Community Seismic Network for Early Warning Rishi Chandy

































































- Slides: 101

Community Seismic Network for Early Warning Rishi Chandy Rita A. and Øisten Skjellum SURF Fellow Daniel Obenshain Kiyo and Eiko Tomiyasu SURF Scholar Daniel Rosenberg Kiyo and Eiko Tomiyasu SURF Scholar Annie Tang Mentors: K. Mani Chandy, Robert Clayton, Andreas Krause California Institute of Technology

Who are we? Daniel Obenshain Annie Tang Rishi Chandy Daniel Rosenberg

Our Mentors Dr. K. Mani Chandy Professor of Computer Science Dr. Andreas Krause Assistant Professor of Computer Science Dr. Rob Clayton Professor of Geophysics Michael Olson Grad Student Computer Science

Background n Earthquakes are dangerous threats – USGS estimates 2000 deaths and $200 billion damages from 7. 8 magnitude quake

Background n Earthquakes are dangerous threats – USGS estimates 2000 deaths and $200 billion damages from 7. 8 magnitude quake n Early warning could minimize suffering – Activate safeguards in critical operations

Background n Earthquakes are dangerous threats – USGS estimates 2000 deaths and $200 billion damages from 7. 8 magnitude quake n Early warning could minimize suffering – Activate safeguards in critical operations n Providing early warning is an interesting problem – Bayesian decision theory, geology, distributed computing

Background n Earthquakes are dangerous threats – USGS estimates 2000 deaths and $200 billion damages from 7. 8 magnitude quake n Early warning could minimize suffering – Activate safeguards in critical operations n Providing early warning is an interesting problem – Bayesian decision theory, geology, distributed computing n Current seismic network is too sparse – Can’t provide enough early warning

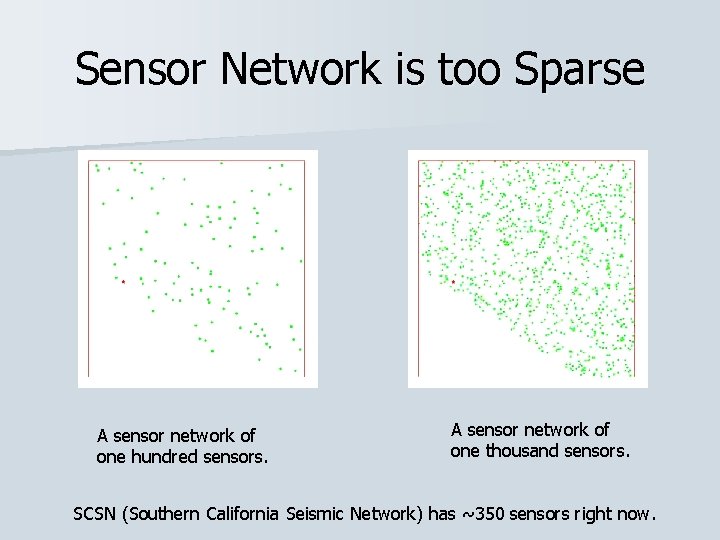
Sensor Network is too Sparse A sensor network of one hundred sensors. A sensor network of one thousand sensors. SCSN (Southern California Seismic Network) has ~350 sensors right now.

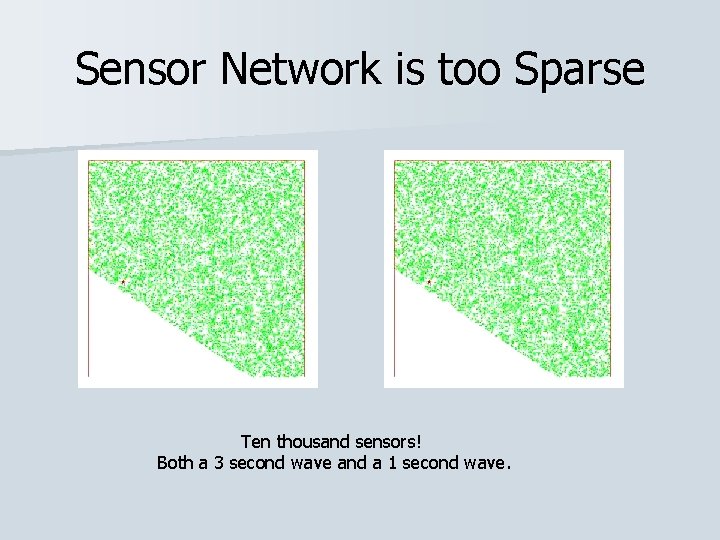
Sensor Network is too Sparse Ten thousand sensors! Both a 3 second wave and a 1 second wave.

