Computer Networks CS 3623 10 Internetworking Intro We












- Slides: 46

Computer Networks (CS 3623) #10 | Internetworking

Intro • We know how to build a single network using point-to-point links, shared media, and switches • Fact & goal: – networks build with various technologies – to communicate with each other

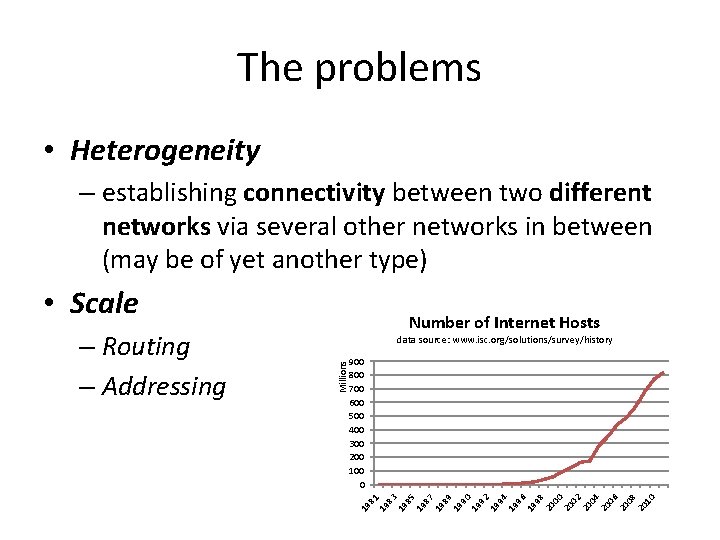
The problems • Heterogeneity – establishing connectivity between two different networks via several other networks in between (may be of yet another type) • Scale data source: www. isc. org/solutions/survey/history 900 800 700 600 500 400 300 200 100 0 19 81 19 83 19 85 19 87 19 89 19 90 19 92 19 94 19 96 19 98 20 00 20 02 20 04 20 06 20 08 20 10 Millions – Routing – Addressing Number of Internet Hosts

Agenda: Simple Internetworking • • • What is an internetwork? Service Model Global Addresses Datagram Forwarding in IP Some protocols : – Address Translation (ARP) – Host Configuration (DHCP) – Error Reporting (ICMP)

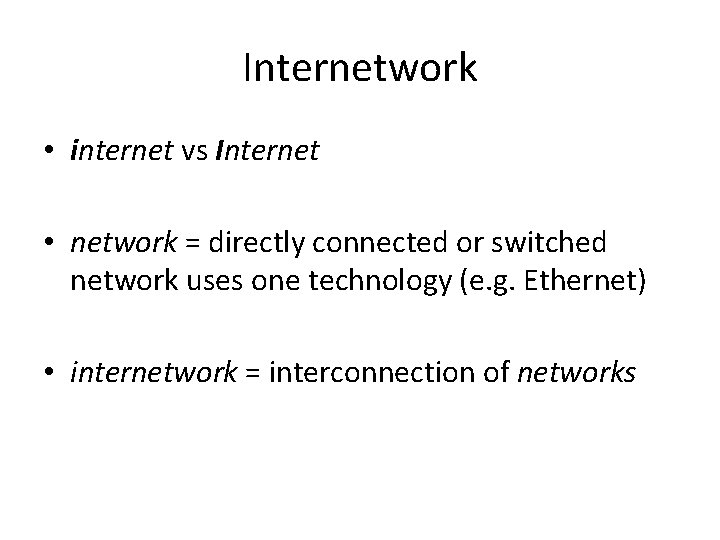
Internetwork • internet vs Internet • network = directly connected or switched network uses one technology (e. g. Ethernet) • internetwork = interconnection of networks

