COMPUTER CRIME IMPACT OF INFORMATION TECHNOLOGY Development of







- Slides: 18

COMPUTER CRIME

IMPACT OF INFORMATION TECHNOLOGY • Development of IT has changed our – societies – commerce – lifestyle (communication, working, shopping) • This creates considerable legal problems in many areas • Its more important than ever to legislate on computer or cyber crime

YOU & COMPUTER CRIMES

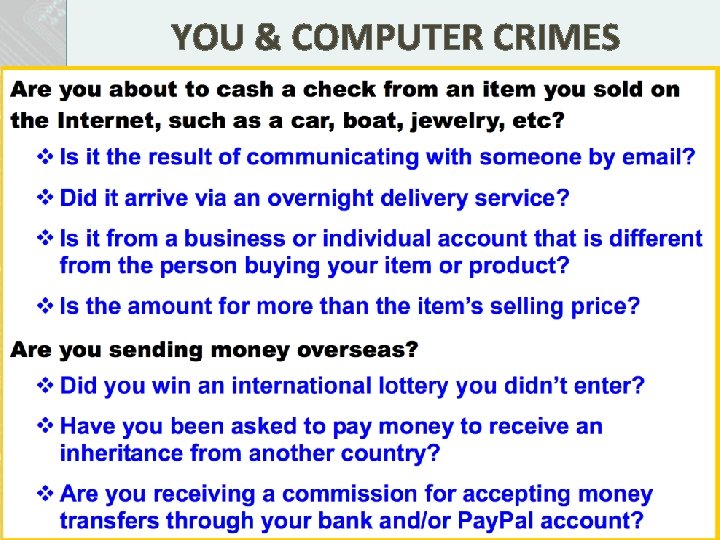
YOU & COMPUTER CRIMES

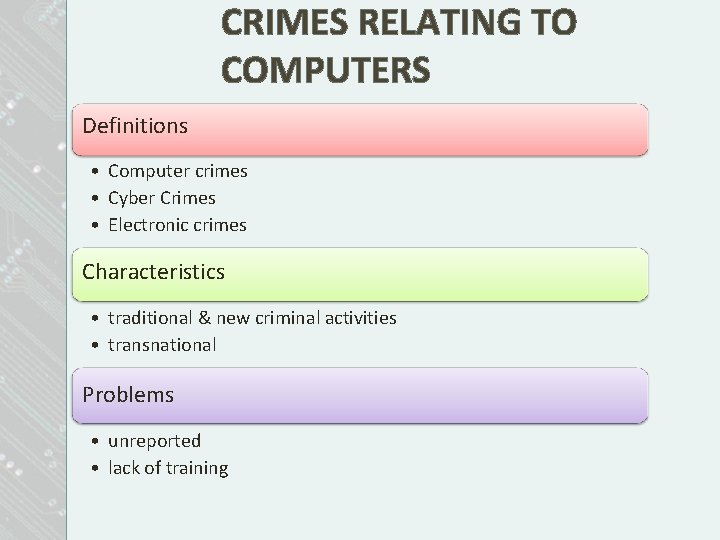
CRIMES RELATING TO COMPUTERS Definitions • Computer crimes • Cyber Crimes • Electronic crimes Characteristics • traditional & new criminal activities • transnational Problems • unreported • lack of training

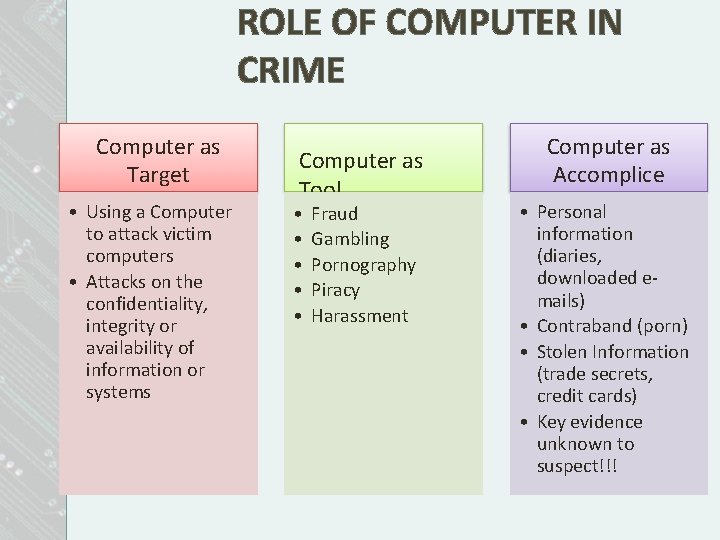
ROLE OF COMPUTER IN CRIME Computer as Target • Using a Computer to attack victim computers • Attacks on the confidentiality, integrity or availability of information or systems Computer as Tool • • • Fraud Gambling Pornography Piracy Harassment Computer as Accomplice • Personal information (diaries, downloaded emails) • Contraband (porn) • Stolen Information (trade secrets, credit cards) • Key evidence unknown to suspect!!!

