Comp 655 Security Commercial for Comp 676 Security




































- Slides: 68

Comp 655 - Security • • Commercial for Comp 676 Security basics Encryption Major functions of a security system 10/30/2020 Distributed Systems - Comp 655 1

Commercial: Comp 676 1. Explain the basic concepts 2. Develop a beginning threat model for analyzing security risks. 3. Basic principles of cryptography and how cryptography is used 4. Understand common exploits 5. Understand the basic principles for designing secure systems. 6. Look at every program or piece of code encountered after completing this course with a certain level of suspicion and paranoia. ; -) 10/30/2020 Distributed Systems - Comp 655 2

More about 676 Prerequisites • COMP 655 - Operating and Distributed Systems is strongly recommended. • Familiarity with C or C++ is essential (Perl or Java would be helpful) • Students should be comfortable reading small code fragments in many languages • Being slightly paranoid is helpful! 10/30/2020 Distributed Systems - Comp 655 3

Ethics and 676 In order to protect both Franklin University and the instructor from potential third party lawsuits, students will be required to sign an agreement that they will not use the knowledge gained within this class to practice unlawful or unethical behavior. This statement must signed and turned into the instructor before the second class, otherwise students will not be admitted into the second and subsequent classes. 10/30/2020 Distributed Systems - Comp 655 4

Comp 655 - Security • • Commercial for Comp 676 Security basics Encryption Major functions of a security system 10/30/2020 Distributed Systems - Comp 655 5

Types of security • Confidentiality – Information disclosed only to authorized parties • Integrity – Information can be created, changed, or deleted only in authorized ways 10/30/2020 Distributed Systems - Comp 655 6

Types of threats • • Interception (confidentiality) Interruption (integrity) Modification (integrity) Fabrication (integrity) 10/30/2020 Distributed Systems - Comp 655 7

Major functions of a security system • • • Authentication Authorization Administration Journaling Intrusion detection 10/30/2020 Distributed Systems - Comp 655 8

Security basics General advice when dealing with security: • Always stay in touch with the basic question: what is the problem you are trying to solve? • Compare the cost of security to the cost of loss These should be covered in a security policy 10/30/2020 Distributed Systems - Comp 655 9

Security policy basics • A security policy defines the security requirements for a system • A security policy identifies – Types of entities in the system For example, “instructor”, “student”, “gradebook application” – Types of actions supported by the system For example, “view grades”, “assign grades” – Which types of entities are allowed to perform which types of actions 10/30/2020 Distributed Systems - Comp 655 10

More about security policy Examples of security policy statements: • An instructor is allowed to assign and view grades for all students in sections taught by the instructor • An instructor is not allowed to assign or view grades for any section that he or she did not teach • A student is allowed to view all of his or her grades • A student is not allowed to assign grades 10/30/2020 Distributed Systems - Comp 655 11

Yet more security policy • Policy deals with roles, not individuals. For example, some Franklin students are also instructors • Policy must be specific to a system – “users may perform only authorized actions” is NOT useful policy – “instructors and administrators may assign grades” is much more useful • Writing a good policy is usually hard – Can any administrator assign a grade? – Or only department chairs and deans with responsibility for the course? – Can the college president assign a grade? 10/30/2020 Distributed Systems - Comp 655 12

Activity: Di. No Security policy • Imagine that Di. No needs to support confidential notebooks • Discuss the security aspects of Di. No – What types of entities and operations are important? • What should the security priorities be? – List at least five policies about who’s allowed to do what • NOTE: “all users must be authenticated” does NOT belong in a security policy – it’s about implementation, not requirements 10/30/2020 Distributed Systems - Comp 655 13

Terms • • • Vulnerability Attack Exploit Cracker White/gray/black hat Script kiddie 10/30/2020 Distributed Systems - Comp 655 14

Kevin Mitnick’s work today • The simple fact is this: People are, and always have been, the most vulnerable aspect of any organization's security infrastructure … http: //www. mitnicksecurity. com/ Interview on 60 Minutes 10/30/2020 Distributed Systems - Comp 655 15

Security – human aspects • “Human engineering” is the most effective way to gain unauthorized access to systems – Helpfulness can be abused – Garbage can be sifted – Etc • Basically, it’s a never-ending dialog between builders and crackers If you remember nothing else from tonight … 10/30/2020 Distributed Systems - Comp 655 16

Tools for the security provider • • Encryption Explicit, well-considered policy QA for code Security education for developers (for example, see http: //www. sans. org/top 25 errors) Security education for others with access to sensitive information Firewalls Audits Monitoring 10/30/2020 Distributed Systems - Comp 655 17

More security tools • Research • Former crackers with changed motives • Good system administration, including keeping up with patches • Virus checkers (pattern, heuristic) 10/30/2020 Distributed Systems - Comp 655 18

Resources • • CERT: www. cert. org/ CSRC (NIST): csrc. nist. gov/ Steve Gibson: grc. com/default. htm Counterpane: www. counterpane. com/cryptogram. html • And 400, 000 others … 10/30/2020 Distributed Systems - Comp 655 19

Activity – implementing your policy • For each of the five statements in your security policy exercise, identify one or more techniques that could be used to enforce it. 10/30/2020 Distributed Systems - Comp 655 20

Comp 655 - Security • • Commercial for Comp 676 Security basics Encryption Major functions of a security system 10/30/2020 Distributed Systems - Comp 655 21

