Computer Forensics Electronic Evidence Presented to ISACA Information

![The Presenter – Jim Wright James M Wright, P. E. James M. [Jim] Wright The Presenter – Jim Wright James M Wright, P. E. James M. [Jim] Wright](https://slidetodoc.com/presentation_image_h2/5a0528e8bc5a21850d3ace98022e6663/image-2.jpg)





![Collecting and Analyzing ESI – Software [cont] • FORENSIC SOFTWARE [cont] • Open Source Collecting and Analyzing ESI – Software [cont] • FORENSIC SOFTWARE [cont] • Open Source](https://slidetodoc.com/presentation_image_h2/5a0528e8bc5a21850d3ace98022e6663/image-11.jpg)



- Slides: 14

Computer Forensics & Electronic Evidence Presented to: ISACA- Information Systems Audit & Controls Association November 13, 2008 Dallas Texas James M. Wright, P. E. Principal- Wright Consulting LLC Houston, TX
![The Presenter Jim Wright James M Wright P E James M Jim Wright The Presenter – Jim Wright James M Wright, P. E. James M. [Jim] Wright](https://slidetodoc.com/presentation_image_h2/5a0528e8bc5a21850d3ace98022e6663/image-2.jpg)
The Presenter – Jim Wright James M Wright, P. E. James M. [Jim] Wright is an independent consultant in Houston Texas, who provides litigation support in the areas of Electronic Discovery and Construction Claims and Disputes. Prior to his independent practice, he was a Director for FTI Consulting in their Forensic and Litigation Consulting practice. Mr. Wright has thirty five years of broad engineering, management, consulting and litigation support experience in the oil & gas, petrochemical and energy industries, including executive and middle management, project management and engineering, expert reporting and testimony, contract dispute and claims negotiation, and a broad range of matters relating to Electronic Discovery. He is a frequently solicited speaker in conferences on Electronic Discovery and participates in various expert forums and advisory groups. Principal Wright Consulting LLC Houston, TX Tel: (281) 813 9031 Wright. Consulting@swbell. net ice University – 1972 Mech Engr. Professional Engineer, Texas 1 Mr. Wright’s practice includes Litigation Readiness/Response Planning assessments for corporations; development, negotiation and subsequent management of comprehensive Discovery Plans with a focus on cost and risk management; Expert analysis, estimating and testimony re: excess burden claims per FRCP [26[b][2][B] rules, and as 30[b][6] deponents re: litigants’ IT systems and protocols for E Discovery. Prior to FTI, Mr. Wright was Director of E Discovery at Halliburton, where he developed the E Discovery protocols for all matters, including litigation and government investigations and participated in development of Enterprise Records Management policies. As a founder of the Corporate E Discovery Forum [with 300+ members from 165+ corporations], he is well informed to the in house perspective of discovery matters. His knowledge and experience in the often complex ground level activities associated with the in house collection, processing, review and production of ESI, and his interest in facilitating the discovery process has led to his recent consideration for Special Master/Neutral Expert assignments by State and Federal Courts.

Learning Objectives • Information that can be gained from a forensic examination of computer media • Reasons why a forensic examination would be required or desired • Special knowledge or certifications required to perform a forensic examination • Differences between E-Discovery and traditional forensic examinations * The effects of all the above on Litigation 2

Agenda Electronically Stored Information - ESI • The new standard Computer Forensics Overview • What is a forensics examination? • When is a forensics examination needed? • Who performs such examinations? • How is a forensics exam performed? Computer System Basics • Hard Drives • File Systems & File Attributes • Operating System Log Files Collecting & Analyzing ESI • Collection Options & Tools • Forensic Software Electronic Evidence 3 • ESI in Litigation • Technology Options

Electronically Stored Information ESI On Dec 01, 2006, the FRCP [Federal Rules of Civil Procedure] were amended to address the expanding issue of electronic data in litigation. One rule change was to replace the previous designation of “data compilations” with ‘electronically stored information” [ESI] which had been previously understood to mean any electronic data from which something meaningful could be extracted. All such ESI is now subject to legal discovery the same as hardcopy materials have been since the 1930’s. In litigation, this has come to include not just computer generated ESI, but things such as Instant Messages, Text Messages, Voice. Mail, VOIP, Cellphone data, digital photographs, etc. Although presently only applicable to litigation in Federal Courts, State courts are following suit, and the broader impact on corporate enterprises is far reaching. It is becoming increasingly common for in house IT personnel to be subpoenaed to testify about Enterprise IT systems, policies, and practices, 4

Computer Forensics Overview • What is a forensics examination? • Collection and analysis of ESI from a computer hard drive or other electronic media. This may include deleted files, file fragments, slack space, unallocated clusters, and examination of operating system logs that indicate the users’ actions. • Why would a forensics examination be needed? • Searching for ESI inadvertently lost or deleted • Performing an internal investigation • Searching for ESI subject to legal discovery • Who performs such examinations? • Experts using special hardware and/or software • Specific training and /or certifications may be required: CCE, CISA, CFE, CISSP, CISM, etc. • CATASTROPHE • May necessitate special licenses in certain jurisdictions. [e. g. , P. I. License]. • How is a forensics exam performed? 5 • Collection • Analysis • Reporting & Testimony [if required]

