COMPUTER NETWORKS BCA 433 Presentation MAC Sublayer Addressing
![COMPUTER NETWORKS [BCA 433] Presentation MAC Sublayer Addressing Prepared by: Gopineedi Chandana (1741120) Harshita COMPUTER NETWORKS [BCA 433] Presentation MAC Sublayer Addressing Prepared by: Gopineedi Chandana (1741120) Harshita](https://slidetodoc.com/presentation_image_h2/734859f583d124859d8b6919662aff02/image-1.jpg)
COMPUTER NETWORKS [BCA 433] Presentation MAC Sublayer Addressing Prepared by: Gopineedi Chandana (1741120) Harshita (1741123) Rashi Khandelwal (1741141) Mission Christ University is a nurturing ground for an individual’s holistic development to make effective Vision Excellence and Service Core Values Faith in God | Moral Uprightness Love of Fellow Beings | Social Responsibility 1

Christ University Contents 1. Introduction 2. MAC Address 3. Types of MAC addresses 4. Function of MAC Sub-layer 5. Taxonomy MAC protocols 6. Controlled Access Reservation, Polling and Token Passing 1. Channelization FDMA, TDMA, CDMA Excellence and Service 2
Christ University Introduction ● In IEEE 802 LAN/MAN standards, the data link layer, i. e. , layer 2 of the OSI model is divided into two sublayers : ● ○ The medium access control (MAC) sublayer ○ The logical link control (LLC) or data link control (DLC) Logical Link Control: It deals with protocols, flow-control, error control and all issues common to both point-to-point and broadcast links. ● Media Access Control: It deals with actual control of media issues specific to broadcast links only. ● We separate these two types of links at the data-link layer Excellence and Service 3
