Computer Networks with Internet Technology William Stallings Chapter




![Dijkstra's Algorithm – Formal (2) [Initialization] T = {s} i. e. set of nodes Dijkstra's Algorithm – Formal (2) [Initialization] T = {s} i. e. set of nodes](https://slidetodoc.com/presentation_image_h2/963aa97da715518bbff235deb15c189b/image-28.jpg)
![Dijkstra's Algorithm – Formal (3) [Update Least-Cost Paths] L(n) = min[L(n), L(x) + w(x, Dijkstra's Algorithm – Formal (3) [Update Least-Cost Paths] L(n) = min[L(n), L(x) + w(x,](https://slidetodoc.com/presentation_image_h2/963aa97da715518bbff235deb15c189b/image-29.jpg)
![Bellman-Ford Algorithm – Formal (2) [Initialization] L 0(n) = , for all n s Bellman-Ford Algorithm – Formal (2) [Initialization] L 0(n) = , for all n s](https://slidetodoc.com/presentation_image_h2/963aa97da715518bbff235deb15c189b/image-36.jpg)












- Slides: 69

Computer Networks with Internet Technology William Stallings Chapter 11 Interior Routing Protocols

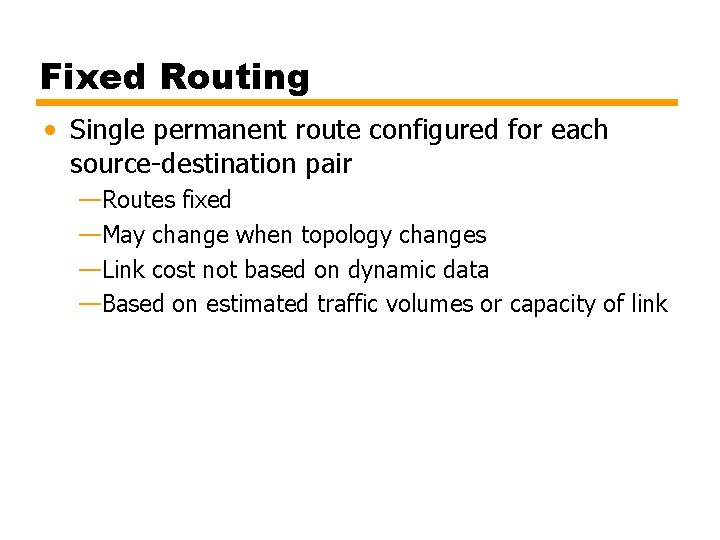
Introduction • Routing protocols essential to operation of an internet • Routers forward IP datagrams from one router to another on path from source to destination • Router must have idea of topology of internet • Routing protocols provide this information

Internet Routing Principles • Routers receive and forward datagrams • Make routing decisions based on knowledge of topology and conditions on internet • Decisions based on some least cost criterion (chapter 14)

Fixed Routing • Single permanent route configured for each source-destination pair —Routes fixed —May change when topology changes —Link cost not based on dynamic data —Based on estimated traffic volumes or capacity of link

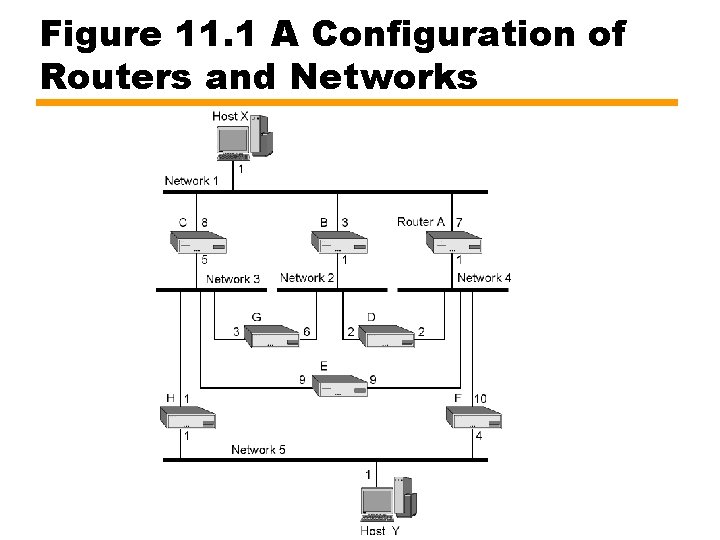
Figure 11. 1 A Configuration of Routers and Networks

Discussion of Example • 5 networks, 8 routers • Link cost for output side of each router for each network —Next slide shows how fixed cost routing may be implemented • Each router has routing table

Routing Table • One required for each router • Entry for each network — Not for each destination — Routing only needs network portion • Once datagram reaches router attached to destination network, that router can deliver to host • IP address typically has network and host portion • Each entry shows next node on route — Not whole route

Routing Tables in Hosts • May also exist in hosts —If attached to single network with single router then not needed • All traffic must go through that router (called the gateway) —If multiple routers attached to network, host needs table saying which to use

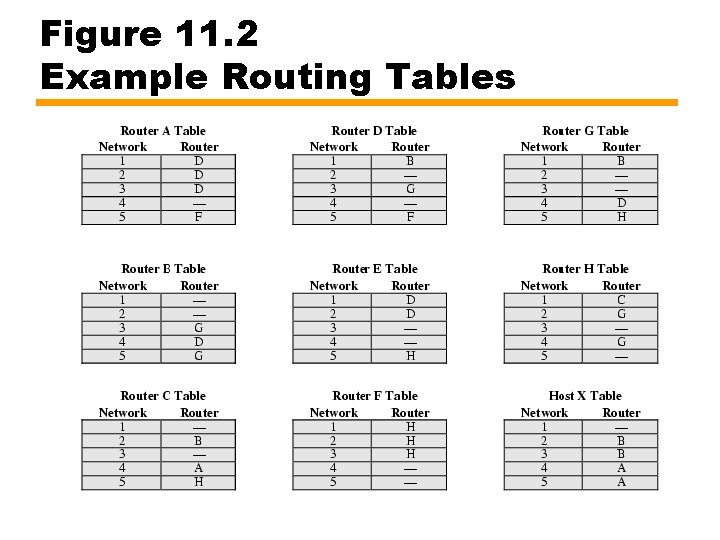
Figure 11. 2 Example Routing Tables

Adaptive Routing • As conditions on internet changes, routes may change —Failure • Can route round problems —Congestion • Can route round congestion • Avoid, or at least not add to further congestion

Drawbacks of Adaptive Routing • More complex routing decisions — Router processing increases • Depends on information collected in one place but used in another — More information exchanged improves routing decisions but increases overhead • May react two fast causing congestion through oscillation • May react to slow, being irrelevant • Can produce pathologies — Fluttering — Looping

