Computer Science Computer systems 13012022 J 27601 Open





















- Slides: 29

Computer Science Computer systems 13/01/2022 (J 276/01) Open source and Proprietary (closed) software

Computer Science Computer systems 13 January 2022 Open Source vs. Proprietary Software (J 276/01) Learning Content: 1. To be able to describe the differences between open source and proprietary software.

Proprietary software (Closed Source) Computer Science Computer systems • Proprietary software is owned by a commercial organisation. (J 276/01) • Creators receive an automatic copyright over anything they write. • It is so easy to copy source code and take it apart to find out how it works. • Anyone publishing the source code to their software risks having someone else steal, modify, and sell it for themselves. • The solution to this is to not publish the source code itself, but to compile it into a set of machine code instructions in an executable file, and sell that file to customers. • This is called closed source, because it is very difficult for anyone to work out what the original source code was. Examples:

Computer Science Computer systems Benefits of Proprietary software (Closed source) (J 276/01) High Profits: • The commercial organisation has invested money into developing the software, often millions for major applications and they sell the product to make profits. • With less possibility of theft or imitation, it is much easier to make closed source software profitable. User Documentation: • Helps support the user and attract as many customers as possible. • Open source does not have this pressure to be as user friendly. Software updates & Customer service: • They also offer formal support in the form of regular software updates and customer support for a specific period after purchase.

Open Source Software Computer Science Computer systems • With open source, the source code itself is freely available to the public. (J 276/01) • They want their work to be used by as many people as possible. • They want others to collaborate and build upon what they have created. • Many licences have been developed to support open source distribution. Examples:

Computer Science Computer systems Benefits of Open source software (J 276/01) • • Source code is available Usually allows redistribution Usually free of charge Bugs are often spotted and fixed quickly Examples of open source software: • GIMP - a photo editing application • Open Office - an office suite with word processor, spreadsheet and database • Audacity - an audio recording and editing application • Linux - operating system

What's in a Creative Commons Licence? Computer Science Computer systems • Creative Commons licences work like a buffet. (J 276/01) • You pick and choose which restrictions you want to add, so that you can say exactly how much freedom you want to give people to use and adapt your work. • So long as people meet the restrictions of the licence you choose, you are letting them do whatever they want with your work.

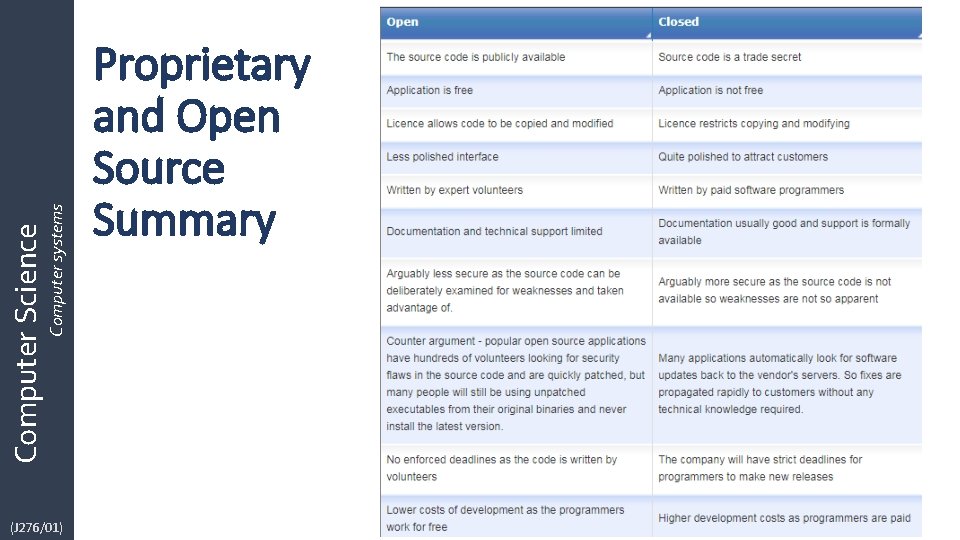
Computer systems Computer Science (J 276/01) Proprietary and Open Source Summary

Computer Science Computer systems Stakeholders (J 276/01) • Stakeholder: A person who may be involved either directly, or indirectly with an issue/problem • Some stakeholders may have more of an influence than others • Most issues and problems will have many stakeholders • Some may be obvious, some may be less obvious • For high-banded responses (marks) you should be able to identify more than just the ‘obvious’