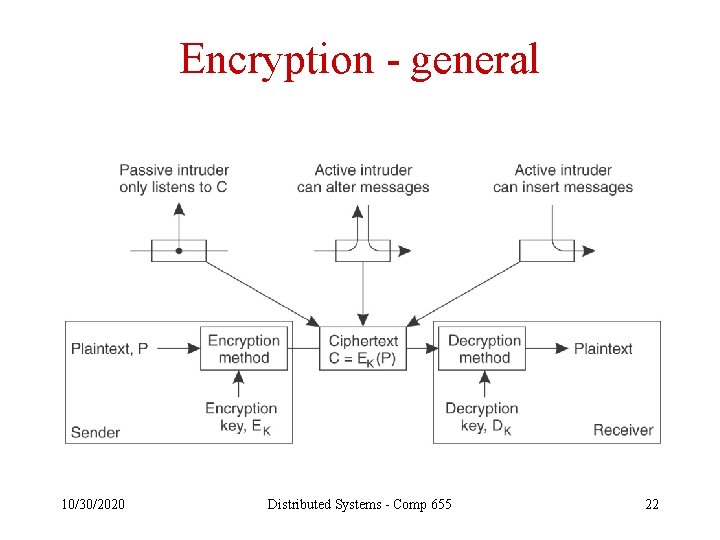
Encryption - general 10/30/2020 Distributed Systems - Comp 655 22

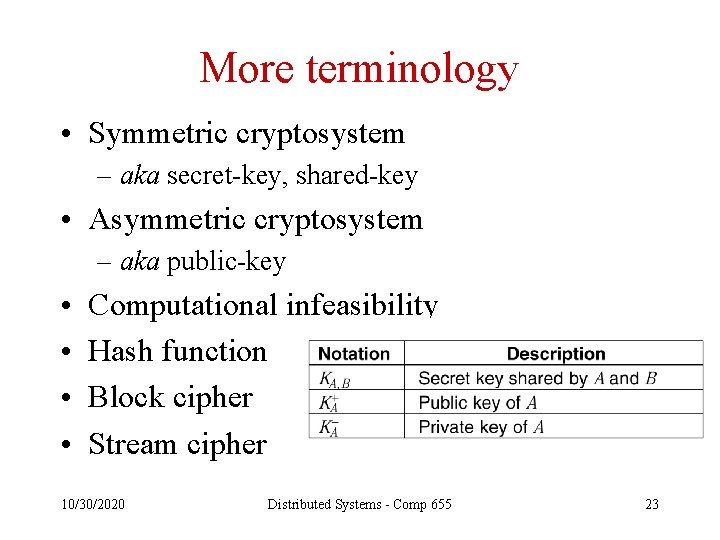
More terminology • Symmetric cryptosystem – aka secret-key, shared-key • Asymmetric cryptosystem – aka public-key • • Computational infeasibility Hash function Block cipher Stream cipher 10/30/2020 Distributed Systems - Comp 655 23

Important encryption algorithms • • • DES AES RSA MD 5 SHA-1 10/30/2020 Distributed Systems - Comp 655 24

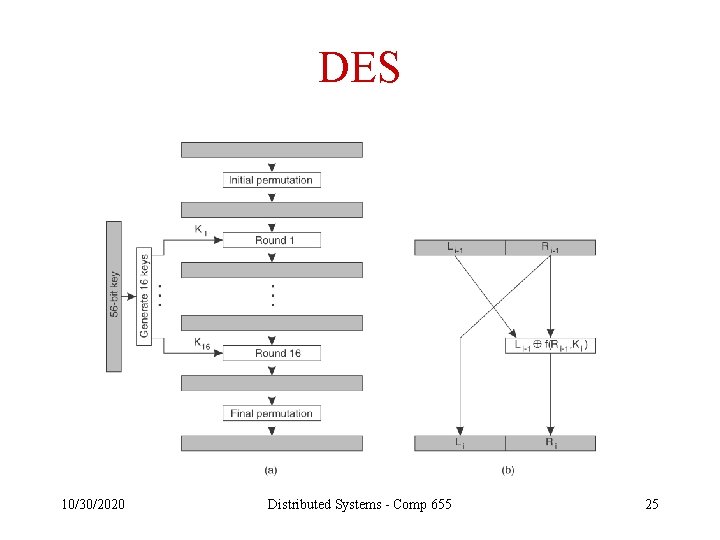
DES 10/30/2020 Distributed Systems - Comp 655 25

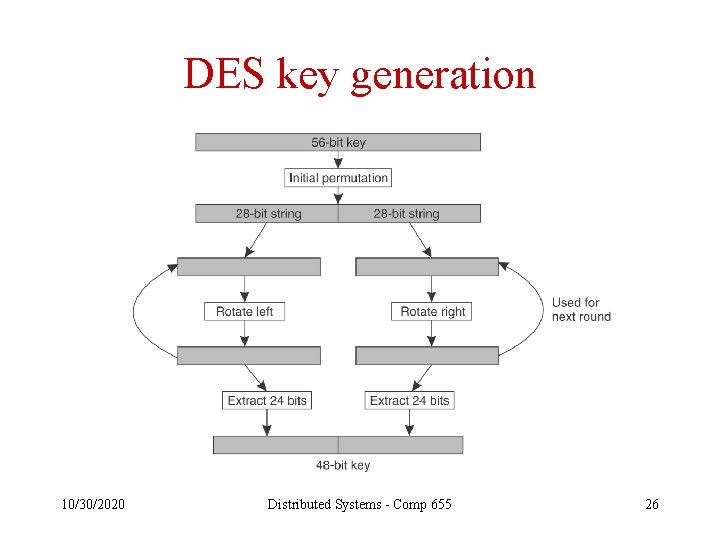
DES key generation 10/30/2020 Distributed Systems - Comp 655 26

Attacks on DES • Analytical – DES has held up pretty well • Brute force – Hardware is now fast enough to allow practical guess-and-check attacks on 56 -bit DES • Triple DES “appears to be safe for the moment” 10/30/2020 Distributed Systems - Comp 655 27

