Computer Networks Why Computer Networks Consider computers in










































- Slides: 60

Computer Networks

Why Computer Networks • Consider computers in ancient times, say the 1970 s – To communicate, two computers separated by a distance had to be connected by a rented phone line to communicate – If you wanted your computer to talk to two other computers, you needed two phone lines. . . and so on.

Why Computer Networks – If you needed to communicate with 100 computers you needed 100 phone lines. – This approach did not, scale up.

Arpanet • DARPA Defense Advance Research Projects Administration. (The bad guys in the X files – Responsible for coordinating much Defense Department Research – They and the Universities they dealt with owned the lions share of the worlds computers. . . and they needed to communicate.

Arpanet • • Dedicated p Phone lines were impossible A better idea was needed Researchers had been exploring the idea of “networking” for five or six years • The better idea looked something like this. . .

The Better Idea • Given computers A, B and C – Where A is connected to B – Where B is connected to C – If C needs to talk to A • • Instead of renting another line Let C send the message for A to B Let B FORWARD the message to A In other words, use existing phone lines

The Better Idea • This was one of those simple ideas that would change the world – Appropriately, the contract was bid in 1968 and let in 1969 – The net came up in late 1969 and included • • UCLA UC Santa Barbara Stanford University of Utah

Arpanet • The net was called Arpanet and is, in fact the internet we use today • The protocol used was TCP/IP which we will study • Originally, the computers that did the message forwarding were called IMPs (Interface Message Processors) We now call machines that forward, routers.

Arpanet • Arpanet in 1977 • http: //en. wikipedia. org/wiki/Image: Arpnetmap-march-1977. png

Arpanet • Arpanet grew rapidly, by the mid eighties most colleges and Universities and private sector research facilities were on the net. • By the time of the Morris worm in the late eighties there were 10 s of thousands of machines connect to what was by then know as the internet.

Internet • In the early 90 s, AOL became the first online service to provide its customers access to the internet. • The intenet community swelled from tens of thousands of users to millions of users quite literally overnight.

World Wide Web • In 1990 CERN, a European physics center, began research on a hyperlinked document distribution system. • On August 6, 1991, a prototype of the system was launched. The collection of servers was called the World Wide Web • The first browser, Mosaic, was launched at this time.

World Wide Web • Originally, the web included mostly researchers and research centers. • Then, on day, when AOL made web browsing available to their clients, the world arrived. • You know the rest of the story

Computer Networks • In effect, the Internet makes it appear to your computer is directly connected to several million other computers. • Your computer has, as far as its concerned, a dedicated connection to that computer in an internet cafe in Kenya where that gentleman is having trouble gain access to 10 million dollars.

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Look at the weather forecast

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Buy a textbook

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Check for a movie at a local theater

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Print out an airline boarding pass

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Check on your class assignments

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Do a literature search for your assignment

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Submit your assignment to your professor

Computer Network Basics Computer Networks • Networks make computers much more useful by connecting them to other systems worldwide. • By connecting them to a network, we can – Contact your friends to go out to celebrate finishing your assignment.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can – Get attacked by a worm exploiting a buffer overflow weakness in your operating system.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can – Receive an Trojan horse in an email and inadvertently open it, turning your computer into a zombie.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can – Open a web page that infects your computer with spyware.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can – Get an email with a phishing attack that fools you into giving your credit card information to an online crook.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can – Give computer access to a friend, who sets up file sharing, getting you sued by the RIAA.

Computer Network Basics Computer Networks • Just as networks make computers much more useful by connecting them to other systems worldwide, they also make them more vulnerable. • By connecting them to a network, we can – You get your password for amazon. com stolen by an eavesdropper, who then buys himself a new gaming system at your expense.

Computer Network Basics Computer Networks • Network-based vulnerabilities and attacks are one of the most important security concerns.

Computer Network Basics Introduction • Traditionally, the motivation in designing computer networks was to move information quickly and reliably between computers.

Computer Network Basics Introduction • So the goal for modern computer networks was to be able to efficiently move information worldwide. • Security was initially not an issue. Speed and reliability were.

Computer Network Basics Introduction • Networks must work for many different kinds of computers. • Computers with different – Processors, – Operating systems, and – Running different network access programs.

Computer Network Basics Introduction • For that reason, networks are designed using agreed upon, standard rules, called protocols. • Any computer, operating system, and program that uses these protocols can interact with other computers over networks using the same protocols. • The protocol called TCP/IP, the Arpanet protocol, has become the defacto standard.

Computer Network Basics The Client/Server Model • Computing in computer networks is organized into a client/server model.

