COMP 6285 Operating System Week 6 Session 11

























- Slides: 45

COMP 6285 – Operating System Week 6 Session 11 Deadlock

Sub Topics • • • Principles of Deadlock Prevention Deadlock Avoidance An Integrted Deadlock Strategy Dining Philosophers Prolem

Acknowledgement These slides have been adapted from: Stallings, W. (2018). Operating Systems: Internals and Design Principles. 9 th. ISBN: 978 -0 -13 -467095 -9 Image(s) Area Chapter 6

Learning Objectives At the end of this lecture, students are able to: LO 1 : Descriibe different technques to prevent, avoid and handle deadlocks LO 2 : Explain the concept of deadlock and methods for prevention, avoidance and detection LO 3 : Demonstrate how to prevent/avoid deadlock LO 4: Write Java program to Simulate deadlock

Principles of deadlock (1) • Deadlock can be defined formally as follows: – A set of processes is deadlocked if each process in the set is waiting for an event that only another process in the set can cause. • Permanent blocking of a set of processes that either compete for system resources or communicate with each other • No efficient solution • Involve conflicting needs for resources by two or more processes

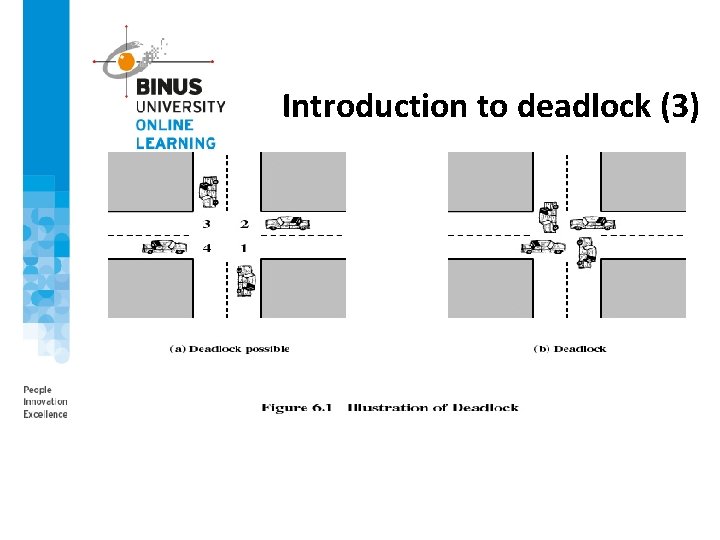
Introduction to deadlock (3)

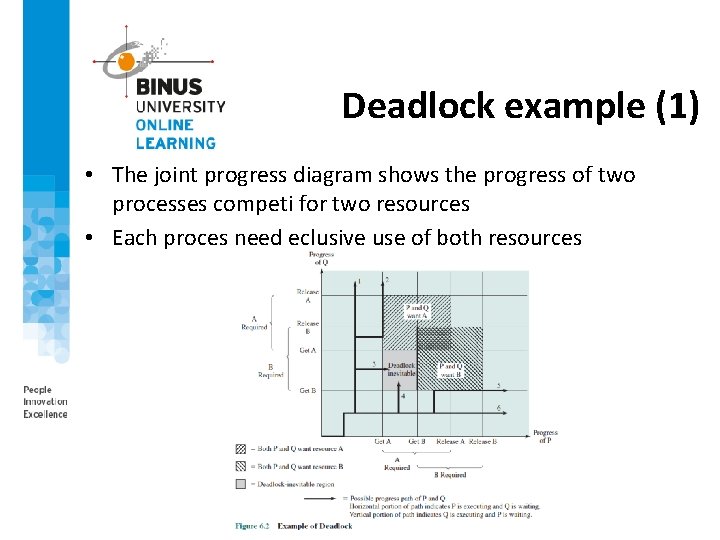
Deadlock example (1) • The joint progress diagram shows the progress of two processes competi for two resources • Each proces need eclusive use of both resources