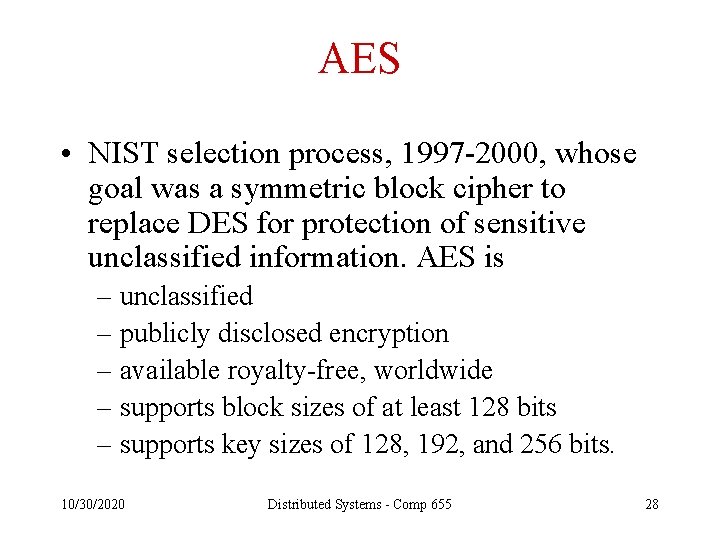
AES • NIST selection process, 1997 -2000, whose goal was a symmetric block cipher to replace DES for protection of sensitive unclassified information. AES is – unclassified – publicly disclosed encryption – available royalty-free, worldwide – supports block sizes of at least 128 bits – supports key sizes of 128, 192, and 256 bits. 10/30/2020 Distributed Systems - Comp 655 28

AES Selection criteria 1. Security was the most important factor, including – – resistance to cryptanalysis soundness of mathematical basis randomness of the algorithm output relative security as compared to other candidates. 2. Cost was a second important area – licensing requirements – speed on various platforms – memory requirements 10/30/2020 Distributed Systems - Comp 655 29

AES Selection Criteria continued • Algorithm characteristics – Adaptability to larger key sizes – Adaptability to other applications, including stream cipher, hash – Adaptability to various implementation environments including software, firmware, hardware – Overall simplicity 10/30/2020 Distributed Systems - Comp 655 30

AES continued • Winner was Rijndael (“Rhine-doll”) • NIST evaluation tested C and Java implementations of the candidates • Implementations have also appeared in Lisp, Pascal, Java. Script, C++, hardware, etc • See the NIST crypto toolkit web site: http: //csrc. nist. gov/Crypto. Toolkit/ 10/30/2020 Distributed Systems - Comp 655 31

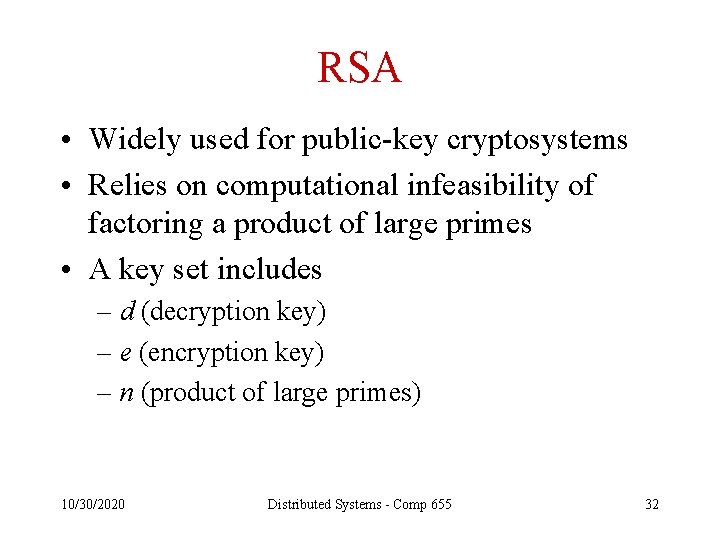
RSA • Widely used for public-key cryptosystems • Relies on computational infeasibility of factoring a product of large primes • A key set includes – d (decryption key) – e (encryption key) – n (product of large primes) 10/30/2020 Distributed Systems - Comp 655 32

RSA continued • Publish n and one key, keep the other key private • Which key gets published depends on the problem you’re trying to solve – Publish encryption key for data protection – Publish decryption key for authentication • Expensive! (2 -3 orders of magnitude slower than DES) 10/30/2020 Distributed Systems - Comp 655 33

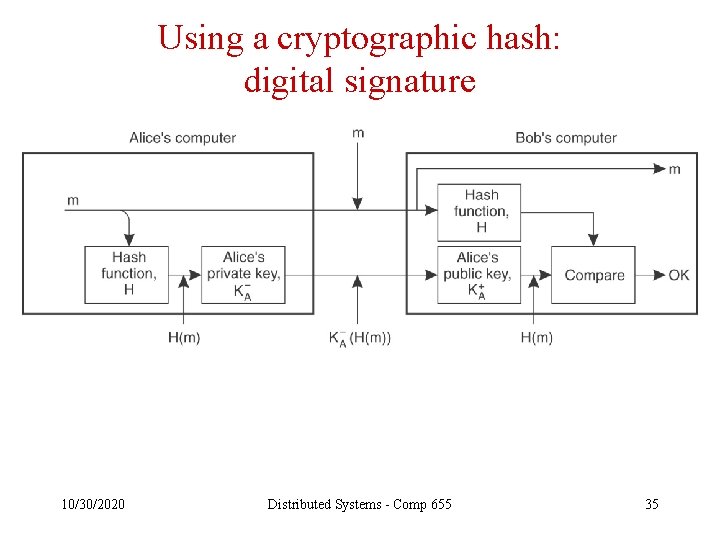
Cryptographic hash functions • With encryption, they guard against modification • (kind of like a checksum or check digit) • A hash computes a fixed-length summary (or digest) of a string (message) that is hard to reproduce – Given a message m, it’s computationally infeasible to find another message m’ such that H(m’) = H(m). – And it’s even harder to find such an m’ that says what you want … 10/30/2020 Distributed Systems - Comp 655 34

