Coexistence Among Cryptography and Noisy Data Theory and









- Slides: 23

Coexistence Among Cryptography and Noisy Data Theory and Applications Alawi A. Al-Saggaf, Ph. D. King Fahd University of Petroleum and Minerals, alawi@kfupm. edu. sa 28 th April, 2014

Motivations for Current Research 2

Motivations for Current Research The bad news about Password and smart card breaches: - Password may be forgotten, easy to guess, difficult to remember. Passwords cracking (such as John the Ripper) easily to defeat the hash value of the password. Smart cad may be lost, stolen, easy to share.

Who Are You?

Motivations for Current Research (Cont’d) Motivations for Current Research 5

Why Biometrics?

Security Level Robustness Method 7

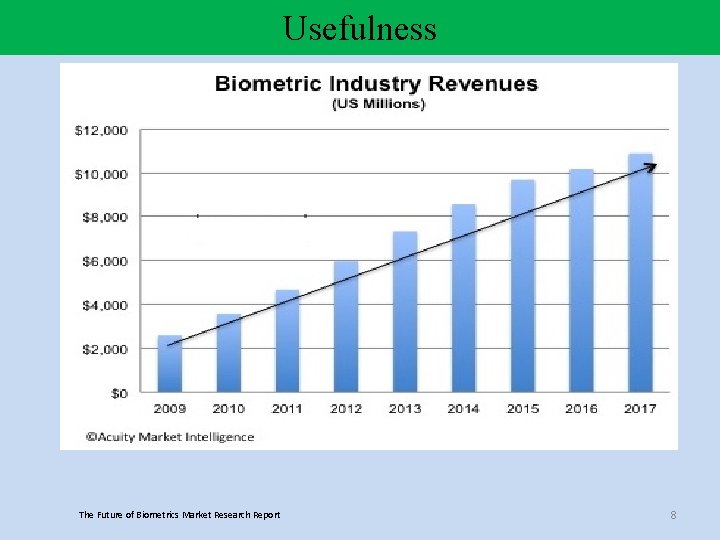
Usefulness The Future of Biometrics Market Research Report 8

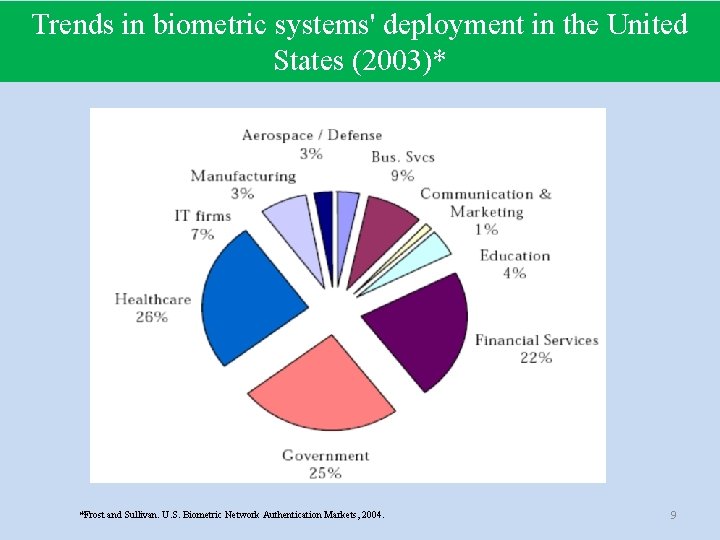
Trends in biometric systems' deployment in the United States (2003)* *Frost and Sullivan. U. S. Biometric Network Authentication Markets, 2004. 9