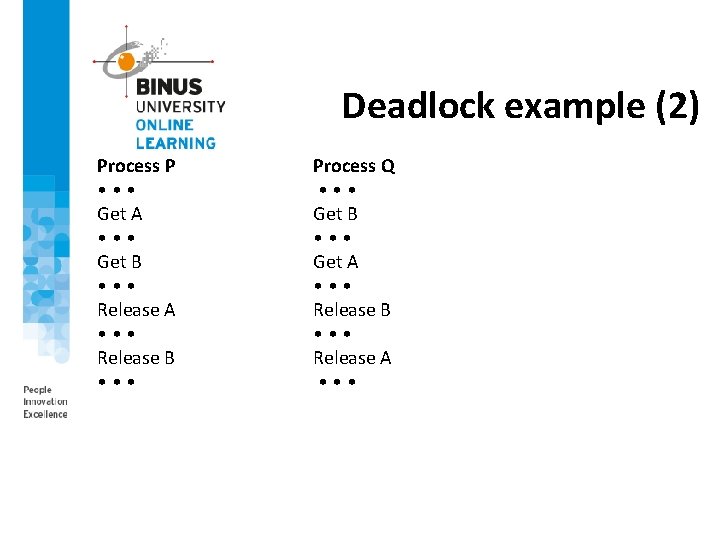
Deadlock example (2) Process P • • • Get A • • • Get B • • • Release A • • • Release B • • • Process Q • • • Get B • • • Get A • • • Release B • • • Release A • • •

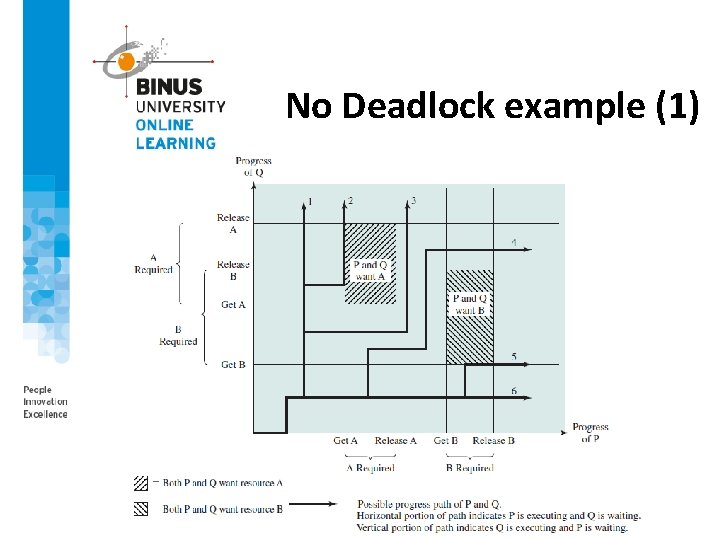
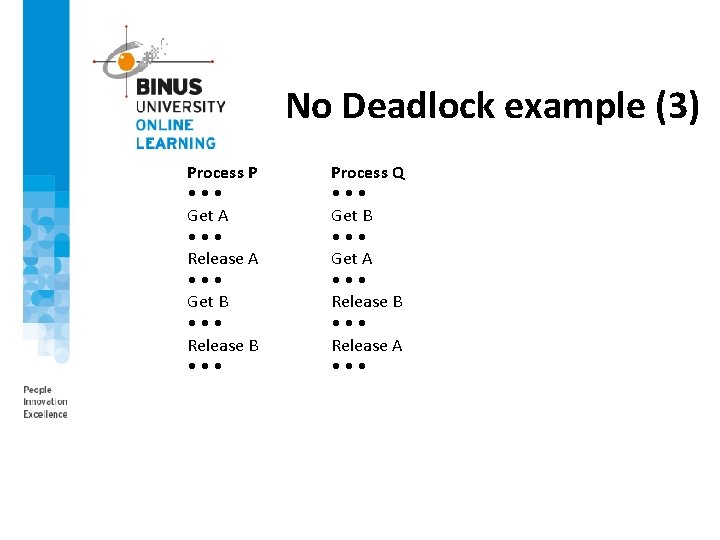
No Deadlock example (1)

No Deadlock example (3) Process P • • • Get A • • • Release A • • • Get B • • • Release B • • • Process Q • • • Get B • • • Get A • • • Release B • • • Release A • • •