Using a cryptographic hash: digital signature 10/30/2020 Distributed Systems - Comp 655 35

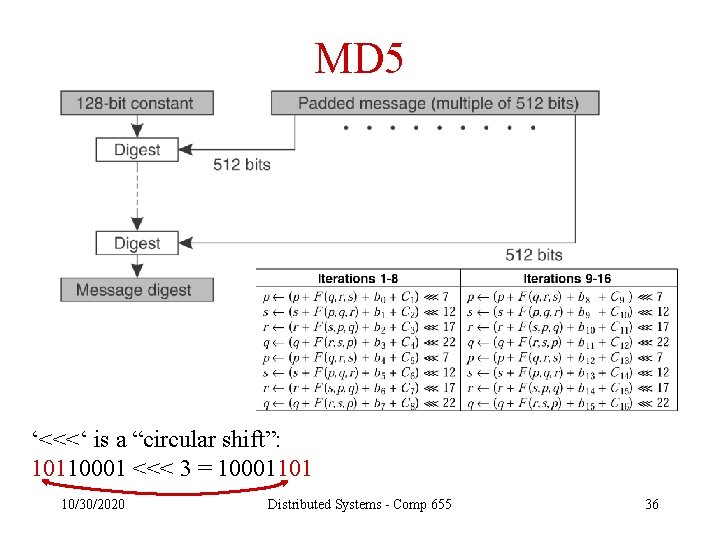
MD 5 ‘<<<‘ is a “circular shift”: 10110001 <<< 3 = 10001101 10/30/2020 Distributed Systems - Comp 655 36

SHA-1 (from Adam Back’s web site) • SHA 1 (Secure Hash Algorithm 1) is a cryptographic message digest algorithm. • It is considered to be more secure than MD 5 – it has longer hash size – Hans Dobbertin discovered a partial weakness in the MD 5 collision function. • There was a SHA 0 but it had some security problems which were fixed in SHA 1. http: //www. cypherspace. org/adam/rsa/sha. html 10/30/2020 Distributed Systems - Comp 655 37

Comp 655 - Security • • Commercial for Comp 676 Security basics Encryption Major functions of a security system 10/30/2020 Distributed Systems - Comp 655 38

Major functions of a security system • • • Authentication Authorization Administration Journaling Intrusion detection 10/30/2020 Distributed Systems - Comp 655 39

Authentication is … Checking that you are who you say you are 10/30/2020 Distributed Systems - Comp 655 40

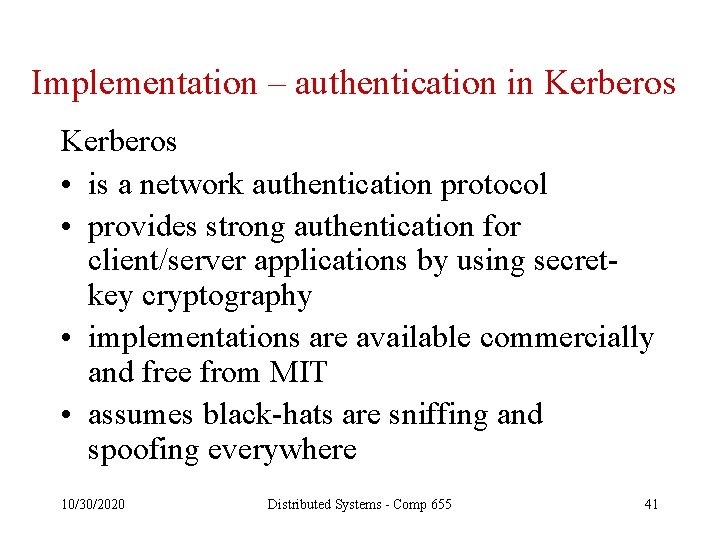
Implementation – authentication in Kerberos • is a network authentication protocol • provides strong authentication for client/server applications by using secretkey cryptography • implementations are available commercially and free from MIT • assumes black-hats are sniffing and spoofing everywhere 10/30/2020 Distributed Systems - Comp 655 41

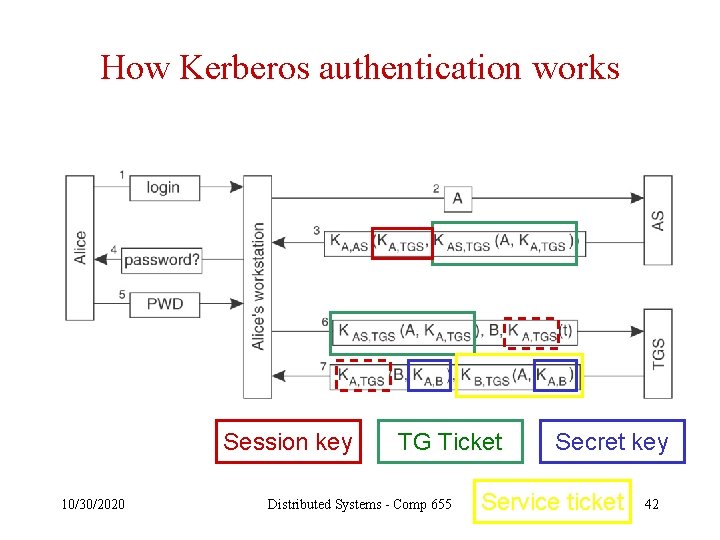
How Kerberos authentication works Session key 10/30/2020 TG Ticket Distributed Systems - Comp 655 Secret key Service ticket 42