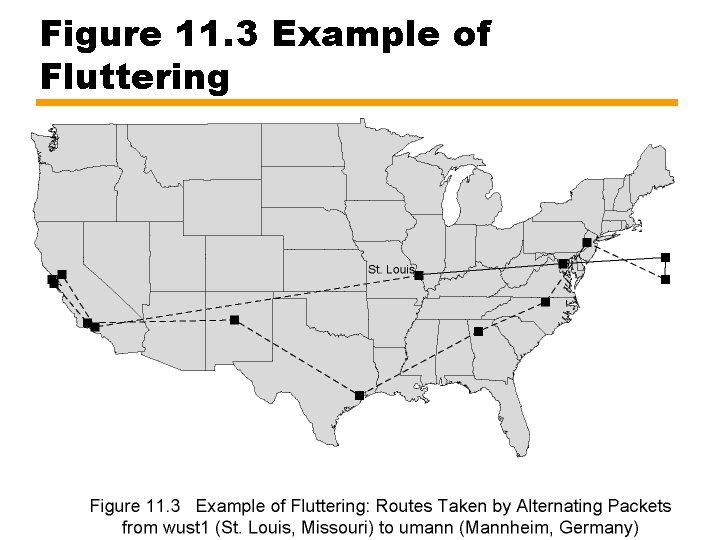
Fluttering • Rapid oscillation in routing • Due to router attempting load balancing or splitting —Splitting traffic among a number of routes —May result in successive packets bound for same destination taking very different routes (see next slide)

Figure 11. 3 Example of Fluttering

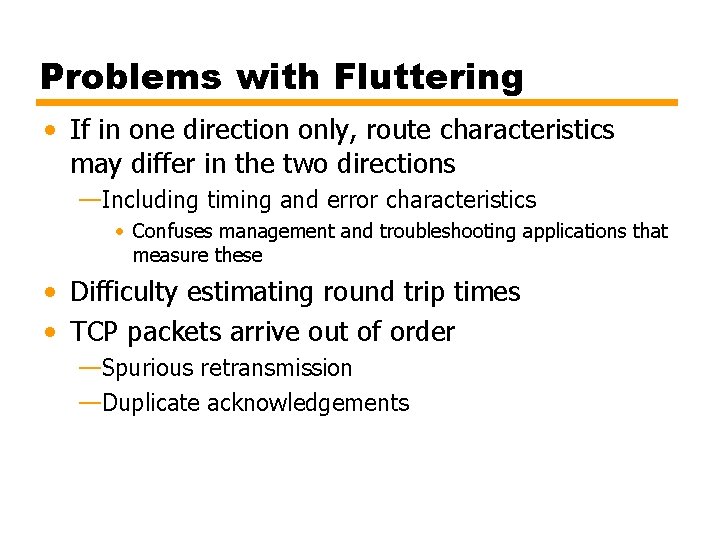
Problems with Fluttering • If in one direction only, route characteristics may differ in the two directions —Including timing and error characteristics • Confuses management and troubleshooting applications that measure these • Difficulty estimating round trip times • TCP packets arrive out of order —Spurious retransmission —Duplicate acknowledgements

Looping • Packet forwarded by router eventually returns to that router • Algorithms designed to prevent looping • May occur when changes in connectivity not propagated fast enough to all other routers

Adaptive Routing Advantages • • Improve performance as seen by user Can aid congestion control Benefits depend on soundness of design Adaptive routing very complex —Continual evolution of protocols

Classification of Adaptive Routing Strategies • Based on information sources —Local • E. g. route each datagram to network with shortest queue • Balance loads on networks • May not be heading in correct direction – Include preferred direction • Rarely used —Adjacent nodes • Distance vector algorithms —All nodes • Link-state algorithms • Both need routing protocol to exchange information

Autonomous Systems (AS) • Group of routers exchanging information via common routing protocol • Set of routers and networks managed by single organization • Connected —Except in time of failure

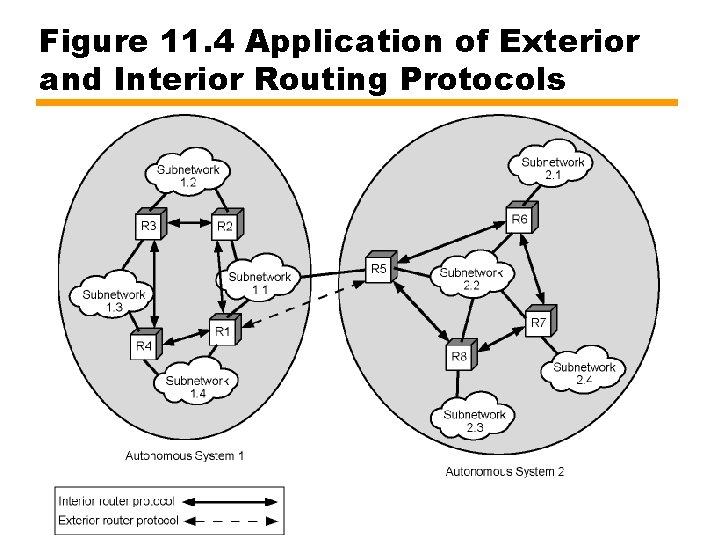
Interior Routing Protocol (IRP) • Passes routing information between routers within AS • Does not need to be implemented outside AS —Allows IRP to be tailored • May be different algorithms and routing information in different connected AS • Need minimum information from other connected AS —At least one router in each AS must talk —Use Exterior Routing Protocol (ERP)

Exterior Routing Protocol (ERP) • Pass less information than IRP • Router in first system determines route to target AS • Routers in target AS then co-operate to deliver datagram • ERP does not deal with details within target AS

Figure 11. 4 Application of Exterior and Interior Routing Protocols

Approaches to Routing – Distance-vector • Each node (router or host) exchange information with neighboring nodes — Neighbors are both directly connected to same network • First generation routing algorithm for ARPANET • Node maintains vector of link costs for each directly attached network and distance and next-hop vectors for each destination • Used by Routing Information Protocol (RIP) • Requires transmission of lots of information by each router — Distance vector to all neighbors — Contains estimated path cost to all networks in configuration — Changes take long time to propagate