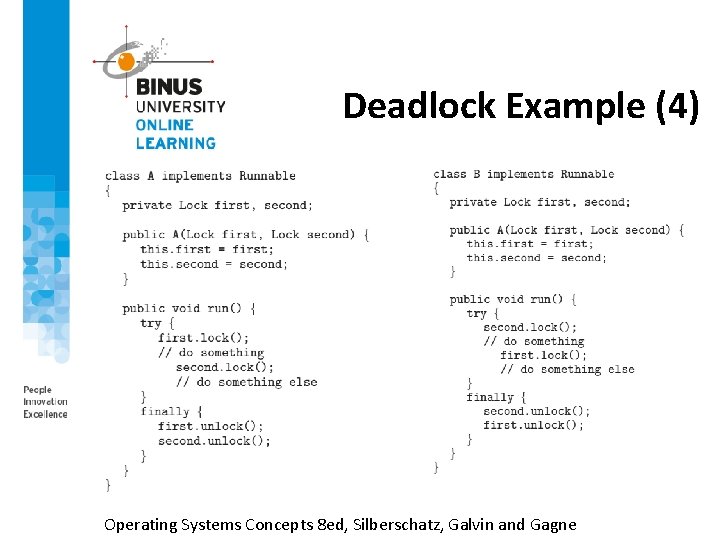
Deadlock Example (4) Operating Systems Concepts 8 ed, Silberschatz, Galvin and Gagne

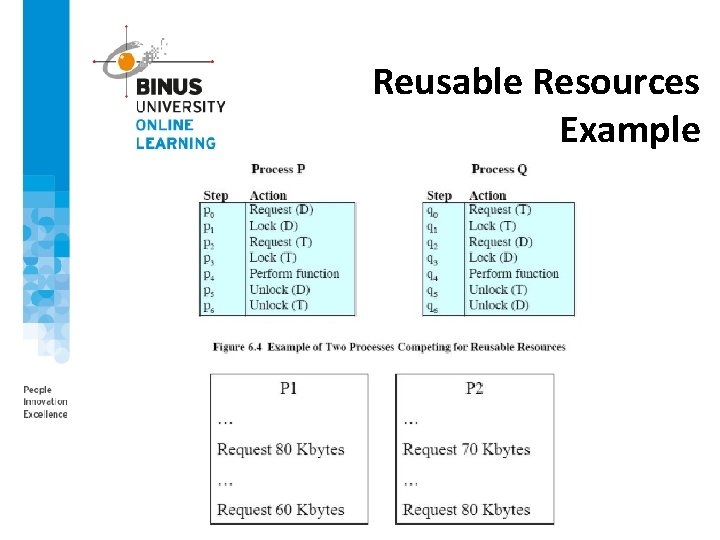
Reusable Resources • A reusable resources is one that can be safely used by only one process at time and is not depleted by that uses. • As an example of deadlock involving reusable resources, consider two process that compete for exclusive access to a disk file D and tape drive T. • Another example of deadlock with a reusale resource has t do with request for main memory.

Reusable Resources Example

Consumable Resources • Consumable resource is one that can be created (produced) and destroyed (consumed). • Example: Consider the following pair of process, attempts to receive a essage from the other process then send a message to the other process. Deadlock occurs if the Receive is blocking.

Consumable Resources (2) • There is no single effective strategy that can deal with all types of deadlock. • Three approaches are common: – Deadlock prevention – Deadlock avoidance – Deadlock detection

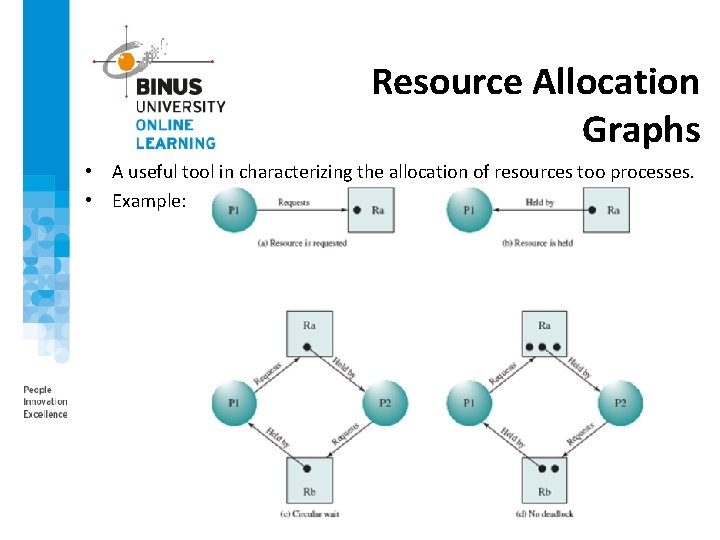
Resource Allocation Graphs • A useful tool in characterizing the allocation of resources too processes. • Example:

Condition for Resource Deadlock (1) • Mutual exclusion: only one process at a time can use a resource. • Hold and wait: a process holding at least one resource is waiting to acquire additional resources held by other processes. • No preemption: a resource can be released only voluntarily by the process holding it, after that process has completed its task. • Circular wait: there exists a set {P 0, P 1, …, P 0} of waiting processes such that P 0 is waiting for a resource that is held by P 1, P 1 is waiting for a resource that is held by P 2, …, Pn– 1 is waiting for a resource that is held by Pn, and P 0 is waiting for a resource that is held by P 0.

