Computer Security models an overview 10242020 1 Finite














- Slides: 52

Computer Security models – an overview. 10/24/2020 1

Finite State Machine Models Automata (=Finite State Machines) are a popular way Of modeling many aspects of computing systems. The essential feature of these are then concepts of: • State transition 10/24/2020 2

Bell-La. Padula (BLP) Model BLP Structure Combines, • . Access permission matrices for access control, • a Security lattice, for security levels, • an Automaton, for access operations. Security policies are reduced to relations in the BLP structure. 10/24/2020 3

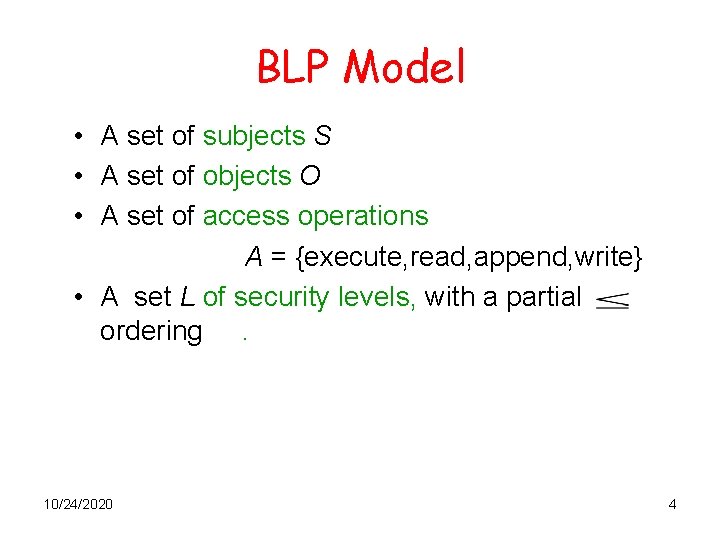
BLP Model • A set of subjects S • A set of objects O • A set of access operations A = {execute, read, append, write} • A set L of security levels, with a partial ordering. 10/24/2020 4

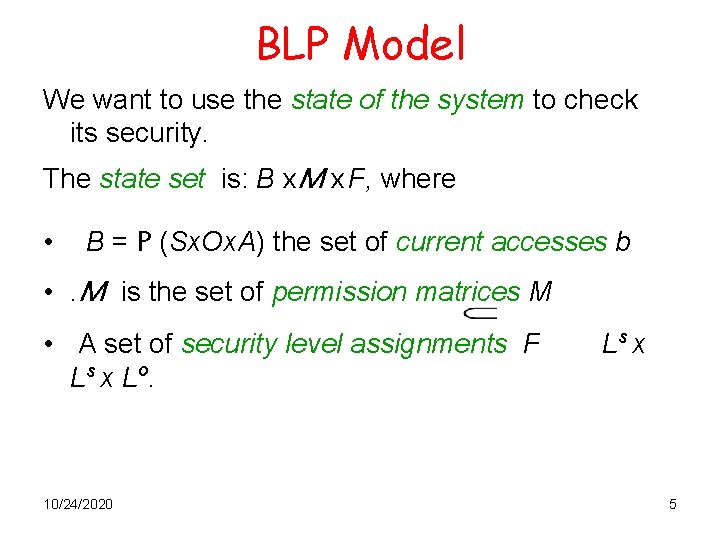
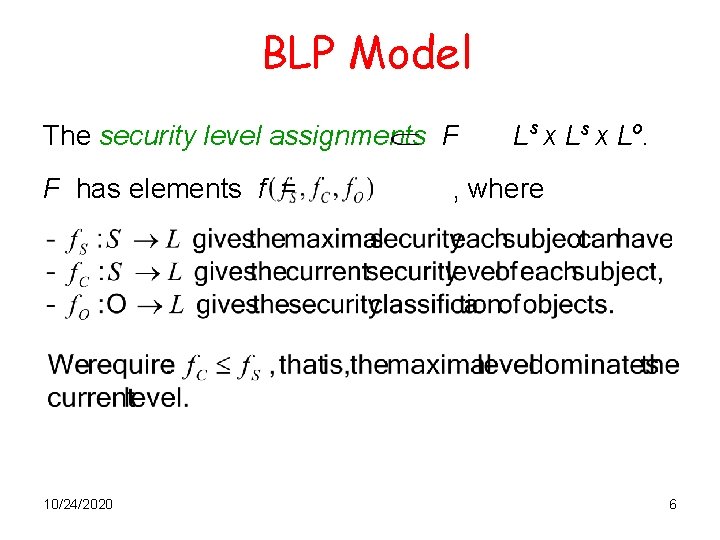
BLP Model We want to use the state of the system to check its security. The state set is: B x. M x F, where • B = P (Sx. Ox. A) the set of current accesses b • . M is the set of permission matrices M • A set of security level assignments F L s x L o. 10/24/2020 Ls x 5

