Collisions for StepReduced SHA 256 Ivica Nikoli Alex







- Slides: 14

Collisions for Step-Reduced SHA 256 Ivica Nikolić, Alex Biryukov University of Luxembourg

Outline § Short description of SHA-256 § Difference between SHA-1 and SHA-2 § Technique for finding collisions for SHA-256 § 20 -step reduced SHA-256 § 21 -step reduced SHA-256 § 23 -step reduced SHA-256 § 25 -step reduced SHA-256 § Conclusions

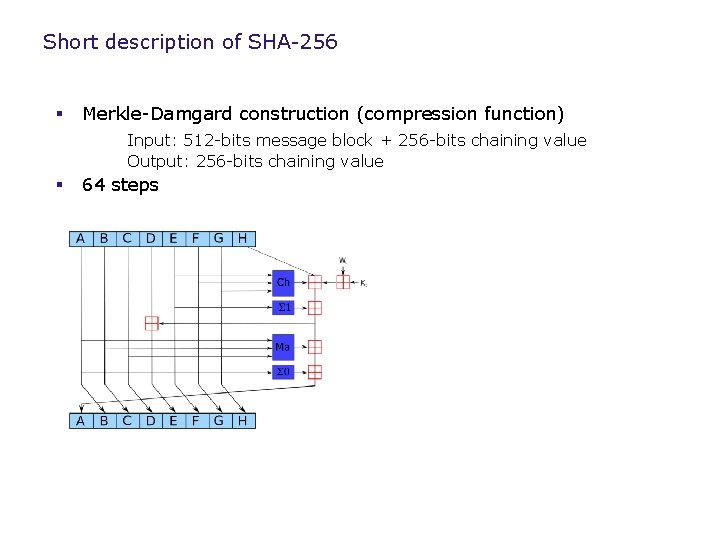
Short description of SHA-256 § Merkle-Damgard construction (compression function) Input: 512 -bits message block + 256 -bits chaining value Output: 256 -bits chaining value § 64 steps

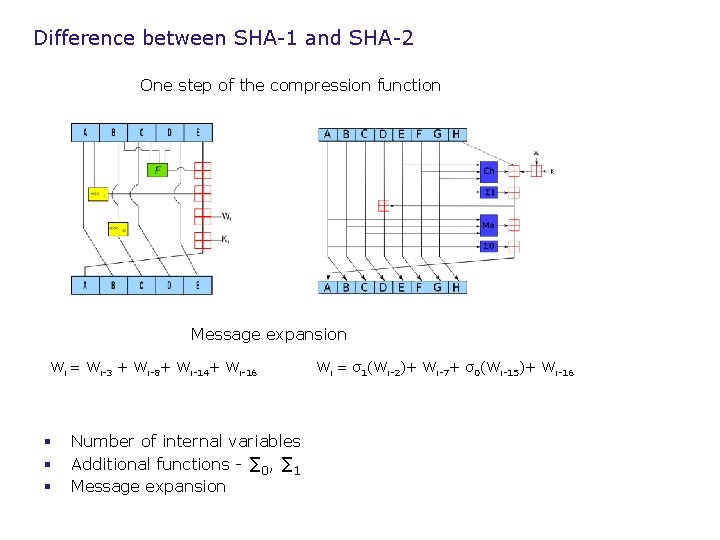
Difference between SHA-1 and SHA-2 One step of the compression function Message expansion Wi = Wi-3 + Wi-8+ Wi-14+ Wi-16 § § § Number of internal variables Additional functions - ∑ 0, ∑ 1 Message expansion Wi = σ1(Wi-2)+ Wi-7+ σ0(Wi-15)+ Wi-16

Difference between SHA-1 and SHA-2 Limit the influence of the new innovations § Additional functions (∑ 0, ∑ 1) Find fixed points, i. e. ∑(x)=x. If x, y are fixed points then ∑(x)- ∑(y)=x-y, i. e. ∑ preserves difference. § Message expansion Expanded words don’t use words with differences.

