Computer networks Name K SUDHA Designation Lecturer Department








![– Substitute the values found in the S-boxes for all B[j ] • Take – Substitute the values found in the S-boxes for all B[j ] • Take](https://slidetodoc.com/presentation_image/dff3f6b2cbe122204946c829aae924b9/image-16.jpg)
![Summaries Key schedule: C[0]D[0] = PC 1(key) for 1 <= i <= 16 C[i] Summaries Key schedule: C[0]D[0] = PC 1(key) for 1 <= i <= 16 C[i]](https://slidetodoc.com/presentation_image/dff3f6b2cbe122204946c829aae924b9/image-17.jpg)
![Decipherment: • • • R[16]L[16] = IP(cipher block) for 1 <= i <= 16 Decipherment: • • • R[16]L[16] = IP(cipher block) for 1 <= i <= 16](https://slidetodoc.com/presentation_image/dff3f6b2cbe122204946c829aae924b9/image-18.jpg)































- Slides: 67

Computer networks Name: K. SUDHA Designation: Lecturer Department: Electrical and Electronics Engineering Subject code: CS 2361 Year: III Unit: IV Title: Data Compression

Data Compression • Represents an information source (e. g. a data file, a speech signal, an image, or a video signal) • as accurately as possible using the fewest number of bits. • process of encoding information using fewer bits(or other information-bearing units) than an unencoded • it helps reduce the consumption of expensive resources, such as hard disk space or transmission bandwidth

Data Compression • allows the exact original data to be reconstructed from the compressed data. • The term lossless is in contrast to lossy data compression, which only allows an approximation of the original data to be reconstructed • is required for text and data files, such as bank records, text articles, etc. • Example: executable programs and source code


Lossy compression • The compressed and decompressing data may well be different from the original • used to compress multimedia data (audio, video, stil images), especially in applications such as streaming media and internet telephony. By contrast, lossless compression is required for text and data files, such as bank records, text articles, etc. • repeatedly compressing and decompressing the file will cause it to progressively lose quality

Two basic lossy compression schemes: • • lossy transform codecs – samples of picture or sound are taken, chopped into small segments, transformed into a new basis space, and quantized. – The resulting quantized values are then entropy coded. lossy predictive codecs – previous and/or subsequent decoded data is used to predict the current sound sample or image frame. – The error between the predicted data and the real data, together with any extra information needed to reproduce the prediction – is then quantized and coded.

Cryptography • Is the science of writing in secret code to provide security • The word is derived from the Greek kryptos, meaning hidden. • Cryptography is closely related to the disciplines of cryptology and cryptanalysis. • Includes techniques such as microdots, merging words with images, and other ways to hide information in storage or transit.

Cryptography • is associated with scrambling plaintext (ordinary text, sometimes referred to as cleartext) into ciphertext (a process called encryption), then back again (known as decryption). • Individuals who practice this field are known as cryptographers. • Objective: – Confidentiality – Integrity – Non-repudiation Authentication

Cryptography

Cryptography

RSA Algorithm • • • Generate two large random primes p and q, of approximately equal size such that their product n = pq is of the required bit length e. g. 1024 bits. Compute n = pq and (φ) phi = (p-1)(q-1). Choose an integer e, 1 < e < phi, such that gcd(e, phi) = 1. Compute the secret exponent d, 1 < d < phi, such that ed ≡ 1 (mod phi) The public key is (n, e) and the private key is (n, d). n is known as the modulus. e is known as the public exponent d is known as the secret exponent

Summary of RSA • • • n = pq, where p and q are distinct primes. phi, φ = (p-1)(q-1) e < n such that gcd(e, phi)=1 d = e-1 mod phi. c = me mod n, 1<m<n. m = cd mod n.

DES(Data Encryption Standard) • DES is the archetypal block cipher • operates on 64 -bit blocks of data, using a 56 -bit key. • It is a 'private key' system. – 1 Process the key. – 2 Process a 64 -bit data block.

Process the key. – Get a 64 -bit key from the user – Calculate the key schedule. • • • Perform the following permutation on the 64 -bit key. Split the permuted key into two halves. Calculate the 16 subkeys. Start with i = 1. Perform one or two circular left shifts on both Permute the concatenation C[i]D[i] as indicated below Loop back to 1. 2. 3. 1 until K[16] has been calculated