BLP Model The security level assignments F F has elements f = 10/24/2020 L s x L o. , where 6

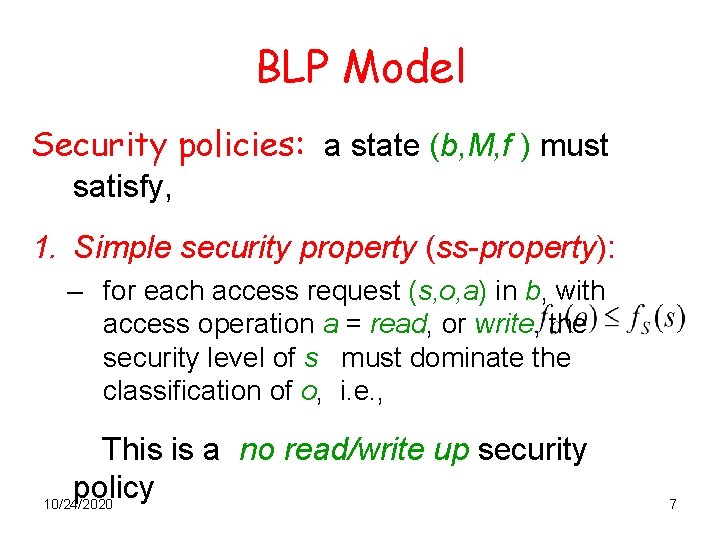
BLP Model Security policies: a state (b, M, f ) must satisfy, 1. Simple security property (ss-property): – for each access request (s, o, a) in b, with access operation a = read, or write, the security level of s must dominate the classification of o, i. e. , This is a no read/write up security policy 10/24/2020 7

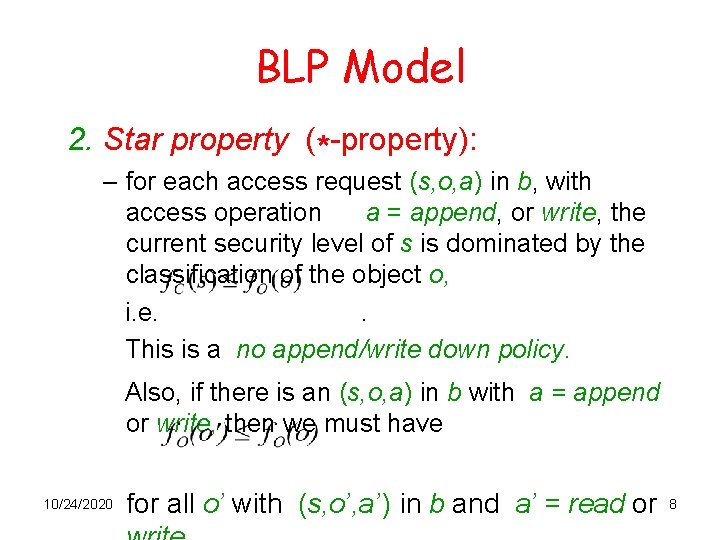
BLP Model 2. Star property (*-property): – for each access request (s, o, a) in b, with access operation a = append, or write, the current security level of s is dominated by the classification of the object o, i. e. . This is a no append/write down policy. Also, if there is an (s, o, a) in b with a = append or write, then we must have 10/24/2020 for all o’ with (s, o’, a’ ) in b and a’ = read or 8

BLP Model 3. Discretionary security property (dsproperty): -- for each access (s, o, a) in b, we must have. 10/24/2020 9

BLP Model The *-property implies that is not possible to send messages to low level subjects. There are two ways to remedy this. • Temporarily downgrade a high level subject this is why we introduced the current security level. • Identify a set of subjects that are permitted to violate the *-property. 10/24/2020 10