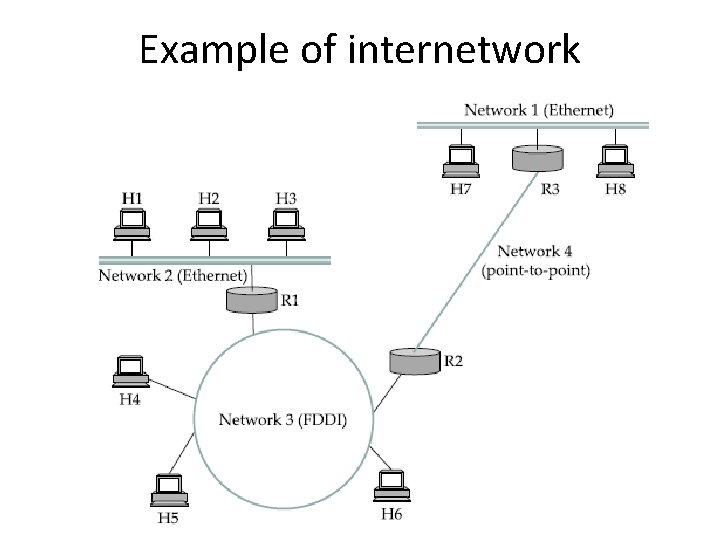
Example of internetwork

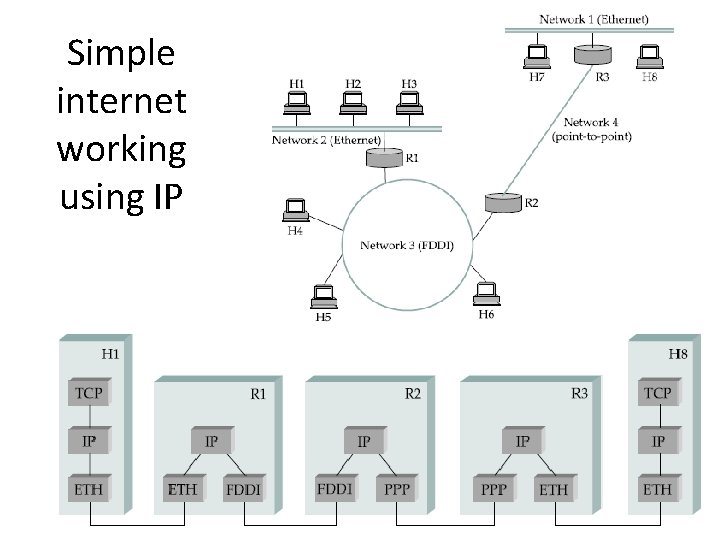
Simple internet working using IP

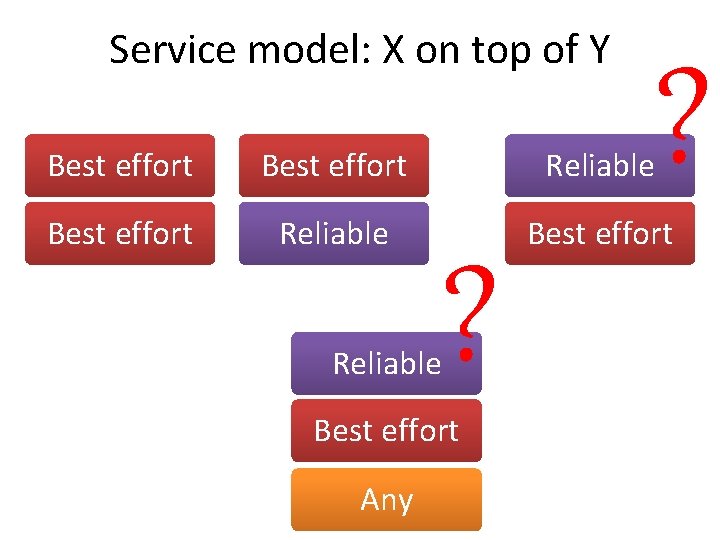
Service Model of an internetwork • = the host-to-host services to provide • The philosophy (in the case of IP): make it undemanding enough that just about any network technology that might turn up in an internetwork would be able to provide the necessary service

IP service model • BEST EFFORT – IP makes every effort to deliver datagrams, it makes no guarantees • Two parts: – Addressing scheme • Identify all hosts in the internetwork – Datagram (connectionless) model of data delivery

Datagram Delivery • Every datagram carries enough information to let the network forwards the packet to its correct destination • ‘best effort’ = unreliable service – if something goes wrong (packet gets lost, corrupted, misdelivered, out of order, duplicated etc. ), the network does nothing

Service model: X on top of Y ? Best effort Reliable Best effort ? Reliable Best effort Any

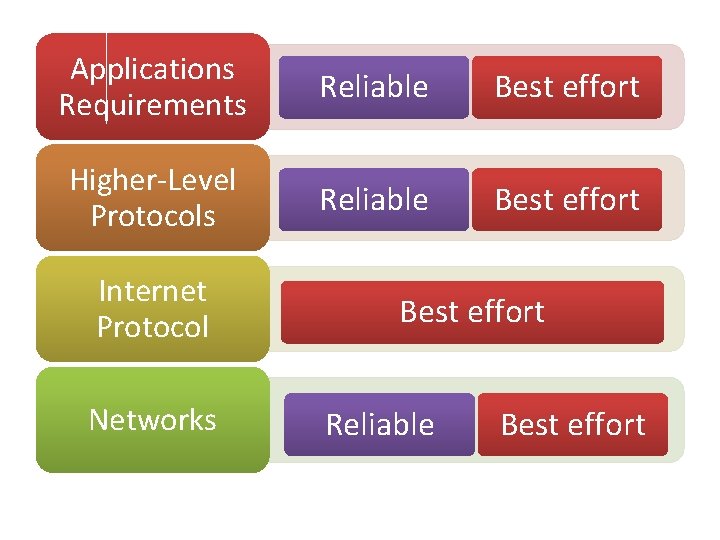
Applications Requirements Reliable Best effort Higher-Level Protocols Reliable Best effort Internet Protocol Networks Best effort Reliable Best effort

The ability of IP • “run over anything” • many of the technologies over which IP runs today did not exist when IP was invented • Best-effort delivery: – packets can get lost – packets can get delivered out of order – the same packet can get delivered more than once • It is up to the higher-level protocols or applications that run above IP to deal with these phenomena

Intermezzo: IP over Avian Carriers www. blug. linux. no/rfc 1149 • RFC 1149 : A Standard for the Transmission of IP Datagrams on Avian Carriers (1 April 1990) • RFC 2549: IP over Avian Carriers with Quality of Service (1 April 1999)

