COMP 3371 Cyber Security Richard Henson University of

COMP 3371 Cyber Security Richard Henson University of Worcester November 2015

Week 7: Prevention Strategies n Objectives: Ø Relate B 2 B and B 2 C hesitancy over use of the www to ignorance about the PKI Ø Use high level Information Security policy to drive change in an organisation Ø Identify potential internal and external threats to company data Ø Use vulnerability/penetration testing to check access to the network from outside

Global Use of SSL/PKI n According to recent figures, nearly all top companies in the US are now using SSL/PKI for secure communications: Ø top 40 e-commerce sites Ø all Fortune 500 companies with a web presence n n Conclusion: technology tried and tested; has become industry-standard Problem Ø is technology implemented correctly? Ø who bothers to check?

Security and Online trading n "Online shopping gets a bad rap in the press, but most of the stories reported are anecdotal tales of companies that haven't put successful defensive measures in place“ n "Web businesses running proper screening of customer information are suffering very little, with average fraud losses held to just over 1%. ” n “Fraud control is clearly possible online, although many companies do not implement stringent screening and prevention measures. ”

Why are security problems STILL arising? n Repeating research findings: Ø SSL/PKI reliable n However… Ø Many companies not applying strict security measures such as SSL/PKI are: » being defrauded » skewing the statistics for more responsible online traders n ````````Solution?

Encryption alone is not enough! n The other aspect of SSL/PKI is the establishment of trust between online vendors and customers Ø usually achieved by providing a digital certificate system: » verifies the identity at each end of the communication link » thereby authenticating the server/user n The savvy user knows about digital certificates and expects to be able to view them online

Security Differences between B 2 B and B 2 C n ASSUMING THAT business sets themselves up properly for online trading Øuse server certificates for their servers Øuse SSL to ensure data is encrypted Øtrain users to be aware of danger signs n A B 2 B customer using the web will (SHOULD!!!) understand implications of security messages from the browser

Organisational Data Security Strategy: Where to start? n Can’t START with technology Ø needs to start with ISSUES that need addressing n Should be primarily “top down” Ø concerned with policies, not technical matters… Ø can be supplemented by “bottom up” approach n Technologies can be used to put policies into practice Ø degree of success in the latter depends on: » communication of policies » understanding of technologies

Information Security Policy matters n Who will quantify the threats? ØHead of IT? ØExternal Consultant? Øboth? n Who will suggest strategies to mitigate against those threats? Øas above? n Who will make the policies? ØSenior Management » with guidance…

Creating a Policy n The same principles apply as with the introduction of ANY change in organisational policy Ø MUST come from the top!!! n n Problem: senior management genereally don’t understand IT… Big responsibility on the IT manager to convince senior management: Ø that policy (change) is necessary! Ø that the organisation won’t suffer financially Ø the consequences of NOT implementing such a change

Going beyond a Creating a Policy… n According to the latest BERR figures, the majority of businesses say they have an information security policy Ø but is it implemented? ? ? n One possible approach to making sure policy gets through to all parts of an organisation is to implement a quality standard Ø e. g. ISO 27001… also ISACA, IASME, others

Role of the Adviser/Consultant n n n Specialist knowledge of Information Security in organisations Aware of the need to convince senior management that the cost involved in achieving a quality standard is worthwhile In an SME: Ø the adviser can provide moral, intellectual, and evidential support for the IT manager’s position n In a microbusiness: Ø there is no IT manager… Ø adviser will usually be supporting the most ITliterate employee against a sceptical senior mgt…

How achieving a quality standard could help with business strategy n Whatever the business: Ø any new work will have a cost Ø that cost needs to be qualified n More cost means less profit… Ø what is the ROI of achieving a high level of information security (assurance)?

Potential Financial Benefits of Information Assurance n Need to be sold to senior mgt… Ø less risk of losing valuable (even strategically important…) data » less likely to get embarrassing leaks, which could even get to the media (!) » less likely to fall foul of the law (!) Ø an ever growing set of examples of businesses who have done both of the above » evidence that they lost customers and share price dropped…

Role of Adviser/Consultant n Needs to have good credentials to be credible: Ø plenty of experience in this area Ø contacts in the industry Ø good track record for: » knowledgeability » keeping up to date » communication of knowledge Ø needs to be able to put technical problems into terms that non-technologists can understand…. » very many technical “solutions” available that would be unnecessary if systems and procedures were properly implemented

