Computer Security Certificates SSL Issue How to Communicate






























- Slides: 35

Computer Security Certificates / SSL

Issue: How to Communicate Information with Public Keys? Java JCE n n Primary Interface: java. security. Key Sub-interfaces (“marker” interfaces” – type safety) java. security. Secret. Key java. security. Private. Key java. security. Public. Key n Generating keys javax. crypto. Key. Generator class generate. Key method Keys generated vary by use of random number generation

Message Digests Generated by applying one-way hash function over data in message Used to guarantee message hasn’t been tampered with Other common usage: storage and validating of passwords

Message Digests (2) Two major algorithms for digests n SHA (Secure Hash Algorithm) SHA-1 - 160 bit digest produced n NOTE: recent collision problems documented Also SHA-256, SHA-384, SHA-512 n n NOTE: still secure / not subject to collisions MD 5 128 bit digest n NOTE: recent collision problems claimed

Message Authentication Codes (MAC) Problem: interceptor could alter digest as well as original message Solution: encrypt digest with secret key MAC – generated by applying secret key to digest Java class: javax. crypto. Mac New Problem: still need to communicate secret key

Digital Signatures Generate signature by processing message with secret signing key Those with public verification key can verify the signature against a received message Java class: java. security. Signature

Key Agreement Idea: sender encrypts message with public key of recipient, recipient decrypts message with private key n n n Problem: high performance overhead Solution: encrypt message with secret key, only use public key crypto for secret key transmission New Problem: can only communicate with known parties

Key Agreement (2) Solution to problem of communicating with new parties n Agree on secret key in a way that key is never transmitted and cannot be determined from any intercepted traffic

Key Agreement (3) Steps n n n 1) Initiator generates public and private key pair and sends public key with algorithm specification to other party 2) Other party generates own public and private key pair using same algorithm spec. and sends public key back 3) Initiator generates secret key using its private key and initiator’s public key 4) Other party also generates secret key using its private key and initiator’s public key NOTE: Algorithm commonly used is the Diffie. Hellman algorithm, which assures that both parties generate the same secret key

Public Key Infrastructure (PKI) Public key encryption is not enough n Problems with Setting up communication channel Compromised keys Incompatible application programs Need for a larger infrastructure

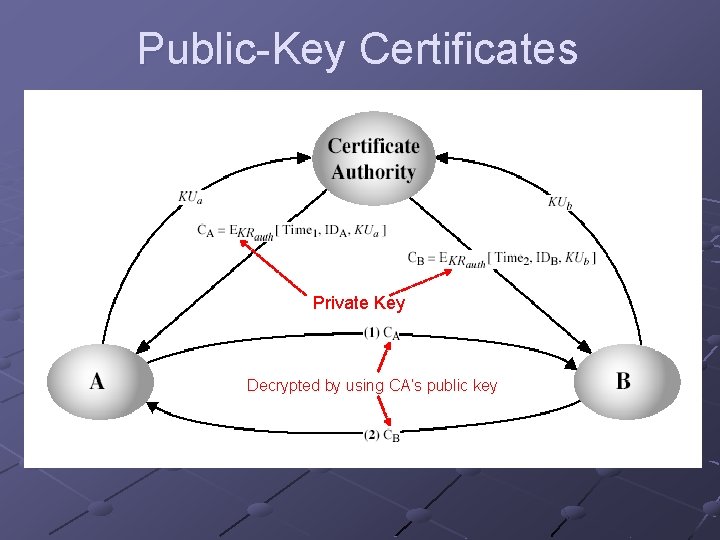
Digital Certificate Aka public key certificate, X. 509 certificate (based on CCITT standard) Idea: generate a document / byte stream that connects a public key to the identity of the corresponding private key’s owner, and is signed by a trusted entity Trusted entity = Certification Authority (CA) Issue such certificates for a limited duration