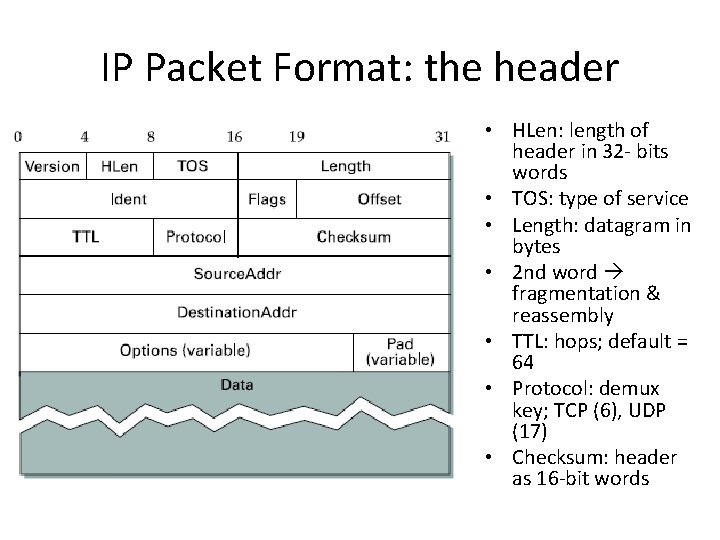
IP Packet Format: the header • HLen: length of header in 32 - bits words • TOS: type of service • Length: datagram in bytes • 2 nd word fragmentation & reassembly • TTL: hops; default = 64 • Protocol: demux key; TCP (6), UDP (17) • Checksum: header as 16 -bit words

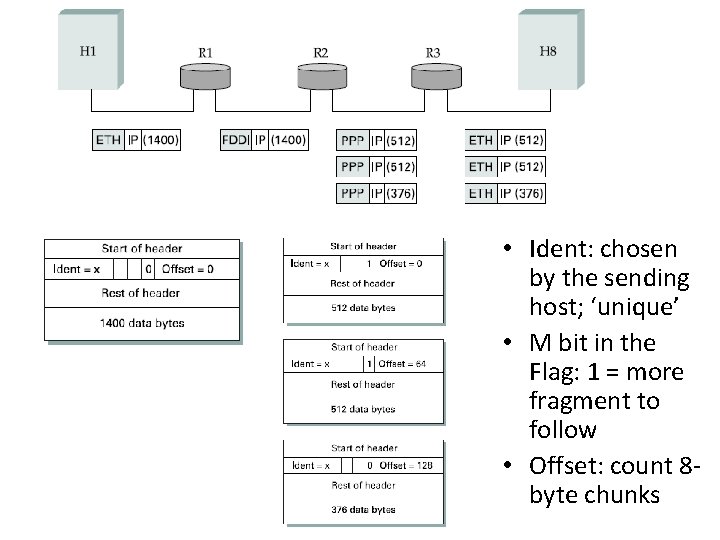
Various MTU • Every network type has its own MTU (maximum transmission unit) – Eth: 1500 bytes; FDDI: 4500 bytes; PPP: 532 bytes • Choices for IP: – Make sure that IP datagram are small enough for any network technology – Packet can be fragmented & reassembled

Fragmentation & Reassembly • When host sends an IP datagram – Reasonable choice: MTU of the network – Fragmentation: only if the MTU is smaller than the datagram size • Reassembly: – Done at the receiving host – not at each router – Missing fragment receiver discard all arrived fragments

• Ident: chosen by the sending host; ‘unique’ • M bit in the Flag: 1 = more fragment to follow • Offset: count 8 byte chunks

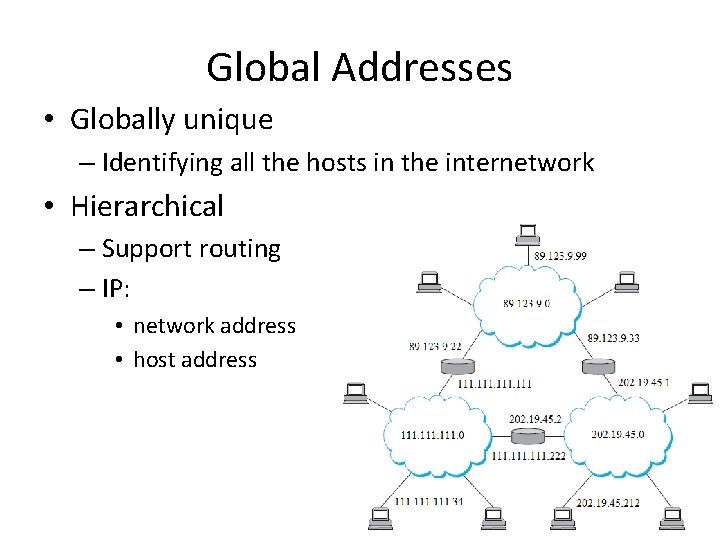
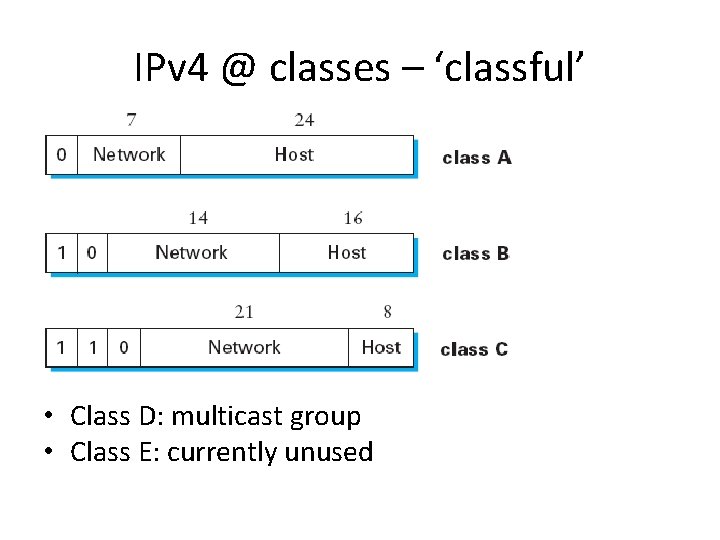
Global Addresses • Globally unique – Identifying all the hosts in the internetwork • Hierarchical – Support routing – IP: • network address • host address