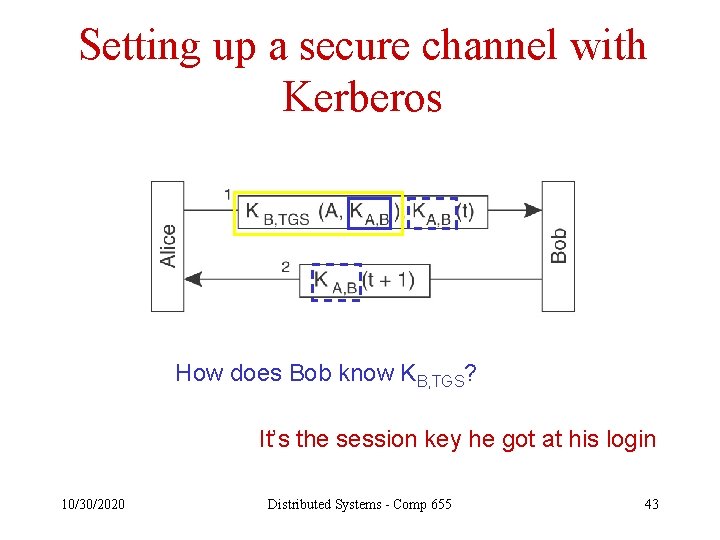
Setting up a secure channel with Kerberos How does Bob know KB, TGS? It’s the session key he got at his login 10/30/2020 Distributed Systems - Comp 655 43

Activity - authentication • When you talk to someone on the phone, how do you know who it is? – List at least three ways – For each way, how can it be spoofed? • If you suspect you’re being spoofed, how can you verify the other person’s identity? • Same two questions for instant messaging 10/30/2020 Distributed Systems - Comp 655 44

Major functions of a security system • • • Authentication Authorization Administration Journaling Intrusion detection 10/30/2020 Distributed Systems - Comp 655 45

Authorization is … Granting access to resources so that the ability to create, read, update, or delete things is available only to those who are authorized. 10/30/2020 Distributed Systems - Comp 655 46

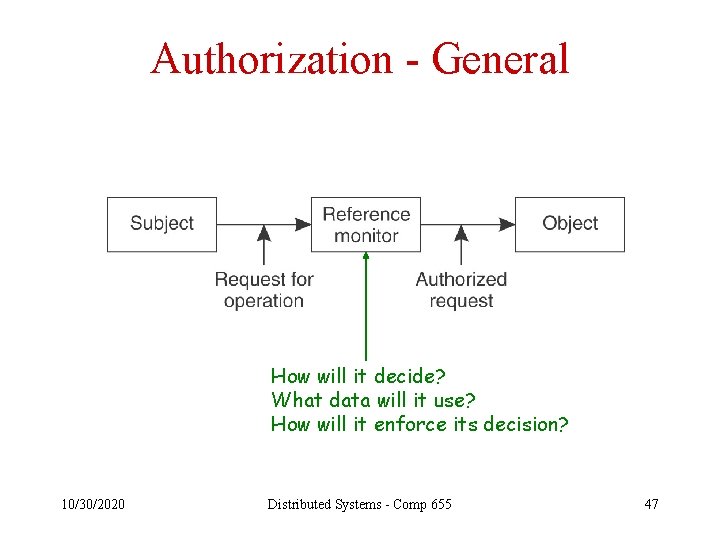
Authorization - General How will it decide? What data will it use? How will it enforce its decision? 10/30/2020 Distributed Systems - Comp 655 47

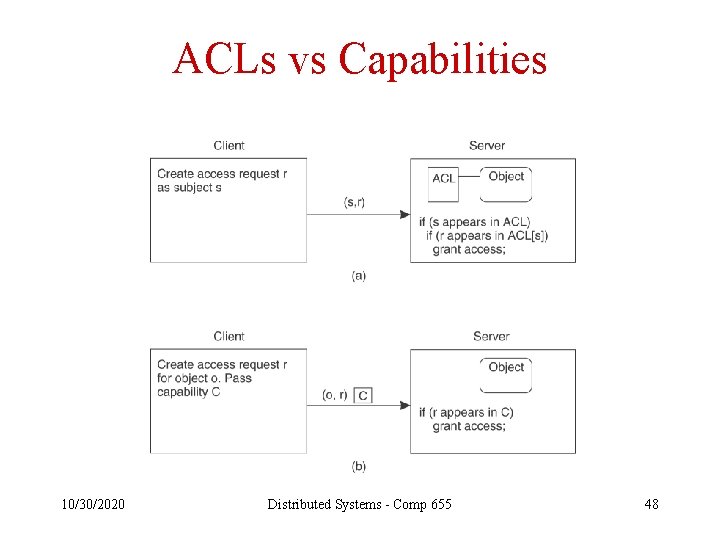
ACLs vs Capabilities 10/30/2020 Distributed Systems - Comp 655 48

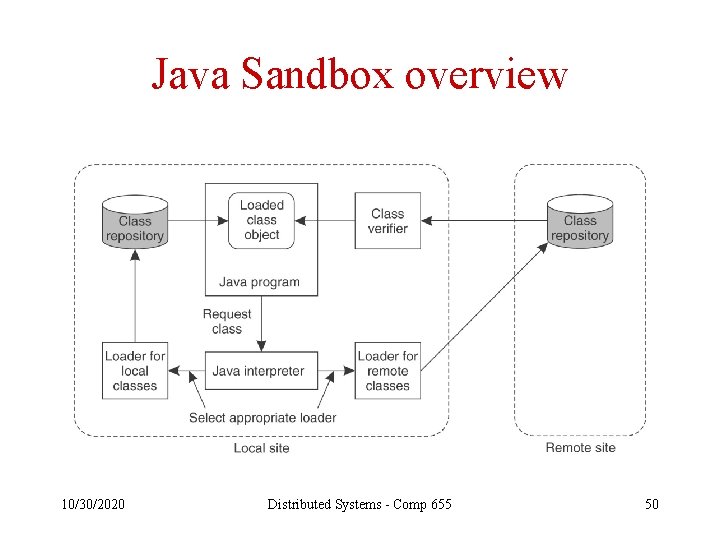
Java Security • Top-priority problem: protect hosts from damage or eavesdropping by mobile Java code. • For applets, security is built on a coordinated authorization system called a “sandbox”. 10/30/2020 Distributed Systems - Comp 655 49