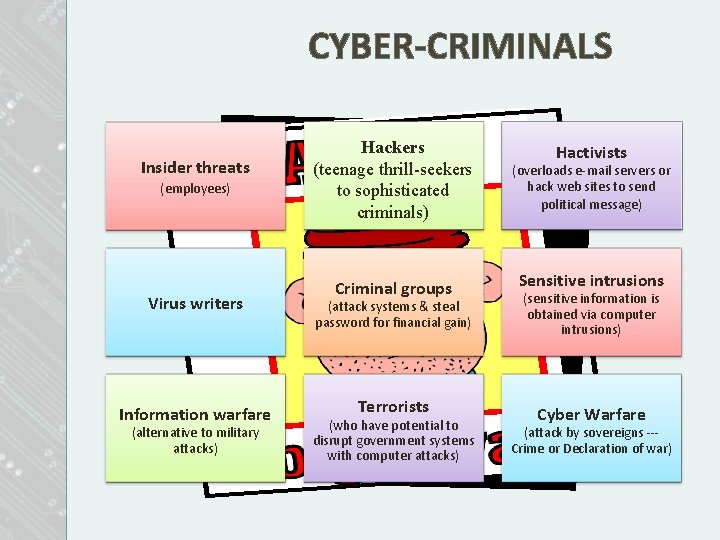
CYBER-CRIMINALS Insider threats (employees) Virus writers Information warfare (alternative to military attacks) Hackers (teenage thrill-seekers to to sophisticated criminals) Hactivists (overloads e-mail servers or hack web sites to send political message) Criminal groups Sensitive intrusions Terrorists Cyber Warfare (attack systems & steal password for financial gain) (who have potential to disrupt government systems with computer attacks) (sensitive information is obtained via computer intrusions) (attack by sovereigns --Crime or Declaration of war)

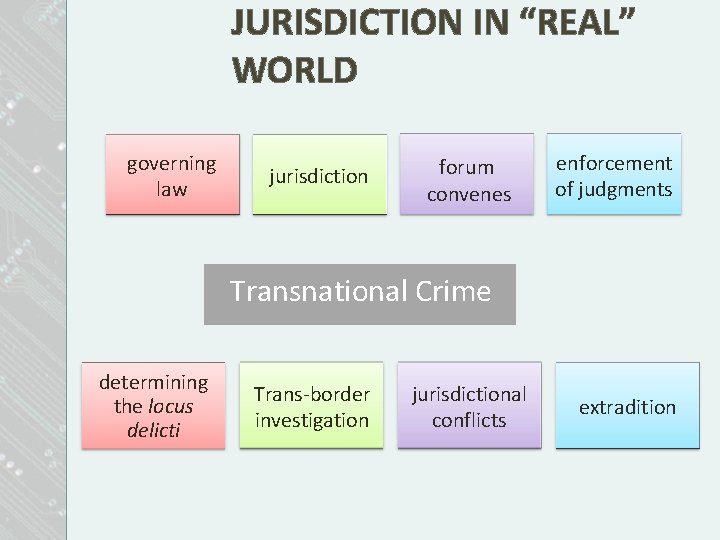
JURISDICTION IN “REAL” WORLD governing law jurisdiction forum conveniens convenes enforcement of judgments Transnational Crime determining the locus delicti Trans-border investigation jurisdictional conflicts extradition

SHOULD THE U. N. INTERVENE IN A TRANSNATIONAL INTERNET DEFAMATION CASE? An American Journalist Sued in Australia Files a Petition Seeking Help By ANITA RAMASASTRY I will argue that the U. N. is not the right forum to resolve these key questions. A few years ago, Australian mining magnate Joe Gutnick sued American reporter Bill Alpert for defamation in Australia. Now, in an unprecedented move, Alpert has taken his case to the U. N. - filing a petition with the Human Rights Committee. The case itself) and the disposition of the petition, are likely to be landmarks in the law regarding international jurisdiction with respect to Internet publications. Alpert claims in his petition that a decision by Australia 1 s High Court, forcing him to face suit there, denied him the right of free speech. For this reason, he argues, it breached Article 19 of the United Nations 1 International Covenant on Civil and Political Rights (ICCPR).