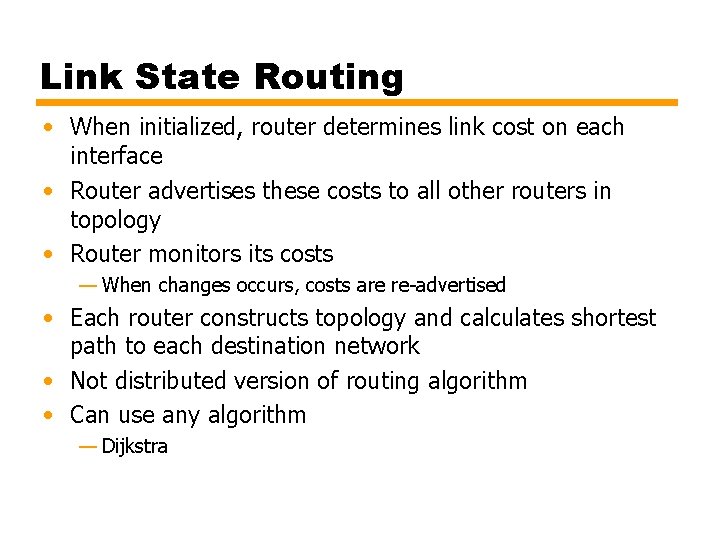
Approaches to Routing – Link-state • Designed to overcome drawbacks of distance-vector • When router initialized, it determines link cost on each interface • Advertises set of link costs to all other routers in topology — Not just neighboring routers • From then on, monitor link costs — If significant change, router advertises new set of link costs • Each router can construct topology of entire configuration — Can calculate shortest path to each destination network • Router constructs routing table, listing first hop to each destination • Router does not use distributed routing algorithm — Use any routing algorithm to determine shortest paths — In practice, Dijkstra's algorithm • Open shortest path first (OSPF) protocol uses link-state routing. • Also second generation routing algorithm for ARPANET

Exterior Router Protocols – Path-vector • Dispense with routing metrics • Provide information about which networks can be reached by a given router and ASs crossed to get there — Does not include distance or cost estimate • Each block of information lists all ASs visited on this route — Enables router to perform policy routing — E. g. avoid path to avoid transiting particular AS — E. g. link speed, capacity, tendency to become congested, and overall quality of operation, security — E. g. minimizing number of transit Ass

Least Cost Algorithms • Least-cost criterion —If minimize number of hops, link value 1 —Link value may be inversely proportional to capacity, proportional to current load, or some combination —May differ in different two directions —E. g. if cost equaled length of queue • Cost of path between two nodes as sum of costs of links traversed • For each pair of nodes, find least cost path • Dijkstra's algorithm • Bellman-Ford algorithm

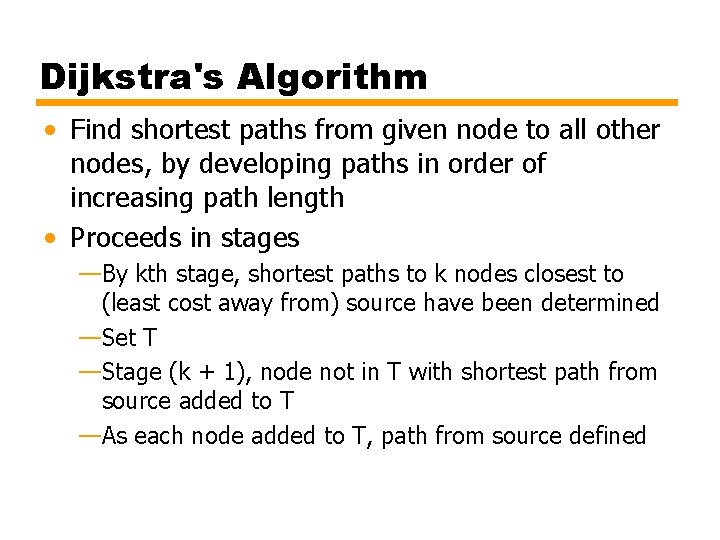
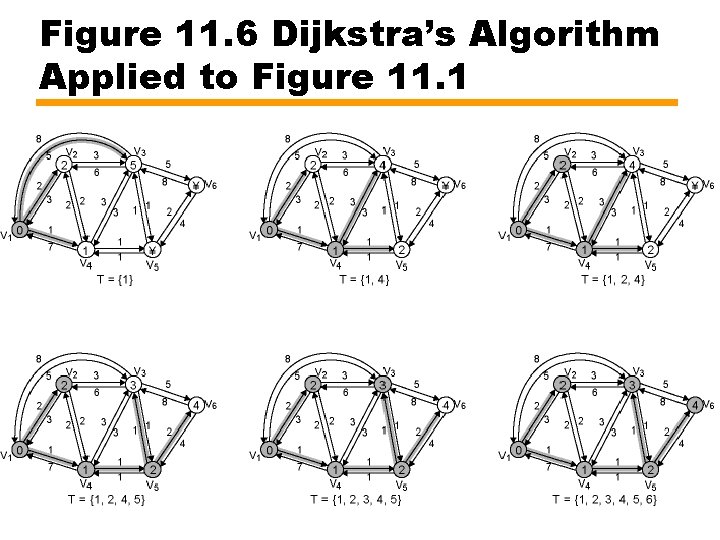
Dijkstra's Algorithm • Find shortest paths from given node to all other nodes, by developing paths in order of increasing path length • Proceeds in stages —By kth stage, shortest paths to k nodes closest to (least cost away from) source have been determined —Set T —Stage (k + 1), node not in T with shortest path from source added to T —As each node added to T, path from source defined

