Computer Networks Architectures and Protocols Flood Routing Jos








- Slides: 31

Computer Networks Architectures and Protocols Flood Routing José Legatheaux Martins Departamento de Informática da FCT/UNL 1

Lecture Outline • Switch protocols and mechanisms – Self learning of the switch table – Spanning trees – Spanning tree protocol • Spanning Trees and Virtual LANs (VLANs) • Motivation to SDN 2

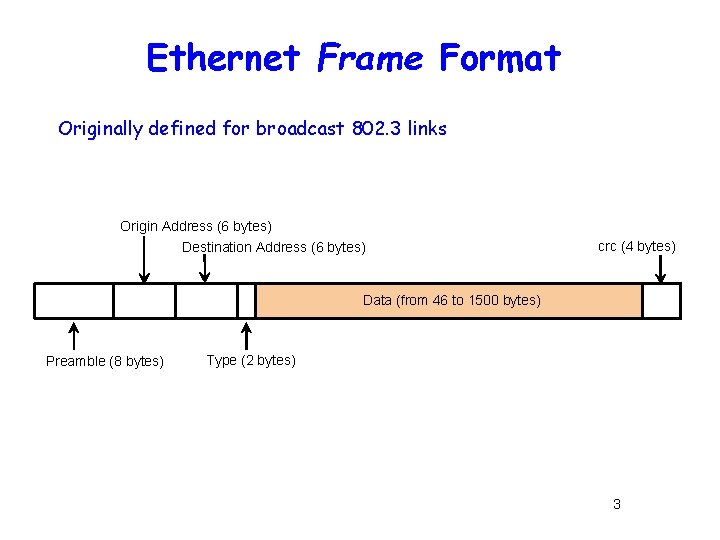
Ethernet Frame Format Originally defined for broadcast 802. 3 links Origin Address (6 bytes) Destination Address (6 bytes) crc (4 bytes) Data (from 46 to 1500 bytes) Preamble (8 bytes) Type (2 bytes) 3

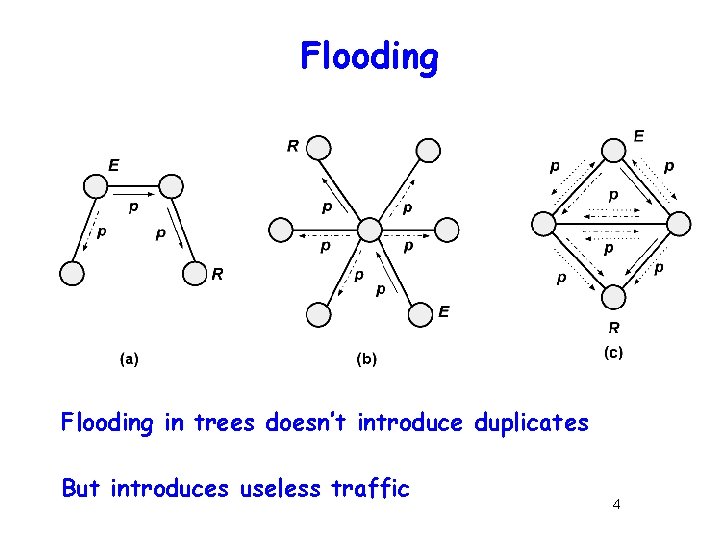
Flooding in trees doesn’t introduce duplicates But introduces useless traffic 4

Ethernet Networks 5

Flood Optimization • Switch filters packets – Frames are only forwarded to the necessary segments • Learning by the reverse path – If there is one only path between two endpoints – The origin end-point is reachable by the interface from where come the packet with its sender MAC address 6

Switch Mac Address Table • Switch mac address table – – Maps mac addresses to interfaces Idealy should be constructed dynamically No need to manually manage it Adapts as end-systems come and go • Switch forward frames selectively – Forward frames only on segments that need it 7