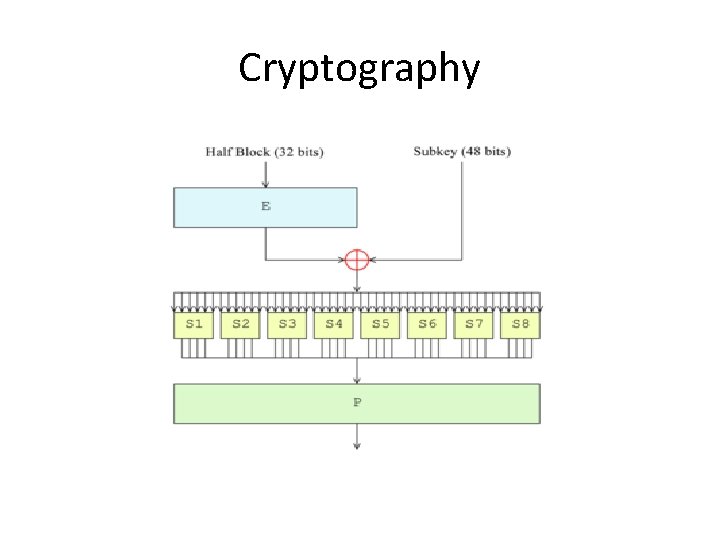
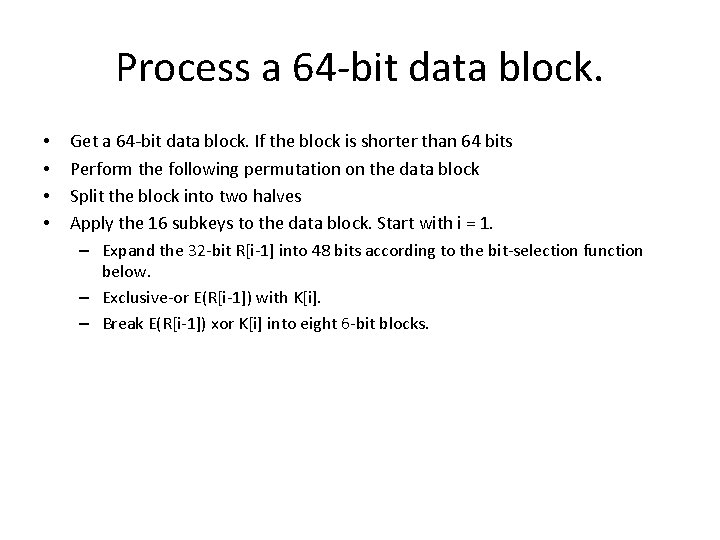
Process a 64 -bit data block. • • Get a 64 -bit data block. If the block is shorter than 64 bits Perform the following permutation on the data block Split the block into two halves Apply the 16 subkeys to the data block. Start with i = 1. – Expand the 32 -bit R[i-1] into 48 bits according to the bit-selection function below. – Exclusive-or E(R[i-1]) with K[i]. – Break E(R[i-1]) xor K[i] into eight 6 -bit blocks.
![Substitute the values found in the Sboxes for all Bj Take – Substitute the values found in the S-boxes for all B[j ] • Take](https://slidetodoc.com/presentation_image/dff3f6b2cbe122204946c829aae924b9/image-16.jpg)
– Substitute the values found in the S-boxes for all B[j ] • Take the 1 st and 6 th bits of B[j] together as a 2 -bit value • Take the 2 nd through 5 th bits of B[j] together as a 4 -bit value • • • Replace B[j] with S[j][m][n]. Substitution Box 1 (S[1]) Permute the concatenation of B[1] through B[8] Exclusive-or the resulting value with L[i-1]. L[i] = R[i-1]. Loop back to 2. 4. 1 until K[16] has been applied.
![Summaries Key schedule C0D0 PC 1key for 1 i 16 Ci Summaries Key schedule: C[0]D[0] = PC 1(key) for 1 <= i <= 16 C[i]](https://slidetodoc.com/presentation_image/dff3f6b2cbe122204946c829aae924b9/image-17.jpg)
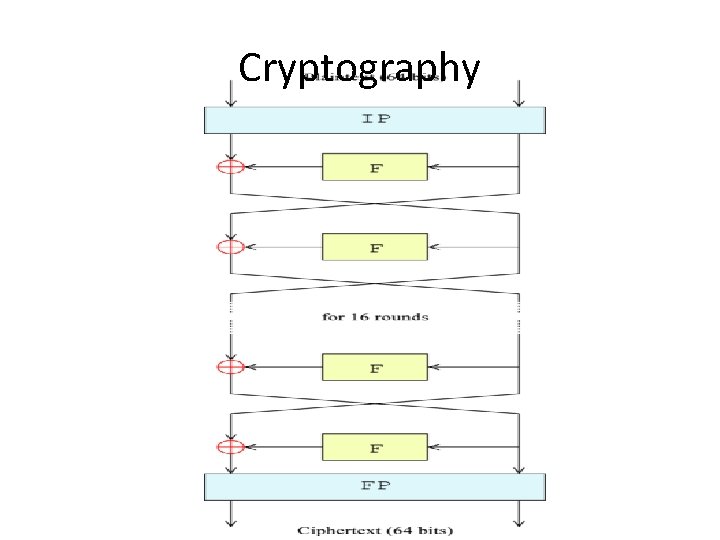
Summaries Key schedule: C[0]D[0] = PC 1(key) for 1 <= i <= 16 C[i] = LS[i](C[i-1]) D[i] = LS[i](D[i-1]) K[i] = PC 2(C[i]D[i]) Encipherment: L[0]R[0] = IP(plain block) for 1 <= i <= 16 L[i] = R[i-1] R[i] = L[i-1]xor f(R[i-1], K[i]) cipher block = FP(R[16]L[16])
![Decipherment R16L16 IPcipher block for 1 i 16 Decipherment: • • • R[16]L[16] = IP(cipher block) for 1 <= i <= 16](https://slidetodoc.com/presentation_image/dff3f6b2cbe122204946c829aae924b9/image-18.jpg)
Decipherment: • • • R[16]L[16] = IP(cipher block) for 1 <= i <= 16 R[i-1] = L[i] L[i-1] = R[i] xor f(L[i], K[i]) plain block = FP(L[0]R[0])

Generating keys • Key generation requires a good source of random bits – Bad key material makes system vulnerable to attacks. Has been done in practice. – Hardware generators provide the best source. – For end-user applications - some user interaction can be used (mouse movement, key strokes, etc. ) – Using system time for high security requirements is a bad idea! • For high-security applications, key generation should take place in a closed environment. Apr 30, 2002 Mårten Trolin 19

Distributing symmetric keys • Symmetric keys are very sensitive and must be distributed with great care. • Depending on how valueable the key is, different approaches are possible. – Send the key to recipient by physically secure means, e. g. , by courier, by registered mail etc. – If a common key exists, send the new key encrypted under the common key. – Split the key into components and send the key components with different security officers. Apr 30, 2002 Mårten Trolin 20