Protection against the Threats n Internal threats? Øshould be addressed directed through implementation of IS policy n External Threats? ØNormally addressed through: » 1. vulnerability scanning » 2. action taken from vulnerability reports

Information Security Strategy n Identify and quantify ALL potential security threat: Ø BOTH internal » Policy should already exist! » Most likely will need updating Ø AND external » May have been neglected as the Internet creeped into the network! n Need to set out a policy that, if implemented correctly, WILL effectively secure data

What and Why of “Footprinting” n Definition: Ø “Gathering information about a “target” system” n Could be Passive (non-penetrative) or active Ø Find out as much information about the digital and physical evidence of the target’s existence as possible » need to use multiple sources… » may (“black hat” hacking) need to be done secretly

Rationale for “passive” Footprinting n Real hacker may be able to gather what they need from public sources Øorganisation needs to know what is “out there” n Methodology: Østart by finding the URL (search engine) » e. g. www. worc. ac. uk Øfrom main website, find other external-facing names » e. g. staffweb. worc. ac. uk
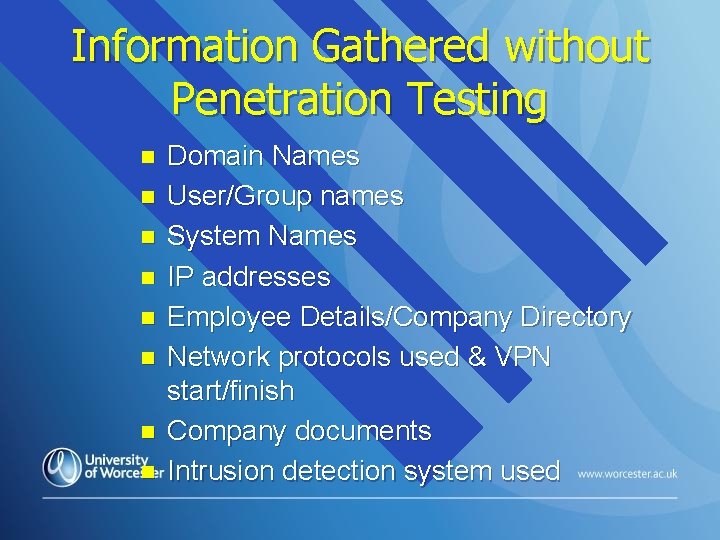
Information Gathered without Penetration Testing n n n n Domain Names User/Group names System Names IP addresses Employee Details/Company Directory Network protocols used & VPN start/finish Company documents Intrusion detection system used

Website Connections & History n History: use www. archive. org: ØThe Wayback Machine Connections: use robtex. com n Business Intelligence: n Øsites that reveal company details Øe. g. www. companieshouse. co. uk

More Company Information… n “Whois” & Check. DNS. com: Ølookups of IP/DNS combinations Ødetails of who owns a domain name Ødetails of DNS Zones & subdomains n Job hunters websites: Øe. g. www. reed. co. uk Øwww. jobsite. co. uk Øwww. totaljobs. com