Digital Certificate (2) Contents n n n Unique serial number (ID of requestor), assigned by issuing CA Encryption public key of requestor Signature verification key Validity period (TTL) Information about the CA (including public key) Other information / extensions some material from Nick Hopper

Digital Certificates (3) How to get a certificate from a CA? n Need to generate a certificate signing request (CSR) CSR - Requestor generates public and private key pair, packages public key with identify information, sends to CA n Note: private key is NOT sent CA has to verify identity of requestor CA generates certificate, signs it, sends it back to requestor Costs $$$

Public-Key Certificates Private Key Decrypted by using CA’s public key

Certificate Authorities Example CA: Verisign Tasks n n Generates certificates as discussed Maintains a repository of unexpired certificates Settles disputes resulting from certificates n Maintains archive of expired certificates

Issue: Who Signs the CA’s Certificate? Needed as private key is included on any certificate generated by the CA Answer: higher level CA’s sign certificates from lower level CA’s. n Certificate chain – a series of signed certificates Final Answer: root CAs sign other CA’s certificates n n Root CAs can sign their own certificates Potential trust issue! some material from Nick Hopper

Other Certificate Options Can generate “self-signed” certificate n n Benefits: quick, low cost Disadvantages: not same level of trust Done using keytool utility Many organizations self-sign in practice Can generate minimal CA Done using certtool utility some material from Nick Hopper

Certificate Issues What to do when certificates are no longer valid? n One idea: revoke certificate Certificate Revocation Lists n n n Certificate can be linked to a “revocation server” Root CA’s publish lists of revoked certificates Validating certificates then requires contacting the revocation servers some material from Nick Hopper

Securing Internet Traffic How to apply PKI to communication on the internet? Historical Problem: many applications transmit usernames, passwords and content in plain text n E. g. telnet, ftp, smtp, http

Secure Socket Layer (SSL) Layered on top of TCP Combined cryptography and PKI to achieve n n n Message confidentiality Message integrity End-point authentication Encapsulates into a cipher suite n n Server authentication algorithm Key exchange algorithm Encryption algorithm Digest algorithm

SSL Versions n n SSLv 1 – original, not secure SSLv 2 – more secure, used often in current applications SSLv 3 – newer TLS – Transport Layer Security – similar to SSLv 3

SSL Process Session established over secure channel n n Server presents X. 509 certificate to client Client validates server certificate, and on request presents its certificate to server for validation Key exchange algorithm used to compute shared secret key Secret key used for encrypting and decrypting all messages

SSL Process (2) Low level steps of handshaking 1) C->S: list of cipher suites supported, highest SSL protocol version supported, a random number, and a compression method 2) S->C: server picks strongest cipher suite and protocol supported, responds with protocol version, another random value, a session id, the cipher suite chosen, and compression method

SSL Process (3) 3) S->C: server certificate passed if cipher suite requires it; else server sends its public key 4) S->C: if server configured for client authentication, it requests the client certificate 5) S->C: signals it’s done with requests; client now verifies server’s certificate, extracts the server’s public key, creates a secret string named pre-master secret, and encrypts it using the server’s public key 6) C->S: client certificate (if asked for)

SSL Process (4) 7) C->S: encrypted pre-master secret back to server 8) C->S: client sends a string encrypted with private key corresponding to public key of certificate sent earlier (not sent if client did not send certificate) 9) C->S: signal that client switching to secret key communication protocol 10) C->S: signal that is finished

SSL Process (5) 11) S->C: signal that server switching to secret key encryption 12) S->C: signal that server finished, as digest of negotiated secret key and handshake messages n Client verifies this At this point, communication can take place using secret key

RC 4 a proprietary cipher owned by RSA DSI another Ron Rivest design, simple but effective variable key size, byte-oriented stream cipher widely used (web SSL/TLS, wireless WEP) key forms random permutation of all 8 -bit values uses that permutation to scramble input info processed a byte at a time