Key splitting • One option for distributing keys with lower risk is to split the key into components and send the parts separately. • After generation, the key is split into n parts. To recreate the key, all n parts must be available. • Knowledge of less than n parts should give as little help as possible for recreating of keys. • How do we do this? Apr 30, 2002 Mårten Trolin 21

Splitting into parts of equal length • When splitting into parts of equal length, the key of length l is split into n components, each of length l / n. • First part consists of bits 1 through (l / n) – 1, second part of bits l / n though 2(l / n) – 1, etc. • A disadvantage of this method is that knowledge of several parts reveals parts of the key, and leaves fewer bits for guessing. Apr 30, 2002 Mårten Trolin 22

Exclusive-or with random bit strings • If we want to distribute an l-bit key k as n components, we first generate (n – 1) l-bit strings u 1, u 2, …, un – 1. • The n’th component is computed as un = k u 1 u 2 … un – 1, where denotes bitwise XOR. • The basic properties of XOR gives that u 1 u 2 … un = k. • This method gives higher security, since knowledge of either n – 1 components reveals nothing about the key. – Recall that with the previous method, this knowledge revealed several key bits, making a brute-force attack on the rest easier. Apr 30, 2002 Mårten Trolin 23

Distributing keys for asymmetric keys • Distributing the public part of asymmetric keys is simple – no special security measures are needed. • Distributing keys in certificates makes it easier to prove the owner of the key. • If the private part is to be distributed, the same techniques as for symmetric keys can be used. Apr 30, 2002 Mårten Trolin 24

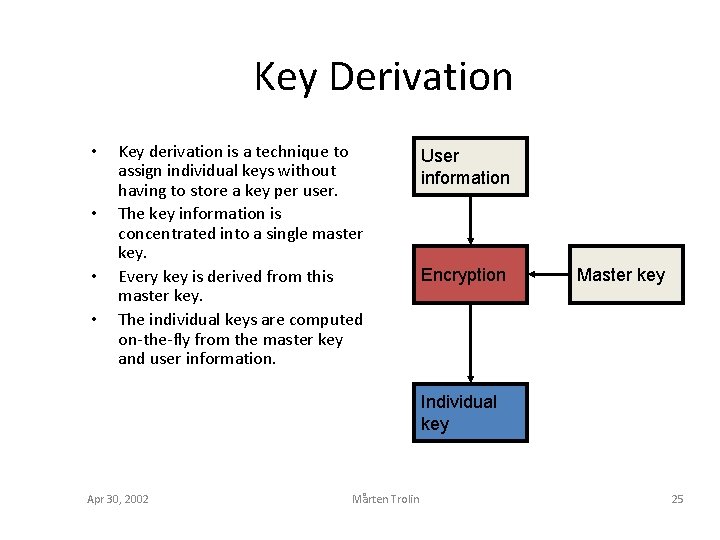
Key Derivation • • Key derivation is a technique to assign individual keys without having to store a key per user. The key information is concentrated into a single master key. Every key is derived from this master key. The individual keys are computed on-the-fly from the master key and user information. User information Encryption Master key Individual key Apr 30, 2002 Mårten Trolin 25

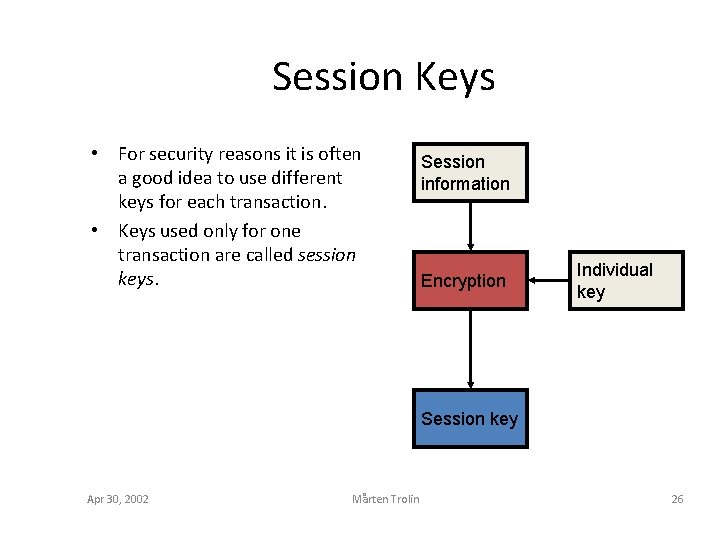
Session Keys • For security reasons it is often a good idea to use different keys for each transaction. • Keys used only for one transaction are called session keys. Session information Encryption Individual key Session key Apr 30, 2002 Mårten Trolin 26

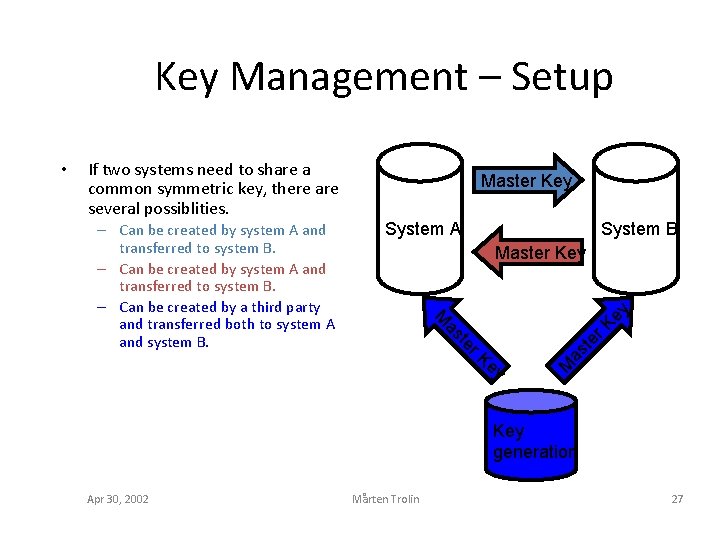
Key Management – Setup If two systems need to share a common symmetric key, there are several possiblities. System A System B ey Master Key y Ke as t r te as er K M – Can be created by system A and transferred to system B. – Can be created by a third party and transferred both to system A and system B. Master Key M • Key generation Apr 30, 2002 Mårten Trolin 27