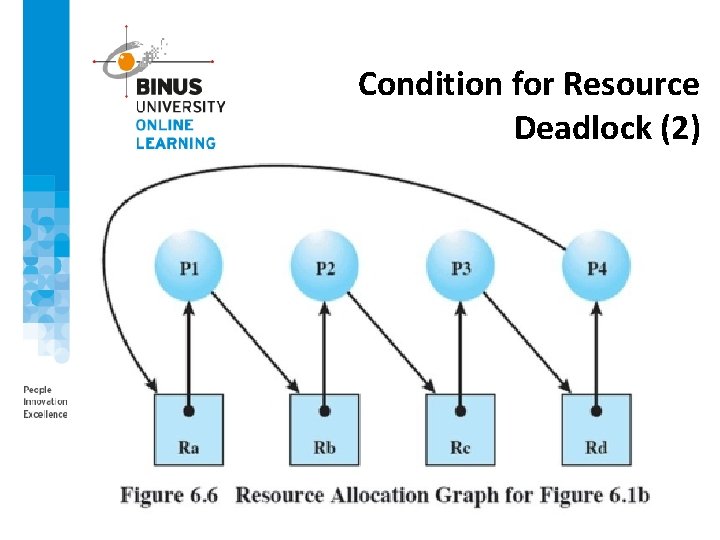
Condition for Resource Deadlock (2)

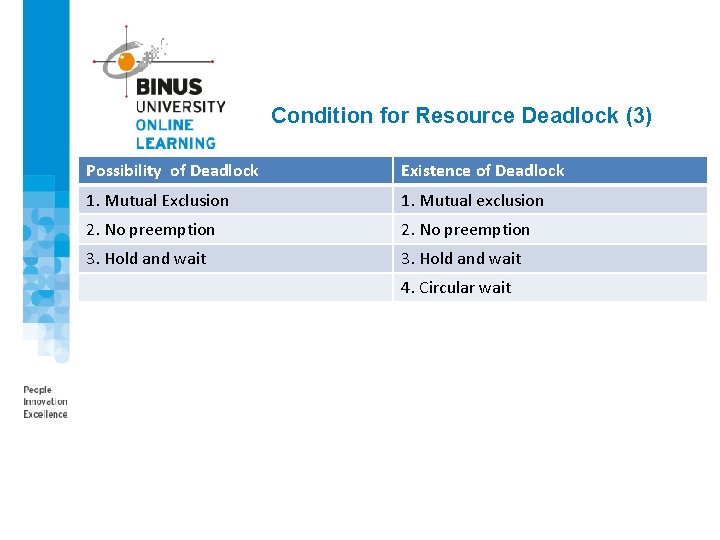
Condition for Resource Deadlock (3) Possibility of Deadlock Existence of Deadlock 1. Mutual Exclusion 1. Mutual exclusion 2. No preemption 3. Hold and wait 4. Circular wait

Deadlock Prevention • The strategy of deadlock prevention is, simply put, to design a system in such a way that the possibility of deadlock is excluded. • We can view deadlock prevention methods as falling into two classes. • An indeirect method of deadlock prevention is to prevent the occurrence of one of the three necessary conditions previously listed. • A direct method of deadlock prevention is to prevent the occurrence of circular wait. • We now examine techniques relate to each of four conditions: – – Mutual exclusion Hold and wait No preemption Circular wait

Deadlock Prevention (1) Restrain the ways request can be made. • Mutual Exclusion – not required for sharable resources; must hold for nonsharable resources. • Hold and Wait – must guarantee that whenever a process requests a resource, it does not hold any other resources. – Require process to request and be allocated all its resources before it begins execution, or allow process to request resources only when the process has none. – Low resource utilization; starvation possible.

