Computer Networks Lecture 5 Network Layer Protocols Arzad




















- Slides: 101

Computer Networks (Lecture 5: Network Layer Protocols ) Arzad Kherani (alam@cse. iitd. ac. in) Dept. of Computer Sc. And Engg. Indian Institute of Technology Delhi Computer Networks, Jan-May 2004 1

Outline l l l Connection-less vs. connection-oriented data transfer Routing protocol Congestion control IP protocol ICMP protocol Computer Networks, Jan-May 2004 2

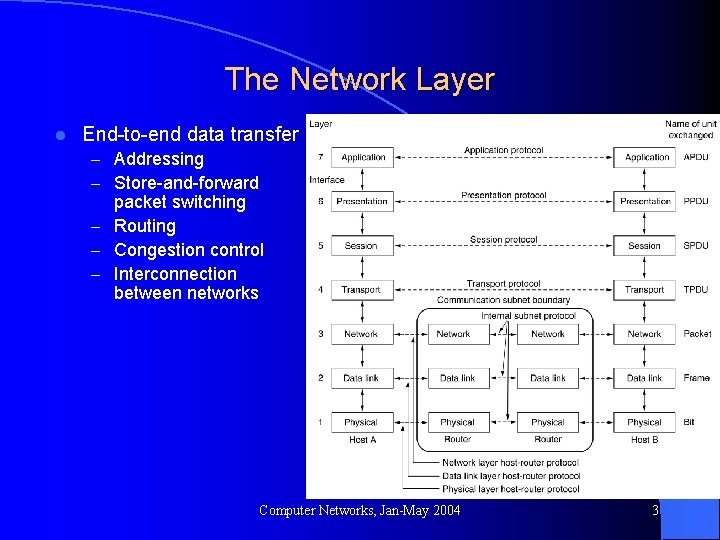
The Network Layer l End-to-end data transfer – Addressing – Store-and-forward packet switching – Routing – Congestion control – Interconnection between networks Computer Networks, Jan-May 2004 3

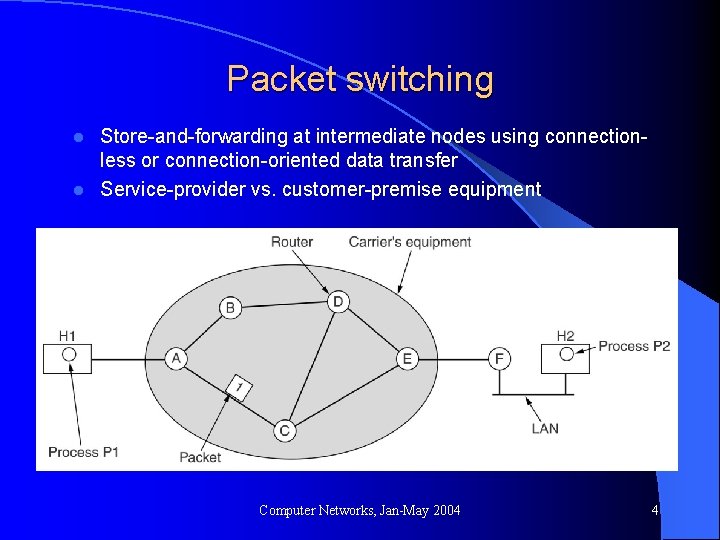
Packet switching Store-and-forwarding at intermediate nodes using connectionless or connection-oriented data transfer l Service-provider vs. customer-premise equipment l Computer Networks, Jan-May 2004 4

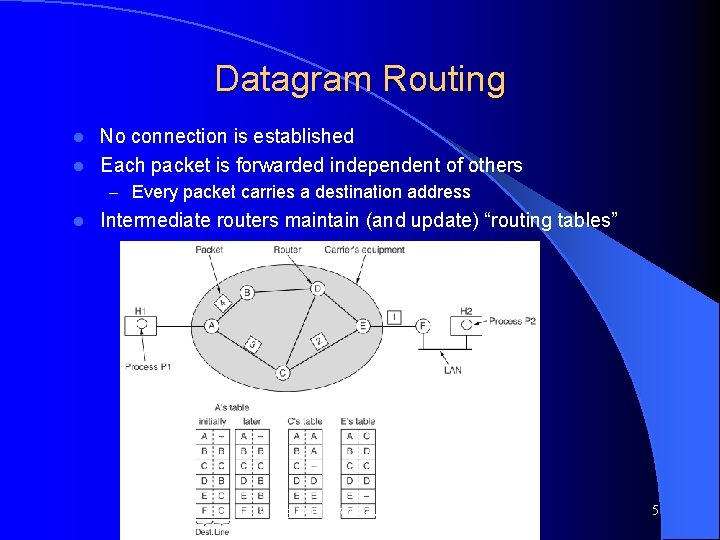
Datagram Routing No connection is established l Each packet is forwarded independent of others l – Every packet carries a destination address l Intermediate routers maintain (and update) “routing tables” Computer Networks, Jan-May 2004 5

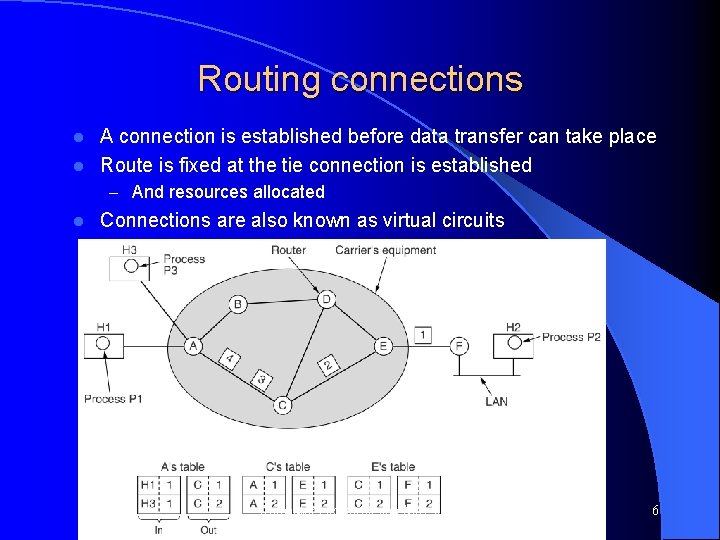
Routing connections A connection is established before data transfer can take place l Route is fixed at the tie connection is established l – And resources allocated l Connections are also known as virtual circuits Computer Networks, Jan-May 2004 6

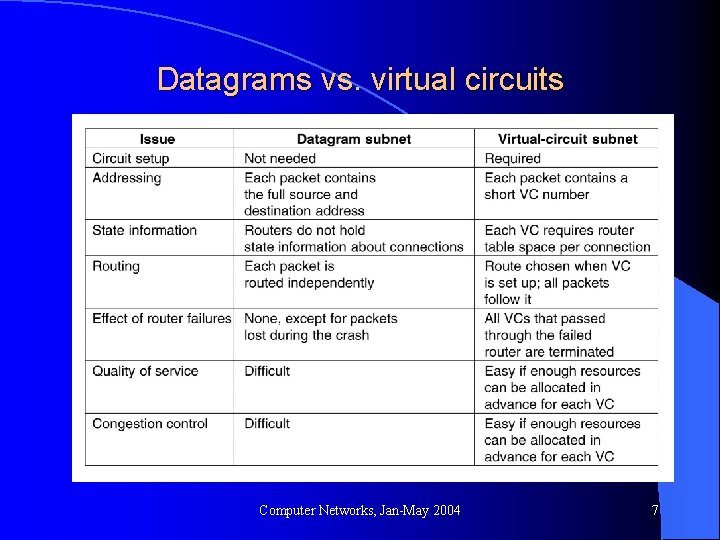
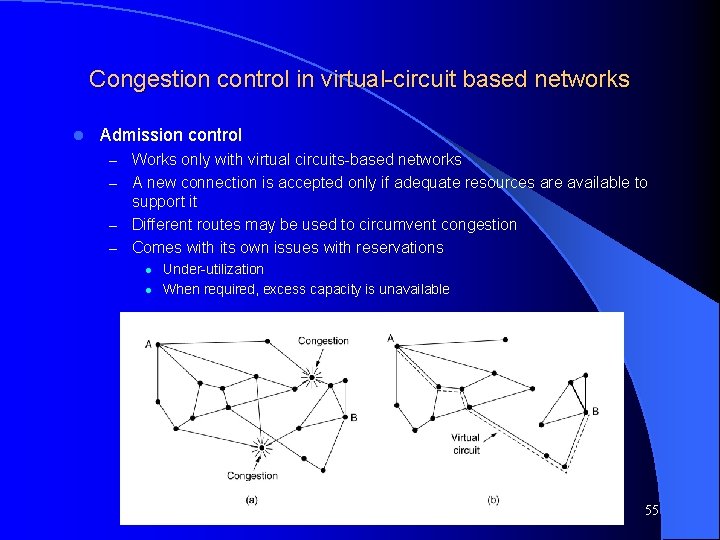
Datagrams vs. virtual circuits Computer Networks, Jan-May 2004 7

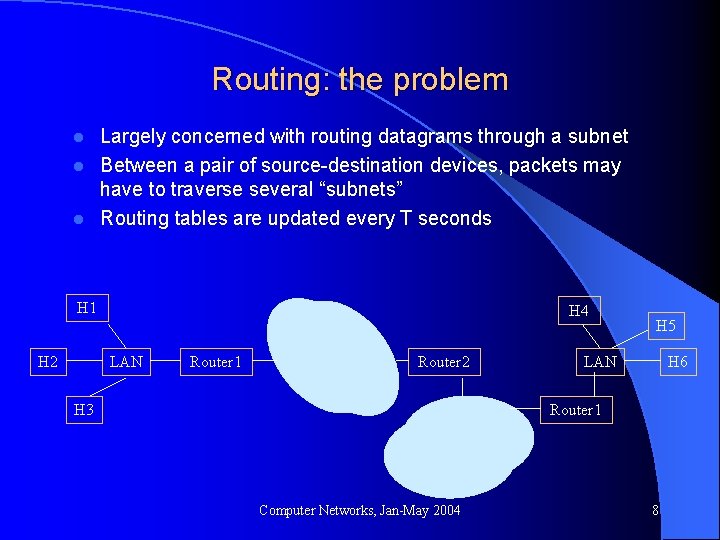
Routing: the problem Largely concerned with routing datagrams through a subnet l Between a pair of source-destination devices, packets may have to traverse several “subnets” l Routing tables are updated every T seconds l H 1 H 2 H 4 LAN Router 1 Router 2 H 3 H 5 LAN H 6 Router 1 Computer Networks, Jan-May 2004 8

Routing: the problem (2) Correct l Simple l Robust l – Address the problems of changing traffic conditions, changes to topology, failures (both transient and permanent) l Stable – In several cases route computation is an iterative process – In such cases the process must converge – Incremental changes in traffic/topology must result in increment changes in routes (I. e. there are no large swings in routes due to increnetal changes) Fair l Optimal l Computer Networks, Jan-May 2004 9

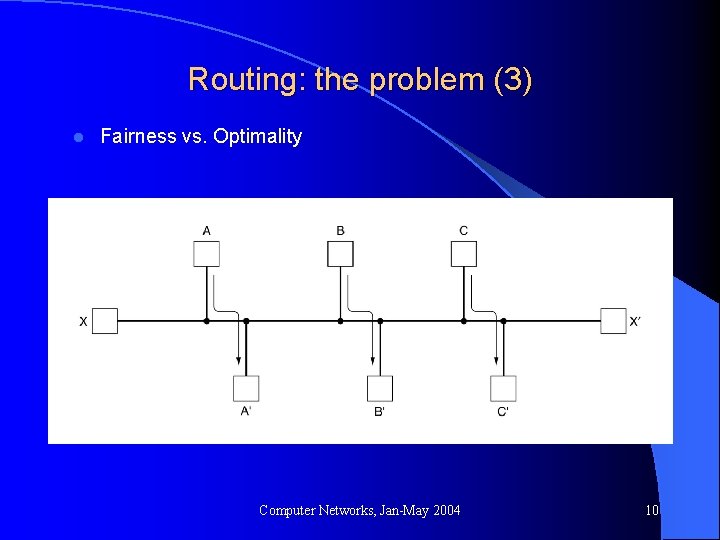
Routing: the problem (3) l Fairness vs. Optimality Computer Networks, Jan-May 2004 10

Routing: the problem (4) l Performance metrics: – Transit delay – Throughput – Number of hops – Security l Delay vs. throughput Computer Networks, Jan-May 2004 11

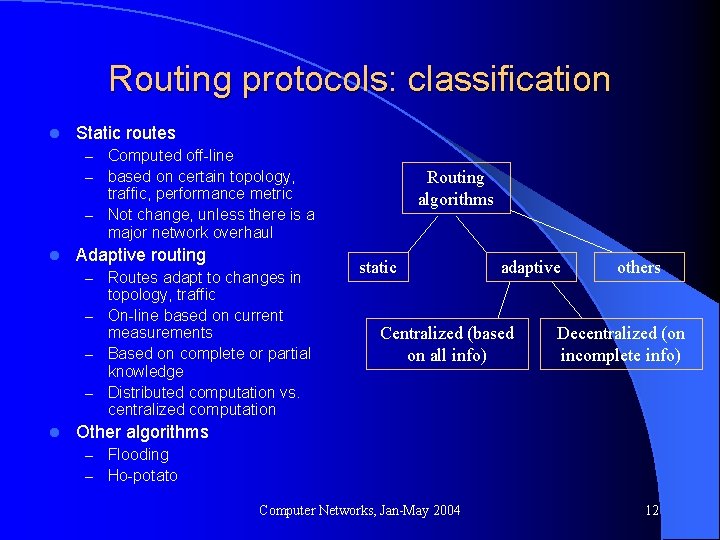
Routing protocols: classification l Static routes – Computed off-line – based on certain topology, Routing algorithms traffic, performance metric – Not change, unless there is a major network overhaul l Adaptive routing – Routes adapt to changes in topology, traffic – On-line based on current measurements – Based on complete or partial knowledge – Distributed computation vs. centralized computation l static adaptive Centralized (based on all info) others Decentralized (on incomplete info) Other algorithms – Flooding – Ho-potato Computer Networks, Jan-May 2004 12