Zone Master Key – ZMK • If the two systems have one common symmetric key, this key can be used to encrypt other keys that are sent between the systems. • This key is often called Zone Master Key, ZMK. • Once this common key has been established, exchanging further keys is simple. Apr 30, 2002 Mårten Trolin 28

Symmetric Key Management – Zone Master Key ZMK Component 1 ZMK Component 2 ZMK Component 3 Configuration system Host system Generation of Zone Master Key sent as components to host by security officers Apr 30, 2002 Mårten Trolin Components reassembled as the host to give the same key 29

Transfer of Zone Master Key • When transferring the Zone Master Key, no single person will see the key. • Key components are given out only one at the time, so that no one person sees all components. • When combining the components, each component is first encrypted. Only when all components are encrypted do the security officers meet and give all components. Apr 30, 2002 Mårten Trolin 30

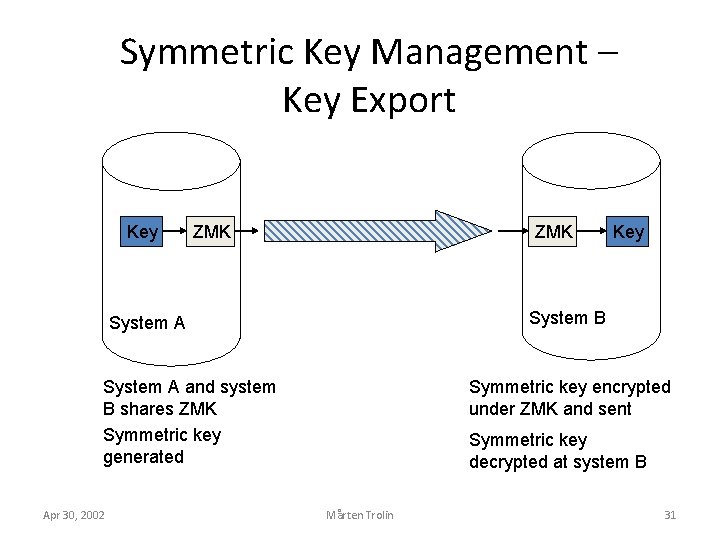
Symmetric Key Management – Key Export Key ZMK System B System A and system B shares ZMK Symmetric key generated Apr 30, 2002 Key Symmetric key encrypted under ZMK and sent Symmetric key decrypted at system B Mårten Trolin 31

Key length • Apart from selecting a good algorithm, the key length to be used must be chosen. • When selecting the key length, you need to take into account security requirements and hardware costs. – Longer keys are more secure, but encryption and decryption takes longer time. – How sensitive is the data? Do we need to protect it for twenty seconds, twenty days or twenty years? – Who do we want to protect ourselves against? The causal eaves-dropper, a competing company or a foreign government? Apr 30, 2002 Mårten Trolin 32

Symmetric key lengths • If the symmetric cipher is good, the only way to break the key is to do exhaustive search. For an n -bit key, this requires 2 n iterations. • As of today, 64 -bit keys take a few years to crack for someone with enough resources. 128 -bit keys are virtually impossible to break, and are likely to stay that way for the foreseeable future. • Since encryption and decryption is fast, there is usually no reason to use less than 128 bits. Apr 30, 2002 Mårten Trolin 33

Symmetric key lengths Time to break • The graph below demonstrates how the time necessary to break a key depends on the key length. Key length Apr 30, 2002 Mårten Trolin 34

Asymmetric key lengths • For asymmetric systems, there are much more efficient ways than exhaustive search to retrieve the key. – For RSA, factoring the modulus gives the private key. • The longest RSA key that is publicly known to have been broken is 512 bits. – Two years ago, this required 30 CPU-years. • 1024 bit keys probably remain secure for the next years. • Be very careful with comparisons between strength of symmetric and asymmetric keys! Apr 30, 2002 Mårten Trolin 35

Asymmetric keys • Asymmetric keys often have a longer life-span than symmetric keys. – Symmetric keys are used for session encryption, which often has to be kept secret only for a limited period. – Asymmetric keys are used for signatures that may have to remain secure for several decades. • Analyze the situation and choose the most appropriate solution! Apr 30, 2002 Mårten Trolin 36

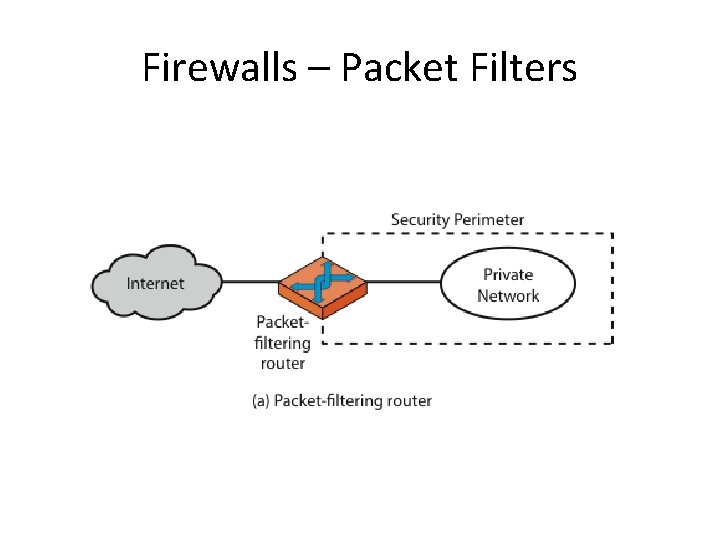
What is a Firewall? • A choke point of control and monitoring • Interconnects networks with differing trust • Imposes restrictions on network services – only authorized traffic is allowed • Auditing and controlling access – can implement alarms for abnormal behavior • Itself immune to penetration • Provides perimeter defence