Christ University Media Access Control address ● A MAC address of a device is a unique identifier embedded to a network interface card (NIC) during the time of manufacturing for communications ● MAC address is used by Media Access Control (MAC) sublayer of Data-Link Layer. MAC Address is word wide unique, since millions of network devices exists and we need to uniquely identify each ● MAC Address is also known as Physical Address, Burned-in address (BIA), Ethernet hardware address (EHA) or Hardware address of a network device ● MAC Address is a 12 -digit hexadecimal number (6 -Byte binary number), represented by Colon. Hexadecimal notation Excellence and Service 4
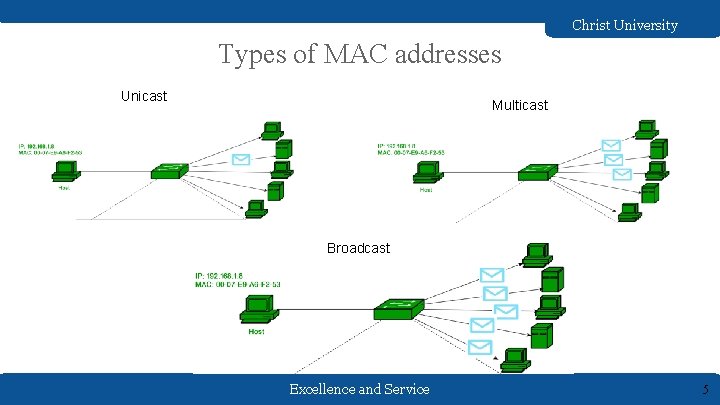
Christ University Types of MAC addresses Unicast Multicast Broadcast Excellence and Service 5
Christ University Functions of MAC Sublayer 1. Provides control abstraction 2. Provides flow control and multiplexing for transmission media 3. Controlling when data is sent and when to wait 4. Responsible for compensating for congestion and collisions 5. Protection against errors 6. Receive/transmit normal frames and discard malformed frames 7. Prepend(tx)/remove(rx) preamble, SFD (start frame delimiter) and padding Excellence and Service 6
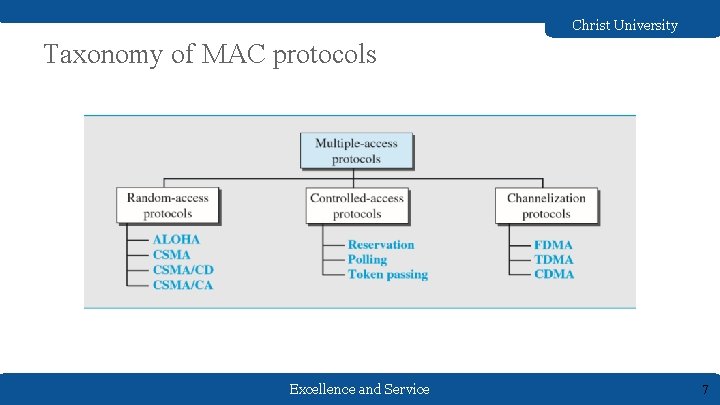
Christ University Taxonomy of MAC protocols Excellence and Service 7