Flooding An incoming packet is sent on all incoming links l Limit the number of hops to avoid infinite loops l – Or, forward packets only once using a packet ID l Or only on selected links (in the right direction) Useful in case some data is to be “broadcasted” l Terribly expensive in terms of resource utilization l But, results in minimum delay l Computer Networks, Jan-May 2004 13

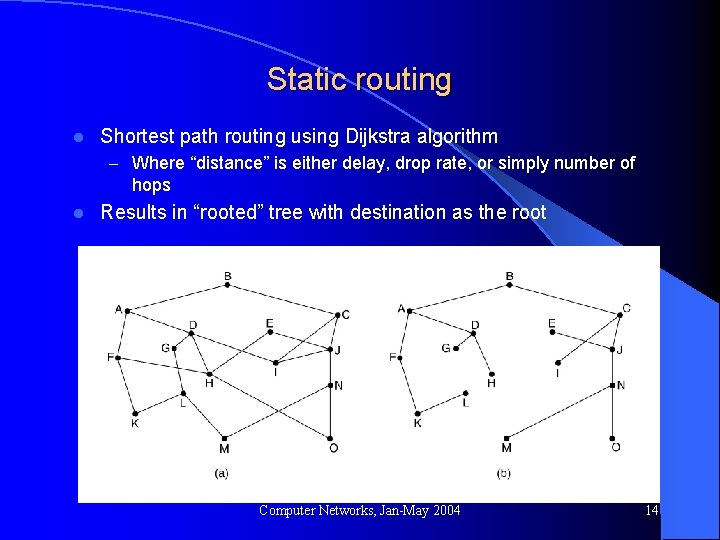
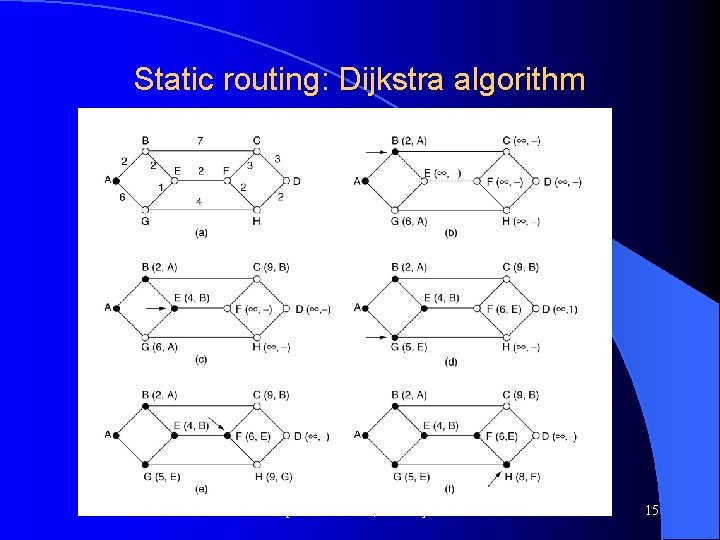
Static routing l Shortest path routing using Dijkstra algorithm – Where “distance” is either delay, drop rate, or simply number of hops l Results in “rooted” tree with destination as the root Computer Networks, Jan-May 2004 14

Static routing: Dijkstra algorithm Computer Networks, Jan-May 2004 15

Adaptive routing Distance-vector routing l Link-state routing l Others l – Hierarchical routing l Standards – OSPF – BGP – MPLS and “traffic engineering” Computer Networks, Jan-May 2004 16

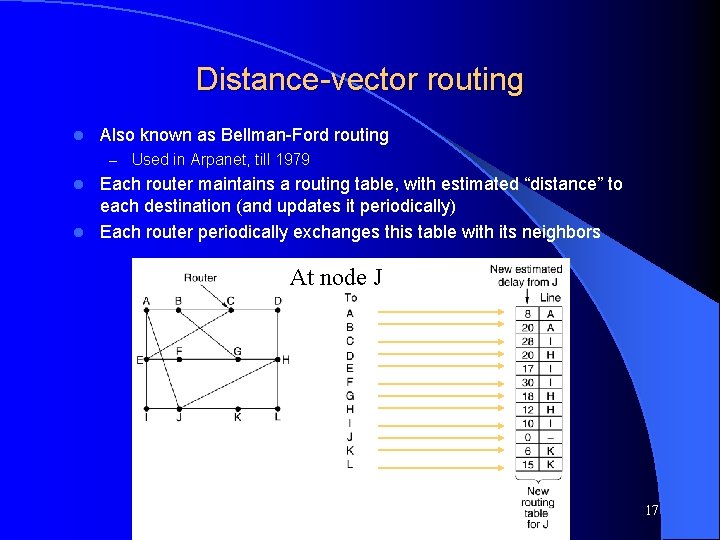
Distance-vector routing l Also known as Bellman-Ford routing – Used in Arpanet, till 1979 Each router maintains a routing table, with estimated “distance” to each destination (and updates it periodically) l Each router periodically exchanges this table with its neighbors l At node J Computer Networks, Jan-May 2004 17

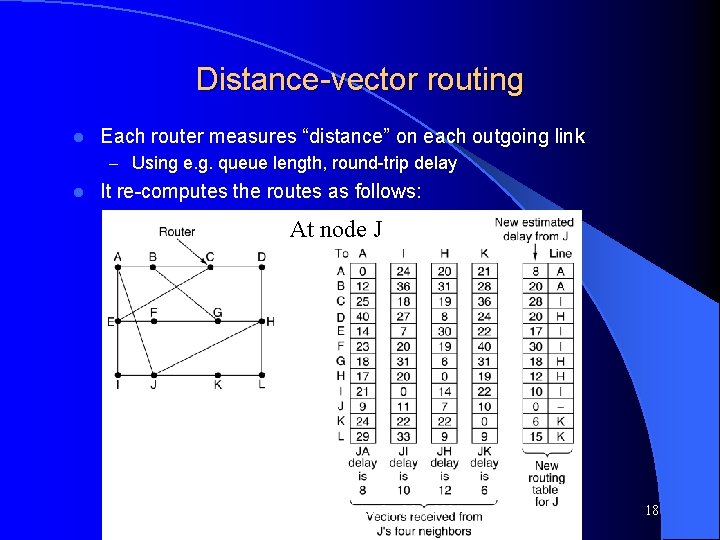
Distance-vector routing l Each router measures “distance” on each outgoing link – Using e. g. queue length, round-trip delay l It re-computes the routes as follows: At node J Computer Networks, Jan-May 2004 18

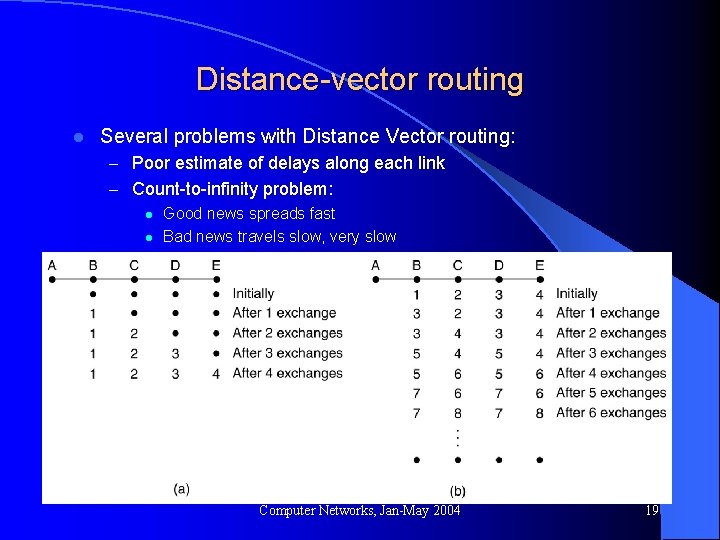
Distance-vector routing l Several problems with Distance Vector routing: – Poor estimate of delays along each link – Count-to-infinity problem: l Good news spreads fast l Bad news travels slow, very slow Computer Networks, Jan-May 2004 19

Link State Routing l Every few seconds (or minutes), each router: – Re-discovers the neighborhood (and their addresses) – Estimate delays (or distances) to each of its neighbors – Construct a packet with above information – Send it to all routers in the network – Collate similar information from all routers in the network – Re-compute the “shortest” routes l Possibly using Dijkstra’s algorithm Computer Networks, Jan-May 2004 20

Two fundamental points l Routing schemes discussed thus far – Belong to “ routes for all source-destination pairs” l As opposed to “on-demand routing”, where a route is determined only if and when needed (as in wire-less networks, MPLS networks) – Belong to schemes where “routing tables” are used to route packets l As opposed to “source-routing”, where each packet carries the route that it must follow Computer Networks, Jan-May 2004 21

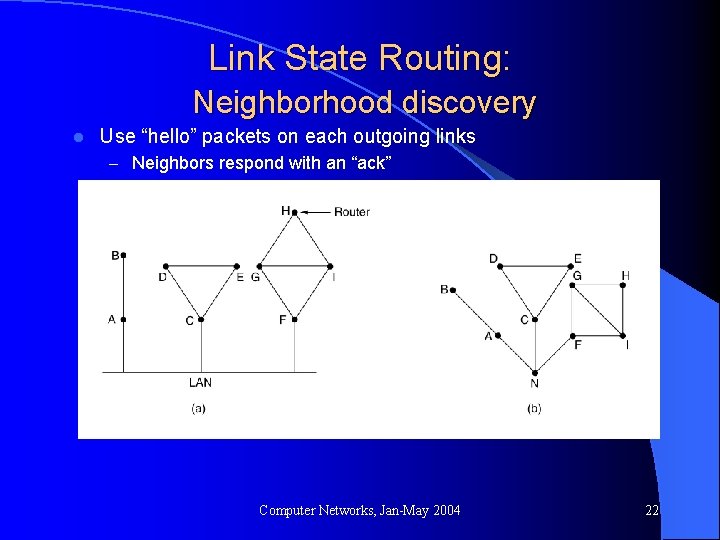
Link State Routing: Neighborhood discovery l Use “hello” packets on each outgoing links – Neighbors respond with an “ack” Computer Networks, Jan-May 2004 22

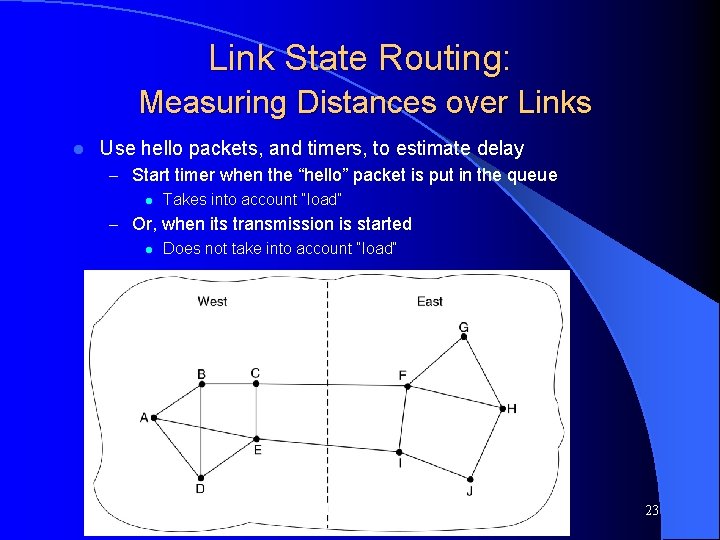
Link State Routing: Measuring Distances over Links l Use hello packets, and timers, to estimate delay – Start timer when the “hello” packet is put in the queue l Takes into account “load” – Or, when its transmission is started l Does not take into account “load” Computer Networks, Jan-May 2004 23

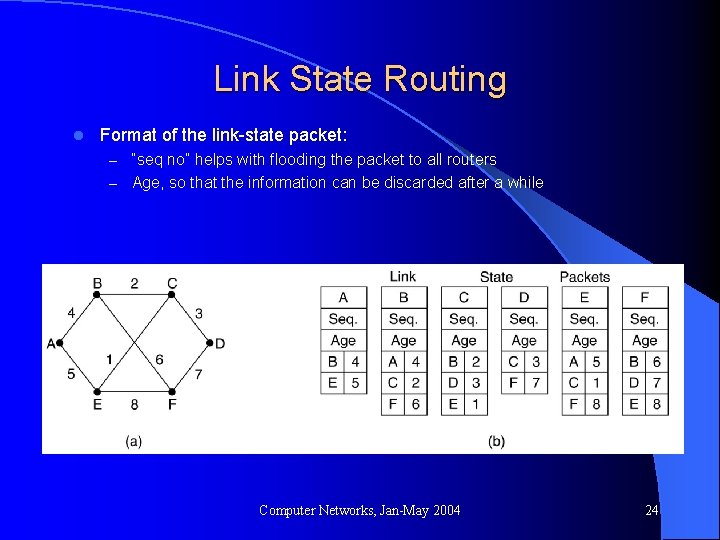
Link State Routing l Format of the link-state packet: – “seq no” helps with flooding the packet to all routers – Age, so that the information can be discarded after a while Computer Networks, Jan-May 2004 24

Link State Routing l Packet processing: – Re-sequencing of link-state info packets l Ignore packets with “lower” sequence numbers (as “stale”) – What if a packet is lost? l No big deal – Other problems l What if a sequence number is corrupted by noise? And this fact goes undetected l What if a router re-boots? – Each packet has an associated “age” in seconds (say 60 sec) l “age” is decremented every second by intermediate routers, and by the router that caches it l processing starts afresh if age 0 Computer Networks, Jan-May 2004 25

Link State Routing l Route computation: – Note every router has identical information – Use Dijkstra’s shortest path algorithm l Problems: – Stale information – Incorrect information – Incomplete information – Inconsistent routes loops Computer Networks, Jan-May 2004 26

Link State Routing l Standards – IS-IS l Used with variety of protocols, including IP, IPX – OSPF l An Internet RFC Computer Networks, Jan-May 2004 27