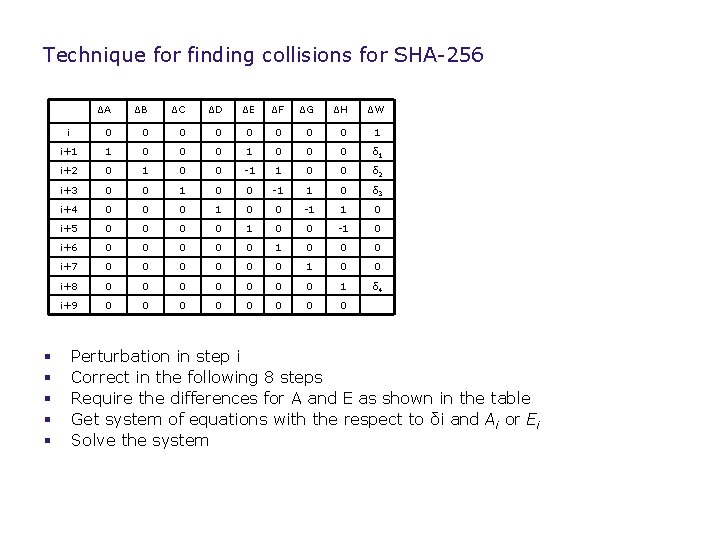
Technique for finding collisions for SHA-256 General technique § Introduce perturbation § Use as less differences as possible to correct the perturbation in the following 8 steps § After the perturbation is gone don’t allow any other new perturbations

Technique for finding collisions for SHA-256 § § § ΔA ΔB ΔC ΔD ΔE ΔF ΔG ΔH ΔW i 0 0 0 0 1 i+1 1 0 0 0 δ 1 i+2 0 1 0 0 -1 1 0 0 δ 2 i+3 0 0 1 0 0 -1 1 0 δ 3 i+4 0 0 0 1 0 0 -1 1 0 i+5 0 0 1 0 0 -1 0 i+6 0 0 0 1 0 0 0 i+7 0 0 0 1 0 0 i+8 0 0 0 0 1 δ 4 i+9 0 0 0 0 Perturbation in step i Correct in the following 8 steps Require the differences for A and E as shown in the table Get system of equations with the respect to δi and Ai or Ei Solve the system

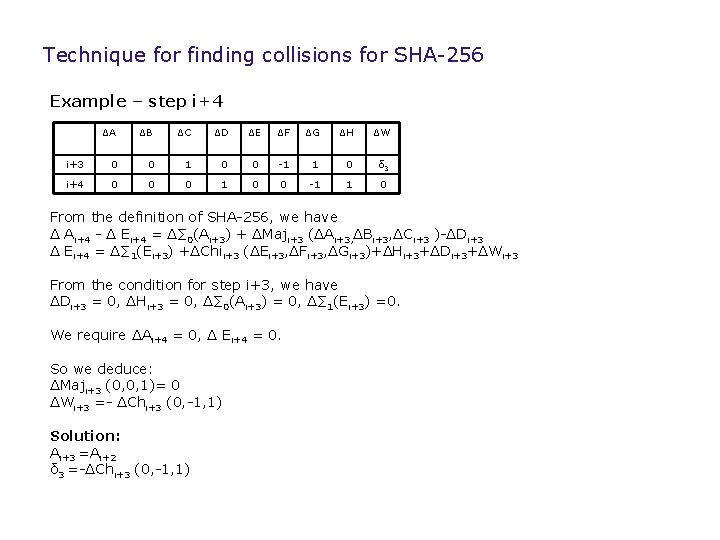
Technique for finding collisions for SHA-256 Example – step i+4 ΔA ΔB ΔC ΔD ΔE ΔF ΔG ΔH ΔW i+3 0 0 1 0 0 -1 1 0 δ 3 i+4 0 0 0 1 0 0 -1 1 0 From the definition of SHA-256, we have Δ Ai+4 - Δ Ei+4 = Δ∑ 0(Ai+3) + ΔMaji+3 (ΔAi+3, ΔBi+3, ΔCi+3 )-ΔDi+3 Δ Ei+4 = Δ∑ 1(Ei+3) +ΔChii+3 (ΔEi+3, ΔFi+3, ΔGi+3)+ΔHi+3+ΔDi+3+ΔWi+3 From the condition for step i+3, we have ΔDi+3 = 0, ΔHi+3 = 0, Δ∑ 0(Ai+3) = 0, Δ∑ 1(Ei+3) =0. We require ΔAi+4 = 0, Δ Ei+4 = 0. So we deduce: ΔMaji+3 (0, 0, 1)= 0 ΔWi+3 =- ΔChi+3 (0, -1, 1) Solution: Ai+3 =Ai+2 δ 3 =-ΔChi+3 (0, -1, 1)