Classification of Firewall Characterized by protocol level it controls in • Packet filtering • Circuit gateways • Application gateways • Combination of above is dynamic packet filter

Firewalls – Packet Filters

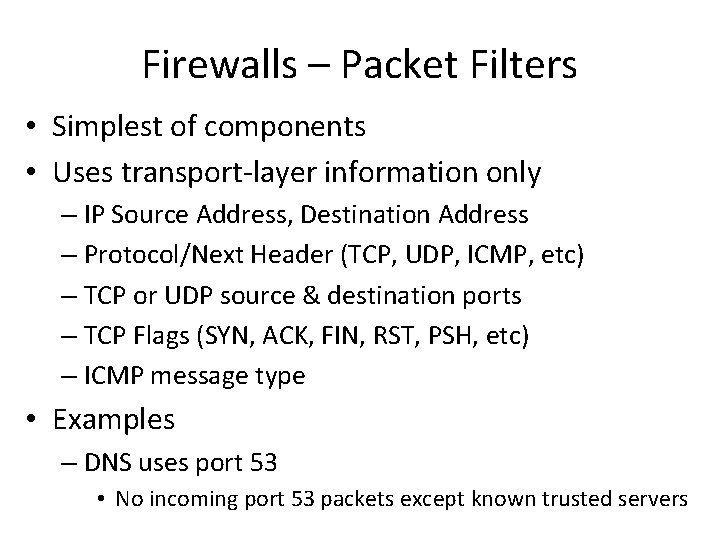
Firewalls – Packet Filters • Simplest of components • Uses transport-layer information only – IP Source Address, Destination Address – Protocol/Next Header (TCP, UDP, ICMP, etc) – TCP or UDP source & destination ports – TCP Flags (SYN, ACK, FIN, RST, PSH, etc) – ICMP message type • Examples – DNS uses port 53 • No incoming port 53 packets except known trusted servers

Usage of Packet Filters • Filtering with incoming or outgoing interfaces – E. g. , Ingress filtering of spoofed IP addresses – Egress filtering • Permits or denies certain services – Requires intimate knowledge of TCP and UDP port utilization on a number of operating systems

How to Configure a Packet Filter • Start with a security policy • Specify allowable packets in terms of logical expressions on packet fields • Rewrite expressions in syntax supported by your vendor • General rules - least privilege – All that is not expressly permitted is prohibited – If you do not need it, eliminate it

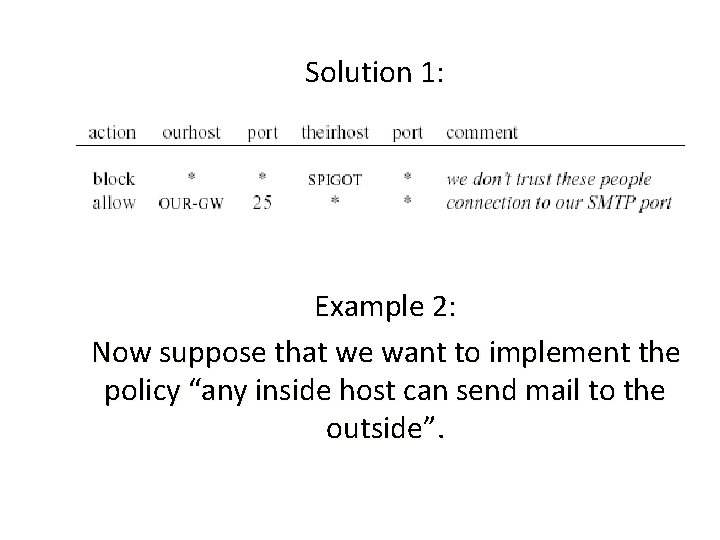
Every ruleset is followed by an implicit rule reading like this. Example 1: Suppose we want to allow inbound mail (SMTP, port 25) but only to our gateway machine. Also suppose that mail from some particular site SPIGOT is to be blocked.

Solution 1: Example 2: Now suppose that we want to implement the policy “any inside host can send mail to the outside”.

Solution 2: This solution allows calls to come from any port on an inside machine, and will direct them to port 25 on the outside. Simple enough… So why is it wrong?

• Our defined restriction is based solely on the outside host’s port number, which we have no way of controlling. • Now an enemy can access any internal machines and port by originating his call from port 25 on the outside machine. What can be a better solution ?

