Coherent Navigation Candidate Non Cryptographic GNSS Spoofing Detection








- Slides: 21

Coherent Navigation Candidate Non. Cryptographic GNSS Spoofing Detection Techniques Brent Ledvina*, Isaac Miller, Bryan Galusha, William Bencze, and Clark Cohen, Coherent Navigation, Inc. GNSS Security Splinter Meeting, Portland, OR 23 September 2010 *Adjunct Professor at Virginia Tech

Coherent Navigation Protecting Civil GPS Receivers § Critical infrastructure relies on civil GPS navigation and timing § Electrical grid timing and control § Banking/financial transactions § Commercial aircraft guidance and landing § Communication systems (cellular) § Public transportation § Asset tracking § Commercial fishing monitoring § Vehicle mileage taxation § Monitoring criminals Non-cryptographic spoofing defenses provide some protection to civil GNSS receivers 9/23/2010

Coherent Navigation Goal and Motivation § Goal § Illustrate six candidate non-cryptographic spoofing detection techniques § Motivation § Non-cryptographic spoofing detection techniques could be implemented today § Non-cryptographic defenses are needed if one is concerned with encryption or authentication key security breaches 9/23/2010

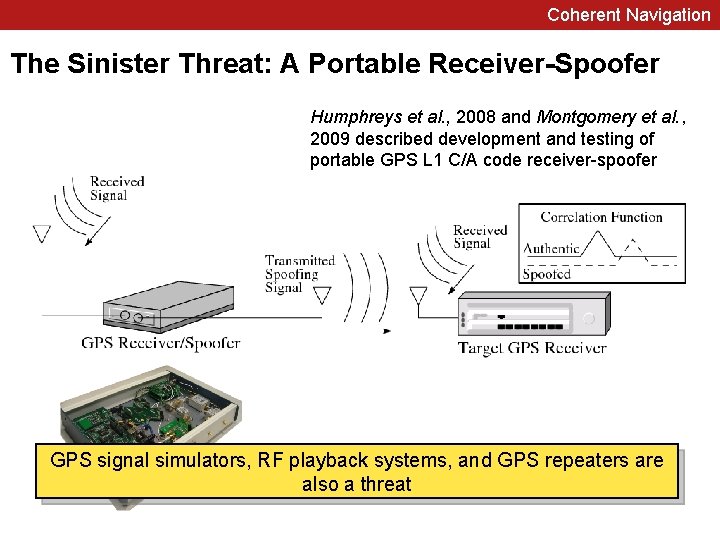
Coherent Navigation The Sinister Threat: A Portable Receiver-Spoofer Humphreys et al. , 2008 and Montgomery et al. , 2009 described development and testing of portable GPS L 1 C/A code receiver-spoofer GPS signal simulators, RF playback systems, and GPS repeaters are also a threat

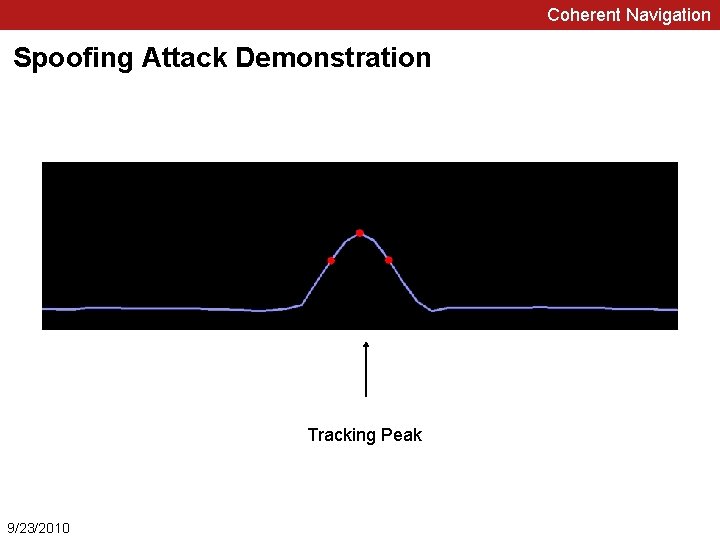
Coherent Navigation Spoofing Attack Demonstration Tracking Peak 9/23/2010