SHOULD THE U. N. INTERVENE IN A TRANSNATIONAL INTERNET DEFAMATION CASE? An American Journalist Sued in Australia Files a Petition Seeking Help By ANITA RAMASASTRY (Continued) In this instance, the nation in which the case is tried is likely to make a significant different to the outcome. Defamation laws in Australia are stricter than in the US, where the First Amendment generally permits comments such as those made in the article. And if Australian defamation law applies) Internet publication may have to be tailored to the country whose laws are most restrictive - a blow to free speech. The issue the case raises is of crucial importance: Will words that appear on the Internet be subject to defamation (and perhaps other) suits wherever they may be read - that is, in any of the world 1 s 3 C 0 -plus jurisdictions? And if not, where can suits be brought, and not brought? What is the dividing line?

CHALLENGES FOR LEGAL REGIME Can we adapt existing law to cyberspace? Do we need new legislation? • Problem comes when very idea of jurisdiction, based on geographic boundaries, is difficult to apply to Internet which does not recognize geographical distinctions What are options other than legislation? • International/regional treaties • International convention • Development by system operators and Internet users of "rules" for behavior on Internet? • Options available to individuals to regulate their conduct on a private basis - through contracts, private associations, custom etc.

INTERNATIONAL EFFORTS 1977 • First comprehensive proposal for computer crime legislation was introduced in US Congress by Senator Ribikoff in 1977 1983 • Recommendations of expert committee of OECD in Paris in 1983 to ensure legislation for certain categories of computer crime 1986 • OECD ‘Computer-Related Crime’ Report 1986 1989 • Council of Europe Recommendation R(89) 9 on computer misuse 1990 -92 • Discussed at 13 th Congress of International Academy of Comparative Law in Montreal in 1990, at UN’s 8 th Criminal Congress in Havana 1990, and at a Conference in Wurzburg, Germany in 1992

INTERNATIONAL EFFORTS 1995 -2000 • Council of Europe Recommendation R(95) 13 (“problems of procedural law connected with information technology”) • Interpol organized its International Conference on Computer Crime in 1995, 1996, 1998, and 4 th Conference was held in 2000 2001 • Convention on Cyber-Crime 2001 2007 • ITU launched the Global Cybersecurity Agenda (GCA) in May 2007 by the Secretary General 2008 • ITU's High Level Experts Group delivered Report with recommendations, including on cybercrime legislation, in August 2008 2011 • ITU in 2011 published a book: Understanding Cybercrime: Phenomena, Challenges and Legal Responses, by Professor Marco Gercke, Germany

CONVENTION ON CYBER CRIME § 30 states sign Convention at opening ceremony at Budapest, on 23. XI. 2001 § First international treaty on cyber crimes, dealing particularly with infringements of copyright, computer-related fraud, child pornography and violations of network security § Contains a series of powers and procedures such as search of computer networks and interception § Main objective is to pursue a common criminal policy aimed at protection of society against cyber-crime, especially by adopting appropriate legislation and fostering international cooperation § Convention is product of four years of work by experts of Council of Europe, United States, Canada, Japan and other countries which are not members of the Organization

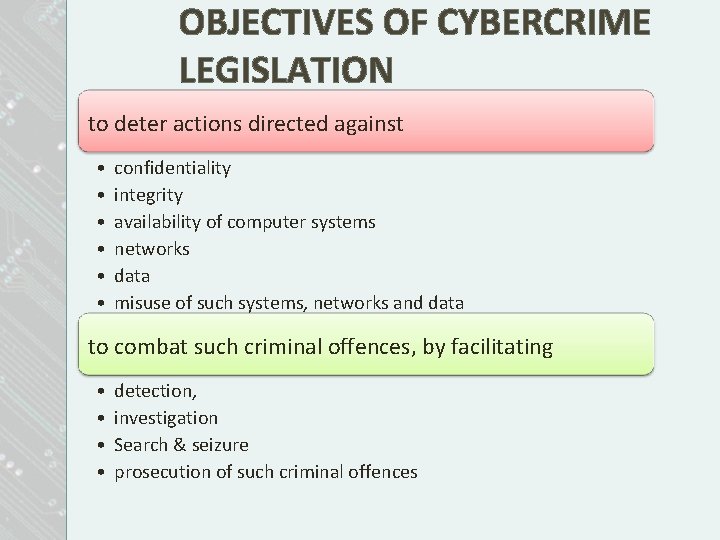
OBJECTIVES OF CYBERCRIME LEGISLATION to deter actions directed against • • • confidentiality integrity availability of computer systems networks data misuse of such systems, networks and data to combat such criminal offences, by facilitating • • detection, investigation Search & seizure prosecution of such criminal offences

