Computer Security Access Control Matrix 12252021 1 States






- Slides: 16

Computer Security Access Control Matrix 12/25/2021 1

States of a Computer System The state of a system is the collection of current values of all components of the system: memory locations, secondary storage, registers etc Protection states are those states that have to be protected. • . P = set of all protection states of the system • . Q = set of all authorized protection states • The system is not secure if the current state is in P-Q • 12/25/2021 A security policy characterizes the states in Q 2

Access Control Matrix Model A model used to describe the protection states. It characterizes the rights of each subject of the system (entity/process) regarding the objects of the system (entities/processes) in terms of a matrix. 12/25/2021 3

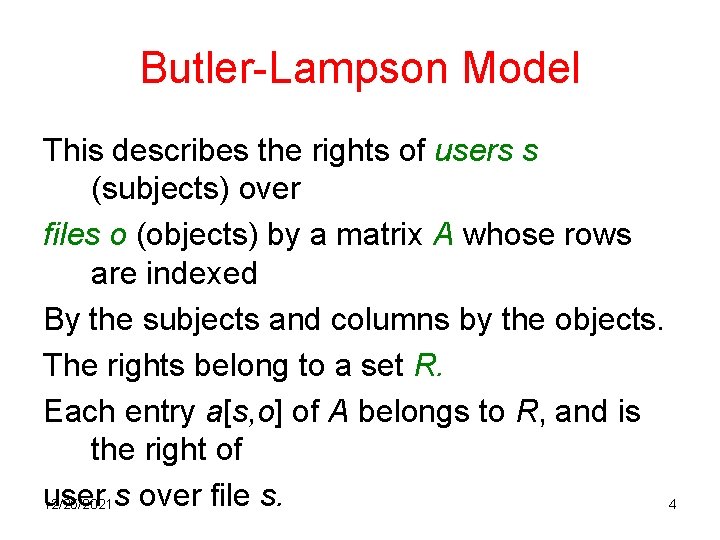
Butler-Lampson Model This describes the rights of users s (subjects) over files o (objects) by a matrix A whose rows are indexed By the subjects and columns by the objects. The rights belong to a set R. Each entry a[s, o] of A belongs to R, and is the right of user s over file s. 12/25/2021 4

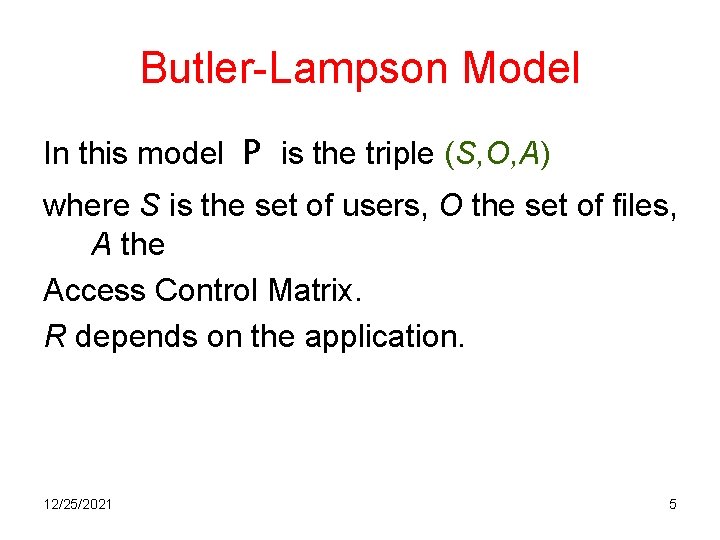
Butler-Lampson Model In this model P is the triple (S, O, A) where S is the set of users, O the set of files, A the Access Control Matrix. R depends on the application. 12/25/2021 5