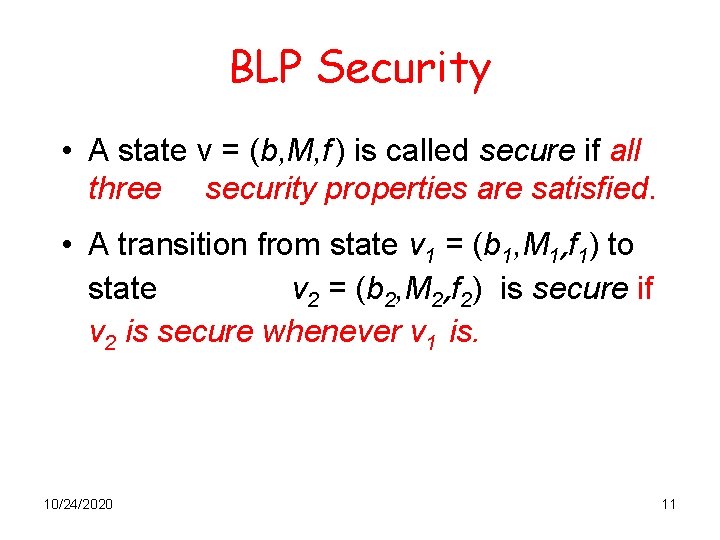
BLP Security • A state v = (b, M, f ) is called secure if all three security properties are satisfied. • A transition from state v 1 = (b 1, M 1, f 1) to state v 2 = (b 2, M 2, f 2) is secure if v 2 is secure whenever v 1 is. 10/24/2020 11

BLP Security Theorem If all state transitions are secure and if the initial state is secure then every subsequent state is secure, no matter which inputs occur. 10/24/2020 12

BLP Security Proof -informal A formal proof would proceed by induction on the length of the input sequences. It would build on the fact that security is preserves by state transitions. Remark This theorem means that to check security you only 10/24/2020 13 need to

BLP Security Proof, the ss-property A state transition from (b 1, M 1, f 1) to (b 2, M 2, f 2) preserves the ss-property if and only if: 10/24/2020 14

BLP Security Proof, the * & ds-property Preservation of the *-property and the dsproperty can be described in a similar way. 10/24/2020 15

BLP Security Mc. Lean defined a BLP system which • downgrades all subjects to the lowest level, • downgrades all objects to the lowest level, • enters all access rights in all positions of the access control matrix M. 10/24/2020 16

BLP Security A BLP system is only as good as its state transitions are. When a security system is designed within the framework of a model, it is important that the implementation of the primitives of the model captures correctly the security 10/24/2020 17 requirements of the system.

Limitations of BLP The BLP model, 1. only deals with confidentiality, not integrity, 2. does not address management of access control, 3. contains covert channels. 10/24/2020 18

Limitations of BLP • • • These are features of BLP, and should not be regarded as flaws. Limiting the goals of a model makes it easier to deal with security issues BLP does not state policies for the modification of access rights. BLP was originally intended for systems with no 10/24/2020 19 changes

Limitations of BLP Covert channels are information channels that are not controlled by the security mechanism of the system. Information can flow (leak) from a high security level to a low security level as follows: 1. A low-level subject creates an object dummy. obj at its ow level, 2. Its high-level accomplice, either upgrades it to a high leve or does not. 3. 10/24/2020 Later the low level subject tries to read dummy. obj. 20 If it can,

Limitations of BLP Telling a subject that a certain operation is or is not permitted, constitutes information flow. 10/24/2020 21

The Harrison-Ruzzo-Ullman (HRU) Model The BLP model is not dynamic: it does not allow for the creation or deletion of subjects and objects and for changing access rights. The HRU model defines authorization systems that 10/24/2020 address this issue. 22