The ACK signifies that the packet is part of an ongoing conversation n Packets without the ACK are connection establishment messages, which we are only permitting from internal hosts n

Security & Performance of Packet Filters • IP address spoofing – Fake source address to be trusted – Add filters on router to block • Tiny fragment attacks – Split TCP header info over several tiny packets – Either discard or reassemble before check • Degradation depends on number of rules applied at any point • Order rules so that most common traffic is dealt with first • Correctness is more important than speed

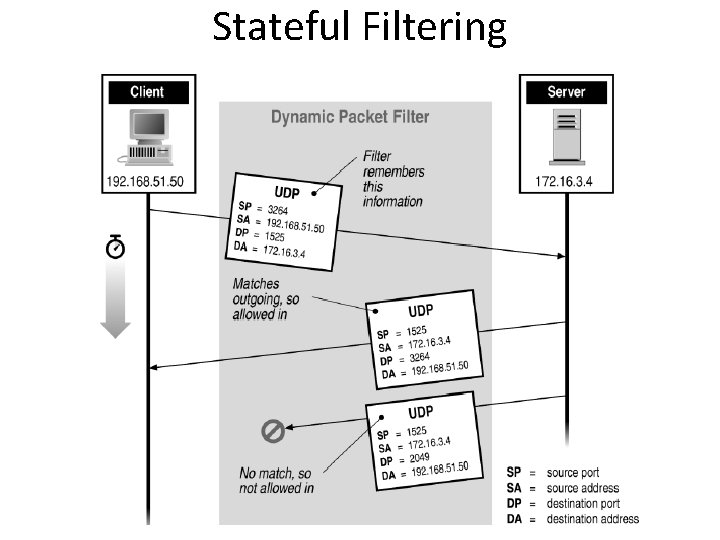
Port Numbering • TCP connection – Server port is number less than 1024 – Client port is number between 1024 and 16383 • Permanent assignment – Ports <1024 assigned permanently • 20, 21 for FTP 23 for Telnet • 25 for server SMTP 80 for HTTP • Variable use – Ports >1024 must be available for client to make any connection – This presents a limitation for stateless packet filtering • If client wants to use port 2048, firewall must allow incoming traffic on this port – Better: stateful filtering knows outgoing requests

Firewalls – Stateful Packet Filters • Traditional packet filters do not examine higher layer context – ie matching return packets with outgoing flow • Stateful packet filters address this need • They examine each IP packet in context – Keep track of client-server sessions – Check each packet validly belongs to one • Hence are better able to detect bogus packets out of context

Stateful Filtering

Firewall Outlines • Packet filtering • Application gateways • Circuit gateways • Combination of above is dynamic packet filter

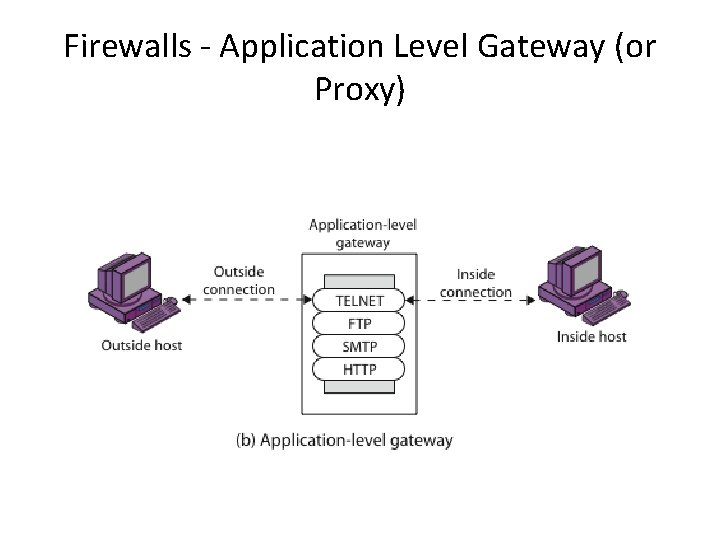
Firewall Gateways • Firewall runs set of proxy programs – Proxies filter incoming, outgoing packets – All incoming traffic directed to firewall – All outgoing traffic appears to come from firewall • Policy embedded in proxy programs • Two kinds of proxies – Application-level gateways/proxies • Tailored to http, ftp, smtp, etc. – Circuit-level gateways/proxies • Working on TCP level

Firewalls - Application Level Gateway (or Proxy)

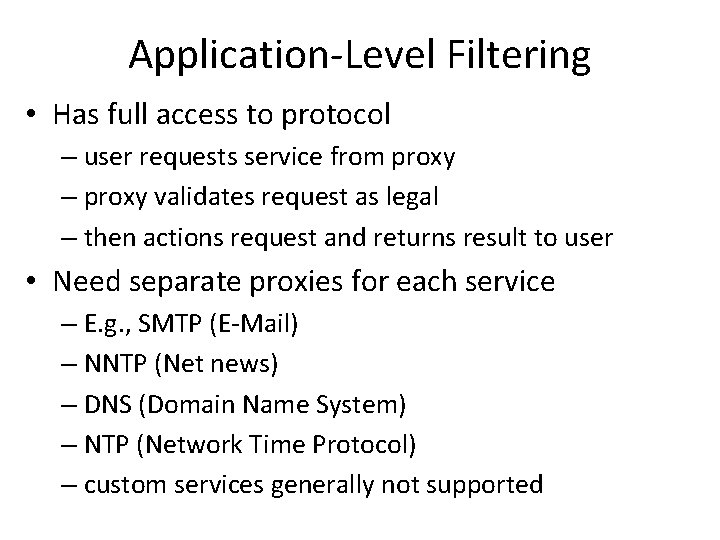
Application-Level Filtering • Has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user • Need separate proxies for each service – E. g. , SMTP (E-Mail) – NNTP (Net news) – DNS (Domain Name System) – NTP (Network Time Protocol) – custom services generally not supported

App-level Firewall Architecture Telnet proxy Telnet daemon FTP proxy FTP daemon SMTP proxy SMTP daemon Network Connection Daemon spawns proxy when communication detected …

Enforce policy for specific protocols • E. g. , Virus scanning for SMTP – Need to understand MIME, encoding, Zip archives

Firewall Outlines • Packet filtering • Application gateways • Circuit gateways • Combination of above is dynamic packet filter