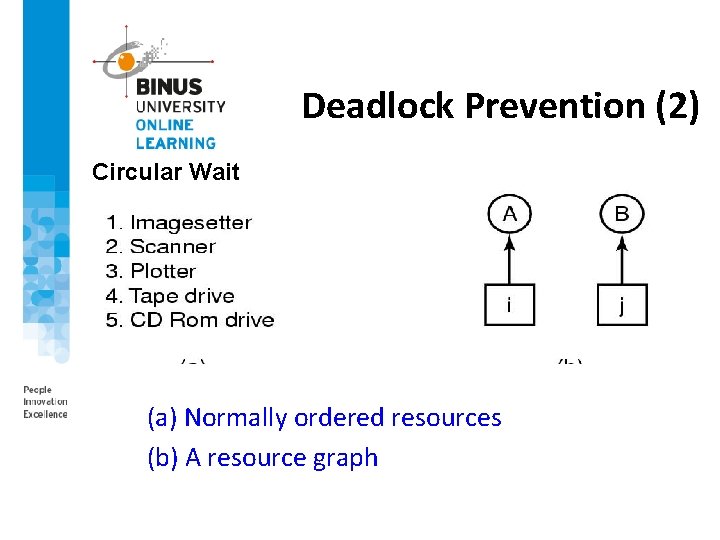
Deadlock Prevention (2) Circular Wait (a) Normally ordered resources (b) A resource graph

Deadlock Prevention (3) No Preemption • This is not a viable option • Consider a process given the printer – halfway through its job – now forcibly take away printer – !!? ?

Deadlock Avoidance • We constrain resource requests ro prevent at least one of the four conditions of deadlock. • On the other hand, allows the three necessary conditions but makes judicious choices to assure that the deadlock point is never reach. • Two approaches to deadlock avoidance: – Do not start a process if its demands might lead to deadlock. – Do not grant an incremental resource request to a process if this allocation might lead to deadlock.

Deadlock Avoidance Requires that the system has some additional a priori information available. • Simplest and most useful model requires that each process declare the maximum number of resources of each type that it may need. • The deadlock-avoidance algorithm dynamically examines the resource-allocation state to ensure that there can never be a circular-wait condition. • Resource-allocation state is defined by the number of available and allocated resources, and the maximum demands of the processes.

Deadlock Avoidance • Process Initiation Denial

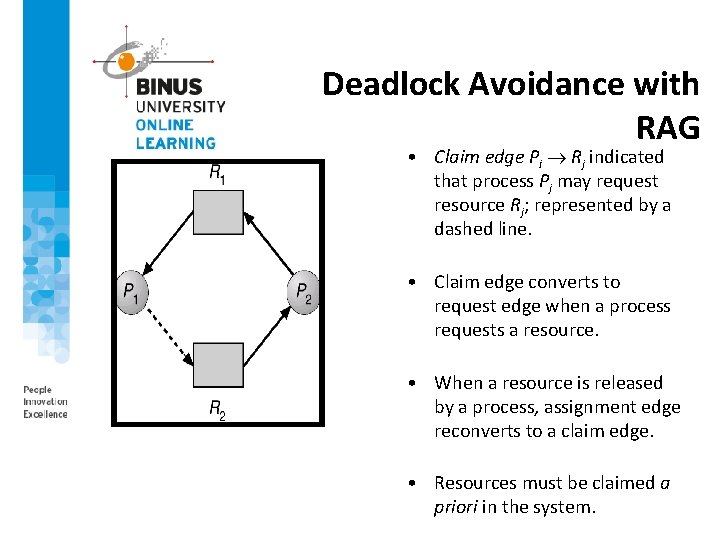
Deadlock Avoidance with RAG • Claim edge Pi Rj indicated that process Pj may request resource Rj; represented by a dashed line. • Claim edge converts to request edge when a process requests a resource. • When a resource is released by a process, assignment edge reconverts to a claim edge. • Resources must be claimed a priori in the system.

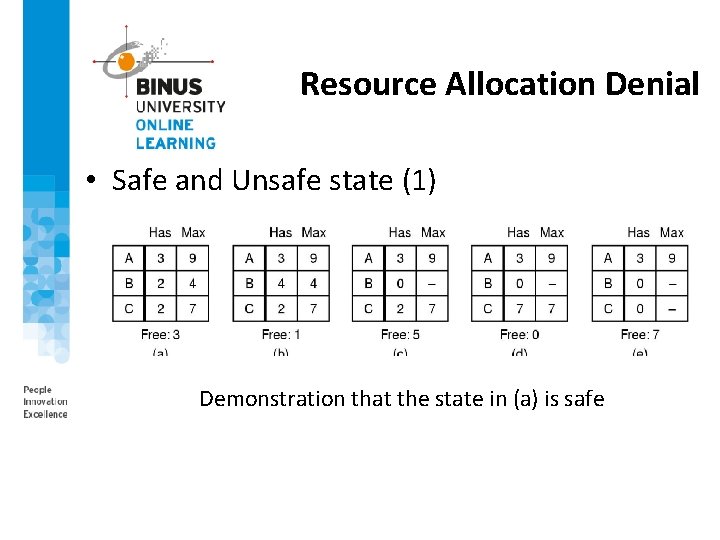
Resource Allocation Denial • Safe and Unsafe state (1) Demonstration that the state in (a) is safe