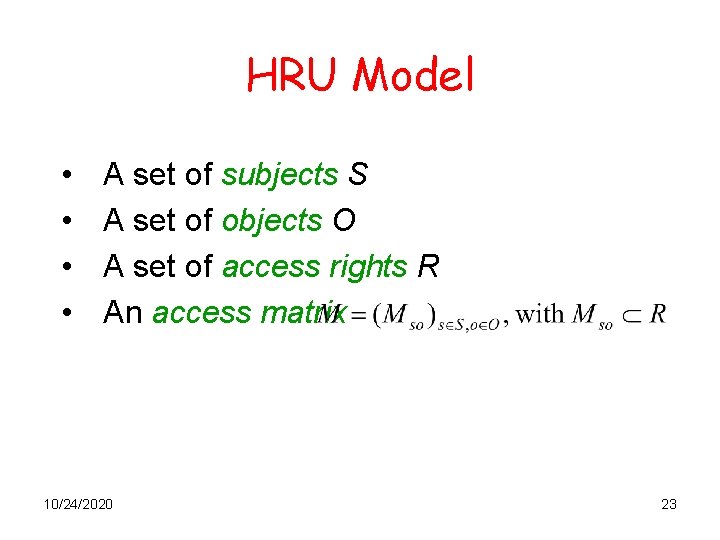
HRU Model • • A set of subjects S A set of objects O A set of access rights R An access matrix 10/24/2020 23

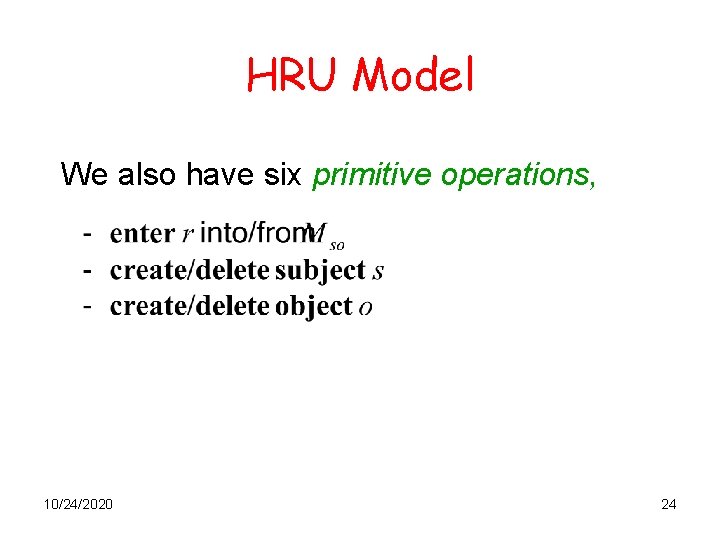
HRU Model We also have six primitive operations, 10/24/2020 24

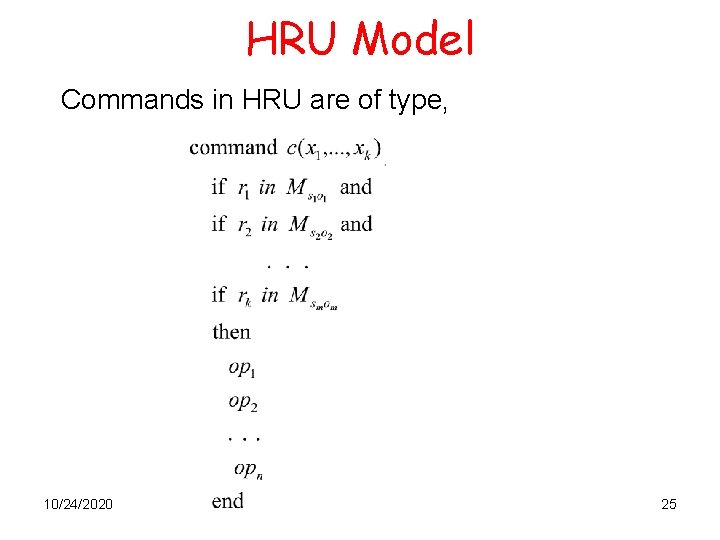
HRU Model Commands in HRU are of type, 10/24/2020 25

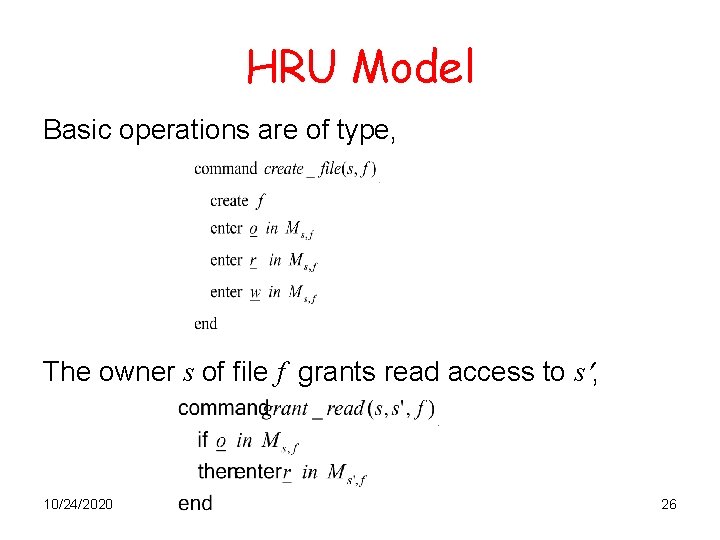
HRU Model Basic operations are of type, The owner s of file f grants read access to s , 10/24/2020 26

