Common Hacking Attacks Learning Outcomes for this Module





















- Slides: 45

Common Hacking Attacks

Learning Outcomes for this Module • Gain an understanding of what hacking is. • How to protect yourself from being hacked. • What you should do if you have been hacked. • Learn about various methods of attacks and hacks. • Understand how passwords are cracked if a strong password is not used. 2

Introduction

What is Hacking? (1 of 2) • An activity that is meant to compromise digital devices • Such as computers, tablets, smartphones, etc. • Hacking is also intended to gain access to information or financial data • While the idea of hacking is not unlawful, many cybercriminals utilize hacking for illegal actions 4

What is Hacking? (2 of 2) • Hacking is largely associated with manipulating devices beyond a developer’s intent. • It can also be applied to a psychological trick, or people hacking, called Social Engineering. • In Social Engineering, someone is trying to take advantage of you to gain access to your information or devices – often through trust, fear, excitement or instinctive reactions. 5

Hacking as a Cybercrime – Why? • Unfortunately hacking is largely used by cybercriminals for: • Financial gain, such as through identity theft. • Corporate espionage to steal an organization’s confidential information. • Their own enjoyment, despite the harm caused to others. 6

What Could Happen if I am Hacked? • Various account login credentials can be stolen. • Attackers may gain access to your financial accounts. • Unauthorized purchases could be made with any saved and stolen credit card information. • Your computer may become a part of an attacker’s network of compromised machines. • Any personal information of yours might be sold to others. 7

Additional Information • A 1983 a Newsweek cover article was the first use of the term “hacker” in mainstream media. • There is a hacking attempt every 39 seconds. • This was found by a Clark School Study at The University of Maryland. • Hacking does not just affect individuals. • Full organizations, cities, and countries have all been victims to various forms of hacks. 8

Common Attacks Common attacks that can happen

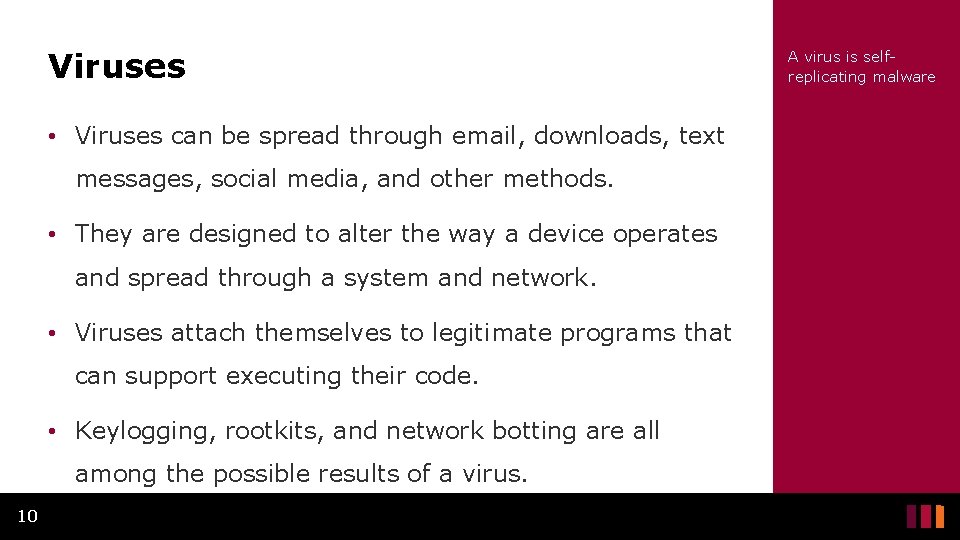
Viruses • Viruses can be spread through email, downloads, text messages, social media, and other methods. • They are designed to alter the way a device operates and spread through a system and network. • Viruses attach themselves to legitimate programs that can support executing their code. • Keylogging, rootkits, and network botting are all among the possible results of a virus. 10 A virus is selfreplicating malware

Keylogging • The malware will read and record the keystrokes that are being used on the victim’s device. • Allow a cybercriminal to gain knowledge such as login and password information. • Keyloggers are largely used for identity theft purposes. 11

Phishing • Contacting groups of people through email. • Emails often are from fraudulent or spoofed sources. • Links or attachments are included in the emails to get victims to either access a site and provide personal information or install malware to their device. • Often rely on urgency, excitement or fear. • For more information, please see our Phishing module. 12

Browser Hijacking • A system’s registry or browser configuration files can fall victim to a hijack. • Attempting to browse certain websites or folders will instead redirect the victim’s system to another website or run specific files that the malware has specified. • This is essentially “hijacking” the system’s browser. • Antivirus software is ideal for removing a hijack. 13