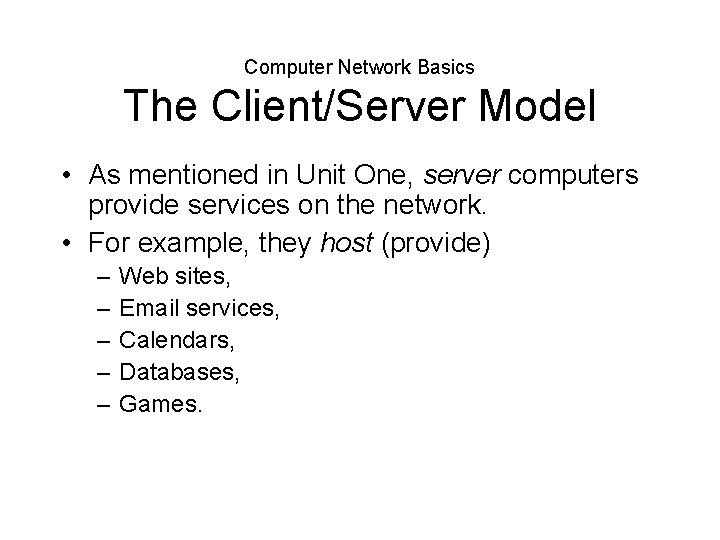
Computer Network Basics The Client/Server Model • As mentioned in Unit One, server computers provide services on the network. • For example, they host (provide) – – – Web sites, Email services, Calendars, Databases, Games.

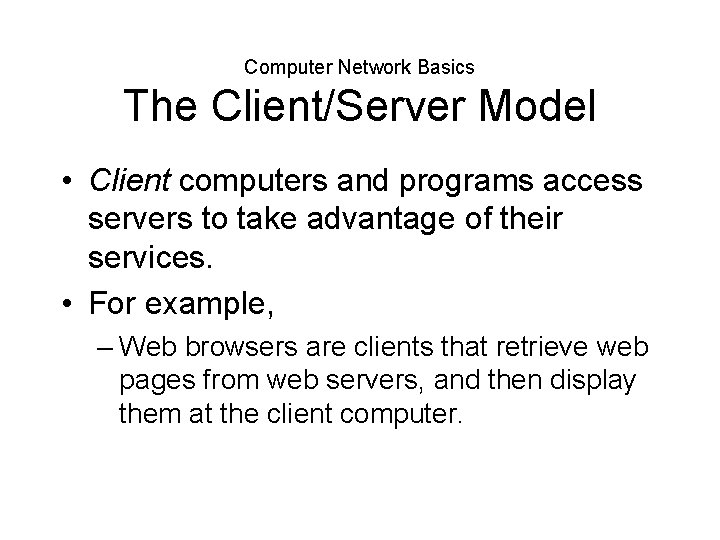
Computer Network Basics The Client/Server Model • Client computers and programs access servers to take advantage of their services.

Computer Network Basics The Client/Server Model • Client computers and programs access servers to take advantage of their services. • For example, – Web browsers are clients that retrieve web pages from web servers, and then display them at the client computer.

Computer Network Basics The Client/Server Model • Client computers and programs access servers to take advantage of their services. • For example, – Email clients like Outlook, Mail, and others embedded in web browsers read and send mail by communicating with mail server computers.