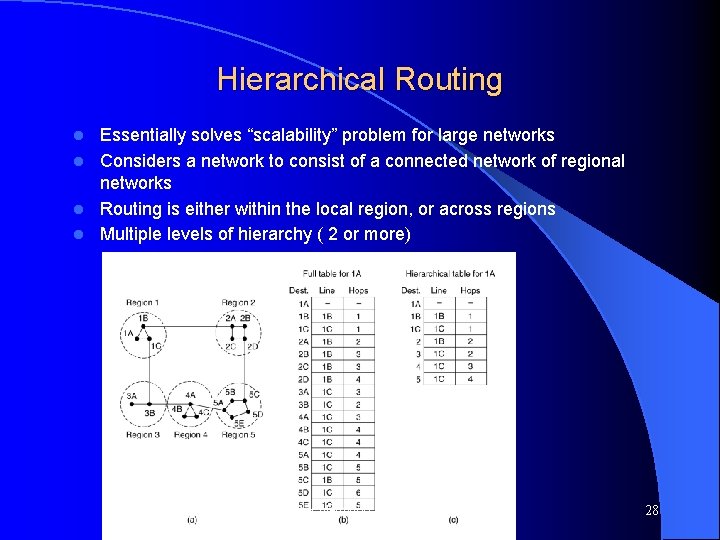
Hierarchical Routing Essentially solves “scalability” problem for large networks l Considers a network to consist of a connected network of regional networks l Routing is either within the local region, or across regions l Multiple levels of hierarchy ( 2 or more) l Computer Networks, Jan-May 2004 28

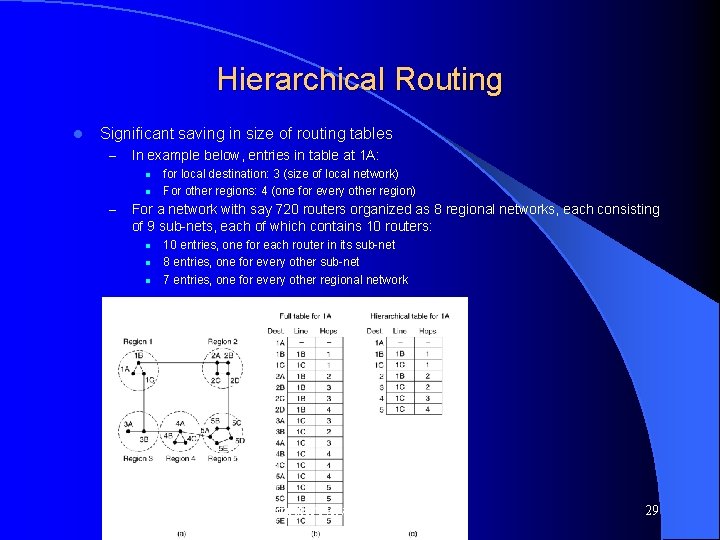
Hierarchical Routing l Significant saving in size of routing tables – In example below, entries in table at 1 A: l l – for local destination: 3 (size of local network) For other regions: 4 (one for every other region) For a network with say 720 routers organized as 8 regional networks, each consisting of 9 sub-nets, each of which contains 10 routers: l l l 10 entries, one for each router in its sub-net 8 entries, one for every other sub-net 7 entries, one for every other regional network Computer Networks, Jan-May 2004 29

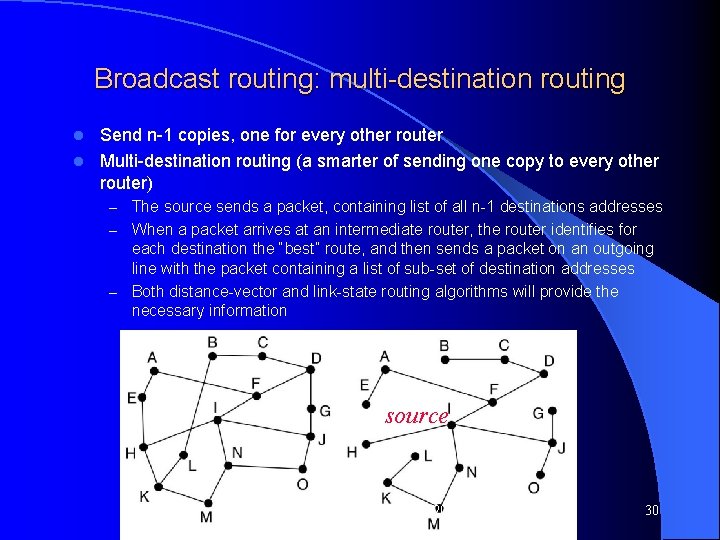
Broadcast routing: multi-destination routing Send n-1 copies, one for every other router l Multi-destination routing (a smarter of sending one copy to every other router) l – The source sends a packet, containing list of all n-1 destinations addresses – When a packet arrives at an intermediate router, the router identifies for each destination the “best” route, and then sends a packet on an outgoing line with the packet containing a list of sub-set of destination addresses – Both distance-vector and link-state routing algorithms will provide the necessary information source Computer Networks, Jan-May 2004 30

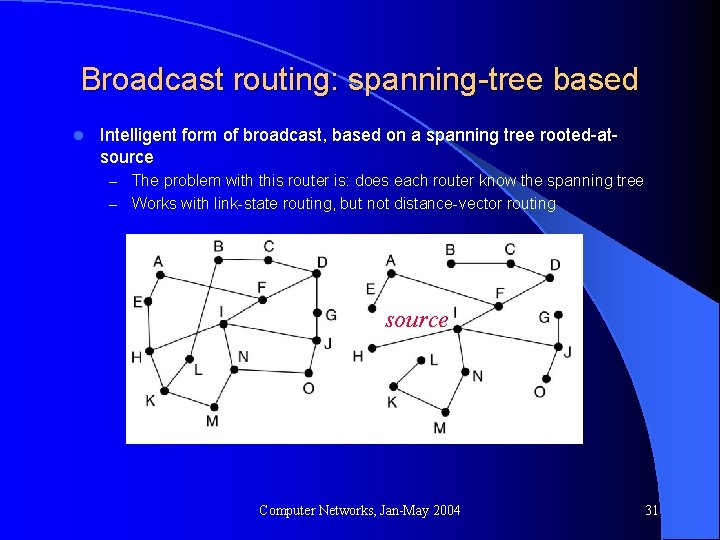
Broadcast routing: spanning-tree based l Intelligent form of broadcast, based on a spanning tree rooted-atsource – The problem with this router is: does each router know the spanning tree – Works with link-state routing, but not distance-vector routing source Computer Networks, Jan-May 2004 31

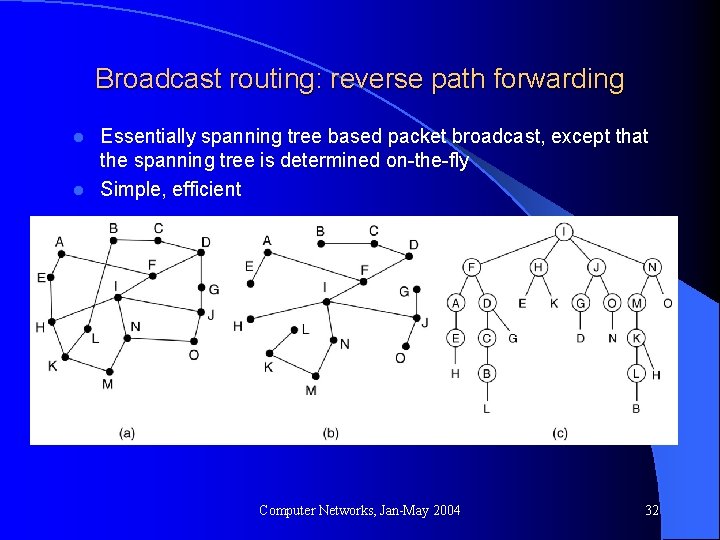
Broadcast routing: reverse path forwarding Essentially spanning tree based packet broadcast, except that the spanning tree is determined on-the-fly l Simple, efficient l Computer Networks, Jan-May 2004 32

Multicast routing l Spanning tree vs. multicast tree l The latter includes nodes that are required to forward packets to all member nodes Multi-destination routing to all K-1 members – – – When a packet arrives at an intermediate router, the router identifies for each destination the “best” route, and then sends a packet on an outgoing line with the packet containing a list of sub-set of destination addresses Both distance-vector and link-state routing algorithms will provide the necessary information Computer Networks, Jan-May 2004 33

Routing in peer-to-peer ad hoc networks l What is different about routing in ad hoc networks – Routing environment l Wireless, mobile hosts resulting in: – Greater probability of link, node failure – Changing topology – Frequent route changes l l Every device is a potential router Potentially different goals: – Stability of routes – Power consumption Computer Networks, Jan-May 2004 34

Classification of routing protocols Multicast routing l Unicast routing l – Proactive protocols l l Where routes between every pair of nodes are computed a-priori Examples: distance-vector, link-state rouitng in IP networks Advantage: reduced latency Dis-advantage: excessive overhead due to route computation – Reactive protocols l l Routes are determined between a pair of devices only when required As in MPLS networks Advantage: overhead is minimized Dis-advantage: Increased latency – Example routing protocols for ad hoc networks l l Flooding Dynamic source routing AODV … Computer Networks, Jan-May 2004 35

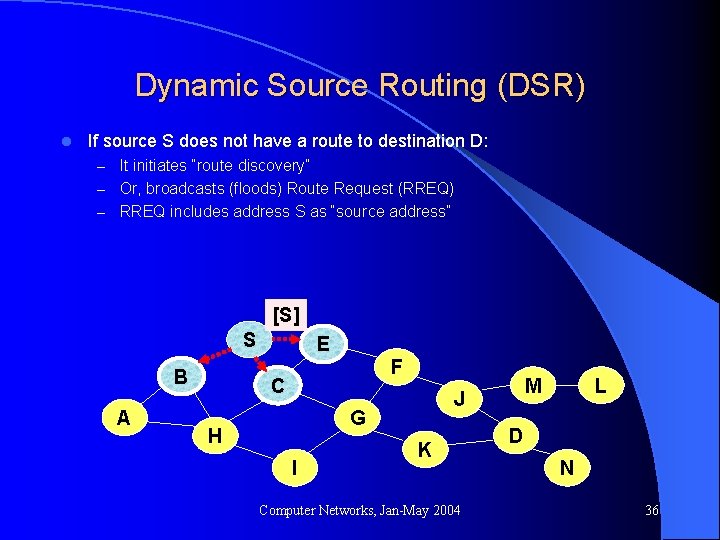
Dynamic Source Routing (DSR) l If source S does not have a route to destination D: – It initiates “route discovery” – Or, broadcasts (floods) Route Request (RREQ) – RREQ includes address S as “source address” [S] S B A E F C G H I M J K Computer Networks, Jan-May 2004 L D N 36

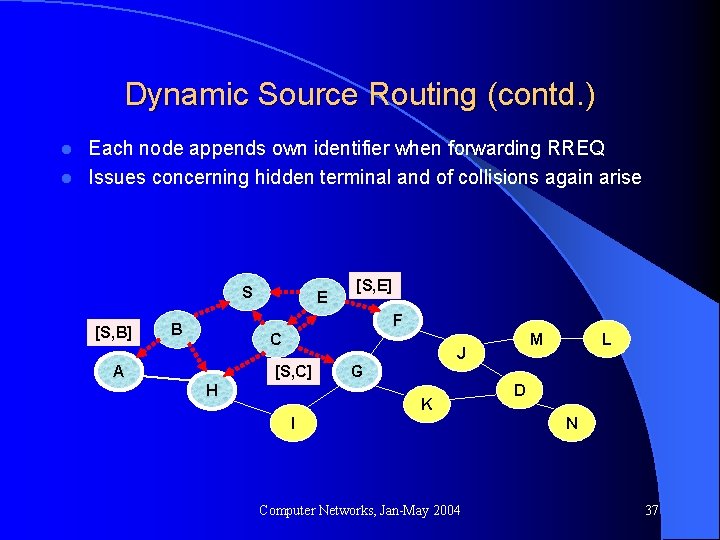
Dynamic Source Routing (contd. ) Each node appends own identifier when forwarding RREQ l Issues concerning hidden terminal and of collisions again arise l S [S, B] E [S, E] F B C [S, C] A M J H L G K I Computer Networks, Jan-May 2004 D N 37

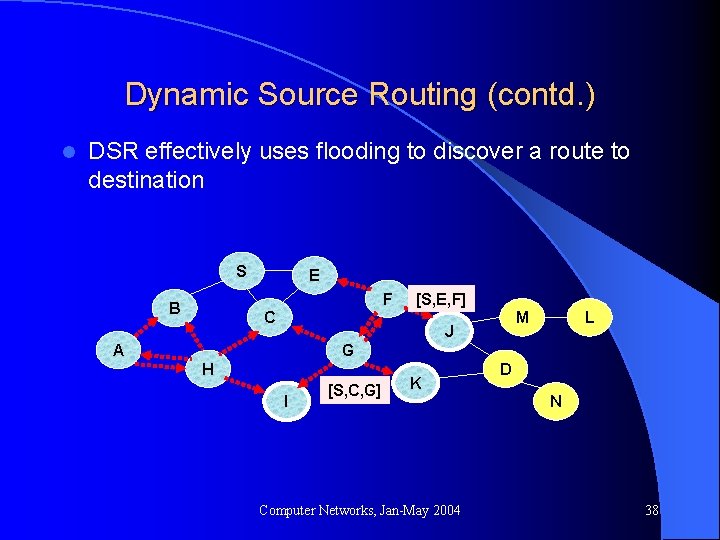
Dynamic Source Routing (contd. ) l DSR effectively uses flooding to discover a route to destination S E F B [S, E, F] C M J A L G H I [S, C, G] K Computer Networks, Jan-May 2004 D N 38

