Computer Networks and Internets with Internet Applications 4






















- Slides: 48

Computer Networks and Internets with Internet Applications, 4 e By Douglas E. Comer Lecture Power. Points By Lami Kaya, LKaya@ieee. org © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

Chapter 13 WAN Technologies And Routing © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

Topics Covered • • • 13. 1 Introduction 13. 2 Large Networks And Wide Areas 13. 3 Packet Switches 13. 4 Forming A WAN 13. 5 Store And Forward 13. 6 Physical Addressing In A WAN 13. 7 Next-Hop Forwarding 13. 8 Source Independence 13. 9 Relationship Of Hierarchical Addresses To Routing © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

Topics Covered (cont) • • 13. 10 Routing In A WAN 13. 11 Use Of Default Routes 13. 12 Routing Table Computation 13. 13 Shortest Path Computation In A Graph 13. 14 Distributed Route Computation 13. 15 Distance Vector Routing 13. 16 Link-State Routing (SPF) 13. 17 Example WAN Technologies – – – 13. 17. 1 13. 17. 2 13. 17. 3 13. 17. 4 13. 17. 5 ARPANET X. 25 Frame Relay SMDS ATM © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 1 Introduction This chapter • considers how those basic technologies can be used to build a NW that spans a large area • describes the basic components used to build a packet switching (PS) system that can span a large area • explains the fundamental concept of routing and shows how routing is used in such NW – a later chapter extends the discussion of routing to the Internet © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 2 Large Networks And Wide Areas • In general, a NW is classified into one of three broad categories depending on the size – LAN – MAN – WAN • The key issue that separates WAN technologies from LAN technologies is – Scalability – a WAN must be able to grow as needed to connect many sites • A technology is not classified as a WAN – unless it can deliver reasonable performance for large size NW – It must provide sufficient capacity to permit the computers to communicate simultaneously © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 3 Packet Switches (1) How can a WAN scale to handle many computers? • The network itself must be able to grow • Instead of using a point-to-point (PTP) leased data circuit that connects one computer directly to another, – a WAN is constructed from many switches to which individual computers connect • The initial size of a WAN is determined by the number of sites and the number of computers connected – Additional switches can be added as needed to connect additional sites or additional computers © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

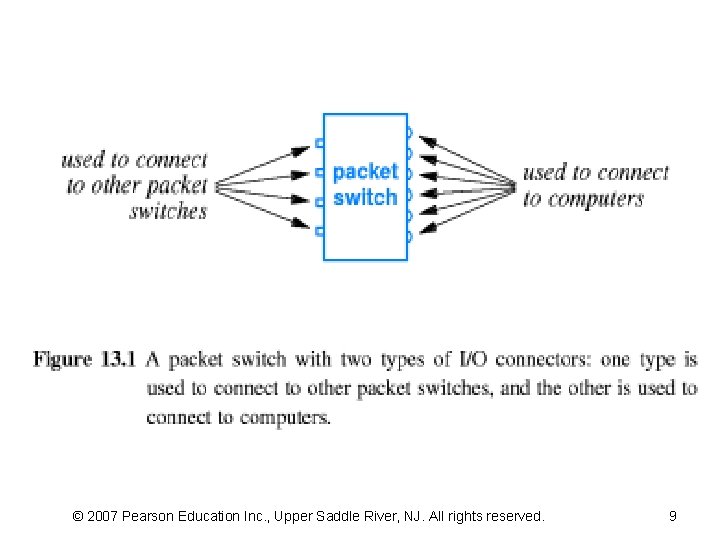
13. 3 Packet Switches (2) • The basic electronic switch used in a WAN – called a packet switch – It moves complete packets from one connection to another. • Each PS is a small computer, special HW – has a processor, memory, I/O devices used to send and receive • Figure 13. 1 illustrates that a packet switch • Almost every form of PTP communication has been used to build a WAN – Copper cables, optical fibers, microwaves, and satellite channels © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 9