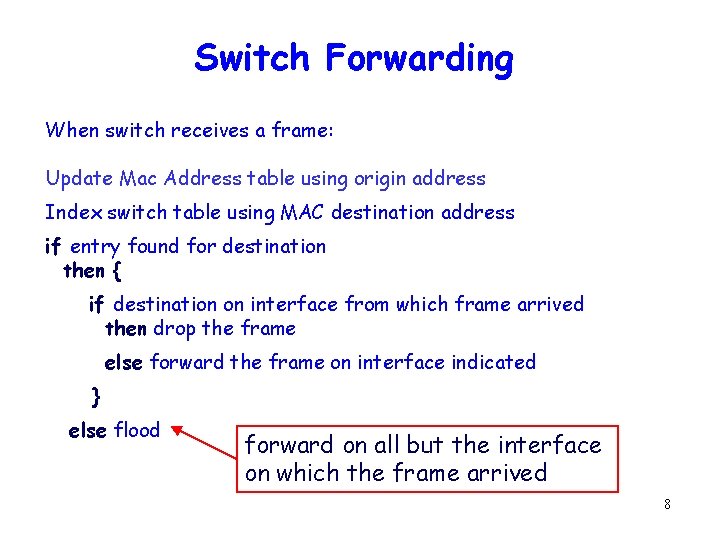
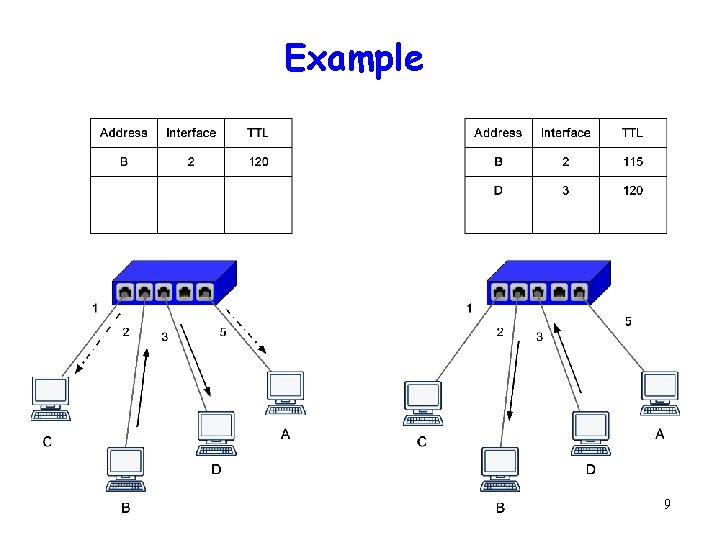
Switch Forwarding When switch receives a frame: Update Mac Address table using origin address Index switch table using MAC destination address if entry found for destination then { if destination on interface from which frame arrived then drop the frame else forward the frame on interface indicated } else flood forward on all but the interface on which the frame arrived 8

Example 9

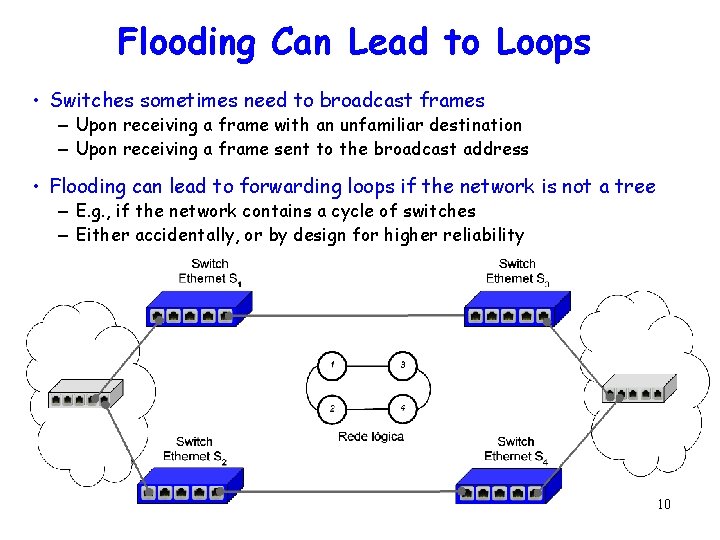
Flooding Can Lead to Loops • Switches sometimes need to broadcast frames – Upon receiving a frame with an unfamiliar destination – Upon receiving a frame sent to the broadcast address • Flooding can lead to forwarding loops if the network is not a tree – E. g. , if the network contains a cycle of switches – Either accidentally, or by design for higher reliability 10

