Computer Networks Chapter 11 Data Link Control and





- Slides: 28

Computer Networks Chapter 11 – Data Link Control and Protocols Spring 2006 Computer Networks

Flow Control § Flow control – controling the sender not to overflow the receiver § Buffers – temporary memory where the receiver stores data sent by the sender before it process them § Buffers can be filled in with data when § sender is running on the fast (or lightly loaded machine) and the reciever is running on a slow (or highly loaded) machine § In case no buffers are available, data can be lost. § Therefore protocols need to control the sender not to overflow the reciever § Protocols for flow control can exist at the data-link layer or the upper layers Spring 2006 Computer Networks 2

Error Control § Errors can appear due to: § Impairments of transmission media § Loss of data because of limitted buffer space § Other unpredictable circumastances § It is necessary that the receiver has mechanisms to discover the occurence of errors § When the error is detected, the receiver can ask the sender to retransmit data. Spring 2006 Computer Networks 3

How to Ask for Retransmission? § Two possibilities § When the frame is recieved without errors, the receiver can send an acknowledgement (ACK) § When there are errors in the frame, the receiver can send a negative acknowledgement (NACK) § ACKs are used in data communication § It is easier to detect lost frames when ACKs are used § Any time error is detected the data are retransmitted § The process is called ARQ (Automated Repeated re. Quest) Spring 2006 Computer Networks 4

How long to wait for ACK? § When a frame is sent the sender starts a timer § The timer is used to detect frame loss or acknowledgement loss § When the timer expires, the sender knows that it needs to send the frame again § The sender keeps a copy of the frame in its sending buffers § For frame identification sequence number are used § Sequence numbers are carried as a part of the header Spring 2006 Computer Networks 5

Protocols for Flow and Error Control § Stop-and-Wait § A single frame is sent at a time § Inefficient with respect to the use of the available bandwidth § Sliding window § Several frames are sent at a time and after each ACK is received a new frame is sent § Effitiency is increased, but complexity is increased, too Spring 2006 Computer Networks 6

Stop-and-Wait ARQ § The sending device keeps a copy of the last frame until it receives an acknowledgement for that frame § Keeping this copy allows the sender to retransmit lost or damaged frames § For identification purposes, both data frames and ACKs are numbered alternatively 0 and 1. § A data frame is acknowledged by an ACK 1 frame, indicating that the receiver has got the frame 0 and is expecting the frame 1 Spring 2006 Computer Networks 7

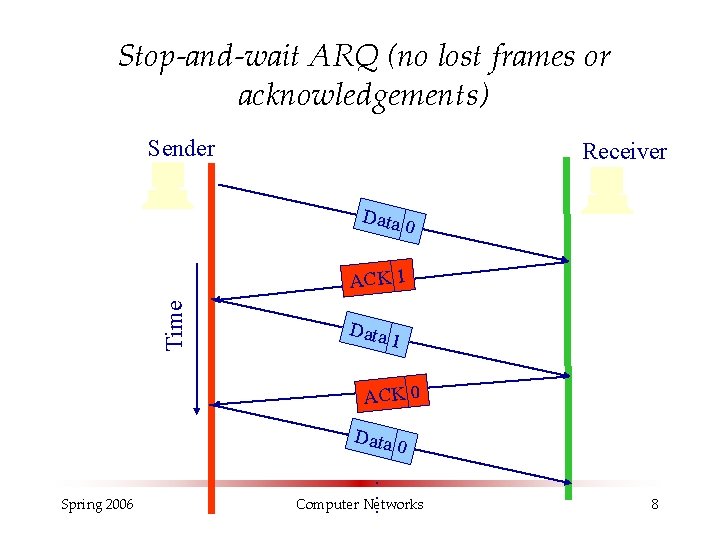
Stop-and-wait ARQ (no lost frames or acknowledgements) Sender Receiver Data 0 Time ACK 1 Data 1 ACK 0 Data Spring 2006 0 . . Computer Networks. 8

