Combination of Mono Alphabetic Transposition Cipher Presented by

Combination of Mono. Alphabetic &Transposition Cipher Presented by 1) Shahid Mumtaz Khan Shahrukh 2) Ahsan Bari 4) Hafiz Amir Nawaz 4) Awais Haider 5) Ali Harris 6) Syed Ahmed Ali Shah
Mono. Alphabetic cipher • Substitution ciphers are probably the most common form of cipher. They work by replacing each letter of the plaintext with another. A monoalphabetic substitution cipher, also known as a simple substitution cipher, relies on a fixed replacement structure. That is, the substitution is fixed for each letter of the alphabet. Thus, if "a" is encrypted to "R", then every time we see the letter "a" in the plaintext, we replace it with the letter "R" in the ciphertext.
Mono. Alphabetic cipher • • • Mixed Alphabetic cipher Caeser cipher Atbash cipher Pigpen cipher Affine cipher
Transposition cypher Transposition Ciphers are a bit different to Substitution Ciphers. Whereas Substitution ciphers replace each letter with a different letter or symbol to produce the ciphertext, in a Transposition cipher, the letters are just moved around. The letters or words of the plaintext are reordered in some way, fixed by a given rule (the key). • Columner cipher • Rail fence cipher • Route cipher • Myzskohski cipher • Permutation cypher
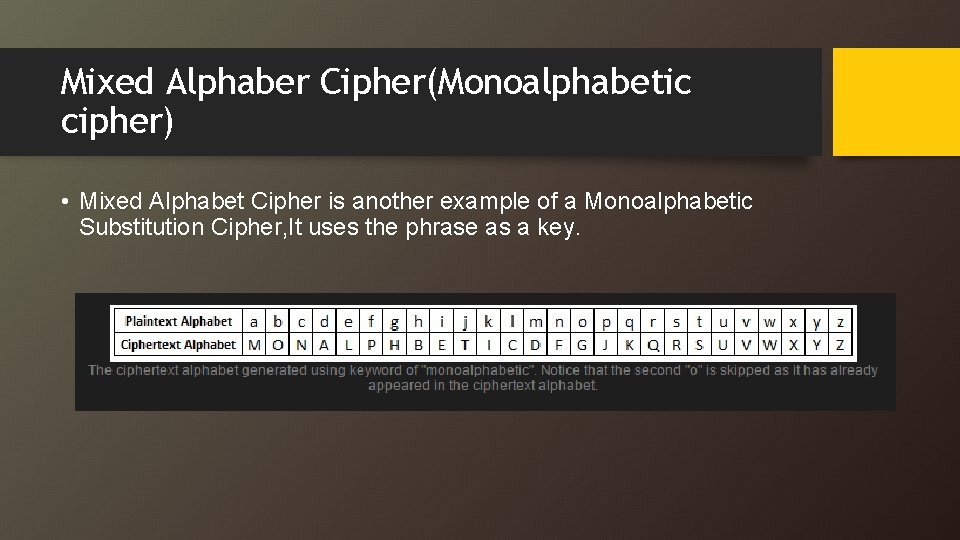
Mixed Alphaber Cipher(Monoalphabetic cipher) • Mixed Alphabet Cipher is another example of a Monoalphabetic Substitution Cipher, It uses the phrase as a key.

Mixed Alphaber Cipher(Monoalphabetic cipher) • Clearly it is not feasible to attack such a cipher with a brute force attack, and because of this, one might suppose that the Mixed Alphabet Cipher is a very secure cipher. 26! = 403, 291, 461, 126, 605, 635, 584, 000
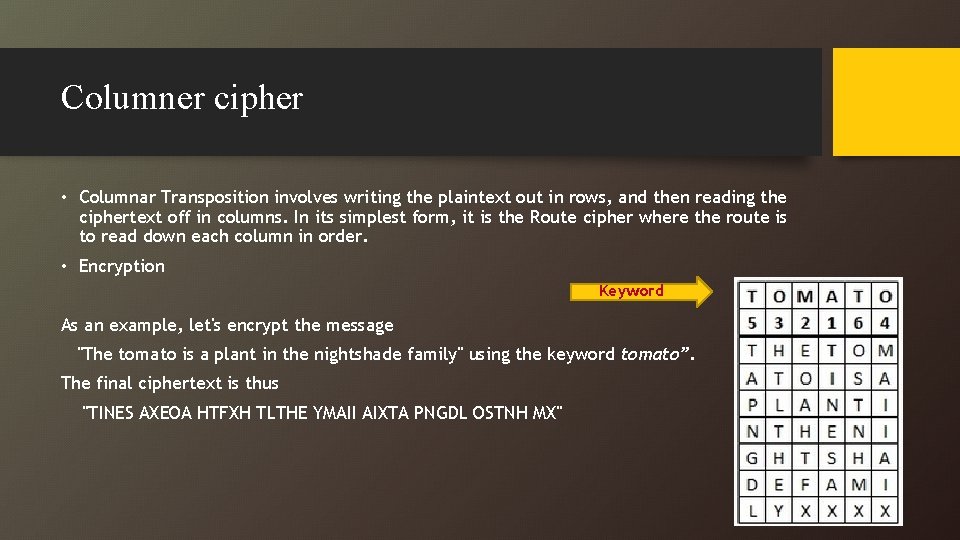
Columner cipher • Columnar Transposition involves writing the plaintext out in rows, and then reading the ciphertext off in columns. In its simplest form, it is the Route cipher where the route is to read down each column in order. • Encryption Keyword As an example, let's encrypt the message "The tomato is a plant in the nightshade family" using the keyword tomato”. The final ciphertext is thus "TINES AXEOA HTFXH TLTHE YMAII AIXTA PNGDL OSTNH MX"
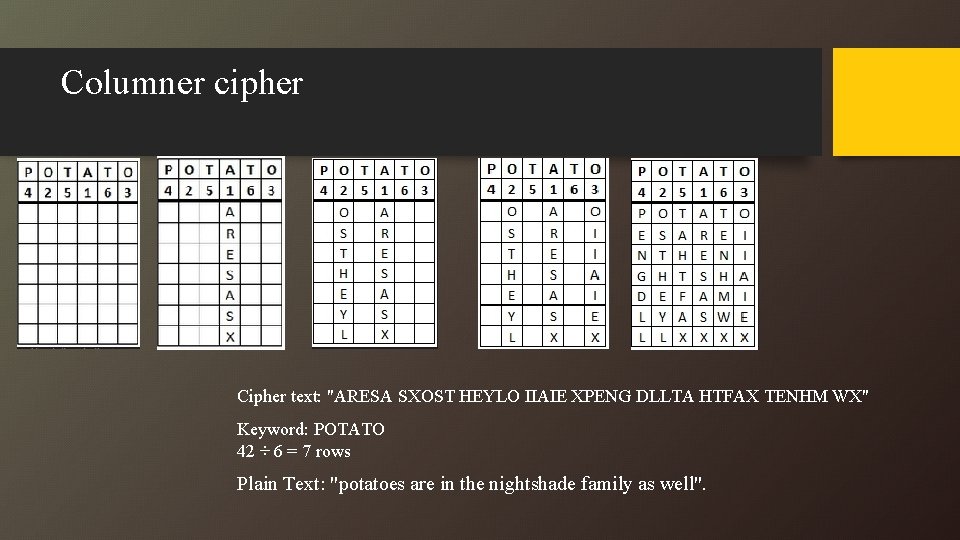
Columner cipher Cipher text: "ARESA SXOST HEYLO IIAIE XPENG DLLTA HTFAX TENHM WX" Keyword: POTATO 42 ÷ 6 = 7 rows Plain Text: "potatoes are in the nightshade family as well".