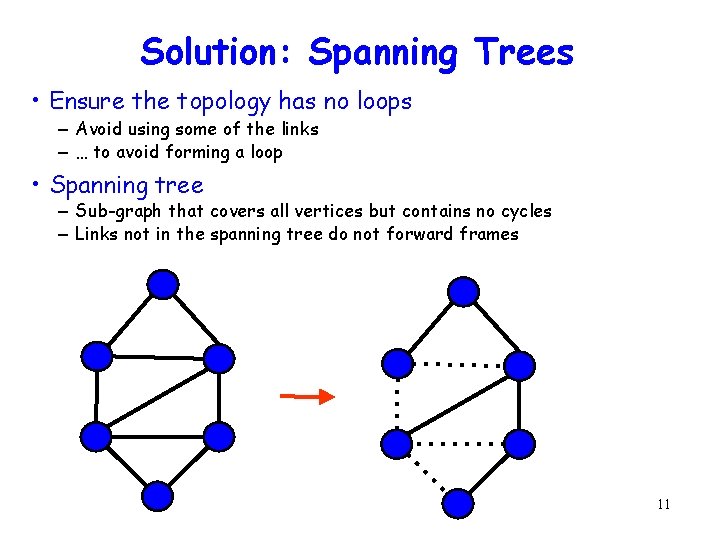
Solution: Spanning Trees • Ensure the topology has no loops – Avoid using some of the links – … to avoid forming a loop • Spanning tree – Sub-graph that covers all vertices but contains no cycles – Links not in the spanning tree do not forward frames 11

Constructing a Spanning Tree • Need a distributed algorithm – Switches cooperate to build the spanning tree – … and adapt automatically when failures occur • Key ingredients of the algorithm – Switches need to elect a “root” • The switch with the smallest identifier – Each switch identifies if its interface is on the shortest path from the root • And excludes it from the tree if not – Messages (Y, d, says X) • From node X • Claiming Y is the root • And the distance is d 12

Steps in Spanning Tree Algorithm • Initially, each switch thinks it is the root – Switch sends a message out every interface – … identifying itself as the root with distance 0 – Example: switch X announces (X, 0, X) • Switches update their view of the root – Upon receiving a message, check the root id – If the new id is smaller, start viewing that switch as root • Switches compute their distance from the root – Add 1 (or K) to the distance received from a neighbour – Identify interfaces not on a shortest path to the root – … and exclude them from the spanning tree 13

Algorithm • When a switch receives a message, it uses its sender as the path to the root – If it identifies a root with a smaller ID, or – If it identifies the same root but with a shorter distance, or – If root ID and distance are equal, but the sender has a smaller ID, or – If everything is equal but port ID has a smaller ID • Additionally, a switch that realizes that it is not the root, stops generating new messages and only relays the received ones after updating to all neighbours (even if it is removed from the tree) • In each link, the port closer to the root becomes the designated port and it forwards frames (if at the same distance, the one of the switch with smaller ID, or if 14 both are equal, the port with smaller port id)

Robust Spanning Tree Algorithm • Algorithm must react to failures – Failure of the root node • Need to elect a new root, with the next lowest identifier – Failure of other switches and links • Need to recompute the spanning tree • Root switch continues sending messages – Periodically reannouncing itself as the root (A, 0, A) – Other switches continue forwarding messages • Detecting failures through timeout (soft state!) – Switch waits to hear from others – Eventually times out and claims to be the root 15

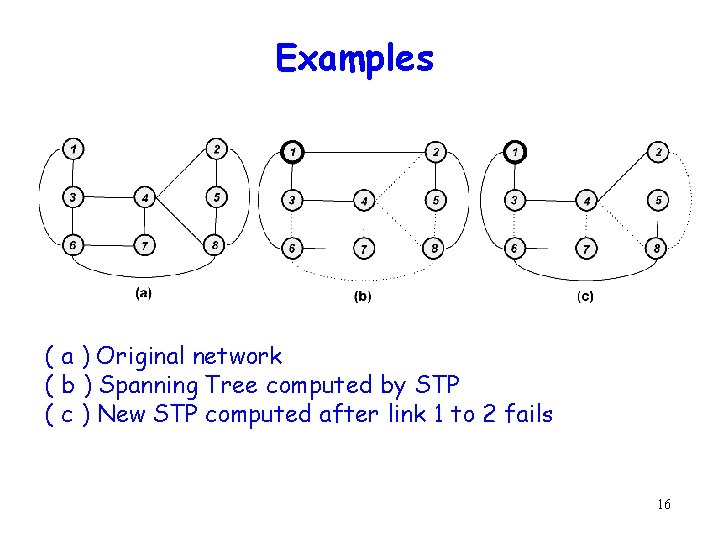
Examples ( a ) Original network ( b ) Spanning Tree computed by STP ( c ) New STP computed after link 1 to 2 fails 16