Early Warning Can Help Slow trains

Early Warning Can Help Slow trains Stop elevators

Early Warning Can Help Slow trains Stop elevators Open fire station doors

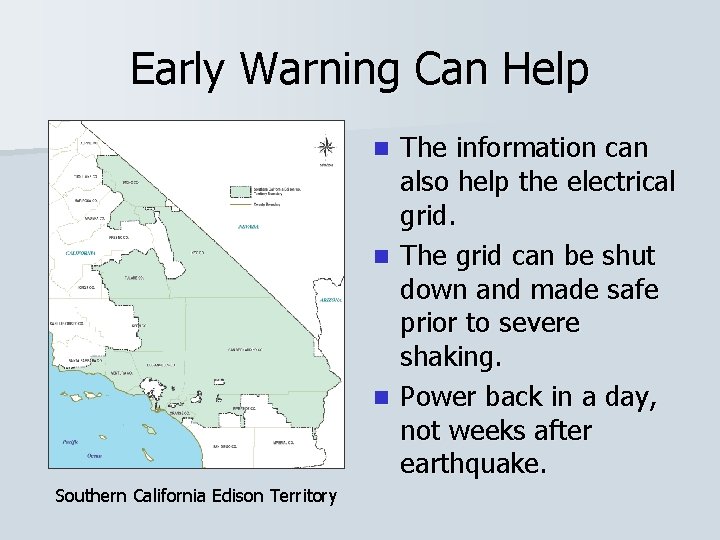
Early Warning Can Help n Southern California Edison Territory The information can also help the electrical grid.

Early Warning Can Help The information can also help the electrical grid. n The grid can be shut down and made safe prior to severe shaking. n Southern California Edison Territory

Early Warning Can Help The information can also help the electrical grid. n The grid can be shut down and made safe prior to severe shaking. n Power back in a day, not weeks after earthquake. n Southern California Edison Territory

Benefits n Provide Early Warning n Easy deployment in areas without existing seismic networks – Peru and Indonesia § Cell phones are prevalent n Identify hard-hit areas quickly – Direct first responders

That’s why we’re doing it. What about how we’re doing it?

Expand the Network n We want to add more data.

Expand the Network n We want to add more data. n Why not get data from as many sources as possible?

Expand the Network n We want to add more data. n Why not get data from as many sources as possible? n Add in acceleration devices of different types, cell phones, laptops, etc.

Expand the Network n We want to add more data. n Why not get data from as many sources as possible? n Add in acceleration devices of different types, cell phones, laptops, etc. n The User installs some client software and his or her acceleration data becomes part of the network.

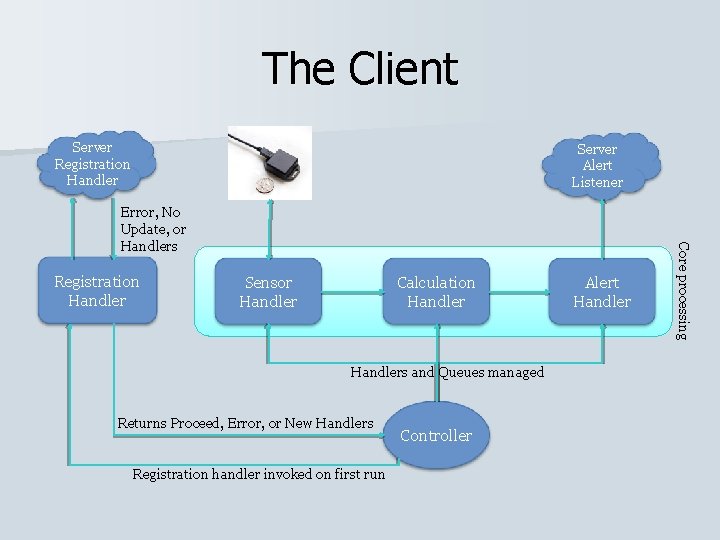
The Client Server Registration Handler Server Alert Listener Registration Handler Sensor Handler Calculation Handlers and Queues managed Returns Proceed, Error, or New Handlers Registration handler invoked on first run Controller Alert Handler Core processing Error, No Update, or Handlers

Picking Algorithm n How often should the client send data to the server?

Picking Algorithm n How often should the client send data to the server? n Only when significant shaking is occurring.

Picking Algorithm n How often should the client send data to the server? n Only when significant shaking is occurring. n How does the client know?

Picking Algorithm n How often should the client send data to the server? n Only when significant shaking is occurring. n How does the client know? n It performs a simple calculation on the incoming data stream.

Picking Algorithm n How often should the client send data to the server? n Only when significant shaking is occurring. n How does the client know? n It performs a simple calculation on the incoming data stream. n We call this the “Picking Algorithm. ”