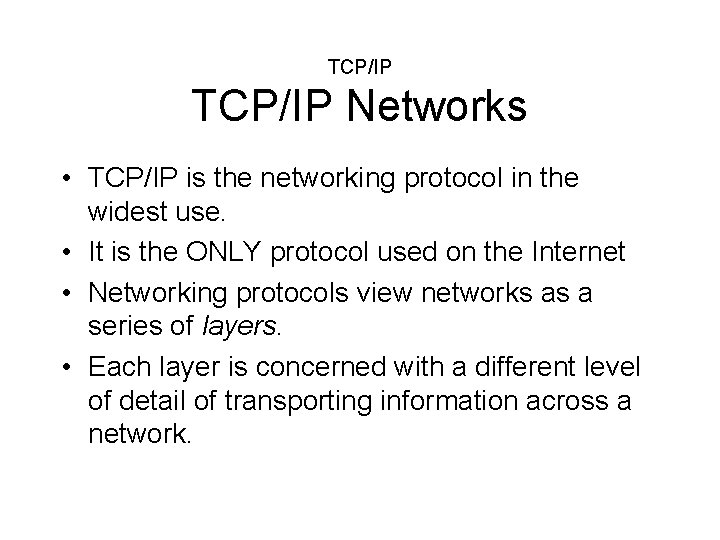
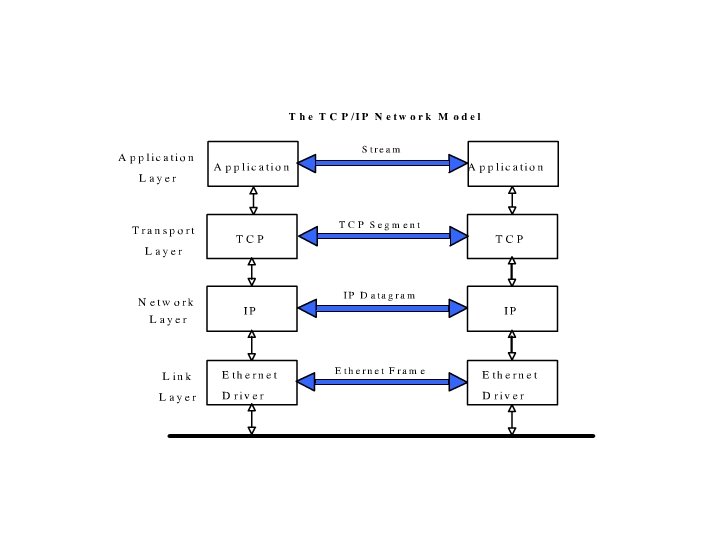
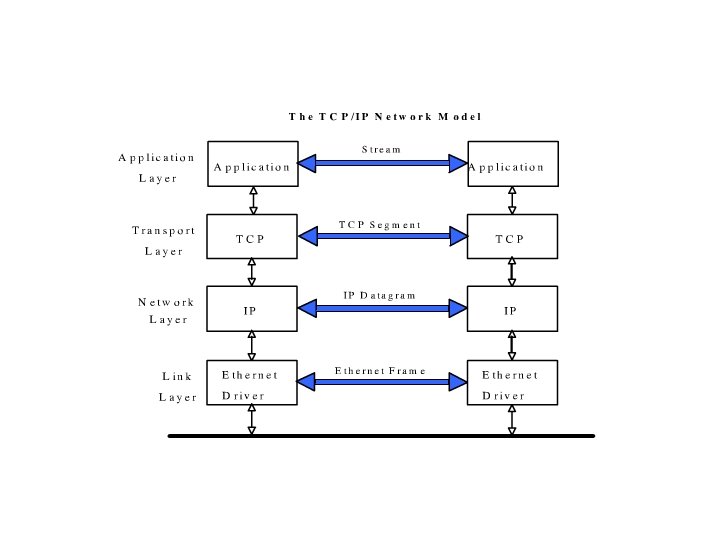
TCP/IP Networks • TCP/IP is the networking protocol in the widest use. • It is the ONLY protocol used on the Internet • Networking protocols view networks as a series of layers. • Each layer is concerned with a different level of detail of transporting information across a network.

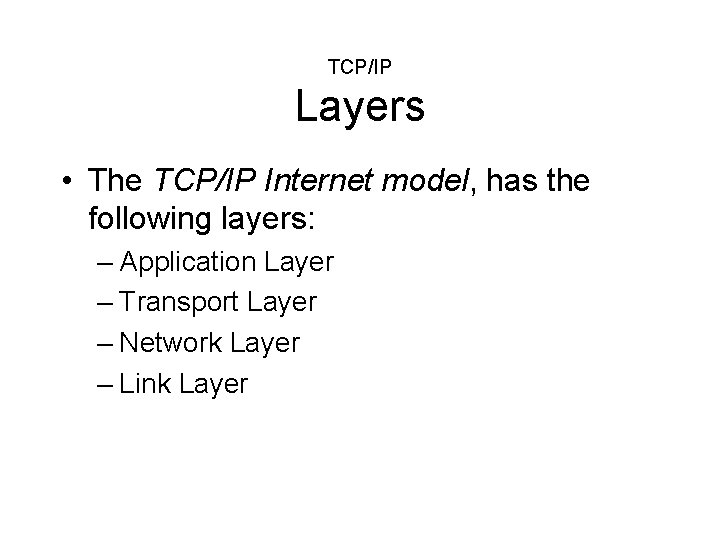
TCP/IP Layers • The TCP/IP Internet model, has the following layers: – Application Layer – Transport Layer – Network Layer – Link Layer


TCP/IP Layers • The different layers are how different parts of the computer view the task of transporting information across a network. • The layers hide detail that isn’t relevant to a particular part of the computer.


TCP/IP Packets • As we mentioned in Section Two, information in computers is in digital format, usually organized as bytes.

TCP/IP Packets • Multiple bytes of information to be sent across the network are organized into packets. – For example, a web server sending an image will send the information as one or more packets with the bytes making up the image.

TCP/IP Application Layer • The application layer is concerned with one program sending packets of data to another program on another computer across a network. • They are not concerned with the details of how this happens. – That is the concern of “lower” layers.


TCP/IP Application Layer • The application layer is controlled by programs that are part of the operating system. • When a program wants to send information, it calls the application layer program, and gives it the information to send.

TCP/IP Application Layer • The application layer is controlled by programs that are part of the operating system. • When the information arrives at the receiving computer, the application layer program delivers it to the program that is to get the information.