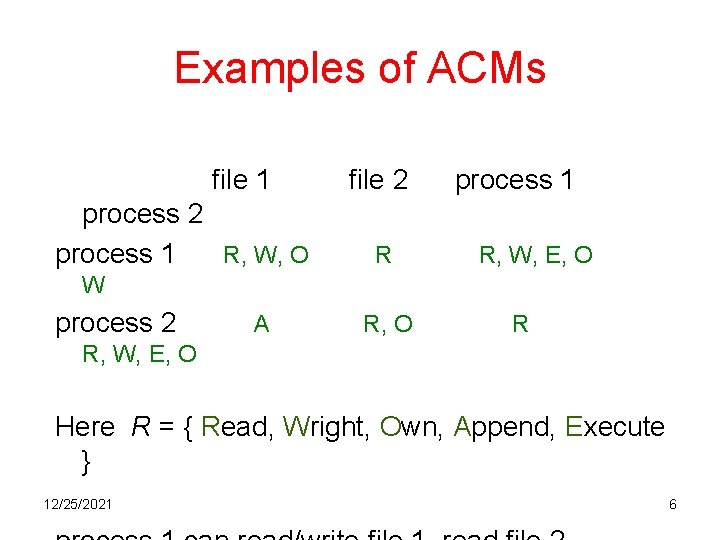
Examples of ACMs file 1 process 2 process 1 R, W, O file 2 R process 1 R, W, E, O W process 2 A R, O R R, W, E, O Here R = { Read, Wright, Own, Append, Execute } 12/25/2021 6

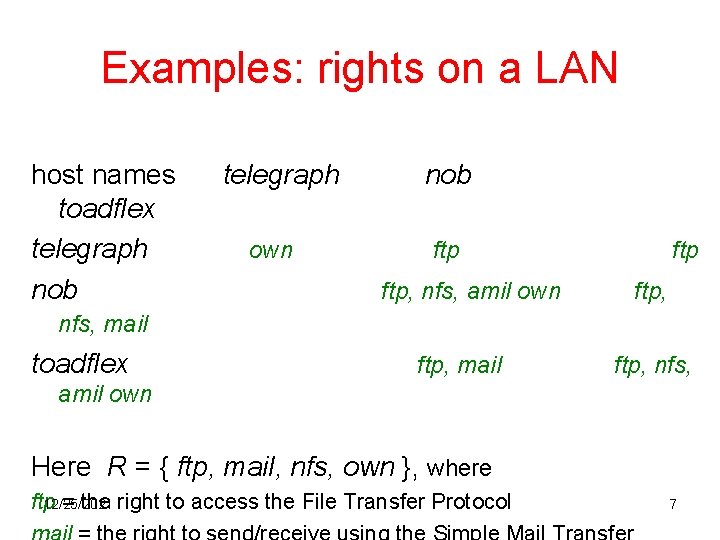
Examples: rights on a LAN host names toadflex telegraph nob telegraph own nob ftp, nfs, amil own ftp, nfs, mail toadflex ftp, mail ftp, nfs, amil own Here R = { ftp, mail, nfs, own }, where 12/25/2021 ftp = the right to access the File Transfer Protocol 7

Examples: rights in a program host names manager inc_ctr dec_ctr manager counter inc_ctr dec_ctr call + - call Here inc_ctr increases a counter and dec_ctr decreases it. 12/25/2021 R = { +, -, call } 8

Other examples • Access Control by Boolean expression evaluation • Access Control by History See textbook 12/25/2021 9

