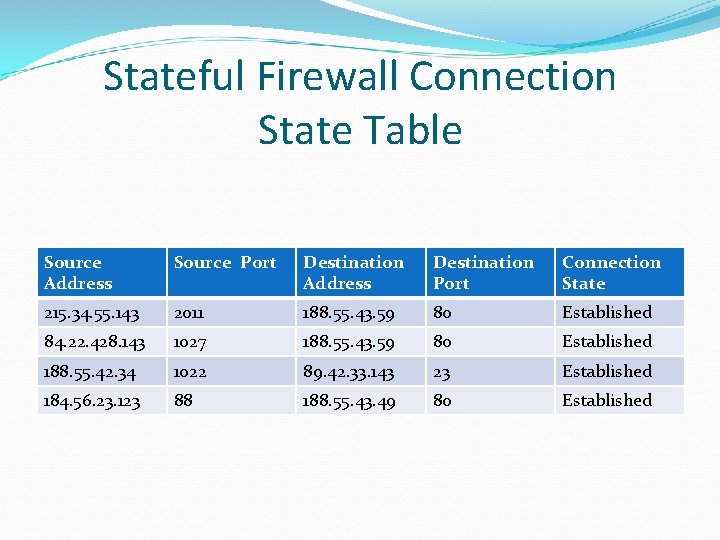
Stateful Firewall Connection State Table Source Address Source Port Destination Address Destination Port Connection State 215. 34. 55. 143 2011 188. 55. 43. 59 80 Established 84. 22. 428. 143 1027 188. 55. 43. 59 80 Established 188. 55. 42. 34 1022 89. 42. 33. 143 23 Established 184. 56. 23. 123 88 188. 55. 43. 49 80 Established

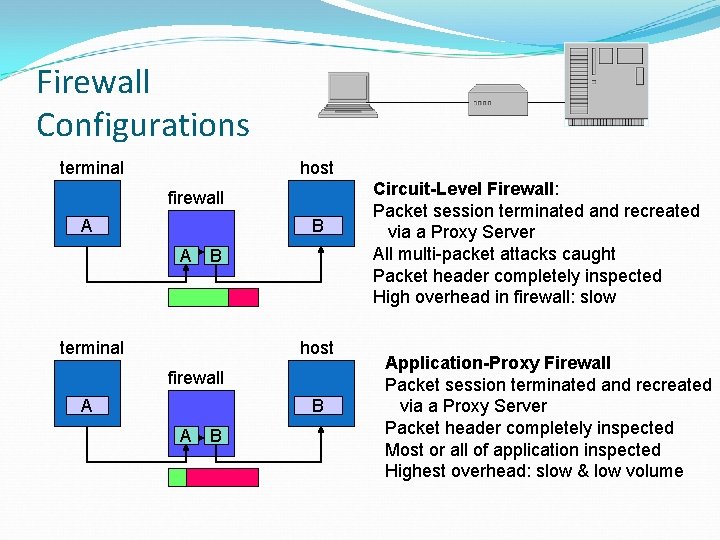
Firewall Configurations terminal host firewall A B A B Circuit-Level Firewall: Packet session terminated and recreated via a Proxy Server All multi-packet attacks caught Packet header completely inspected High overhead in firewall: slow Application-Proxy Firewall Packet session terminated and recreated via a Proxy Server Packet header completely inspected Most or all of application inspected Highest overhead: slow & low volume