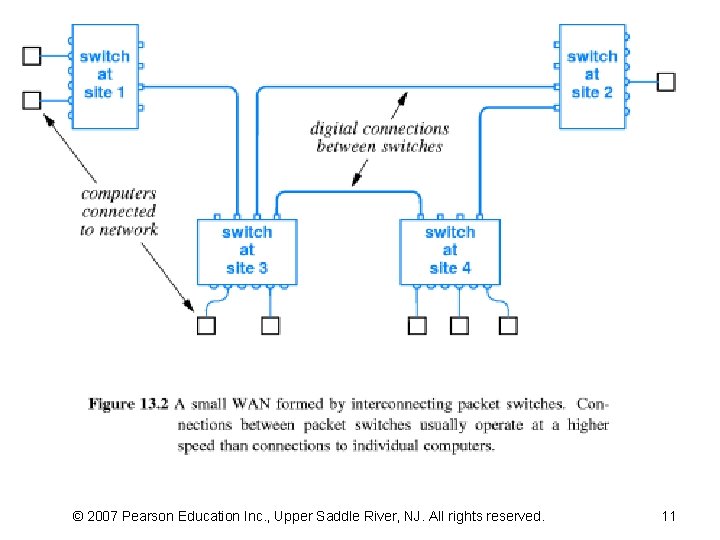
13. 4 Forming A WAN • Packet switches are interconnected to form a WAN • A switch usually has multiple I/O connectors – making it possible to form many different topologies and to connect multiple computers • Figure 13. 2 illustrates one possible way to form a WAN • As the figure shows, a WAN need not be symmetric • The interconnections among switches and the capacity of each connection is chosen – to accommodate the expected traffic – to provide redundancy in case of failure © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 11

13. 5 Store And Forward • Unlike a shared LAN that allows only one pair of computers to exchange a frame at a given time – a WAN permits many computers to send packets simultaneously • The fundamental paradigm used with wide area PS systems is – “store and forward” switching • To perform store and forward, a PS must buffer packets in memory – the store operation occurs when a packet arrives – the forward operation occurs next • the processor examines the packet • determines over which interface it should be sent • and starts the output hardware device to send the packet • if multiple packets must be sent to the same output device – the PS can hold packets in memory, until the output device is ready © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

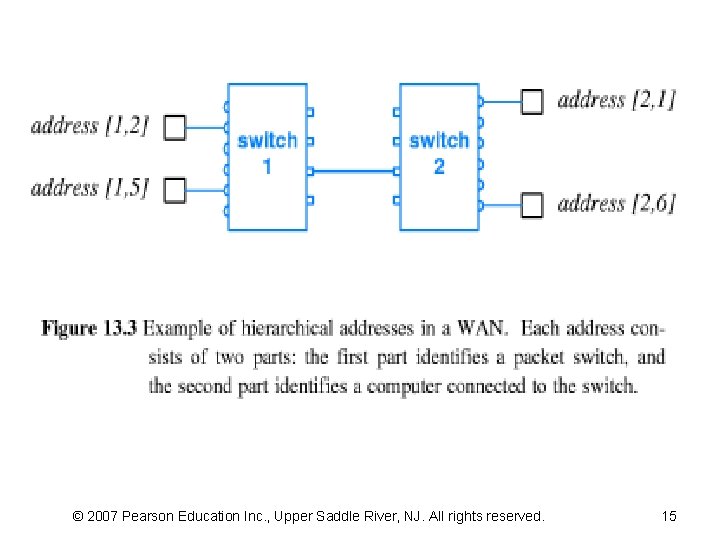
13. 6 Physical Addressing In A WAN • Each WAN technology defines the exact frame format • Each computer connected to a WAN is assigned a PA – the sender must supply the destination's address • Many WANs use a hierarchical addressing – divides an address into multiple parts – the simplest hierarchical scheme partitions an address into two • the first part identifies a PS • and the second part identifies a computer attached to that PS • Figure 13. 3 shows two-part hierarchical addresses • An address is represented as a single binary value – Some bits of the binary value used to represent the first part – Some other bits used to represent the second part – users and application programs can treat the address as a whole • they do not need to know that addresses are assigned hierarchically © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