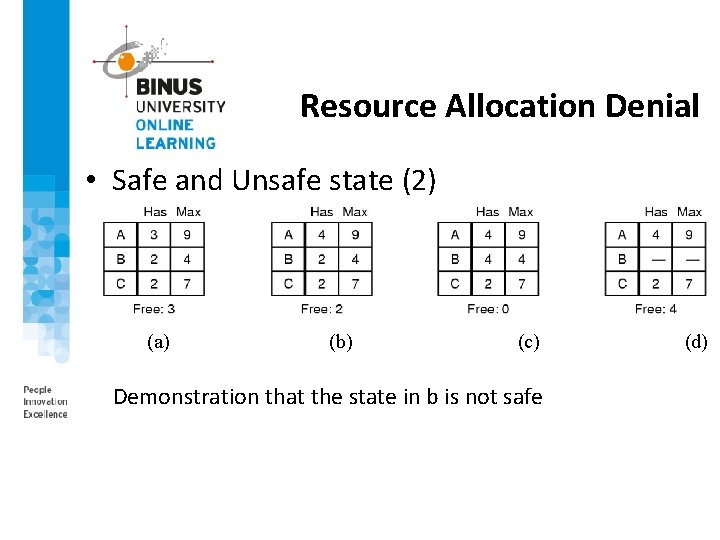
Resource Allocation Denial • Safe and Unsafe state (2) (a) (b) (c) Demonstration that the state in b is not safe (d)

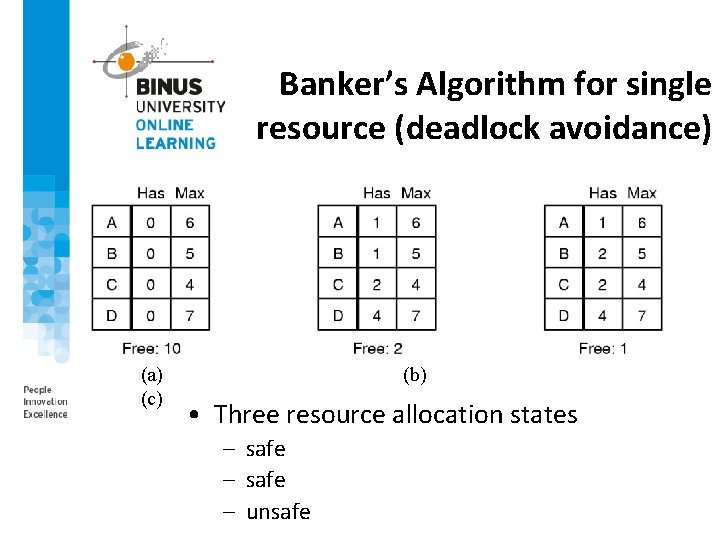
Banker’s Algorithm for single resource (deadlock avoidance) (a) (c) (b) • Three resource allocation states – safe – unsafe

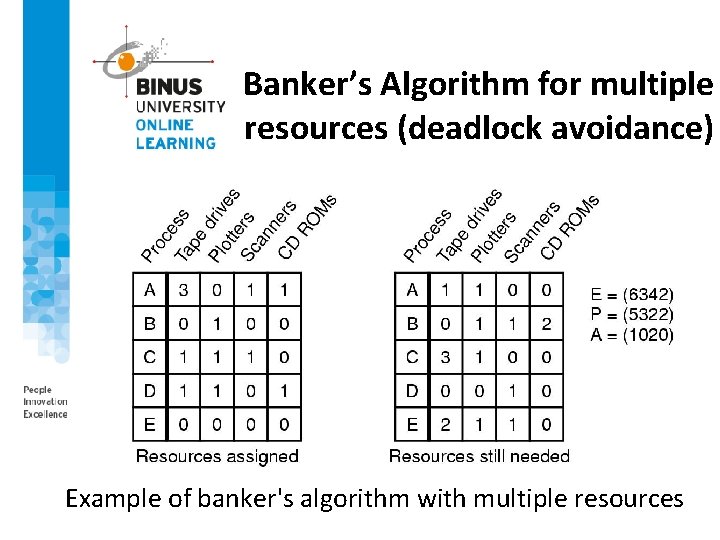
Banker’s Algorithm for multiple resources (deadlock avoidance) Example of banker's algorithm with multiple resources