IPv 4 @ classes – ‘classful’ • Class D: multicast group • Class E: currently unused

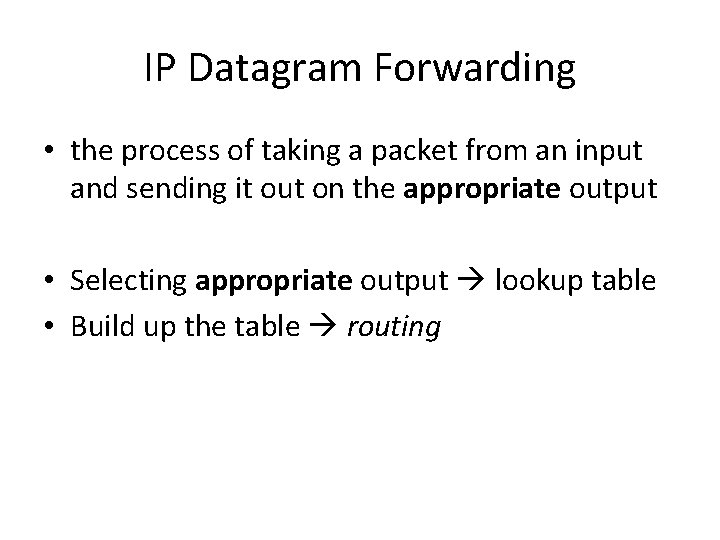
IP Datagram Forwarding • the process of taking a packet from an input and sending it out on the appropriate output • Selecting appropriate output lookup table • Build up the table routing

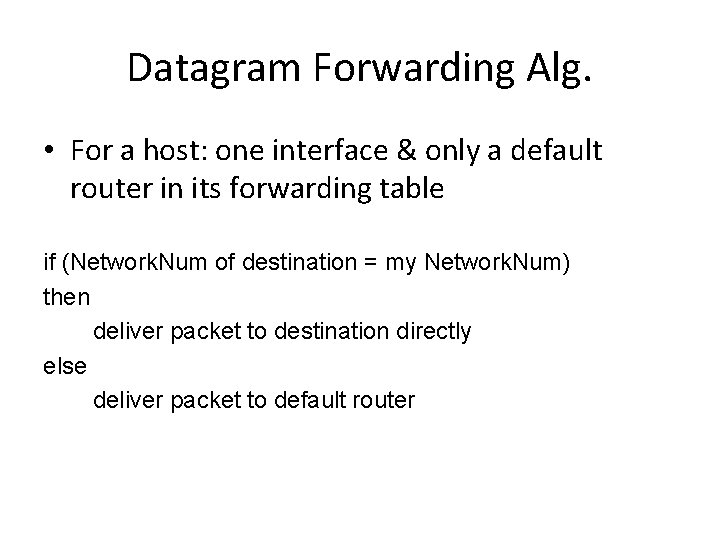
Datagram Forwarding Alg. • For a host: one interface & only a default router in its forwarding table if (Network. Num of destination = my Network. Num) then deliver packet to destination directly else deliver packet to default router

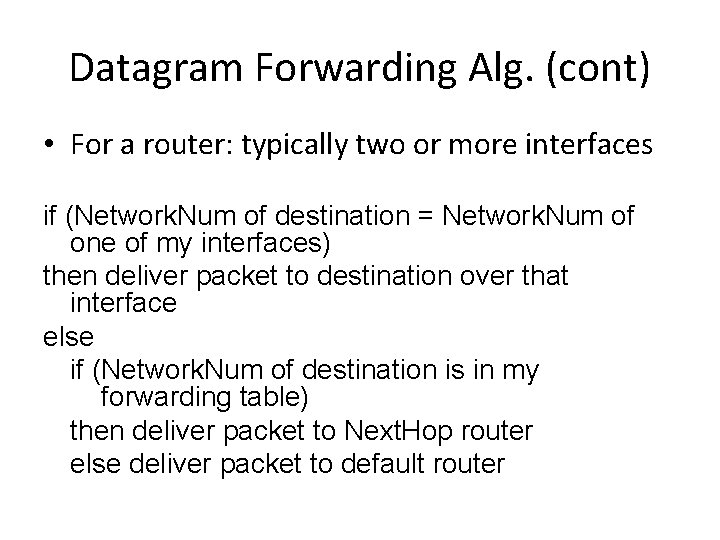
Datagram Forwarding Alg. (cont) • For a router: typically two or more interfaces if (Network. Num of destination = Network. Num of one of my interfaces) then deliver packet to destination over that interface else if (Network. Num of destination is in my forwarding table) then deliver packet to Next. Hop router else deliver packet to default router