Coherent Navigation Candidate Spoofing Defenses/Detection Techniques 1 Standalone Receiver-Based § § § § § 2 Monitor the relative GPS signal strength Monitor satellite identification codes and the number of satellite Defenses suggested by signals received Dept. of Homeland Security (2003) in italics Check the time intervals Do a time comparison (look at code phase jitter) Monitor the absolute GPS signal strength Data bit latency detection Vestigial signal detection Signal quality monitoring Employ two antennas; check relative phase against know satellite directions Extended RAIM External-Aiding § § 3 Perform a sanity check with relative position estimate (compare with IMU) Compare with independent absolute position or time-bearing information (e. g. , Galileo and GLONASS) Cryptographic § § 9/23/2010 Encrypt navigation message Spreading code authentication

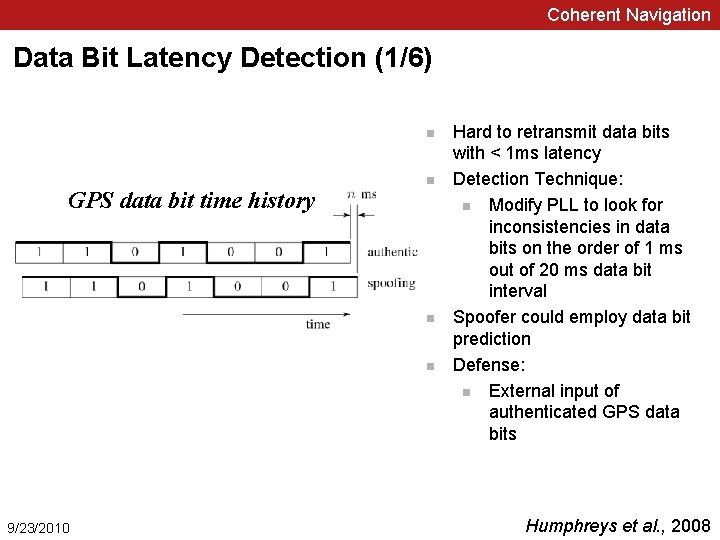
Coherent Navigation Data Bit Latency Detection (1/6) n GPS data bit time history n n n 9/23/2010 Hard to retransmit data bits with < 1 ms latency Detection Technique: n Modify PLL to look for inconsistencies in data bits on the order of 1 ms out of 20 ms data bit interval Spoofer could employ data bit prediction Defense: n External input of authenticated GPS data bits Humphreys et al. , 2008

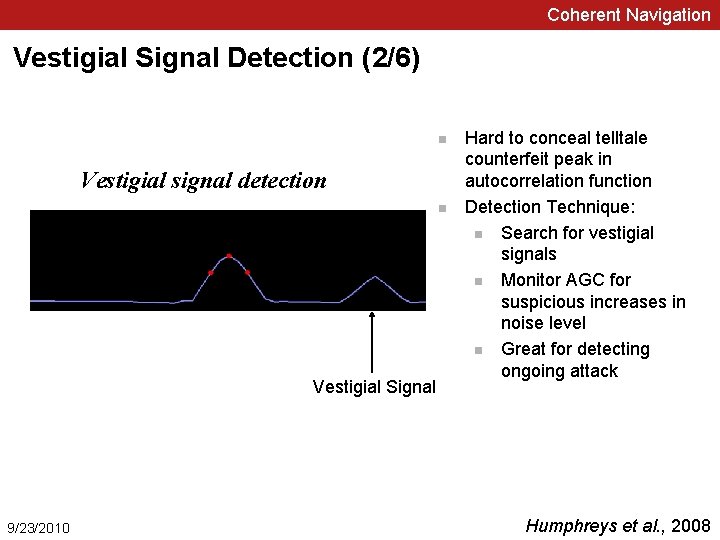
Coherent Navigation Vestigial Signal Detection (2/6) n Vestigial signal detection n Vestigial Signal 9/23/2010 Hard to conceal telltale counterfeit peak in autocorrelation function Detection Technique: n Search for vestigial signals n Monitor AGC for suspicious increases in noise level n Great for detecting ongoing attack Humphreys et al. , 2008