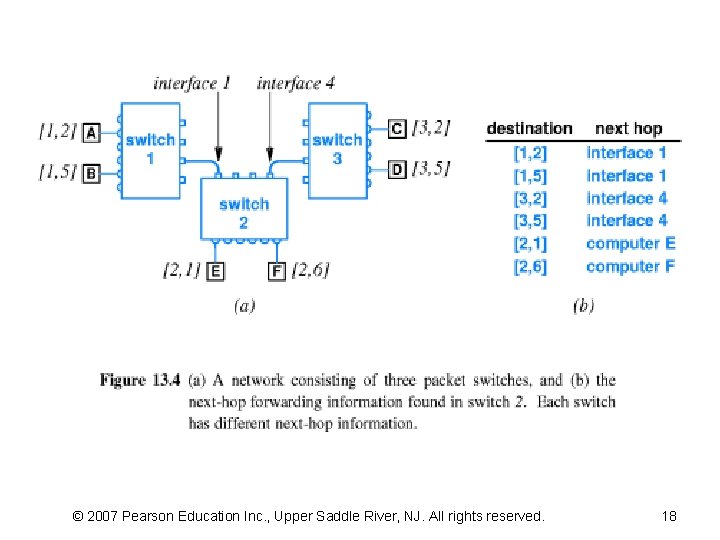
13. 7 Next-Hop Forwarding • A PS must choose an outgoing path – If the packet is for one of the computers attached directly, • the switch forwards the packet to the computer – If the packet is destined for a computer attached to another PS • the packet must be forwarded further that leads to the switch • a PS uses the destination address stored • A PS does not keep complete information about how to reach all possible destinations – A switch simply sends to next processing point • Called “next-hop forwarding” – The concept is analogous to the way airlines list flights – Figure 13. 4 illustrates next-hop forwarding in a PS NW – PS usually assigns each interface a small integer, “port #” © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 15

13. 8 Source Independence • Next-hop forwarding depends only on the destination – known as “source independence” • Airport analogy: forwarding in an airport is source independent • because the set of outgoing flights does not depend on the city from which a passenger arrived at the airport • Source independence allows the forwarding mechanism – to be compact and efficient – Because all packets follow the same path • only one table is required – Because forwarding does not use source information • only the destination address needs to be extracted from a packet – Furthermore, a single mechanism handles forwarding uniformly • packets that originate on directly connected computers • and packets that arrive from other PS use the same mechanism © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 9 Relationship Of Hierarchical Addresses To Routing (1) • The table used to store next-hop information is commonly called a – routing table (RT) • The process of forwarding a packet to its next hop is known as – routing • The advantage of two-part hierarchical addressing should be apparent from the RT in Figure 13. 4 – Observe that more than one entry contains the same next-hop value – all destination addresses that have an identical first part will be forwarded to the same PS • Thus, a PS only needs to examine the first part of a hierarchical address © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 18

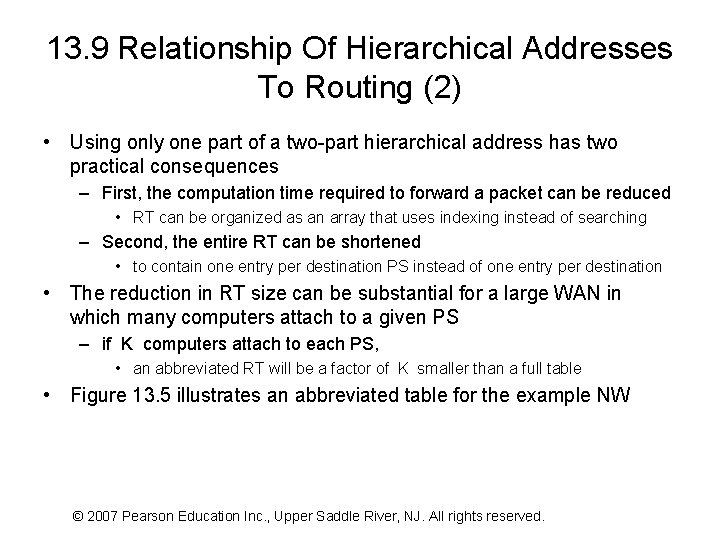
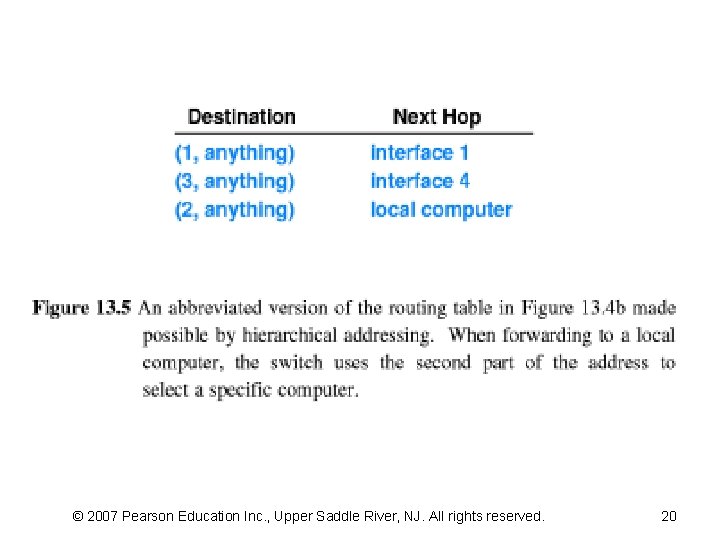
13. 9 Relationship Of Hierarchical Addresses To Routing (2) • Using only one part of a two-part hierarchical address has two practical consequences – First, the computation time required to forward a packet can be reduced • RT can be organized as an array that uses indexing instead of searching – Second, the entire RT can be shortened • to contain one entry per destination PS instead of one entry per destination • The reduction in RT size can be substantial for a large WAN in which many computers attach to a given PS – if K computers attach to each PS, • an abbreviated RT will be a factor of K smaller than a full table • Figure 13. 5 illustrates an abbreviated table for the example NW © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 20