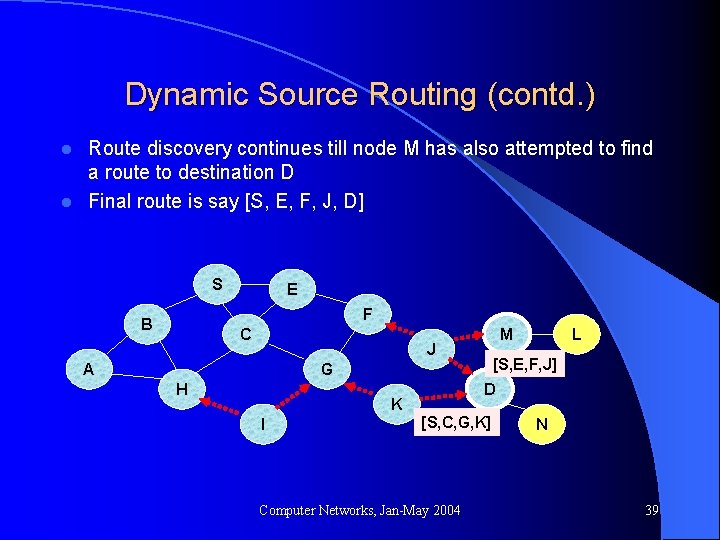
Dynamic Source Routing (contd. ) Route discovery continues till node M has also attempted to find a route to destination D l Final route is say [S, E, F, J, D] l S E F B C M J A [S, E, F, J] G H D K I L [S, C, G, K] Computer Networks, Jan-May 2004 N 39

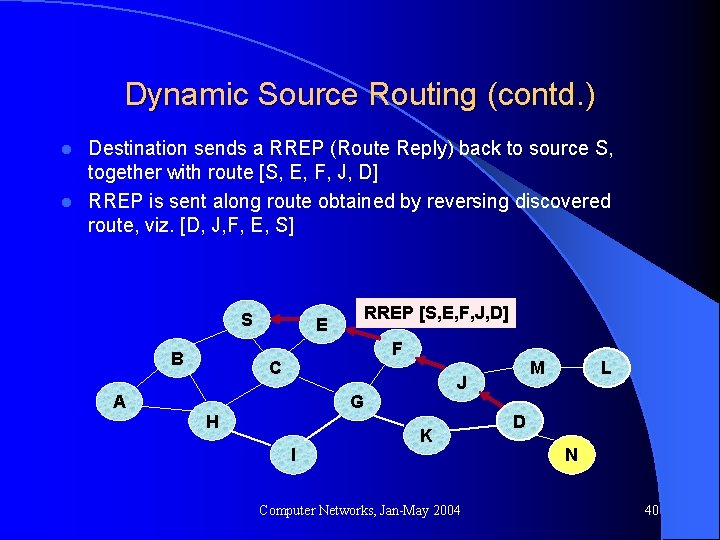
Dynamic Source Routing (contd. ) Destination sends a RREP (Route Reply) back to source S, together with route [S, E, F, J, D] l RREP is sent along route obtained by reversing discovered route, viz. [D, J, F, E, S] l S B A E RREP [S, E, F, J, D] F C J G H I M K Computer Networks, Jan-May 2004 L D N 40

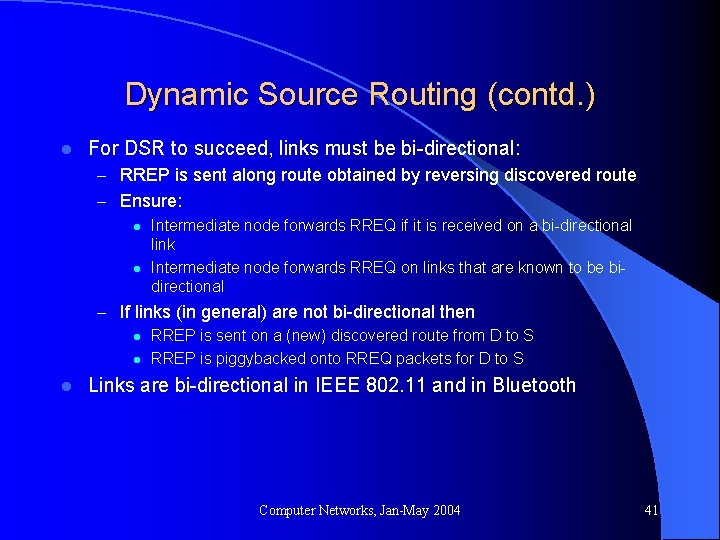
Dynamic Source Routing (contd. ) l For DSR to succeed, links must be bi-directional: – RREP is sent along route obtained by reversing discovered route – Ensure: l Intermediate node forwards RREQ if it is received on a bi-directional link l Intermediate node forwards RREQ on links that are known to be bidirectional – If links (in general) are not bi-directional then l RREP is sent on a (new) discovered route from D to S l RREP is piggybacked onto RREQ packets for D to S l Links are bi-directional in IEEE 802. 11 and in Bluetooth Computer Networks, Jan-May 2004 41

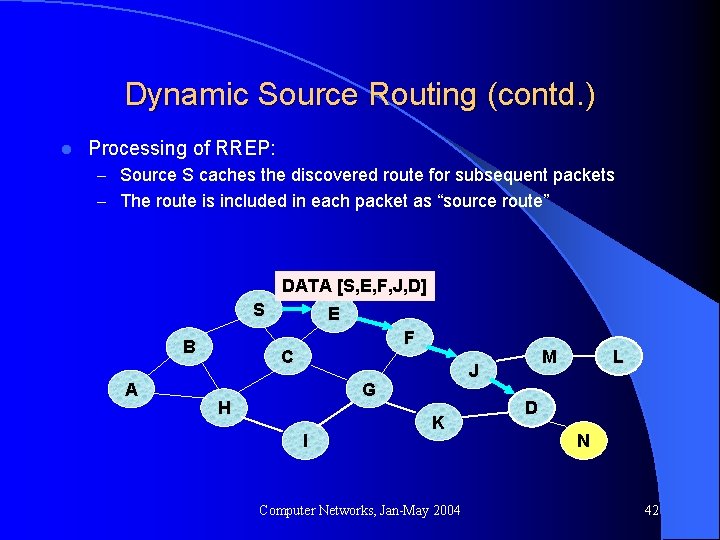
Dynamic Source Routing (contd. ) l Processing of RREP: – Source S caches the discovered route for subsequent packets – The route is included in each packet as “source route” DATA [S, E, F, J, D] S B A E F C J G H I M K Computer Networks, Jan-May 2004 L D N 42

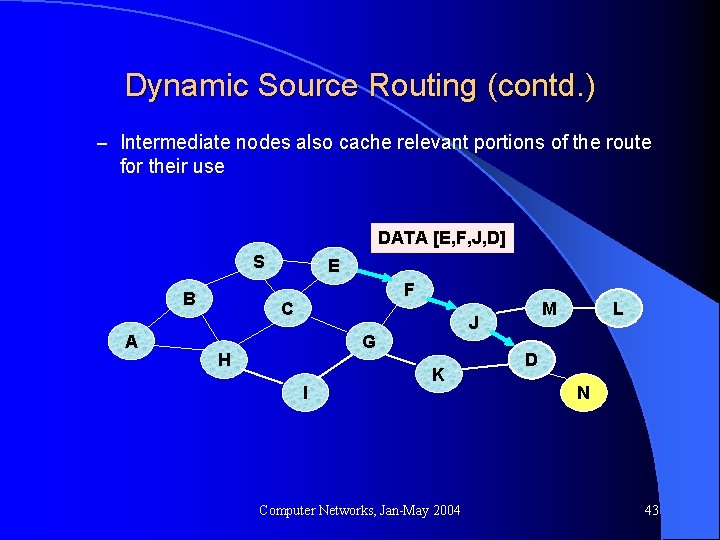
Dynamic Source Routing (contd. ) – Intermediate nodes also cache relevant portions of the route for their use DATA [E, F, J, D] S B A E F C J G H I M K Computer Networks, Jan-May 2004 L D N 43

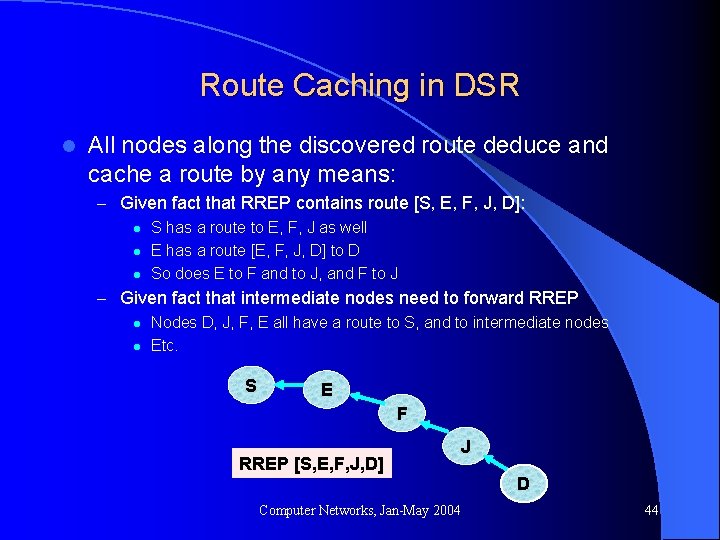
Route Caching in DSR l All nodes along the discovered route deduce and cache a route by any means: – Given fact that RREP contains route [S, E, F, J, D]: l S has a route to E, F, J as well l E has a route [E, F, J, D] to D l So does E to F and to J, and F to J – Given fact that intermediate nodes need to forward RREP l Nodes D, J, F, E all have a route to S, and to intermediate nodes l Etc. S E F RREP [S, E, F, J, D] J D Computer Networks, Jan-May 2004 44

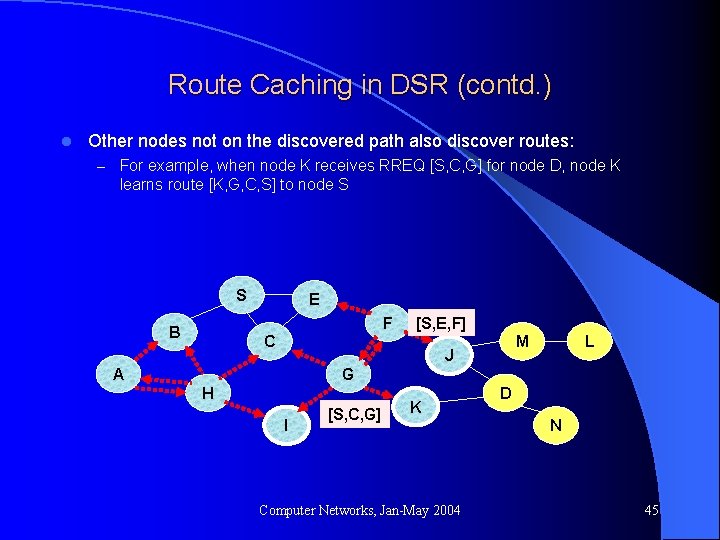
Route Caching in DSR (contd. ) l Other nodes not on the discovered path also discover routes: – For example, when node K receives RREQ [S, C, G] for node D, node K learns route [K, G, C, S] to node S S E F B [S, E, F] C M J A L G H I [S, C, G] K Computer Networks, Jan-May 2004 D N 45

Route Caching in DSR (contd. ) l Cached routes are used: – To route packets – To obtain alternate routes when a route in use is broken l speed up recovery – To respond to RREQ if a route is cached l speed up route discovery l limit propagation of RREQ Computer Networks, Jan-May 2004 46

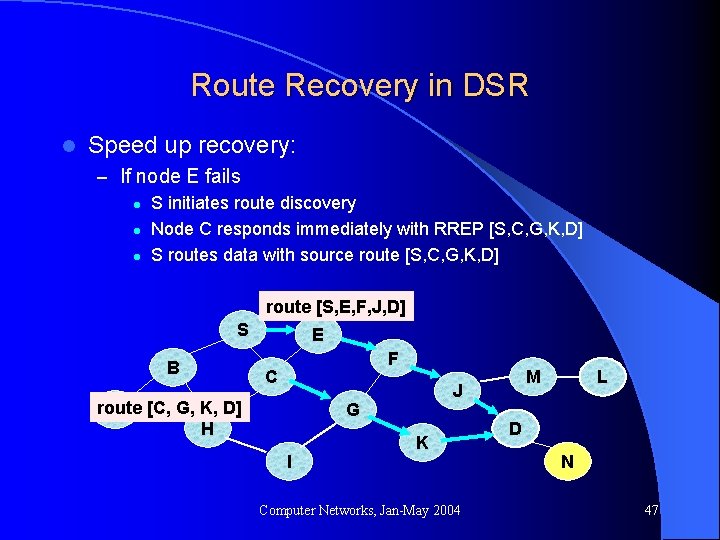
Route Recovery in DSR l Speed up recovery: – If node E fails l S initiates route discovery l Node C responds immediately with RREP [S, C, G, K, D] l S routes data with source route [S, C, G, K, D] route [S, E, F, J, D] S B E F C route A [C, G, K, D] H J G I M K Computer Networks, Jan-May 2004 L D N 47

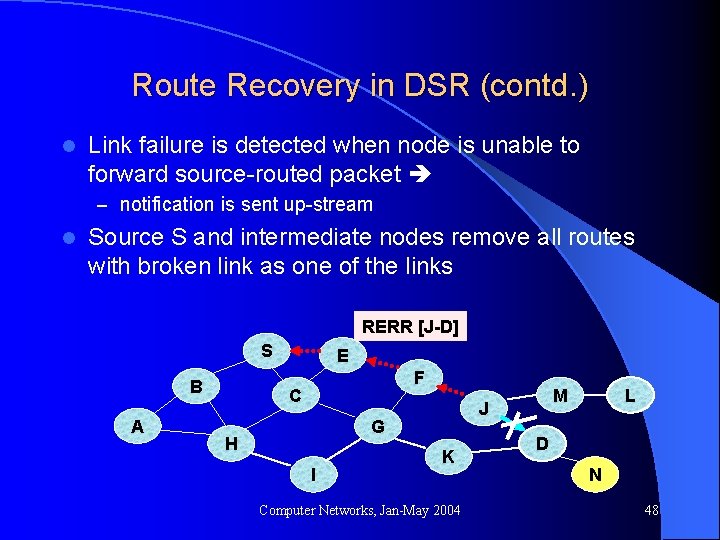
Route Recovery in DSR (contd. ) l Link failure is detected when node is unable to forward source-routed packet – notification is sent up-stream l Source S and intermediate nodes remove all routes with broken link as one of the links RERR [J-D] S B A E F C G H I M J K Computer Networks, Jan-May 2004 L D N 48