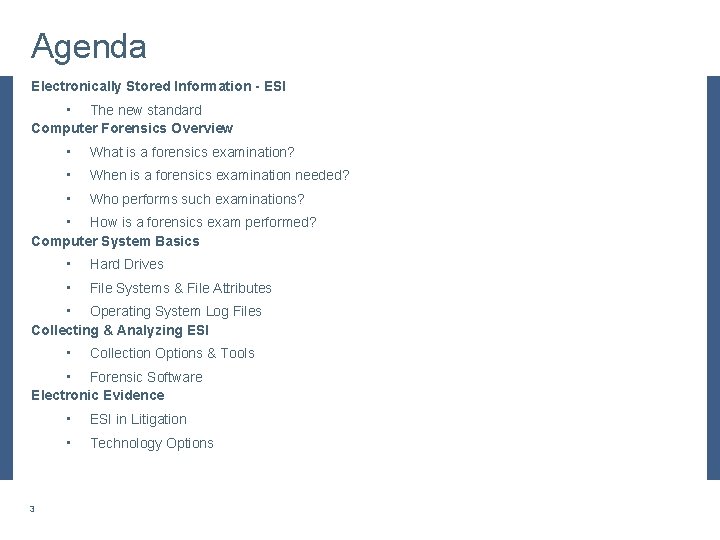
Computer Systems Basics – Hard Drives Disks [or “Platters” if on a hard drive, stacked into a “Cylinder”] are physically divided into “Tracks” [circular bands], which are further divided into clusters” of “Sectors”. 6

Computer Systems Basics File Systems & File Attributes • File Systems – most common types • FAT [File Allocation Table] • Used for DOS thru Windows NT 4. • Fat 12 [floppies], FAT 16 [OS files] and FAT 32 [NT 4] • Contains limited file attributes, history info. • EZ to analyze and recover data from • NTFS • Windows NT 4/2000/2003/XP • Lots of attributes: permissions/encryption/auditing/compression, etc. • Uses MFT [Master File Table] to keep info • File Attributes 7 • Filetypes – Read only/hidden/system/archive/compressed/encrypted/permissions, etc. • Time. Stamps – Modified/Accessed/Created [+ more for Email] • Checksums – Quick hashes for comparison

Computer System Basics – Operating System Log Files • Installation Logs • Created during OS/APP install – records events, successes, failures. • Windows Event Logs • System – OS specific events • Application some app events [e. g. updates] • Audit/Security – MUST BE TURNED ON –DEFAULT IS OFF • LOGS access, log on/off –object creation/deletion • Application & Error Logs • Start/stop processes • Maybe file access • Browser Artifacts • Cookies/net cache/IE history • INDEX. DAT file exists for all user profiles – contains browsing history • Firewall/IDS Logs • IDS=Intrusion Detection System 8

Collecting and Analyzing ESI – Options, Tools & Software • Hard Drive Imaging Options • Simple File Copy – can affect metadata • Advanced File Copy – can capture hidden, etc files, but dates can be affected • Partition Duplication – Capture entire partition – may be able to get slack/unallocated • Forensic Duplication – Bitstream, verified • FORENSIC SOFTWARE • Commercial Software • ENCASE [Guidance SW]. full featured, Windows based, expensive • FTK [Forensics Tool Kit] –by Access Data – Windows FTK Imager free download • DRIVE SPY – Digital Intelligence –Bootable DOS disk can acquire unallocated/slack • PARABEN – Suite of tools. Incl cellphone & PDA capabilities • GHOST [Symantic[Norton]] used mainly for disk dupes 9
![Collecting and Analyzing ESI Software cont FORENSIC SOFTWARE cont Open Source Collecting and Analyzing ESI – Software [cont] • FORENSIC SOFTWARE [cont] • Open Source](https://slidetodoc.com/presentation_image_h2/5a0528e8bc5a21850d3ace98022e6663/image-11.jpg)
Collecting and Analyzing ESI – Software [cont] • FORENSIC SOFTWARE [cont] • Open Source Software • LINUX dd – Most popular. Command line/w some GUI • HELIX – Most popular bootable CD based. Lots of tools. Free Download • AUTOPSY & TSK [The Sleuth Kit] – Browser interface – very popular suite • FIRE [Forensic Incident Response Environment] – similar to HELIX bootable CD • KNOPPIX – not really forensic, but lots of good tools • Windows Open Source Software • FTK Imager [part of FTK] • Foundstone Utilities • HELIX [Windows Response portion 10

Electronic Evidence • The impacts of the introduction of ESI into Litigation • The cost of litigation has risen dramatically • Can exceed the merit value of the matter in dispute • The risks of sanctions have risen dramatically • Spoliation • Discovery disputes are increasing • When merits are weak, litigate about discovery • Litigants are working to establish “Complaint” Enterprises • Know what ESI exists • Know where it resides • Have the means to preserve it when the duty to do so arises • Have defensible audit procedures in place • The downside to non compliant enterprises are significant and serious • Adverse results in litigation • Sanctions • Monetary • Legal [Adverse Inference] • Security Third party access to the Enterprise 11

Electronic Evidence • Technology has developed to address ESI in Discovery • Developed to collect, analyze, de duplicate, search, and support legal review of high volumes of ESI. • Speed [& cost] of technology is driven by full content indexing • Over 500 technology companies offering a wide array of solutions • As a service or in house • Soup to nuts enterprise, or specific portion[s] thereof • Pricing models vary widely • Linear review, auto content clustering, enterprise crawlers, A. I. , etc. • Enterprise Records [Content] Management is the ultimate goal • Most litigants are working towards the goal • E Discovery cost avoidance is a significant driving force • Many Enterprise ERM solutions coming to market • Will technology be the ultimate solution? 12

Computer Forensics & Electronic Evidence Discussion 13