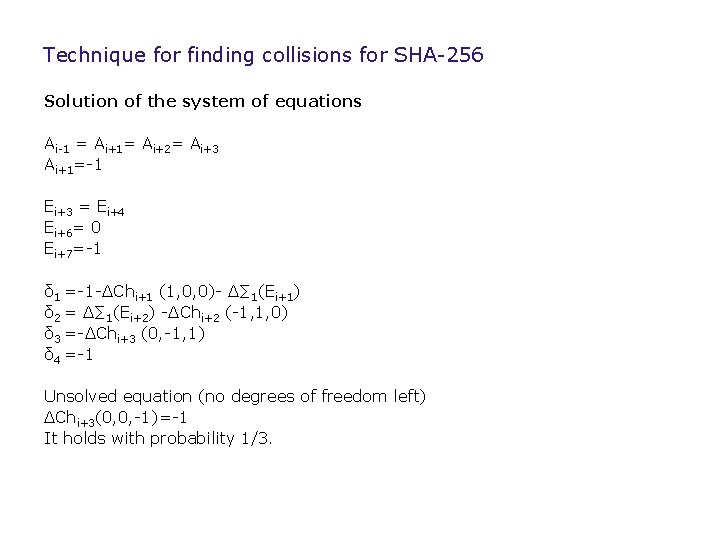
Technique for finding collisions for SHA-256 Solution of the system of equations Ai-1 = Ai+1= Ai+2= Ai+3 Ai+1=-1 Ei+3 = Ei+4 Ei+6= 0 Ei+7=-1 δ 1 =-1 -ΔChi+1 (1, 0, 0)- Δ∑ 1(Ei+1) δ 2 = Δ∑ 1(Ei+2) -ΔChi+2 (-1, 1, 0) δ 3 =-ΔChi+3 (0, -1, 1) δ 4 =-1 Unsolved equation (no degrees of freedom left) ΔChi+3(0, 0, -1)=-1 It holds with probability 1/3.

20 -step reduced SHA-256 W 0 0 x 1 1 2 3 4 5 6 7 8 9 10 11 12 13 14 x 2 x 4 § Corrections in W 6, W 7, W 8, W 13. x 5 x 6 x 7 § Message expansion after the step 13 doesn’t use any of these words x 8 x 9 x 10 x 11 § Complexity = 1/3 x 12 x 13 x 14 x 15 x x 17 18 x 19 20 x 21 22 Collision § Perturbation in W 5. x 3 16 15 x x x x x x x x x x x x x