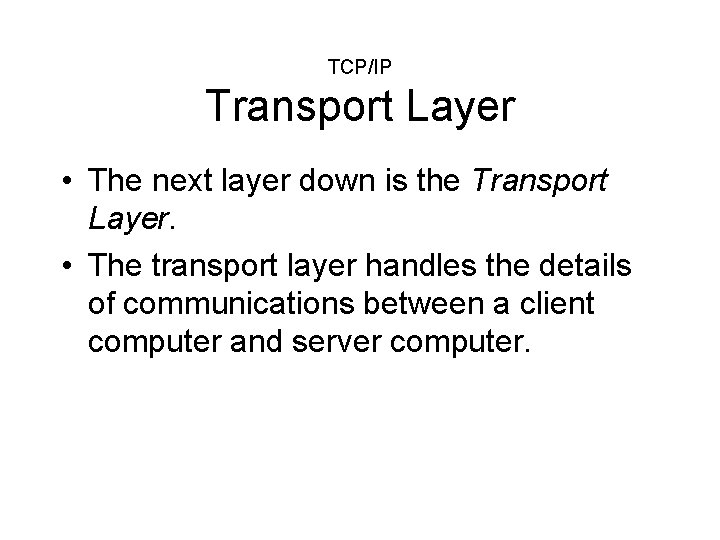
TCP/IP Transport Layer • The next layer down is the Transport Layer. • The transport layer handles the details of communications between a client computer and server computer.

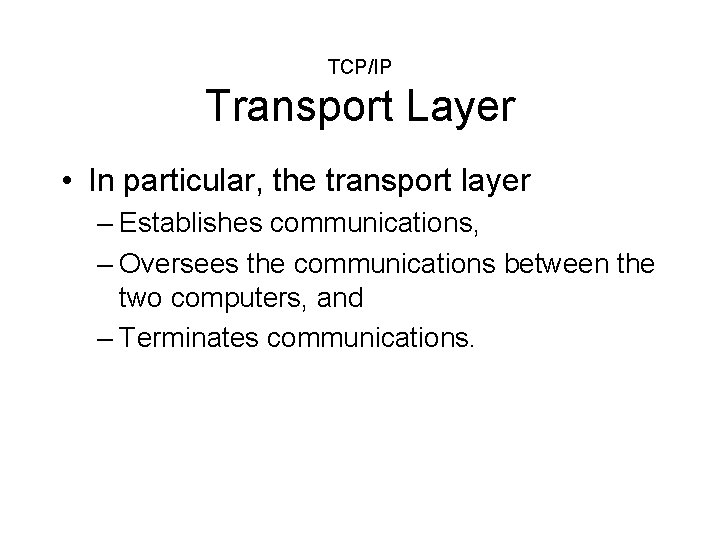
TCP/IP Transport Layer • In particular, the transport layer – Establishes communications, – Oversees the communications between the two computers, and – Terminates communications.

TCP/IP Transport Layer • The transport layer can also track information and verify that it has been received.

TCP/IP Transport Layer • The programs that handle the transport layer on a computer are contacted by the application layer programs in the operating system, not the applications themselves. • This simplifies interactions between the application programs and the layers.



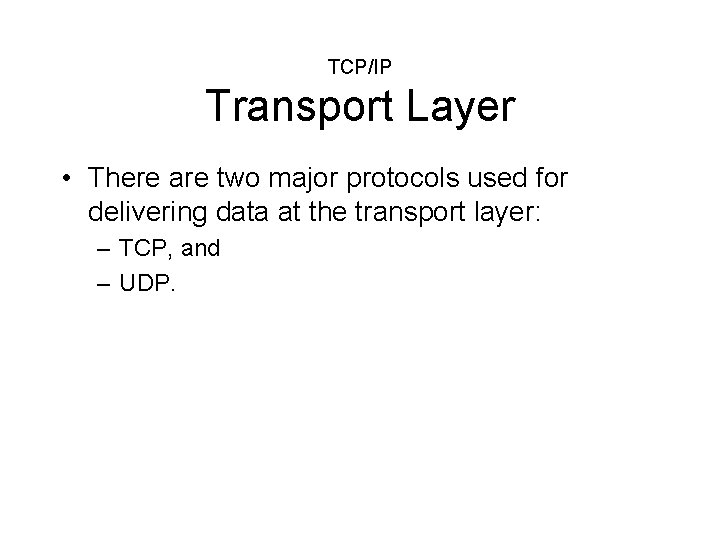
TCP/IP Transport Layer • There are two major protocols used for delivering data at the transport layer: – TCP, and – UDP.

TCP/IP Transport Layer • UDP is a simple protocol that does not promise delivery of packets.

TCP/IP Transport Layer • TCP is a more complicated protocol that does promise packet delivery.