Zombie Computing • A network of computers that are already compromised. • Phishing is a method that can lead to this. • Victims may open a link that will open a portal between their computer and a hacker’s giving them remote access to their device and network. • Frequently used for Distributed Denial-of-Service (DDo. S) attacks. 14

Distributed Denial-of-Service Attack - 1 • Abbreviated as a DDo. S Attack. • DDo. S attacks are targeted attacks. • Rather than attempting to gain access to information, DDo. S attacks are used to disrupt traffic to a server. • A network of computers, made up of bots (or zombies), repeatedly send requests to the target’s IP (Internet Protocol) address to overwhelm the server, which may slow or even crash the server. 15

Distributed Denial-of-Service Attack - 2 • DDo. S attacks may happen between corporate competitors. • Intentionally slowing a service on an important day, such as launch of a new product, can often be an attempt to get users to leave the attacked platform and move to a competitor’s platform. 16

Ransomware (1 of 2) • An attack that uses encryption to lock out a victim’s files and device(s). • The attacker generates a public key that is used to encrypt files on their target’s system. • A private key is generated that stays on the attacker’s system that can be used to decrypt the files. 17 Encryption is the scrambling of data into an unreadable format

Ransomware (2 of 2) • The attacker often demands a ransom from their victims, such as something of monetary value, with the claim that they will exchange the private key to decrypt the data. • A ransom should never be paid. • There is no guarantee the attacker will uphold their end of their demands. 18

Social Engineering (1 of 2) • A technique used to manipulate people into giving up information or access through human error. • It can be done on a computer through means such as phishing or off a computer with methods such as spam phone calls. • Criminals use Social Engineering to gain access to sensitive information. 19

Social Engineering (2 of 2) • Criminals will often claim to be someone who should have access, without being checked for proper authorization. • Social media websites are often filled with alleged games or quizzes that will not allow a user to “play” them until they authorize giving access to personal information. • This is also social engineering. 20

Fake Network and Backdoor Access • Hackers can setup fake Wi-Fi networks to get victims to connect to their own network. • The attacker can then gain access to the system that has connected and install other kinds of malware onto the connected device. • The victim’s system can even be used to further spread malware to other networks and systems as a backdoor. 21

Wi-Fi Pineapple • A Wi-Fi Pineapple is used to deauthorize a victim from their current public network and then connect them to the attacker’s network. • A victim may not even realize that their network connection changed. • It is important to protect yourself when using a public network Ensure networks are secure with a lock or consider getting a VPN (Virtual Private Network). 22

Hacking on Mobile Platforms • In the digital age, hacking has gone beyond personal computers and now affects smartphones as well. • Android phones are a large target of smartphone hacking. • A phone hack could grant access to voicemails, calls, and the microphone and camera of the phone. • Always keep a phone’s operating system up to date and avoid installing software from unknown sources. 23

Password Hacking Methods Common methods used to hack passwords

Think About the Following • Do you use long or short passwords? • A longer password (8+ characters) is more secure. • Does your password mix uppercase and lowercase. characters? Does it contain symbols? • Variation in a password can help improve security. • Do you use the same password on multiple accounts? • Use a unique password for every account! 25

Why Hackers Crack Passwords • Getting access to a password is the easiest way to gain access to any account. • Many individuals use the same password across multiple accounts. • This makes them even more vulnerable and cracking one account can give an attacker access to many accounts. 26

Brute Force Attack • Attempts to use every possible character combination to guess a password. • It is a slow but incredibly popular method of attack. • Given enough time and resources, a brute force attack will eventually figure out the password. • A strong password can exponentially increase the timeframe it takes for a brute force attack to be successful, from seconds to years. 27

Dictionary Attack • Uses a tool to check every word in a dictionary to see if there is a match. • If the password is a word found within the dictionary, it can be cracked. • Dictionary files exist for many languages, not only in English. 28

Guessing Attack • An attack that involves guessing a password to gain access to an account. • Requires no additional software. • Often used against victims whom the attacker has some pre-existing knowledge of. • Is effective against simple passwords, such as “password” or words related to an interest of an individual, such as a pet’s name. 29

Hybrid Attack • Uses the same technique as a Dictionary attack. • Checks for dictionary words with a combination of characters set before and/or after the word. • An example is: password 123 30

Story – CRA Hacked

Story – CRA Hacked (1 of 2) • In Summer 2020 the Canadian Revenue Agency was targeted by multiple cyberattacks. • The website had to be temporarily shut down. • Several thousand accounts were affected by the data breach. • The shutdown impacted services and prevented Canadians from being able to access their accounts. 32