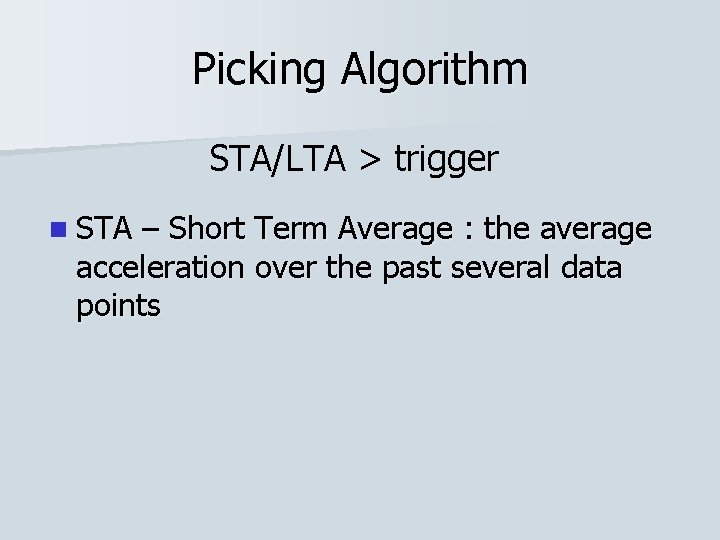
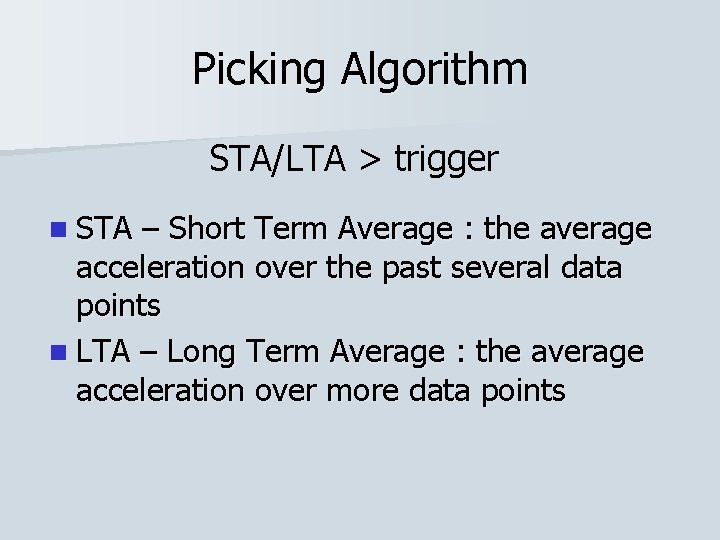
Picking Algorithm STA/LTA > trigger

Picking Algorithm STA/LTA > trigger n STA – Short Term Average : the average acceleration over the past several data points

Picking Algorithm STA/LTA > trigger n STA – Short Term Average : the average acceleration over the past several data points n LTA – Long Term Average : the average acceleration over more data points

Picking Algorithm STA/LTA > trigger n STA – Short Term Average : the average acceleration over the past several data points n LTA – Long Term Average : the average acceleration over more data points n trigger – a threshold

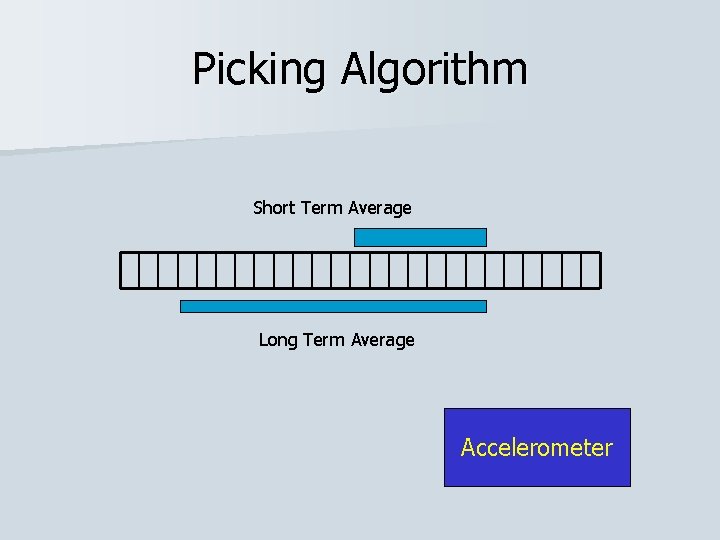
Picking Algorithm Short Term Average Long Term Average Accelerometer

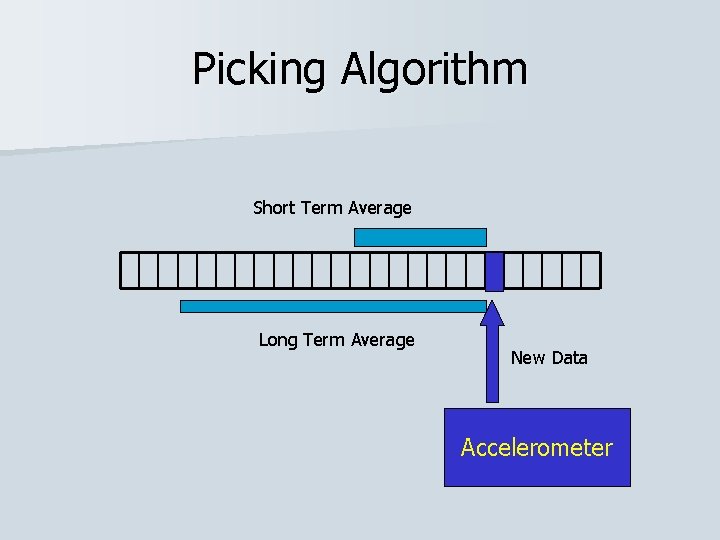
Picking Algorithm Short Term Average Long Term Average New Data Accelerometer