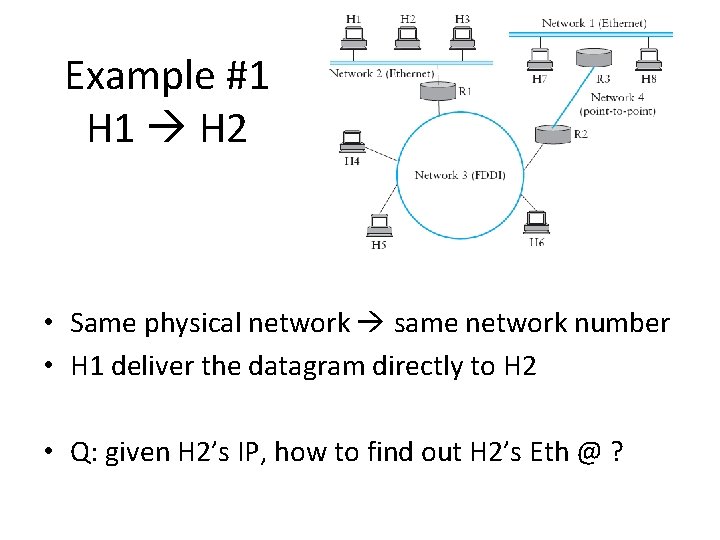
Example #1 H 1 H 2 • Same physical network same network number • H 1 deliver the datagram directly to H 2 • Q: given H 2’s IP, how to find out H 2’s Eth @ ?

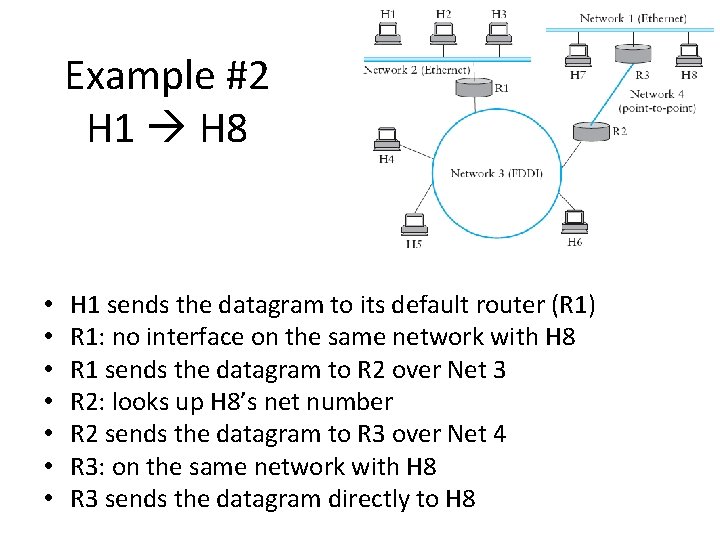
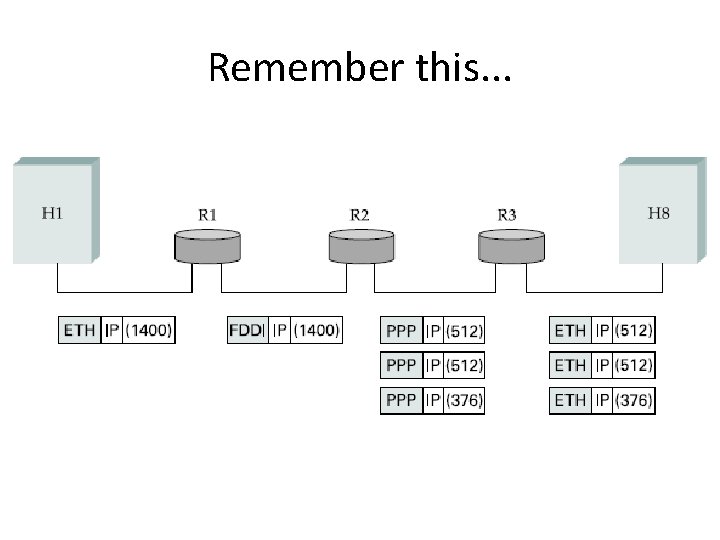
Example #2 H 1 H 8 • • H 1 sends the datagram to its default router (R 1) R 1: no interface on the same network with H 8 R 1 sends the datagram to R 2 over Net 3 R 2: looks up H 8’s net number R 2 sends the datagram to R 3 over Net 4 R 3: on the same network with H 8 R 3 sends the datagram directly to H 8