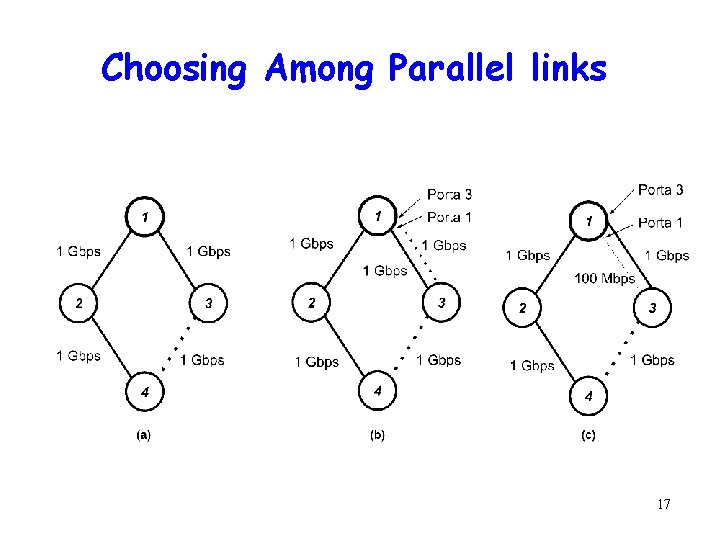
Choosing Among Parallel links 17

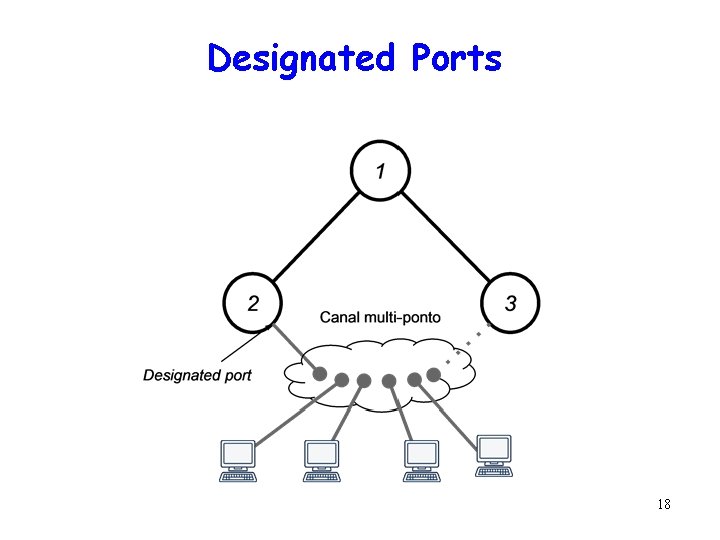
Designated Ports 18

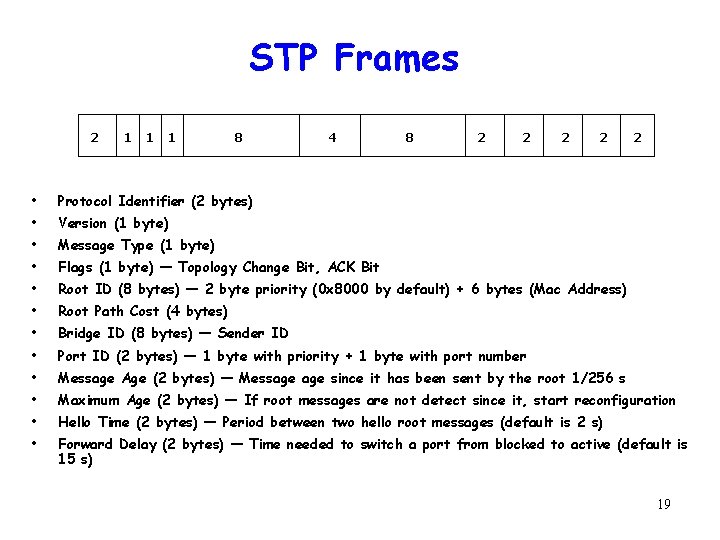
STP Frames 2 1 1 1 8 4 8 2 2 2 • Protocol Identifier (2 bytes) • Version (1 byte) • Message Type (1 byte) • Flags (1 byte) — Topology Change Bit, ACK Bit • Root ID (8 bytes) — 2 byte priority (0 x 8000 by default) + 6 bytes (Mac Address) • Root Path Cost (4 bytes) • Bridge ID (8 bytes) — Sender ID • Port ID (2 bytes) — 1 byte with priority + 1 byte with port number • Message Age (2 bytes) — Message since it has been sent by the root 1/256 s • Maximum Age (2 bytes) — If root messages are not detect since it, start reconfiguration • Hello Time (2 bytes) — Period between two hello root messages (default is 2 s) • Forward Delay (2 bytes) — Time needed to switch a port from blocked to active (default is 15 s) 19