Picking Algorithm Short Term Average Long Term Average Accelerometer

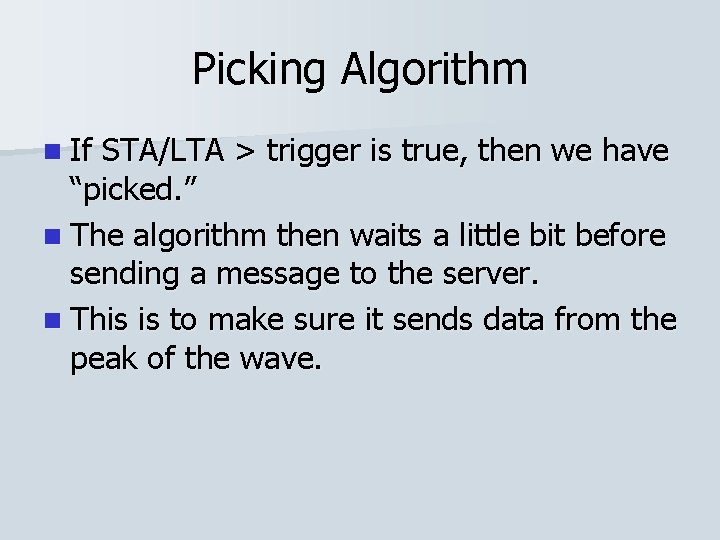
Picking Algorithm n If STA/LTA > trigger is true, then we have “picked. ”

Picking Algorithm n If STA/LTA > trigger is true, then we have “picked. ” n The algorithm then waits a little bit before sending a message to the server.

Picking Algorithm n If STA/LTA > trigger is true, then we have “picked. ” n The algorithm then waits a little bit before sending a message to the server. n This is to make sure it sends data from the peak of the wave.

Picking Algorithm 1 2 3 Pause for this length of time before sending a message to the server. 1. Detected significant shaking 2. Maximum shaking 3. Sent message to server

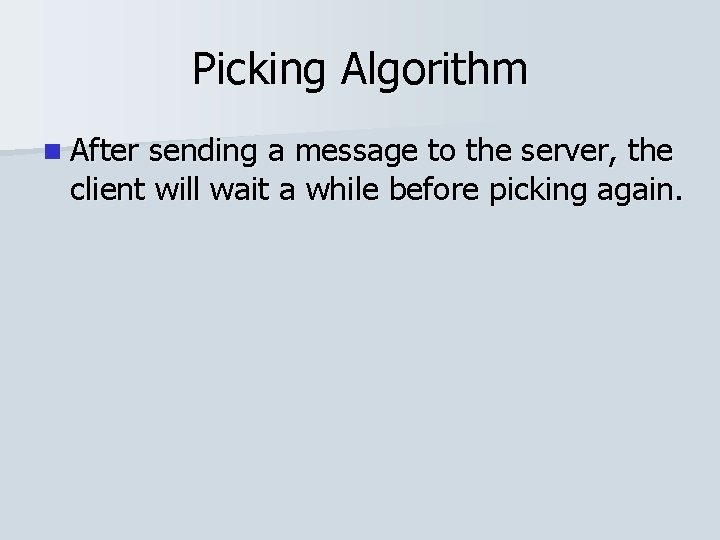
Picking Algorithm n After sending a message to the server, the client will wait a while before picking again.

Picking Algorithm n After sending a message to the server, the client will wait a while before picking again. n This is to stop the client from picking multiple times for the same shaking.

Picking Algorithm 1 2 Delay for this length of time before picking again. 1. Last message sent to server 2. The coda of the earthquake, where we don’t want to pick

Picking Algorithm n Five tunable parameters.

Picking Algorithm n Five tunable parameters. – Length of STA

Picking Algorithm n Five tunable parameters. – Length of STA – Length of LTA

Picking Algorithm n Five tunable parameters. – Length of STA – Length of LTA – Value of trigger

Picking Algorithm n Five tunable parameters. – Length of STA – Length of LTA – Value of trigger – How long to wait after picking before sending a message to the server

Picking Algorithm n Five tunable parameters. – Length of STA – Length of LTA – Value of trigger – How long to wait after picking before sending a message to the server – How long to wait between messages

Picking Algorithm n Five tunable parameters. – Length of STA – Length of LTA – Value of trigger – How long to wait after picking before sending a message to the server – How long to wait between messages n They can all be tuned by the server, on a client-by-client basis.

GUI n Acceleration data is displayed in real time on the user’s screen.

GUI n Acceleration data is displayed in real time on the user’s screen. n Promotes use of the software.

GUI n Acceleration data is displayed in real time on the user’s screen. n Promotes use of the software. n Can be used in science classrooms to explain project.

GUI n Acceleration data is displayed in real time on the user’s screen. n Promotes use of the software. n Can be used in science classrooms to explain project. n Each message to the server marked by a red line.