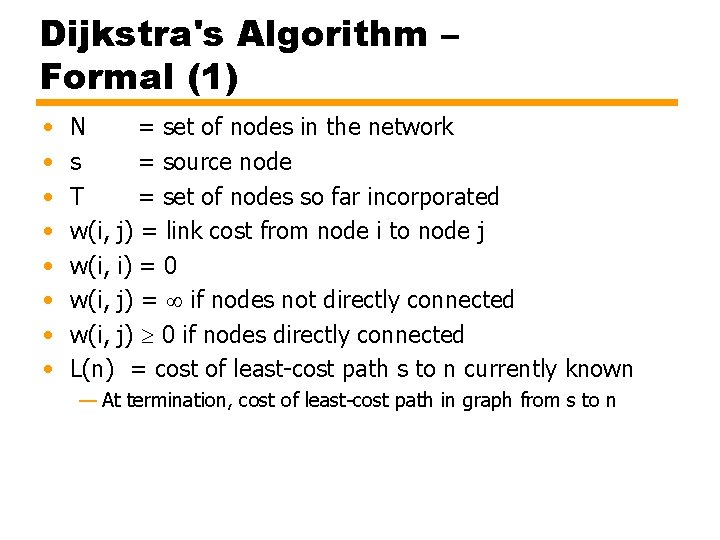
Dijkstra's Algorithm – Formal (1) • • N = set of nodes in the network s = source node T = set of nodes so far incorporated w(i, j) = link cost from node i to node j w(i, i) = 0 w(i, j) = if nodes not directly connected w(i, j) 0 if nodes directly connected L(n) = cost of least-cost path s to n currently known — At termination, cost of least-cost path in graph from s to n
![Dijkstras Algorithm Formal 2 Initialization T s i e set of nodes Dijkstra's Algorithm – Formal (2) [Initialization] T = {s} i. e. set of nodes](https://slidetodoc.com/presentation_image_h2/963aa97da715518bbff235deb15c189b/image-28.jpg)
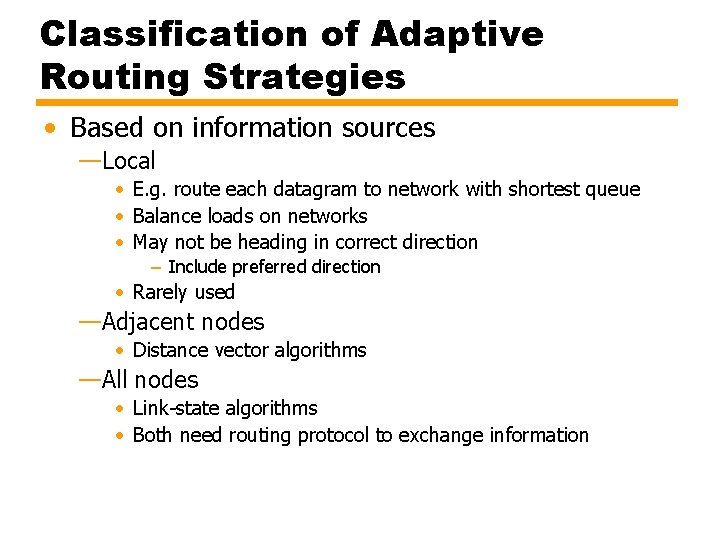
Dijkstra's Algorithm – Formal (2) [Initialization] T = {s} i. e. set of nodes so far incorporated consists of only source node L(n) = w(s, n) for n ≠ s i. e. initial path costs to neighboring nodes are link costs [Get Next Node] Find neighboring node not in T with least-cost path from s Incorporate node into T Also incorporate edge incident on that node and node in T that contributes to the path. This can be expressed as: Find x Ï T such that Add x to T; add to T the edge that is incident on x and that contributes the least component to L(x), that is, the last hop in the path.
![Dijkstras Algorithm Formal 3 Update LeastCost Paths Ln minLn Lx wx Dijkstra's Algorithm – Formal (3) [Update Least-Cost Paths] L(n) = min[L(n), L(x) + w(x,](https://slidetodoc.com/presentation_image_h2/963aa97da715518bbff235deb15c189b/image-29.jpg)
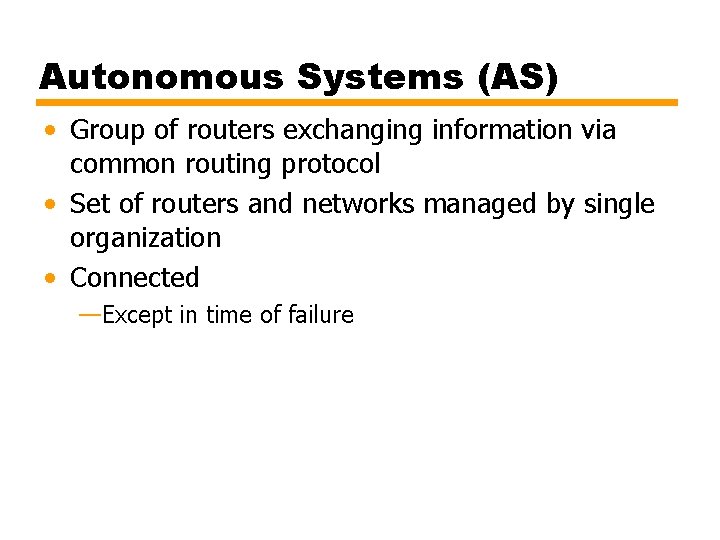
Dijkstra's Algorithm – Formal (3) [Update Least-Cost Paths] L(n) = min[L(n), L(x) + w(x, n)] for all n Ï T If the latter term is the minimum, the path from s to n is now the path from s to x concatenated with the edge from x to n. The algorithm terminates when all nodes have been added to T