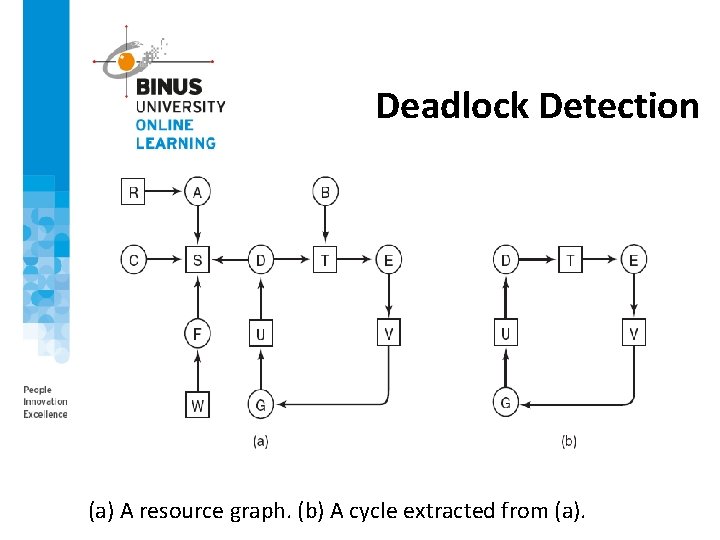
Deadlock Detection (a) A resource graph. (b) A cycle extracted from (a).

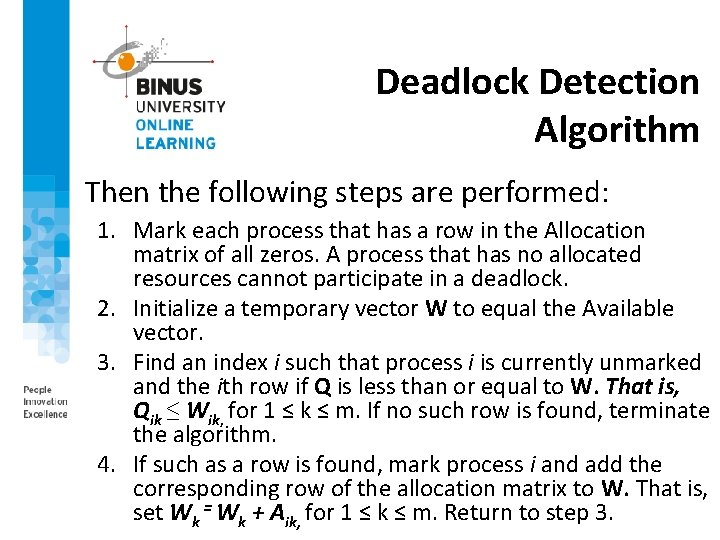
Deadlock Detection Algorithm Then the following steps are performed: 1. Mark each process that has a row in the Allocation matrix of all zeros. A process that has no allocated resources cannot participate in a deadlock. 2. Initialize a temporary vector W to equal the Available vector. 3. Find an index i such that process i is currently unmarked and the ith row if Q is less than or equal to W. That is, Qik ≤ Wik, for 1 ≤ k ≤ m. If no such row is found, terminate the algorithm. 4. If such as a row is found, mark process i and add the corresponding row of the allocation matrix to W. That is, set Wk = Wk + Aik, for 1 ≤ k ≤ m. Return to step 3.

Deadlock Detection Recovery 1. Abort all deadlocked processes. 2. Back up each deadlock process to some previously defined checkpoint, and restart all processes. 3. Successively abort deadlocked processes until deadlock no longer exist. 4. Succesively peempt resources until deadlock no longer exist.

Deadlock Recovery (Resource preemption) • Selecting a victim – minimize cost. • Rollback – return to some safe state, restart process for that state. • Starvation – same process may always be picked as victim, include number of rollback in cost factor.

An Integrated Deadlock Strategy Suggest one approach: • Group resources into a number of different resource classes. • Use the linear ordering strategy defined previously for the prevention of circular wait to prevent deadlocks between resource classes. • Within a resource class, use the algorithm that is most appropriate for thet class.

An Integrated Deadlock Strategy • As an example of this technique, consider the following classes of resources: – Swappable space – Process resources – Main memory – Internal resources.