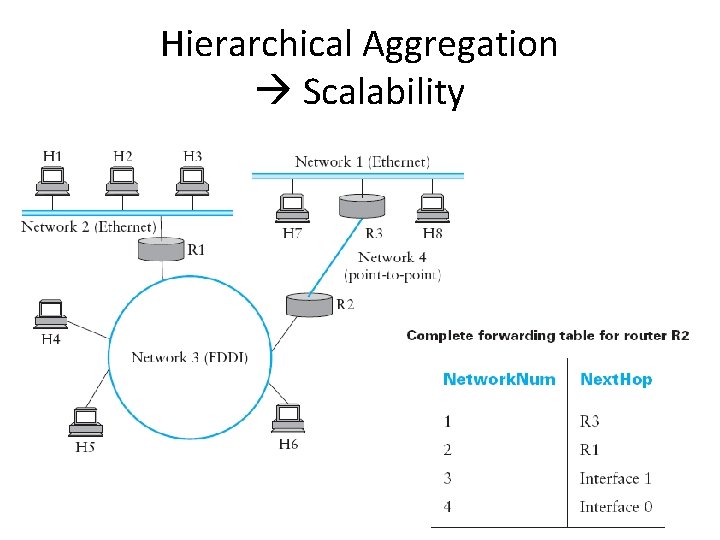
Hierarchical Aggregation Scalability

Details on IPv 4 RFC 791 http: //www. ietf. org/rfc 0791. txt

Address Translation: The main issue • IP datagrams contain IP addresses • The physical interface on the host or router only understands the addressing scheme of that particular network • We need to: – translate the IP address to a link-level address that makes sense on this network – encapsulate the IP datagram inside a frame that contains that link-level address

Remember this. . .

Address Resolution Protocol (ARP) • Enable each host to build up a table of mapping between IP @ and link-level @ • The entries are timed out periodically (typically 15 minutes) • If a host want to send an IP datagram to a host (or router) on the same network, it checks in the ARP table. • If no mapping exist, it invokes the ARP

The ARP • Broadcasting an ARP query onto the network – Contains the target IP address • Each host receives the query and checks to see if it matches its IP address • If it does match, the host sends a response message – Contains its link-level address • The originator adds the information to its ARP table

The query message. . . • Also include the IP @ and link-layer @ of the sending host • Broadcasted • On receiving query message: A. If a host already has entry for that sending host ‘refreshes’ (reset the timeout counter) B. If the host is the target of the query adds the information into the ARP table C. Not (A or B) do nothing

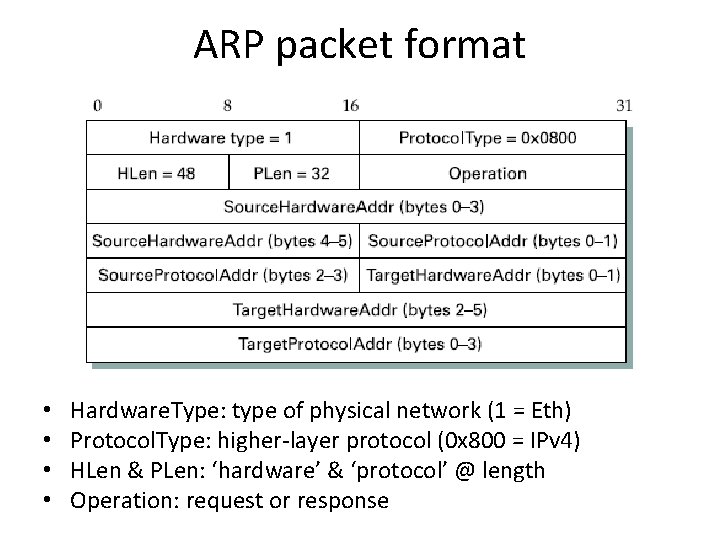
ARP packet format • • Hardware. Type: type of physical network (1 = Eth) Protocol. Type: higher-layer protocol (0 x 800 = IPv 4) HLen & PLen: ‘hardware’ & ‘protocol’ @ length Operation: request or response

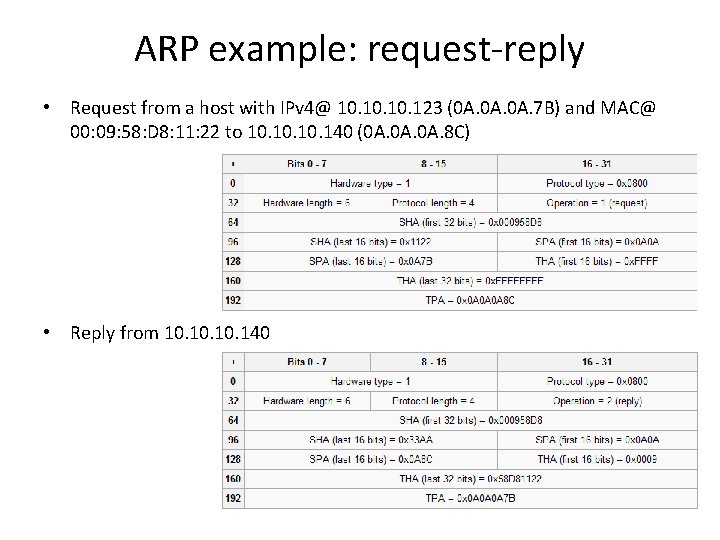
ARP example: request-reply • Request from a host with IPv 4@ 10. 10. 123 (0 A. 0 A. 7 B) and MAC@ 00: 09: 58: D 8: 11: 22 to 10. 10. 140 (0 A. 0 A. 8 C) • Reply from 10. 10. 140

