Computer Security Incident Response Team Angel Rivera March















- Slides: 21

Computer Security Incident Response Team Angel Rivera March 5, 2001 Organization: G 24 Project: FISSEA 703 -883 -5628 arivera@mitre. org

Outline l Management plan l Policy l Computer security incident definition l Skill mix and resources l Proactive activities l OIG & GAO audits l CSIRT & IDS l CSIRT & vulnerability assessments l CSIRT as a marketing tool l Discussion topics l Questions

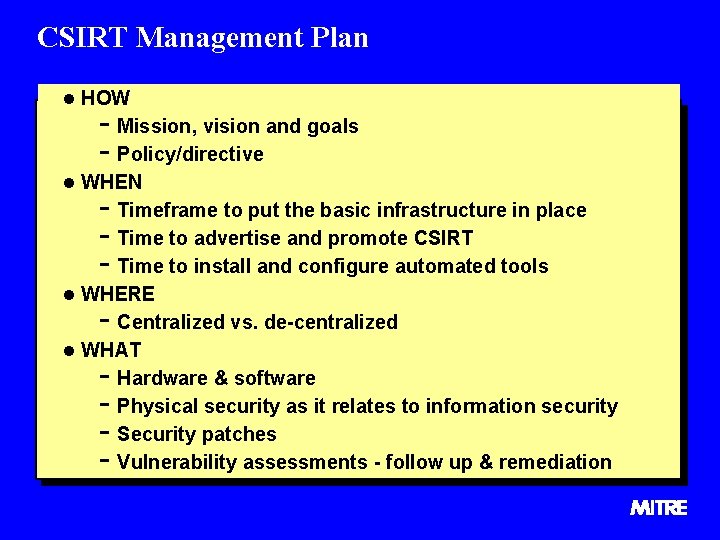
CSIRT Management Plan l HOW - Mission, vision and goals - Policy/directive l WHEN - Timeframe to put the basic infrastructure in place - Time to advertise and promote CSIRT - Time to install and configure automated tools l WHERE - Centralized vs. de-centralized l WHAT - Hardware & software - Physical security as it relates to information security - Security patches - Vulnerability assessments - follow up & remediation

CSIRT - SAMPLE MISSION CSIRT’s mission is to provide technical assistance to effectively investigate, resolve, and close security vulnerabilities and incidents involving the “Agency’s” automated information systems. CSIRT should be proactive as well as reactive

CSIRT Policy l Reporting computer security incidents vs. CSIRT - Define computer security incident - good luck! - Reporting chain l Users l CSIRT - to MGMT l Outside entities OMB - GISRA Law enforcement FEDCIRC Give examples Provide POC information Define responsibilities Users Management CSIRT OIG

Computer Security Incident - Definition l Computer security incidents are adverse events associated with a computer or network system, such as (1) an attempted, suspected, or actual compromise of sensitive information; (2) waste, fraud, abuse, or loss of information assets; (3) disruption of general or application support systems. l An introduction of a vulnerability or exposure that could have the potential to adversely affect the integrity, availability, accountability, and/or confidentiality of a computer system. l The discovery of a Common Vulnerability and/or Exposure (CVE) through vulnerability testing.