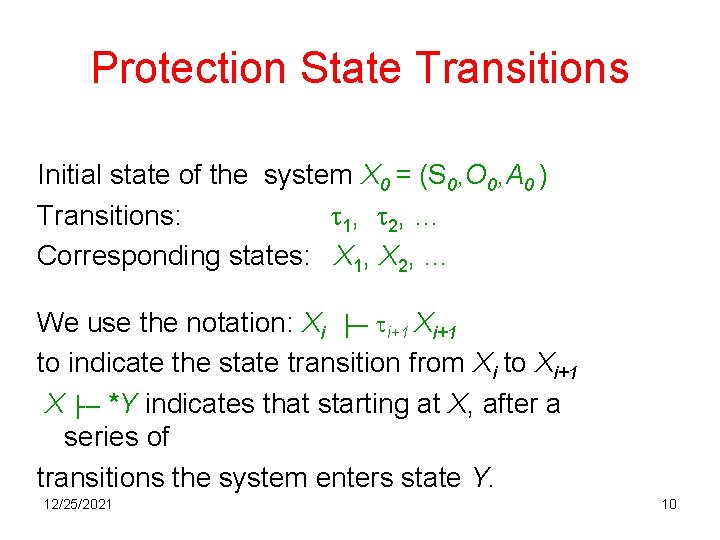
Protection State Transitions Initial state of the system X 0 = (S 0, O 0, A 0 ) Transitions: t 1, t 2, … Corresponding states: X 1, X 2, … We use the notation: Xi ├─ ti+1 Xi+1 to indicate the state transition from Xi to Xi+1 X ├─ *Y indicates that starting at X, after a series of transitions the system enters state Y. 12/25/2021 10

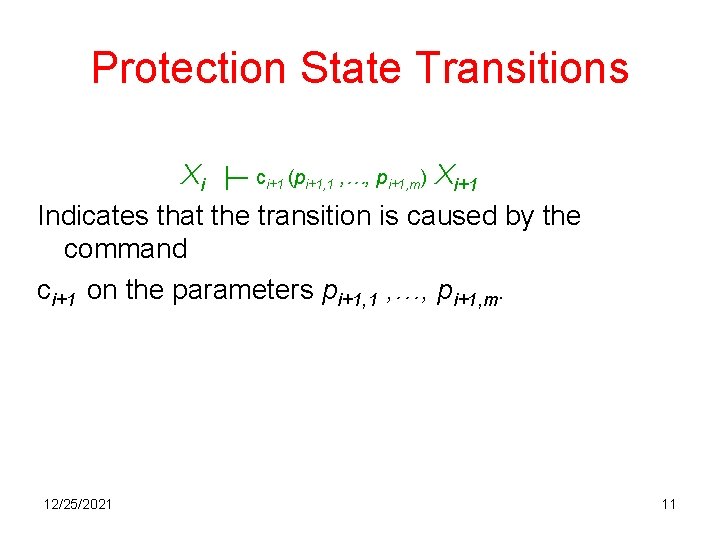
Protection State Transitions Xi ├─ ci+1 (pi+1, 1 , …, pi+1, m) Xi+1 Indicates that the transition is caused by the command ci+1 on the parameters pi+1, 1 , …, pi+1, m. 12/25/2021 11

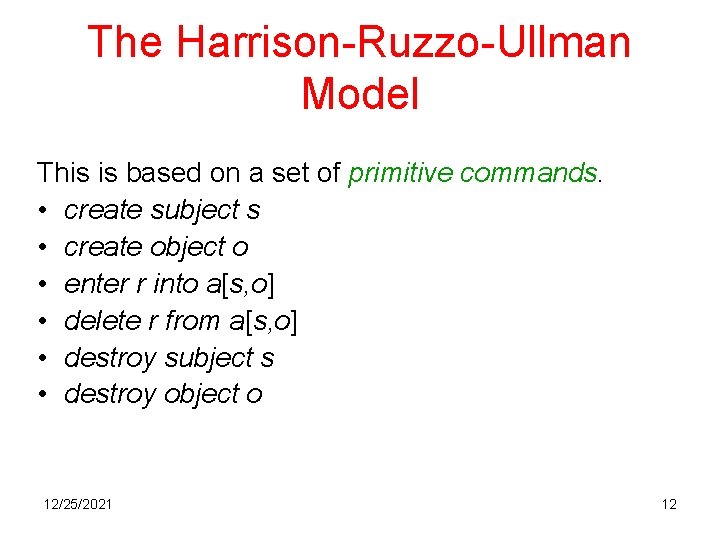
The Harrison-Ruzzo-Ullman Model This is based on a set of primitive commands. • create subject s • create object o • enter r into a[s, o] • delete r from a[s, o] • destroy subject s • destroy object o 12/25/2021 12