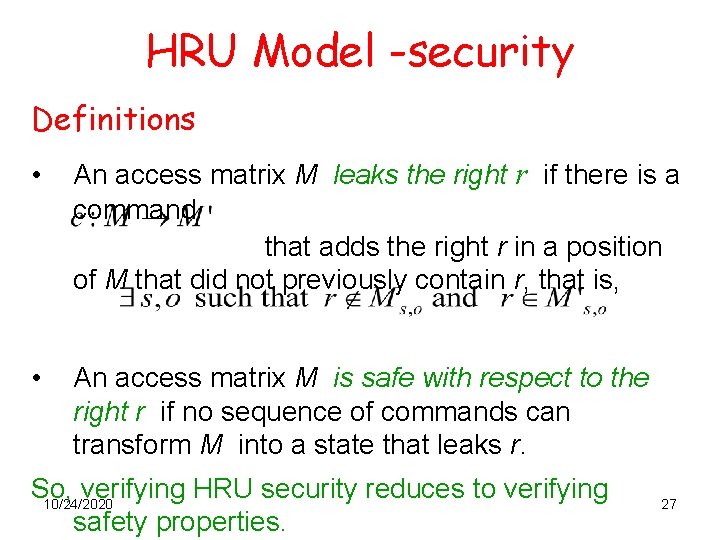
HRU Model -security Definitions • An access matrix M leaks the right r if there is a command that adds the right r in a position of M that did not previously contain r, that is, • An access matrix M is safe with respect to the right r if no sequence of commands can transform M into a state that leaks r. So, verifying HRU security reduces to verifying 10/24/2020 safety properties. 27

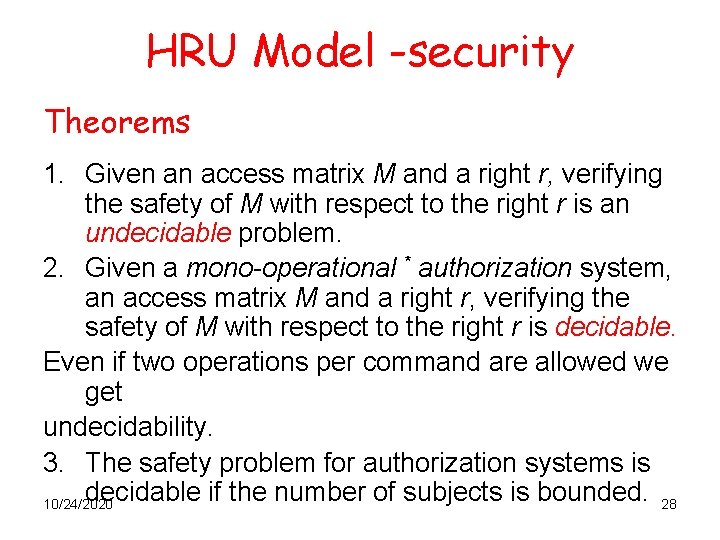
HRU Model -security Theorems 1. Given an access matrix M and a right r, verifying the safety of M with respect to the right r is an undecidable problem. 2. Given a mono-operational * authorization system, an access matrix M and a right r, verifying the safety of M with respect to the right r is decidable. Even if two operations per command are allowed we get undecidability. 3. The safety problem for authorization systems is decidable if the number of subjects is bounded. 28 10/24/2020

The Chinese Wall Model This models a consultancy business where analysts have to make sure that no conflicts arise when dealing with different clients (companies). Informally, a conflict arises when clients are direct competitors in the same market, or because of the ownership of 10/24/2020 29 companies.