People Information Company information will reveal names n Use names in n Øsearch engines ØFacebook ØLinked. In n Google Earth reveals: Øcompany location(s)
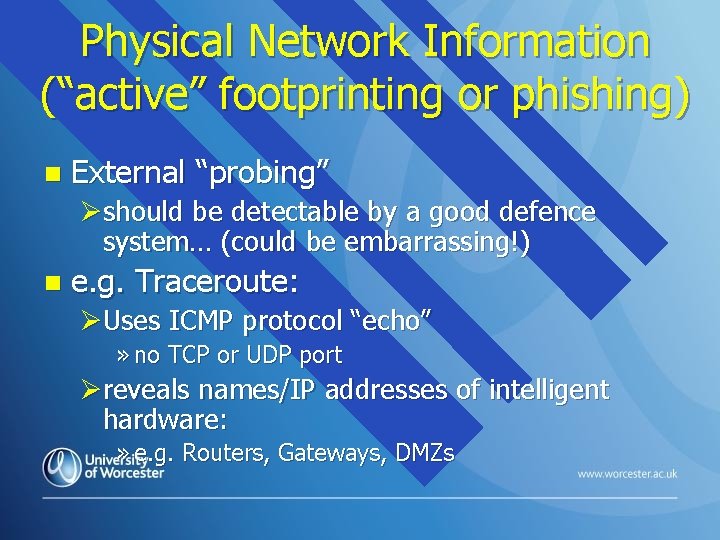
Physical Network Information (“active” footprinting or phishing) n External “probing” Øshould be detectable by a good defence system… (could be embarrassing!) n e. g. Traceroute: ØUses ICMP protocol “echo” » no TCP or UDP port Øreveals names/IP addresses of intelligent hardware: » e. g. Routers, Gateways, DMZs
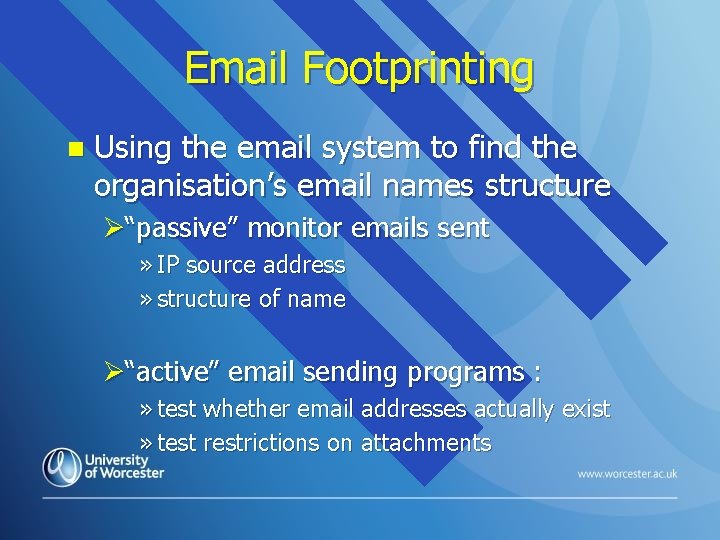
Email Footprinting n Using the email system to find the organisation’s email names structure Ø“passive” monitor emails sent » IP source address » structure of name Ø“active” email sending programs : » test whether email addresses actually exist » test restrictions on attachments