RC 4 Encryption

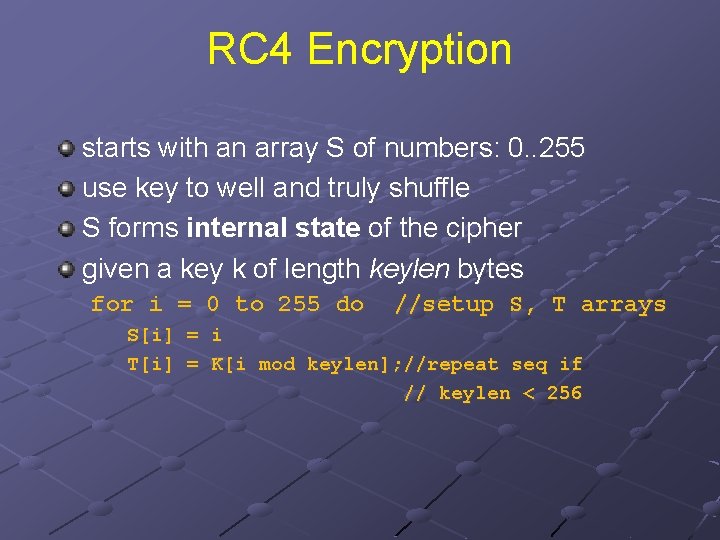
RC 4 Encryption starts with an array S of numbers: 0. . 255 use key to well and truly shuffle S forms internal state of the cipher given a key k of length keylen bytes for i = 0 to 255 do //setup S, T arrays S[i] = i T[i] = K[i mod keylen]; //repeat seq if // keylen < 256

RC 4 Encryption //Initial permutation of S is seq; // get a random index and randomize S j = 0 for i = 0 to 255 do j = (j + S[i] + k[i mod keylen]) mod 256 swap (S[i], S[j])

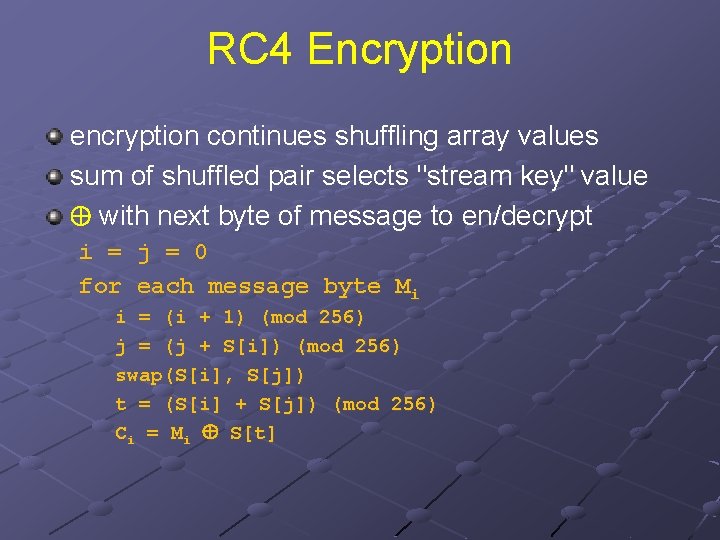
RC 4 Encryption encryption continues shuffling array values sum of shuffled pair selects "stream key" value with next byte of message to en/decrypt i = j = 0 for each message byte Mi i = (i + 1) (mod 256) j = (j + S[i]) (mod 256) swap(S[i], S[j]) t = (S[i] + S[j]) (mod 256) Ci = Mi S[t]

Java API for SSL JSSE included in standard Java classes: java. net. Socket java. net. Server. Socket javax. net. Server. Socket. Factory javax. net. ssl. SSLServer. Socket. Factory

SSL Applications SSL over telnet n n Tera. Term SSH (TTSSH) Pu. TTY SSL over ftp n n sftp Win. SCP SSL over http n HTTPS

Practical Consequences of SSL More secure Slower n Handshaking and encryption overhead take time

References J 2 EE Security (for Servlets, EJBs and Web Services); Pankaj Kumar, Prentice Hall/PTR, 2004