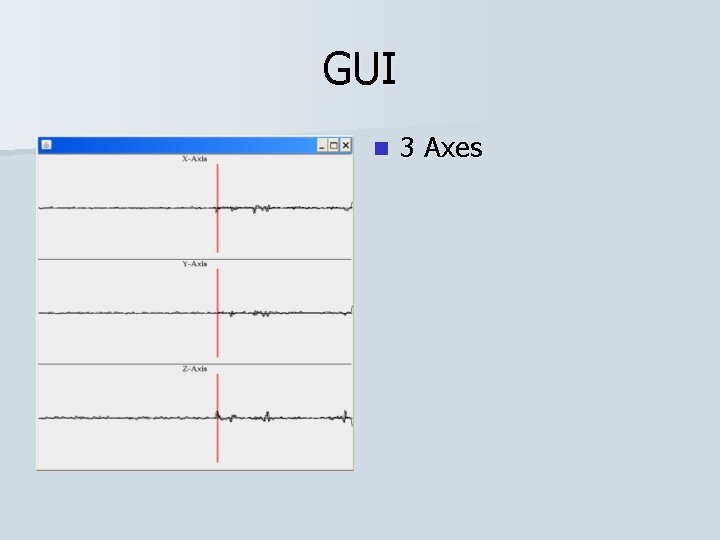
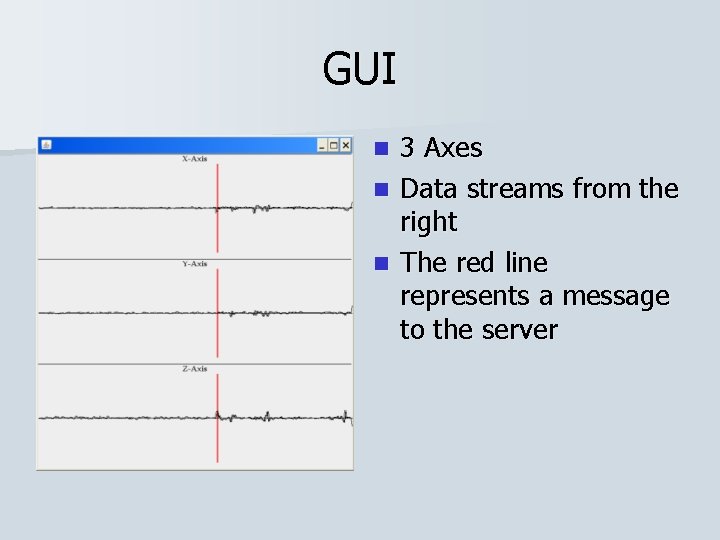
GUI n 3 Axes

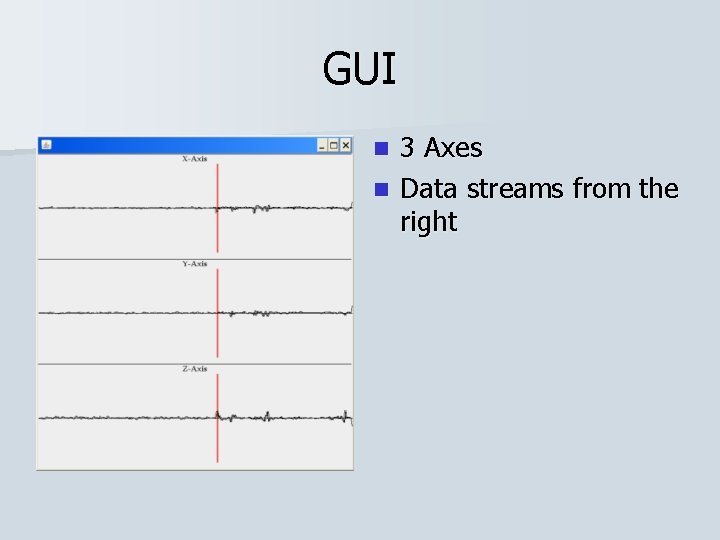
GUI 3 Axes n Data streams from the right n

GUI 3 Axes n Data streams from the right n The red line represents a message to the server n

Sensor Validation n Tested our sensor with artificial event.

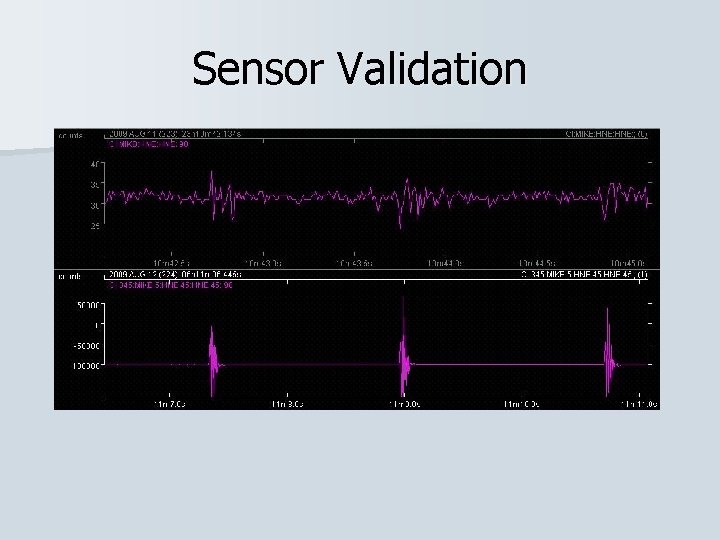
Sensor Validation n Tested our sensor with artificial event. n Compared our sensor to the SCSN (Southern California Seismic Network) sensor in the basement of Millikan Library.

Sensor Validation n Tested our sensor with artificial event. n Compared our sensor to the SCSN (Southern California Seismic Network) sensor in the basement of Millikan Library. n Caused seismic activity with a sledgehammer.