Biometrics Template Attacks

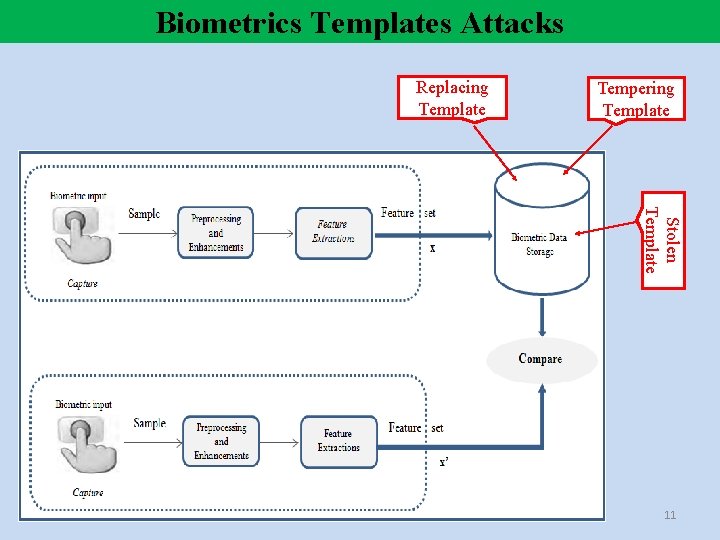
Biometrics Templates Attacks Replacing Template Tempering Template Stolen Template 11

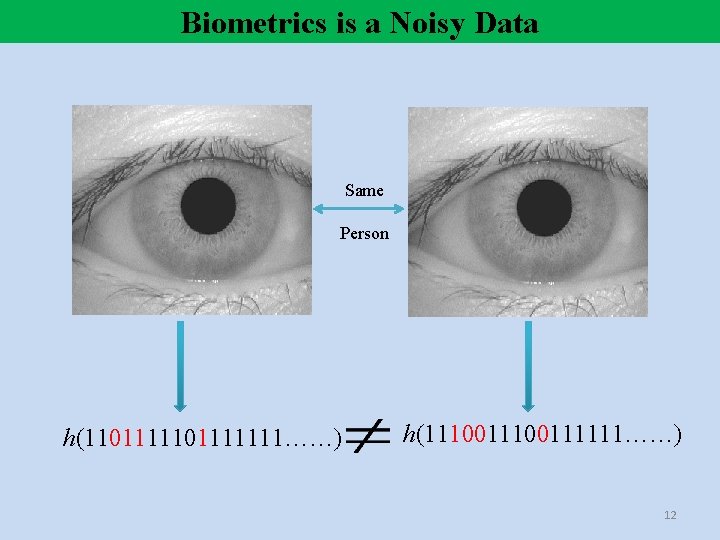
Biometrics is a Noisy Data Same Person h(1101111111……) h(11100111111……) 12

Mathematical framework For Coexistence among Cryptography and Noisy Data

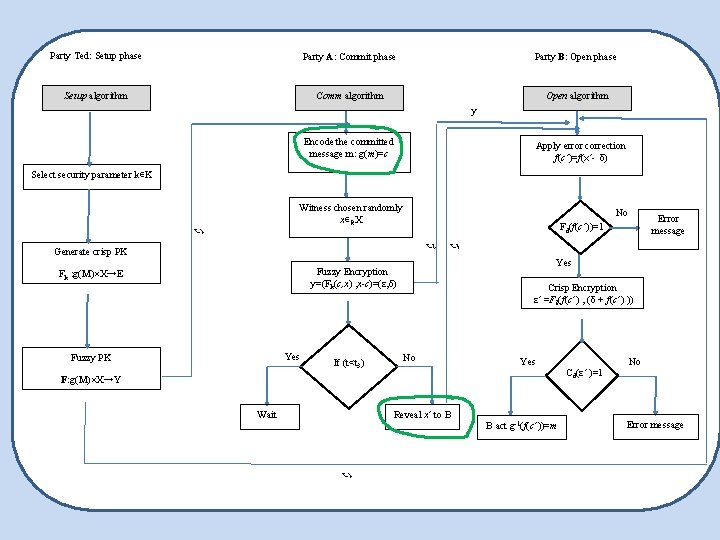
Party Ted: Setup phase Party A: Commit phase Party B: Open phase Setup algorithm Comm algorithm Open algorithm y Encode the committed message m: g(m)=c Apply error correction f(c’)=f(x’- δ) Select security parameter k∊K Witness chosen randomly x∊RX t 1 No t 2 Generate crisp PK Yes Fuzzy PK If (t<t 3) t 3 Yes Fuzzy Encryption y=(Fk(c, x) , x-c)=(ε, δ) Fk : g(M)×X→E Crisp Encryption ε’ =Fk(f(c’) , (δ + f(c’) )) No Yes F: g(M)×X→Y Wait Reveal x’ to B t 1 Error message Fd(f(c’))=1 B act g-1(f(c’))=m Cd(ε’ )=1 No Error message