Activity Draw a table that looks like this…. Positive Negative Robots have rapidly evolved from being human controlled to being automated and now they are becoming fully autonomous. Computer Science Computer systems These robots are designed to make their own decisions without human involvement or guidance. (J 276/01) All – Create two lists of positives and negatives relating to the case study above. Most – Identify from either list any of the items which you feel have a potential ethical issue or concern. Some – Write a passage discussing the positives and negatives you previously identified. What are the ethical issues that need to be considered? Are there situations where the use of the technology is deemed as ethically sound. Keyword - autonomous The ability to act on their own without human input

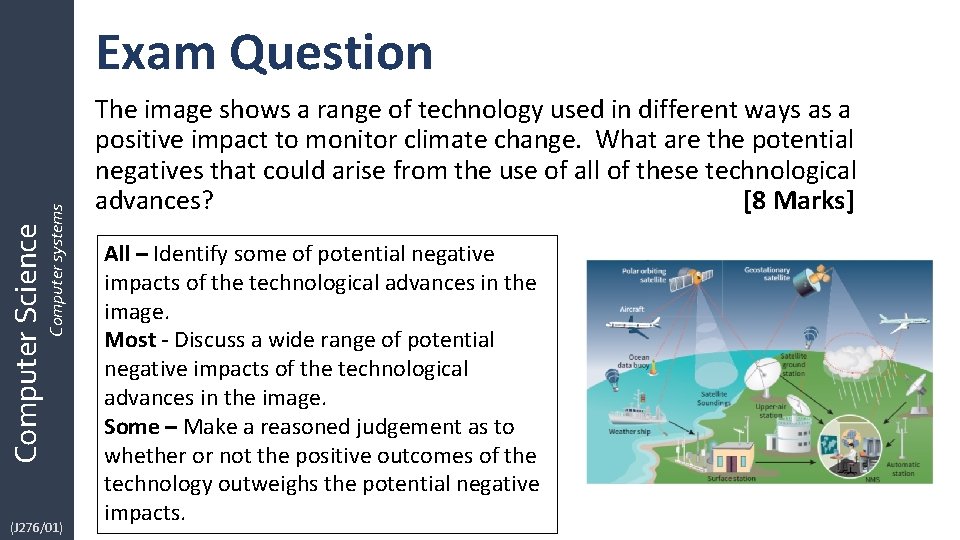
Computer Science Computer systems Exam Question (J 276/01) The image shows a range of technology used in different ways as a positive impact to monitor climate change. What are the potential negatives that could arise from the use of all of these technological advances? [8 Marks] All – Identify some of potential negative impacts of the technological advances in the image. Most - Discuss a wide range of potential negative impacts of the technological advances in the image. Some – Make a reasoned judgement as to whether or not the positive outcomes of the technology outweighs the potential negative impacts.

Exam Question Starter Computer Science Computer systems A supermarket replaces all of their staffed checkouts with electronic self-service checkouts. The owners of the supermarket notice an increase in profits, but employees who work on the checkouts lose their jobs. (J 276/01) Identify two stakeholders in the decision to replace the staffed checkouts. State whether the effect in these stakeholders was positive or negative and give a reason for your answer. Stakeholder 1: ………………………………………………………… The effect on this stakeholder was: Positive/Negative Reason: ……………………………………………………………. . Stakeholder 2: ………………………………………………………… The effect on this stakeholder was: Positive/Negative Reason: ……………………………………………………………. .

Computer systems Computer Science 13/01/2022 (J 276/01) Legal Issues

Data Protection Act 1998 Computer Science Computer systems Legal Responsibilities of data holders Data must be processed fairly. A right of access to a copy of the information comprised in their personal data. It can only be used for the purpose for which it was collected. A right to object to processing that is likely to cause or is causing damage or distress. Only data that is actually needed should be held. A right to prevent processing for direct marketing. Data must be accurate and up to date. A right to certain circumstances to have inaccurate personal data rectified, blocked, erased or destroyed. Data must not be held longer than it is needed for. A right to claim compensation for damages caused by a breach of the Act. Data will be used in accordance with the rights of the data subjects. Data will be kept safe. Data will not be transferred to any country where they don’t have similar laws. (J 276/01) Rights of data subjects Key Terms Data Holder: A person/organisation who holds personal data about someone else. Data Subject: Someone who the personal data is about.