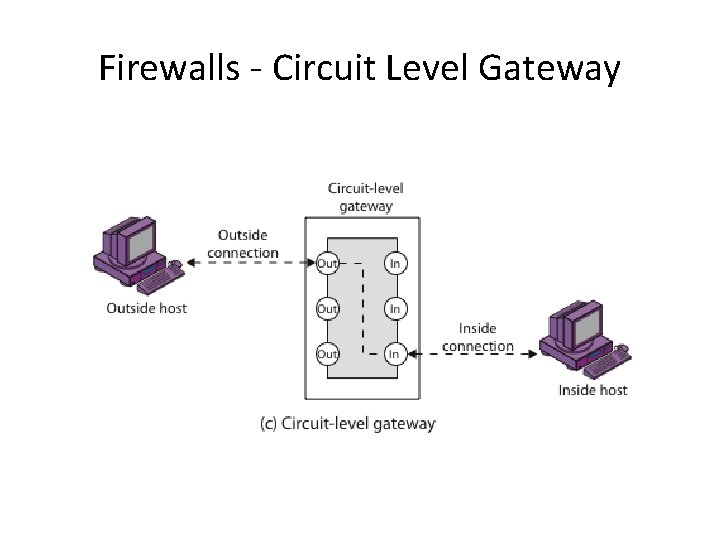
Firewalls - Circuit Level Gateway

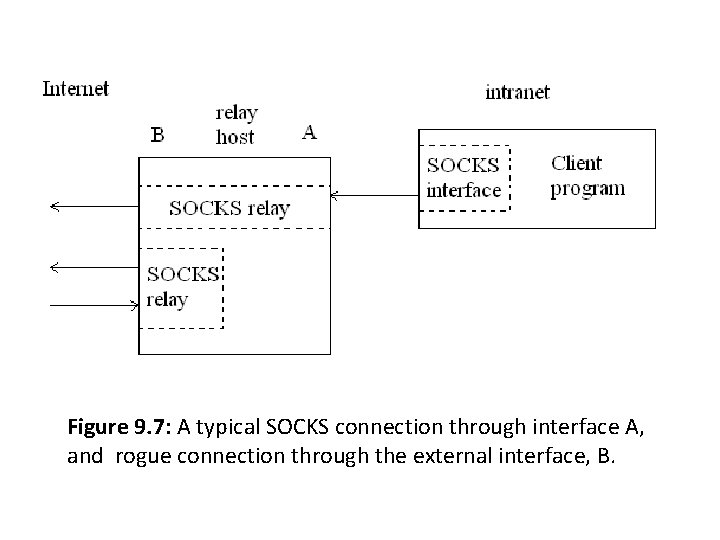
Figure 9. 7: A typical SOCKS connection through interface A, and rogue connection through the external interface, B.

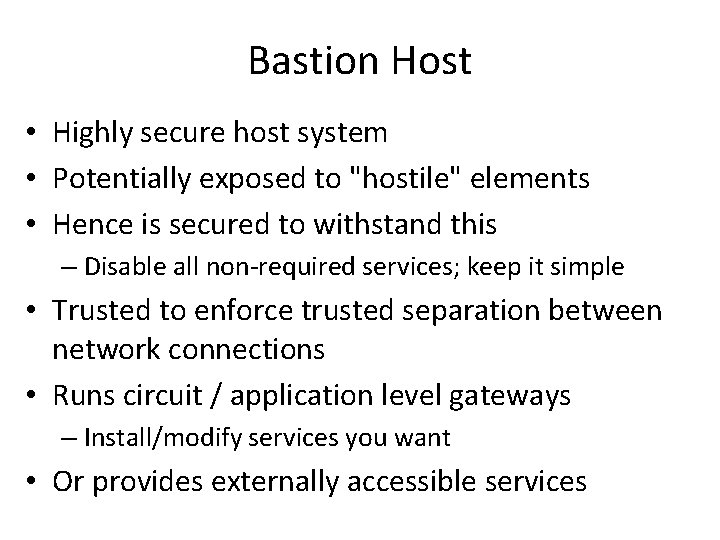
Bastion Host • Highly secure host system • Potentially exposed to "hostile" elements • Hence is secured to withstand this – Disable all non-required services; keep it simple • Trusted to enforce trusted separation between network connections • Runs circuit / application level gateways – Install/modify services you want • Or provides externally accessible services