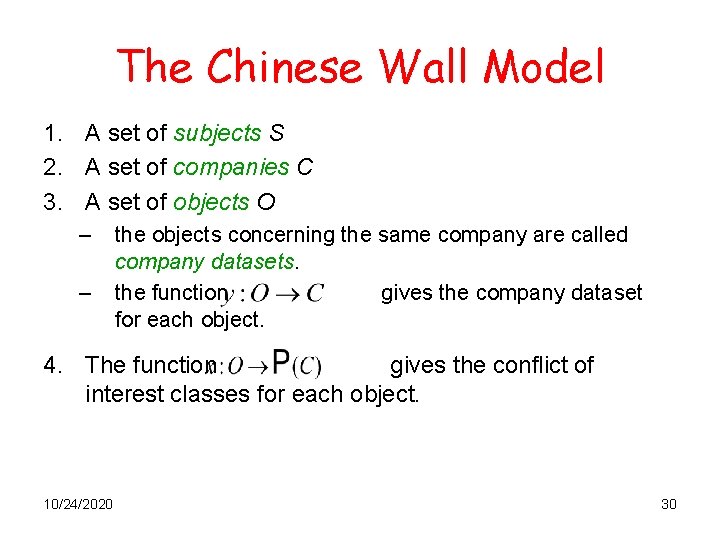
The Chinese Wall Model 1. A set of subjects S 2. A set of companies C 3. A set of objects O – – the objects concerning the same company are called company datasets. the function gives the company dataset for each object. 4. The function gives the conflict of interest classes for each object. 10/24/2020 30

The Chinese Wall Model Conflicts of interest may also arise from objects that have been accessed in then past. Let Ns, o = true, if subject s had access to object o false, if subject s never had access to object o 10/24/2020 31

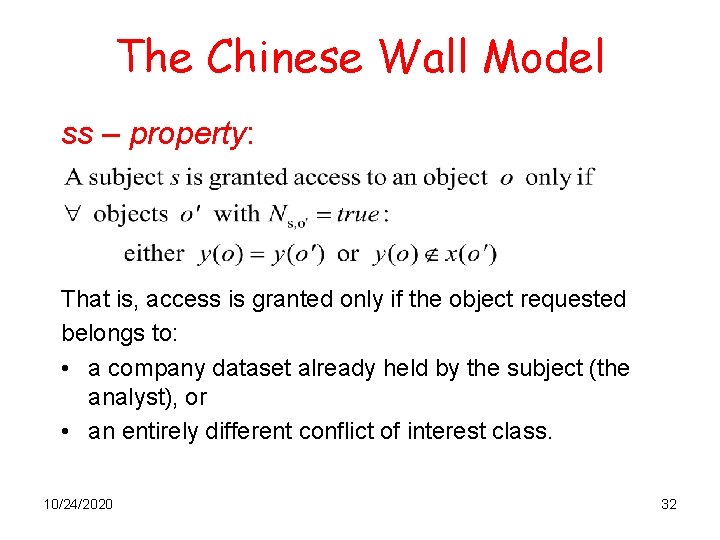
The Chinese Wall Model ss – property: That is, access is granted only if the object requested belongs to: • a company dataset already held by the subject (the analyst), or • an entirely different conflict of interest class. 10/24/2020 32

The Chinese Wall Model * - property: That is, write access to an object is only granted if no other object can be read which is in a different company dataset and contains unsanitised information. 10/24/2020 33

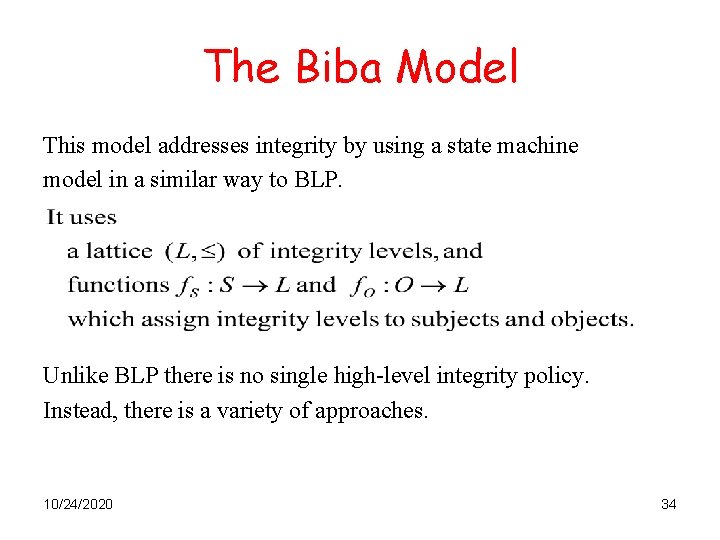
The Biba Model This model addresses integrity by using a state machine model in a similar way to BLP. Unlike BLP there is no single high-level integrity policy. Instead, there is a variety of approaches. 10/24/2020 34