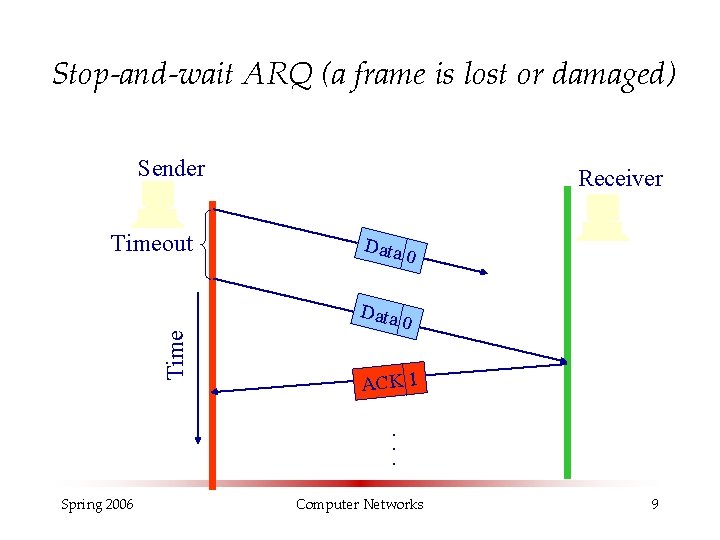
Stop-and-wait ARQ (a frame is lost or damaged) Sender Timeout Receiver Data 0 ACK 1 . . . Spring 2006 Computer Networks 9

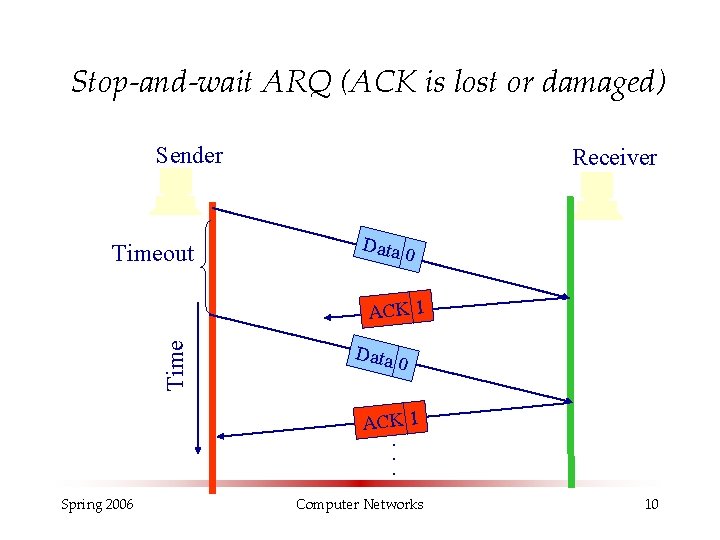
Stop-and-wait ARQ (ACK is lost or damaged) Sender Timeout Receiver Data 0 Time ACK 1 Data 0 ACK 1 . . . Spring 2006 Computer Networks 10

Performace of Stop-and-Wait Protocol § Good for relatively short links for which the ratio between the transmission and propagation time is very small § This includes short links or longer links with low data rates § The limitation is a consequense of the rule to wait for an acknowledgement before sending another frame § Require one-bit storage for the sequence numbers § Inadequate for longer links and higher data rates Spring 2006 Computer Networks 11