Security Analysis

Bound derivation for hiding property Theorem 5. 1: Suppose that (witness space) and (error correcting code set) are two independent random variables over the sample space , and let be a random variable (difference vector) obtained by “exclusive OR” of elements of and. Then the probability that an attacker is able to compute either or from the difference vector is no more than , where is the size of the error correcting code. 16

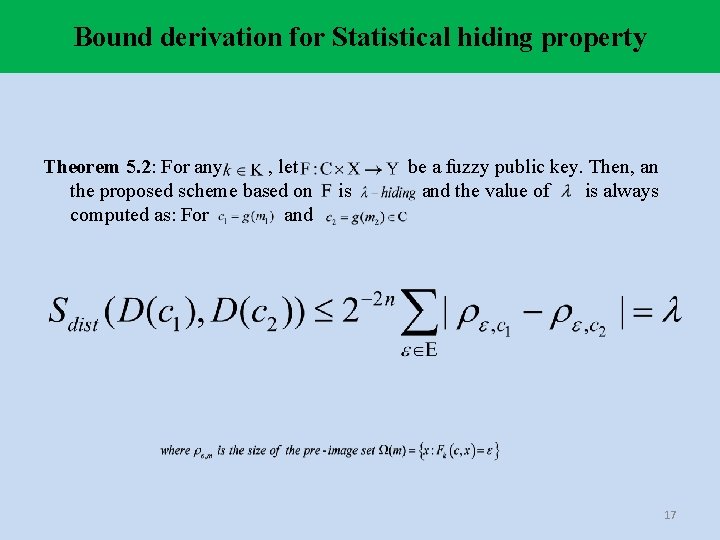
Bound derivation for Statistical hiding property Theorem 5. 2: For any , let the proposed scheme based on computed as: For and is be a fuzzy public key. Then, an and the value of is always 17

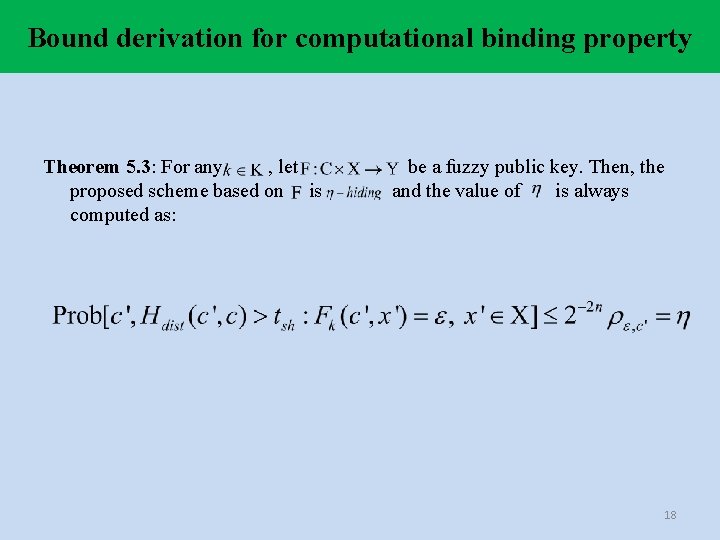
Bound derivation for computational binding property Theorem 5. 3: For any , let proposed scheme based on is computed as: be a fuzzy public key. Then, the and the value of is always 18