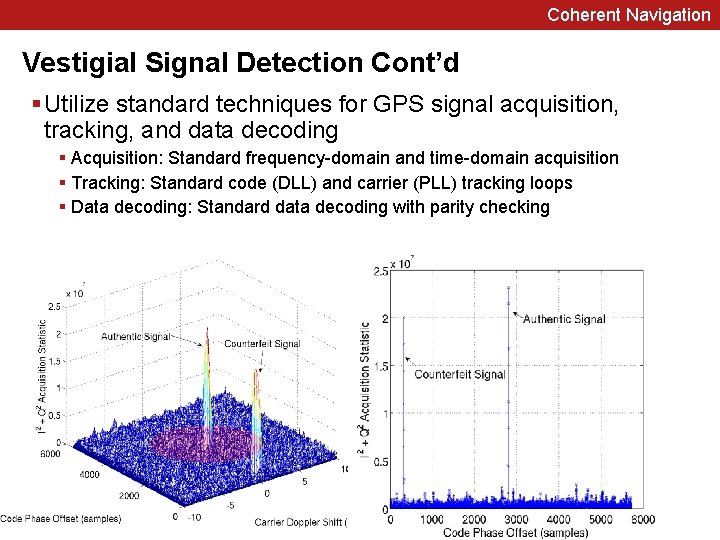
Coherent Navigation Vestigial Signal Detection Cont’d § Utilize standard techniques for GPS signal acquisition, tracking, and data decoding § Acquisition: Standard frequency-domain and time-domain acquisition § Tracking: Standard code (DLL) and carrier (PLL) tracking loops § Data decoding: Standard data decoding with parity checking

Coherent Navigation Extended Receiver Autonomous Integrity Monitoring (RAIM) (3/6) § RAIM provides statistical method to detect signal with unacceptable pseudorange error and remove it from navigation solution § Vestigial signals could appear at an erroneous pseudorange or carrier Doppler shift frequency § Extend RAIM to include carrier Doppler shift frequency § Create single test statistic based on pseudorange and carrier Doppler shift frequency measurements § Test statistic is normalized chi-square random variable with 2*N – 8 degrees of freedom, where N is number of tracking signals § Provides statistical hypothesis test to throw out at least 1 signal Ledvina et al. , ION NTM 2010

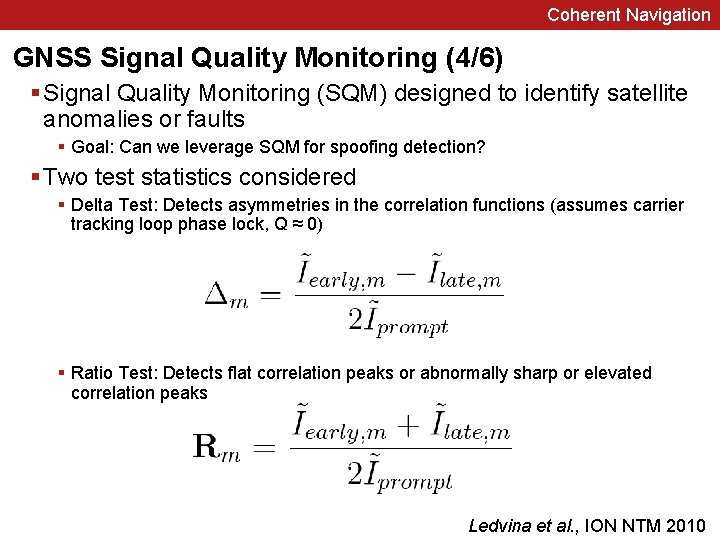
Coherent Navigation GNSS Signal Quality Monitoring (4/6) § Signal Quality Monitoring (SQM) designed to identify satellite anomalies or faults § Goal: Can we leverage SQM for spoofing detection? § Two test statistics considered § Delta Test: Detects asymmetries in the correlation functions (assumes carrier tracking loop phase lock, Q ≈ 0) § Ratio Test: Detects flat correlation peaks or abnormally sharp or elevated correlation peaks Ledvina et al. , ION NTM 2010

Coherent Navigation Testing SQM: Two Spoofing Signal Alignment Techniques § Two ways a counterfeit signal interacts with authentic signal § 1. Counterfeit signal marches into code phase alignment with authentic signal § 2. Counterfeit signal is code-phase aligned with authentic signals and grows in amplitude § Do not necessarily assume carrier phase alignment § Requires cm-level knowledge of 3 -D vector between spoofer and target receiver § Assume spoofer has a priori knowledge of 12. 5 -minute GPS navigation message 9/23/2010