The Biba Model • The integrity policies guarantee that information only flows downwards. • In particular, “clean” high level entities cannot be corrupted by “dirty” low level entities. 10/24/2020 35

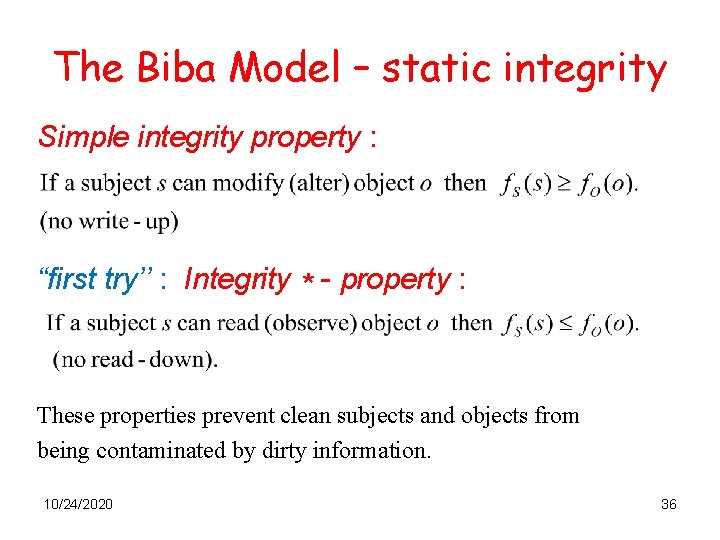
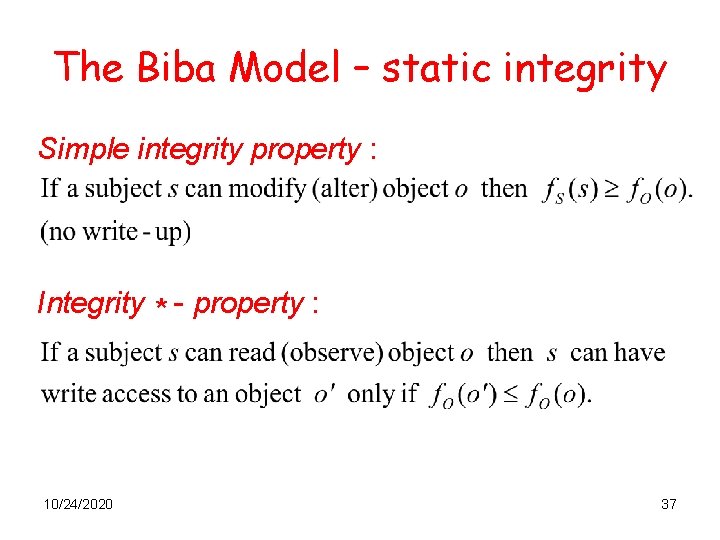
The Biba Model – static integrity Simple integrity property : “first try’’ : Integrity * - property : These properties prevent clean subjects and objects from being contaminated by dirty information. 10/24/2020 36

The Biba Model – static integrity Simple integrity property : Integrity * - property : 10/24/2020 37

The Biba Model – dynamic integrity This uses an approach similar to the Chinese Wall model, in which the integrity of a subject is adjusted if the subject comes into contact with low-level information. 10/24/2020 38

The Biba Model – dynamic integrity Subject low watermark property: Object low watermark property: 10/24/2020 39

The Clark - Wilson Model This model addresses the security requirements of commercial applications. The requirements of this model are to secure data integrity. Integrity requirements are divided into, • internal consistency: properties of the internal state that can be enforced by the computer system. • external consistency: the relation of the internal state to the real world: enforced by means outside the system, e. g. auditing. 10/24/2020 40

The CW Model Integrity is enforced by, • well formed transactions: data items can be manipulated only by a specific set of programs; users have access to programs rather than data items. • separation of duties: users have to collaborate to manipulate data and collude to penetrate the system. 10/24/2020 41