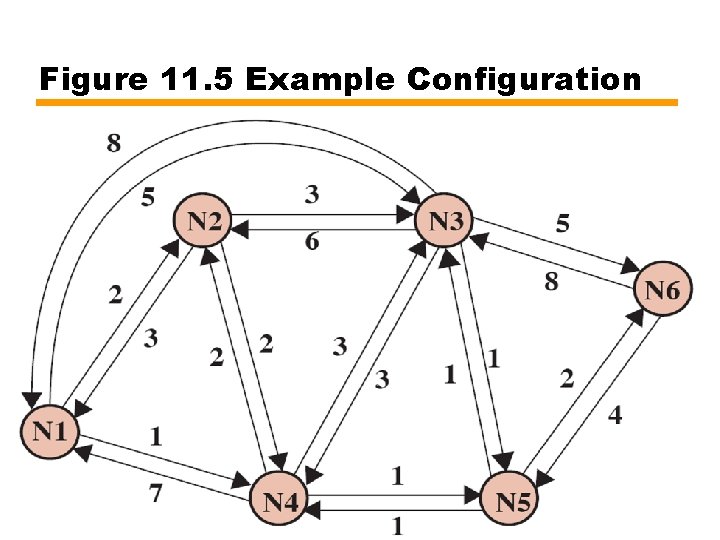
Figure 11. 5 Example Configuration

Figure 11. 6 Dijkstra’s Algorithm Applied to Figure 11. 1

Table 11. 1 Example of Least-Cost Routing Algorithms

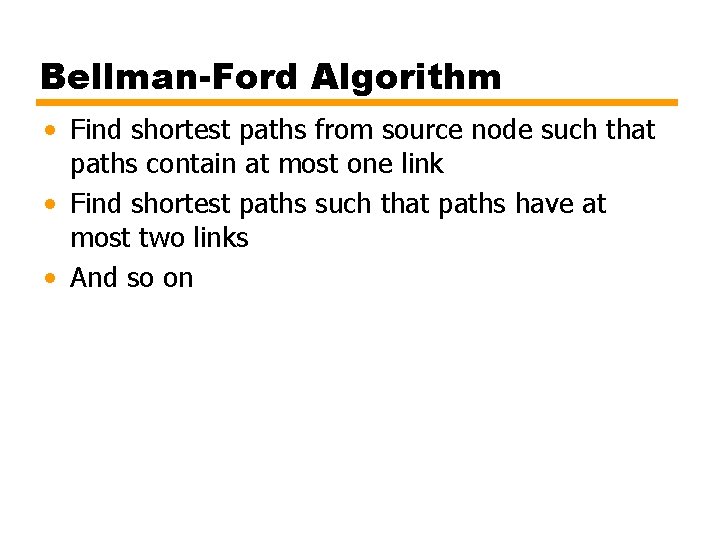
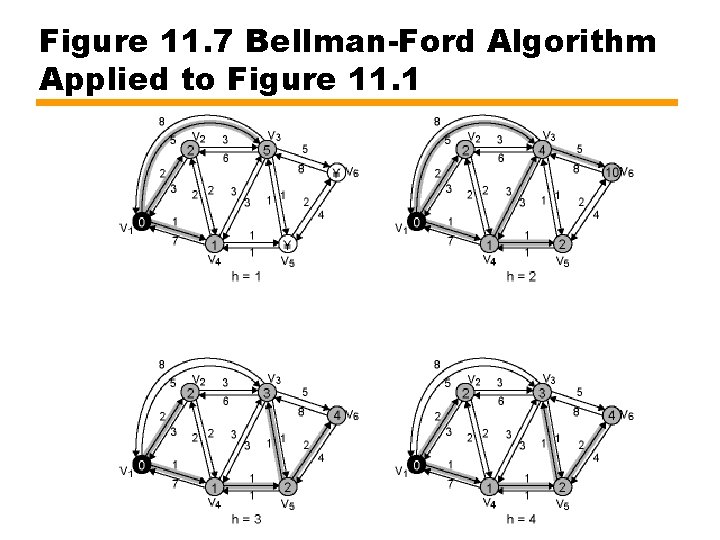
Bellman-Ford Algorithm • Find shortest paths from source node such that paths contain at most one link • Find shortest paths such that paths have at most two links • And so on

Figure 11. 7 Bellman-Ford Algorithm Applied to Figure 11. 1

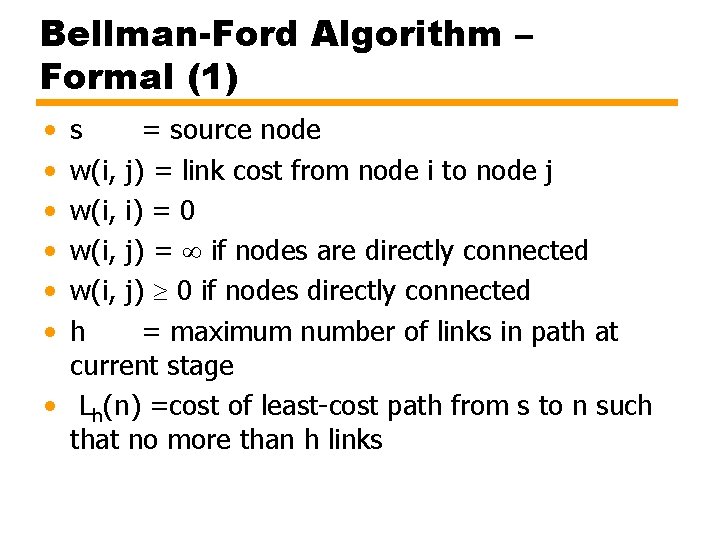
Bellman-Ford Algorithm – Formal (1) • • • s = source node w(i, j) = link cost from node i to node j w(i, i) = 0 w(i, j) = if nodes are directly connected w(i, j) 0 if nodes directly connected h = maximum number of links in path at current stage • Lh(n) =cost of least-cost path from s to n such that no more than h links
![BellmanFord Algorithm Formal 2 Initialization L 0n for all n s Bellman-Ford Algorithm – Formal (2) [Initialization] L 0(n) = , for all n s](https://slidetodoc.com/presentation_image_h2/963aa97da715518bbff235deb15c189b/image-36.jpg)
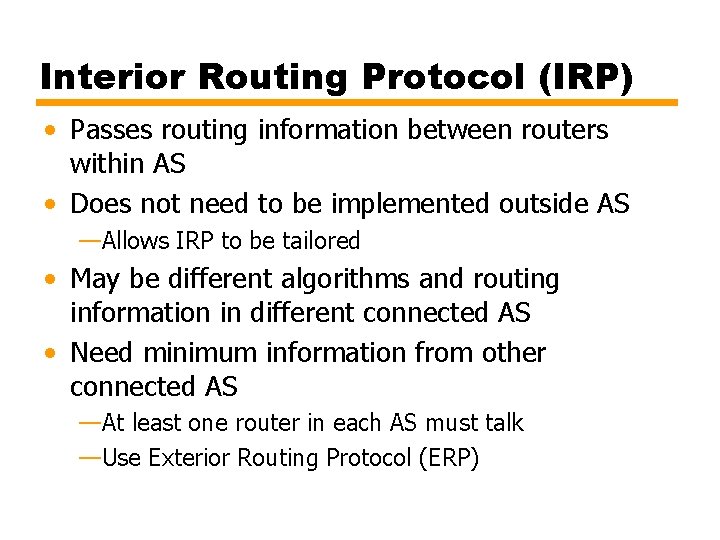
Bellman-Ford Algorithm – Formal (2) [Initialization] L 0(n) = , for all n s Lh(s) = 0, for all h [Update] For each successive h 0: For each n ≠ s, compute Connect n with predecessor node j that achieves minimum Eliminate any connection of n with different predecessor node formed during an earlier iteration Path from s to n terminates with link from j to n

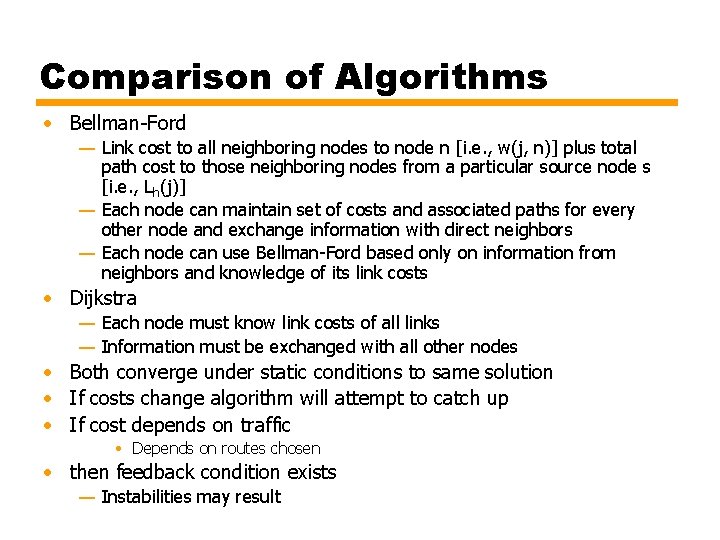
Comparison of Algorithms • Bellman-Ford — Link cost to all neighboring nodes to node n [i. e. , w(j, n)] plus total path cost to those neighboring nodes from a particular source node s [i. e. , Lh(j)] — Each node can maintain set of costs and associated paths for every other node and exchange information with direct neighbors — Each node can use Bellman-Ford based only on information from neighbors and knowledge of its link costs • Dijkstra — Each node must know link costs of all links — Information must be exchanged with all other nodes • Both converge under static conditions to same solution • If costs change algorithm will attempt to catch up • If cost depends on traffic • Depends on routes chosen • then feedback condition exists — Instabilities may result