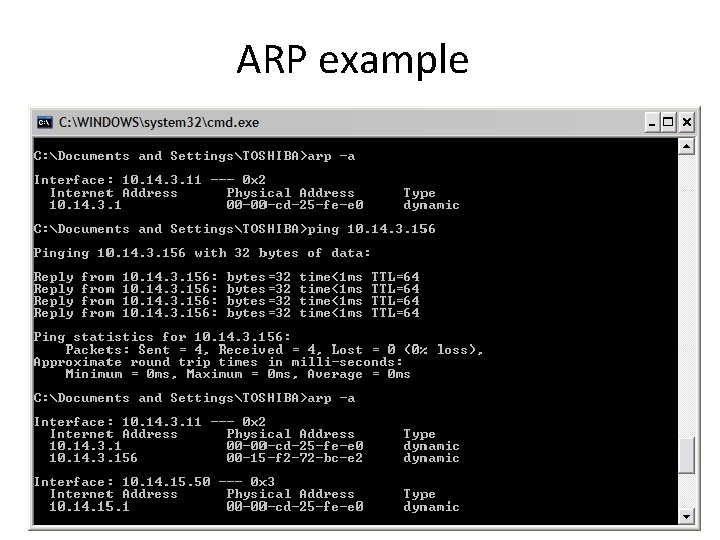
ARP example

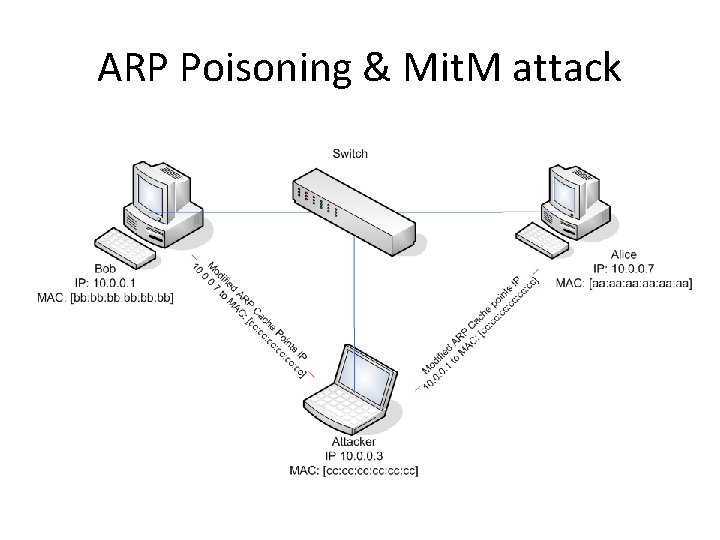
ARP Poisoning & Mit. M attack

Automated Host Configuration • Dynamic Host Configuration Protocol (DHCP) • Simplest level: – DHCP server as a centralized repository for host configuration information – Automatically retrieved by each host when it is booted or connected to the network • More sophisticated model: – DHCP server maintain a pool of available addresses that it hands out to host on demand

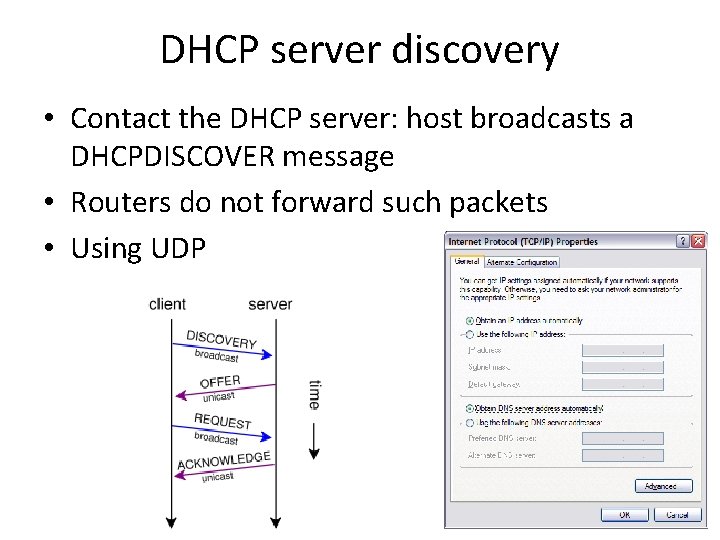
DHCP server discovery • Contact the DHCP server: host broadcasts a DHCPDISCOVER message • Routers do not forward such packets • Using UDP

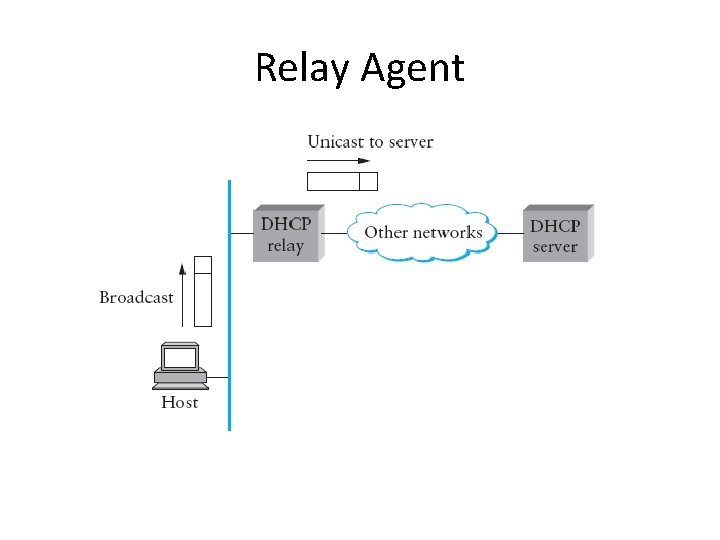
DHCP cases • The simplest case: – One DHCP server per network – The server reply to the host generated the message • For a large number of networks: – Use a relay agent, at least one per network – When RA receives a DHCPDISCOVER, it unicasts it to the DHCP server, awaits the response, then send it back to the requesting client