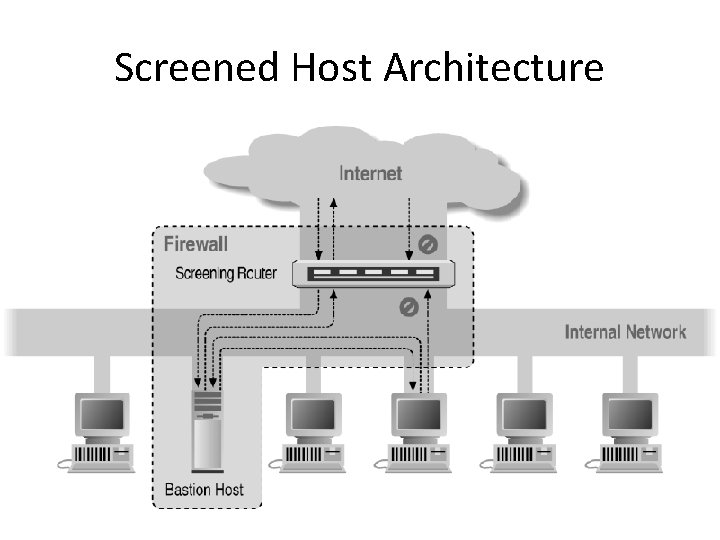
Screened Host Architecture

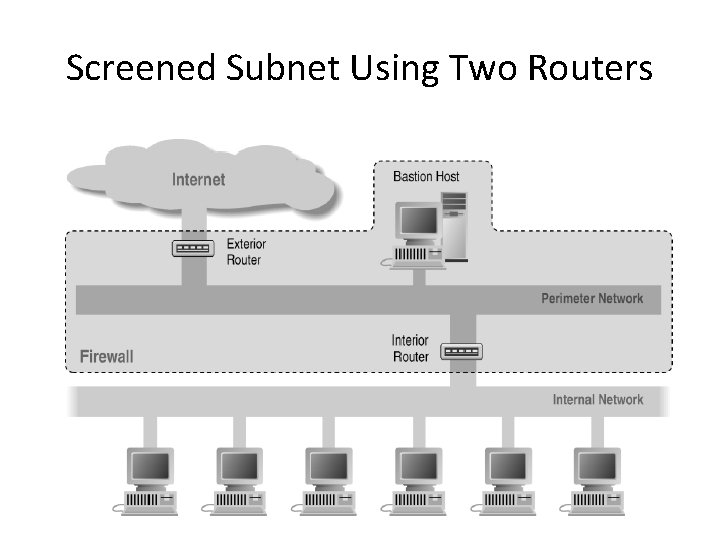
Screened Subnet Using Two Routers

Firewalls Aren’t Perfect? • Useless against attacks from the inside – Evildoer exists on inside – Malicious code is executed on an internal machine • Organizations with greater insider threat – Banks and Military • Protection must exist at each layer – Assess risks of threats at every layer • Cannot protect against transfer of all virus infected programs or files – because of huge range of O/S & file types

Quiz • In this question, we explore some applications and limitations of a stateless packet filtering firewall. For each of the question, briefly explain how the firewall should be configured to defend against the attack, or why the firewall cannot defend against the attack. – Can the firewall prevent a SYN flood denial-of-service attack from the external network? – Can the firewall prevent a Smurf attack from the external network? Recall that as we discussed in the class before, the Smurf attack uses the broadcast IP address of the subnet.

– Can the firewall prevent external users from exploiting a security bug in a CGI script on an internal web server (the web server is serving requests from the Internet)? – Can the firewall prevent an online password dictionary attack from the external network on the telnet port of an internal machine? – Can the firewall prevent a user on the external network from opening a window on an X server in the internal network? Recall that by default an X server listens for connections on port 6000 – Can the firewall block a virus embedded in an incoming email? – Can the firewall be used to block users on the internal network from browsing a specific external IP address?

Thank u
 Lecturer's name or lecturer name
Lecturer's name or lecturer name Designation lecturer
Designation lecturer Designation of lecturer
Designation of lecturer Lecturer name
Lecturer name A switched wan is normally implemented as a network
A switched wan is normally implemented as a network Basestore iptv
Basestore iptv Sudha chandran smoking
Sudha chandran smoking Sudha yalamanchili
Sudha yalamanchili Sudha balla
Sudha balla Dr sudha gupta
Dr sudha gupta Domain name service in computer networks
Domain name service in computer networks System domain
System domain Student id name department name
Student id name department name Jeannie watkins
Jeannie watkins Spe distinguished lecturer
Spe distinguished lecturer Hello good afternoon teacher
Hello good afternoon teacher Photography lecturer
Photography lecturer Lecturer in charge
Lecturer in charge Guest lecturer in geography
Guest lecturer in geography Pearson lecturer resources
Pearson lecturer resources 140000/120
140000/120 Lector vs lecturer
Lector vs lecturer Lecturer in charge
Lecturer in charge Cfa lecturer handbook
Cfa lecturer handbook Lecturer asad ali
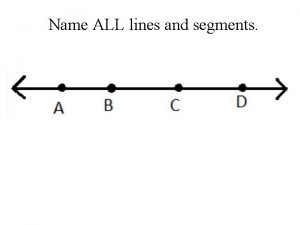
Lecturer asad ali Name 3 points
Name 3 points Symbole roulement
Symbole roulement Drawing and disbursing officer powers
Drawing and disbursing officer powers Vis designation normalisee
Vis designation normalisee 25 cr mo 4 désignation
25 cr mo 4 désignation Trou taraudé débouchant
Trou taraudé débouchant Aluminium designation
Aluminium designation Smaw electrode designation
Smaw electrode designation Certified exhibition management
Certified exhibition management Crsp certification canada
Crsp certification canada Professor designation
Professor designation Désignation normalisée des vis
Désignation normalisée des vis 888-663-8081
888-663-8081 125+35
125+35 Cid course descriptors
Cid course descriptors The use of uniform terminology and plain english
The use of uniform terminology and plain english Cmrp designation
Cmrp designation Cmrp certification
Cmrp certification Designation
Designation The use of uniform terminology and plain english
The use of uniform terminology and plain english Health care surrogate definition
Health care surrogate definition Rwa designation
Rwa designation Sgs mdr designation
Sgs mdr designation Sgs mdr designation
Sgs mdr designation Post/designation
Post/designation Désignation
Désignation Ces vis
Ces vis Designation agreement pst
Designation agreement pst Chrp requirements
Chrp requirements What is cmrp certification
What is cmrp certification Crc in computer networks
Crc in computer networks Crc in computer networks
Crc in computer networks Traffic management in computer networks
Traffic management in computer networks Tanenbaum
Tanenbaum What is optimality principle in computer networks
What is optimality principle in computer networks Snmp osi model
Snmp osi model What is optimality principle in computer networks
What is optimality principle in computer networks Business applications of computer networks
Business applications of computer networks Classify computer networks based on transmission technology
Classify computer networks based on transmission technology Dns in computer networks
Dns in computer networks Intserv vs diffserv
Intserv vs diffserv Icmp in computer networks
Icmp in computer networks Http computer networks
Http computer networks