Java Sandbox overview 10/30/2020 Distributed Systems - Comp 655 50

Security. Manager 10/30/2020 Distributed Systems - Comp 655 51

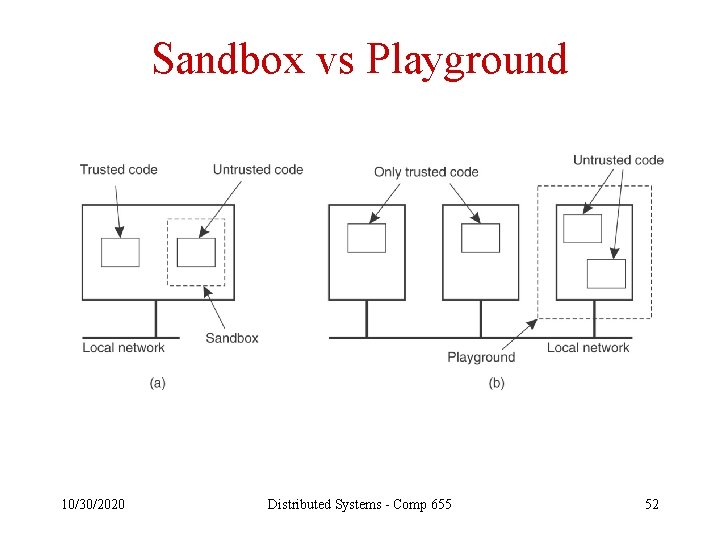
Sandbox vs Playground 10/30/2020 Distributed Systems - Comp 655 52

Leaning out of the sandbox … • Object references as capabilities • Stack introspection • Name space management (bait-n-switch based on class names) 10/30/2020 Distributed Systems - Comp 655 53

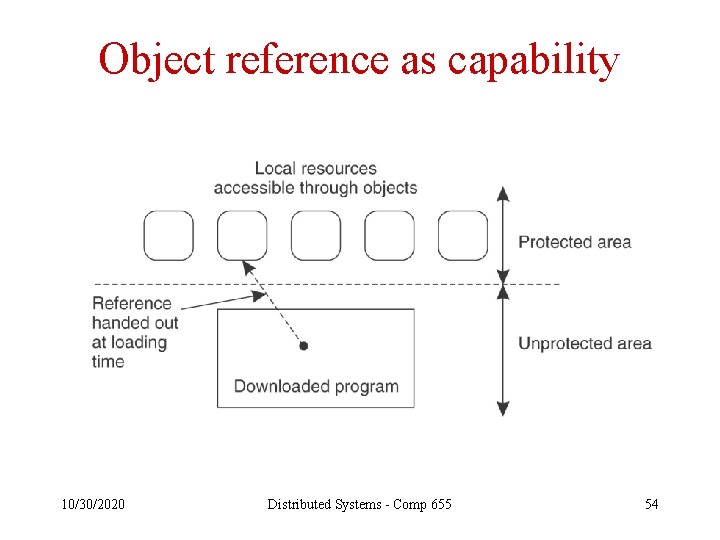
Object reference as capability 10/30/2020 Distributed Systems - Comp 655 54

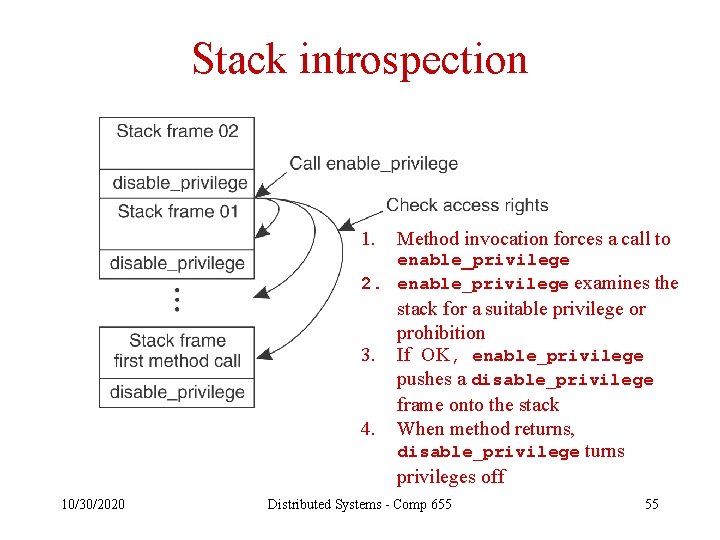
Stack introspection 1. Method invocation forces a call to enable_privilege 2. enable_privilege examines the 3. 4. 10/30/2020 stack for a suitable privilege or prohibition If OK, enable_privilege pushes a disable_privilege frame onto the stack When method returns, disable_privilege turns privileges off Distributed Systems - Comp 655 55

Major functions of a security system • • • Authentication Authorization Administration Journaling Intrusion detection 10/30/2020 Distributed Systems - Comp 655 56