Route Caching in DSR (contd. ) l Cached routes may become invalid due to changes in topology (or mobility) – Stale, invalid cache pollute neighboring caches – Impact on performance l No route is available l Route is poor l Need to implement policy to “purge” stale/invalid cache entries Computer Networks, Jan-May 2004 49

DSR: pros and cons l Pros: – On demand routing – Caching speeds up route discovery – Route discovery uses flooding discovers minimum delay routes – Routing tables are not maintained l Cons: – Requires entire route to be included in packet header – Requires symmetric links – Inherits all problems associated with flooding (too many RREQs, collisions, hidden terminals) – Stale, invalid cache Computer Networks, Jan-May 2004 50

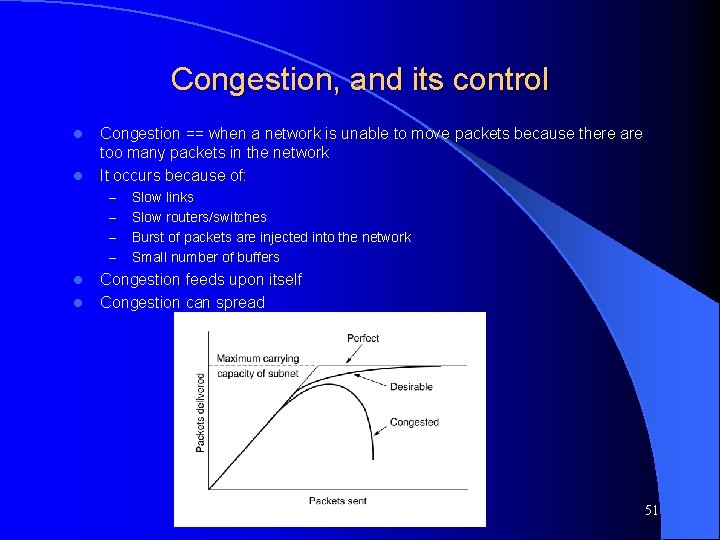
Congestion, and its control l l Congestion == when a network is unable to move packets because there are too many packets in the network It occurs because of: – – l l Slow links Slow routers/switches Burst of packets are injected into the network Small number of buffers Congestion feeds upon itself Congestion can spread Computer Networks, Jan-May 2004 51

Congestion, and its control l Difference between “flow control” and “congestion control” – Congestion has to do with networks carrying capacity l Flow control has to do with a destination node having to receive and process incoming packets – Congestion is a global issue l l Flow control is an issue pertaining to communication between a pair of devices Yet, methods used for flow control and congestion control CAN be similar Computer Networks, Jan-May 2004 52

Congestion control l Open loop control – Good design l l Accept new traffic carefully Discard traffic Schedule packet transmission Allocate buffers – Attempted in all protocol layers l Closed loop control – Closely monitor congestion l l Queue lengths packets dropped due to unavailability of buffers Link utilization Transit delay, and jitter – Exchange information with other nodes (particularly those responsible for taking actions) l adds to congestion – Adjust network operation (re-schedule, re-route, drop packets, block traffic, …) Computer Networks, Jan-May 2004 53

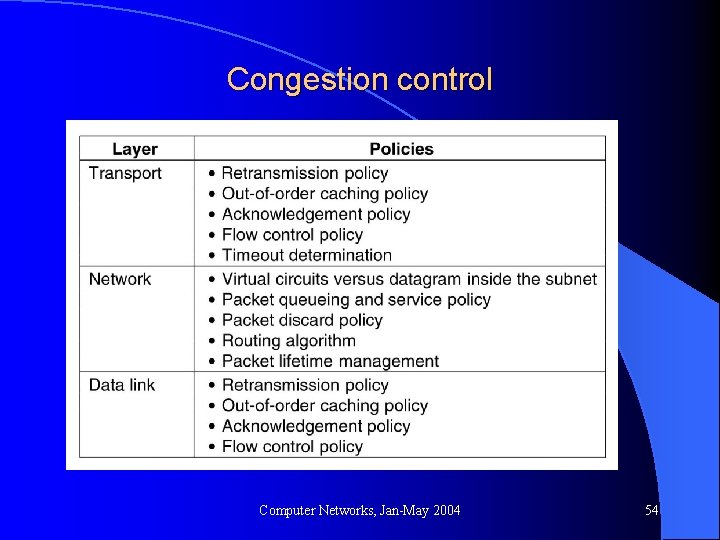
Congestion control Computer Networks, Jan-May 2004 54

Congestion control in virtual-circuit based networks l Admission control – Works only with virtual circuits-based networks – A new connection is accepted only if adequate resources are available to support it – Different routes may be used to circumvent congestion – Comes with its own issues with reservations l l Under-utilization When required, excess capacity is unavailable Computer Networks, Jan-May 2004 55

Congestion control in datagram-based networks Each node is responsible for monitoring, communicating status, and controlling it l Monitor congestion by measuring: l – Queue length, channel utilization, delays, etc. – Usually work with averages l l l Averaging interval? Averaging process? E. g. Signaling congestion to source – Implicitly: l l Set a “congestion bit” in packet sent to destination, which in turn sets the bit in an ACK Simply drop the packet, and let source discover that fact, as with – Drop-tail – RED – Explicitly: l Send a “choke” packet to source Computer Networks, Jan-May 2004 56

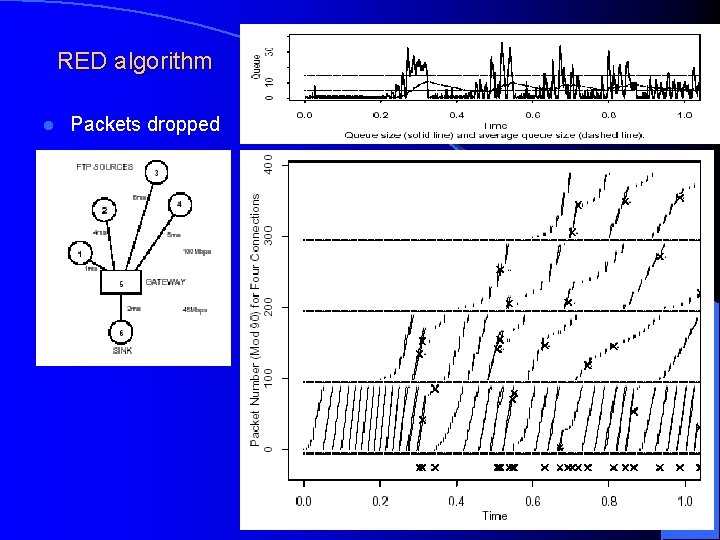
Random Early Detection (RED) algorithm-based congestion avoidance l RED algorithm – Developed by Sally Floyd and Van Jacobson, 1993 – Used extensively in Internet l Design goals: – Avoid congestion, rather than remove congestion early detect l Do so by ensuring that the queue does not overflow – Also ensures that the queuing delay is small – Avoid global and synchronous pull-back of traffic l Thus ensures that throughput remains high – Not be biased against bursty traffic l Basic idea – Act upon when average queue length begins to grow – Randomly “mark” a packet, in the hope that TCP connection will slow down l In the present context “mark” == ”drop” Computer Networks, Jan-May 2004 57

Random Early Detection (RED) algorithm Computer Networks, Jan-May 2004 58

Random Early Detection (RED) algorithm Computer Networks, Jan-May 2004 59

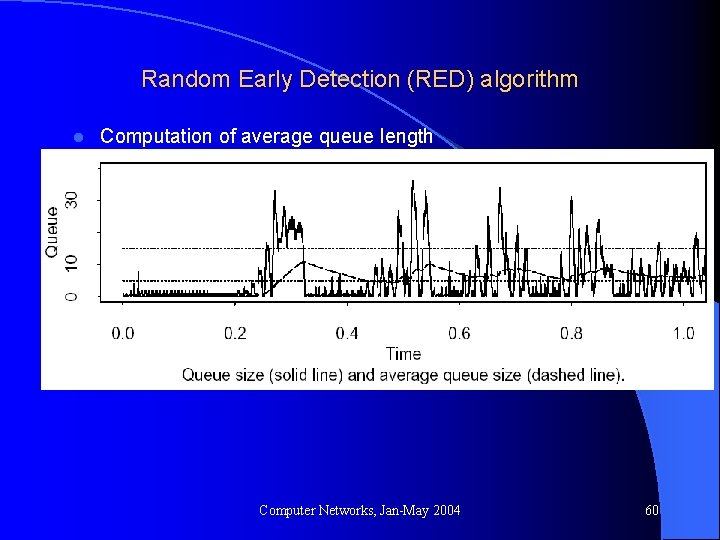
Random Early Detection (RED) algorithm l Computation of average queue length Computer Networks, Jan-May 2004 60

RED algorithm l Packets dropped Computer Networks, Jan-May 2004 61

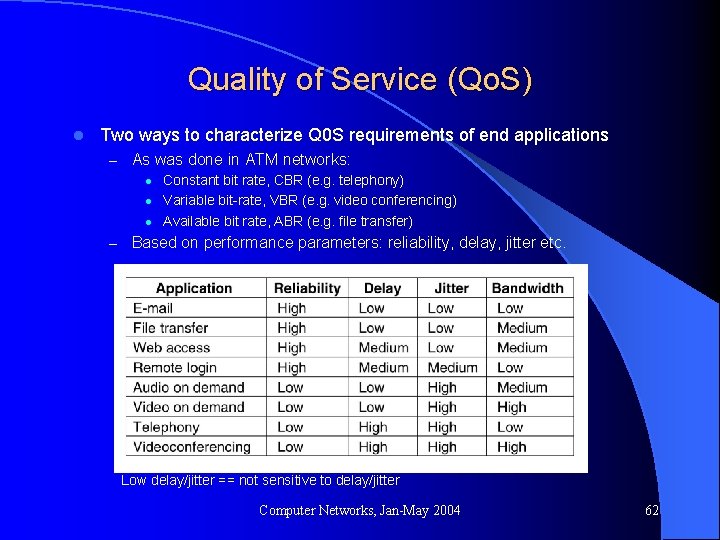
Quality of Service (Qo. S) l Two ways to characterize Q 0 S requirements of end applications – As was done in ATM networks: l l l Constant bit rate, CBR (e. g. telephony) Variable bit-rate, VBR (e. g. video conferencing) Available bit rate, ABR (e. g. file transfer) – Based on performance parameters: reliability, delay, jitter etc. Low delay/jitter == not sensitive to delay/jitter Computer Networks, Jan-May 2004 62

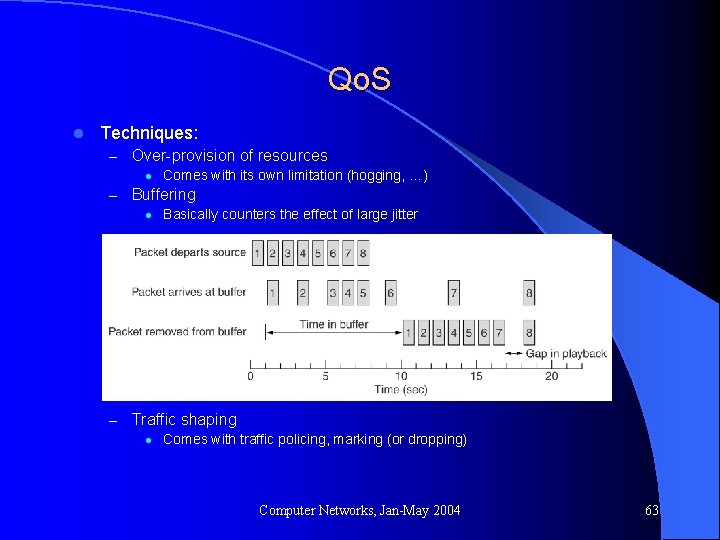
Qo. S l Techniques: – Over-provision of resources l Comes with its own limitation (hogging, …) – Buffering l Basically counters the effect of large jitter – Traffic shaping l Comes with traffic policing, marking (or dropping) Computer Networks, Jan-May 2004 63

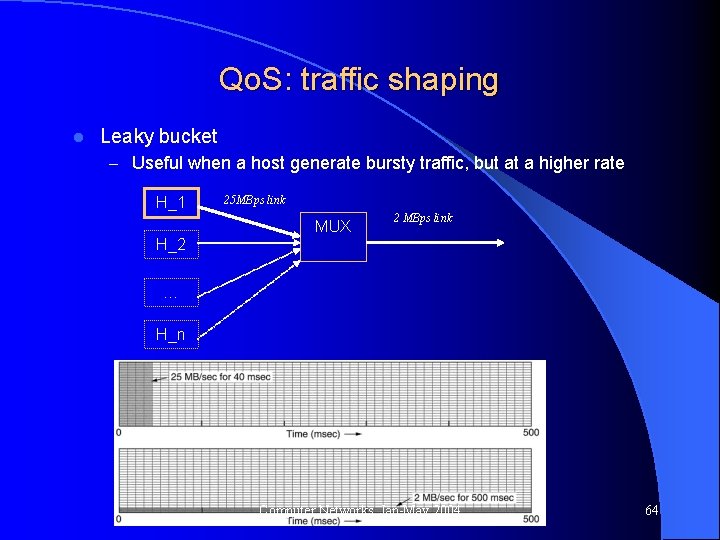
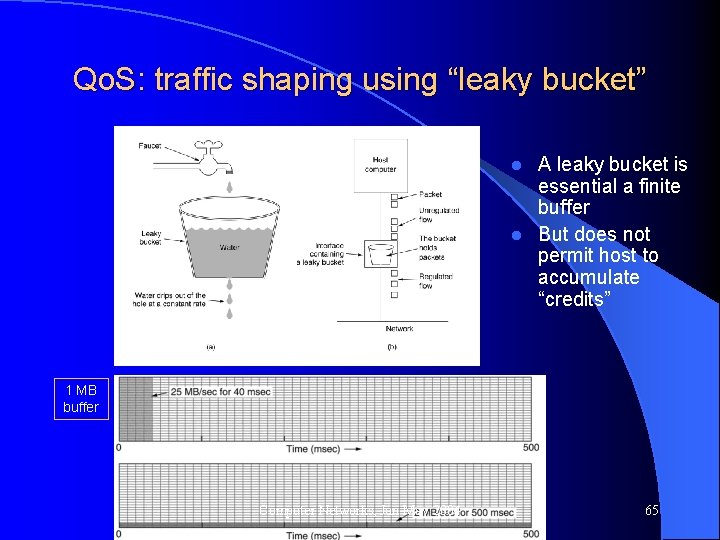
Qo. S: traffic shaping l Leaky bucket – Useful when a host generate bursty traffic, but at a higher rate H_1 25 MBps link MUX 2 MBps link H_2 … H_n Computer Networks, Jan-May 2004 64