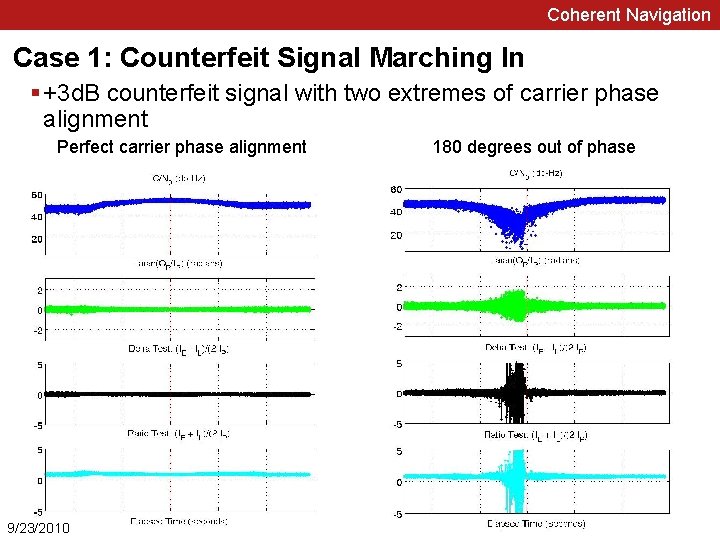
Coherent Navigation Case 1: Counterfeit Signal Marching In § +3 d. B counterfeit signal with two extremes of carrier phase alignment Perfect carrier phase alignment 9/23/2010 180 degrees out of phase

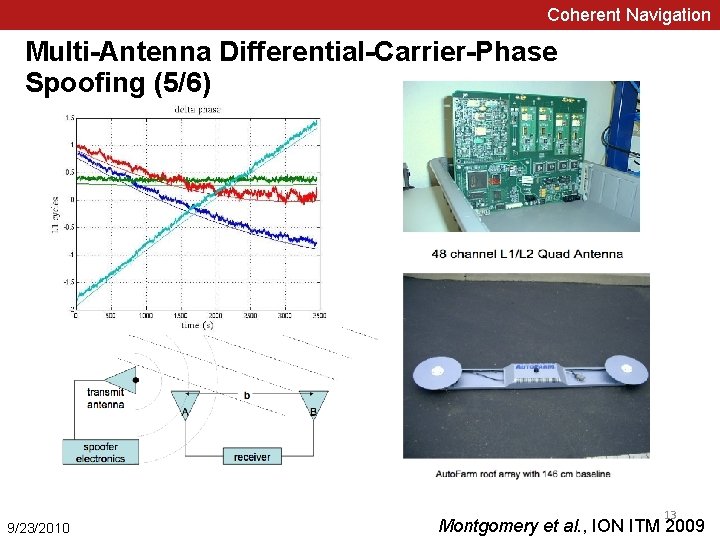
Coherent Navigation Multi-Antenna Differential-Carrier-Phase Spoofing (5/6) 9/23/2010 13 Montgomery et al. , ION ITM 2009

Coherent Navigation External Aiding: High-Quality Frequency Reference (6/6) §Time and Frequency Synchronization via GPS Receivers § 70% of GPS receivers are utilized for timing applications providing time and frequency reference sources §GPS timing receivers § Implemented with a high-quality crystal oscillator, a coupled GPS receiver, and control logic § Control logic cross-checks with high-quality oscillator providing some protection against GPS time spoofing attacks • Control logic implementation and oscillator quality primarily dictate rate at which time spoofing attack can be successfully carried out Symmetricom XL-GPS Time and Frequency Receiver 9/23/2010

Coherent Navigation Conclusions § Described six candidate spoofing detection techniques § Spoofing detection § Simple software-based solutions provide some protection § Multi-antenna differential carrier phase and external aiding provide more protection § Strength of each detection scheme needs to be mathematically defined and tested to understand protection level § Best Non-Cryptographic Spoofing Detection Technique Multi-Antenna Differential Carrier Phase Spoofing Detection Technique

Coherent Navigation Back-Up Slides 9/23/2010

Coherent Navigation Additional Observations Relevant to Signal Quality Monitoring § Counterfeit signal +1 d. B above an authentic signal can cause successful lift-off § +3 d. B counterfeit signal up to 30 degrees out-of-phase causes detectable deconstructive interference § Time rate of attack shortens deconstructive interference period, and thus shortens time in which an attack can be detected § Code tracking loop bandwidth becomes important for fast attacks § Data bit latency or data bit errors causes deconstructive interference, thereby improving detection 9/23/2010

