Computer Networks Fundamental terminology Network standards organizations Standard












- Slides: 27

Computer Networks · Fundamental terminology · Network standards organizations · Standard network hardware examples – ethernet – token ring – ATM · Future issues · Protocols · OSI layers and internetworking – bridging and routing · Web-based commerce (9. 1)

Computer Networks (9. 2) · Networks are simply a set of computers connected by a communication medium, communicating by established conventions – typically bursty transmission characteristics · Network goals – resource sharing » expensive equipment » large, reliable data storage – high reliability » replication of services » although network may be single point of failure – lower overall system costs with better performance » a few shared high-end machines, many individual low-end machines

Computer Networks (continued) · Network categories – local area networks (LAN) » typically single transmission – wide area networks (WAN) » typically store and forward – interconnected networks (internets) (9. 3)

Fundamental Terminology (9. 4) · Circuit switched / packet switched – circuit switched = telephone » connection route established at start of communication, maintained as long as communication continues » route is dedicated to one communication – packet switched » whole communication is broken down into smaller chunks called packets » each packet may take a different route to the destination » routes may be shared by other communications

Fundamental Terminology (continued) (9. 5) · Another categorization of packet switched networks is – virtual circuit » packets all take same route, set up in advance – datagram » each packet routed independently, no connection established » typically more robust

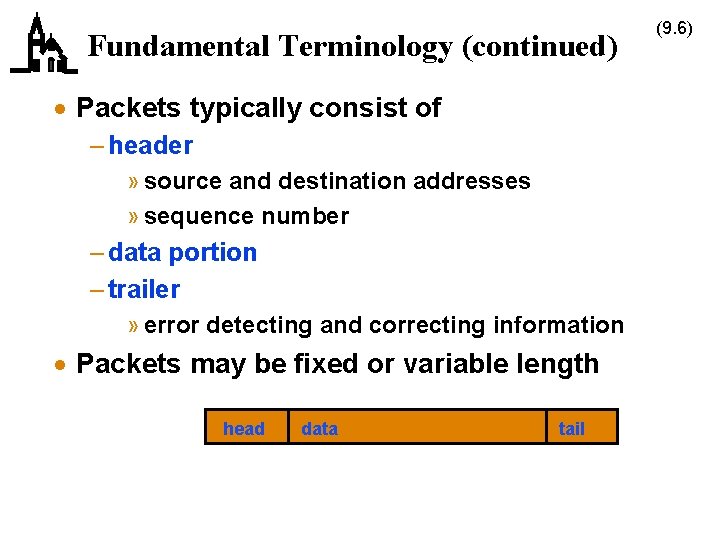
Fundamental Terminology (continued) · Packets typically consist of – header » source and destination addresses » sequence number – data portion – trailer » error detecting and correcting information · Packets may be fixed or variable length head data tail (9. 6)

Network Standards Organizations (9. 7) · International Standards Organization (ISO) – makes standards for many different activities · American National Standards Institute (ANSI) – US representative to ISO · CCITT – one part of the UN agency International Telecommunications Union – concerned with telephone and data communication services – US representative is the State Department

Network Standards Organizations (cont. ) (9. 8) · National Instituted of Standards and Technology (NIST) – standards body for US government purchases · Institute of Electrical and Electronics Engineers (IEEE) – key standards for LANs · Internet Engineering Task Force (IETF)

Local Area Network Standards (9. 9) · Ethernet (IEEE 802. 3) – Carrier Sense Multiple Access / Collision Detect (CSMA/CD) » listen to cable, no one transmitting go ahead » if collide, delay random time and retransmit – multiple topologies – multiple media » coaxial cable (thick or thin) » twisted pair wire (10 Base. T) – minimum packet size 64 bytes » heavy overhead for one byte of data – fast ethernet technologies allow 100 Mbps on twisted pair » 1000 Mbps now available on optical fiber

(9. 10) Local Area Network Standards (continued) · Token ring (IEEE 802. 5) – token determines which host gets to transmit » special bit pattern used for token » when station wants to transmit • watch network for token • take token off ring and transmit packet • drain packet as it comes around again • put token back on ring when done – single topology – one node monitors ring to regenerate token if necessary

(9. 11) Local Area Network Standards (continued) · Ethernet – faster access if light load – degrades rapidly as load increases » > 60% utilization is a problem – no guaranteed access » host can “starve” – most popular LAN technology

(9. 12) Local Area Network Standards (continued) · Token ring – minimum delay to transmit, since have to wait for token – delivers much better performance under heavy load » can reach close to 100% utilization – fair » host can hold token for 10 msec, then must put back on network » each host gets token at least every 10 * number of hosts msec – “sick” monitor station cause problems

Frame Relay and ATM (9. 13) · Frame Relay – virtual circuit organization – uses leased or private lines » vc set up at time subscribers are connected to the network – “light” protocol » no error checking by network, just delivery mechanism – 64 Kbps to 45 Mbps