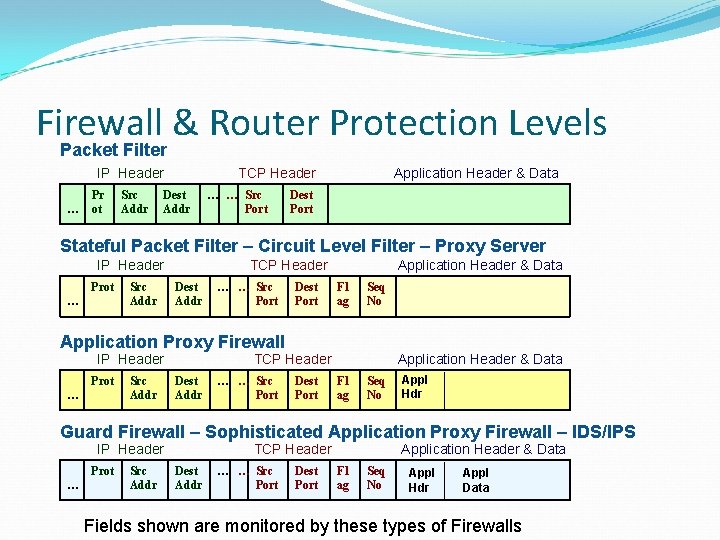
Firewall & Router Protection Levels Packet Filter IP Header … Pr ot Src Addr TCP Header Dest Addr … … Src Port Application Header & Data Dest Port Stateful Packet Filter – Circuit Level Filter – Proxy Server IP Header Prot … Src Addr TCP Header Dest Addr … … Src Port Dest Port Application Header & Data Fl ag Seq No Application Proxy Firewall IP Header Prot … Src Addr TCP Header Dest Addr … … Src Port Dest Port Application Header & Data Fl ag Seq No Appl Hdr Guard Firewall – Sophisticated Application Proxy Firewall – IDS/IPS IP Header Prot … Src Addr TCP Header Dest Addr … … Src Port Dest Port Application Header & Data Fl ag Seq No Appl Hdr Appl Data Fields shown are monitored by these types of Firewalls

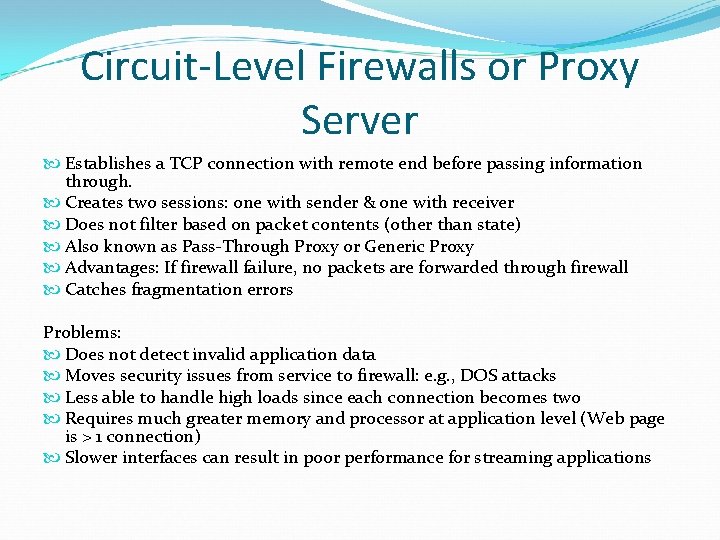
Circuit-Level Firewalls or Proxy Server Establishes a TCP connection with remote end before passing information through. Creates two sessions: one with sender & one with receiver Does not filter based on packet contents (other than state) Also known as Pass-Through Proxy or Generic Proxy Advantages: If firewall failure, no packets are forwarded through firewall Catches fragmentation errors Problems: Does not detect invalid application data Moves security issues from service to firewall: e. g. , DOS attacks Less able to handle high loads since each connection becomes two Requires much greater memory and processor at application level (Web page is > 1 connection) Slower interfaces can result in poor performance for streaming applications

Application Proxy Firewall Examines packets and their contents at the Application Layer Can cause delay due to additional processing May strip info on internal servers, server version on outgoing messages (e. g. , email) May allow only certain types of sessions through: FTP: May permit receives, no sends. Or sends of specific files only. Email: Encrypts email between all of company’s offices HTTP: May filter PUT commands, URL names. Can cache replies. Authentication: Perform extra authentication for external access (via dialup or internet)

Application-Level Gateway acts as a relay of application-level traffic user contacts gateway with remote host name authenticates themselves gateway contacts application on remote host and relays TCP segments between server and user must have proxy code for each application may restrict application features supported more secure than packet filters but have higher overheads

SOCKS Circuit-Level Gateway SOCKS v 5 defined as RFC 1928 to allow TCP/UDP client-server applications to use firewall components: SOCKS server on firewall SOCKS client library on all internal hosts SOCKS-ified client applications client app contacts SOCKS server, authenticates, sends relay request server evaluates & establishes relay connection UDP handled with parallel TCP control channel