Qo. S: traffic shaping using “leaky bucket” A leaky bucket is essential a finite buffer l But does not permit host to accumulate “credits” l 1 MB buffer Computer Networks, Jan-May 2004 65

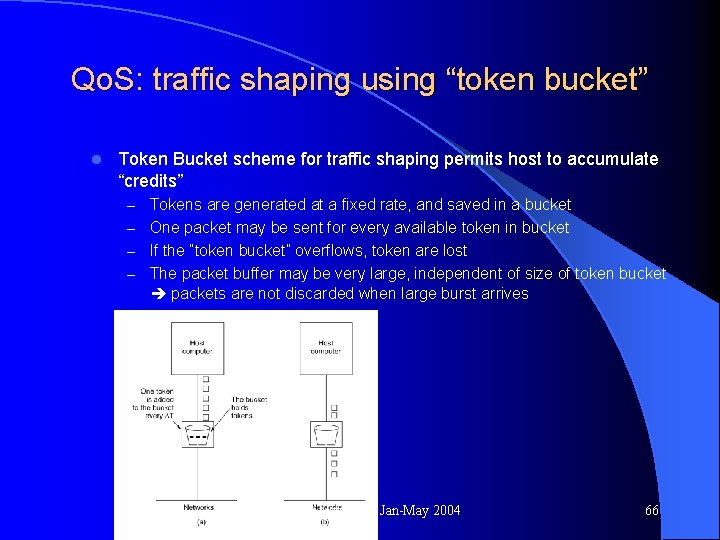
Qo. S: traffic shaping using “token bucket” l Token Bucket scheme for traffic shaping permits host to accumulate “credits” – Tokens are generated at a fixed rate, and saved in a bucket – One packet may be sent for every available token in bucket – If the “token bucket” overflows, token are lost – The packet buffer may be very large, independent of size of token bucket packets are not discarded when large burst arrives Computer Networks, Jan-May 2004 66

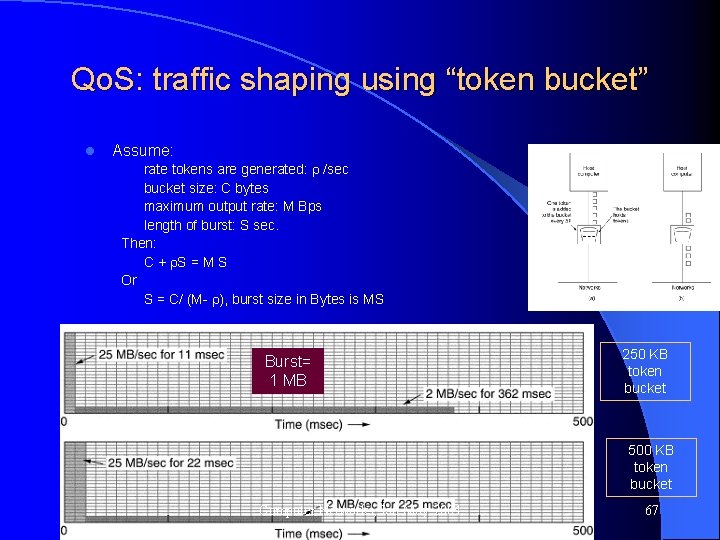
Qo. S: traffic shaping using “token bucket” l Assume: rate tokens are generated: /sec bucket size: C bytes maximum output rate: M Bps length of burst: S sec. Then: C + S = M S Or S = C/ (M- ), burst size in Bytes is MS Burst= 1 MB 250 KB token bucket 500 KB token bucket Computer Networks, Jan-May 2004 67

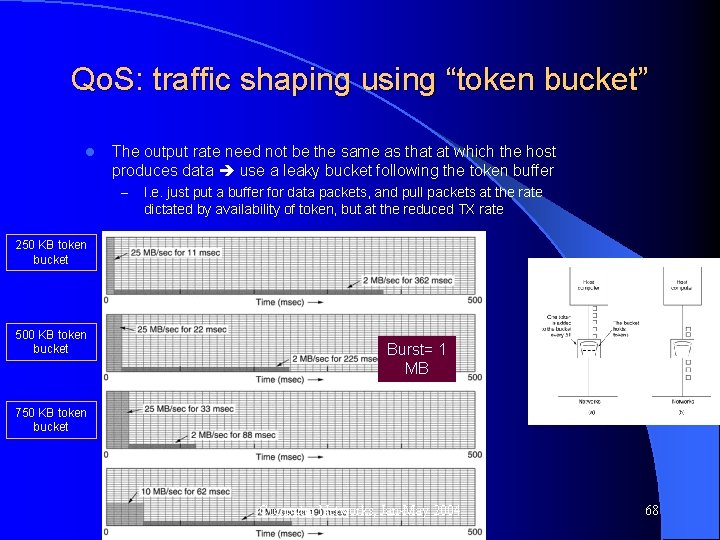
Qo. S: traffic shaping using “token bucket” l The output rate need not be the same as that at which the host produces data use a leaky bucket following the token buffer – I. e. just put a buffer for data packets, and pull packets at the rate dictated by availability of token, but at the reduced TX rate 250 KB token bucket 500 KB token bucket Burst= 1 MB 750 KB token bucket Computer Networks, Jan-May 2004 68

Resource Reservation l Resources need to be reserved in order to guarantee committed Qo. S – Bandwidth l l Easy enough to determine Need to keep some spare bandwidth to handle bursts and “best-effort” traffic – Buffer space l l somewhat difficult, unless “burst length” is specified else estimate using avg_q_length = /( - ), where and are respectively arrival and service rates – Service rate is determined by available bandwidth & CPU capacity – CPU cycles l l l Even more difficult Router characterized by routing capacity, X packets/sec Need to specify required processing capacity in terms of Y packets/sec – May be calculated using peak & avg data rate, burst size, min and max packet size Computer Networks, Jan-May 2004 69

Admission control l If resources are to be reserved, each “flow” needs to be “admitted” using an “admission control” scheme – Qo. S requirements for each flow is a must (e. g. – Control based on available resources, viz. -a-viz. resources required by a flow or the aggregate of flows – Yet there must be spare capacity Computer Networks, Jan-May 2004 70

Routing Ensure that each “flow” or an “aggregate” is routed suitably, so that Qo. S constraints can be met l MPLS is one way to route l Computer Networks, Jan-May 2004 71

Routing (using MPLS) Has been around for decades l Uses “maximal prefix match” to route packets l – l Slows down routing Routing is based on destination IP address – But, one may prefer routes based on Qo. S, security, etc. Computer Networks, Jan-May 2004 72

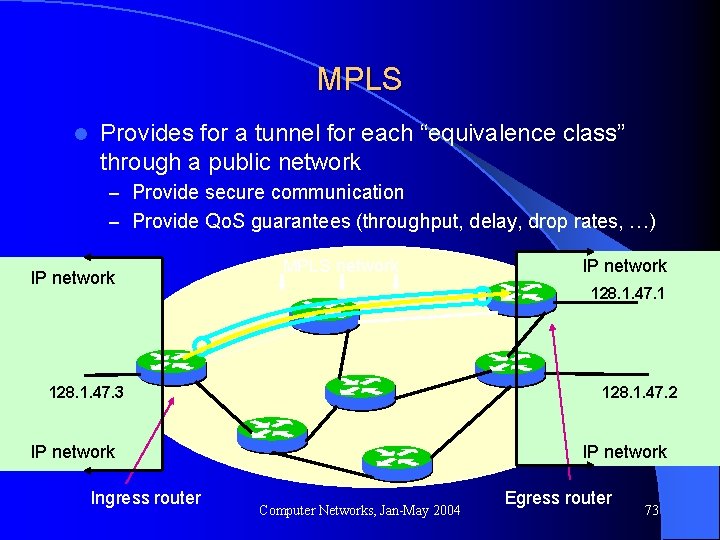
MPLS l Provides for a tunnel for each “equivalence class” through a public network – Provide secure communication – Provide Qo. S guarantees (throughput, delay, drop rates, …) IP network MPLS network 128. 1. 47. 1 128. 1. 47. 3 128. 1. 47. 2 IP network Ingress router IP network Computer Networks, Jan-May 2004 Egress router 73

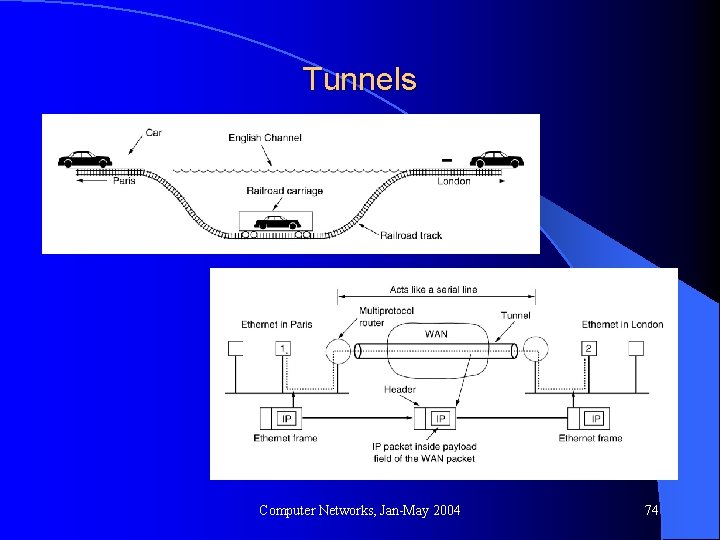
Tunnels Computer Networks, Jan-May 2004 74

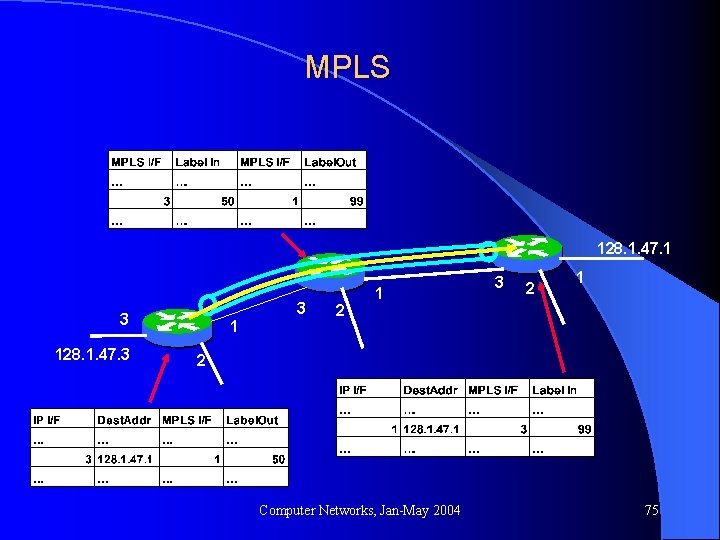
MPLS 128. 1. 47. 1 3 3 128. 1. 47. 3 1 2 1 3 2 1 2 Computer Networks, Jan-May 2004 75

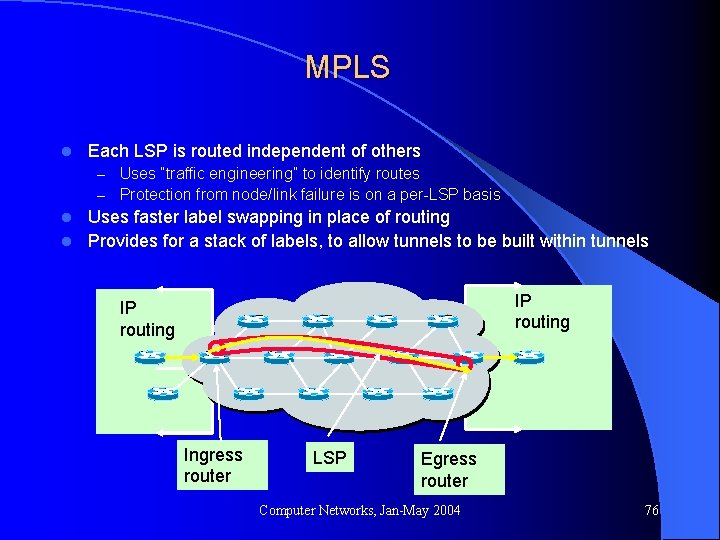
MPLS l Each LSP is routed independent of others – Uses “traffic engineering” to identify routes – Protection from node/link failure is on a per-LSP basis Uses faster label swapping in place of routing l Provides for a stack of labels, to allow tunnels to be built within tunnels l IP routing Ingress router LSP Egress router Computer Networks, Jan-May 2004 76