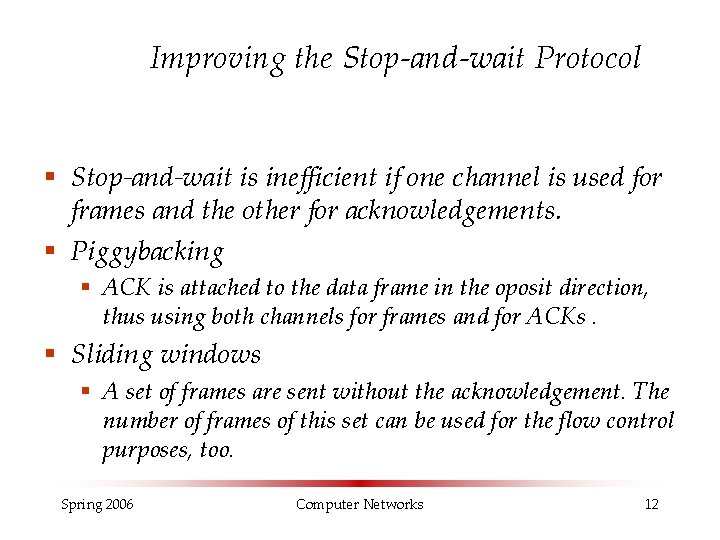
Improving the Stop-and-wait Protocol § Stop-and-wait is inefficient if one channel is used for frames and the other for acknowledgements. § Piggybacking § ACK is attached to the data frame in the oposit direction, thus using both channels for frames and for ACKs. § Sliding windows § A set of frames are sent without the acknowledgement. The number of frames of this set can be used for the flow control purposes, too. Spring 2006 Computer Networks 12

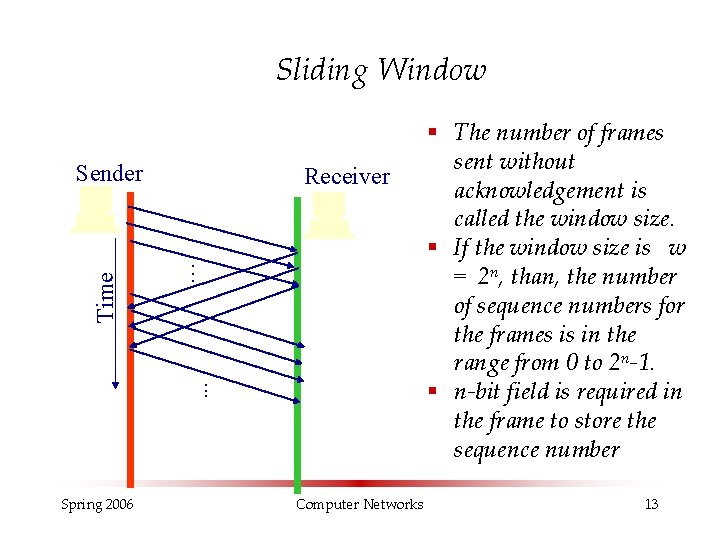
Sliding Window Time Sender Receiver. . . Spring 2006 Computer Networks § The number of frames sent without acknowledgement is called the window size. § If the window size is w = 2 n, than, the number of sequence numbers for the frames is in the range from 0 to 2 n-1. § n-bit field is required in the frame to store the sequence number 13