Phishing to extract user data (not intelligence gathering) n Send email user a message with a link or attachment Ølink is a form which tries to get their personal data Øattachment contains malware which will infect their system n Phishing a bit obvious to professionals… » wouldn’t be used by network infiltrators trying to hide their tracks
![Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ] Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ]](http://slidetodoc.com/presentation_image_h2/af9c36900a37faffbb5069b131ae5319/image-27.jpg)
Utilizing Google etc. (“passive”) Google: Advanced Search options: n Uses [site: ] [intitle: ] [allintitle: ] [inurl: ] n ØIn each case a search string should follow Øe. g. “password” n Maltego Øgraphical representations of data
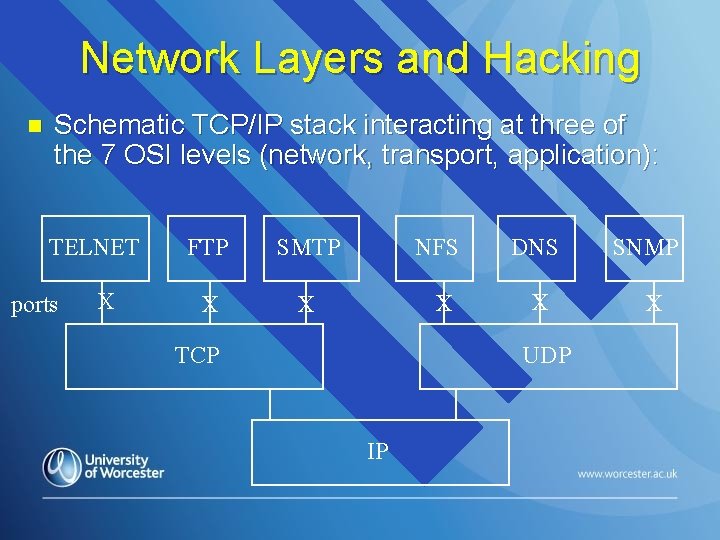
Network Layers and Hacking n Schematic TCP/IP stack interacting at three of the 7 OSI levels (network, transport, application): TELNET ports X FTP SMTP NFS DNS X X TCP UDP IP SNMP X
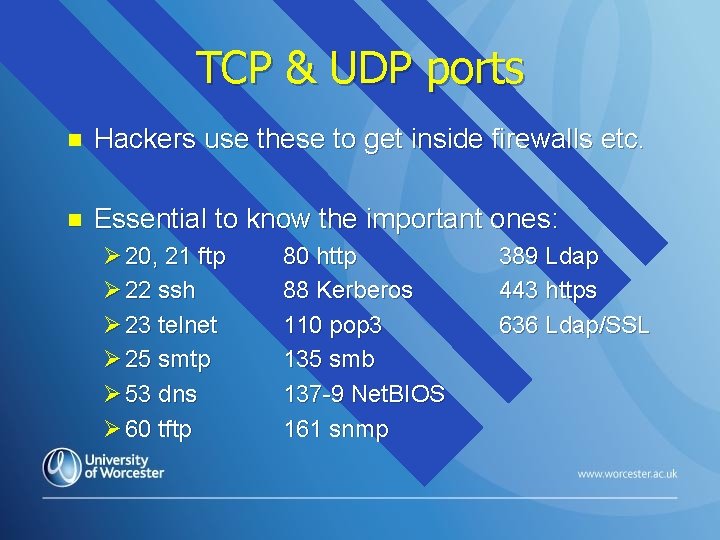
TCP & UDP ports n Hackers use these to get inside firewalls etc. n Essential to know the important ones: Ø 20, 21 ftp Ø 22 ssh Ø 23 telnet Ø 25 smtp Ø 53 dns Ø 60 tftp 80 http 88 Kerberos 110 pop 3 135 smb 137 -9 Net. BIOS 161 snmp 389 Ldap 443 https 636 Ldap/SSL
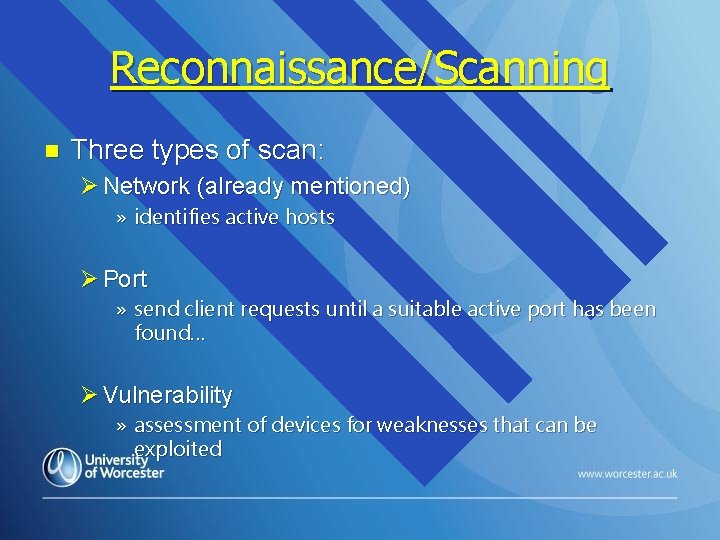
Reconnaissance/Scanning n Three types of scan: Ø Network (already mentioned) » identifies active hosts Ø Port » send client requests until a suitable active port has been found… Ø Vulnerability » assessment of devices for weaknesses that can be exploited

Scanning Methodology Check for Live Systems n Check for open ports n “Banner Grabbing” n Scan for vulnerabilities n Draw Network diagram(s) n Prepare proxies… n

Legality and Vulnerability Scanning n Depends on whether you have asked! Ørunning tests like this requires equipment and an experts time Øwould charge for the service, so… yes, would be normal! n Hacker wouldn’t want organisation to know Øwouldn’t ask! Øillegal but gambles on not being caught!

Ethical Hacking Principles n Hacking is a criminal offence in the UK Øcovered through The Computer Misuse Act (1990) Øtightened in 2006 n Can only be done ”legally” by a trained (or trainee) professional Øa computing student would be considered in this context under the law

Ethical Hacking principles Even if it legal, doesn’t mean it is ethical! n Professionals only hack without permission if there is reason to believe a law is being broken n Øif not… they must ask permission Øotherwise definitely unethical (and illegal… “gaining access without permission”)