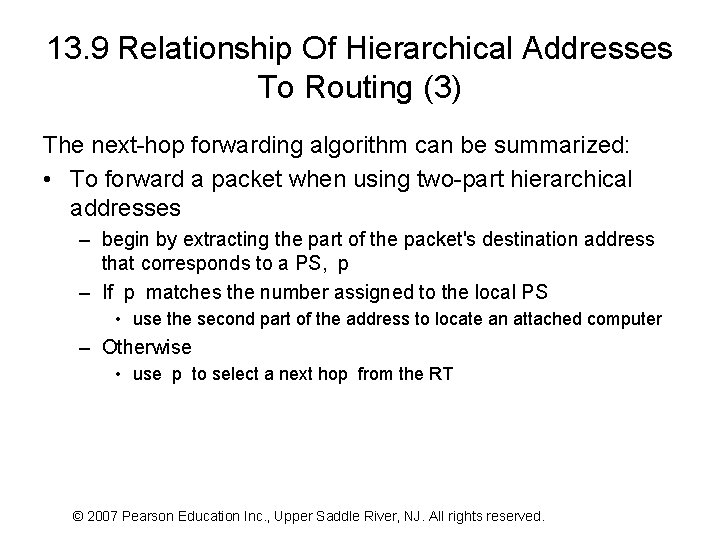
13. 9 Relationship Of Hierarchical Addresses To Routing (3) The next-hop forwarding algorithm can be summarized: • To forward a packet when using two-part hierarchical addresses – begin by extracting the part of the packet's destination address that corresponds to a PS, p – If p matches the number assigned to the local PS • use the second part of the address to locate an attached computer – Otherwise • use p to select a next hop from the RT © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 10 Routing In A WAN (1) • PS having computers attached “interior switches” • PS not having computers attached “exterior switches” • Both interior and exterior PS must have a RT and both types must forward packets • Values in the RT must guarantee the following: – Universal routing • The RT in a switch must contain a next-hop route for each possible destination – Optimal routes • In a switch, the next-hop value in the RT for a given destination must point to the shortest path to the destination © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