Combination Cipher • A Combination Cipher is a Cipher using 2 or more codes. • Both Mono. Alphabetic and simple transposition cipher are susceptible to different means of cryptanalysis, and neither has been secure for quite some time. Even more so, with the invention of the computer, these types of codes have fallen, and are not used for any truly important pieces of information. • However, by combining them, we can take the strengths of both systems, and dramatically reduce the weaknesses of either. A piece of ciphertext that has been encrypted with both of these simple ciphers would not have the letter frequencies equal to the native language but when frequency analysis is attempted, the letters are in no coherent order.
Combination Cipher • The best way to combine these two systems is to use the Mixed Alphabetic cipher , alongside the columner transposition cipher. • To do this we use either a single keyword for both, or two keywords, and perform one cipher after the other. It does not matter which order they are performed, but it is usually easier to do the transposition first, and substitute at the end.
• As an example we shall encrypt the plaintext "a fool thinks himself wise, but a wise man knows himself to be a fool", and we shall use the keyword william. We start by making up our grid for the Columnar Transposition. • This grid is then read off, down the columns to get the first step in the encryption process:
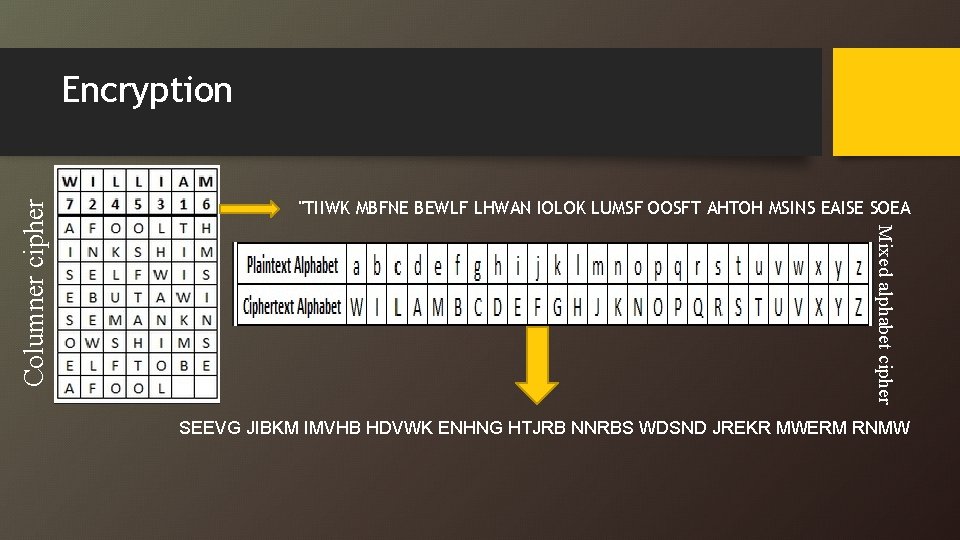
"TIIWK MBFNE BEWLF LHWAN IOLOK LUMSF OOSFT AHTOH MSINS EAISE SOEA Mixed alphabet cipher Columner cipher Encryption SEEVG JIBKM IMVHB HDVWK ENHNG HTJRB NNRBS WDSND JREKR MWERM RNMW
Decryption • The decryption process when using two ciphers combined is to take it one step at a time. First undo the substitution using the ciphertext alphabet. Once this is done, you must then reorder the letters using the transposition grid. These individual processes are identical to the decryption techniques we saw in Mixed cipher and columner cipher.
- Slides: 13