ATM (9. 14) · Asynchronous Transfer Mode (ATM) – being standardized by CCITT – switched, virtual circuit approach – allows reserving network capacity – uses fixed size packets » easier for hardware to handle – twisted pair or fiber medium » 100 m to few km – 155 Mbps to 2400 Mbps – also used for LAN interconnect as backbone

Future Issues (9. 15) · Mobility – mobility within an office complex is possible now » wireless LANs at 10 Mbps » low power radio connecting to wired communication – problem with computing outside the office – several factors force mobile computing outside office » cellular phone popularity » centrality of computing » reliance on networking and communication – problems are » creating enough bandwidth • possibly need multiple channels » not enough spectrum • current transmission / broadcast activities may swap

Network Protocols (9. 16) · A protocol is a set of conventions for communicating · Concerned with issues such as – addressing and routing – error detection and correction – flow control and congestion control – higher level coordination depending on the purpose of the communication · International Standards Organization Open Systems Interconnection model (ISO OSI) – 7 layers of protocols – defined interfaces between each layer – lower layers typically implemented in hardware, upper in software

Network Protocols (continued) (9. 17)

Network Protocols (continued) (9. 18) · ISO layers – application - detailed information about data being exchanged – presentation - conventions for representing data – session - management of connections between programs – transport - delivery (reliable or otherwise) of sequences of packets – network - format of individual data packets – link - access to and control of transmission medium – physical - medium of transmission · Internet protocols (IP) are a competing set for lower layers – network and transport – defacto standard

Bridging · Bridging happens at Link layer – between LANs – provides » filtering - only forward packets destined offnet » repacketization » speed matching (9. 19)

Routing (9. 20) · Internetworking (in WANs) – happens at network layer – routers connect WANs with very dissimilar characteristics » also called gateways · Routing – routers know whole network topology » determines which network to send packet on next from destination address – protocol conversion – fragmentation » when packet too large for next network it must pass through

Routing (continued) (9. 21)

Routing (continued) (9. 22)

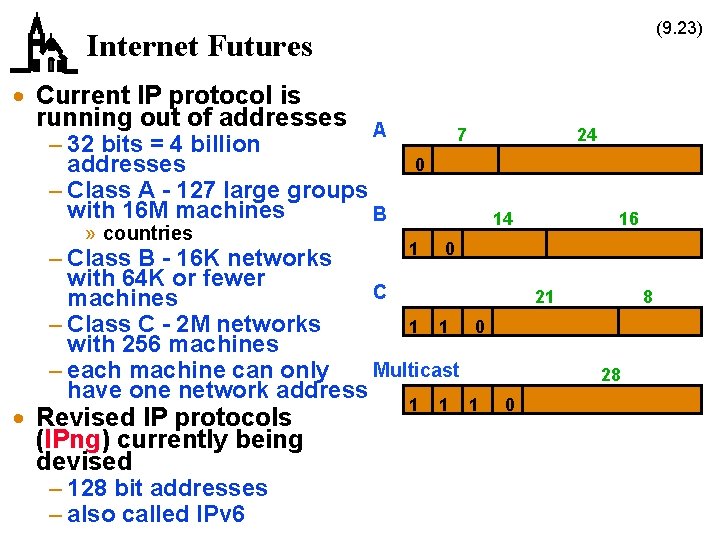
(9. 23) Internet Futures · Current IP protocol is running out of addresses A – 32 bits = 4 billion addresses – Class A - 127 large groups with 16 M machines B 7 24 0 14 » countries 1 0 – Class B - 16 K networks with 64 K or fewer C machines – Class C - 2 M networks 1 1 with 256 machines Multicast – each machine can only have one network address · Revised IP protocols (IPng) currently being devised – 128 bit addresses – also called IPv 6 1 1 16 21 8 0 28 1 0

(9. 24) Web-based Commerce · Conducting business (exchanging money) over the Internet requires several features that aren’t yet available – confidentiality » no one else listens to the transaction encryption – authentication » you really are who I think you are – data integrity » no one increases my order enroute – nonrepudiation » I can’t back out after I buy – selective application of services digital signatures and certificates » seller never sees my credit card number » I seal it and only give name of the bank, who authorizes payment

Web-based Commerce (continued) · Public-key systems provide confidentiality – I choose 2 keys, one public and one private » publish public key widely – I encode with private key – you decode with public key or – you encode with public key – I decode with private key (9. 25)

Web-based Commerce (continued) (9. 26) · Digital signatures use public key algorithms, usually on digest of message to speed up – encode message digest (hash function) – cleartext message also digested at receiving end – if my decoded digest matches calculated one, I sent it and it hasn’t been changed

Web-based Commerce (continued) (9. 27) · Authentication provided by authentication entities – I don’t send order directly to Nordstroms – send to authenticator instead, who verifies I’m me and sends the order to a prestored Nordstroms address – other variations exist · Several proposals to modify IP protocols at various levels to help this – IP protocol – Secure Sockets Layer session protocol – secure HTTP and MIME messaging