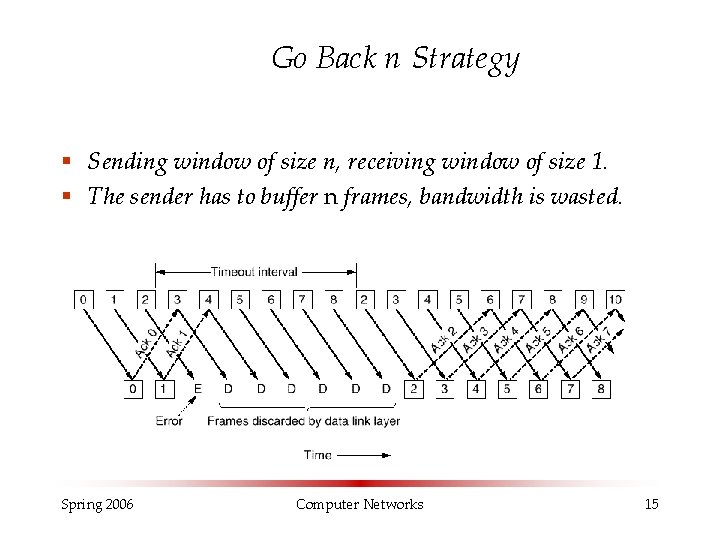
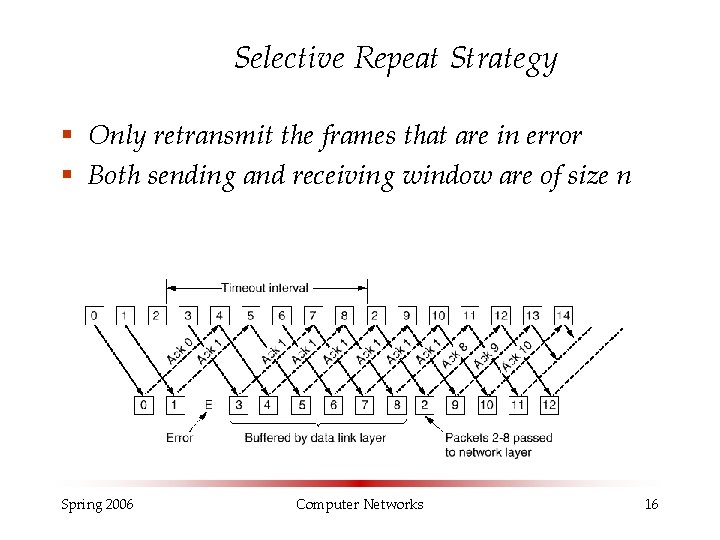
Sliding Window (Cont. ) § Problems arise when some of the frames are discarded. Two strategies are developed to deal with this problem § Go back n strategy § The reciever simply discards all frames after the damaged frame without sending acknowledgement. § Selective repeat strategy § The receiver keeps all the frames after the damaged frame. When sender finaly notice that something is wrong it retransmits the bad frame. § The two strategies are trade-offs between bandwidth and data -link buffer space. Spring 2006 Computer Networks 14

Go Back n Strategy § Sending window of size n, receiving window of size 1. § The sender has to buffer n frames, bandwidth is wasted. Spring 2006 Computer Networks 15

Selective Repeat Strategy § Only retransmit the frames that are in error § Both sending and receiving window are of size n Spring 2006 Computer Networks 16

Visualisation of Data-link Protocols § You can check the animation of stop-and-wait and sliding window protocol using the java applet presented on the following page http: //www. cs. bham. ac. uk/%7 Egkt/Teaching/SE M 335/dlsim/Simulation. html Spring 2006 Computer Networks 17

Example Data-link Protocols § Character oriented protocols § Kermit, X modem § Simple transfer protocols used extensively for PC to PC communication § Bit oriented protocols § HDLC - § Data-link protocols in the Internet (SLIP and PPP) § ATM and Data-link protocols in ATM Spring 2006 Computer Networks 18

SLIP (Serial Line IP) § Predecessor to PPP (not an Internet standard) § Very simple, but has some serious problems § Supports only IP as a network layer protocol § Does not do any error detection or correction (left to the upper protocols) § Each side must know the other’s IP address § Does not provide any form of authentication Spring 2006 Computer Networks 19

PPP (Point-to-Point Protocol) § Internet Standard (RFC 1661) § Handles error detection § Supports multiple protocols in the network layer (IP, IPX, OSI CLNP, XNS) § Allows IP addresses to be nagotiated at connection time § Used for dial-up and for leased lines Spring 2006 Computer Networks 20

Framing § Data Link Layer packets are called frames. § Frames are always transmitted between directly connected ends (there is a physical connection). Spring 2006 Computer Networks 21