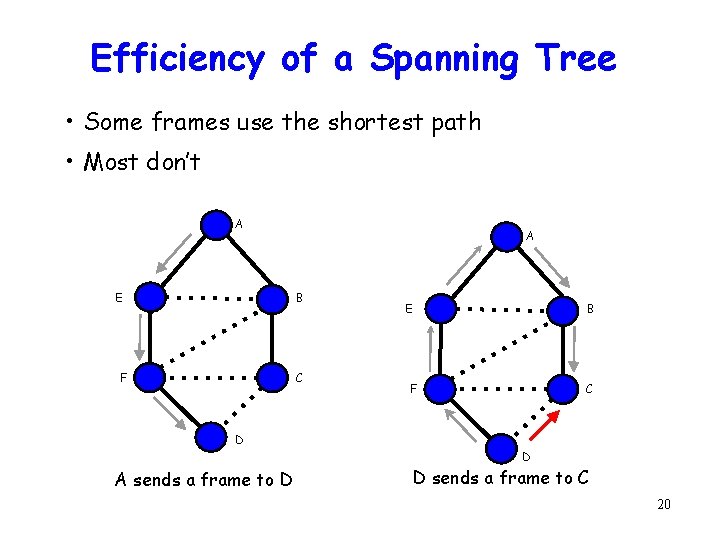
Efficiency of a Spanning Tree • Some frames use the shortest path • Most don’t A E A B C F E B C F D D A sends a frame to D D sends a frame to C 20

Several LANs Require Lots of Switches • Many switches and parallel cabling – Each logical LAN needs a different switch – Needs as many as at least one different switch per LAN • In large buildings with many LANs – The number of required switches explodes • In a data centre one faces a similar problem – The number of required switches explodes since we need a different LAN per tenant 21

How Many Networks in an Institution? • Security – – Wireless LANs are often completely open Any interface card can be put into “promiscuous” mode … and get a copy of part of the traffic and can send packets So, isolating traffic on separate LANs improves security • Load – – – – Some LANs are more heavily used than others E. g. if a group of computers broadcast often E. g. , researchers running experiments get out of hand … can saturate their own segment and not the others Wireless LANs should be independent Plus, there may be natural locality of communication E. g. , traffic between people in the same research group 22