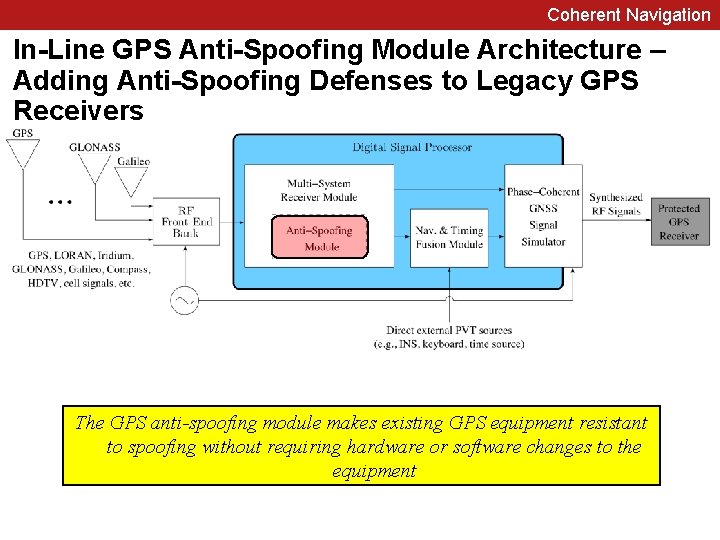
Coherent Navigation In-Line GPS Anti-Spoofing Module Architecture – Adding Anti-Spoofing Defenses to Legacy GPS Receivers The GPS anti-spoofing module makes existing GPS equipment resistant to spoofing without requiring hardware or software changes to the equipment

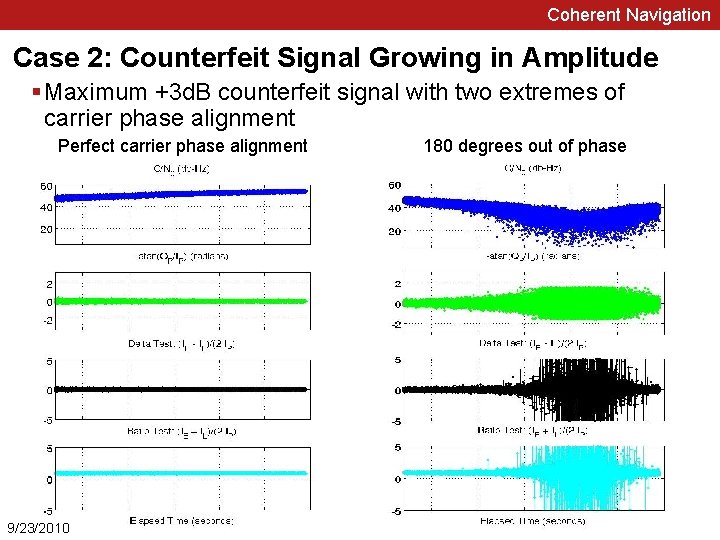
Coherent Navigation Case 2: Counterfeit Signal Growing in Amplitude § Maximum +3 d. B counterfeit signal with two extremes of carrier phase alignment Perfect carrier phase alignment 9/23/2010 180 degrees out of phase

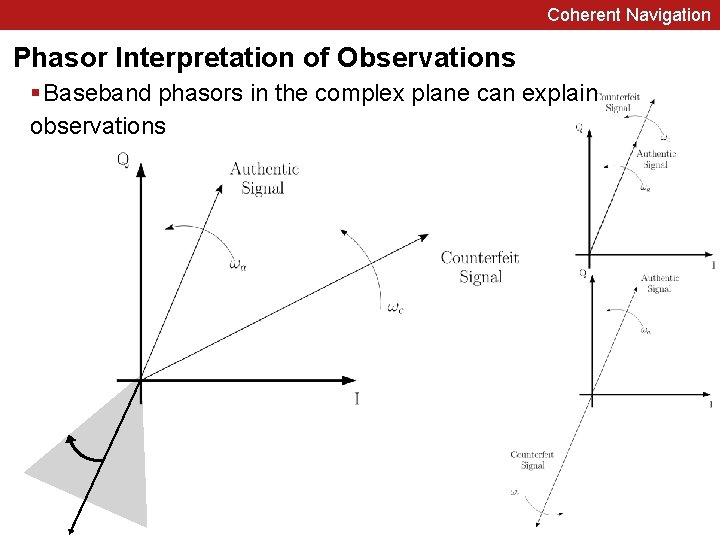
Coherent Navigation Phasor Interpretation of Observations § Baseband phasors in the complex plane can explain observations