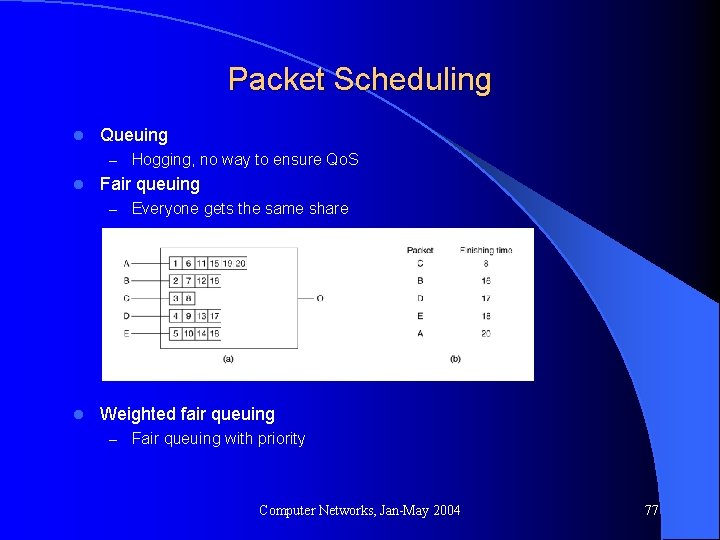
Packet Scheduling l Queuing – Hogging, no way to ensure Qo. S l Fair queuing – Everyone gets the same share l Weighted fair queuing – Fair queuing with priority Computer Networks, Jan-May 2004 77

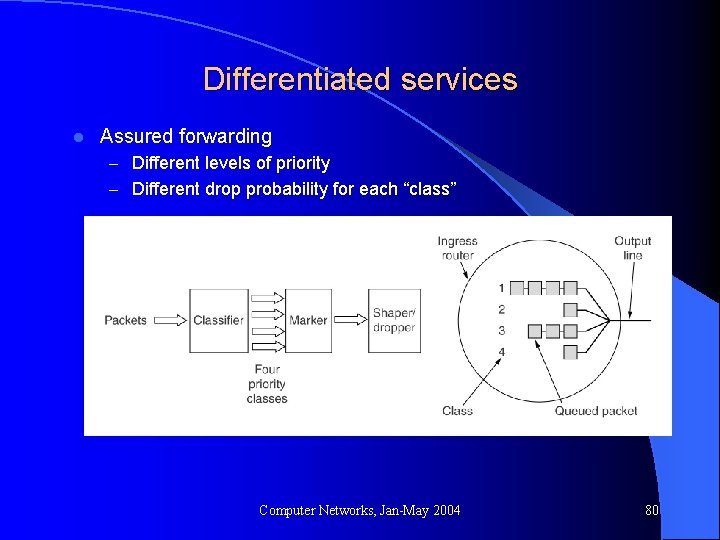
Differentiated services l A simpler approach – No initial set up – No per-flow information – Defines several “types of services” l Expedited forwarding l Assured forwarding l Etc. l Classification of packets, based on – SRC, DST addresses and port nos. – “type of service” byte in IP packet header (actually 6 bits) Once classified, traffic may still be subject to policing, marking l Once classified, packets are treated differently l Computer Networks, Jan-May 2004 78

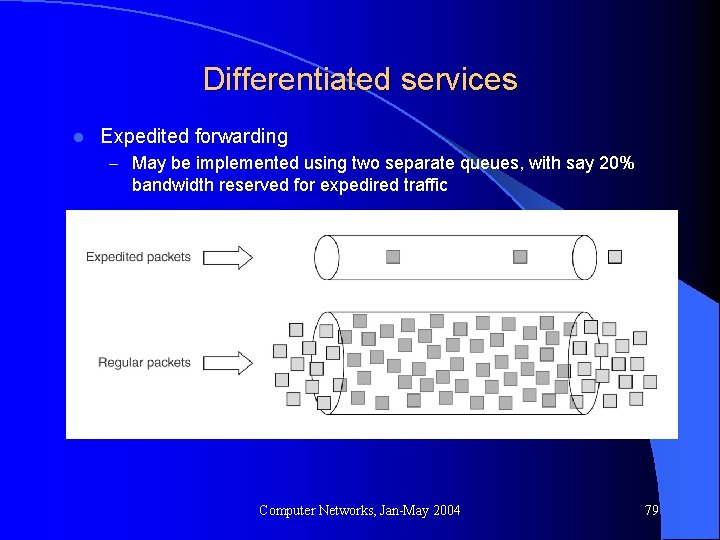
Differentiated services l Expedited forwarding – May be implemented using two separate queues, with say 20% bandwidth reserved for expedired traffic Computer Networks, Jan-May 2004 79

Differentiated services l Assured forwarding – Different levels of priority – Different drop probability for each “class” Computer Networks, Jan-May 2004 80

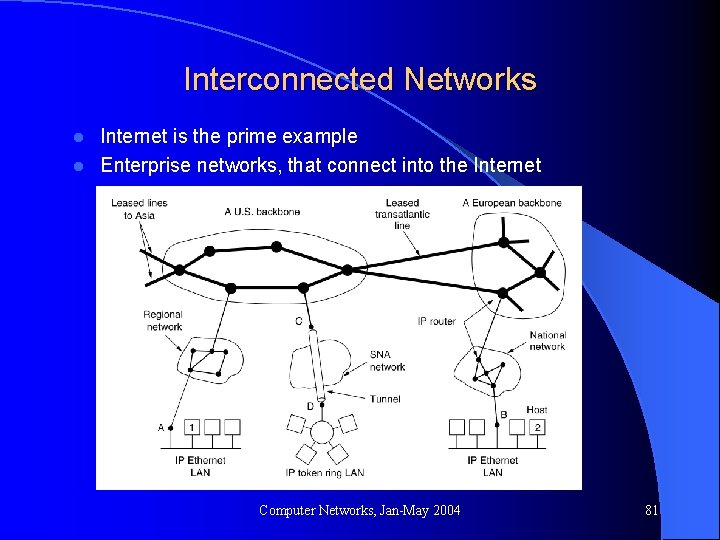
Interconnected Networks Internet is the prime example l Enterprise networks, that connect into the Internet l Computer Networks, Jan-May 2004 81

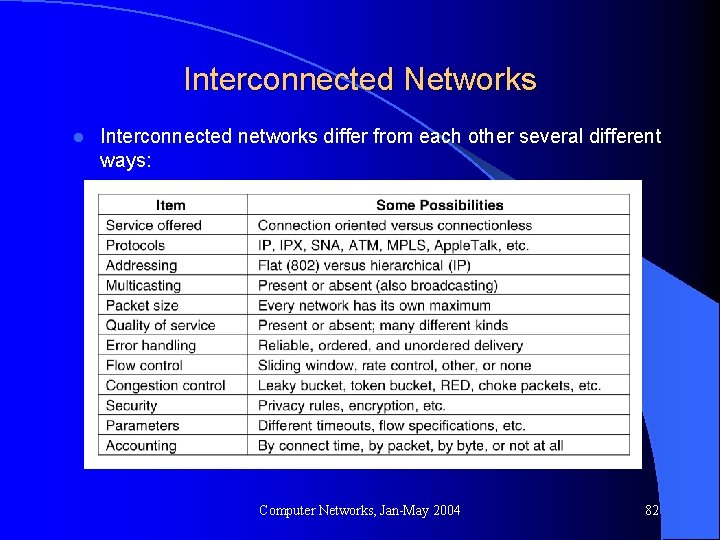
Interconnected Networks l Interconnected networks differ from each other several different ways: Computer Networks, Jan-May 2004 82

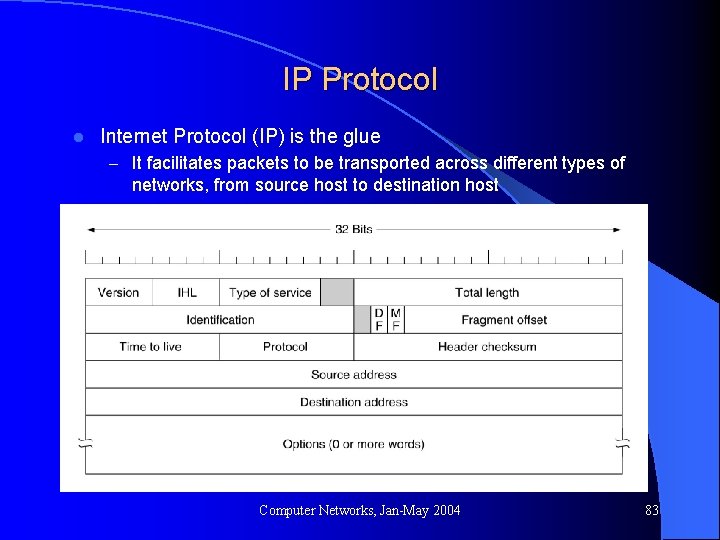
IP Protocol l Internet Protocol (IP) is the glue – It facilitates packets to be transported across different types of networks, from source host to destination host Computer Networks, Jan-May 2004 83

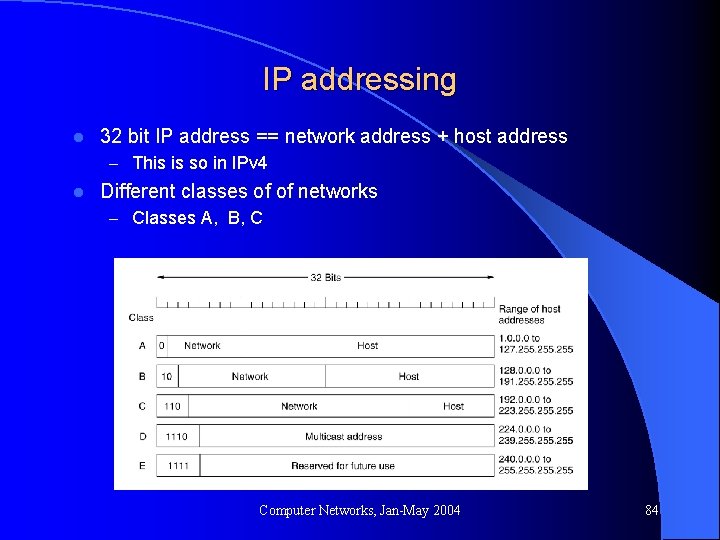
IP addressing l 32 bit IP address == network address + host address – This is so in IPv 4 l Different classes of of networks – Classes A, B, C Computer Networks, Jan-May 2004 84

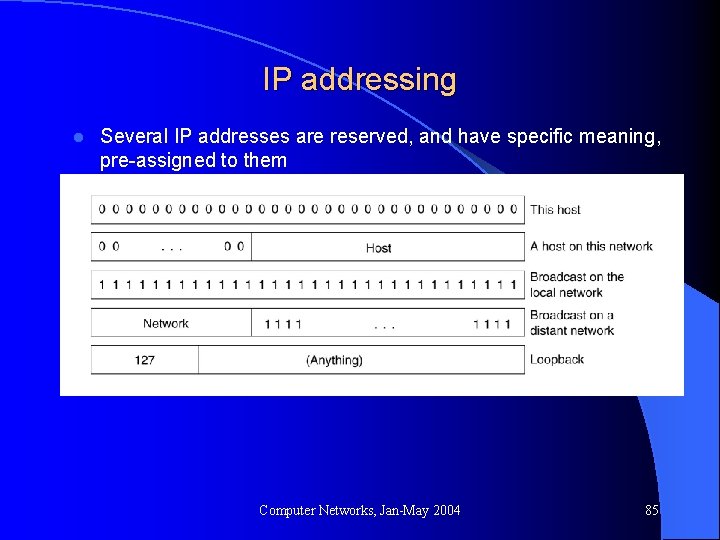
IP addressing l Several IP addresses are reserved, and have specific meaning, pre-assigned to them Computer Networks, Jan-May 2004 85

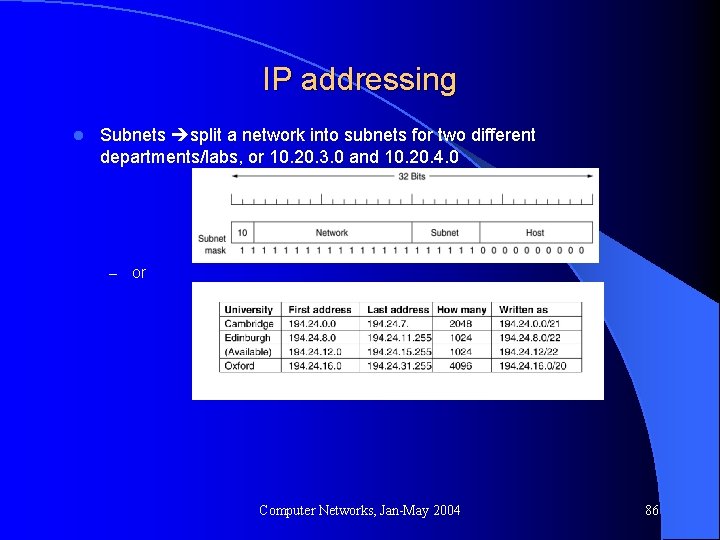
IP addressing l Subnets split a network into subnets for two different departments/labs, or 10. 20. 3. 0 and 10. 20. 4. 0 – or Computer Networks, Jan-May 2004 86

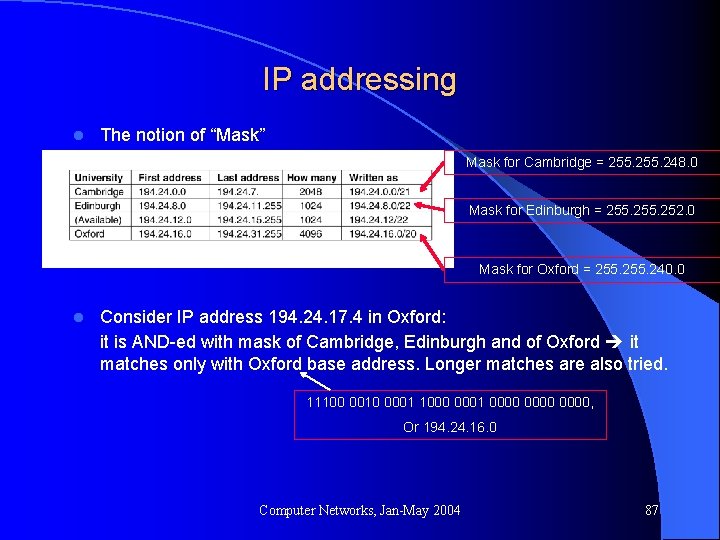
IP addressing l The notion of “Mask” Mask for Cambridge = 255. 248. 0 Mask for Edinburgh = 255. 252. 0 Mask for Oxford = 255. 240. 0 l Consider IP address 194. 24. 17. 4 in Oxford: it is AND-ed with mask of Cambridge, Edinburgh and of Oxford it matches only with Oxford base address. Longer matches are also tried. 11100 0010 0001 1000 0001 0000, Or 194. 24. 16. 0 Computer Networks, Jan-May 2004 87