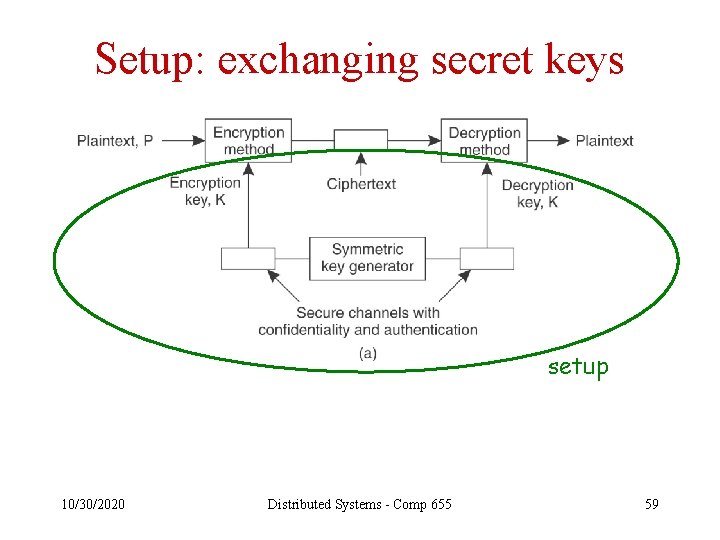
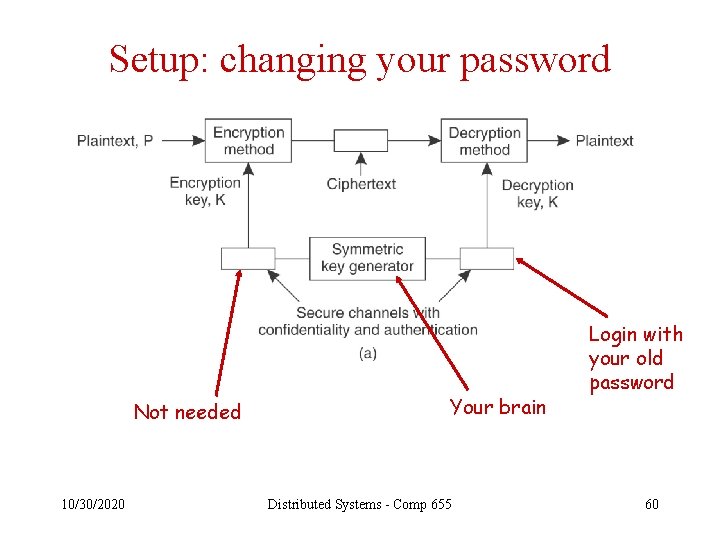
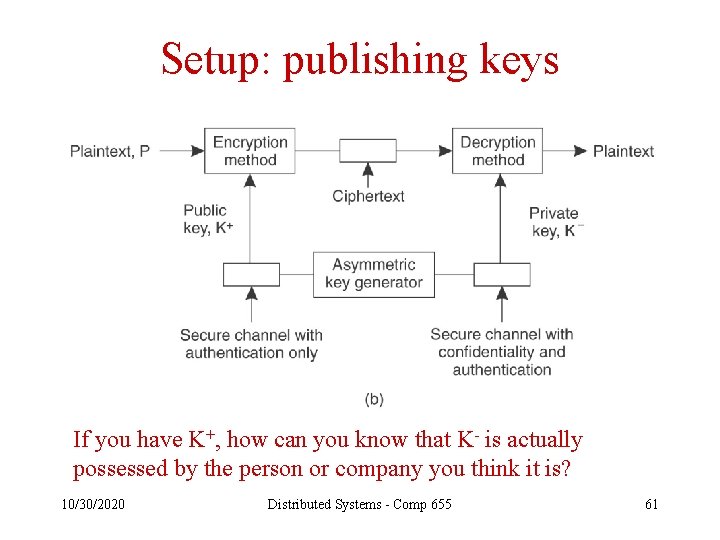
Administrative functions • Setting up – Exchanging secret keys – Publishing public keys – Granting privileges • Tearing down – Removing privileges – Changing compromised secret keys – Revoking compromised public keys • Managing trust – Adding or removing a server – Delegating privileges 10/30/2020 Distributed Systems - Comp 655 57

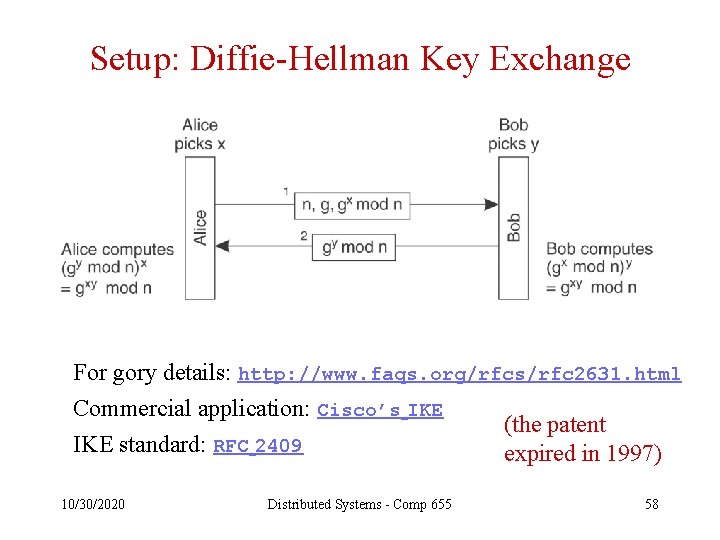
Setup: Diffie-Hellman Key Exchange For gory details: http: //www. faqs. org/rfcs/rfc 2631. html Commercial application: Cisco’s IKE (the patent IKE standard: RFC 2409 expired in 1997) 10/30/2020 Distributed Systems - Comp 655 58

Setup: exchanging secret keys setup 10/30/2020 Distributed Systems - Comp 655 59

Setup: changing your password Not needed 10/30/2020 Your brain Distributed Systems - Comp 655 Login with your old password 60

Setup: publishing keys If you have K+, how can you know that K- is actually possessed by the person or company you think it is? 10/30/2020 Distributed Systems - Comp 655 61

Setup: establishing trust in public keys • Usually, public keys are published in a certificate, consisting of – Public key – String identifying the owner – Digital signature of a certificate authority 10/30/2020 Distributed Systems - Comp 655 62