Distributed Firewalls

Host-Based Firewalls often used on servers used to secure individual host available in/add-on for many O/S filter packet flows advantages: taylored filter rules for specific host needs protection from both internal / external attacks additional layer of protection to org firewall

Personal Firewall controls traffic flow to/from PC/workstation for both home or corporate use may be software module on PC or in home cable/DSL router/gateway typically much less complex primary role to deny unauthorized access may also monitor outgoing traffic to detect/block worm/malware activity

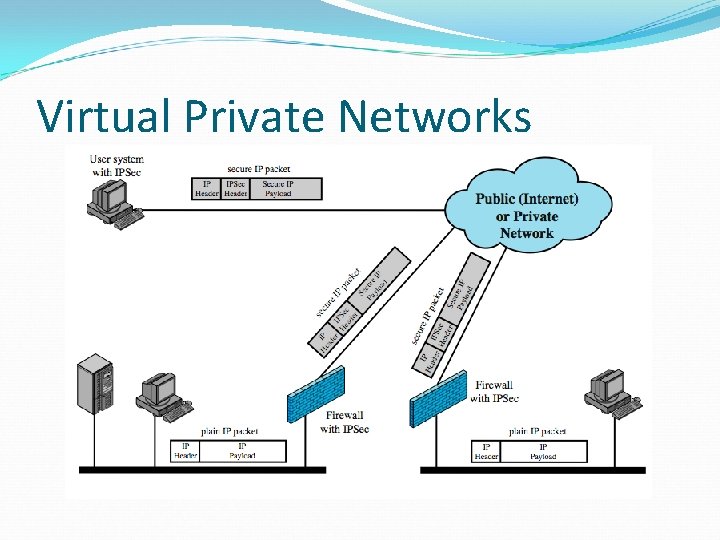
Virtual Private Networks

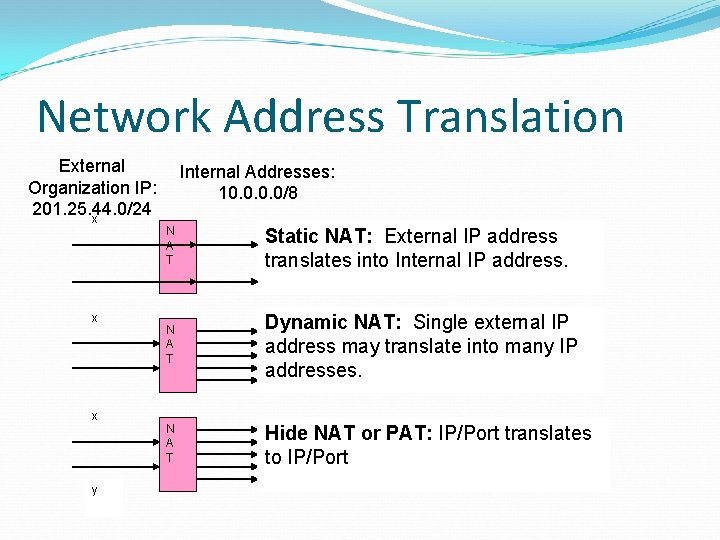
Network Address Translation External Organization IP: 201. 25. 44. 0/24 x x x y Internal Addresses: 10. 0/8 N A T Static NAT: External IP address translates into Internal IP address. N A T Dynamic NAT: Single external IP address may translate into many IP addresses. N A T Hide NAT or PAT: IP/Port translates to IP/Port

Network Address Translation Static NAT: One external IP address translates into one fixed internal IP address Dynamic NAT: Internal IP addresses are assigned an external IP address on a FCFS basis. Port Address Translation (PAT) or Hide NAT: Translates one incoming IP address/port into an internal IP address/port. Multiple internal IP addresses can map to one external IP address

Firewall Capabilities & Limits capabilities: defines a single choke point provides a location for monitoring security events convenient platform for some Internet functions such as NAT, usage monitoring, IPSEC VPNs limitations: cannot protect against attacks bypassing firewall may not protect fully against internal threats improperly secure wireless LAN laptop, PDA, portable storage device infected outside then used inside

Firewall Vulnerabilities Firewalls can be bypassed via other means (e. g. , modem, CDs) Data transmitted to the outside may be vulnerable Firewalls may lie: in heavy loads attack packets may get through without logging. Extra software on the firewall device increase vulnerability Firewalls are vulnerable if installed above a generalpurpose OS Firewalls do not prevent malicious acts within the network Layers of defense are safer than a single firewall Auditing: Scan weekly or at every change Retain a baseline of perimeter device configurations