“Scanning” Methodology Check for Live Systems n Check for open ports n “Banner Grabbing” n Øe. g. bad html request Scan for vulnerabilities n Draw Network diagram(s) n Prepare proxies… n
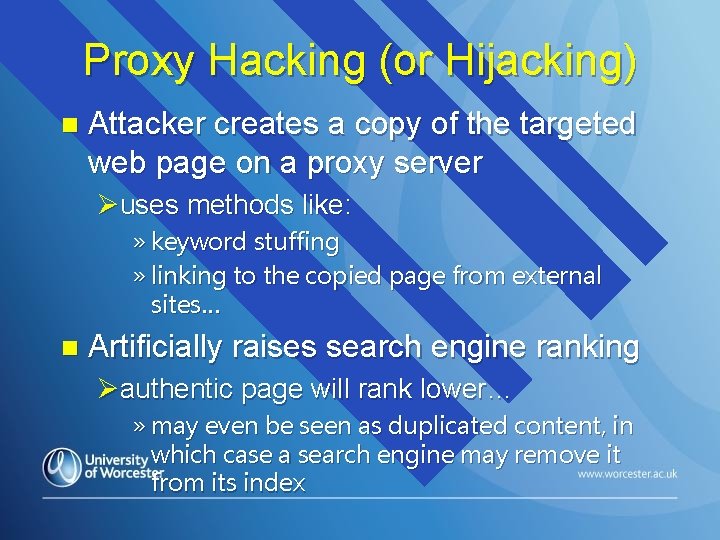
Proxy Hacking (or Hijacking) n Attacker creates a copy of the targeted web page on a proxy server Øuses methods like: » keyword stuffing » linking to the copied page from external sites… n Artificially raises search engine ranking Øauthentic page will rank lower… » may even be seen as duplicated content, in which case a search engine may remove it from its index
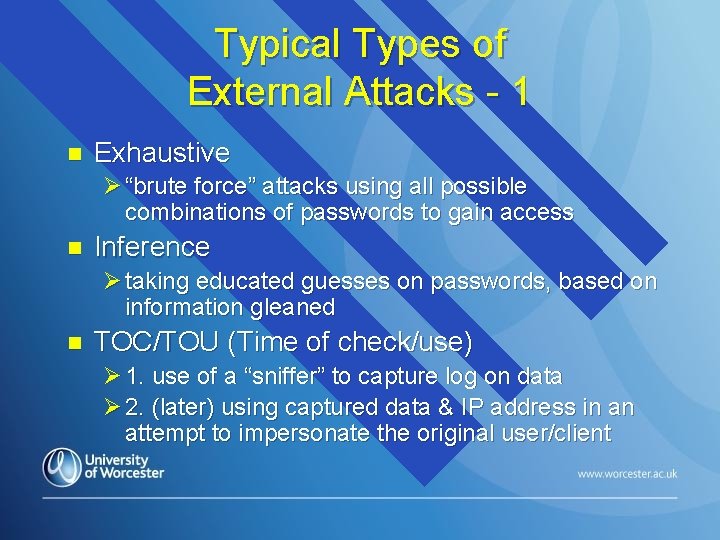
Typical Types of External Attacks - 1 n Exhaustive Ø “brute force” attacks using all possible combinations of passwords to gain access n Inference Ø taking educated guesses on passwords, based on information gleaned n TOC/TOU (Time of check/use) Ø 1. use of a “sniffer” to capture log on data Ø 2. (later) using captured data & IP address in an attempt to impersonate the original user/client

Typical Types of External Attacks - 2 n Three other types of attacks that firewalls should be configured to protect against: Ø denial of service (DOS) attacks Ø distributed denial of service (DDOS) attacks Ø IP Spoofing (pretence that the data is coming from a “safe” source IP address

Blocking TCP ports with a Firewall n Very many TCP and UDP ports: Ø 0 - 1023 are tightly bound to application services Ø 1024 – 49151 more loosely bound to services Ø 49152 – 65535 are private, or “dynamic” n n In practice, any port over 1023 could be assigned dynamically to a service… One of the more useful features of a firewall is that ports can be configured, and therefore data flow can be monitored and controlled
Blocking TCP ports with a Firewall n Generally, TCP ports should be: ØEITHER open for a service (e. g. HTTP on port 80) ØOR… blocked if no service, to stop opportunists n But if the firewall only allows “official services” this can cause problems for legitimate users Øe. g. if port 25 is blocked, email data cannot be sent
Protecting Against TCP/IP Attacks, Probes and Scans n TCP/IP protocol stack has been largely unchanged since the early 1980's: Ømore than enough time for hackers to discover their weaknesses Øoften attack through a particular TCP port
TCP Port 21: FTP (File Transfer Protocol) n FTP servers excellent Ø BUT by their very nature they open up very big security holes Ø those that allow anonymous logins are used: » to launch attacks on the server itself, by connecting to the C: drive and downloading viruses or overwriting/deleting files » to store pirated files and programs n Precaution: Ø configure FTP servers NOT to accept anonymous logins Ø only allow access to port 21 through the firewall to that particular server
TCP Port 23: Telnet n Telnet is really good for providing access to servers and other devices Ø accessing a server via Telnet is very much like being physically located at the server console n Protecting against Telnet is simple: Ø block ALL access to port 23 from the outside Ø block perimeter networks to the inside n Protecting internal servers from attack from the inside: Ø configure them to accept telnet connections from very few sources Ø block port 23 completely…