Computer Misuse Act 1990 Computer Science Computer systems The Computer Misuse Act 1990 was enacted to counteract hacking. (J 276/01) This act lists three types of offence: Unauthorised access to computer material: using a computer to attempt to access a program or data to which you know you are not unauthorised. Just trying to access the information is an offence, even if you aren’t actually successful in doing so. Unauthorised access with intent to commit further offences: to attempt to access a computer system with the intention of committing a further offence. This could, for example, be trying to access personal details with the intention of committing identity theft. Intentional and unauthorised destruction of software or data: to gain unauthorised access to a computer with the intention to change the data or impair the running of the computer, e. g. by planting a virus.

Computer Science Computer systems Activity: Computer Misuse Act 1990 (J 276/01) Sub-heading in your book!!! Identify which of the three crimes in the Computer Misuse Act is being committed in the following examples: a. A user sees that another user has left their computer unattended and alters and deletes files from their personal area. b. A user accesses a computer to find out a person’s credit card number and security code so they can use it to buy goods online. c. A student tries to guess the password of a class member and tries to log into the network as that person.

Computer Science Computer systems Freedom of Information Act (J 276/01) The Freedom of Information Act was set up to end a culture of secrecy in In 2015, the Freedom Information the Act UK meant all MPs’ expense were government. Before itsofintroduction, hadthat no legislation obligingclaims the public sector to make information available togeneral the general public. published for the public to see. Thisact made for some embarrassing reading. held Some of the expenses included: The creates a rightvery of access to information by public authorities, which include central and local government, the health service, schools, colleges, • 49 p for a pint of milk universities, the police and courts. • £ 4. 99 for a bottle of weed killer • £ 2 for use of public transport The person requesting the information does not have to give a reason but the £ 14. 60 The for tea and coffee holder does if they refuse a • requester can appeal to the Information Commissioner. • £ 1, 645 for a floating duck island for a garden pond There have been many disclosures of information in the press enabled by the Freedom of Information Act, including, in May 2015, details of expense claims made by leading politicians.

Exam Question Practise Computer Science Computer systems A member of the public has sent a Freedom of Information request to their local council. (J 276/01) a) Outline how the local council should respond to the request. b) The local council’s computer network was recently hacked. The stolen data included sensitive information about members of the public, some of whom has left the area years ago. Explain the legal issues for both the hackers and the local council. [4] [2]

Computer Science Computer systems Copyright, Designs & Patents Act (J 276/01) Computer scientists like artists, authors, photographers and musicians, earn their money by charging people to use their work, e. g. to use their software, listen to their songs or read their books. They own the copyright to their work – no one can use it without paying for it, or asking them first. For example, only the creator has the right to make copies or perform it in public or give other people permission to do so. This is covered by the Copyright Designs and Patents Act 1988. Sometimes people try to copy their work. Copying software such as games and applications, scanning books, downloading pirate tracks, etc. … means the creators are not paid. This is illegal and unethical. The increased use of digital technology and the internet has made piracy easier. This has a serious impact on computer scientists and other creators who cannot continue their work if they are not paid. Even in pre-digital, analogue, times there were infringements when people copied vinyl records on to tape cassettes. Some companies have been fighting for years in the American courts over software and technology used om mobile phones and who owns the rights to special features.

Computer Science Computer systems High Profile Cases (J 276/01) Ed Sheeran vs Matt Cardle: It was claimed that Ed Sheeran’s song “Photograph” sounded not for note identical to that of Matt Cardle’s dong “Amazing”. The chorus of the song shared 39 identical notes within it. Ed Sheeran settled out of court at a cost of £ 16 m. James Dyson vs Hoover: Dyson sued Hoover claiming that they had stolen their idea of using cyclone technology to create a bag less vacuum cleaner. The High court also ruled that Hoover had indeed stolen their idea, and they had to amend it in order to be able to also sell bag less vacuum cleaners. A&M Records vs Napster: Napster was a very popular peer-to-peer file sharing service launched in 1999. People could go on and download and share music. A&M Records sued Napster for infringement of their intellectual property. They won the case and Napster were forced to shut down their website and pay $26 m in damages.