Applications

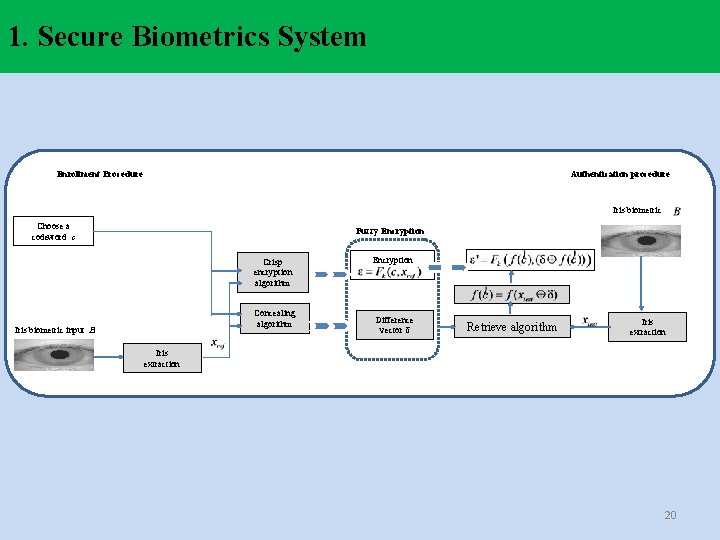
1. Secure Biometrics System Enrollment Procedure Authentication procedure Iris biometric Choose a codeword c Fuzzy Encryption Crisp encryption algorithm Concealing algorithm Iris biometric input B Encryption Difference vector δ Retrieve algorithm Iris extraction 20

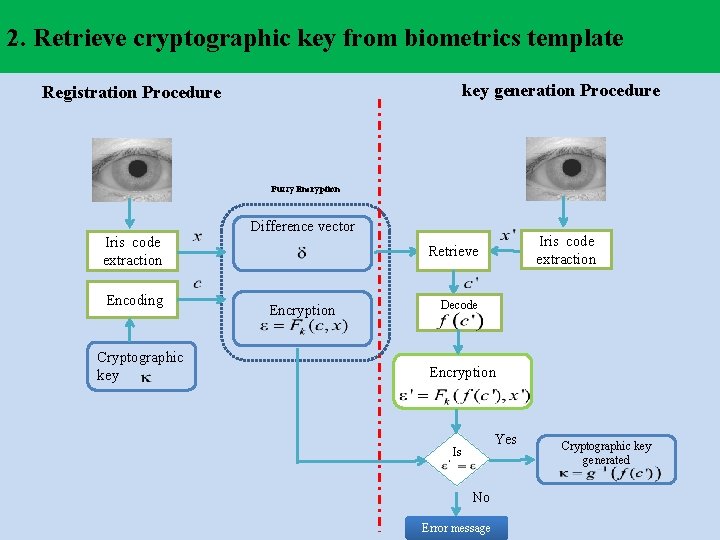
2. Retrieve cryptographic key from biometrics template key generation Procedure Registration Procedure Fuzzy Encryption Iris code extraction Encoding Cryptographic key Difference vector Iris code extraction Retrieve Encryption Decode Encryption Yes Is No Error message Cryptographic key generated

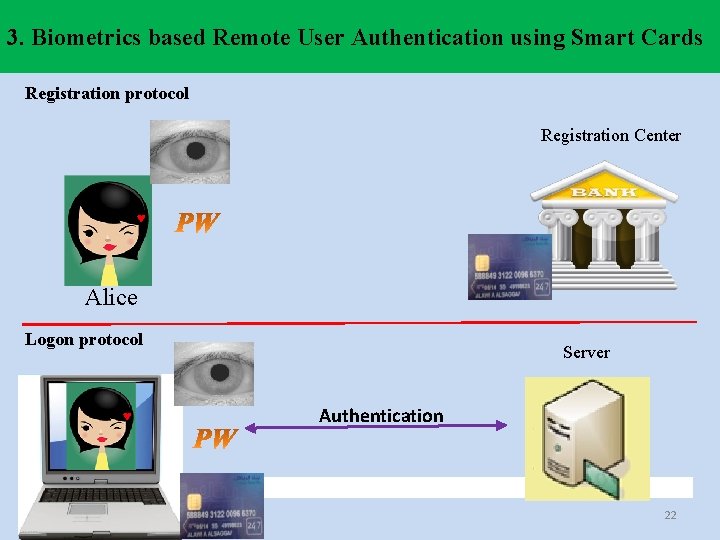
3. Biometrics based Remote User Authentication using Smart Cards Registration protocol Registration Center ♥ Alice Logon protocol ♥ Server Authentication 22

Thank you