Computer Networks Topology n Physical Layout of Network







- Slides: 19

Computer Networks

Topology n Physical Layout of Network q q n It is the study of the arrangement or mapping of the elements (links, nodes, etc. ) of a network, especially the physical (real) and logical (virtual) interconnections between nodes How devices will communicate with each other Four Common Types q Bus, Ring, Star and Mesh

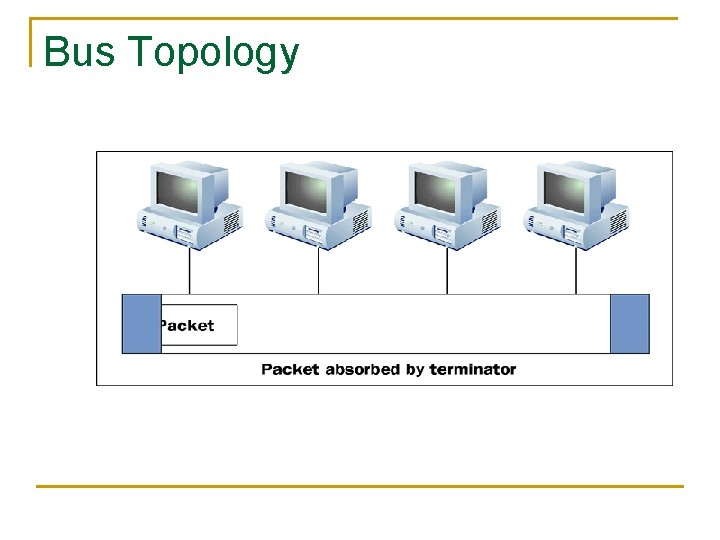
Bus Topology n n n Multipoint Topology Shared by multiple devices A starting and ending terminal point Packets stop and access each node Only one device at a time can transmit

Bus Topology

Bus Topology n n Used by old LANs Advantage q q n Inexpensive Easy to install Disadvantage q q q Slows exponentially with the number of nodes More nodes, less bandwidth More nodes, more collisions

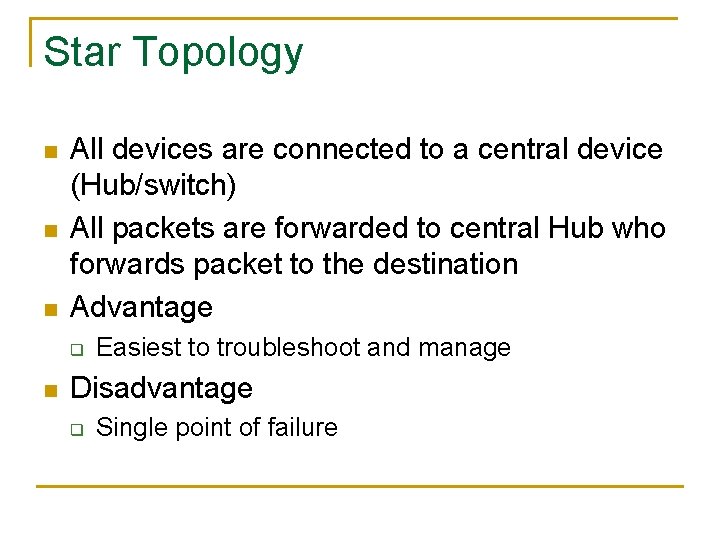
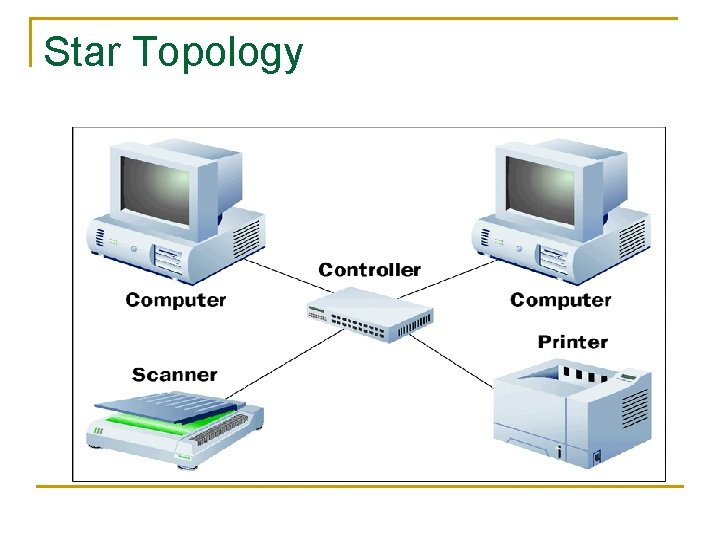
Star Topology n n n All devices are connected to a central device (Hub/switch) All packets are forwarded to central Hub who forwards packet to the destination Advantage q n Easiest to troubleshoot and manage Disadvantage q Single point of failure

