COMP 3122 Network Management Richard Henson March 2011




































- Slides: 42

COMP 3122 Network Management Richard Henson March 2011

Week 8: Internet Access, Web Services, and Remote Access n Objectives: – Configure a specified web server to support www & ftp sites – Run a world wide web site that includes server scripting – Configure a server to accept services by remote access

Web Services n Client-Server principles… – installed on a web server – used on a web browser n n By default, provide a network service that runs on TCP port 80, but port could vary Products tend to be specific to the operating system e. g. – Internet Information Server runs on Windows NT/2000/XP/2003/2008/7 – Apache runs on Unix/Linux

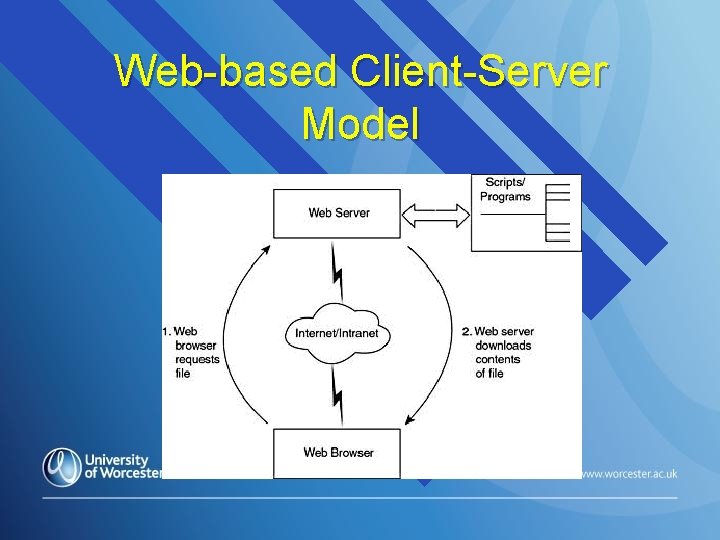
Request for Service access The following diagram illustrates the relationship between web client and web server processes: client requests information server processes the request and sends a response back to the client…

Other web-related Network Services n Most popular: – ftp (file transfer), TCP port 21 – smtp (mail between internet sites) port 25 n With IIS, each service provides a default folder, default port, to act as the root e. g. – Wwwroot (80) – Ftproot (21) – Mailroot (25)

Accessing Web Services across a local network n Each web service also has a unique name – e. g. mywebsite, myftpsite n For Internal Access… – used with IP address to access web services across the Intranet – www services accessed at the client end using an Internet Browser – local name maps by default to root www service folder e. g. wwwroot n Could also in theory be used externally e. g. » \myservermywebsite

Access Control and Internal Web Services (Intranet) n Access controlled by: – EITHER username/password protection of pages beyond the home page – OR user login name authentication with active directory (or equivalent) for access to the service

Accessing Web Services through the world wide web n Full URL needed to gain access – i. e. local www name. domain name n Access to service controlled through a requirement to login – by default, all users automatically logged on to an “anonymous” account (Internet Guest)

Web-based Client-Server Model

IIS and Security n IIS has been coupled with Windows Servers since 1996… – originally enabled VB code to create. asp files to perform tasks and interact directly with the client browser » included a number of COM+ objects – by 2000 generally acknowledged to be one of the major security weaknesses of Microsoft platforms interfacing with the web » most viruses came in via IIS & VB code

The. net framework and web services n Major change in 2001 ->. net framework – server scripts no longer contained source code (except HTML) – not supported by Windows 2000 (IIS v 5) » not yet developed at that time… – Windows 2003 has. net built-in (IIS v 6) n Windows 2000 setups need to add the. net framework and upgrade IIS if they are to be used for supporting. net based websites

. net framework and Active Directory n n To get maximum benefit from the structure of. net, the object framework should interface well with active directory – this was not the case with. net v 1. 1 – and therefore also with the first release of 2003 Server… Windows 2003 WAS a success… – But NOT because of. net framework!

. net framework v 2. 0 and Active Directory n v 2 released some time after 2003 server – included “Active Directory namespace” » System. Directory. Services – allowed more effective linking of active directory objects with. net objects. e. g. ’s » http: //www. vsj. co. uk/dotnet/display. asp? id=409 – helped. net to become a popular platform

. net framework v 3. 5, v 4. 0 and Active Directory n Problem: – System. Directory. Services often needs further coding to be effective… n Recent developments… –. net v 3. 5, 4. 0 – use System. Directory. Services. Account. Management namespace » manages directory objects independent of the System. Directory. Services namespace – uniform access and manipulation of user, computer, and group security principals across the multiple principal stores: » Active Directory Domain Services (AD DS) » Active Directory Lightweight Directory Services (AD LDS) » Machine SAM (MSAM).