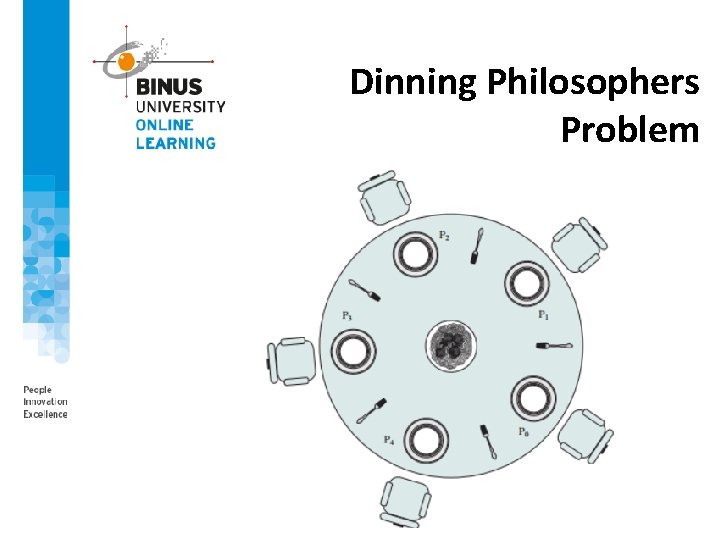
Dinning Philosophers Problem

• Eating Arrangement Dinning Philosophers Problem • A round table on which is set a large serving bowl pf spaghetti, five plates, one for each philosopher, and five forks. • A philosopher wishing to eat goes to his, or her assigned place at the table, and using the two fork on either side of the plate, takes and eats some spaghetti. • The Problem • Devise a ritual (algorithm) that will allow the philosophers to eat. • The algorithm must satify mutual exclusion (no two philosophers can use the same fork at the same time) while avoiding deadlock and starvation (in this case, the term has literal as well as algorithmic meaning).

Solution • Eating Arrangement • A round table on which is set a large serving bowl pf spaghetti, five plates, one for each philosopher, and five forks. • A philosopher wishing to eat goes to his, or • her Theassigned Problem place at the table, and using the • Devise a ritual (algorithm) that will allow the two fork on either side of the plate, takes philosophers to eat. and eats some spaghetti. • The algorithm must satify mutual exclusion (no two philosophers can use the same fork at the same time) while avoiding deadlock and starvation (in this case, the term has literal as well as algorithmic meaning).

Dinning Philosophers • Solution Using Semaphores Problem • Each philosopher first picks up the fork on the left then the fork on the right. • After the philosopher is finished eating, the two forks are replaced on the table. • This solution, alas, leads to deadlock: If allof the philosophers are hungry at the same time, they all sit down, they all pick up the fork on their left, and they all reach out for the other fork, which is not there. • In this undignified position, all philosophers starve. • To overcome the risk of deadlock, we could buy five additional forks (a more sanitary solution) oor teach the philosophers to eat spaghetti with just one fork. • As another approach, we could consider adding an attendant who only allows four philosophers at a time into dining room. • With at most four scated philosophers, at least one philosopher will have access to two fork.

Dinning Philosophers • Solution Using a Monitor Problem • A vector of five condition variables is defined, one condition variable per fork. • This condition variables are used to enable a philosopher to wait for the availability of a fork. • In addition, there is Boolean vector that records the availability status of each fork (true eans the fork is available). • The monitor consist of two procedures. The get_forks procedure is used by a philosopher to seize his or her left and right forks. • If either fork is unavailable, the philosopher process is queued on an appropriate condition variable. • This enables another philosopher process to enter the monitor. • The release_forks procedure is used to make two forks available. • Note the structure of this solution is similar to that of the semaphore solution proposed.

Dinning Philosophers • Solution Using a Monitor Problem • In both cases, a philosopher seizes first the left fork then the right fork. • Unlike the semaphore solution, this monitor solution does not suffer from deadlock, because only one process at a time may be in the monitor. • For example, the first philosopher process to enter the monitor is guaranteed that it can pick up the right fork after it picks up the left fork before the next philosopher to the right has a chance to seize his I her left fork, which is this philosopher’s right fork.

References • Stallings, W. (2018). Operating Systems: Internals and Design Principles. 9 th. ISBN: 978 -0 -13 -467095 -9 A. Tanenbaum(2007), Modern Operating System, 3 rd ISBN: 978 -0136006633 • Abraham Silberschatz, Peter B. Galvin, Greg Gagne (2010). Operating System Concepts 8 th ed. With Java

Thank You