Star Topology

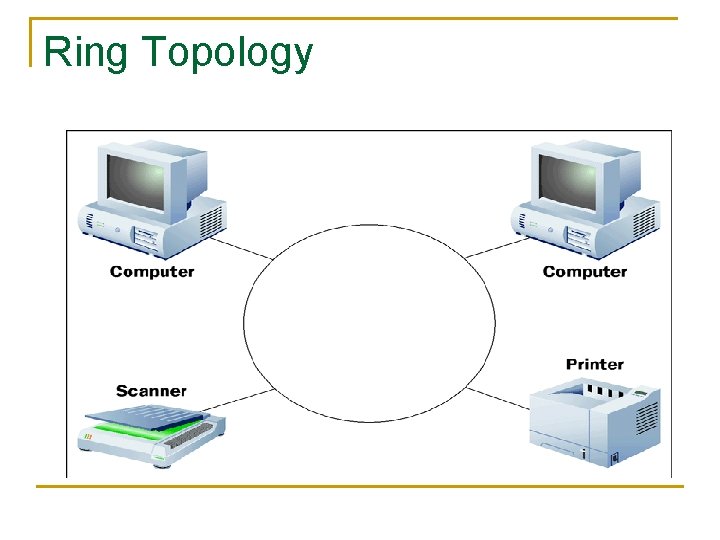
Ring Topology n It is the opposite of Bus q n n n Has no ends Nodes are placed in a circle Packets are sent from one device to the next Advantage q q Suitable for larger number of devices to be connected Token Passing Collision Avoidance Slow

Ring Topology

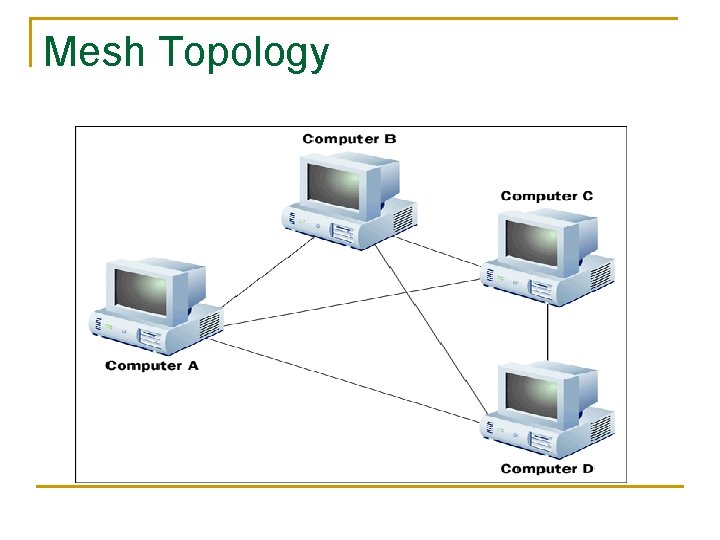
Mesh Topology n n n Point-to-Point topology Each device is DIRECTLY connected to every other device on the network Usually used for Fault Tolerance It is not usually used as it is most expensive and size of network is very large Some WAN architectures use it for better redundancy and robustness.

Mesh Topology

Hybrid Topologies n Mixture of Two or more basic topologies q Star Bus Topology n q Multiple hubs are connected in a Star topology with a Bus Star Ring Topology n Wired like Star but functions like Ring

Design Consideration n n Choice of selection of a particular topology depends upon the environment in which the nodes will operate The physical arrangement of the computers do not necessarily dictate some specific topology

Channel Access Methods n n Cooperative Rules merely used to avoid/minimize/control collisions Some commonly used access rules are: q q q CSMA/CD CSMA/CA Token Passing Polling Demand Priority