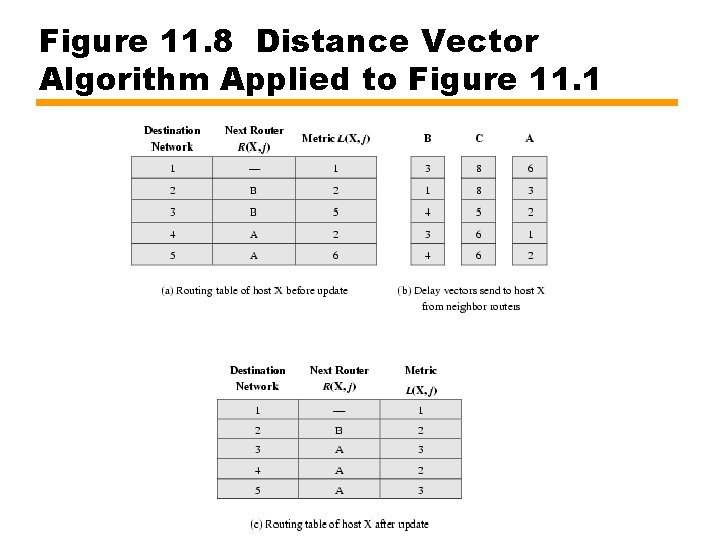
Distance Vector Routing • Each node exchange information with neighbors —Directly connected by same network • Each node maintains three vectors —Link cost —Distance vector —Next hop vector • Every 30 seconds, exchange distance vector with neighbors • Use this to update distance and next hop vector

Figure 11. 8 Distance Vector Algorithm Applied to Figure 11. 1

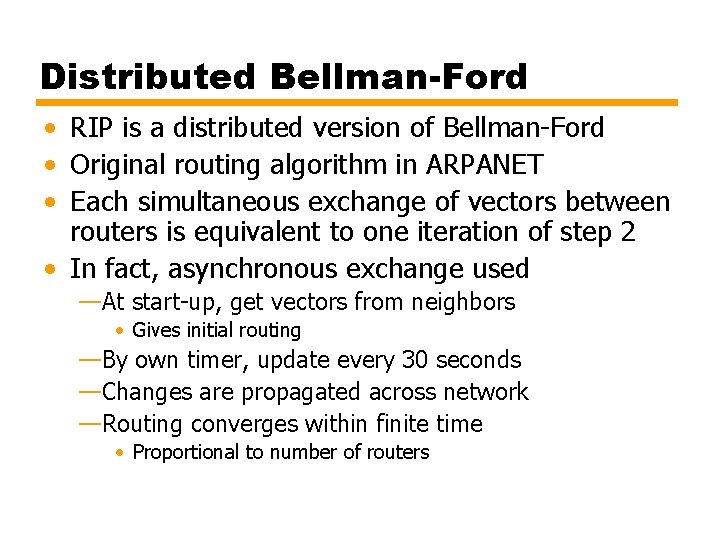
Distributed Bellman-Ford • RIP is a distributed version of Bellman-Ford • Original routing algorithm in ARPANET • Each simultaneous exchange of vectors between routers is equivalent to one iteration of step 2 • In fact, asynchronous exchange used —At start-up, get vectors from neighbors • Gives initial routing —By own timer, update every 30 seconds —Changes are propagated across network —Routing converges within finite time • Proportional to number of routers

RIP Details – Incremental Update • Updates do not arrive from neighbors within small time window • RIP packets use UDP • Tables updated after receipt of individual distance vector —Add any new destination network —Replace existing routes with small delay ones —If update from router R, update all routes using R as next hop

RIP Details – Topology Change • If no updates received from a router within 180 seconds, mark route invalid —Assumes router crash or network connection unstable —Set distance value to infinity • Actually 16

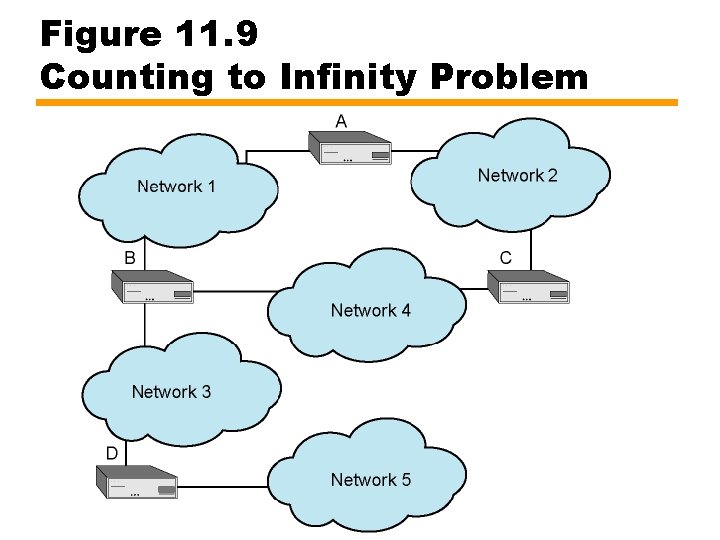
Counting to Infinity Problem (1) • • Slow convergence may cause: All link costs 1 B has distance to network 5 as 2, next hop D A & C have distance 3 and next hop B

Counting to Infinity Problem (2) • Suppose router D fails: — B determines network 5 no longer reachable via D • Sets distance to 4 based on report from A or C — At next update, B tells A and C this — A and C receive this and increment their network 5 distance to 5 • 4 from B plus 1 to reach B — B receives distance count 5 and assumes network 5 is 6 away — Repeat until reach infinity (16) — Takes 8 to 16 minutes to resolve

Figure 11. 9 Counting to Infinity Problem

Split Horizon • Counting to infinity problem caused by misunderstanding between B and A, and B and C —Each thinks it can reach network 5 via the other • Split Horizon rule says do not send information about a route back in the direction it came from —Router sending information is nearer destination than you —Erroneous route now eliminated within time out period (180 seconds)

Poisoned Reverse • Send updates with hop count of 16 to neighbors for route learned from those neighbors —If two routers have routes pointing at each other advertising reverse route with metric 16 breaks loop immediately