Christ University Controlled Access In controlled access, the stations consult one another to find which station has the right to send. A station cannot send unless it has been authorized by other stations. There are three control access protocols : ● Reservation ● Polling ● Token passing Excellence and Service 8
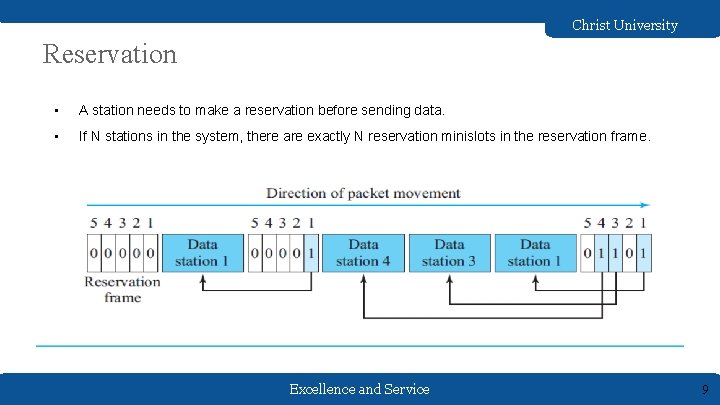
Christ University Reservation • A station needs to make a reservation before sending data. • If N stations in the system, there are exactly N reservation minislots in the reservation frame. Excellence and Service 9
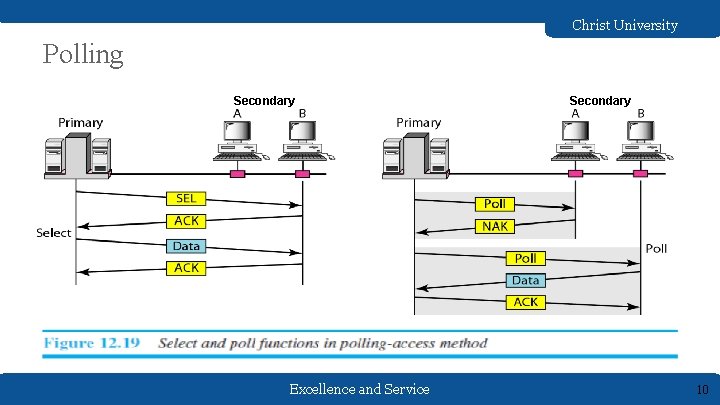
Christ University Polling Secondary Excellence and Service Secondary 10

Christ University • Polling works with topologies in which one device is designated as a primary station and the other devices are secondary stations. • All data exchanges must be made through the primary device even when the ultimate destination is a secondary device. • Primary device controls the link initiator of a session • Secondary devices - follows the instructions of primary device. • Uses poll and select functions to prevent collisions. • Drawback - If the primary station fails, the system goes down. Excellence and Service 11
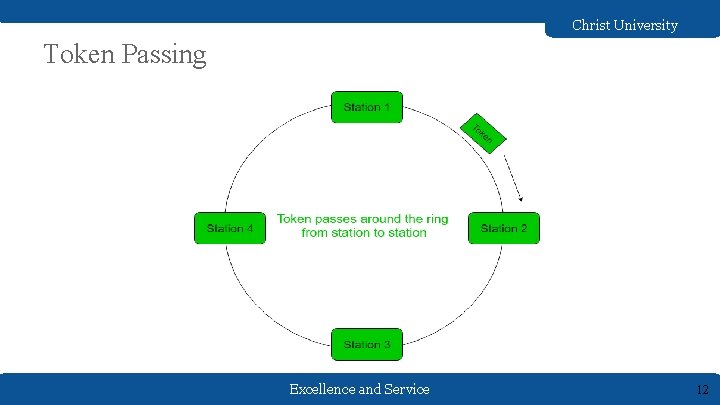
Christ University Token Passing Excellence and Service 12
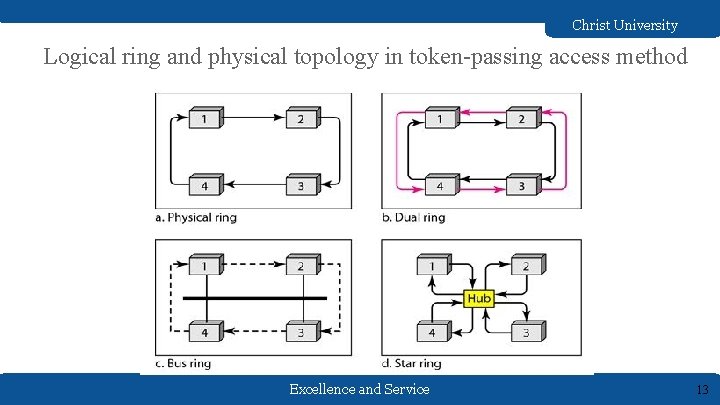
Christ University Logical ring and physical topology in token-passing access method Excellence and Service 13

Christ University Channelization Protocols Channelization (or channel partition, as it is sometimes called) is a multiple-access method in which the available bandwidth of a link is shared in time, frequency, or through code, among different stations. Three channelization protocols ● FDMA(Frequency Division Multiple Access) ● TDMA(Time Division Multiple Access) ● CDMA (Code Division Multiple Access) Excellence and Service 14