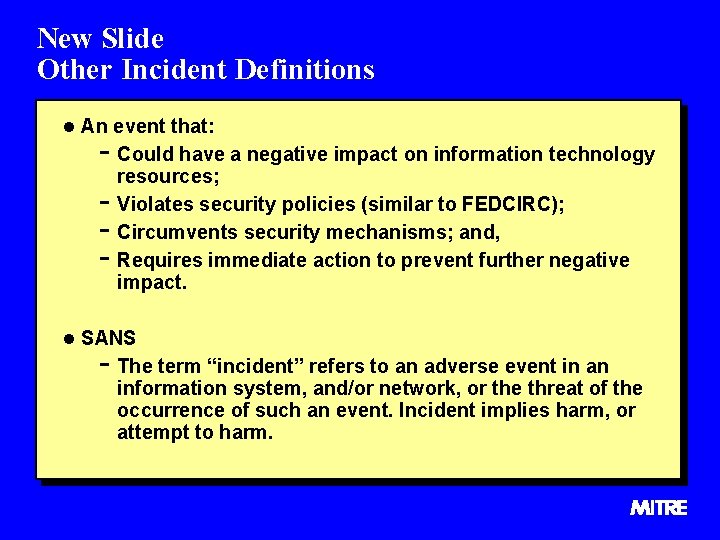
New Slide Other Incident Definitions l An event that: - Could have a negative impact on information technology - resources; Violates security policies (similar to FEDCIRC); Circumvents security mechanisms; and, Requires immediate action to prevent further negative impact. l SANS - The term “incident” refers to an adverse event in an information system, and/or network, or the threat of the occurrence of such an event. Incident implies harm, or attempt to harm.

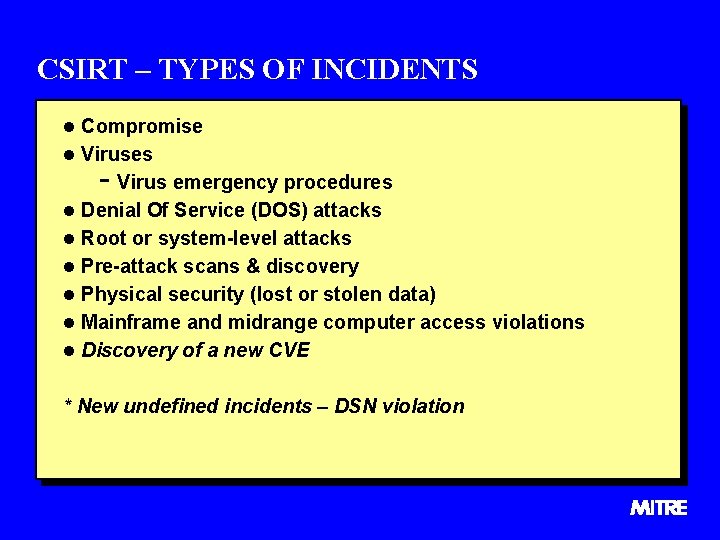
CSIRT – TYPES OF INCIDENTS l Compromise l Viruses - Virus emergency procedures l Denial Of Service (DOS) attacks l Root or system-level attacks l Pre-attack scans & discovery l Physical security (lost or stolen data) l Mainframe and midrange computer access violations l Discovery of a new CVE * New undefined incidents – DSN violation

CSIRT – SKILL MIX l Core Members - CSIRT coordinator - Junior level computer analyst – Data entry, referrals & - telephone support Mid level computer analyst – Virus support and proactive activities Senior level analyst – CVE and IDS analysis and remediation

CSIRT – SKILL MIX Cont. l Support Members - Firewall administrator - LAN administrators - Help desk - ISO - Mainframe & mid-range access control personnel - Database developer - Network operations center - OIG

CSIRT RESOURCES for 10 K USERS l Personnel - One CSIRT coordinator (50%) - One Jr. level computer analyst - Two mid level computer analysts - Two senior level analysts *IDS Expert l Equipment Telephones & cell phones, pagers, fax, secure file cabinets, non networked printer 2 laptops, 4 workstations, 2 IDS consoles l Facilities Secure room Independent electrical power/UPS Secure file cabinet 800 number with roll-over -

CSIRT 24 X 7 Operation l M-F 6: 00 AM to 8: OO PM support l Evenings and week-ends - Contractor support on call and on a rotating basis - Required to monitor web information sources and E-mail - IDS would issue a page or an E-mail alert and might - require the contractor to come in. VPN might be required for IDS console access Fully staffed 24 X 7 can be expensive and unnecessary