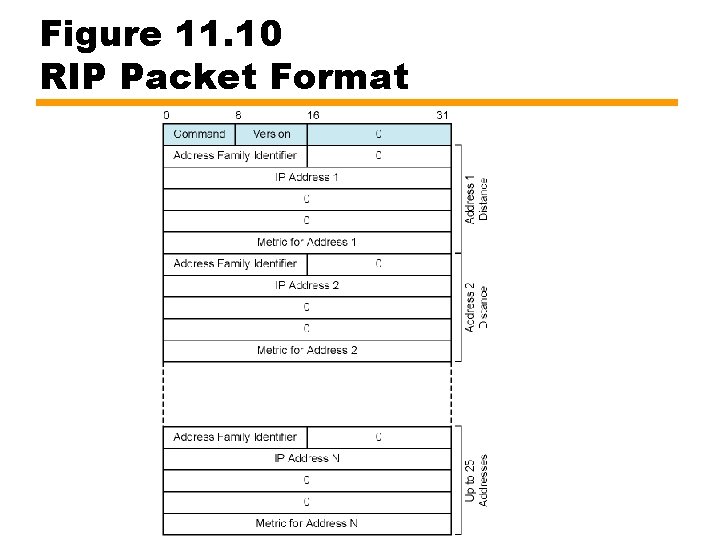
Figure 11. 10 RIP Packet Format

RIP Packet Format Notes • Command: 1=request 2=reply — Updates are replies whether asked for or not — Initializing node broadcasts request — Requests are replied to immediately • Version: 1 or 2 • Address family: 2 for IP • IP address: non-zero network portion, zero host portion — Identifies particular network • Metric — Path distance from this router to network — Typically 1, so metric is hop count

RIP Limitations • Destinations with metric more than 15 are unreachable —If larger metric allowed, convergence becomes lengthy • Simple metric leads to sub-optimal routing tables —Packets sent over slower links • Accept RIP updates from any device —Misconfigured device can disrupt entire configuration

Open Shortest Path First (OSPF) • RIP limited in large internets • OSPF preferred interior routing protocol for TCP/IP based internets • Link state routing used

Link State Routing • When initialized, router determines link cost on each interface • Router advertises these costs to all other routers in topology • Router monitors its costs — When changes occurs, costs are re-advertised • Each router constructs topology and calculates shortest path to each destination network • Not distributed version of routing algorithm • Can use any algorithm — Dijkstra

Table 11. 2 A Comparison if Routing Philosophies

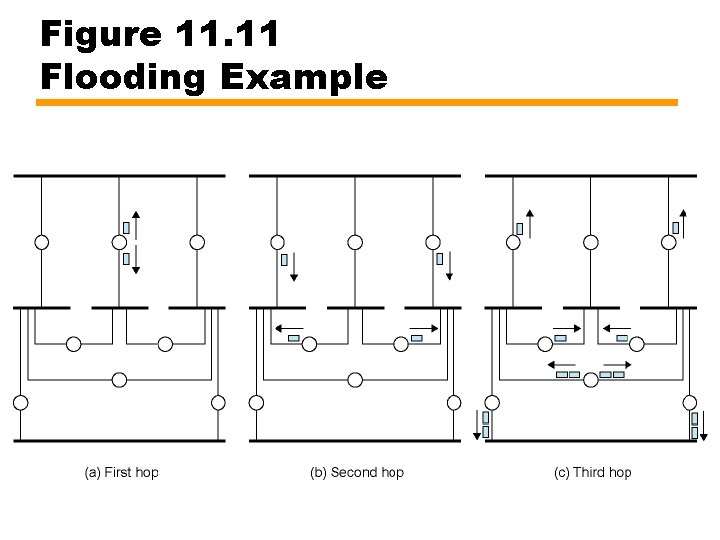
Flooding • Packet sent by source router to every neighbor • Incoming packet resent to all outgoing links except source link • Duplicate packets already transmitted are discarded — Prevent incessant retransmission • All possible routes tried so packet will get through if route exists — Highly robust • At least one packet follows minimum delay route — Reach all routers quickly • All nodes connected to source are visited — All routers get information to build routing table • High traffic load

Figure 11. 11 Flooding Example

OSPF Overview • Router maintains descriptions of state of local links • Transmits updated state information to all routers it knows about • Router receiving update must acknowledge —Lots of traffic generated • Each router maintains database —Directed graph

Router Database Graph • Vertices —Router —Network • Transit • Stub • Edges —Connecting two routers —Connecting router to network • Built using link state information from other routers

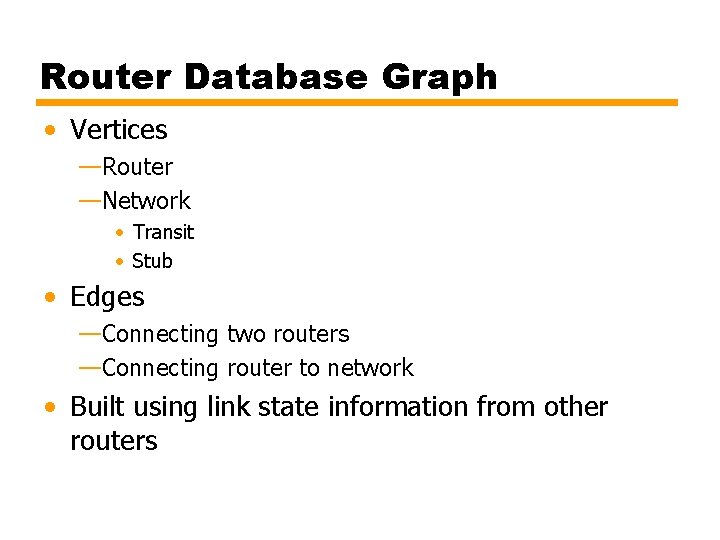
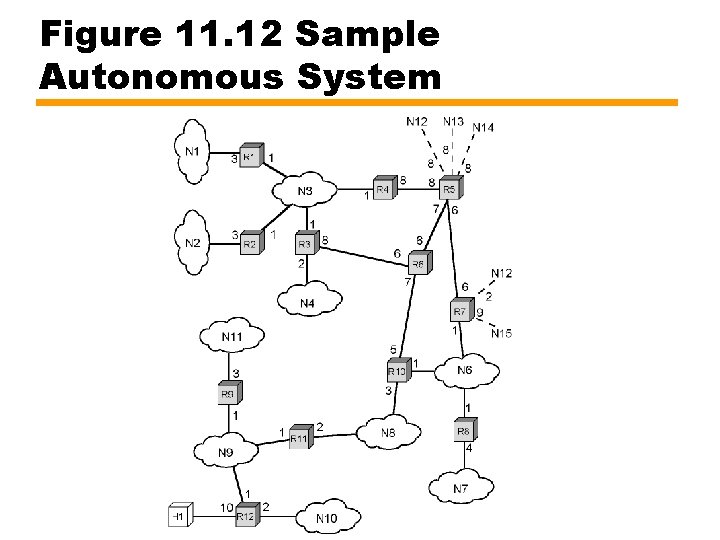
Figure 11. 12 Sample Autonomous System