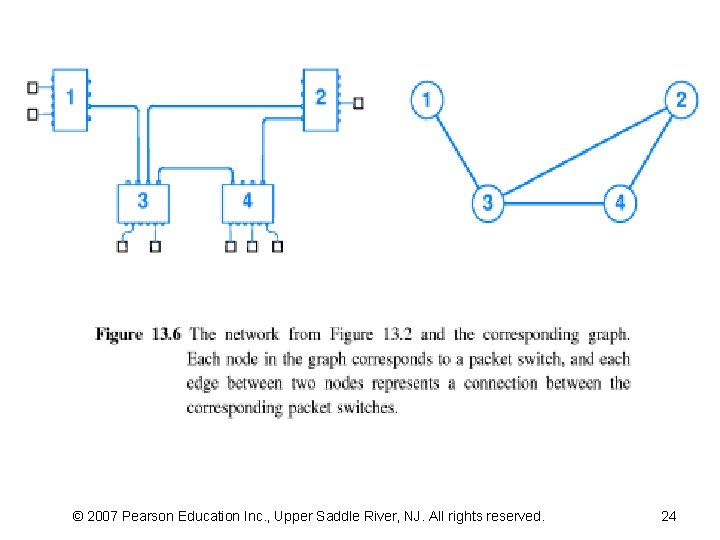
13. 10 Routing In A WAN (2) • The easiest way to think about routing in a WAN is – to imagine a graph that models the network • Each node in the graph corresponds to a PS in the NW – If the NW contains a direct connection between a pair of PS, • graph contains an edge or link between the corresponding nodes • Relationship between graph theory and NW is strong – a machine attached to a NW is often called a NW node • A serial data circuit connecting two machines – is often called a “link” • Figure 13. 6 shows a WAN and the corresponding graph © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 24

13. 10 Routing In A WAN (3) • A graph representation of a network is useful – Because a graph represents PS without attached computers • a graph shows the essence of a NW – A graph can be used to compute and understand next-hop routes • Figure 13. 7 shows the RT that correspond to Figure 13. 6 © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 26

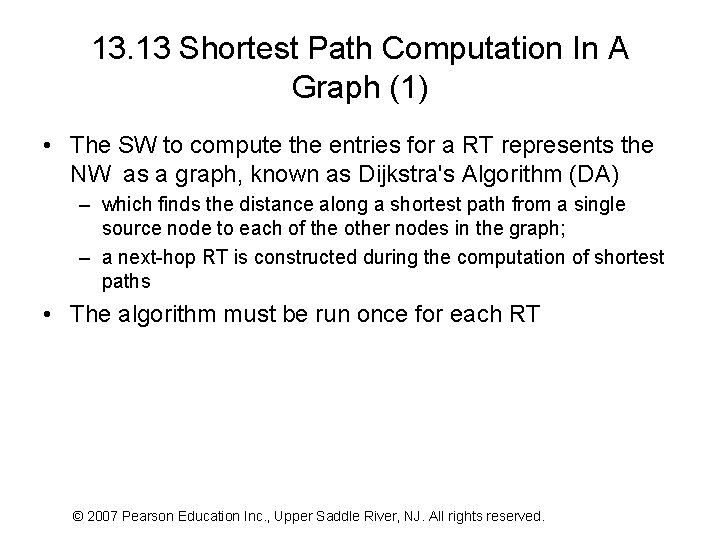
13. 11 Use Of Default Routes • Although hierarchical addressing reduces the size of the RT – by removing duplicate routes for individual computers • abbreviated RT still contains many entries with the same next hop • Most WAN systems include a mechanism that can be used to eliminate the common case of duplicate entries – Called a “default route” or a “default routing table entry” • the mechanism allows a single entry in a RT to replace a long list of entries that have the same next-hop value – Only one default entry is allowed in any RT, • and the entry has lower priority than other entries – If the forwarding mechanism does not find an explicit entry • it uses the default entry, if exist (optional) • Figure 13. 8 shows how the RT in Figure 13. 7 might be revised © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 12 Routing Table Computation (1) • How is a routing table constructed? • Manual computation suffices for trivial examples, but – such methods are impractical in large NW s – Consequently, software is used to compute RT entries There are two basic approaches • Static routing – A program computes and installs routes when a PS boots; – the routes do not change • Dynamic routing – A program builds an initial RT when a PS boots; – the program then alters the RT as conditions in the NW change © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 12 Routing Table Computation (2) Each type of routing has advantages and disadvantages • The chief advantages of static routing – are simplicity and low NW overhead • The chief disadvantage – is inflexibility -- static routes cannot be changed easily • Most NW s use dynamic routing because – it allows the NW to handle problems automatically – For example, programs can monitor traffic in the NW as well as the status of the NW hardware – The programs can then modify routes to accommodate failure • Because large NW s are designed with redundant connections to handle occasional HW failures © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 13 Shortest Path Computation In A Graph (1) • The SW to compute the entries for a RT represents the NW as a graph, known as Dijkstra's Algorithm (DA) – which finds the distance along a shortest path from a single source node to each of the other nodes in the graph; – a next-hop RT is constructed during the computation of shortest paths • The algorithm must be run once for each RT © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