Sensor Validation

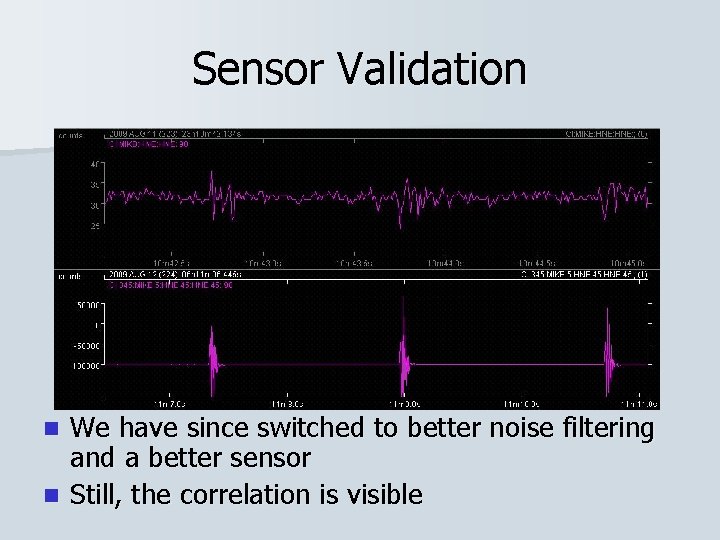
Sensor Validation We have since switched to better noise filtering and a better sensor n Still, the correlation is visible n

Client Side Overview n Registration – Keys, location, sensor type, address (optional) – Client ID n Data Storage – SAC file, ring buffer n Heartbeat – Sensor “check in”, log request, playback request

Registration n TCP Message: – Keys, location, sensor type, address (optional) – Client ID n Key Generator: – Key pair: public key & private key – DSA

Registration n Skyhook – Software only Hybrid Positioning System (XPS) § Combine WPS, GPS, and Cellular Towers – Accuracy: 10 to 20 meters – Latitude, longitude, address – Reasons to choose Skyhook: § GPS signal is not always available § Fast and accurate § Cons: needs Wi-Fi – IP Address

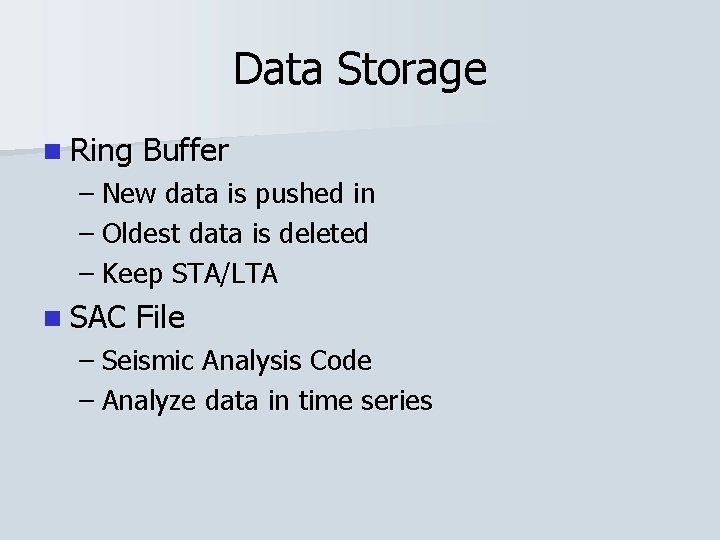
Data Storage n Ring Buffer – New data is pushed in – Oldest data is deleted – Keep STA/LTA n SAC File – Seismic Analysis Code – Analyze data in time series

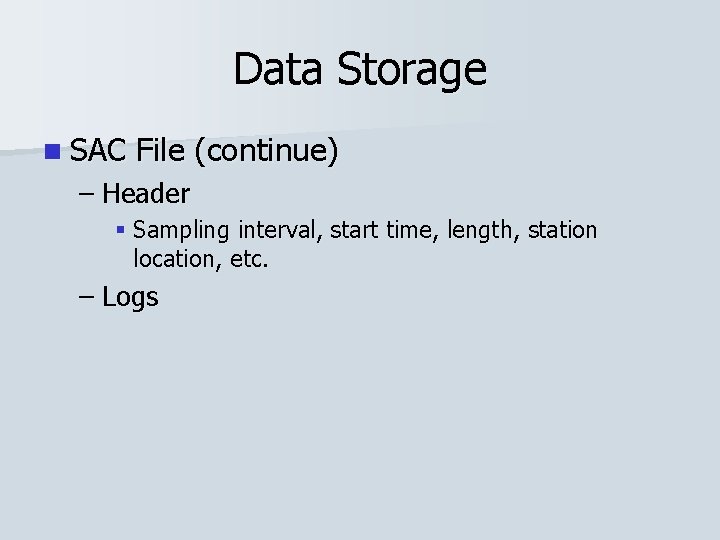
Data Storage n SAC File (continue) – Header § Sampling interval, start time, length, station location, etc. – Logs

Heartbeat n TCP Message – Time, location, Client ID – Log Request, Playback Request, Updates n Purpose – Active Sensors – Current Locations – Communication between client and server – Calibration

Data

Data We have lots of it.