Management of Groups of Web Pages n IIS needs to perform a number of server tasks, but especially to provide: – access to the contents of web sites in a controlled way – home or “root” directory path – name definition(s) for “home page” e. g index. html, index. aspx – the right scripting “engine” for website files so they are compiled, interpreted, or (if runtime e. g. active X) just executed

Home Page Service for websites n Agreed home page convention by ISPs: – home page is index. htm, index. html – this page is downloaded when the domain name is entered in the browser window n Microsoft home page convention: – default. html – default. aspx n Latter can (should? ) be changed to conform to general convention

Setting up an IIS FTP service n FTP protocol is ancient (RFC 238, 1972) – still popular & works well for uploading/downloading n IIS allows configuration of an FTP server for: – Internal ftp access: » local ftp service name – External ftp access: » local name. domain name n FTP server can be accessed: – directly through the browser – using an ftp client

Accessing an IIS SMTP service SMTP protocol (or Internet Mail forwarding) developed from FTP (RFC 821, 1978) n Web-based or Internal SMTP service set up in the same way as FTP n – same access rights/limitations, etc. n Further software (Exchange Server) needed to provide a full mail service

Setting up an Exchange Mail Server Service n Exchange is complex software – Mail. Servers have large resource requirements n Uses x 500 data storage standard – store for details of mailbox users – can interface with details of Active Directory users! n Further stores: – incoming messages that need distributing to mailboxes – mailboxes & their messages – database of existing mailbox names

A POP 3 service n n SMTP sends messages between Internet servers Cannot be used to download mail from mailboxes to clients – need to use the POP 3 protocol n POP 3 Server principles: – user logs on to server – if user is authorised: » any messages in that user’s mailbox are located » all messages downloaded to local folder by POP 3 client software

Administering the Web Service n Software GUI tools for IIS administration – MMC – management snap-in n Command line tools for IIS administration – direct access via browser n n n Access to these tools needs to be restricted… Service should allow a number of different web sites to be set up in different folders Excellent website (for W 2003, IIS v 6) – http: //www. windowsnetworking. com/articles_tutorial s/Web-Sites-Windows-2003. html

Administering the WWW Service n IP address of the web server is normally that of the host machine – needs to be provision for » » n manual settings several addresses e. g. multiple websites running through separate folders Typical set up & management tasks required for each website: – website name, port, home directory, default filename pecking order – optional username/password & access permissions – “virtual directories” – security permissions for use with server certificates and the public key infrastructure (PKI)

Web Services and The Cloud n Companies like Amazon, Google (apps), and salesforce. com have created web services (XML/http) and made them available to a wider public for storing their data – this approach benefits companies most that are experience relatively quick growth – instead of getting new storage resources every year, organisations can quickly and easily purchase more "cloud space"

Cloud Services, the future, and Security n Cloud computing can offer applications as-aservice as well… – a future is predicted where everything is outsourced and no kind of local CPU is even needed – employees will simply have a monitor, keyboard, and mouse that will allow them to connect to the cloud for all of their resources (!) – but will this be secure? And what comeback will organisations have if something goes wrong?

Open Access v Logon to Web Server? Allowing network or external users to access part of the server has its risks! n One strategy: use “anonymous login” n – anyone can log on and gain access to the service – but they only get “guest-equivalent” (i. e. minimum) access rights » can be frustrating…

Open Access v Logon to Web Server? n Alternative: request username/password access – access rights then depend on user privilege – no longer “open access” – but good for auditing and control

Open Access v Logon to Web Server? n Servers in general: – potentially open to attack by both internal and external network users (security vital) n Standard web server practice: – no file access possible other than at and below the designated root – main issue for the system regarding user requests for web access: » whether or not to allow access at all » whether to allow read only or read-write access