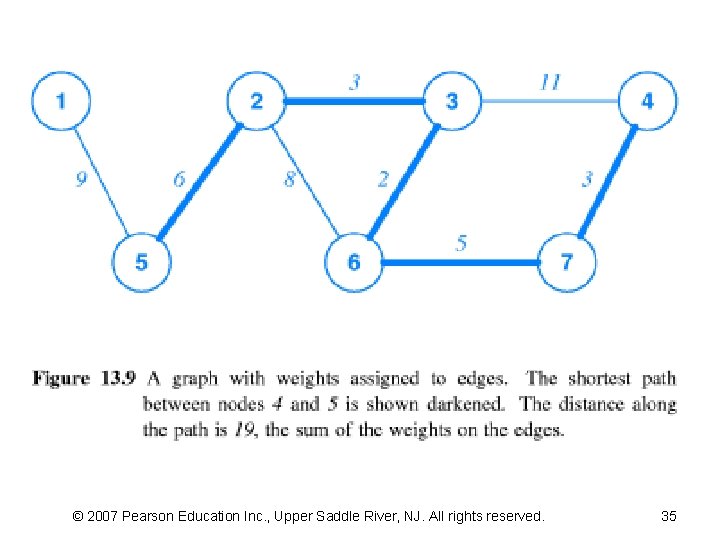
13. 13 Shortest Path Computation In A Graph (2) • DA is popular because it can be used with various definitions of “shortest path” – it does not require edges to represent geographic distance – it allows each edge to be assigned a value, called a “weight” – and defines the distance between two nodes to be the sum of the weights along a path between the nodes • DA computes shortest paths in a graph by using weights on edges as a measure of distance – A path with the fewest number of edges may not be the path with least weight • Figure 13. 9 illustrates the concept by showing © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 32

13. 13 Shortest Path Computation In A Graph (3) • DA maintains a set of nodes, S – for which the minimum distance and next hop have not been computed • The set is initialized to all nodes except the source • DA then iterates – On each iteration, it selects and deletes a node from S that has the least distance from the source – As it deletes node u , it examines the current distance from the source to each neighbor of u that remains in the set – If a path from the source through u has less weight than the current path • it updates the distance to the neighbor – After all nodes have been deleted from S • it will have computed the minimum distance to each node and a correct next-hop RT for all possible paths © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 13 Shortest Path Computation In A Graph (4) • DA needs three data structures to store: – The current distance to each node, – the next hop for the shortest path, – and information about the remaining set of nodes • Nodes can be numbered from 1 to n as Figure 13. 9 demonstrates – Doing so makes the implementation efficient because it allows a node number to be used as an index into a data structure • DA uses weight (i, j) as a function that returns the weight of the edge from node i to node j • Function weight is assumed to return a reserved value infinity if no edge exists from node i to node j – In practice, any value can be used to represent infinity provided the value is larger than the sum of weights along any path in the graph – One way to generate a value infinity consists of adding one to the sum of all weights on all edges © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