Synchronization § A sequence of binary digit, transmitted at some regular rate over a link, has to be recovered at the reciever § Synchronization § Clocking or timing (the instance at which the reciever will be looking for individual bits) is an important issue § Different places where synchronization is needed § Bit synchronization (start of bit) § Character or byte synchronization (start of byte or character) § Frame synchronization (start of frame) Spring 2006 Computer Networks 22

Two Approaches Exist § Asynchronous transmission § The reciever has a free-running clock (ussually fixed multiple of the sender clock). § Short bit sequences are emitted to allow the reciever to know when to start looking for bits. § The receiver clock assumes to maintain correct timing over short spans of few bits. § Synchronous transmission § Clock information has to be embeded within the bit stream, so that the reciever can either extract the clock information, or use the embeded information to fine tune its clock. § The clock signal can be sent via separate channel (additional bandwidth required). Spring 2006 Computer Networks 23

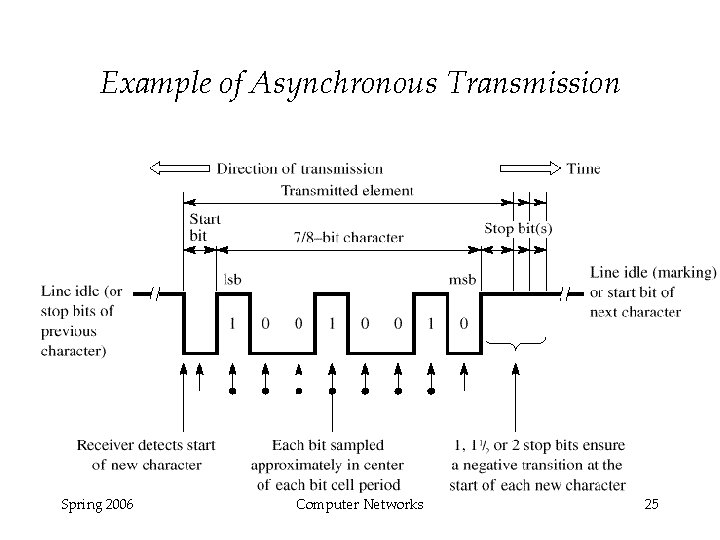
Asynchronous Transmission § If the line is in the idle state (some electrical state) and one 7 or 8 bit group need to be sent, these bits are preceded by a start bit and followed by one to two stop bits. § The receiver continously samples at rate nominally N times the transmit clock rate. § It is looking for the first transition from ”high” to ”low” after its previous idle or ”stop” bits. § After this, it sets the next sampling instant to be half of the transmitter clock period (this should be near the center of the start bit). § It then samples at multiples of N receiver clock pulses until ending stop bits return the line to logic high Spring 2006 Computer Networks 24

Example of Asynchronous Transmission Spring 2006 Computer Networks 25

Synchronous Transmission § Assynchronous transmittion is ineficient (extra overhead bits needed) and cannot be used at high transmittion rates. § In synchronous transmission we tailor the way in which binary data is encoded onto the electrical signal to obtain a signal with properties such that the receiver can receive the clock information. Spring 2006 Computer Networks 26

Frame Synchronization § Character count § Specify number of characters in the header § Not convinient because of possibility to get out of synchronization when there is a transmission error § Starting and ending characters § STX: start-of-text character signal at start of frame, ETX: end-of-text character signal at start of frame § Starting and ending flags § Each frame starts and ends with a special bit pattern called a flag byte § Using special coding sheme § If Manchester encoding sheme is used the high-high and low-low combinations can be used for this purpose Spring 2006 Computer Networks 27

Character and Bit Stuffing § STX and ETX can be data § DLE-STX signal for start of frame, DLE-ETX signal for end of frame § DLE can be data, thus some solution is necessary § Character stuffing – insert a DLE character for any DLE character in data § Bit stuffing – analogous to character stuffing § If the flag byte = 01111110, than after five 1’s a 0 is inserted in the data string § Stuffed 0 s are removed at the receiver Spring 2006 Computer Networks 28