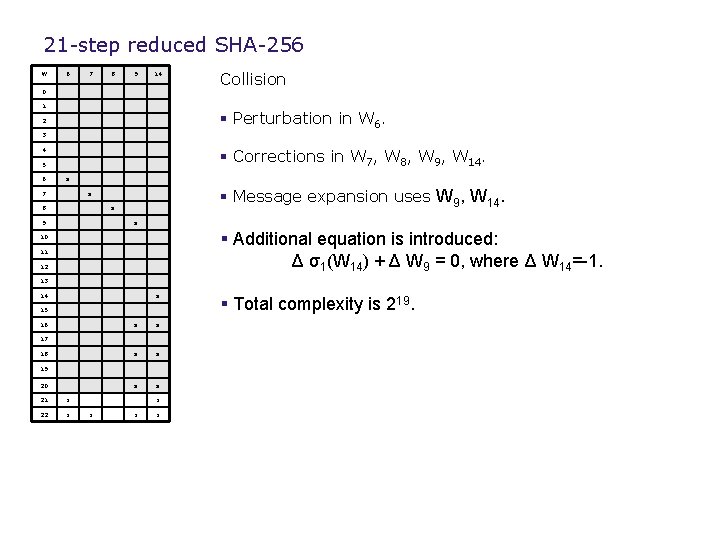
21 -step reduced SHA-256 W 6 7 8 9 14 0 1 Collision § Perturbation in W 6. 2 3 4 § Corrections in W 7, W 8, W 9, W 14. 5 6 x 7 § Message expansion uses W 9, W 14. x 8 x 9 x § Additional equation is introduced: Δ σ1(W 14) + Δ W 9 = 0, where Δ W 14=-1. 10 11 12 13 14 x 15 16 x x x 17 18 19 20 21 x 22 x x x § Total complexity is 219.

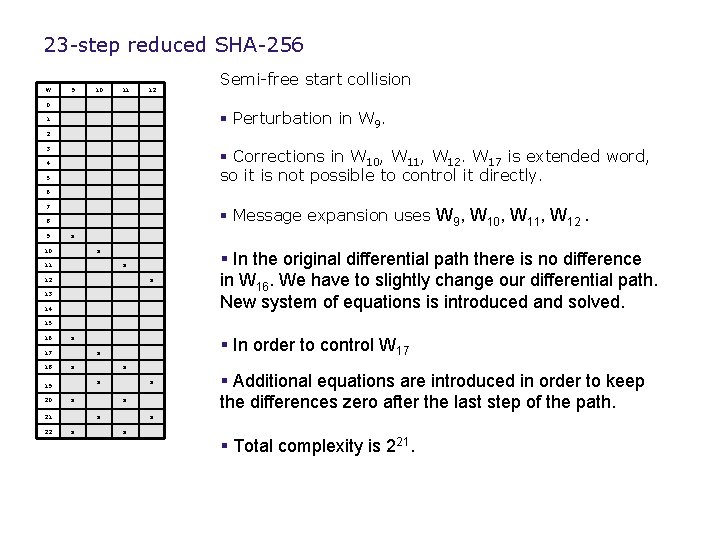
23 -step reduced SHA-256 W 9 10 11 12 0 Semi-free start collision § Perturbation in W 9. 1 2 3 § Corrections in W 10, W 11, W 12. W 17 is extended word, so it is not possible to control it directly. 4 5 6 7 § Message expansion uses W 9, W 10, W 11, W 12. 8 9 x 10 x 11 x 12 x 13 14 § In the original differential path there is no difference in W 16. We have to slightly change our differential path. New system of equations is introduced and solved. 15 16 x 17 18 x x 21 22 x x 19 20 § In order to control W 17 x x x § Additional equations are introduced in order to keep the differences zero after the last step of the path. x x § Total complexity is 221.

25 -step reduced SHA-256 W 9 10 11 12 0 Semi-free start near collision with Hamming distance of 17 bits 1 § Extend semi-free start collision for 23 -step reduced SHA-256. 2 3 4 5 § Minimize the Hamming distance of the introduced differences for A and E registers. 6 7 8 9 x 10 § Total complexity is 234. x 11 x 12 x 13 14 15 16 x 17 18 x x 19 20 x 21 22 x x x x

Conclusions § Technique applicable to SHA-224, SHA-384, and SHA-512. § No real treat for the security of SHA-2.