The CW Model In the Clark-Wilson model, • Subjects must be identified and authenticated, • Objects can be manipulated only by a restricted set of programs, • Subjects can execute only a restricted set of programs, • A proper audit log has to be maintained, • The system must be certified to work properly. 10/24/2020 42

The CW Model In the Clark-Wilson model, • Data items governed by the security policy are called Constrained Data Items (CDIs), • Inputs captured as Unconstrained Data Items (UDIs), • Conversion of UDIs to CDIs is a critical part of the system which cannot be controlled solely by the security mechanisms in the system, • CDIs can be manipulated by Transformation Procedures (TPs) • 10/24/2020 The integrity of a state is checked by Integrity 43 Verification Procedure (IVPs)

The CW Model Security procedures are defined by 5 certification rules: 1. 2. 3. 4. 5. Integrity Verification Procedures must ensure that all Constrained Data Items are in a valid state when the IVP is run. Transformation Procedures must be certified to be valid, i. e. CDIs must always be transformed into CDIs. The access rules must certify any separation of duties requirements. All TPs must write to an append-only log. Any TP that takes a UDI as input must either convert it into a CDI or reject it. 10/24/2020 44

The CW Model Security procedures are enforced by the 4 rules: 1. The system must maintain and protect the list of entries: (TPi: CDIa, CDIb, … ) giving the CDIs that the TP is certified to access. 2. The system must maintain and protect the list of entries: (User. ID, TPi: CDIa, CDIb, … ) specifying the TPs that users can execute. 3. The system must authenticate each user requesting to execute a TP. 4. Only a subject that may certify an access rule for a TP may modify the respective entry in the list. This subject must not have execute rights on that TP. 45 10/24/2020

Information - Flow Models In the BLP model information can flow from a low security level to a high security level through access operations without any loss of confidential information. Informally, a state transition from one object x to another object y causes information flow if we learn more about x by observing y. 10/24/2020 46

Information - Flow Models If you already know x then no information can flow from x. Otherwise we have: • • Explicit information flow -- Observing y after the assignment y: =x tells you the value of x. Implicit information flow -- Observing y after the conditional statement • If x=0 then y: =1 may tell you something about x even if y is not 1, e. g. if y = 2. Then we deduce that x is not 0. 10/24/2020 47

Information - Flow Models A precise quantitative definition for information flow can be given in terms of Information Theory. – 10/24/2020 The information flow from x to y is measured by the equivocation (conditional entropy) H (x | y) of x, given y. 48

Information - Flow Models The components of the information flow model are: • • A lattice A set of labeled objects • 10/24/2020 49

Information - Flow Models An IF system is secure if there is no illegal information flow. • • Advantages: it covers all kinds of information flow. Disadvantages: far more difficult to design such systems. E. g. checking whether a given system in the IF model is secure is an undecidable problem. 10/24/2020 50

Information - Flow Models One must also distinguish between – static enforcement and – dynamic enforcement of the information flow policies. 10/24/2020 51

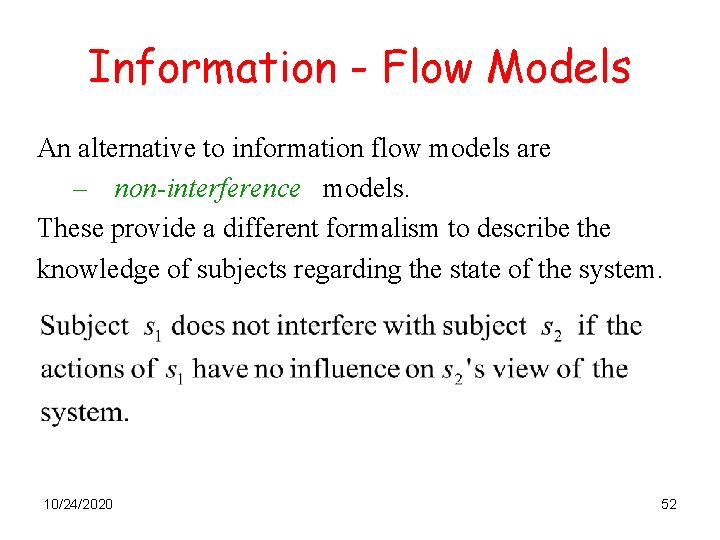
Information - Flow Models An alternative to information flow models are – non-interference models. These provide a different formalism to describe the knowledge of subjects regarding the state of the system. 10/24/2020 52