Designing Firewalls/Routers Before creating a firewall configuration, create firewall policies. Firewall policy: An Access Control List (ACL) item in English Policies can be reviewed, turned into ACLs, and tested Example Policy: IP addresses with internal source addresses shall not be allowed into the internal network from the outside. Often ports > 1000 cannot be closed due to applications like FTP Other policies may deal with failover protection, detecting malicious code, …

Configuring Firewalls/Routers Put specific rules first, then general rules When a rule matches, no further testing is done. Minimize tests & speed processing by placing common rules first

Auditing Firewalls If there is no security policy, speak with mgmt about their expectations of the firewall After configuring the firewall, test the firewall by launching an attack Use a sniffer to determine which attack packets get through Other required operations include: Log Monitoring and Notification User Mgmt and Password policy Patch Update and Backup Change Control Secure build for firewall platforms

Audit Testing Scan all TCP and UDP ports 0 -65, 535 on the firewall Ping devices to see if Echo Requests pass Scan using ‘TCP Connect Scan’ (Full SYN-ACK) Do a slow SYN scan (with 15 second delay) to se if port scans are detected (by IDS) Scan with FINs, ACKs, and fragmented ACKs , Xmas Tree scans (URG, PUSH, FIN flags) to see how all perform Scan the subnet using UDP ports to look for open applications Check routing capability, including NAT Test other blocked source IP addresses: Spoofed, private, loopback, undefined Test other protocols: ICMP, IP fragmentation, all policies, all directions. Verify logging occurs for illegal probes Always get signed-off permission first!!!

Intrusion Prevention Systems (IPS) enhanced security product which inline net/host-based IDS that can block traffic functional addition to firewall that adds IDS capabilities can block traffic like a firewall alternatively send commands to firewall uses IDS algorithms may be network or host based

Host-Based IPS addresses: modification of system resources privilege-escalation exploits buffer overflow exploits access to email contact list directory traversal identifies attacks using: sandbox applets to monitor behavior signature techniques anomaly detection techniques can be tailored to the specific platform e. g. general purpose, web/database may protect file access, system registry, I/O, system calls

Network-Based IPS inline NIDS that can discard packets or terminate TCP connections can provide flow data protection reassembling whole packets monitoring full application flow content can identify malicious packets using: pattern matching, stateful matching, protocol anomaly, traffic anomaly, statistical anomaly cf. SNORT inline can drop/modify packets

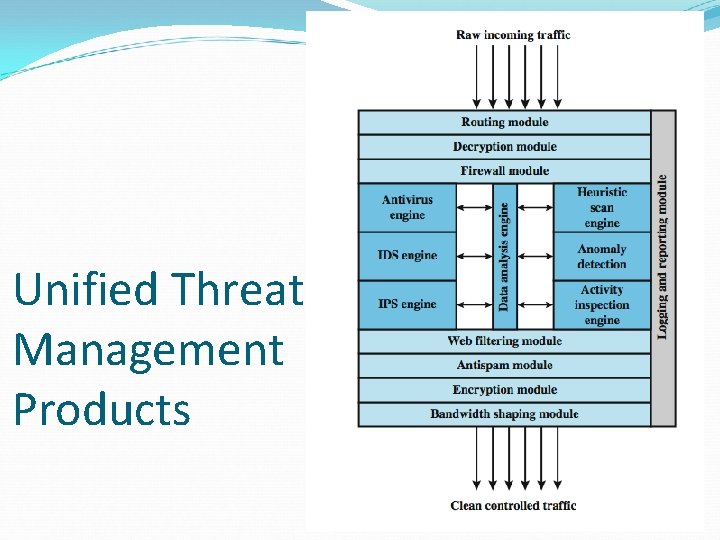
Unified Threat Management Products

Summary Firewall filters packets Types of networks double inline, T or multihomed, distributed, load balanced, screening router Types of firewalls packet filter, stateful inspection, application and circuit gateways Other capabilities Virtual Private Network (VPN), Network Address Translation (NAT) Advanced configurations: IPS, Unified Threat Management