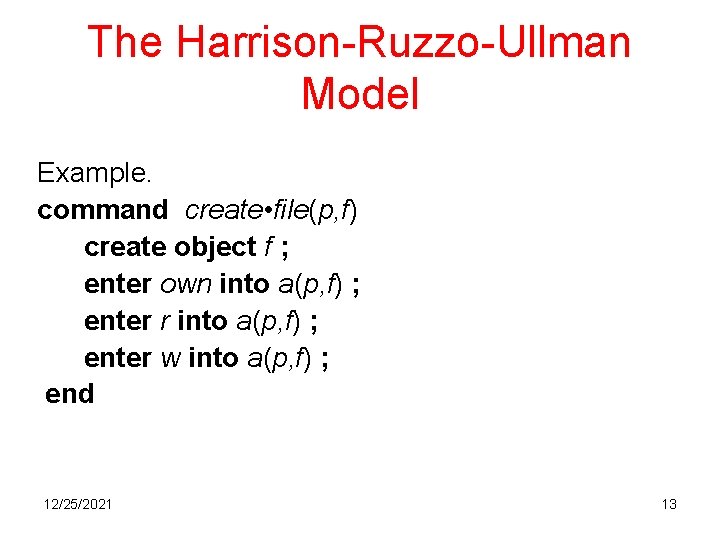
The Harrison-Ruzzo-Ullman Model Example. command create • file(p, f) create object f ; enter own into a(p, f) ; enter r into a(p, f) ; enter w into a(p, f) ; end 12/25/2021 13

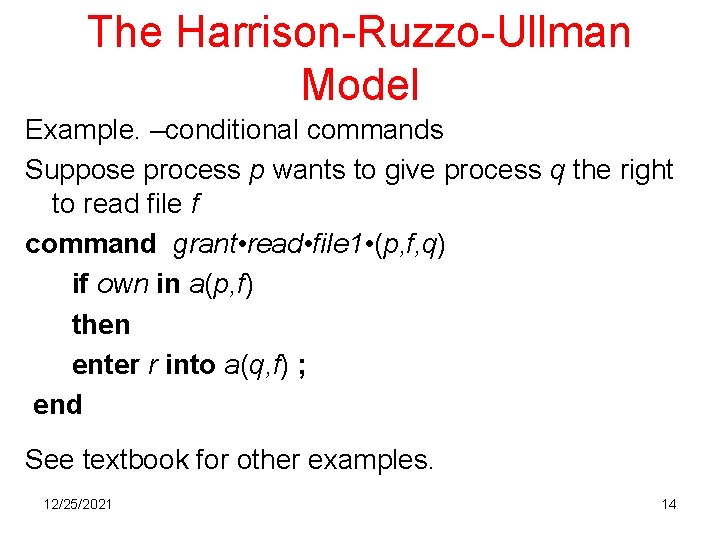
The Harrison-Ruzzo-Ullman Model Example. –conditional commands Suppose process p wants to give process q the right to read file f command grant • read • file 1 • (p, f, q) if own in a(p, f) then enter r into a(q, f) ; end See textbook for other examples. 12/25/2021 14

Copying and owning Rights • copy right (grant right) – augments existing rights • own right Copy right allows its possessor to grant rights (this right is often considered a flag attachment –hence flag right) Own right allows its possessor to add or delete privileges to themselves. 12/25/2021 15

Attenuation of privilege The Principle of Attenuation of Privilege says that • a subject may not give rights it does not possess to another subject. 12/25/2021 16