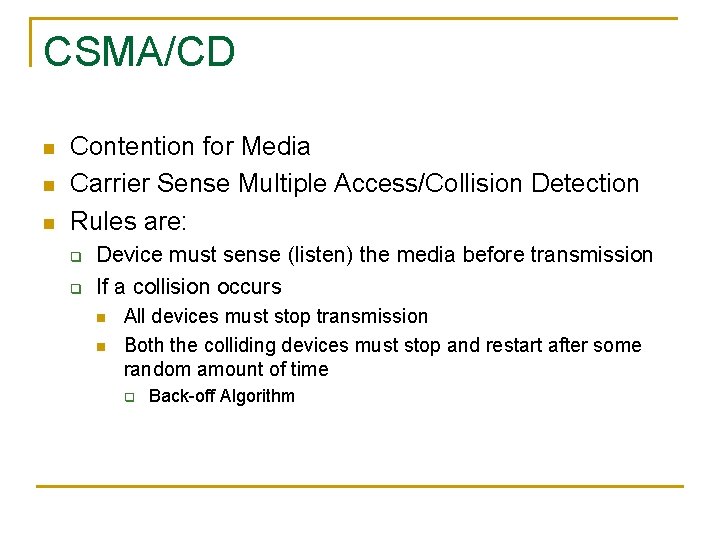
CSMA/CD n n n Contention for Media Carrier Sense Multiple Access/Collision Detection Rules are: q q Device must sense (listen) the media before transmission If a collision occurs n n All devices must stop transmission Both the colliding devices must stop and restart after some random amount of time q Back-off Algorithm

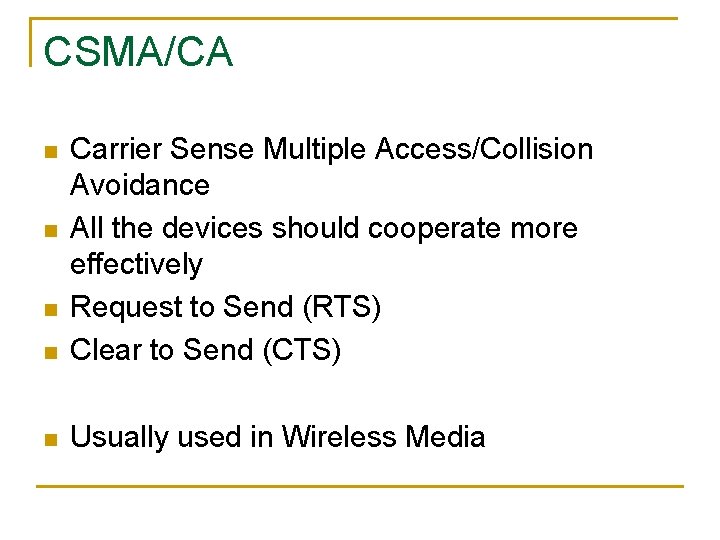
CSMA/CA n Carrier Sense Multiple Access/Collision Avoidance All the devices should cooperate more effectively Request to Send (RTS) Clear to Send (CTS) n Usually used in Wireless Media n n n

Token Passing n n n Special Packet known as TOKEN is forwarded from one node to the next in a ring Only the node who possesses the TOKEN could send a message If a computer doesn’t need to send the message (don’t have data to transfer or have completed transfer), TOKEN is passed to next system Node who has message to send, waits until it captures the TOKEN Active Monitor

Polling n n Is similar to Token Passing but have a centralized control Each computer on the network is asked, or polled, in sequence whether it wants to transmit. If it does, it sends its packet while everyone else waits; if it has nothing to send, the next computer is polled.

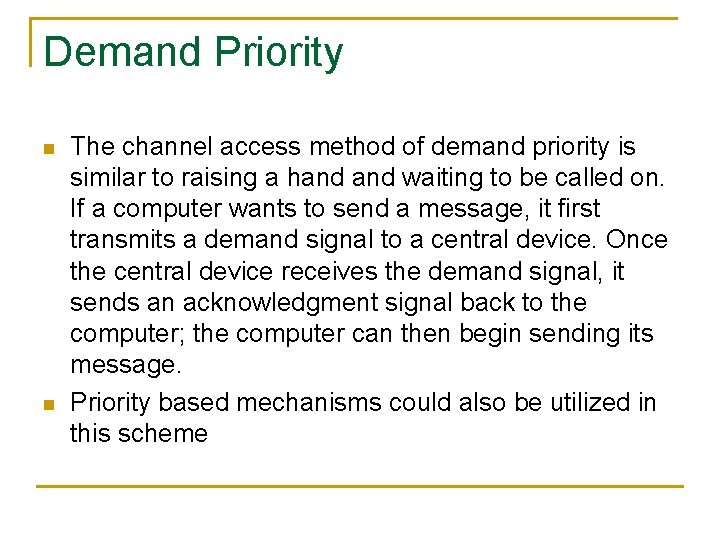
Demand Priority n n The channel access method of demand priority is similar to raising a hand waiting to be called on. If a computer wants to send a message, it first transmits a demand signal to a central device. Once the central device receives the demand signal, it sends an acknowledgment signal back to the computer; the computer can then begin sending its message. Priority based mechanisms could also be utilized in this scheme