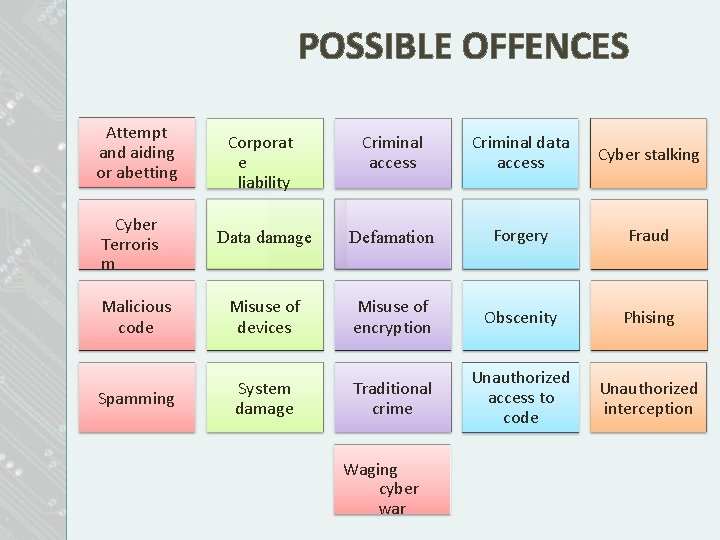
POSSIBLE OFFENCES Attempt and aiding or abetting Corporat e liability Criminal access Criminal data access Cyber stalking Data damage Defamation Forgery Fraud Malicious code Misuse of devices Misuse of encryption Obscenity Phising Spamming System damage Traditional crime Unauthorized access to code Unauthorized interception Cyber Terroris m Waging cyber war

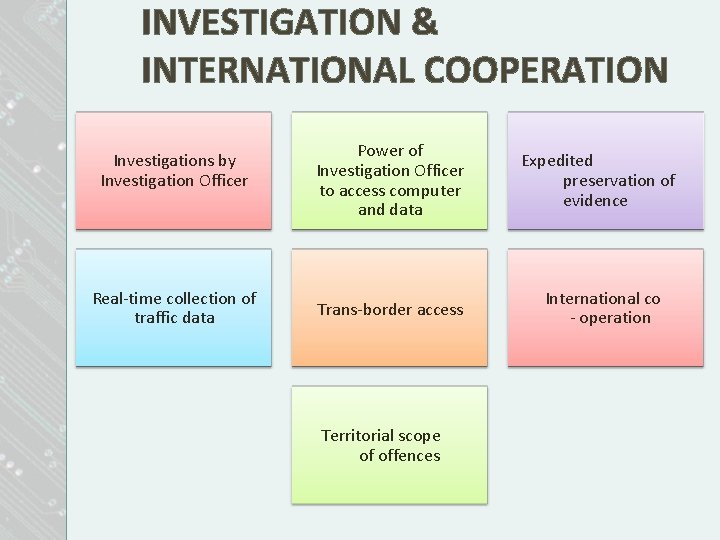
INVESTIGATION & INTERNATIONAL COOPERATION Investigations by Investigation Officer Real-time collection of traffic data Power of Investigation Officer to access computer and data Expedited preservation of evidence Trans-border access International co - operation Territorial scope of offences

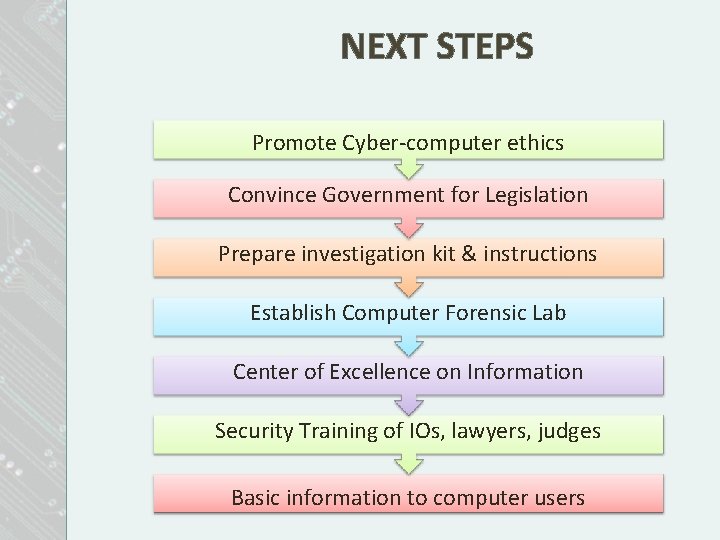
NEXT STEPS Promote Cyber-computer ethics Convince Government for Legislation Prepare investigation kit & instructions Establish Computer Forensic Lab Center of Excellence on Information Security Training of IOs, lawyers, judges Basic information to computer users