© 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved. 35

13. 13 Shortest Path Computation In A Graph (5) • Allowing arbitrary weights to be assigned to edges of a graph means – one algorithm can be used with different measures of distance – Ex, some WAN technologies measure distance by counting the number of PS along a path • To use the algorithm for such technologies, – each edge in the graph is assigned a weight of 1 • In other WAN technologies – weights are assigned to reflect the capacity of connections • Some WAN technologies assign weights to implement administrative policies © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 14 Distributed Route Computation (1) • The alternative technique – is a distributed route computation • Each PS computes its RT locally, • Then sends messages across the NW to neighboring PS to inform them of the result • Each PS to send its routing information to neighbors periodically (e. g. , seconds) • After an initial startup period – each PS learns the shortest paths to all destinations – a distributed algorithm (DA) produces the same next-hop RTs as previous algorithm © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 14 Distributed Route Computation (2) • The continuous periodic messages – allow the NW to adapt if an individual PS or an individual communication link fails • After a failure – a PS stops receiving updates from the HW that failed • The switch continues receiving updates from working neighbors – and if an alternative path exists, the switch can modify its RT to avoid the failed HW © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 15 Distance Vector Routing (1) • One of the best-known algorithms for distributed route computation – distance-vector algorithm (DVA) • Messages sent from one PS to another contain pairs of values – that each specify a destination and a distance to that destination • Each link in the NW is assigned a weight • The distance to a destination is defined to be the sum of weights along the path to the destination • A PS periodically sends routing information across the NW to neighbors – Each message contains pairs of ( destination, distance ) © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 15 Distance Vector Routing (2) • When a message arrives at a PS from neighbor N – the PS examines each item in the message – and changes its RT if the neighbor has a shorter path to some destination than the path the PS has been using • Algorithm 13. 2 specifies precisely how routes are updated • DVA for route computation used each PS in a WAN • Each switch periodically sends the list its RT to all neighbors © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 16 Link-State Routing (SPF) (1) • An alternative form of distributed route computation exists – that uses a version of Algorithm 13. 1 instead of a DVA – called link-state routing (LSR) – the scheme is known as “Shortest Path First” • The name is somewhat misleading because all routing algorithms are aimed to find shortest paths • Each message carries the status of a link between two PS – and the message is broadcast to all switches • Each switch collects incoming status messages – and uses them to build a graph of the NW • Then PS uses Algorithm 13. 1 to produce a RT with itself as the source © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 16 Link-State Routing (SPF) (2) • Like a DVA, an SPF algorithm can adapt to HW failures • In addition, SPF has the advantage that all computations can be carried out simultaneously – After the status of a link changes, – all PS receive a status message, – and each switch begins computing its RT • In contrast, a DVA it requires a PS to update its RT – before sending a message to another PS © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 17 Example WAN Technologies • Many technologies have been created for experimental and production use in WAN • This section presents a few example technologies – that illustrate some of the diversity • Next chapter continues the discussion by examining fundamental communication paradigms – and showing which paradigm each technology follows © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 17. 1 ARPANET • In the late 1960 s, the Advanced Research Projects Agency (ARPA) – Sponsored by USA Department of Defense (Do. D) • A major ARPA research project developed a WAN – to determine whether PS technology could be used in battlefields – Developed network is known as the ARPANET © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 17. 2 X. 25 • The organization that sets international telephone standards, – International Telecommunications Union (ITU) • developed an WAN technology, and public carriers such as telephone companies have offered the service for many years • The ITU was formerly known as – Consultative Committee for Int. Telephone and Telegraph (CCITT) • The standard is still known as the CCITT X. 25 standard • X. 25 NW s are more popular in Europe than in the US • Each X. 25 NW consists of two or more X. 25 PS interconnected by leased lines that can send and receive packets • Although X. 25 can be used for communication between computers – the technology is expensive for the performance it delivers – and has limits on the speed at which it can deliver data © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 17. 3 Frame Relay • Frame Relay (FR) is designed to accept and deliver blocks of data – Where each block can contain up to 8 K octets of data • Motivation for the large data size arises – because the inventors designed FR service for use in bridging LAN segments • An organization with offices in two cities can obtain a FR connection for each office • To handle data from a LAN segment – a FR connection must operate at high data rates – FR running at speeds between 4 and 100 Mbps – In practice, many FR subscribers choose to use 1. 5 Mbps or 56 Kbps © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 17. 4 SMDS • • Switched Multi-megabit Data Service (SMDS) SMDS is designed to carry data SMDS is optimized to operate at the highest speeds Header in packets can require a significant amount of the available BW – To minimize header overhead, SMDS uses a small header and allows each packet to contain up to 9188 octets of data • SMDS also defines a special HW interface used to connect computers to the NW • SMDS NW s often operate at speeds faster than FR © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.

13. 17. 5 ATM • ATM had ambitious goals – it was designed to handle conventional telephone voice traffic as well as data traffic – and to serve as a local area technology as well as a wide area technology • The next chapter describes ATM in more detail © 2007 Pearson Education Inc. , Upper Saddle River, NJ. All rights reserved.