Relay Agent

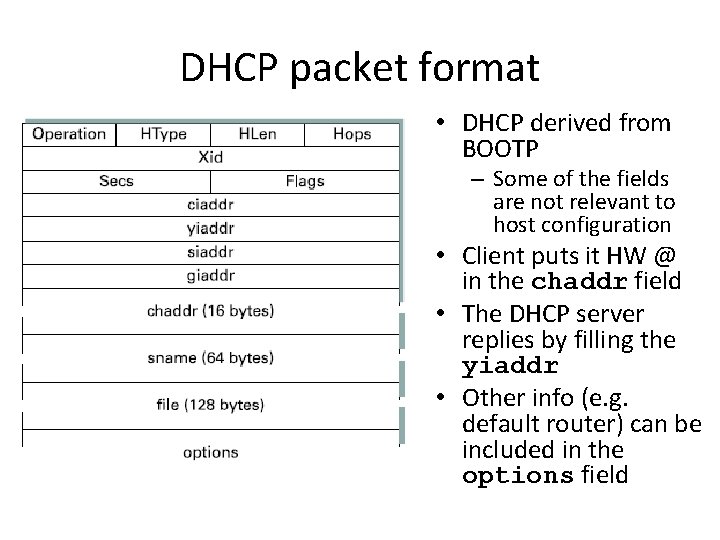
DHCP packet format • DHCP derived from BOOTP – Some of the fields are not relevant to host configuration • Client puts it HW @ in the chaddr field • The DHCP server replies by filling the yiaddr • Other info (e. g. default router) can be included in the options field

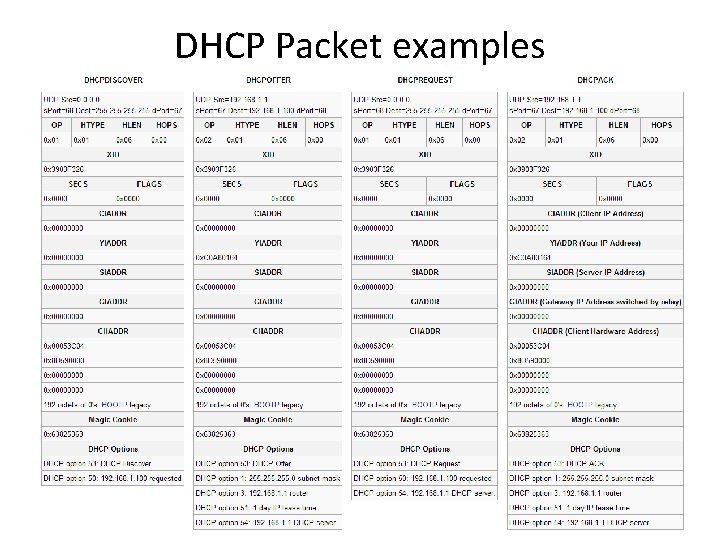
DHCP Packet examples

‘Leased’ address • Host cannot keep address indefinitely and cannot depended upon to give back its address • DHCP allows addresses to be ‘leased’ for some period of time • A host with a leased address clearly needs to renew the lease periodically

Error Reporting • Internet Control Message Protocol (ICMP) • Defines a collection of error messages that are sent back to the source host whenever a router or host is unable to process an IP datagram successfully – Destination host unreachable, reassembly process failed, TTL has reached 0, IP header checksum failed etc. • Also defines control messages that a router can send back to a source host.

ICMP-Redirect • One of the most useful control message • Tells the source host that there is a better route to the destination • Example: – A network with two routers R 1 & R 2 attached to it – A host uses R 1 as a default router – R 1 receive a datagram from the host, based on its forwarding table R 2 would have been better for a particular destination – R 1 sends an ICMP-Redirect back to the host, instructing it to use R 2 for the particular destination

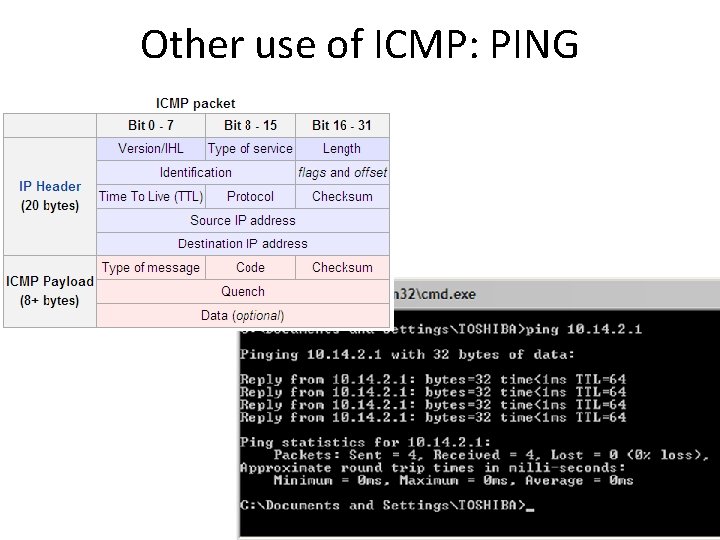
Other use of ICMP: PING