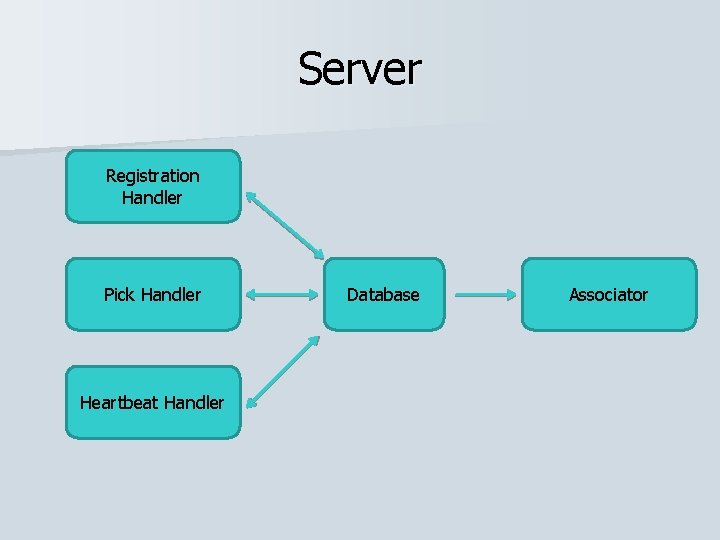
Server n Four main tasks – Handle new user registration

Server n Four main tasks – Handle new user registration – Listen for pick messages

Server n Four main tasks – Handle new user registration – Listen for pick messages – Handle heartbeat messages

Server n Four main tasks – Handle new user registration – Listen for pick messages – Handle heartbeat messages – Analyze data n Main tech – Java, PHP, Javascript, XML – My. SQL – Apache Java Libraries

Server Registration Handler Pick Handler Heartbeat Handler Database Associator

Messaging n Open and extensible XML schema – Allows others to join the network n We use TCP and UDP

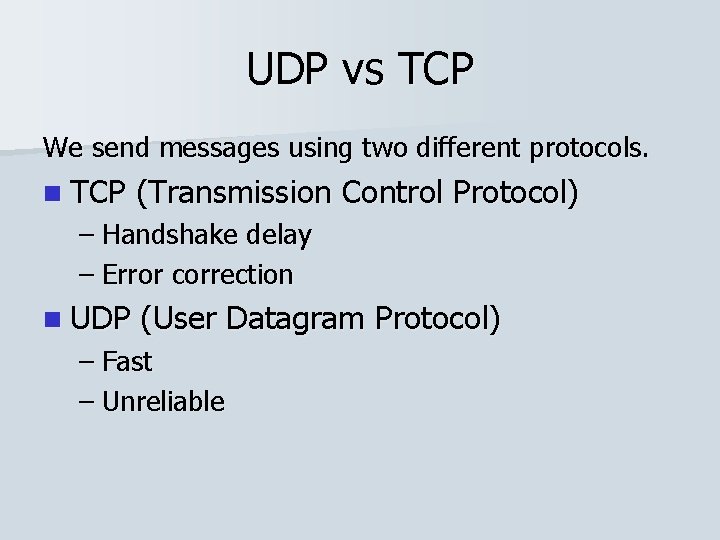
UDP vs TCP We send messages using two different protocols. n TCP (Transmission Control Protocol) – Handshake delay – Error correction

UDP vs TCP We send messages using two different protocols. n TCP (Transmission Control Protocol) – Handshake delay – Error correction n UDP (User Datagram Protocol) – Fast – Unreliable

Pick Message Handler Pick messages are sent using UDP packets. n Reasons: – Unsure of condition of network – Speed is important

Pick Message Handler n Listen for incoming picks

Pick Message Handler n Listen for incoming picks – Parse message

Pick Message Handler n Listen for incoming picks – Parse message – Check signature

Pick Message Handler n Listen for incoming picks – Parse message – Check signature – Check for playback flag § If the flag is not present, the pick is stored in the database. § If the message is flagged as playback, it is written to a separate table in the database.

Security n All messages from the client are verified using XML signatures.

Security n All messages from the client are verified using XML signatures. – Client has private key, Server knows public key

Security n All messages from the client are verified using XML signatures. – Client has private key, Server knows public key – Client signs messages using its private key

Security n All messages from the client are verified using XML signatures. – Client has private key, Server knows public key – Client signs messages using its private key – Server verifies messages using the stored public key

Security n All messages from the client are verified using XML signatures. – Client has private key, Server knows public key – Client signs messages using its private key – Server verifies messages using the stored public key n This prevents any message interception attacks n We can control valid client. IDs

Server-side Challenges n Incoming messages from a vast network – Can’t get overwhelmed – Want to grab as much data as we can – Application must be scalable n Response time is critical – Excessive latency is unacceptable – Indiana Jones effect n Methods must be accurate and precise – EW is useless otherwise

Registration n Clients sends XML – Latitude, Longitude – Public Key n Server returns XML – Unique client. ID

Example Registration XML <registration> <public. Key>349 oi 3 j 4 oij 32 ui 23</public. Key> <location> <latitude>40. 779761</latitude> <longitude>-74. 0310</longitude> </location> <location. Description> 1200 E California Blvd Pasadena, CA 91125 </location. Description> <sensor>usb: device. ID</sensor> </registration>

Heartbeat n Clients update us on their status – location n Server returns: – Software updates – Tunable parameters – Playback waveforms – Log Requests n Location is updated in DB