Computer Science Computer systems Creative Commons Licensing (J 276/01) Creative Commons is an organisation that provides licenses that allow the creators to give the public permission to share and use their work under certain conditions. They give people the right to share, use, and even build upon a work that an artist, musician or writer has created. There are several levels including: • Public Domain: there are no restrictions. It can be used without permission or attribution for any purpose. • Attribution License: the work can be used, distributed and copied as long as the creator is given credit for having created it. • Attribution-non-commercial: as above but only if it used for noncommercial purposes.

Exam Question Practise: Legislation Computer Science Computer systems A cinema collects information from customers who book seats to watch movies. The cinema would like to store this information for the following reasons: • To make it easier for customers when they book seats in the future • To enable the cinema to contact customers with details of future films. (J 276/01) Explain the measures that the cinema should take to ensure that customer data is stored legally. [6 Marks] ……………………………………………………………. . . ………………………………………………………………………………………………………………………… ……………………………………………………………

Computer Science Computer systems Research Task: Changes to the DPA (J 276/01) Sub-heading in your book!!! In May 2018 the Data Protection Act is changing. The EU is putting into place a new version of the Act called the EU’s General Data Protection Regulation (GDPR). As the UK moves out of the EU soon, this is likely to be converted in to UK law. Task: Find out what the major changes are in the new version of the Data Protection Act. • Answers in your exercise book. • Use full sentences.

Computer Science Computer systems 13/01/2022 (J 276/01) Cultural Concerns

Impact on Culture & Society Computer Science Computer systems Computing technology has had a huge impact on many aspects of our lives. (J 276/01) Health: • Full body scanners assist in the early diagnosis of cancer, cardiac disease and other abnormalities. • Computers are used in medical research such as the analysis of DNA. • They are also used to store patient records and allow easy access to them in emergencies. Traffic Management: • All of the traffic lights in a town or city are computer controlled and centrally coordinated using wireless networks. • That can be a problem if the network is not secure: http: //www. dailymail. co. uk/sciencetech/article-2730096/How-green-lights-way-work-Hackersreveal-simple-control-traffic-lights-major-cities-using-just-laptop. html

Activity: Society & Culture Computer Science Computer systems Here are some of the areas of society and culture on which the use of digital technology has had an impact. (J 276/01) Task: Choose two of the areas below and give three examples of the impact that digital technology has had. • • • Work & Employment They way in which people interact with each other Education Leisure Gaming Sub-heading in your book!!!

Computer Science Computer systems The Digital Divide (J 276/01) People without access to technology, or who don’t know how to use it, are at a disadvantage to those who do. This is known as the digital divide. There is a digital divide between countries and also between individuals within the same country. For example, in England, there areas without high-speed Internet access. The digital divide can have a huge impact on people who have little or limited access to computer science technologies. • Having poor IT literacy can lead to low-paid employment or even being unemployed. • The Office for National Statistics has calculated that in 2015 over 3. 5 million of households in the United Kingdom have no Internet access and in 2013 it was estimated by the charity Age UK, that it costs those households £ 276 per year because they cannot shop or pay bills online. • 38% of those that are not online are also unemployed, but • From 2013 they have had to prove that they are actively searching for jobs online using the government’s Universal Jobmatch website. • If they do not do this, their benefits can be stopped. They therefore have to travel to libraries for access.

Computer Science Computer systems Digital Divide: Additional Facts (J 276/01) • 5. 9 million adults in the UK have never used the internet • There are 4. 1 million adults living in social housing that are offline • The South East had the highest proportion of recent internet users (90%) and Northern Ireland was the area with the lowest proportion (80%) • 27% of disabled adults (3. 3 million) had never used the internet • Adults aged 16 to 24 years have consistently shown the highest rates of internet use • between 75% and 90% of jobs require at least some computer use

The barriers to getting online Computer Science Computer systems 1. Access: (J 276/01) • • • Affordability of equipment or usage Lack of time Lack of training or support Low literacy levels Disabilities 2. Motivation: • Lack of interest of perceived need • Cost/benefit ratio too high • Lack of appropriate content 3. Skills & Confidence: • Skills • Confidence in ability • Concerns about security