CSIRT PROACTIVE ACTIVITIES l Anti-virus vendor web sites - Use their escalation procedures - Subscribe to their prime support l SANS institute & mail list l Bugtraq l CERT l FEDCIRC l NIPC l IDS vendor web sites l Hacker sites l News groups l Hacker conferences

CSIRT - Security Related Web-Sites

CSIRT OIG & GAO AUDITS l Standards and guidance used by auditors - GISRA - OMB A-130 - NIST Special Publication 800 -3 1991 - FISCAM l Typical findings - No official CSIRT exists - No policy & procedures for reporting incidents - Lack of a clear definition of an incident - Poor or no user awareness of the existence of CSIRT - Poor database (for incident tracking) development - Lack of clear connection between vulnerability testing and CSIRT

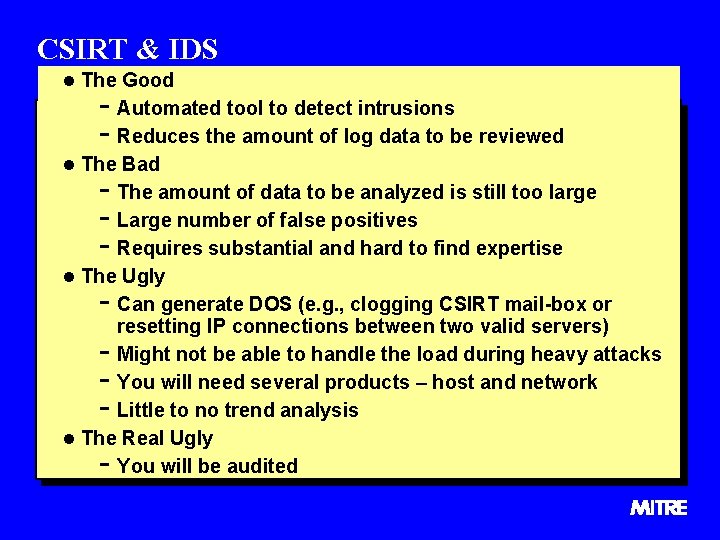
CSIRT & IDS l The Good - Automated tool to detect intrusions - Reduces the amount of log data to be reviewed l The Bad - The amount of data to be analyzed is still too large - Large number of false positives - Requires substantial and hard to find expertise l The Ugly - Can generate DOS (e. g. , clogging CSIRT mail-box or resetting IP connections between two valid servers) Might not be able to handle the load during heavy attacks You will need several products – host and network Little to no trend analysis l The Real Ugly You will be audited -

CSIRT & VULNERABILITY ASSESMENTS l CSIRT has the mechanisms, POCs and knowledgeable staff to track and remediate vulnerability testing findings. l Develop a yearly process (quarterly recommended) to perform vulnerability tests. l Decide which findings you will concentrate on and prioritize them: High Medium Low - not worth the time l Treat each finding as an incident and follow the normal process of tracking and resolution. -

CSIRT AS A MARKETING TOOL l Advertise, advertise your success l Weekly report to management (2 levels up recommended) should include the following: Number of probes against your network and main sources of probes - e. g. , China, Ukraine, Korea, Russia Numbers of Discovery attempts IDS statistics including massive proves by worms like Code Red. Number of viruses found and removed, found and not removed (servers & workstations) Release of new viruses Numbers of vulnerabilities that were closed Number of security patches released Number of phone calls -

CSIRT AS A MARKETING TOOL - Cont. l Use global e-mail to communicate serious new threats to all users. Don’t forget the contractors l Share the results of your proactive research with upper management. Advise them of serious and highly visible threats Inform them and what steps have been taken to minimize thread and provide an assessment of the situation -

CSIRT - Discussion Topics l CSIRT’s role in URL blocking/filtering l Outsourcing CSIRT l Splitting CSIRT and a Security Operations Center and/or the NOC

CSIRT Questions?