Figure 11. 13 Directed Graph of Autonomous System of Figure 19. 7

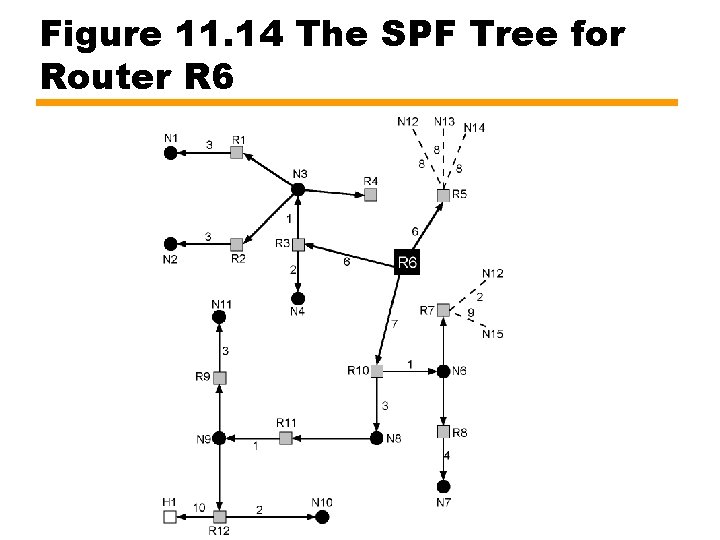
Link Costs • Cost of each hop in each direction is called routing metric • OSPF provides flexible metric scheme based on type of service (TOS) —Normal (TOS) 0 —Minimize monetary cost (TOS 2) —Maximize reliability (TOS 4) —Maximize throughput (TOS 8) —Minimize delay (TOS 16) • Each router generates 5 spanning trees (and 5 routing tables)

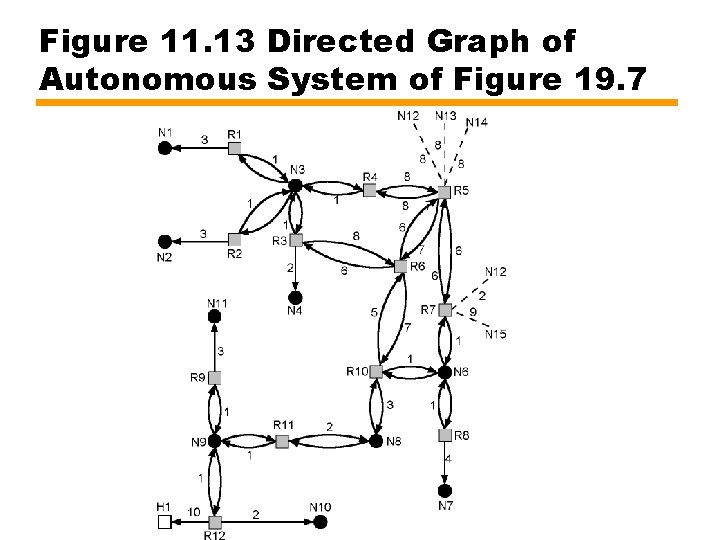
Figure 11. 14 The SPF Tree for Router R 6

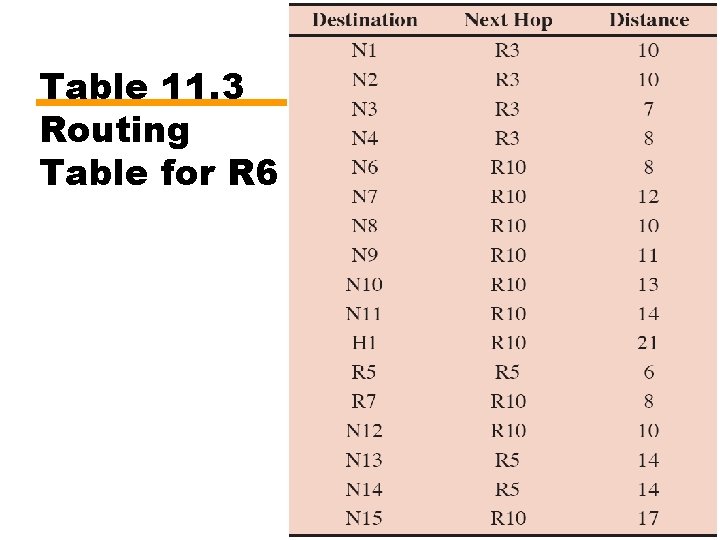
Table 11. 3 Routing Table for R 6

Areas • Make large internets more manageable • Configure as backbone and multiple areas • Area – Collection of contiguous networks and hosts plus routers connected to any included network • Backbone – contiguous collection of networks not contained in any area, their attached routers and routers belonging to multiple areas

Operation of Areas • Each are runs a separate copy of the link state algorithm —Topological database and graph of just that area —Link state information broadcast to other routers in area —Reduces traffic —Intra-area routing relies solely on local link state information

Inter-Area Routing • Path consists of three legs —Within source area • Intra-area —Through backbone • Has properties of an area • Uses link state routing algorithm for inter-area routing —Within destination area • Intra-area

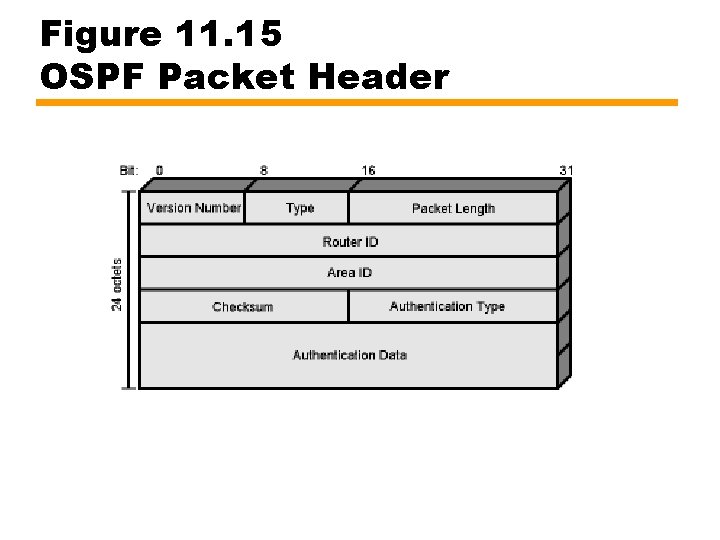
Figure 11. 15 OSPF Packet Header

Packet Format Notes • • • Version number: 2 is current Type: one of 5, see next slide Packet length: in octets including header Router id: this packet’s source, 32 bit Area id: Area to which source router belongs Authentication type: null, simple password or encryption • Authentication data: used by authentication procedure

OSPF Packet Types • Hello: used in neighbor discovery • Database description: Defines set of link state information present in each router’s database • Link state request • Link state update • Link state acknowledgement

Required Reading • Stallings chapter 11