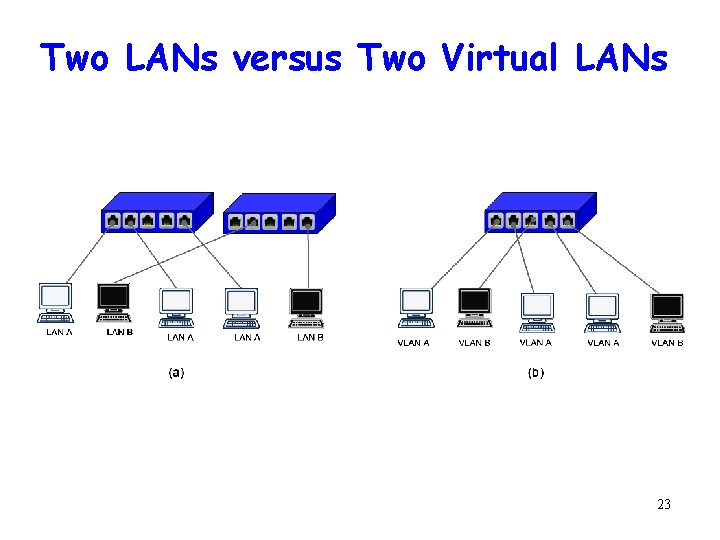
Two LANs versus Two Virtual LANs 23

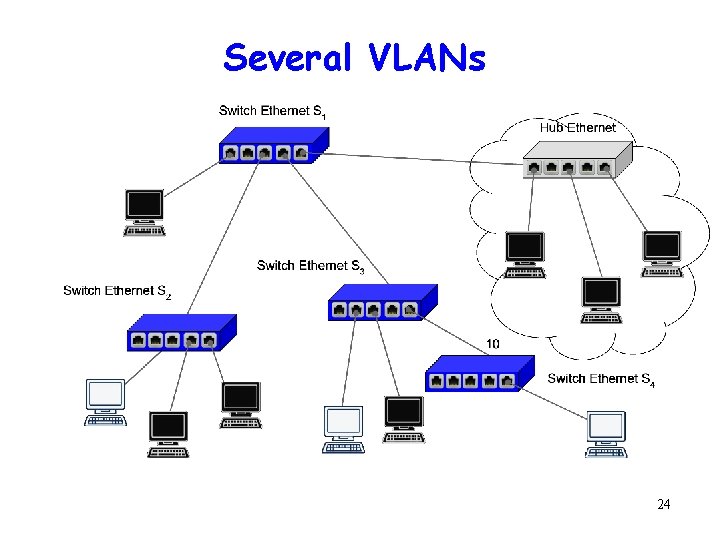
Several VLANs 24

Making VLANs Work • Switches need configuration tables – Saying which VLANs are accessible via which interfaces • Approaches to mapping to VLANs – Each interface has one or more VLAN colour • Only works if all hosts on same segment belong to same VLAN – Each MAC address has a VLAN colour • Useful when hosts on same segment belong to different VLANs • Useful when hosts move from one physical location to another • Changing the Ethernet header – Adding a field for a VLAN tag – Implemented on the bridges/switches – … but can still interoperate with old Ethernet cards 25

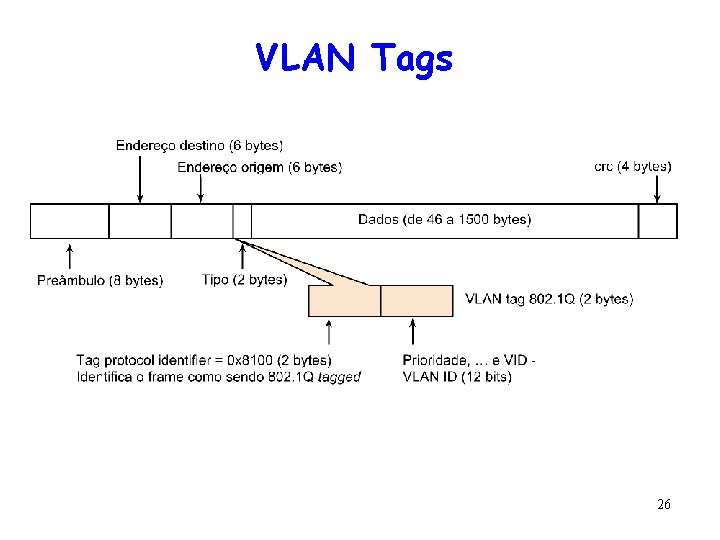
VLAN Tags 26

Making VLANs Work (continued) • The VLANs standard: 802. 1 Q • The Spanning Tree Protocol Standard: 802. 1 D • Each VLAN has its own Spanning Tree • VLANS can be interconnected by routers 27

Pros and Cons of VLANs • Pros: very flexible allocation of interfaces or hosts to different VLANs, based on switching, which increases domain, role and traffic separation • Pros: compatible with automatic host configuration • Cons: STP = poor network utilization • Cons: STP = some paths are not the shorter ones • Cons: Fine protection policies requires the explosion of the number of VLANs • Cons: flooding doesn’t scale, we still need routing to scale 28

Evolution of Switched Networks • Short Term solutions – Spanning trees per VLAN and Pruned Spanning Trees – Improved versions of the Spanning Tree Protocol – Link aggregation and load balancing – IGMP snooping – ARP and DHCP Proxies – Lots of proprietary extensions and lots of hacks • Long Term Evolution – Software Defined Networks 29

Conclusion • Shuttling data from one link to another – Bits, frames, packets, … – Switches, routers, … • Key ideas in flooding switches –Self learning of the switch table –Spanning trees –Virtual LANs (VLANs) • Key open problems in switches – How to increase the utilization of the network – How to segregate different domains – How to allow greater flexibility and easy management 30

Optional Reading Radia Perlman, “An Algorithm for Distributed Computation of Spanning Trees in a Extended LAN, ” Proceedings of the 9 th Data Communications Symposium, pp. 124 -133, September 1985 31