TCP Port 25: SMTP n Email programs large, complex, accessible… Ø Therefore an easy target… Ø Buffer overrun: » attacker enters more characters – perhaps including executable code - into an email field (e. g. To: ) than is expected by an email server – error could be generated – hackers could gain access to the server and the network Ø SPAM attack: » protocol design allows a message to go directly from the originator's email server to the recipient's email server n n can ALSO be relayed by one or more mail servers in the middle BUT… this is routinely abused by spammers – forward message to thousands of unwilling recipients
Port 25 SMTP: solution… n Buffer Overrun: ØSolution: put server on a perimeter network n Spam Attack ØSolution: DISABLE the relaying facility…
TCP and UDP Port 53: DNS (Domain Name Service) n One of the core protocols of the Internet Øwithout it, domain name to IP address translation would not exist n PROBLEMS: If a site hosts DNS, attackers will try to: Ømodify DNS entries Ødownload a copy of your DNS records (a process called zone transfer)

Port 53 DNS: Solution… n Solution: Ø configure firewall to accept connections from the outside to TCP port 53 only from your secondary DNS server » the one downstream from you e. g. your ISP Ø consider creating two DNS servers: one on your perimeter network, the other on the internal network: » perimeter DNS will answer queries from the outside » internal DNS will respond to all internal lookups » configure a Stateful inspection firewall to allow replies to internal DNS server, but deny connections being initiated from it

TCP Port 79: Finger n A service that enumerates all the services you have available on your network servers: Øinvaluable tool in probing or scanning a network prior to an attack! n To deny all this information about network services to would-be attackers, just block port 79…
TCP Ports 109 -110: POP (Post Office Protocol) n POP easy-to-use… Øbut sadly it has a number of insecurities n The most insecure version is POP 3 which runs on port 110 Øif the email server requires POP 3, block all access to port 110 except to that server Øif POP 3 not used, block port 110 entirely…

TCP Ports 135 and 137 Net. BIOS n The Microsoft Windows protocol used for file and print sharing Ølast thing you probably want is for users on the Internet to connect to your servers' files and printers! n Block Net. BIOS. Period!
UDP Port 161 SNMP n SNMP is important for remote management of network devices: Ø but also it poses inherent security risks Ø stores configuration and performance parameters in a database that is then accessible via the network… n n If network is open to the Internet, hackers can gain a large amount of very valuable information about the network… So… if SNMP is used: Ø allow access to port 161 from internal network only Ø otherwise, block it entirely

Denial of Service (Do. S) Attacks An attempt to harm a network by flooding it with traffic so that network devices are overwhelmed and unable to provide services. n One of the primary DOS attacks uses Ping, an ICMP (Internet Control Message Protocol) service: n Øsends a brief request to a remote computer asking it to echo back its IP address

“Ping” Attacks n n Dubbed the "Ping of Death“ Two forms: Ø the attacker deliberately creates a very large ping packet and then transmits it to a victim » ICMP can't deal with large packets » the receiving computer is unable to accept delivery and crashes or hangs Ø an attacker will send thousands of ping requests to a victim so that its processor time is taken up answering ping requests, preventing the processor from responding to other, legitimate requests n Protection: Ø block ICMP echo requests and replies Ø ensure there is a rule blocking "outgoing time exceeded" & "unreachable" messages

Distributed Denial of Service Attacks/IP Spoofing n Related : Ø A DDOS attack has occurred when attackers gain access to a wide number of PCs and then use them to launch a coordinated attack against a victim » often rely on home computers, since they are less frequently protected (they can also use worms and viruses) Ø If IP spoofing is used, attackers can gain access to a PC within a protected network by obtaining its IP address and then using it in packet headers

Protection against DDOS & IP Spoofing n n Block traffic coming into the network that contains IP addresses from the internal network… In addition, block the following private IP, illegal and unroutable addresses: Ø Illegal/unroutable: » 255, 27. 0. 0. 0, 240. 0, & 0. 0 Ø “Private” addresses useful for NAT, or Proxy Servers (RFC 1918): » » » n 10. 0 -10. 255 172. 16. 0. 0 -172. 31. 255 192. 168. 0. 0 -192. 168. 255 Finally, keep anti-virus software up-to-date, & firewall software patched and up-to-date
- Slides: 55