Playback Operation n We can distribute waveforms for clients to simulate

Playback Operation n We can distribute waveforms for clients to simulate n Stress-test the network n Evaluate new algorithms n Determine network latencies

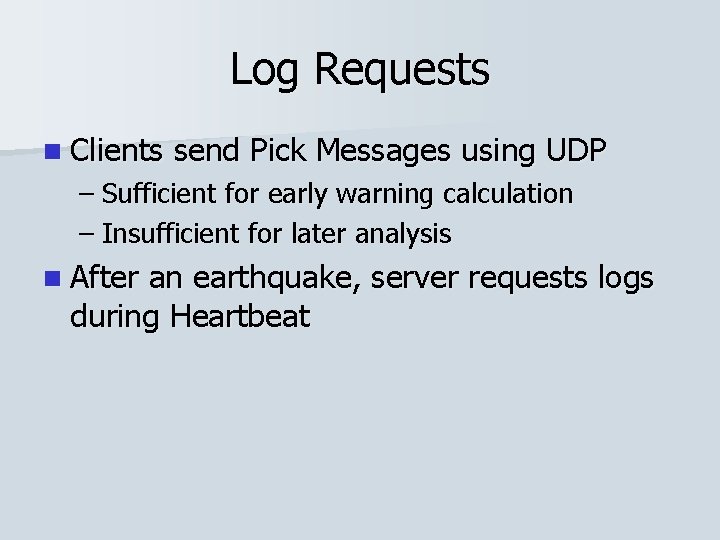
Log Requests n Clients send Pick Messages using UDP – Sufficient for early warning calculation

Log Requests n Clients send Pick Messages using UDP – Sufficient for early warning calculation – Insufficient for later analysis n After an earthquake, server requests logs during Heartbeat

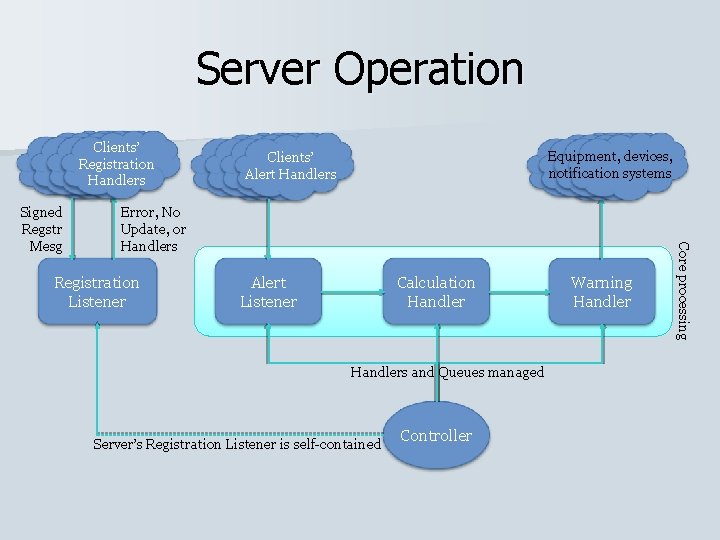
Server Operation Clients’ Registration Handlers Equipment, devices, notification systems Error, No Update, or Handlers Registration Listener Alert Listener Calculation Handlers and Queues managed Server’s Registration Listener is self-contained Controller Warning Handler Core processing Signed Regstr Mesg Clients’ Registration Alert Handlers

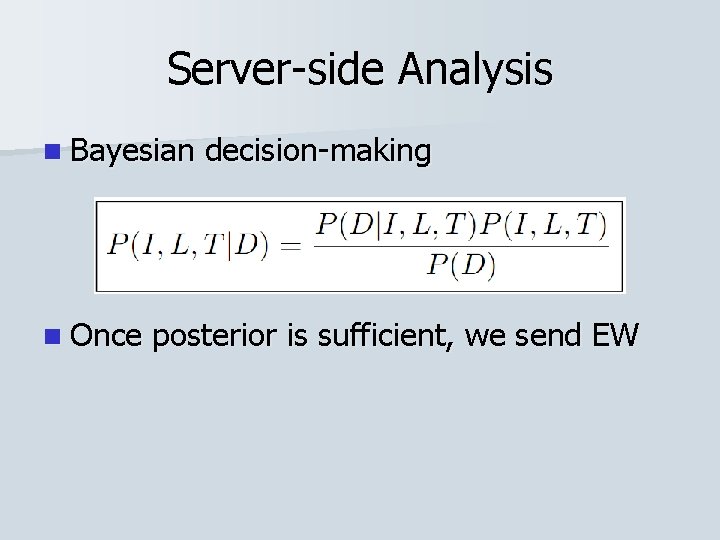
Server-side Analysis n Bayesian decision-making

Server-side Analysis n Bayesian n Once decision-making posterior is sufficient, we send EW


Next Steps n Cell phones w/ accelerometers – Android n Laptops w/ accelerometers n Google App Engine – Robust, scalable

Acknowledgements n Thanks to Professors K. Mani Chandy, Rob Clayton, Andreas Krause, and Michael Olson for their mentorship and guidance n Our generous SURF sponsors – Rita A. and Øisten Skjellum – Kiyo and Eiko Tomiyasu

Thank You Q&A Session