Story – CRA Hacked (2 of 2) • The hack was discovered after many Canadians began to report their personal information on the CRA website had changed. • Information including direct deposit info was altered in order to have money sent to unauthorized accounts. • Many of the accounts that were illegally accessed were from usernames and passwords acquired from hacks and data breaches from other websites. 33

Conclusions

In Conclusion (1 of 5) • Hacking is usually associated with being a method of altering or compromising digital devices. • Often hacking is associated with cybercrimes. • For financial gain, identity theft, personal enjoyment, and other reasons. • Hacking can also be done without a device through a manipulated technique called social engineering. 35

In Conclusion (2 of 5) • A hack can compromise your personal information, including financial accounts. • Use strong varied passwords and update them regularly • Be creative with security questions. • Turn on two-factor authentication when able. 36

In Conclusion (3 of 5) • Always have a firewall running and have antivirus solutions installed on your system. • Keep your devices updated. • Only give personal information online after ensuring the website is secure. • Practice safe email habits and avoid phishing scams. 37

In Conclusion (4 of 5) • Be careful of what information you provide and the links you click on social media. • Destroy the data on old hardware before recycling it. • Scan your devices with antivirus solutions if you have been hacked. • Change your passwords on any affected accounts. 38

In Conclusion (5 of 5) • Monitor your financial accounts such as credit card usage Report any suspicious or unauthorized purchases. • Contact the proper authorities regarding the hack. • Be aware of the many kinds of hacks that exist. • Visit sites such as Have I Been Pwned to verify if your email is associated with sites that have experienced data breaches. • https: //haveibeenpwned. com/ 39

Canadian Internet Registration Authority (CIRA) These modules were made possible by the contributions of CIRA and their Community Investment Program. 40

References (1 of 5) • "Hackers Attack Every 39 Seconds. " Security Magazine, Feb. 2017, www. securitymagazine. com/articles/87787 -hackers-attack-every 39 -seconds. Accessed 3 Feb. 2021. • Rubenking, Neil J. "What to Do When You've Been Hacked. " PC Mag, July 2019, www. pcmag. com/how-to/what-to-do-when-youvebeen-hacked. Accessed 3 Feb. 2021. • "Cracking Passwords: 11 Password Attack Methods (And How They Work). " Data. Recovery. com, Sept. 2017, datarecovery. com/rd/cracking-passwords-11 -password-attackmethods-work/. Accessed 3 Feb. 2021. 41

References (2 of 5) • Johnson, Leighton. "Password Cracking. " Science. Direct, 2020, www. sciencedirect. com/topics/computer-science/password-cracking. Accessed 3 Feb. 2021. • Zurkus, Kacy. "Are hackers gonna hack anymore? Not if we keep reusing passwords. " Malwarebytes, Nov. 2019, blog. malwarebytes. com/cybercrime/2019/03/hackers-gonna-hackanymore-not-keep-reusing-passwords/. Accessed 3 Feb. 2021. • "What is a rootkit? " Emsisoft, blog. emsisoft. com/en/29468/rootkits/. Accessed 3 Feb. 2021. 42

References (3 of 5) • Johansen, Alison G. "What is antivirus software? " Norton, Feb. 2019, https: //us. norton. com/internetsecurity-malware-what-isantivirus. html. Accessed 4 Feb. 2021. • “What is a computer virus? " Norton, https: //us. norton. com/internetsecurity-malware-what-isantivirus. html. Accessed 4 Feb. 2021. • "What Is Ransomware? " Mc. Afee, www. mcafee. com/enterprise/enca/security-awareness/ransomware. html. Accessed 4 Feb. 2021. 43

References (4 of 5) • Grimes, Roger A. "15 signs you've been hacked—and how to fight back. " CSO, Aug. 2020, www. csoonline. com/article/2457873/signsyouve-been-hacked-and-how-to-fight-back. html. Accessed 4 Feb. 2021. • "What is a DDo. S Attack? " Cloudflare, www. cloudflare. com/engb/learning/ddos/what-is-a-ddos-attack/. Accessed 4 Feb. 2021. 44

References (5 of 5) • Zamora, Wendy. "10 ways to protect against hackers. " Malwarebytes, Aug. 2018, blog. malwarebytes. com/101/2015/10/10 -ways-to-protect-against-hackers/. Accessed 4 Feb. 2021. • Patel, Raisa, and Phillip Ling. "CRA shuts down online services after thousands of accounts breached in cyberattacks. " Malwarebytes, Aug. 2020, www. cbc. ca/news/politics/canada-revenue-agency-cracyberattack-1. 5688163. Accessed 4 Feb. 2021. 45