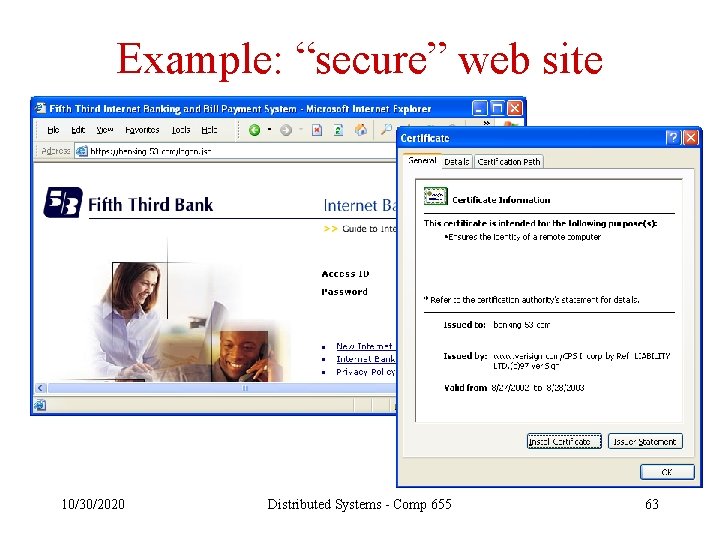
Example: “secure” web site 10/30/2020 Distributed Systems - Comp 655 63

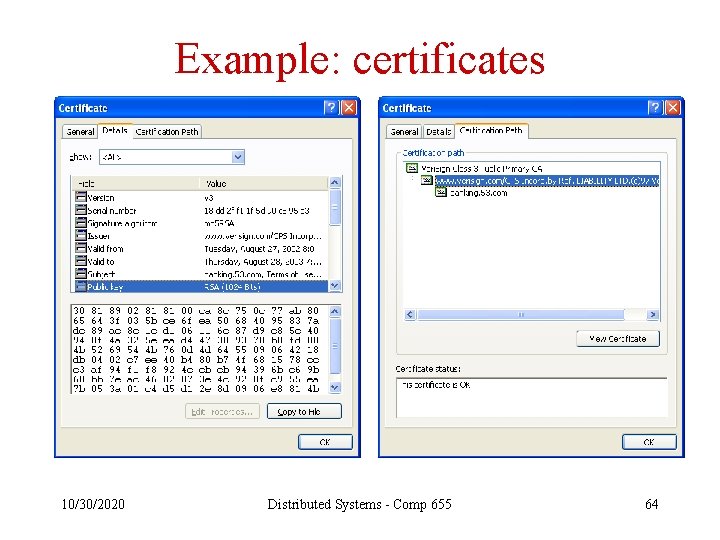
Example: certificates 10/30/2020 Distributed Systems - Comp 655 64

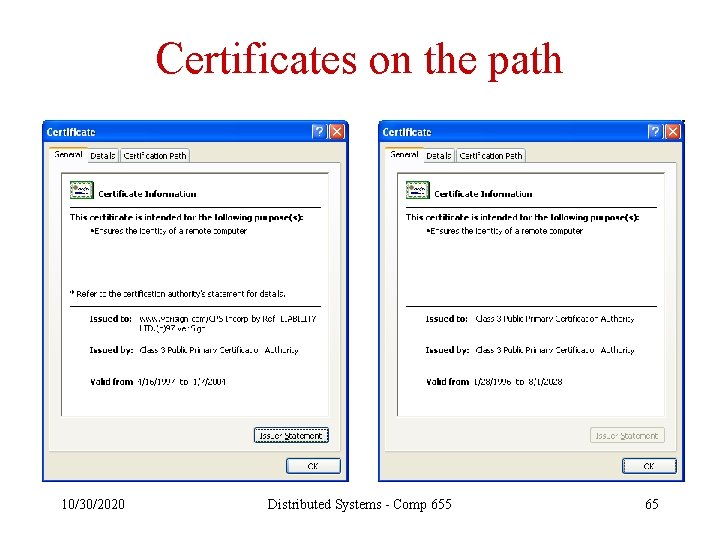
Certificates on the path 10/30/2020 Distributed Systems - Comp 655 65

Certification practice statement https: //www. verisign. com/repository/CPS 2. 1/cps 2 -1. pdf Why is this such an elaborate document? The simple fact is this: People are, and always have been, the most vulnerable aspect of any organization's security infrastructure … and that means lawsuits 10/30/2020 Distributed Systems - Comp 655 66

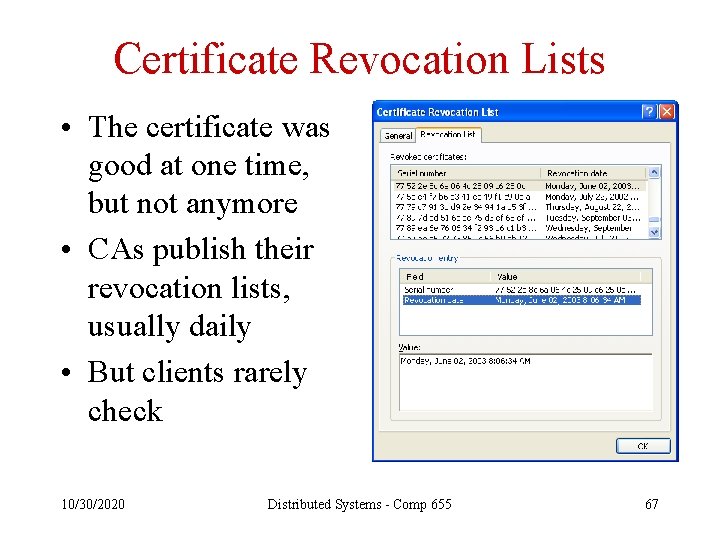
Certificate Revocation Lists • The certificate was good at one time, but not anymore • CAs publish their revocation lists, usually daily • But clients rarely check 10/30/2020 Distributed Systems - Comp 655 67

Major functions of a security system • • • Authentication Authorization Administration Journaling Intrusion detection http: //www. informit. com/articles/article. asp? p=174342 10/30/2020 Distributed Systems - Comp 655 68