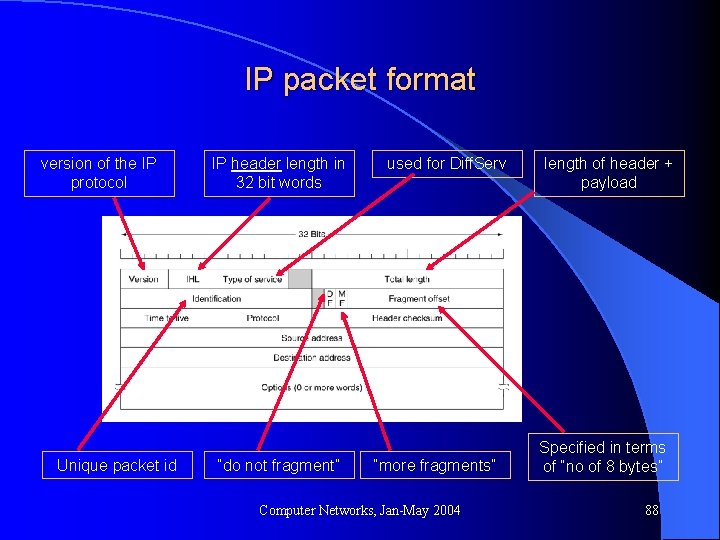
IP packet format version of the IP protocol Unique packet id IP header length in 32 bit words “do not fragment” used for Diff. Serv “more fragments” Computer Networks, Jan-May 2004 length of header + payload Specified in terms of “no of 8 bytes” 88

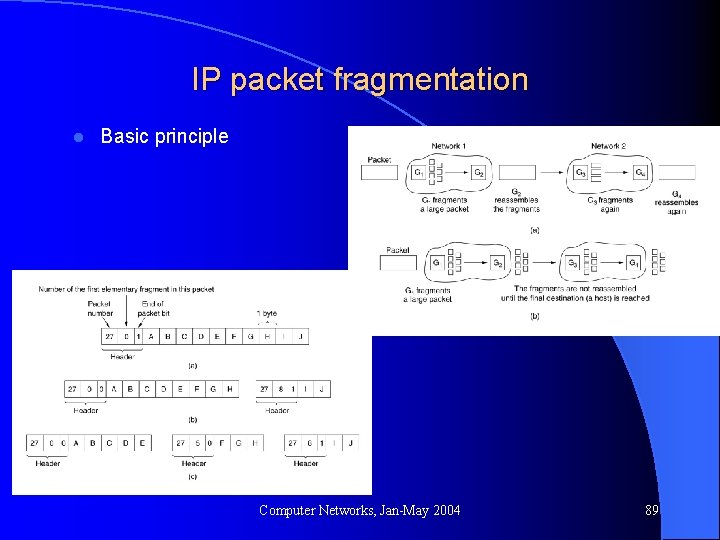
IP packet fragmentation l Basic principle Computer Networks, Jan-May 2004 89

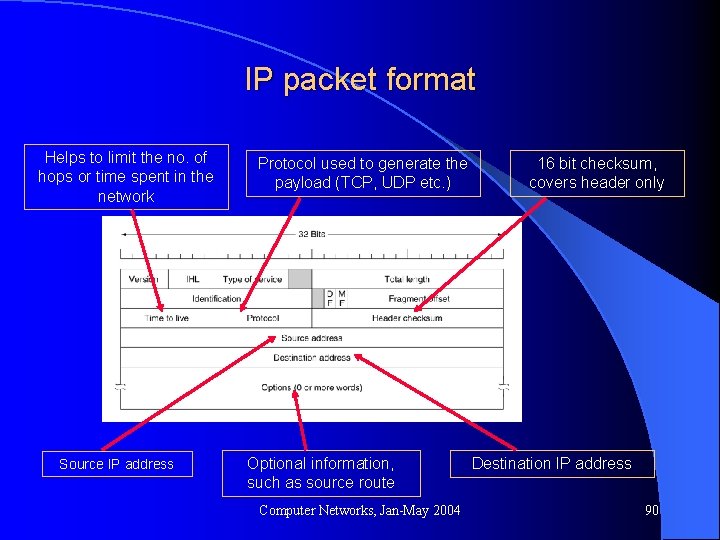
IP packet format Helps to limit the no. of hops or time spent in the network Source IP address Protocol used to generate the payload (TCP, UDP etc. ) Optional information, such as source route Computer Networks, Jan-May 2004 16 bit checksum, covers header only Destination IP address 90

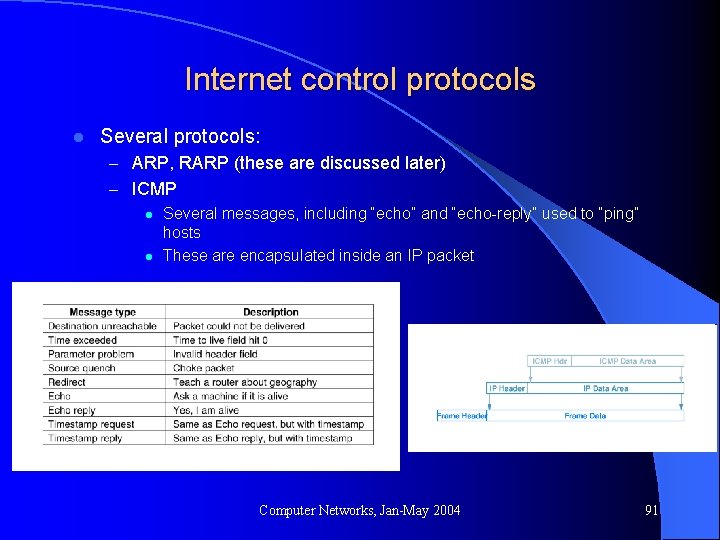
Internet control protocols l Several protocols: – ARP, RARP (these are discussed later) – ICMP l Several messages, including “echo” and “echo-reply” used to “ping” hosts l These are encapsulated inside an IP packet Computer Networks, Jan-May 2004 91

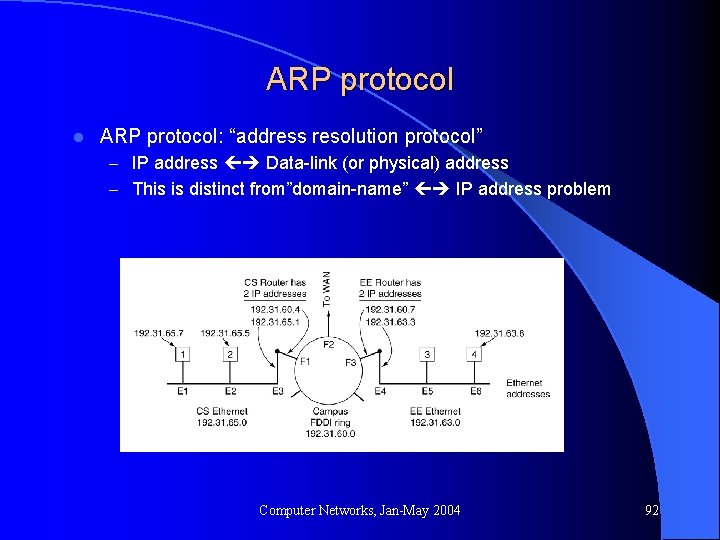
ARP protocol l ARP protocol: “address resolution protocol” – IP address Data-link (or physical) address – This is distinct from”domain-name” IP address problem Computer Networks, Jan-May 2004 92

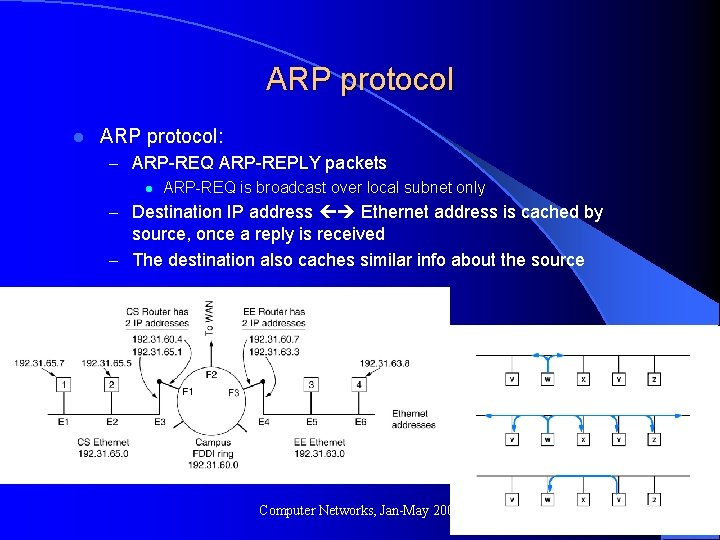
ARP protocol l ARP protocol: – ARP-REQ ARP-REPLY packets l ARP-REQ is broadcast over local subnet only – Destination IP address Ethernet address is cached by source, once a reply is received – The destination also caches similar info about the source Computer Networks, Jan-May 2004 93

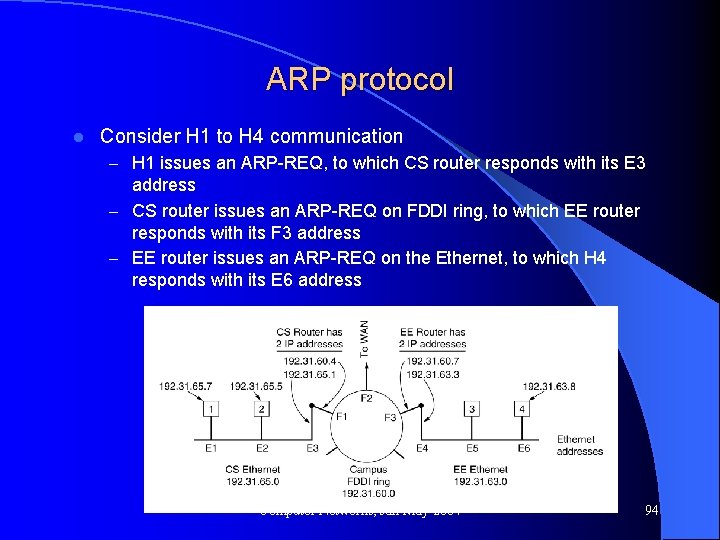
ARP protocol l Consider H 1 to H 4 communication – H 1 issues an ARP-REQ, to which CS router responds with its E 3 address – CS router issues an ARP-REQ on FDDI ring, to which EE router responds with its F 3 address – EE router issues an ARP-REQ on the Ethernet, to which H 4 responds with its E 6 address Computer Networks, Jan-May 2004 94

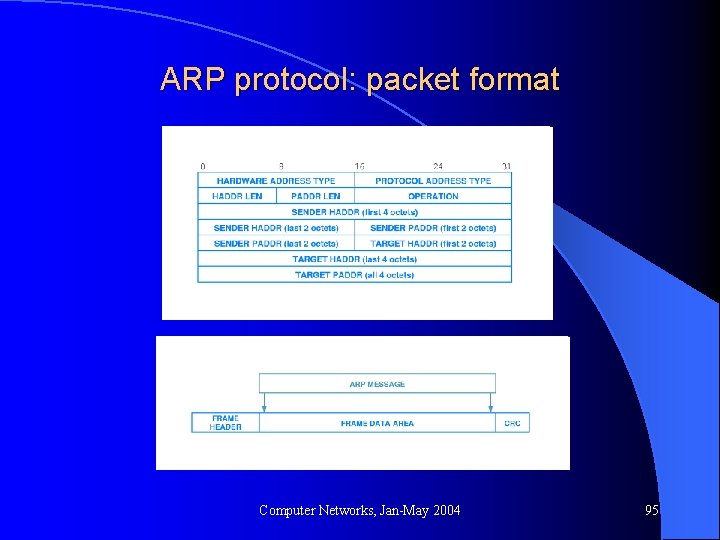
ARP protocol: packet format Computer Networks, Jan-May 2004 95

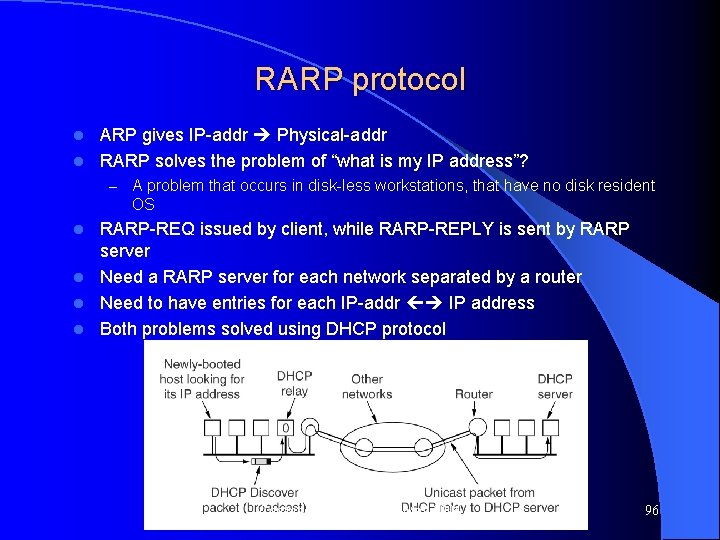
RARP protocol ARP gives IP-addr Physical-addr l RARP solves the problem of “what is my IP address”? l – A problem that occurs in disk-less workstations, that have no disk resident OS RARP-REQ issued by client, while RARP-REPLY is sent by RARP server l Need a RARP server for each network separated by a router l Need to have entries for each IP-addr IP address l Both problems solved using DHCP protocol l Computer Networks, Jan-May 2004 96

? l ? Computer Networks, Jan-May 2004 97

? l ? Computer Networks, Jan-May 2004 98

? l ? Computer Networks, Jan-May 2004 99

? l ? Computer Networks, Jan-May 2004 100

Thanks Computer Networks, Jan-May 2004 101