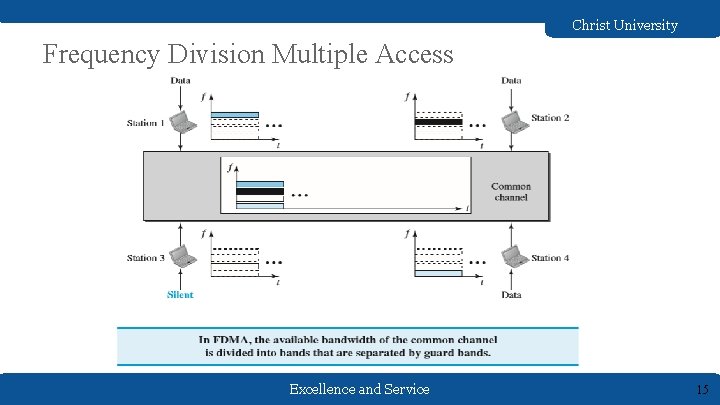
Christ University Frequency Division Multiple Access Excellence and Service 15
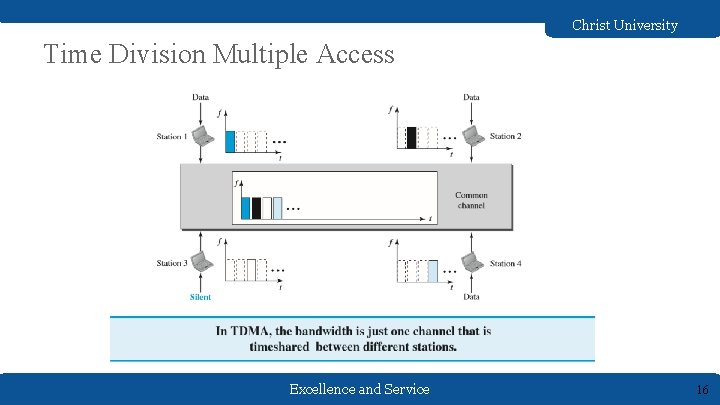
Christ University Time Division Multiple Access Excellence and Service 16
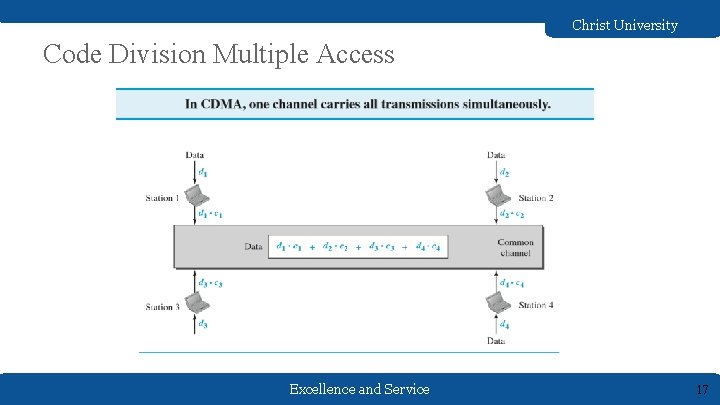
Christ University Code Division Multiple Access Excellence and Service 17
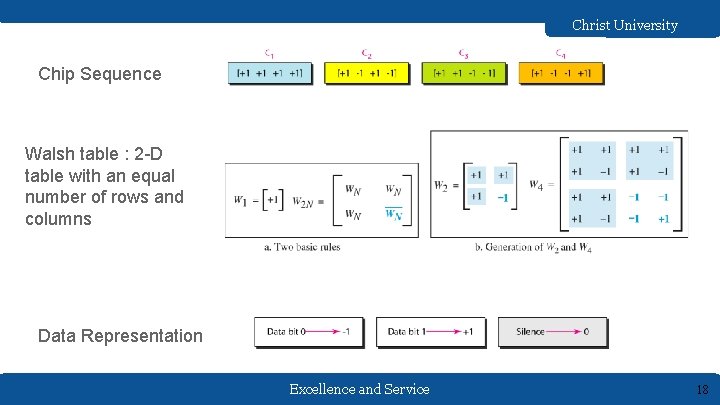
Christ University Chip Sequence Walsh table : 2 -D table with an equal number of rows and columns Data Representation Excellence and Service 18
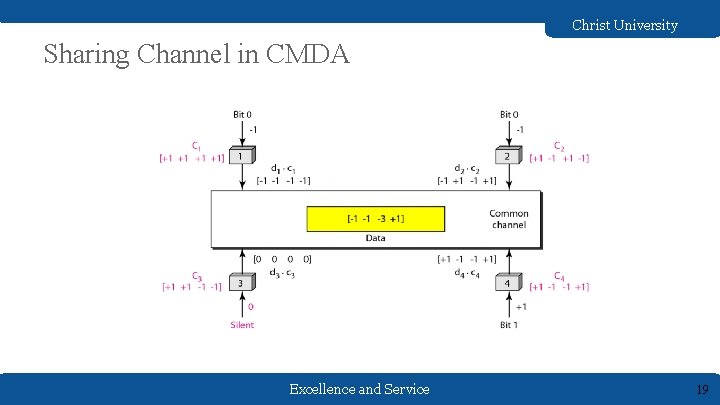
Christ University Sharing Channel in CMDA Excellence and Service 19
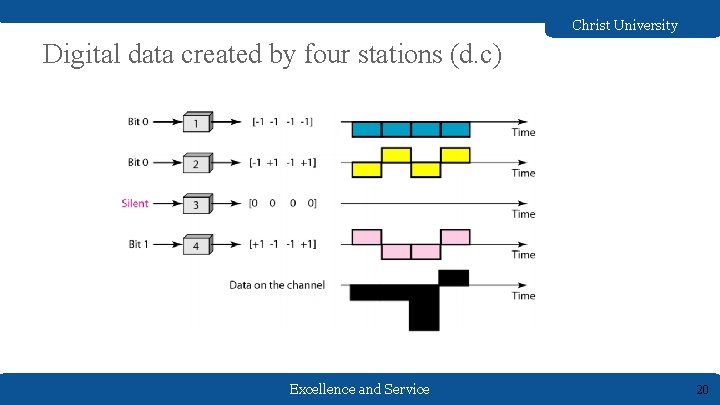
Christ University Digital data created by four stations (d. c) Excellence and Service 20
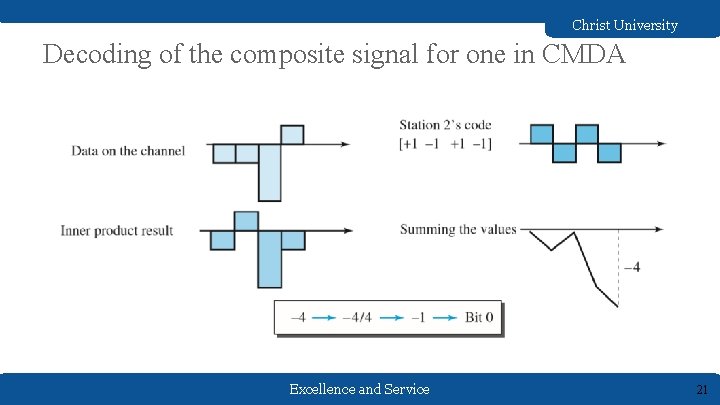
Christ University Decoding of the composite signal for one in CMDA Excellence and Service 21

Christ University Questions Covered Questions Marks Illustrate about Reservation, Polling and Token passing. 10. 0 Describe and distinguish between FDMA and CDMA. 10. 0 Explain channelization. Give valid examples of FDMA, TDMA, CDMA. 10. 0 What is a controlled access? Explain three protocols used in controlled access with valid examples. 10. 0 Excellence and Service 22

Christ University THANK YOU Excellence and Service 23
- Slides: 23