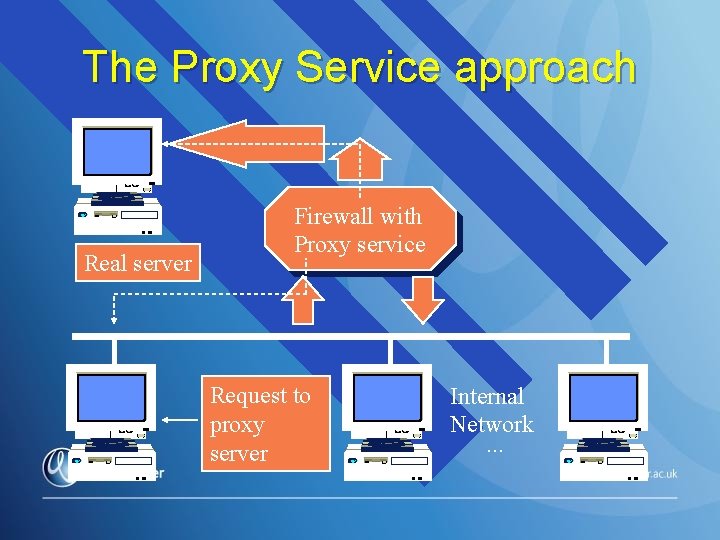
Offering a Proxy Service n n A Proxy Server runs on a server being used as a Firewall Acts as an intermediate party between the Internet and local network services: – intercepts user requests for services such as FTP – decides whether or not to forward them to the true server n The effect is that the internal and external computers talk to the proxy service rather than directly to each other

The Proxy Service approach Real server Firewall with Proxy service Request to proxy server Internal Network. . .

Proxy Service - continued n n n The user on either side of the firewall is presented with an illusion that they are talking to a real server when in fact they are dealing with a proxy So if an outside user tries to “hack” into the network server the actual internal network architecture is hidden A proxy server can be programmed to block certain requests, sites, actions e. g: – blocking certain WWW sites – preventing FTP downloads

Proxy Service Provides network client machine with controlled access to the Internet n Clients can only gain access to the Internet via the Proxy Service n Enables the network administrator to control: n – which TCP ports, and therefore which protocols can be used – which (if any) external IP addresses can be accessed/filtered

Proxy Service Can also provide a storage facility for web pages (web cache) n Mans that clients don’t need to keep going out onto the Internet to access the same page n – web cache speeds up access to regularly accessed web pages – less actual www traffic, so more bandwidth available to those accessing pages that haven’t been previously downloaded

Streaming Media Service n Serves streaming sound/video/animation files to multiple users simultaneously – across the network – across the Internet » If connection has sufficient bandwidth n Also provides the conversion software codecs to produce and run the streaming media files

How Does Streaming Technology Work? A streaming sound file is no longer in a. wav or. mid format n Using special software, any sound file can be: n – converted/compressed into a streaming format – Accessed remotely using e. g. rtsp: //server/path/filename n A suitable Audio player is then needed to play the streaming audio – must contains its own software codecs

Real Audio Probably the most popular Internet streaming system n. ram file contains the search string for the local browser n. ra file contains the sound file that can be sent bit by bit using streaming technologies n

How Does Streaming Technology Work? n The. ra file is stored on a remote server – path begins with rtsp: // » tells an application that: » the file is located externally on a streaming sever » it is using Real Time Streaming Protocols – next in the path: » name of the folder on the streaming server where the file resides » finally the name of the target file itself

Remote Access Service (RAS) n Configured in Windows 2003 as Routing and Remote Access service – not available by default – needs to be installed n Provides ways of allowing access to the server/network externally

Remote Access Service n ISPs use RAS to provide logon connections for multiple users via: – standard (analogue) phone link » one modem needed on/connected to the server for each remote connection – ISDN – ADSL n As with www, ftp, email services: – appropriate security arrangements need to be in place – appropriate client-server TCP protocols required

Remote Access Service n Public Telephone network, security options: – Callback security » » » server makes a note of the caller’s number hangs up calls the caller back! – Logon » only authorised users are allowed to log on – Encryption » log on data can/should? be encrypted – PPTP filtering » only allows PPTP packets through

Remote Access Service n Dial-up (OSI level 1/2) Protocols – SLIP (Serial Line Interface Protocol) » developed in 1984 » now old hat! – PPP (Point-Point Protocol) » current standard » more flexible than PPP » allows a greater range of transport protocols » Allows remote allocation of IP addresses to clients by DHCP server

Remote Access via VPN within the Internet n Protocols for creating a secure channel through the Internet: – PPTP (Point-Point Tunnelling Protocol) » secure version of PPP » port 1723 – L 2 TP now more popular » port 1701

Thanks for Listening